Algorithms Lecture 4: Sorting Algorithms I
19 likes13,780 views
The document discusses three sorting algorithms: bubble sort, selection sort, and insertion sort. Bubble sort works by repeatedly swapping adjacent elements that are in the wrong order. Selection sort finds the minimum element and swaps it into the sorted portion of the array. Insertion sort inserts elements into the sorted portion of the array, swapping as needed to put the element in the correct position. Both selection sort and insertion sort have a time complexity of O(n^2) in the worst case.
1 of 92
Downloaded 815 times























































































Ad
Recommended
Algorithms Lecture 6: Searching Algorithms



Algorithms Lecture 6: Searching AlgorithmsMohamed Loey We will discuss the following: Search Algorithms, Linear Search, Binary Search, Jump Search, and Interpolation Search
Algorithms Lecture 5: Sorting Algorithms II



Algorithms Lecture 5: Sorting Algorithms IIMohamed Loey We will discuss the following: Sorting Algorithms, Counting Sort, Radix Sort, Merge Sort.Algorithms, Time Complexity & Space Complexity, Algorithm vs Pseudocode, Some Algorithm Types, Programming Languages, Python, Anaconda.
Algorithms Lecture 2: Analysis of Algorithms I



Algorithms Lecture 2: Analysis of Algorithms IMohamed Loey This document discusses analysis of algorithms and time complexity. It explains that analysis of algorithms determines the resources needed to execute algorithms. The time complexity of an algorithm quantifies how long it takes. There are three cases to analyze - worst case, average case, and best case. Common notations for time complexity include O(1), O(n), O(n^2), O(log n), and O(n!). The document provides examples of algorithms and determines their time complexity in different cases. It also discusses how to combine complexities of nested loops and loops in algorithms.
Algorithms Lecture 7: Graph Algorithms



Algorithms Lecture 7: Graph AlgorithmsMohamed Loey We will discuss the following: Graph, Directed vs Undirected Graph, Acyclic vs Cyclic Graph, Backedge, Search vs Traversal, Breadth First Traversal, Depth First Traversal, Detect Cycle in a Directed Graph.
Algorithms Lecture 1: Introduction to Algorithms



Algorithms Lecture 1: Introduction to AlgorithmsMohamed Loey We will discuss the following: Algorithms, Time Complexity & Space Complexity, Algorithm vs Pseudo code, Some Algorithm Types, Programming Languages, Python, Anaconda.
Algorithms Lecture 3: Analysis of Algorithms II



Algorithms Lecture 3: Analysis of Algorithms IIMohamed Loey We will discuss the following: Maximum Pairwise Product, Fibonacci, Greatest Common Divisors, Naive algorithm is too slow. The Efficient algorithm is much better. Finding the correct algorithm requires knowing something interesting about the problem
Sorting Algorithms



Sorting AlgorithmsMohammed Hussein This document discusses different sorting algorithms including bubble sort, insertion sort, and selection sort. It provides details on each algorithm, including time complexity, code examples, and graphical examples. Bubble sort is an O(n2) algorithm that works by repeatedly comparing and swapping adjacent elements. Insertion sort also has O(n2) time complexity but is more efficient than bubble sort for small or partially sorted lists. Selection sort finds the minimum value and swaps it into place at each step.
Divide and conquer



Divide and conquerDr Shashikant Athawale The document discusses divide and conquer algorithms. It describes divide and conquer as a design strategy that involves dividing a problem into smaller subproblems, solving the subproblems recursively, and combining the solutions. It provides examples of divide and conquer algorithms like merge sort, quicksort, and binary search. Merge sort works by recursively sorting halves of an array until it is fully sorted. Quicksort selects a pivot element and partitions the array into subarrays of smaller and larger elements, recursively sorting the subarrays. Binary search recursively searches half-intervals of a sorted array to find a target value.
Hashing



HashingAmar Jukuntla Hashing is a technique used to uniquely identify objects by assigning each object a key, such as a student ID or book ID number. A hash function converts large keys into smaller keys that are used as indices in a hash table, allowing for fast lookup of objects in O(1) time. Collisions, where two different keys hash to the same index, are resolved using techniques like separate chaining or linear probing. Common applications of hashing include databases, caches, and object representation in programming languages.
Priority Queue in Data Structure



