lossless data compression and decompression using simple byte coding
- 2. Introduction Fundamentals of compression Technique Simple byte compression technique Simple byte decompression technique Results Conclusion
- 3. In multimedia application, the number of byte required to represent the data can be very large. This will increase computational complexity of the system like Transition activity, area, delay and power dissipation. To overcome these effects a simple byte compression algorithm with data coding Technique has been implemented. INTRODUCTION:
- 4. FUNDAMENTALS OF COMPRESSION TECHNIQUE: Compression is the art or science of representing information in a compact form. Data compression is essential need for modern day to day life, Because information are generated and used in digital form and is represented by array of data A compression technique consists of two basic components such as an encoding (Compression) and decoding (De compression) process. Original input data K Compressed data C(K) Output KDecompression Compression Message K Reconstructed data (K)
- 5. Classification of compression Based on the requirement of data compression it is broadly classified in to: Lossy Compression Lossless Compression Lossless compression Entropy Based Dictionary Based RLE Arithmetic Huffman Simple byte
- 6. Data Compression is always useful for encoding information using fewer bits than the original representation. There are many issues the size of information would affect data transmission as well as can affect the cost too. The idea of simple byte lossless compression algorithm is to reduce the standard 8 bit coding technique to some specific 5 bit coding technique. Assume random sample with 8 Characters length, each character in the random sample need 8 bits to represent it. So 64 bits are needed to represent the total random sample. Using simple byte compression algorithm 5 bits are enough to represent a character instead of 8 bits. So 40 bits are enough to represent the same 8 characters instead of 64 bits. SIMPLE BYTE COMPRESSION TECHNIQUE:
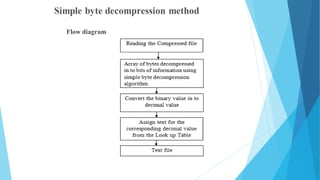
- 7. Flow diagram
- 8. character value character Value a 1 q 17 b 2 r 18 c 3 s 19 d 4 t 20 e 5 u 21 f 6 v 22 g 7 w 23 h 8 x 24 i 9 y 25 j 10 z 26 k 11 “ “ 0 l 12 “ , “ 27 m 13 “. “ 28 n 14 o 15 p 16 Lookup table:
- 9. Example Let’s assume that a text contains 8 characters like ‘birthday’ From the Look up Table the values of the characters in the given example are; b – 2, i – 9, r – 18, t – 20, h – 8 , d – 4, a – 1, y – 25. Convert decimal value into 8 bit binary form and are arranged as follows, KE=/00000010/00001001/00010010/00010100/00001000/00000100/00000001/00011001/ KE = 64 bits / 8 bytes Then chop 3 bits from left side and extract 5 least significant bits as follows KE = /00010/01001/10010/10100/01000/ 00100/00001/11001/ Then rearrange these bits in an array of bytes as follows; KC = /00010010/01100101/01000100/0 0010000/00111001/ KC = 40 bits / 5 bytes
- 10. SIMPLE BYTE DECOMPRESSION TECHNIQUE: When an array of compressed data is given, each 8 bit in the array of received data is regrouped into 5 bits of binary information. These 5 bits of binary information is changed to decimal value. To the obtained decimal values characters are assigned from the Look up Table . Thus the compressed information received was reconstructed properly without any loss.
- 11. Flow diagram
- 12. character value character Value a 1 q 17 b 2 r 18 c 3 s 19 d 4 t 20 e 5 u 21 f 6 v 22 g 7 w 23 h 8 x 24 i 9 y 25 j 10 z 26 k 11 “ “ 0 l 12 “ , “ 27 m 13 “. “ 28 n 14 o 15 p 16 Lookup table:
- 13. Example The received compressed data contains 5 byte of information KC = /00010010/01100101/01000100/00010000/00111001/ Then split into set of 5 bits starting from left KD = /00010 010/01 10010 1/0100 0100/0 00100 00/001 11001/ These sets converted in to decimal value. 00010 – 2,01001 – 9,10010 – 18,10100 – 20,01000 – 8,00100 – 4,00001 – 1, 11001 – 25 With help of Look up Table character value is assigned to the corresponding decimal value extracted from the 5 bit binary information. 2 – b, 9 – i, 18 – r, 20 – r, 8 – h, 4 – d, 1 – a, 25 – y. Finally ‘birthday’ is decoded correctly.
- 14. Discussions Performance of four different Lossless compression techniques like Run length encoding (RLE), Huffman coding, Arithmetic coding and Simple byte compression (SBC) algorithms are analyzed and tested with eight text files. Each is different file sizes and different contents. The input file sizes are 256 bytes, 240 bytes, 592 bytes,, 640 bytes, 816 bytes, 232 bytes, 192 bytes, 1232 bytes. To evaluate the compression effectiveness various compression parameters which are analyzed and listed below Bits per Character (BPC) It is defined as the difference between number of bits used in the compressed text and number of characters used in the original (input) text
- 15. Analysis of BPC for different compression techniques
- 16. Compression Ratio(CR) It is defined as the ratio of the number of bytes in the uncompressed representation to the number of bytes in the compressed representation. CR = Size of uncompressed data / Size of compressed data CR < 1 indicate Compression and CR >1 indicate Expansion K – Input data (Uncompressed data) KC – Compressed data Compression ratio (CR) = Bits in K / Bits in Kc CR = 64 bits / 40 bits X 100 CR = 62.5
- 17. It is reciprocal of compression ratio. It is defined as the ratio between sizes of compressed data to the size of uncompressed data. The value gives how much compression has been achieved. CF=1/CR
- 18. Performance evaluation simple byte compression
- 19. Compression ratios of different compression techniques Compression factor analyses for different compression techniques
- 20. Saving Percentage (SP ) It is also a reasonable measure of compression performance. The value gives how much percentage of space occupied by the output data of its original size.
- 21. A simple byte compression algorithm was compared with sevaral existing loss less compression techniques. By using this technique compression ratio up to 62.5 % can be achieved. The output values of this algorithm are at an acceptable range and it shows better result for any kind of text files.
- 22. THANK YOU