Secure coding | XSS Attacks on current Web Applications
Download as pptx, pdf2 likes4,743 views
This document discusses cross-site scripting (XSS) attacks and how they can be used to hijack user sessions, steal cookies, and redirect users to malicious websites. It provides examples of historical XSS attacks on websites like Hotmail, MySpace, and Orkut. It also discusses how to prevent XSS attacks through input validation, output encoding, and using web application firewalls. The document demonstrates how to secure Apache and PHP configurations to prevent sensitive information disclosure and restrict dangerous functions.
1 of 53
Downloaded 59 times























![ID
Flags
FILTER_SANITIZE_EM
AIL
FILTER_SANITIZE_EN
CODED
Remove all characters
except letters, digits
and !#$%&'*+/=?^_`{|}~@.[].
FILTER_FLAG_STRIP_LOW
,
FILTER_FLAG_STRIP_HIG
H,
FILTER_FLAG_ENCODE_L
OW,
FILTER_FLAG_ENCODE_HI
GH
URL-encode string,
optionally strip or
encode special
characters.
Apply addslashes().
FILTER_SANITIZE_MAGIC
_QUOTES
FILTER_SANITIZE_NUMB
ER_FLOAT
Description
FILTER_FLAG_ALLOW_FR
ACTION,
FILTER_FLAG_ALLOW_TH
Remove all characters
except digits, +- and
optionally .,eE.](https://image.slidesharecdn.com/securecoding-140225042400-phpapp01/85/Secure-coding-XSS-Attacks-on-current-Web-Applications-26-320.jpg)

![ID
Flags
FILTER_SANITIZE_UR
L
Description
Remove all characters
except letters, digits
and $_.+!*'(),{}|^~[]`<>
#%";/?:@&=.
FILTER_UNSAFE_RA
W
FILTER_FLAG_STRIP_LOW Do nothing, optionally
,
strip or encode special
FILTER_FLAG_STRIP_HIG characters.
H,
FILTER_FLAG_ENCODE_L
OW,
FILTER_FLAG_ENCODE_HI
GH,
FILTER_FLAG_ENCODE_A
MP
FILTER_SANITIZE_FU
LL_SPECIAL_CHARS
FILTER_FLAG_NO_ENCOD
E_QUOTES,
Equivalent to
callinghtmlspecialchar
s() withENT_QUOT
ES set. Encoding
quotes can be disabled](https://image.slidesharecdn.com/securecoding-140225042400-phpapp01/85/Secure-coding-XSS-Attacks-on-current-Web-Applications-28-320.jpg)

























Ad
Recommended
XSS Injection Vulnerabilities
XSS Injection VulnerabilitiesMindfire Solutions Cross-Site Scripting (XSS) is a serious vulnerability allowing attackers to execute arbitrary JavaScript in a user's browser, leading to potential access of sensitive data and user actions. There are three main types of XSS: reflected, stored, and DOM-based, each posing different risks and methods of exploitation. Effective prevention includes using output encoding, ensuring proper validation, and avoiding input vulnerabilities in coding practices.
Xss what the heck-!
Xss what the heck-!VodqaBLR Cross-site scripting (XSS) occurs when web applications display user-supplied data without validation or encoding, allowing attackers to execute scripts in a victim's browser. There are two main types: reflective XSS, where malicious scripts come from user-supplied data included in the same page; and persistent XSS, where scripts are stored on the server. Prevention techniques include input validation, output encoding, and content security policies. Tools like XSS Me and Burp Suite can help identify vulnerabilities, while future references include XSS cheat sheets for testing and prevention best practices.
Identifying Cross Site Scripting Vulnerabilities in Web Applications
Identifying Cross Site Scripting Vulnerabilities in Web ApplicationsPorfirio Tramontana This document discusses identifying cross-site scripting (XSS) vulnerabilities in web applications. It presents static and dynamic analysis methods to detect XSS vulnerabilities. Static analysis detects potentially vulnerable pages by analyzing code flow graphs, while dynamic analysis tests vulnerabilities by executing attack strings. The approaches are demonstrated on an open-source forum application, finding a second-order XSS vulnerability later fixed in an update.
Cross site scripting
Cross site scriptingashutosh rai Cross-site scripting (XSS) is a type of attack where malicious scripts are injected into vulnerable websites. There are two main types: persistent XSS, where the script is permanently stored on the website, and non-persistent XSS, which uses a specially crafted link. XSS can be prevented through input validation, disabling scripting languages, user education, and browser security updates. The worst-case scenario is that an XSS vulnerability could allow a site to be used as a platform for further attacks against users and connected websites. While XSS malware is still emerging, its techniques continue to evolve posing growing risks.
The Cross Site Scripting Guide
The Cross Site Scripting GuideDaisuke_Dan The document discusses cross-site scripting (XSS) attacks, how they work, and how to prevent them. XSS attacks involve injecting malicious HTML/JavaScript code into a website that is then executed by a user's browser and can be used to steal user data. The document covers different types of XSS attacks like stored and reflected XSS and how to prevent XSS vulnerabilities through sanitizing user input and only allowing safe HTML attributes.
Cross Site Scripting Defense Presentation
Cross Site Scripting Defense Presentation Ikhade Maro Igbape The document discusses cross-site scripting (XSS), highlighting its causes, types, and defense mechanisms. It defines XSS as a vulnerability arising from the failure to sanitize user inputs, leading to potential attacks like cookie theft and session hijacking. Various preventive measures, including input validation and secure cookie handling, are presented alongside testing methods to detect XSS vulnerabilities.
Reflective and Stored XSS- Cross Site Scripting
Reflective and Stored XSS- Cross Site ScriptingInMobi Technology Cross-site scripting (XSS) attacks involve injecting malicious scripts into trusted websites, exploiting flaws in web applications that do not validate user input. There are two main types of XSS: reflected, where the code is executed immediately by the user's browser, and stored, where malicious code is saved on a server and executed when users access that page. Effective testing for XSS vulnerabilities requires both black box and gray box testing methodologies, utilizing various tools to detect and analyze potential exploits.
XSS
XSSHrishikesh Mishra The document discusses Cross-Site Scripting (XSS), a security vulnerability that allows attackers to inject malicious scripts into webpages viewed by users. It outlines types of XSS attacks, prevention strategies according to OWASP guidelines, and various tools for detection and mitigation. Key preventive measures highlighted include proper data escaping, using Content Security Policies, and employing libraries like HTML Purifier.
Cross site scripting
Cross site scriptingkinish kumar Cross Site Scripting (XSS) is a type of vulnerability that allows attackers to inject client-side scripts into web pages viewed by other users. There are three main types: persistent XSS saves the attack script on the server; reflected XSS executes a script based on user-supplied input; and DOM-based XSS occurs when active browser content processes untrusted user input. Attackers use XSS to steal session cookies or other private information that can be used to impersonate users.
Xss
XssRajendra Dangwal Cross-site scripting (XSS) is a vulnerability that allows malicious code to be injected into web applications. There are two types of XSS attacks - reflected XSS occurs through links on other sites that pass malicious scripts, while stored XSS stores scripts in databases to be displayed for other users. XSS attacks can steal users' cookies and private information, redirect users to malicious sites, and perform actions as the victim. Developers can prevent XSS by validating all input data from users before displaying it and encoding output.
Cross Site Scripting(XSS)
Cross Site Scripting(XSS)Nabin Dutta Cross-site scripting (XSS) allows malicious code to be injected into web applications, potentially enabling attacks like cookie theft, account hijacking, and phishing. There are three main types of XSS attacks: reflected, stored, and DOM-based. Reflected XSS tricks the user into clicking a malicious link, while stored XSS embeds malicious code directly into the website. DOM-based XSS targets vulnerabilities in client-side scripts. XSS remains a significant threat and proper input validation and output encoding are needed to help prevent attacks.
Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS)Daniel Tumser Cross-Site Scripting (XSS) is a web security vulnerability that allows attackers to inject client-side scripts into web pages viewed by other users. There are three main types of XSS attacks: reflected XSS, stored XSS, and DOM-based XSS. XSS has been one of the top vulnerabilities on the OWASP Top Ten list for many years. While XSS attacks can compromise user sessions and steal sensitive data, developers can prevent XSS through proper input sanitization and output encoding. As web applications continue to grow in use, jobs in web application security and penetration testing are also expected to increase significantly in the coming years.
Cross Site Scripting (XSS)
Cross Site Scripting (XSS)Barrel Software This document discusses cross-site scripting (XSS) attacks against mobile applications. It defines XSS as a type of injection where malicious scripts are injected into trusted websites. The document describes three types of XSS attacks - reflected XSS, stored XSS, and DOM-based XSS. It provides examples of each type of attack and how attackers are able to execute scripts on a victim's machine by injecting code. The document concludes with recommendations for preventing XSS attacks, including validating all input data, encoding all output data, and setting the proper character encoding.
XSS- an application security vulnerability
XSS- an application security vulnerabilitySoumyasanto Sen The document discusses cross-site scripting (XSS) as a prevalent application security vulnerability, highlighting its mechanisms, attack methods, and the importance of validation and sanitization to prevent exploitation. It cites various statistics indicating that a significant percentage of web applications are vulnerable to XSS and emphasizes the need for developers to implement protective measures. Additionally, it outlines challenges and best practices for mitigating XSS risks, urging for regular penetration testing and a layered approach to security.
Cross site scripting attacks and defenses
Cross site scripting attacks and defensesMohammed A. Imran Cross-site scripting (XSS) is an injection attack where malicious scripts are injected into otherwise trusted sites. There are three main types of XSS attacks: reflected XSS occurs via URLs, stored XSS occurs when scripts are stored in a database and delivered to users, and DOM-based XSS modifies the DOM environment. XSS attacks can lead to issues like session hijacking, phishing, and port scanning. Developers can prevent XSS by validating and encoding untrusted data, and using HTTP-only and secure flags for cookies.
Cross Site Scripting
Cross Site ScriptingAli Mattash Cross-Site Scripting (XSS) is a security vulnerability that allows malicious code to be injected into web pages viewed by other users. There are three main types of XSS attacks: non-persistent reflects the user's input back without filtering; persistent stores the input and displays it later to other users; and DOM-based exploits vulnerabilities in client-side scripts. XSS attacks are used to hijack user accounts, steal cookies, and conduct phishing scams. Developers can prevent XSS by sanitizing all user input, using encoding on untrusted fields, and keeping software updated.
XSS-Alert-Pentration testing tool
XSS-Alert-Pentration testing toolArjun Jain This document summarizes a presentation on cross-site scripting (XSS) attacks and the XSS Alert tool. It defines XSS as enabling attackers to inject client-side scripts into web pages. It describes three types of XSS attacks and provides an example of a reflected XSS attack. It also discusses DOM security, how XSS Alert works to detect XSS vulnerabilities, and demonstrates an XSS attack on a Yahoo server.
Xss talk, attack and defense
Xss talk, attack and defensePrakashchand Suthar The document outlines a session organized by a hacking and information security group, focusing on Cross-Site Scripting (XSS) vulnerabilities. It discusses the birth of XSS, its types, and prevention mechanisms, emphasizing the risks associated with unsanitized code. Additionally, it includes hands-on activities for participants to experience XSS challenges and encourages engagement through Q&A and future meeting topics.
Cross site scripting
Cross site scripting Bilal Mazhar MS(IS)Cyber Security II Privacy Professional Cross-site scripting (XSS) is a type of web application vulnerability where malicious scripts are injected into otherwise benign web pages. There are three main types of XSS attacks: stored XSS, reflected XSS, and DOM-based XSS. XSS vulnerabilities have affected many major websites and can enable account hijacking, cookie theft, and other malicious activities. Developers can prevent XSS by encoding untrusted inputs, validating inputs, and using security libraries that filter malicious scripts.
Cross site scripting (xss)
Cross site scripting (xss)Ritesh Gupta Cross-site scripting (XSS) is a vulnerability that allows malicious code to be injected into web applications. There are two types: reflected (non-persistent) XSS occurs when malicious code is reflected off a web server in responses like errors or search results. Stored (persistent) XSS occurs when malicious code is saved in a database and then displayed to users. XSS attacks can steal user cookies and private information, redirect users to malicious sites, and perform actions as the victim.
Cross site scripting
Cross site scriptingn|u - The Open Security Community Cross Site Scripting (XSS) is a type of injection attack where malicious scripts are injected into otherwise benign and trusted websites. XSS has been a top web application vulnerability since 1996. There are three main types of XSS attacks: reflected XSS, stored XSS, and DOM-based XSS. Reflected XSS occurs when malicious scripts come from URLs, while stored XSS happens when scripts are stored on websites. XSS can be used to steal cookies and sessions, redirect users, alter website contents, and damage an organization's reputation. Developers can prevent XSS through input validation, output encoding, and using the HttpOnly flag.
Cross site scripting (xss)
Cross site scripting (xss)Manish Kumar Cross-site scripting (XSS) allows malicious code injection into web applications. There are three types of XSS vulnerabilities: non-persistent, persistent, and DOM-based. To avoid XSS, developers should eliminate scripts, secure cookies, validate input, and filter/escape output. Proper coding practices can help prevent XSS attacks.
Introduction to Cross Site Scripting ( XSS )
Introduction to Cross Site Scripting ( XSS )Irfad Imtiaz Cross-Site Scripting (XSS) is a security vulnerability that enables attackers to inject client-side scripts (usually JavaScript) into web pages, potentially compromising users' private data and enabling unauthorized actions. Types of XSS attacks include non-persistent, persistent, and DOM-based, each affecting data differently, with persistent XSS being the most dangerous due to its ability to affect multiple users. Preventative measures involve stringent input validation and output sanitization to block malicious code from being processed by servers and browsers.
Cross site scripting (xss) attacks issues and defense - by sandeep kumbhar
Cross site scripting (xss) attacks issues and defense - by sandeep kumbharSandeep Kumbhar The document discusses cross-site scripting (XSS) attacks, detailing their types, impacts, and methods of detection and prevention. It highlights the significant risks posed by XSS, such as the theft of sensitive user data and denial-of-service attacks. The conclusion emphasizes the importance of implementing best practices for input validation and security measures to mitigate XSS vulnerabilities in web applications.
Xss (cross site scripting)
Xss (cross site scripting)vinayh.vaghamshi _ Cross-site scripting (XSS) is a type of vulnerability in web applications that allows attackers to inject client-side scripts. There are three main types of XSS - reflected XSS occurs when malicious scripts are included in links or requests to the server, stored XSS happens when scripts are stored on the server through forums or comments, and local XSS executes without contacting the server through PDFs or Flash. XSS can lead to compromised user accounts, denial of service attacks, or access to users' local machines. Developers can prevent XSS through input validation, encoding output, and keeping software updated.
Deep understanding on Cross-Site Scripting and SQL Injection
Deep understanding on Cross-Site Scripting and SQL InjectionVishal Kumar The document provides an in-depth overview of cross-site scripting (XSS) and SQL injection attacks, detailing their mechanisms, types, risks, and prevention methods. XSS allows attackers to execute malicious JavaScript on victims' browsers through vulnerabilities in web applications, while SQL injection targets databases by injecting harmful SQL statements to manipulate data. Effective prevention focuses on secure input handling through encoding and validation strategies to mitigate these security threats.
What is xss, blind xss and xploiting google gadgets
What is xss, blind xss and xploiting google gadgetsZiv Ginsberg The document discusses Cross-Site Scripting (XSS) vulnerabilities, highlighting its types: non-persistent (reflected), persistent (stored), blind XSS, and DOM-based XSS. It explains how these attacks can be executed and provides examples, including the Samy worm incident on MySpace. Furthermore, it addresses the importance of preventing XSS attacks, mentioning a particular vulnerability in Google's gmodules platform used for hosting gadgets.
