Distributed Programming using RMI
- 1. IADCS Diploma Course Distributed Programming with Java U Nyein Oo COO/Director(IT) Myanma Computer Co., Ltd
- 2. Why Distributed Application? Most of development and deployment environments are Networked Applications design to be distributed (which is become necessary) Process is distributed across multiple networked computers Implemented as Client/server Systems.
- 3. Client/Server Systems? Client requests resource from Server Server accept the client’s request and process and give result back to client Typically there are three components in client/server system.
- 4. Three components of CSS User Interface Layer( implemented by application client like web browser) Information Processing Layer( implemented by application client/server/server support) Information Storage Layer( implemented by database server like web server,FTP server)
- 5. IPL at Client Machine User Interface Layer (Web Browser) Information Processing Layer (Application Client) Information Storage Layer (Application Server) Client Machine Server Machine
- 6. IPL at Server Machine User Interface Layer (Web Browser) Information Processing Layer (Application Client) Information Storage Layer (Application Server) Client Machine Server Machine
- 7. Different type of Method Invocation Distributed Computing Environment(DCE) Distributed Components Object Model(DCOM) Common Object Request Broker Architecture (CORBA) Java’s Remote Methods Invocation(RMI)
- 8. Distributed Computing Environment(DCE) Industry standard of the OSF(Open Software Foundation) Vendor-neutral set of Distributed Computing Provide security services to protect and control access to data Run of the major computing platforms and designed to support distributed application Key Technology for security,www and Distributed Objec
- 9. How Distributed Systems work? Organized into cell(which is nothing but a group of processing resources,services and users that support a common function and share a common set of DCE devices) For example …separate department in a company like(admin,finance..ect)
- 10. The services and Technologies used within DCE Cell Directories Service Distributed File Service(DFS) Distributed Time Service(DTS) Security Service Remote Procedure Calls(RPC) DCE Threads
- 11. What is a DCOM? Distributed Component Object Model Product of Microsoft Corporation Started with OLE technology that used to support compound documents.(one that is product of multiple application) COM is solution for OLE and different from DCE in its design approach.
- 12. DCOM(cont) COM is object oriented whereas DCE is procedural oriented A model ,programming Language can be used COM to create distributed application DCOM allows a COM object on one computer to access methods of another COM object on some other computers. The remote object is accessed the same manner as the local object.
- 13. DCOM(cont) DCOM is distributed COM over multiple computers. Local Object invokes the methods of Local COM library of the remote object it is trying to access. COM library process the functions calls using COM runtime COM Runtime communicate using Object RPC The most important feature is application security is based on Windows NT Policy.
- 14. CORBA Common Object Request Broker Architecture Most popular architecture for building distributed object oriented application Is open standard not tied to particular vendor Objects are accessible via ORBs The client interface to ORB is written by IDLKnown as IDL stub The Server interface to ORB is IDL Skeleton
- 15. Method invocation in CORBA IDL Stub IDL Skeleton Client Host Server Host client Object Server Object ORB
- 16. Benefits using CORBA Open standard and works on all platforms Both clients and servers can be distributed Language independent Just have to provide IDL interface to object An international standard and recognized by most of software vendors.
- 17. Why Java Distributed Object Model Need? TCP Socket is big Overhead DCE ‘s RPC does not gel with Java OODA. DCOM has good performance for Windows and does not support java object fully. CORBA is excellent but Java programmer will have to learn IDL to develop DJA.
- 18. RMI (your best choice for java) JavaSoft design for Object oriented distributed pure java application. RMI also need client stub & server skeleton Support seamless remote invocation on objects in different VMs. Support callbacks from server to applets. Integrated DO model into Java Language
- 19. RMI(cont;) Make differences between DO model and Local Java Object model apparent. Writing reliable distributed applications as simple as possible. Preserve the type-safety provided by the Java Runtime Environment Save Java environment provided by security managers and class loaders.
