Diffie hellman key algorithm
- 1. GANDHINAGAR INSTITUTE OF TECHNOLGY Department of Information Technology Diffie-Hellman Key Algorithm Group ID: IT_B1_00 Student Name(Enroll No): Shaishav Shah(170120116094) Name of Faculty: Prof. Alpa Oza INS(2170709)
- 2. Introduction • The Diffie-Hellman key agreement protocol was developed by Diffie and Hellman in 1976. • This protocol allows two users to exchange a secret key over an insecure medium without any prior secrets. • The protocol has two system parameters p and g. • They are both public and may be used by all users in a system. • Parameter p is a prime number and parameter g is an integer less than p, with the following property: – For every number n between 1 and p – 1 inclusive. – There is a power k of g such that n = 𝑔𝑘 𝑚𝑜𝑑 𝑝.
- 3. Introduction • The protocol depends on the discrete algorithm problem for its security. • It assumes that it is computationally infeasible to calculate the shared secret key 𝑘 = 𝑔𝑎𝑏 𝑚𝑜𝑑 𝑝 given the two public values 𝑔𝑎 𝑚𝑜𝑑 𝑝 and 𝑔𝑏 𝑚𝑜𝑑 𝑝 when the prime p is sufficiently large. • The Diffie – Hellman key exchange is vulnerable to a man-in-the- middle attack. • This vulnerability is present because Diffie-Hellman key exchange does not authenticate the participants. • Possible solutions include the use of digital signatures and other protocol variants.
- 4. Algorithm • Select two numbers: 1. Prime number 𝑞. 2. 𝛼 an integer that is a primitive root of 𝑞. • Suppose the users A and B wish to exchange a key. 1. User A select a random integer 𝑋𝐴 < 𝑞 and computes 𝑌 𝐴 = 𝛼𝑋𝐴 𝑚𝑜𝑑 𝑞. 2. User A select a random integer 𝑋𝐵 < 𝑞 and computes 𝑌𝐵 = 𝛼𝑋𝐵 𝑚𝑜𝑑 𝑞. 3. Both side keeps the X value private and makes the Y value available publicly to the other sides. 4. User A computes the key as 𝐾 = (𝑌𝐵)𝑋𝐴 𝑚𝑜𝑑 𝑞. 5. User B computes the key as 𝐾 = (𝑌𝐴)𝑋𝐵 𝑚𝑜𝑑 𝑞.
- 5. Algorithm • Both side gets same results: 𝐾 = (𝑌𝐵)𝑋𝐴 𝑚𝑜𝑑 𝑞 = (𝛼𝑋𝐵 𝑚𝑜𝑑 𝑞)𝑋𝐴 𝑚𝑜𝑑 𝑞 = (𝛼𝑋𝐵)𝑋𝐴 𝑚𝑜𝑑 𝑞 = 𝛼𝑋𝐵𝑋𝐴𝑚𝑜𝑑 𝑞 = (𝛼𝑋𝐴 𝑚𝑜𝑑 𝑞)𝑋𝐵 𝑚𝑜𝑑 𝑞 = (𝑌𝐴)𝑋𝐵 𝑚𝑜𝑑 𝑞
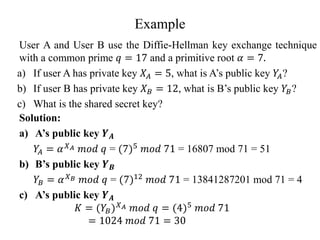
- 6. Example User A and User B use the Diffie-Hellman key exchange technique with a common prime 𝑞 = 17 and a primitive root 𝛼 = 7. a) If user A has private key 𝑋𝐴 = 5, what is A’s public key 𝑌 𝐴? b) If user B has private key 𝑋𝐵 = 12, what is B’s public key 𝑌𝐵? c) What is the shared secret key? Solution: a) A’s public key 𝒀𝑨 𝑌 𝐴 = 𝛼𝑋𝐴 𝑚𝑜𝑑 𝑞 = (7)5 𝑚𝑜𝑑 71 = 16807 mod 71 = 51 b) B’s public key 𝒀𝑩 𝑌𝐵 = 𝛼𝑋𝐵 𝑚𝑜𝑑 𝑞 = (7)12 𝑚𝑜𝑑 71 = 13841287201 mod 71 = 4 c) A’s public key 𝒀𝑨 𝐾 = (𝑌𝐵)𝑋𝐴 𝑚𝑜𝑑 𝑞 = (4)5 𝑚𝑜𝑑 71 = 1024 𝑚𝑜𝑑 71 = 30
- 7. Advantages 1. Any user can choose a random x and publish 𝑔𝑥 in a public database such as a phone book. 2. Phone book must be maintained by a TTP. 3. Other users can look up the database and get the public key for the individual and use it to encrypt the message. 4. Ideal for use with emails.
- 8. Disadvantages 1. Does not protect against man in middle attacks. 2. Even can intercept all traffic between Alice and Bob and generate separate keys for communication with them. 3. If Alice sends an encrypted message for Bob with his public key, Even simply forwards it. 4. For large prime 𝑝, 𝑝 − 1 is an even number and so 𝑍𝑝 ∗ will have an subgroup of order 2.
- 9. Thank You