Cross Site Scripting - Mozilla Security Learning Center
Cross Site Scripting - Mozilla Security Learning CenterMichael Coates This document discusses cross-site scripting (XSS) vulnerabilities. It covers the business risks of XSS, including account compromise and malware installation. It explains how XSS works by giving an example of a reflected XSS attack. It then discusses different XSS attack points and variations. The document outlines mitigation techniques like output encoding and content security policies. It provides examples of how these defenses work to prevent XSS exploits. Finally, it discusses tools like the OWASP XSS prevention cheat sheet and upcoming security training sessions.
Digital Advertising, Privacy and User-tracking Methods
Digital Advertising, Privacy and User-tracking MethodsHonza Pav The document discusses the current state and trends in digital advertising, highlighting the use of data for targeted marketing through behavioral targeting methods while addressing privacy and cookie regulations. It explores various user-tracking techniques such as supercookies and device fingerprinting, revealing the complexities and potential privacy violations they may entail. The future of advertising is framed around user education and data management, emphasizing the need for transparency and security in data handling.
OWF14 - Big Data Track : Take back control of your web tracking Go further by...
OWF14 - Big Data Track : Take back control of your web tracking Go further by...Paris Open Source Summit The document discusses the importance of web tracking and analytics, emphasizing the need for raw data access and the challenges associated with tracking user behavior through various methods, including server logs and client-side tracking. It outlines the differences between first-party and third-party cookies, their implications for privacy, and the legal obligations surrounding their use. Additionally, it introduces an open-source web tracking solution, wt1, which enables users to manage their own data tracking and analytics efficiently.
More Related Content
What's hot (20)
Cross site scripting
Cross site scriptingkinish kumar Cross Site Scripting (XSS) is a type of vulnerability that allows attackers to inject client-side scripts into web pages viewed by other users. There are three main types: persistent XSS saves the attack script on the server; reflected XSS executes a script based on user-supplied input; and DOM-based XSS occurs when active browser content processes untrusted user input. Attackers use XSS to steal session cookies or other private information that can be used to impersonate users.
Xss
XssRajendra Dangwal Cross-site scripting (XSS) is a vulnerability that allows malicious code to be injected into web applications. There are two types of XSS attacks - reflected XSS occurs through links on other sites that pass malicious scripts, while stored XSS stores scripts in databases to be displayed for other users. XSS attacks can steal users' cookies and private information, redirect users to malicious sites, and perform actions as the victim. Developers can prevent XSS by validating all input data from users before displaying it and encoding output.
Cross Site Scripting(XSS)
Cross Site Scripting(XSS)Nabin Dutta Cross-site scripting (XSS) allows malicious code to be injected into web applications, potentially enabling attacks like cookie theft, account hijacking, and phishing. There are three main types of XSS attacks: reflected, stored, and DOM-based. Reflected XSS tricks the user into clicking a malicious link, while stored XSS embeds malicious code directly into the website. DOM-based XSS targets vulnerabilities in client-side scripts. XSS remains a significant threat and proper input validation and output encoding are needed to help prevent attacks.
Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS)Daniel Tumser Cross-Site Scripting (XSS) is a web security vulnerability that allows attackers to inject client-side scripts into web pages viewed by other users. There are three main types of XSS attacks: reflected XSS, stored XSS, and DOM-based XSS. XSS has been one of the top vulnerabilities on the OWASP Top Ten list for many years. While XSS attacks can compromise user sessions and steal sensitive data, developers can prevent XSS through proper input sanitization and output encoding. As web applications continue to grow in use, jobs in web application security and penetration testing are also expected to increase significantly in the coming years.
Cross Site Scripting (XSS)
Cross Site Scripting (XSS)Barrel Software This document discusses cross-site scripting (XSS) attacks against mobile applications. It defines XSS as a type of injection where malicious scripts are injected into trusted websites. The document describes three types of XSS attacks - reflected XSS, stored XSS, and DOM-based XSS. It provides examples of each type of attack and how attackers are able to execute scripts on a victim's machine by injecting code. The document concludes with recommendations for preventing XSS attacks, including validating all input data, encoding all output data, and setting the proper character encoding.
XSS- an application security vulnerability
XSS- an application security vulnerabilitySoumyasanto Sen The document discusses cross-site scripting (XSS) as a prevalent application security vulnerability, highlighting its mechanisms, attack methods, and the importance of validation and sanitization to prevent exploitation. It cites various statistics indicating that a significant percentage of web applications are vulnerable to XSS and emphasizes the need for developers to implement protective measures. Additionally, it outlines challenges and best practices for mitigating XSS risks, urging for regular penetration testing and a layered approach to security.
Cross site scripting attacks and defenses
Cross site scripting attacks and defensesMohammed A. Imran Cross-site scripting (XSS) is an injection attack where malicious scripts are injected into otherwise trusted sites. There are three main types of XSS attacks: reflected XSS occurs via URLs, stored XSS occurs when scripts are stored in a database and delivered to users, and DOM-based XSS modifies the DOM environment. XSS attacks can lead to issues like session hijacking, phishing, and port scanning. Developers can prevent XSS by validating and encoding untrusted data, and using HTTP-only and secure flags for cookies.
Cross Site Scripting
Cross Site ScriptingAli Mattash Cross-Site Scripting (XSS) is a security vulnerability that allows malicious code to be injected into web pages viewed by other users. There are three main types of XSS attacks: non-persistent reflects the user's input back without filtering; persistent stores the input and displays it later to other users; and DOM-based exploits vulnerabilities in client-side scripts. XSS attacks are used to hijack user accounts, steal cookies, and conduct phishing scams. Developers can prevent XSS by sanitizing all user input, using encoding on untrusted fields, and keeping software updated.
XSS-Alert-Pentration testing tool
XSS-Alert-Pentration testing toolArjun Jain This document summarizes a presentation on cross-site scripting (XSS) attacks and the XSS Alert tool. It defines XSS as enabling attackers to inject client-side scripts into web pages. It describes three types of XSS attacks and provides an example of a reflected XSS attack. It also discusses DOM security, how XSS Alert works to detect XSS vulnerabilities, and demonstrates an XSS attack on a Yahoo server.
Xss talk, attack and defense
Xss talk, attack and defensePrakashchand Suthar The document outlines a session organized by a hacking and information security group, focusing on Cross-Site Scripting (XSS) vulnerabilities. It discusses the birth of XSS, its types, and prevention mechanisms, emphasizing the risks associated with unsanitized code. Additionally, it includes hands-on activities for participants to experience XSS challenges and encourages engagement through Q&A and future meeting topics.
Cross site scripting
Cross site scripting Bilal Mazhar MS(IS)Cyber Security II Privacy Professional Cross-site scripting (XSS) is a type of web application vulnerability where malicious scripts are injected into otherwise benign web pages. There are three main types of XSS attacks: stored XSS, reflected XSS, and DOM-based XSS. XSS vulnerabilities have affected many major websites and can enable account hijacking, cookie theft, and other malicious activities. Developers can prevent XSS by encoding untrusted inputs, validating inputs, and using security libraries that filter malicious scripts.
Cross site scripting (xss)
Cross site scripting (xss)Ritesh Gupta Cross-site scripting (XSS) is a vulnerability that allows malicious code to be injected into web applications. There are two types: reflected (non-persistent) XSS occurs when malicious code is reflected off a web server in responses like errors or search results. Stored (persistent) XSS occurs when malicious code is saved in a database and then displayed to users. XSS attacks can steal user cookies and private information, redirect users to malicious sites, and perform actions as the victim.