- 20. RMI Architecture JDOM is simply extension of JOM Objects interact each other within same JVM in Java’s Object Model Objects interact with an object in another JVM at Java Distributed Object Model Client Object(local object) does not reference directly on Server Object(remote object) and references a remote interface
- 21. Allows server objects to differentiate between their local and remote interface Present different access modes No need to have server class file at the compilation of client objects RMI follow like CORBA except ORB RMI Setup the Remote Reference Layer Advantages using Remote Interface
- 22. Three tier Architecture of Java RMI Client Object Server Object Stub Skeleton Remote Reference Layer Remote Reference Layer Transport Layer Transport Layer Lower Layer Protocols Lower Layer Protocols
- 23. Explain java.rmi packages: java.rmi java.rmi.registry java.rmi.server java.rmi.activation java.rmi.dgc Three tiered layering of Java RMI Inside RMI
- 24. java.rmi Package This package provides the remote interface It does not have any methods It supports the following classes: MarshalledObject class Naming class RMISecurityManager class It defines exceptions such as RemoteException
- 25. java.rmi.registry Package This package provides classes and interfaces for remote registry
- 26. java.rmi.server Package This package implements remote stubs and skeletons It is also used to support RMI communications It consists of the following classes: RemoteObject class RemoteServer class RMILoader class Operation class LogStream class
- 27. java.rmi.activation Package This package is used to activate remote objects, when needed It consists of the following classes: Activable class ActivationDesc class getClassName( ) getCodeSource( ) getData( ) getGroupID( ) getRestartMode( ) ActivationGroup class
- 28. java.rmi.dgc Package This package provides classes and interfaces that the RMI distributed garbage collector uses The server side of the distributed garbage collector uses this package It has two methods, dirty( ) and clean( ) , which indicate that the client has referenced a remote object, and that the remote reference has been completed, respectively
- 29. Three Tiered Layering of Java RMI The client object evokes the methods of stub The stub uses the remote layer to communicate with the skeleton The remote layer uses the transport layer to establish the connection between local and remote server
- 30. Implementing RMI Implementing RMI involves two steps namely: Implementing RMI on Remote Host Implementing RMI on Local Host
- 31. Implementing RMI on Remote Host Step 1 Create a remote interface: This has to be public and must extend the Remote interface This method must throw RemoteException Step 2 Create a class that implements the remote interface: This class should create and initialize the remote object It should implement all the methods defined in the remote interface There should be a main( ) method that will be executed as a remote class This main( ) method should also take care of security using the setSecurityManager( ) method
- 32. Implementing RMI on Remote Host (Contd…) Step 3 Create stub and skeleton classes using the rmic command. Step 4 Copy the remote interface and stub file to the client host. Step 5 Start the Remote Registry Server using the command start rmiregistry. Step 6 Execute the program using the java command to create an object of class. This class registers itself with the remote registry
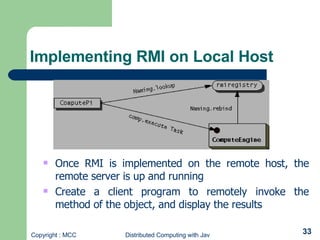
- 33. Implementing RMI on Local Host Once RMI is implemented on the remote host, the remote server is up and running Create a client program to remotely invoke the method of the object, and display the results
- 34. Genreation Remote Interface //remote interface import java.net.*; import java.security.*; import java.rmi.*; public interface MyServer extends java.rmi.Remote{ String getAndSetMessage(String message) throws java.rmi.RemoteException; }
- 35. Generation Client RMI import java.rmi.RMISecurityManager; import java.rmi.Naming; import java.net.*; import java.security.*; public class MyClient{ public static void main(String args[]){ System.setSecurityManager(new RMISecurityManager()); try{ MyServerser=(MyServer)Naming.lookup("//147.81.10.2/ServerTest"); String serverString=ser.getAndSetMessage("I amd Trying "); System.out.println("reply from the server is "+serverString); }catch(Exception e){ System.out.println(e); } } }
- 36. Generation Server RMI import java.rmi.*; import java.rmi.server.*; import java.rmi.registry.*; import java.security.*; import java.net.*; public class MyServerImpl extends UnicastRemoteObject implements MyServer{ static String hostName="147.81.10.2"; String name; public MyServerImpl(String name) throws RemoteException{ super(); this.name=name; }