Priority Queue in Data StructureMeghaj Mallick This document discusses priority queues. It defines a priority queue as a queue where insertion and deletion are based on some priority property. Items with higher priority are removed before lower priority items. There are two main types: ascending priority queues remove the smallest item, while descending priority queues remove the largest item. Priority queues are useful for scheduling jobs in operating systems, where real-time jobs have highest priority and are scheduled first. They are also used in network communication to manage limited bandwidth.
linked list in data structure 



linked list in data structure shameen khan This document discusses data structures and linked lists. It provides definitions and examples of different types of linked lists, including:
- Single linked lists, which contain nodes with a data field and a link to the next node.
- Circular linked lists, where the last node links back to the first node, forming a loop.
- Doubly linked lists, where each node contains links to both the previous and next nodes.
- Operations on linked lists such as insertion, deletion, traversal, and searching are also described.
SEARCHING AND SORTING ALGORITHMS



SEARCHING AND SORTING ALGORITHMSGokul Hari The document discusses various searching and sorting algorithms. It describes linear search, binary search, and interpolation search for searching unsorted and sorted lists. It also explains different sorting algorithms like bubble sort, selection sort, insertion sort, quicksort, shellsort, heap sort, and merge sort. Linear search searches sequentially while binary search uses divide and conquer. Sorting algorithms like bubble sort, selection sort, and insertion sort are in-place and have quadratic time complexity in the worst case. Quicksort, mergesort, and heapsort generally have better performance.
Sorting



SortingAshim Lamichhane The document discusses sorting algorithms. It begins by defining sorting as arranging data in logical order based on a key. It then discusses internal and external sorting methods. For internal sorting, all data fits in memory, while external sorting handles data too large for memory. The document covers stability, efficiency, and time complexity of various sorting algorithms like bubble sort, selection sort, insertion sort, and merge sort. Merge sort uses a divide-and-conquer approach to sort arrays with a time complexity of O(n log n).
Time complexity



Time complexityKatang Isip Basic info about how to use time complexity and how to get the time of each program to solve the problem.
Greedy Algorithm - Knapsack Problem



Greedy Algorithm - Knapsack ProblemMadhu Bala The document discusses the knapsack problem and greedy algorithms. It defines the knapsack problem as an optimization problem where given constraints and an objective function, the goal is to find the feasible solution that maximizes or minimizes the objective. It describes the knapsack problem has having two versions: 0-1 where items are indivisible, and fractional where items can be divided. The fractional knapsack problem can be solved using a greedy approach by sorting items by value to weight ratio and filling the knapsack accordingly until full.
Sorting Techniques



Sorting TechniquesRafay Farooq This document provides an overview and comparison of insertion sort and shellsort sorting algorithms. It describes how insertion sort works by repeatedly inserting elements into a sorted left portion of the array. Shellsort improves on insertion sort by making passes with larger increments to shift values into approximate positions before final sorting. The document discusses the time complexities of both algorithms and provides examples to illustrate how they work.
AVL Tree



AVL TreeDr Sandeep Kumar Poonia An AVL tree is a self-balancing binary search tree that guarantees search, insertion, and deletion operations will take O(log n) time on average. It achieves this by ensuring the heights of the left and right subtrees of every node differ by at most one. When an insertion or deletion causes a height imbalance of two, rotations are performed to rebalance the tree.
Bubble sort



Bubble sortManek Ar The document describes the bubble sort algorithm. Bubble sort works by repeatedly swapping adjacent elements that are in the wrong order until the list is fully sorted. Each pass of bubble sort bubbles up the largest remaining element to its correct place near the end of the list. It takes multiple passes, with fewer comparisons each time, to fully sort the list from lowest to highest.
Queue in Data Structure 



Queue in Data Structure Janki Shah Contents:
1. What is Queue?
2. Operations perform on Queue with Algorithm & Example
3. Types of Queue with required example
Quick sort-Data Structure



Quick sort-Data StructureJeanie Arnoco Quicksort is a divide and conquer sorting algorithm that works by partitioning an array around a pivot value. It then recursively sorts the sub-arrays on each side. The key steps are: 1) Choose a pivot element to split the array into left and right halves, with all elements on the left being less than the pivot and all on the right being greater; 2) Recursively quicksort the left and right halves; 3) Combine the now-sorted left and right halves into a fully sorted array. The example demonstrates quicksorting an array of 6 elements by repeatedly partitioning around a pivot until the entire array is sorted.
Applications of stack