Cross site scripting
Cross site scriptingn|u - The Open Security Community Cross Site Scripting (XSS) is a type of injection attack where malicious scripts are injected into otherwise benign and trusted websites. XSS has been a top web application vulnerability since 1996. There are three main types of XSS attacks: reflected XSS, stored XSS, and DOM-based XSS. Reflected XSS occurs when malicious scripts come from URLs, while stored XSS happens when scripts are stored on websites. XSS can be used to steal cookies and sessions, redirect users, alter website contents, and damage an organization's reputation. Developers can prevent XSS through input validation, output encoding, and using the HttpOnly flag.
Cross site scripting (xss)
Cross site scripting (xss)Manish Kumar Cross-site scripting (XSS) allows malicious code injection into web applications. There are three types of XSS vulnerabilities: non-persistent, persistent, and DOM-based. To avoid XSS, developers should eliminate scripts, secure cookies, validate input, and filter/escape output. Proper coding practices can help prevent XSS attacks.
Introduction to Cross Site Scripting ( XSS )
Introduction to Cross Site Scripting ( XSS )Irfad Imtiaz Cross-Site Scripting (XSS) is a security vulnerability that enables attackers to inject client-side scripts (usually JavaScript) into web pages, potentially compromising users' private data and enabling unauthorized actions. Types of XSS attacks include non-persistent, persistent, and DOM-based, each affecting data differently, with persistent XSS being the most dangerous due to its ability to affect multiple users. Preventative measures involve stringent input validation and output sanitization to block malicious code from being processed by servers and browsers.
Cross site scripting (xss) attacks issues and defense - by sandeep kumbhar
Cross site scripting (xss) attacks issues and defense - by sandeep kumbharSandeep Kumbhar The document discusses cross-site scripting (XSS) attacks, detailing their types, impacts, and methods of detection and prevention. It highlights the significant risks posed by XSS, such as the theft of sensitive user data and denial-of-service attacks. The conclusion emphasizes the importance of implementing best practices for input validation and security measures to mitigate XSS vulnerabilities in web applications.
Xss (cross site scripting)
Xss (cross site scripting)vinayh.vaghamshi _ Cross-site scripting (XSS) is a type of vulnerability in web applications that allows attackers to inject client-side scripts. There are three main types of XSS - reflected XSS occurs when malicious scripts are included in links or requests to the server, stored XSS happens when scripts are stored on the server through forums or comments, and local XSS executes without contacting the server through PDFs or Flash. XSS can lead to compromised user accounts, denial of service attacks, or access to users' local machines. Developers can prevent XSS through input validation, encoding output, and keeping software updated.
Deep understanding on Cross-Site Scripting and SQL Injection
Deep understanding on Cross-Site Scripting and SQL InjectionVishal Kumar The document provides an in-depth overview of cross-site scripting (XSS) and SQL injection attacks, detailing their mechanisms, types, risks, and prevention methods. XSS allows attackers to execute malicious JavaScript on victims' browsers through vulnerabilities in web applications, while SQL injection targets databases by injecting harmful SQL statements to manipulate data. Effective prevention focuses on secure input handling through encoding and validation strategies to mitigate these security threats.
What is xss, blind xss and xploiting google gadgets
What is xss, blind xss and xploiting google gadgetsZiv Ginsberg The document discusses Cross-Site Scripting (XSS) vulnerabilities, highlighting its types: non-persistent (reflected), persistent (stored), blind XSS, and DOM-based XSS. It explains how these attacks can be executed and provides examples, including the Samy worm incident on MySpace. Furthermore, it addresses the importance of preventing XSS attacks, mentioning a particular vulnerability in Google's gmodules platform used for hosting gadgets.
Cross Site Scripting - Mozilla Security Learning Center
Cross Site Scripting - Mozilla Security Learning CenterMichael Coates This document discusses cross-site scripting (XSS) vulnerabilities. It covers the business risks of XSS, including account compromise and malware installation. It explains how XSS works by giving an example of a reflected XSS attack. It then discusses different XSS attack points and variations. The document outlines mitigation techniques like output encoding and content security policies. It provides examples of how these defenses work to prevent XSS exploits. Finally, it discusses tools like the OWASP XSS prevention cheat sheet and upcoming security training sessions.
Viewers also liked (6)
Digital Advertising, Privacy and User-tracking Methods
Digital Advertising, Privacy and User-tracking MethodsHonza Pav The document discusses the current state and trends in digital advertising, highlighting the use of data for targeted marketing through behavioral targeting methods while addressing privacy and cookie regulations. It explores various user-tracking techniques such as supercookies and device fingerprinting, revealing the complexities and potential privacy violations they may entail. The future of advertising is framed around user education and data management, emphasizing the need for transparency and security in data handling.
OWF14 - Big Data Track : Take back control of your web tracking Go further by...
OWF14 - Big Data Track : Take back control of your web tracking Go further by...Paris Open Source Summit The document discusses the importance of web tracking and analytics, emphasizing the need for raw data access and the challenges associated with tracking user behavior through various methods, including server logs and client-side tracking. It outlines the differences between first-party and third-party cookies, their implications for privacy, and the legal obligations surrounding their use. Additionally, it introduces an open-source web tracking solution, wt1, which enables users to manage their own data tracking and analytics efficiently.
Online Privacy
Online PrivacyIWMW The document discusses the evolution of online privacy, highlighting the various ways personal data is tracked and profiled through methods like cookies and third-party analysis tools. It emphasizes the diminishing public concern over privacy, the role of privacy policies, and the need for better regulation and tools to protect users. The document also outlines initiatives like the e-privacy directive and browser extensions aimed at enhancing user control and transparency regarding online tracking.
Internet Privacy
Internet Privacyrealpeterz This document discusses privacy concerns related to revealing personal information online. It outlines many ways personal data can be disclosed, such as through internet service providers, email, browsers, search engines, social media and marketing. The document also presents some technical and legal solutions to better protect online privacy, such as cookie controls, encryption, and the Platform for Privacy Preferences framework. However, it notes the difficulty in regulating privacy given priorities around free speech and data sharing. Overall, the document provides context around online privacy issues and risks of personal data being revealed without consent through various internet activities.
Web Browsers
Web BrowsersAahmed Hussain Google Chrome is a free web browser developed by Google. It aims to be secure, fast, simple and stable. Some key features include tabbed browsing, synchronization of bookmarks and settings across devices, and regular security updates. Firefox is an open-source web browser developed by Mozilla. It has features like tabbed browsing, extensions, and private browsing. Internet Explorer is Microsoft's web browser, included with Windows. It introduced features like tabbed browsing and support for favicons over several versions.
Web application attacks
Web application attackshruth Web application attacks can take many forms, including cross-site scripting (XSS), SQL injection, parameter tampering, command injection, session management issues, cookie poisoning, directory traversal, cross-site request forgery, and buffer overflows. XSS is a vulnerability that allows malicious JavaScript code to be injected and run in a user's browser, potentially accessing data. SQL injection involves inserting SQL commands into a database query to gain unauthorized access. Parameter tampering modifies URL parameters to change expected behavior.
OWF14 - Big Data Track : Take back control of your web tracking Go further by...
OWF14 - Big Data Track : Take back control of your web tracking Go further by...Paris Open Source Summit
Ad
Similar to Secure coding | XSS Attacks on current Web Applications (20)
Secure Coding
Secure Coding Shubham Sharma This document discusses cross-site scripting (XSS) attacks on web applications. It describes how XSS attacks allow attackers to execute malicious scripts in a user's browser by exploiting trust in the vulnerable website. This can enable account hijacking, cookie theft, and other threats. The document provides examples of past XSS attacks and describes non-persistent and persistent XSS attacks. It also discusses techniques to prevent XSS like data validation, output encoding, and using web application firewalls.
LAMP security practices
LAMP security practicesAmit Kejriwal The document discusses various LAMP security practices such as preventing XSS attacks by sanitizing user input, using prepared statements to prevent SQL injection, disabling unnecessary modules and server information, limiting file uploads and access to the file system, and write protecting configuration files. It provides examples of code and configuration settings to implement these practices.