- 37. Generation Server RMI (cont) public String getAndSetMessage(String message)throws RemoteException{ return("My name is "+name+"Thanks for message"+message); } public static void main(String args[]){ System.setSecurityManager(new RMISecurityManager()); try{ String objectname="Servertest"; MyServerImpl theServer=new MyServerImpl(objectname); Naming.rebind("//"+hostName+"/"+objectname,theServer); System.out.println("I am Registered"); }catch(Exception e) { System.out.println(e); } }}
- 38. Steps to Compilation Compilation Remote Interface File (same as regular .java file) Compilation Remote Client File (same as regular .java file) Compilation Remote Server File I.same as regular .java file II. User rmic compiler to create stub and skeleton class files like c:\jdk1.3.1\bin>rmic MyServerImpl
- 39. Starting rmi registry >start rmiregistry Run as follow >java –Djava.security.policy=policy MyServerIMpl Edit policy for permission grant Steps to Compilation(cont)
- 40. Example-2(Remote Interface) //Remote Interface import java.rmi.*; import java.net.*; public interface Server1 extends Remote { public void doSomething() throws RemoteException; }
- 41. Client Remote import java.rmi.*; import java.net.*; import java.rmi.server.*; public class Client1 { public static void main(String[] args) { System.setSecurityManager(new RMISecurityManager()); try { Server1 ro = (Server1)Naming.lookup("doSomething"); System.out.println("Location: "+System.getProperty("LOCATION")); ro.doSomething(); } catch (Exception e){ e.printStackTrace(); System.exit(-1); } } }
- 42. Server Remote import java.rmi.*; import java.rmi.server.*; import java.rmi.registry.*; public class Server1Impl extends java.rmi.server.UnicastRemoteObject implements Server1 { public static void main(String[] args) { System.setSecurityManager(new RMISecurityManager()); try { Server1Impl obj = new Server1Impl(); Naming.rebind("doSomething", obj); System.out.println("doSomething bound in registry"); } catch (Exception e) { e.printStackTrace(); return; } }
- 43. Server Remote (cont) public Server1Impl() throws RemoteException { } public void doSomething() throws RemoteException { System.out.println("This message is printed by the Server1 object"); System.out.println("Location: " + System.getProperty("LOCATION")); } }
- 44. Invoke rmi registry & Run Client Remote
































![Generation Client RMI import java.rmi.RMISecurityManager; import java.rmi.Naming; import java.net.*; import java.security.*; public class MyClient{ public static void main(String args[]){ System.setSecurityManager(new RMISecurityManager()); try{ MyServerser=(MyServer)Naming.lookup("//147.81.10.2/ServerTest"); String serverString=ser.getAndSetMessage("I amd Trying "); System.out.println("reply from the server is "+serverString); }catch(Exception e){ System.out.println(e); } } }](https://image.slidesharecdn.com/distributed-programming-using-rmi-1197645104413613-3/85/Distributed-Programming-using-RMI-35-320.jpg)

![Generation Server RMI (cont) public String getAndSetMessage(String message)throws RemoteException{ return("My name is "+name+"Thanks for message"+message); } public static void main(String args[]){ System.setSecurityManager(new RMISecurityManager()); try{ String objectname="Servertest"; MyServerImpl theServer=new MyServerImpl(objectname); Naming.rebind("//"+hostName+"/"+objectname,theServer); System.out.println("I am Registered"); }catch(Exception e) { System.out.println(e); } }}](https://image.slidesharecdn.com/distributed-programming-using-rmi-1197645104413613-3/85/Distributed-Programming-using-RMI-37-320.jpg)



![Client Remote import java.rmi.*; import java.net.*; import java.rmi.server.*; public class Client1 { public static void main(String[] args) { System.setSecurityManager(new RMISecurityManager()); try { Server1 ro = (Server1)Naming.lookup("doSomething"); System.out.println("Location: "+System.getProperty("LOCATION")); ro.doSomething(); } catch (Exception e){ e.printStackTrace(); System.exit(-1); } } }](https://image.slidesharecdn.com/distributed-programming-using-rmi-1197645104413613-3/85/Distributed-Programming-using-RMI-41-320.jpg)
![Server Remote import java.rmi.*; import java.rmi.server.*; import java.rmi.registry.*; public class Server1Impl extends java.rmi.server.UnicastRemoteObject implements Server1 { public static void main(String[] args) { System.setSecurityManager(new RMISecurityManager()); try { Server1Impl obj = new Server1Impl(); Naming.rebind("doSomething", obj); System.out.println("doSomething bound in registry"); } catch (Exception e) { e.printStackTrace(); return; } }](https://image.slidesharecdn.com/distributed-programming-using-rmi-1197645104413613-3/85/Distributed-Programming-using-RMI-42-320.jpg)


























































