Applications of stackeShikshak The document discusses applications of stacks, including reversing strings and lists, Polish notation for mathematical expressions, converting between infix, prefix and postfix notations, evaluating postfix and prefix expressions, recursion, and the Tower of Hanoi problem. Recursion involves defining a function in terms of itself, with a stopping condition. Stacks can be used to remove recursion by saving local variables at each step.
Linear search-and-binary-search



Linear search-and-binary-searchInternational Islamic University This document provides an overview of linear search and binary search algorithms.
It explains that linear search sequentially searches through an array one element at a time to find a target value. It is simple to implement but has poor efficiency as the time scales linearly with the size of the input.
Binary search is more efficient by cutting the search space in half at each step. It works on a sorted array by comparing the target to the middle element and determining which half to search next. The time complexity of binary search is logarithmic rather than linear.
stack & queue



stack & queuemanju rani This document discusses stacks and queues as linear data structures. It defines stacks as last-in, first-out (LIFO) collections where the last item added is the first removed. Queues are first-in, first-out (FIFO) collections where the first item added is the first removed. Common stack and queue operations like push, pop, insert, and remove are presented along with algorithms and examples. Applications of stacks and queues in areas like expression evaluation, string reversal, and scheduling are also covered.
Linked List



Linked ListAshim Lamichhane a. Concept and Definition✓
b. Inserting and Deleting nodes ✓
c. Linked implementation of a stack (PUSH/POP) ✓
d. Linked implementation of a queue (Insert/Remove) ✓
e. Circular List
• Stack as a circular list (PUSH/POP) ✓
• Queue as a circular list (Insert/Remove) ✓
f. Doubly Linked List (Insert/Remove) ✓
For more course related material:
https://github.com/ashim888/dataStructureAndAlgorithm/
Personal blog
www.ashimlamichhane.com.np
Linked list



Linked listakshat360 Linked lists are linear data structures where each node contains a data field and a pointer to the next node. There are two types: singly linked lists where each node has a single next pointer, and doubly linked lists where each node has next and previous pointers. Common operations on linked lists include insertion and deletion which have O(1) time complexity for singly linked lists but require changing multiple pointers for doubly linked lists. Linked lists are useful when the number of elements is dynamic as they allow efficient insertions and deletions without shifting elements unlike arrays.
Algorithm analysis



Algorithm analysissumitbardhan This document provides an overview of algorithm analysis. It discusses how to analyze the time efficiency of algorithms by counting the number of operations and expressing efficiency using growth functions. Different common growth rates like constant, linear, quadratic, and exponential are introduced. Examples are provided to demonstrate how to determine the growth rate of different algorithms, including recursive algorithms, by deriving their time complexity functions. The key aspects covered are estimating algorithm runtime, comparing growth rates of algorithms, and using Big O notation to classify algorithms by their asymptotic behavior.
Hashing PPT



Hashing PPTSaurabh Kumar This document discusses hashing and different techniques for implementing dictionaries using hashing. It begins by explaining that dictionaries store elements using keys to allow for quick lookups. It then discusses different data structures that can be used, focusing on hash tables. The document explains that hashing allows for constant-time lookups on average by using a hash function to map keys to table positions. It discusses collision resolution techniques like chaining, linear probing, and double hashing to handle collisions when the hash function maps multiple keys to the same position.
Searching techniques in Data Structure And Algorithm



Searching techniques in Data Structure And Algorithm03446940736 Searching techniques in Data Structure And Algorithm
with animations with algorithms and details
try it to believe it
best way to explain every word
Convolutional Neural Network Models - Deep Learning



Convolutional Neural Network Models - Deep LearningMohamed Loey Convolutional Neural Network Models - Deep Learning
Convolutional Neural Network
ILSVRC
AlexNet (2012)
ZFNet (2013)
VGGNet (2014)
GoogleNet 2014)
ResNet (2015)
Conclusion
Convolutional Neural Network (CNN) is a multi-layer neural network
Computer Security Lecture 7: RSA



Computer Security Lecture 7: RSAMohamed Loey We will discuss the following: RSA Key generation , RSA Encryption , RSA Decryption , A Real World Example, RSA Security.
https://www.youtube.com/watch?v=x7QWJ13dgGs&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf&index=7
More Related Content
What's hot (20)
Hashing