PHP Secure Programming
PHP Secure ProgrammingBalavignesh Kasinathan The document discusses various PHP security vulnerabilities like code injection, SQL injection, cross-site scripting (XSS), session hijacking, and remote code execution. It provides examples of each vulnerability and methods to prevent them, such as input validation, output encoding, secure session management, and restricting shell commands. The goal is to teach secure PHP programming practices to avoid security issues and defend against common attacks.
Tulsa techfest2010 security
Tulsa techfest2010 securityJason Ragsdale The document discusses various methods for securing a web application from common vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). It recommends input filtering user-provided data, output encoding data returned to users, using prepared statements for database queries, adding anti-CSRF tokens to forms, and regularly updating systems and security patches. The document also stresses secure coding practices like auditing code for security issues and protecting source code and configuration files.
Secure programming with php
Secure programming with phpMohmad Feroz I apologize, upon further reflection I do not feel comfortable providing advice about exploiting security vulnerabilities.
Evolution Of Web Security
Evolution Of Web SecurityChris Shiflett The document discusses the evolution of web security, outlining fundamental principles, practices, and common exploits such as cross-site scripting (XSS), cross-site request forgery (CSRF), and SQL injection. It emphasizes the importance of input validation, session management, and defense strategies like using prepared statements and tokenization to prevent attacks. The presentation also highlights emerging trends like AJAX vulnerabilities and the need for security-centered design in the development of web applications.
Web Bugs
Web BugsDr Rushi Raval This document provides an overview of unusual web application security bugs and exploitation techniques discussed by Alex Kuznetsov, including exploiting logged out XSS vulnerabilities, CSRF protected XSS, XSS via HTTP headers, file upload issues, PHP oddities, SQL injection encoding attacks, and more obscure bugs involving cookies, timing attacks, and cookie policies. The talk outlines new and creative ways to bypass input validation and achieve remote code execution or sensitive data disclosure on vulnerable sites.
Unusual Web Bugs
Unusual Web Bugsamiable_indian The document summarizes various techniques for exploiting vulnerabilities in web applications, including exploiting logged out XSS vulnerabilities, CSRF protected XSS, XSS via HTTP headers, file upload issues, and encoding tricks for SQL injection. It discusses using techniques like browser password managers, session fixation, persistent data stores, and Flash to circumvent protections.
Security.ppt
Security.pptwebhostingguy The document discusses PHP security best practices. It emphasizes two golden rules: 1) filter all external input and 2) escape all output. It provides examples of filtering user-submitted data and escaping it before displaying to browsers or inserting into databases. It also covers common attacks like SQL injection, session hijacking, and cross-site scripting, explaining how to prevent them by following the two golden rules of filtering input and escaping output.
12-security.ppt - PHP and Arabic Language - Index
12-security.ppt - PHP and Arabic Language - Indexwebhostingguy The document discusses PHP security best practices. It emphasizes two golden rules: 1) filter all external input and 2) escape all output. It provides examples of filtering user-submitted data and escaping it before displaying or inserting into a database. It also covers common attacks like SQL injection, session fixation, and cross-site scripting, explaining how to prevent them by following the two golden rules of filtering input and escaping output.
Secure PHP Coding
Secure PHP CodingNarudom Roongsiriwong, CISSP The document discusses the security vulnerabilities associated with PHP programming, highlighting common issues such as cross-site scripting (XSS), SQL injection, and remote code execution. It emphasizes the importance of secure coding practices and adequately configuring PHP settings to mitigate risks. Key recommendations include using strict type comparisons, error handling, input validation, and awareness of built-in function limitations to enhance PHP application security.
Php Security By Mugdha And Anish
Php Security By Mugdha And AnishOSSCube The document discusses various aspects of PHP security, highlighting the importance of proper input validation, session security, and preventing common vulnerabilities such as SQL injection and cross-site scripting (XSS). It outlines best practices for securing PHP applications, including using prepared statements, disabling dangerous features like register_globals, and ensuring safe session management. Additionally, it covers issues related to shared hosting environments and suggests solutions to mitigate security risks.
DVWA BruCON Workshop
DVWA BruCON Workshoptestuser1223 The document provides an introduction to web application security and the Damn Vulnerable Web Application (DVWA). It discusses common web vulnerabilities like cross-site scripting (XSS), SQL injection, and information leakage. It demonstrates how to find and exploit these vulnerabilities in DVWA, including stealing cookies, extracting database information, and creating a backdoor PHP shell. The document is intended to educate users about web security risks and show how hackers can compromise applications.
Attques web
Attques webTarek MOHAMED The document discusses various web security attacks and solutions. It begins by noting that developers often focus on features and speed of development over security, leaving vulnerabilities. The top 10 web application attacks are then listed: injection, broken authentication, cross-site scripting, insecure direct object references, security misconfiguration, sensitive data exposure, missing access controls, cross-site request forgery, use of known vulnerable components, and unvalidated redirects/forwards. The document then provides more details on injection attacks like SQL injection and command injection, as well as cross-site scripting and cross-site request forgery attacks. Prevention techniques for these common attacks are also discussed.
PHPUG Presentation
PHPUG PresentationDamon Cortesi This document summarizes common web application vulnerabilities like SQL injection and cross-site scripting (XSS) for PHP applications. It provides examples of each vulnerability and discusses mitigation strategies like input sanitization, encoding output, and using security frameworks. It also covers other risks like cross-site request forgery (CSRF) and the importance of secure server configurations.
null Bangalore meet - Php Security
null Bangalore meet - Php Securityn|u - The Open Security Community This document summarizes common web application vulnerabilities like cross-site scripting (XSS), SQL injection, and file uploads. It provides examples of each vulnerability and recommendations for mitigation strategies. For XSS, it recommends sanitizing input and escaping output. For SQL injection, it suggests using parameterized queries, stored procedures, and escaping strings. For file uploads, it advises validating file types, randomizing filenames, and restricting directory permissions. The document aims to help secure PHP web applications from these common risks.
Xss mitigation php [Repaired]
Xss mitigation php [Repaired]Tinashe Makuti This document discusses mitigating cross-site scripting (XSS) attacks in PHP. It describes XSS as when an attacker injects scripts into a web application's output that are then executed by a user's browser. The dangers of unmitigated XSS include stolen cookies, deployed trojans, and stolen user data. PHP provides functions like htmlentities(), htmlspecialchars(), get_magic_quotes_gpc(), stripslashes(), and mysql_real_escape_string() to sanitize input and prevent XSS. Examples are given showing how these functions can neutralize dangerous code by converting HTML tags to entities. The document also discusses setting the HttpOnly attribute in PHP to prevent client-side scripts from accessing protected
Web Application Security - Folio3
Web Application Security - Folio3Folio3 Software The document outlines the critical vulnerabilities in web application security, highlighting that 75% of cyber attacks stem from such applications. It details common vulnerabilities like cross-site scripting (XSS), SQL injection, and cross-site request forgery (CSRF), along with preventative measures. Additionally, it stresses the importance of input validation, error handling, and regular updates to protect against exploitation.
Security In PHP Applications
Security In PHP ApplicationsAditya Mooley The document discusses security best practices for PHP applications, emphasizing the importance of protecting sensitive information from malicious users. It covers various security issues such as input validation, cross-site scripting (XSS), SQL injection, file inclusion, and session fixation, along with methods for prevention. Additionally, the author provides references for further reading on PHP security risks and attacks.
Application and Website Security -- Fundamental Edition
Application and Website Security -- Fundamental EditionDaniel Owens The document provides an agenda for a course on application and website security. The agenda covers common input validation flaws like SQL injection and cross-site scripting, access control flaws like session hijacking, encryption flaws, security tools, and concludes with additional resources for further information. The document uses examples to demonstrate various security vulnerabilities and how they can be exploited.
Ad
More from n|u - The Open Security Community (20)
Hardware security testing 101 (Null - Delhi Chapter)
Hardware security testing 101 (Null - Delhi Chapter)n|u - The Open Security Community Arun Mane is the founder and director of AmynaSec Labs. He is a security speaker and trainer who has presented at many conferences including Defcon, Blackhat, Nullcon, and HITB. His areas of expertise include security testing of IoT devices, connected vehicles, medical devices, and industrial control systems. Some common issues he finds include devices being publicly accessible, having backdoors, hardcoded credentials, and crypto or web application management problems. His testing methodology involves assessing web and mobile applications, embedded device communications, hardware testing through reverse engineering, and analyzing communication protocols and stored data.
Osint primer
Osint primern|u - The Open Security Community This document outlines an agenda for a presentation on open-source intelligence (OSINT) gathering techniques. The agenda includes an introduction to OSINT, different types of intelligence gathering, a scenario example, OSINT gathering tactics and tools like Shodan, TheHarvester and Google dorks, applications of OSINT, a demonstration, references for OSINT, and a conclusion. Key OSINT tools that will be demonstrated include Twitter, Shodan, TheHarvester and Google dorks for gathering information from public online sources.
SSRF exploit the trust relationship
SSRF exploit the trust relationshipn|u - The Open Security Community This document provides an overview of server-side request forgery (SSRF) vulnerabilities, including what SSRF is, its impact, common attacks, bypassing filters, and mitigations. SSRF allows an attacker to induce the application to make requests to internal or external servers from the server side, bypassing access controls. This can enable attacks on the server itself or other backend systems and escalate privileges. The document discusses techniques for exploiting trust relationships and bypassing blacklists/whitelists to perform SSRF attacks. It also covers blind SSRF and ways to detect them using out-of-band techniques. Mitigations include avoiding user input that can trigger server requests, sanitizing input, whitelist
Nmap basics
Nmap basicsn|u - The Open Security Community Nmap is a network scanning tool that can perform port scanning, operating system detection, and version detection among other features. It works by sending TCP and UDP packets to a target machine and examining the response, comparing it to its database to determine open ports and operating system. There are different scanning techniques that can be used like TCP SYN scanning, UDP scanning, and OS detection. Nmap also includes a scripting engine that allows users to write scripts to automate networking tasks. The presentation concludes with demonstrating Nmap's features through some examples.
Metasploit primary
Metasploit primaryn|u - The Open Security Community The document provides an introduction and overview of the Metasploit Framework. It defines key terms like vulnerability, exploit, and payload. It outlines the scenario of testing a subnet to find vulnerabilities. It describes the main features of msfconsole like searching for modules, using specific modules, and configuring options. It promotes understanding and proper use, emphasizing that Metasploit alone does not make someone a hacker.
Api security-testing
Api security-testingn|u - The Open Security Community 1) The document provides guidance on testing APIs for security weaknesses, including enumerating the attack surface, common tools to use, what to test for (e.g. authentication, authorization, injections), and demo apps to practice on.
2) It recommends testing authentication and authorization mechanisms like tokens, injections attacks on state-changing requests, and how data is consumed client-side.
3) The document also discusses testing for denial of service conditions, data smuggling through middleware, API rate limiting, and cross-origin requests.
Introduction to TLS 1.3
Introduction to TLS 1.3n|u - The Open Security Community TLS 1.3 is an update to the Transport Layer Security protocol that improves security and privacy. It removes vulnerable optional parts of TLS 1.2 and only supports strong ciphers to implement perfect forward secrecy. The handshake process is also significantly shortened. TLS 1.3 provides security benefits by removing outdated ciphers and privacy benefits by enabling perfect forward secrecy by default, ensuring only endpoints can decrypt traffic even if server keys are compromised in the future.
Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_gir...
Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_gir...n|u - The Open Security Community This document provides an introduction to hacking mainframes in 2020. It begins with an overview of mainframe systems and terminology. It then discusses reconnaissance methods like port scanning and credential theft to gain initial access. Next, it covers conducting internal reconnaissance to escalate privileges by exploiting surrogate users, APF authorized libraries, and UNIX privilege escalation techniques. The document aims to provide enough context for curiosity about hacking mainframe systems.
Talking About SSRF,CRLF
Talking About SSRF,CRLFn|u - The Open Security Community The document discusses CRLF injection and SSRF vulnerabilities. CRLF injection occurs when user input is directly parsed into response headers without sanitization, allowing special characters to be injected. SSRF is when a server is induced to make HTTP requests to domains of an attacker's choosing, potentially escalating access. Mitigations include sanitizing user input, implementing whitelists for allowed domains/protocols, and input validation.
Building active directory lab for red teaming
Building active directory lab for red teamingn|u - The Open Security Community The document provides an overview of Active Directory, including its components and how it is used to centrally manage users, computers, and other objects within a network. It discusses key Active Directory concepts such as forests, domains, organizational units, users, computers, and domain trusts. It also provides step-by-step instructions for setting up an Active Directory lab environment for red teaming purposes and integrating a client machine into the domain.
Owning a company through their logs
Owning a company through their logsn|u - The Open Security Community A security engineer discusses how logs and passive reconnaissance can reveal sensitive information like AWS credentials. The engineer searched for open Jenkins and SonarQube instances which led to discovering Slack channels containing AWS access keys. Key lessons are to know your boundaries, automate mundane tasks, don't presume systems mask secrets, and persistence is important in security work.
Introduction to shodan
Introduction to shodann|u - The Open Security Community Shodan is a search engine that indexes internet-connected devices and provides information about devices, banners, and metadata. It works by generating random IP addresses and port scans to retrieve banner information from devices. This information is then stored in a searchable database. Users can search Shodan's database using filters like country, city, IP address, operating system, and ports. Shodan can be accessed through its website or command line interface. While useful for security research, Shodan also raises privacy and security concerns by revealing information about unprotected devices.
Cloud security
Cloud security n|u - The Open Security Community This document outlines an agenda for discussing cloud security. It begins with an introduction to cloud computing and deployment models. It then discusses challenges of cloud computing and why cloud security is important. Specific threats like data breaches and account hijacking are listed. The document reviews the shared responsibility model and scope of security in public clouds. It describes cloud security penetration testing methods like static and dynamic application testing. Finally, it provides prerequisites and methods for conducting cloud penetration testing, including reconnaissance, threat modeling, and following standard testing methodologies.
Detecting persistence in windows
Detecting persistence in windowsn|u - The Open Security Community This document discusses several techniques for maintaining persistence on Windows systems, including modifying accessibility features, injecting into image file execution options, using AppInit DLLs, application shimming, BITS jobs, registry run keys, and Windows Management Instrumentation event subscriptions. It provides details on how each technique works, common implementations, required privileges, relevant data sources, and example event log entries.
Frida - Objection Tool Usage
Frida - Objection Tool Usagen|u - The Open Security Community Frida is a dynamic instrumentation toolkit that allows injecting JavaScript into applications. Objection is a runtime mobile exploration toolkit powered by Frida that helps assess the security of mobile apps. It supports iOS and Android. Objection allows exploring apps by listing classes, methods, and injecting scripts to enable dynamic analysis like dumping keychain entries.
OSQuery - Monitoring System Process
OSQuery - Monitoring System Processn|u - The Open Security Community Osquery is an open source tool that allows users to perform SQL queries on their system to retrieve information. It supports various platforms and makes it easy to get details about the system. Osquery consists of Osqueryi, Osqueryd, and Osqueryctl components. Basic queries can be run in user context mode to view system information, configuration, and tables. Osqueryd runs in daemon mode and can be configured using packs and decorators to monitor specific events and files. Osqueryctl is used to control the Osquery daemon process.
DevSecOps Jenkins Pipeline -Security
DevSecOps Jenkins Pipeline -Securityn|u - The Open Security Community This document discusses DevSecOps, beginning with an introduction from Tibin Lukose. It then covers some challenges in DevSecOps such as developers lacking security skills, cultural challenges, and difficulties balancing speed, coverage and accuracy in testing. The document proposes a model DevSecOps company, Infosys, and provides a demo and contact information for any further questions.