HashingAmar Jukuntla Hashing is a technique used to uniquely identify objects by assigning each object a key, such as a student ID or book ID number. A hash function converts large keys into smaller keys that are used as indices in a hash table, allowing for fast lookup of objects in O(1) time. Collisions, where two different keys hash to the same index, are resolved using techniques like separate chaining or linear probing. Common applications of hashing include databases, caches, and object representation in programming languages.
Priority Queue in Data Structure



Priority Queue in Data StructureMeghaj Mallick This document discusses priority queues. It defines a priority queue as a queue where insertion and deletion are based on some priority property. Items with higher priority are removed before lower priority items. There are two main types: ascending priority queues remove the smallest item, while descending priority queues remove the largest item. Priority queues are useful for scheduling jobs in operating systems, where real-time jobs have highest priority and are scheduled first. They are also used in network communication to manage limited bandwidth.
linked list in data structure 



linked list in data structure shameen khan This document discusses data structures and linked lists. It provides definitions and examples of different types of linked lists, including:
- Single linked lists, which contain nodes with a data field and a link to the next node.
- Circular linked lists, where the last node links back to the first node, forming a loop.
- Doubly linked lists, where each node contains links to both the previous and next nodes.
- Operations on linked lists such as insertion, deletion, traversal, and searching are also described.
SEARCHING AND SORTING ALGORITHMS



SEARCHING AND SORTING ALGORITHMSGokul Hari The document discusses various searching and sorting algorithms. It describes linear search, binary search, and interpolation search for searching unsorted and sorted lists. It also explains different sorting algorithms like bubble sort, selection sort, insertion sort, quicksort, shellsort, heap sort, and merge sort. Linear search searches sequentially while binary search uses divide and conquer. Sorting algorithms like bubble sort, selection sort, and insertion sort are in-place and have quadratic time complexity in the worst case. Quicksort, mergesort, and heapsort generally have better performance.
Sorting



SortingAshim Lamichhane The document discusses sorting algorithms. It begins by defining sorting as arranging data in logical order based on a key. It then discusses internal and external sorting methods. For internal sorting, all data fits in memory, while external sorting handles data too large for memory. The document covers stability, efficiency, and time complexity of various sorting algorithms like bubble sort, selection sort, insertion sort, and merge sort. Merge sort uses a divide-and-conquer approach to sort arrays with a time complexity of O(n log n).
Time complexity



Time complexityKatang Isip Basic info about how to use time complexity and how to get the time of each program to solve the problem.
Greedy Algorithm - Knapsack Problem



Greedy Algorithm - Knapsack ProblemMadhu Bala The document discusses the knapsack problem and greedy algorithms. It defines the knapsack problem as an optimization problem where given constraints and an objective function, the goal is to find the feasible solution that maximizes or minimizes the objective. It describes the knapsack problem has having two versions: 0-1 where items are indivisible, and fractional where items can be divided. The fractional knapsack problem can be solved using a greedy approach by sorting items by value to weight ratio and filling the knapsack accordingly until full.
Sorting Techniques



Sorting TechniquesRafay Farooq This document provides an overview and comparison of insertion sort and shellsort sorting algorithms. It describes how insertion sort works by repeatedly inserting elements into a sorted left portion of the array. Shellsort improves on insertion sort by making passes with larger increments to shift values into approximate positions before final sorting. The document discusses the time complexities of both algorithms and provides examples to illustrate how they work.
AVL Tree



AVL TreeDr Sandeep Kumar Poonia An AVL tree is a self-balancing binary search tree that guarantees search, insertion, and deletion operations will take O(log n) time on average. It achieves this by ensuring the heights of the left and right subtrees of every node differ by at most one. When an insertion or deletion causes a height imbalance of two, rotations are performed to rebalance the tree.
Bubble sort



Bubble sortManek Ar The document describes the bubble sort algorithm. Bubble sort works by repeatedly swapping adjacent elements that are in the wrong order until the list is fully sorted. Each pass of bubble sort bubbles up the largest remaining element to its correct place near the end of the list. It takes multiple passes, with fewer comparisons each time, to fully sort the list from lowest to highest.
Queue in Data Structure 



Queue in Data Structure Janki Shah Contents:
1. What is Queue?
2. Operations perform on Queue with Algorithm & Example
3. Types of Queue with required example
Quick sort-Data Structure