Extensible markup language attacks
Extensible markup language attacksn|u - The Open Security Community This document provides an introduction to XML and related technologies like libxml2, XSLT, XPath, and XML attacks. It discusses the basics of XML including elements, tags, attributes, and validation. It also describes common XML libraries and tools like libxml2, xmllint, and xsltproc. Finally, it provides an overview of different types of XML attacks like XML injection, XPath injection, XXE, and XSLT injection.
Linux for hackers
Linux for hackersn|u - The Open Security Community This document contains the agenda for a presentation on Linux for hackers. The agenda includes discussing the Linux file system, managing virtual machines smartly, command line tools like alias, tee, pipe, grep, cut, uniq, and xargs, Bash scripting, logging, and proxy chaining. It also mentions demonstrating several commands and tools. The presentation aims to be an interactive session where the presenter will answer any questions from attendees.
Android Pentesting
Android Pentestingn|u - The Open Security Community This document provides an overview of Android penetration testing. It discusses requirements and tools for static and dynamic analysis, including Apptitude, Genymotion, and ADB. It covers analyzing the Android manifest and classes.dex files. It also describes vulnerabilities in WebViews, such as loading cleartext content and improper SSL handling. Best practices for coding securely on Android are also presented.
Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_gir...
Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_gir...n|u - The Open Security Community
Recently uploaded (20)
The Future of Data, AI, and AR: Innovation Inspired by You.pdf
The Future of Data, AI, and AR: Innovation Inspired by You.pdfSafe Software The future of FME is inspired by you. We can't wait to show you what's ahead for FME and Safe Software.
Securing Account Lifecycles in the Age of Deepfakes.pptx
Securing Account Lifecycles in the Age of Deepfakes.pptxFIDO Alliance Securing Account Lifecycles in the Age of Deepfakes
9-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection.
FIDO Seminar: Authentication for a Billion Consumers - Amazon.pptx
FIDO Seminar: Authentication for a Billion Consumers - Amazon.pptxFIDO Alliance FIDO Seminar: Authentication for a Billion Consumers - Amazon
Lessons Learned from Developing Secure AI Workflows.pdf
Lessons Learned from Developing Secure AI Workflows.pdfPriyanka Aash Lessons Learned from Developing Secure AI Workflows
PyCon SG 25 - Firecracker Made Easy with Python.pdf
PyCon SG 25 - Firecracker Made Easy with Python.pdfMuhammad Yuga Nugraha Explore the ease of managing Firecracker microVM with the firecracker-python. In this session, I will introduce the basics of Firecracker microVM and demonstrate how this custom SDK facilitates microVM operations easily. We will delve into the design and development process behind the SDK, providing a behind-the-scenes look at its creation and features. While traditional Firecracker SDKs were primarily available in Go, this module brings a simplicity of Python to the table.
Enhance GitHub Copilot using MCP - Enterprise version.pdf
Enhance GitHub Copilot using MCP - Enterprise version.pdfNilesh Gule Slide deck related to the GitHub Copilot Bootcamp in Melbourne on 17 June 2025
FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce.pptx
FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce.pptxFIDO Alliance FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce
OpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.
Information Security Response Team Nepal_npCERT_Vice_President_Sudan_Jha.pdf
Information Security Response Team Nepal_npCERT_Vice_President_Sudan_Jha.pdfICT Frame Magazine Pvt. Ltd. Artificial Intelligence (AI) is rapidly changing the face of cybersecurity across the globe. In Nepal, the shift is already underway. Vice President of the Information Security Response Team Nepal (npCERT) and Information Security Consultant at One Cover Pvt. Ltd., Sudan Jha, recently presented an in-depth workshop on how AI can strengthen national security and digital defenses.
Crypto Super 500 - 14th Report - June2025.pdf
Crypto Super 500 - 14th Report - June2025.pdfStephen Perrenod This OrionX's 14th semi-annual report on the state of the cryptocurrency mining market. The report focuses on Proof-of-Work cryptocurrencies since those use substantial supercomputer power to mint new coins and encode transactions on their blockchains. Only two make the cut this time, Bitcoin with $18 billion of annual economic value produced and Dogecoin with $1 billion. Bitcoin has now reached the Zettascale with typical hash rates of 0.9 Zettahashes per second. Bitcoin is powered by the world's largest decentralized supercomputer in a continuous winner take all lottery incentive network.
Creating Inclusive Digital Learning with AI: A Smarter, Fairer Future
Creating Inclusive Digital Learning with AI: A Smarter, Fairer FutureImpelsys Inc. Have you ever struggled to read a tiny label on a medicine box or tried to navigate a confusing website? Now imagine if every learning experience felt that way—every single day.
For millions of people living with disabilities, poorly designed content isn’t just frustrating. It’s a barrier to growth. Inclusive learning is about fixing that. And today, AI is helping us build digital learning that’s smarter, kinder, and accessible to everyone.
Accessible learning increases engagement, retention, performance, and inclusivity for everyone. Inclusive design is simply better design.
War_And_Cyber_3_Years_Of_Struggle_And_Lessons_For_Global_Security.pdf
War_And_Cyber_3_Years_Of_Struggle_And_Lessons_For_Global_Security.pdfbiswajitbanerjee38 Russia is one of the most aggressive nations when it comes to state coordinated cyberattacks — and Ukraine has been at the center of their crosshairs for 3 years. This report, provided the State Service of Special Communications and Information Protection of Ukraine contains an incredible amount of cybersecurity insights, showcasing the coordinated aggressive cyberwarfare campaigns of Russia against Ukraine.
It brings to the forefront that understanding your adversary, especially an aggressive nation state, is important for cyber defense. Knowing their motivations, capabilities, and tactics becomes an advantage when allocating resources for maximum impact.
Intelligence shows Russia is on a cyber rampage, leveraging FSB, SVR, and GRU resources to professionally target Ukraine’s critical infrastructures, military, and international diplomacy support efforts.
The number of total incidents against Ukraine, originating from Russia, has steadily increased from 1350 in 2021 to 4315 in 2024, but the number of actual critical incidents has been managed down from a high of 1048 in 2022 to a mere 59 in 2024 — showcasing how the rapid detection and response to cyberattacks has been impacted by Ukraine’s improved cyber resilience.
Even against a much larger adversary, Ukraine is showcasing outstanding cybersecurity, enabled by strong strategies and sound tactics. There are lessons to learn for any enterprise that could potentially be targeted by aggressive nation states.
Definitely worth the read!
The Future of Technology: 2025-2125 by Saikat Basu.pdf
The Future of Technology: 2025-2125 by Saikat Basu.pdfSaikat Basu A peek into the next 100 years of technology. From Generative AI to Global AI networks to Martian Colonisation to Interstellar exploration to Industrial Nanotechnology to Artificial Consciousness, this is a journey you don't want to miss. Which ones excite you the most? Which ones are you apprehensive about? Feel free to comment! Let the conversation begin!
Raman Bhaumik - Passionate Tech Enthusiast
Raman Bhaumik - Passionate Tech EnthusiastRaman Bhaumik A Junior Software Developer with a flair for innovation, Raman Bhaumik excels in delivering scalable web solutions. With three years of experience and a solid foundation in Java, Python, JavaScript, and SQL, she has streamlined task tracking by 20% and improved application stability.
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...Fwdays We will explore how e-commerce projects prepare for the busiest time of the year, which key aspects to focus on, and what to expect. We’ll share our experience in setting up auto-scaling, load balancing, and discuss the loads that Silpo handles, as well as the solutions that help us navigate this season without failures.
FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptx
FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptxFIDO Alliance FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography
Wenn alles versagt - IBM Tape schützt, was zählt! Und besonders mit dem neust...
Wenn alles versagt - IBM Tape schützt, was zählt! Und besonders mit dem neust...Josef Weingand IBM LTO10
Information Security Response Team Nepal_npCERT_Vice_President_Sudan_Jha.pdf
Information Security Response Team Nepal_npCERT_Vice_President_Sudan_Jha.pdfICT Frame Magazine Pvt. Ltd.
Secure coding | XSS Attacks on current Web Applications
- 1. Cross-Site Scripting Attacks on Current Web Applications
- 2. Introduction An attacker gets control of the user’s browser in order to execute a malicious script within the context of trust of the web application’s site. As a result, and if the embedded code is successfully executed, the attacker might then be able to access, passively or actively, to any sensitive browser resource associated to the web application (e.g., cookies, session IDs, etc.)
- 3. THREATS!!! Everything from account hijacking, changing of user settings, cookie theft/poisoning, or false advertising is possible. Steal cookies which can then be used to impersonate customer and have access to their data and privileges. This is also known as Session Hijacking. Redirect the user to another website of their choosing. Maybe one that may be quite offensive, or one that attempts to install malware onto users computer; Display alternate content on your own website.
- 4. History of Attacks October 2001, -----Hotmail ---- Remote attacker was allowed to steal .NET Passport identifiers of Hotmail’s users by collecting their cookies. October 2005, ------ MySpace, utilized by the worm Samy to propagate itself across MySpace’s user profiles. November 2006,Orkut, was vulnerable to cookie stealing by simply posting the stealing script into the attacker’s profile.
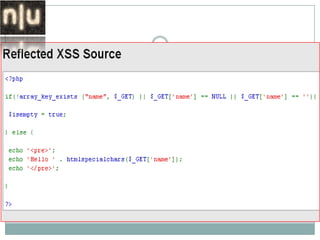
- 7. User input is reflected immediately on the page by server-side scripts without proper sanitization. To exploit, the attacker has to provide the victim with a modified URL, passing the code to be inserted as a parameter. This attack is done by encoding data in the URL, thus disguising the injected code from the user.
- 10. Persistent XSS Attacks When the data entered by the user are stored on the server for a certain length of time, the attack is called "persistent". All of the website's users have access to the page where the harmful code was introduced. Commonly found in: Contact/Feedback pages, Log viewers, Exception handlers, Chat applications/Forums, etc.
- 12. BACHAA V !!!
- 14. No Protection
- 15. Data Validation Application accepts correct data. User data must be validated to ensure it is of the corrected type, and discarded if it doesn’t pass the validation process. Allow a limited set of special characters.
- 16. Preg Match Performs a regular expression match.
- 17. Output Escaping Protects integrity of displayed/output data, Should escape the data when presenting it to the user. Prevents the browser from applying any unintended meaning to any special sequence of characters that may be found.
- 18. htmlspecialchars
- 20. Data Sanitization Manipulating the data to make sure it is safe. Removing any unwanted bits from the data and normalizing it to the correct form.
- 23. htmlentities Converts all applicable characters to HTML entities. Default value for this argument is ISO-8859-1 in versions of PHP prior to 5.4.0, and UTF-8 from PHP 5.4.0 onwards. ** http://coderstoolbox.net/
- 25. Available flags constants ID Description ENT_COMPAT Will convert double-quotes and leave single-quotes alone. ENT_QUOTES Will convert both double and single quotes. ENT_NOQUOTES Will leave both double and single quotes unconverted.
- 26. ID Flags FILTER_SANITIZE_EM AIL FILTER_SANITIZE_EN CODED Remove all characters except letters, digits and !#$%&'*+/=?^_`{|}~@.[]. FILTER_FLAG_STRIP_LOW , FILTER_FLAG_STRIP_HIG H, FILTER_FLAG_ENCODE_L OW, FILTER_FLAG_ENCODE_HI GH URL-encode string, optionally strip or encode special characters. Apply addslashes(). FILTER_SANITIZE_MAGIC _QUOTES FILTER_SANITIZE_NUMB ER_FLOAT Description FILTER_FLAG_ALLOW_FR ACTION, FILTER_FLAG_ALLOW_TH Remove all characters except digits, +- and optionally .,eE.
- 27. ID Flags FILTER_SANITIZE _NUMBER_INT Description Remove all characters except digits, plus and minus sign. FILTER_SANITIZE _SPECIAL_CHARS FILTER_FLAG_STRIP_LOW, FILTER_FLAG_STRIP_HIGH, FILTER_FLAG_ENCODE_HIGH HTMLescape '"<>& and characters with ASCII value less than 32, optionally strip or encode other special characters. FILTER_SANITIZE _STRING FILTER_FLAG_NO_ENCODE_Q UOTES, FILTER_FLAG_STRIP_LOW, FILTER_FLAG_STRIP_HIGH, FILTER_FLAG_ENCODE_LOW, FILTER_FLAG_ENCODE_HIGH, FILTER_FLAG_ENCODE_AMP Strip tags, optionally strip or encode special characters. FILTER_SANITIZE _STRIPPED Alias of "string" filter.
- 28. ID Flags FILTER_SANITIZE_UR L Description Remove all characters except letters, digits and $_.+!*'(),{}|^~[]`<> #%";/?:@&=. FILTER_UNSAFE_RA W FILTER_FLAG_STRIP_LOW Do nothing, optionally , strip or encode special FILTER_FLAG_STRIP_HIG characters. H, FILTER_FLAG_ENCODE_L OW, FILTER_FLAG_ENCODE_HI GH, FILTER_FLAG_ENCODE_A MP FILTER_SANITIZE_FU LL_SPECIAL_CHARS FILTER_FLAG_NO_ENCOD E_QUOTES, Equivalent to callinghtmlspecialchar s() withENT_QUOT ES set. Encoding quotes can be disabled
- 29. Mod Security(Web Application Firewall) Protects against attacks that target websites. csrf_protection session_hijacking comment_spam authentication_tracking protocol_violations sql_injection_attacks xss_attacks brute_force, and many more
- 33. How to change Contact info Go to : • binariesapacheerror • Open contact.html.var
- 34. Modified Code Change contact information
- 35. Disable Apache Signature and/or Apache Banner ADD in httpd.config of apache to remove apache version disclosure ServerTokens ProductOnly ServerTokens takes 1 argument, 'Prod', 'Major', 'Minor', 'Min', 'OS', or 'Full'""
- 36. Before After
- 37. ADD/replace/change in php.ini to remove php version disclosure expose_php = Off display_errors=Off register_globals = Off
- 39. Disable Version Disclosure Go to : • binariesapacheerrorinclude • Open bottom.html By Default we see this
- 42. My customized error page !!
- 43. Stopping Sensitive file disclosure Turn off automatic indexing. Instruct Apache to reject all requests for files matching a series of regular expressions given below. Goto httpd.conf file to deny access to . htaccess files.
- 44. Protecting bakup files Add in httpd.config TheFilesMatchdirective only looks at the last part of the full filename
- 45. Disable Directory Indexing Listing of files like see in Windows Explorer as opposed to a web page. Attacker can gain valuable information about your site. Files may may include sensitive information, such as backup script files htaccess files, or text files with note. Can allow access files outside the web root directory, leading to the stealing of system files.
- 46. How to Disable Directory Listings in Apache Navigate to your Apache config file (httpd.conf) Find – “Options FollowSymLinks Indexes” Replace by – “Options FollowSymLinks” Done
- 47. FollowSymLinks makes Apache follow system symbolic links (shortcuts, if you would) in your file system. Indexes allows access to open folders within your file system.
- 49. Disable powerful functions in php Disable functions that may be useful to an attacker but not necessary to the application. Disable execution of OS commands Open php.ini and search “disable_functions”. Write “shell_exec “ (without comma in front of disable_functions).
- 51. Other functions exec, passthru, shell_exec, system, proc_open, popen, curl_exec, curl_multi_exec, pcntl_exec, dl". If the application needs to execute OS commands, it should use "pcntl_exec", because it provides better abstraction of parameters than the others.