Quick sort-Data StructureJeanie Arnoco Quicksort is a divide and conquer sorting algorithm that works by partitioning an array around a pivot value. It then recursively sorts the sub-arrays on each side. The key steps are: 1) Choose a pivot element to split the array into left and right halves, with all elements on the left being less than the pivot and all on the right being greater; 2) Recursively quicksort the left and right halves; 3) Combine the now-sorted left and right halves into a fully sorted array. The example demonstrates quicksorting an array of 6 elements by repeatedly partitioning around a pivot until the entire array is sorted.
Applications of stack



Applications of stackeShikshak The document discusses applications of stacks, including reversing strings and lists, Polish notation for mathematical expressions, converting between infix, prefix and postfix notations, evaluating postfix and prefix expressions, recursion, and the Tower of Hanoi problem. Recursion involves defining a function in terms of itself, with a stopping condition. Stacks can be used to remove recursion by saving local variables at each step.
Linear search-and-binary-search



Linear search-and-binary-searchInternational Islamic University This document provides an overview of linear search and binary search algorithms.
It explains that linear search sequentially searches through an array one element at a time to find a target value. It is simple to implement but has poor efficiency as the time scales linearly with the size of the input.
Binary search is more efficient by cutting the search space in half at each step. It works on a sorted array by comparing the target to the middle element and determining which half to search next. The time complexity of binary search is logarithmic rather than linear.
stack & queue



stack & queuemanju rani This document discusses stacks and queues as linear data structures. It defines stacks as last-in, first-out (LIFO) collections where the last item added is the first removed. Queues are first-in, first-out (FIFO) collections where the first item added is the first removed. Common stack and queue operations like push, pop, insert, and remove are presented along with algorithms and examples. Applications of stacks and queues in areas like expression evaluation, string reversal, and scheduling are also covered.
Linked List



Linked ListAshim Lamichhane a. Concept and Definition✓
b. Inserting and Deleting nodes ✓
c. Linked implementation of a stack (PUSH/POP) ✓
d. Linked implementation of a queue (Insert/Remove) ✓
e. Circular List
• Stack as a circular list (PUSH/POP) ✓
• Queue as a circular list (Insert/Remove) ✓
f. Doubly Linked List (Insert/Remove) ✓
For more course related material:
https://github.com/ashim888/dataStructureAndAlgorithm/
Personal blog
www.ashimlamichhane.com.np
Linked list



Linked listakshat360 Linked lists are linear data structures where each node contains a data field and a pointer to the next node. There are two types: singly linked lists where each node has a single next pointer, and doubly linked lists where each node has next and previous pointers. Common operations on linked lists include insertion and deletion which have O(1) time complexity for singly linked lists but require changing multiple pointers for doubly linked lists. Linked lists are useful when the number of elements is dynamic as they allow efficient insertions and deletions without shifting elements unlike arrays.
Algorithm analysis



Algorithm analysissumitbardhan This document provides an overview of algorithm analysis. It discusses how to analyze the time efficiency of algorithms by counting the number of operations and expressing efficiency using growth functions. Different common growth rates like constant, linear, quadratic, and exponential are introduced. Examples are provided to demonstrate how to determine the growth rate of different algorithms, including recursive algorithms, by deriving their time complexity functions. The key aspects covered are estimating algorithm runtime, comparing growth rates of algorithms, and using Big O notation to classify algorithms by their asymptotic behavior.
Hashing PPT



Hashing PPTSaurabh Kumar This document discusses hashing and different techniques for implementing dictionaries using hashing. It begins by explaining that dictionaries store elements using keys to allow for quick lookups. It then discusses different data structures that can be used, focusing on hash tables. The document explains that hashing allows for constant-time lookups on average by using a hash function to map keys to table positions. It discusses collision resolution techniques like chaining, linear probing, and double hashing to handle collisions when the hash function maps multiple keys to the same position.
Searching techniques in Data Structure And Algorithm



Searching techniques in Data Structure And Algorithm03446940736 Searching techniques in Data Structure And Algorithm
with animations with algorithms and details
try it to believe it
best way to explain every word
Viewers also liked (6)
Convolutional Neural Network Models - Deep Learning



Convolutional Neural Network Models - Deep LearningMohamed Loey Convolutional Neural Network Models - Deep Learning
Convolutional Neural Network
ILSVRC
AlexNet (2012)
ZFNet (2013)
VGGNet (2014)
GoogleNet 2014)
ResNet (2015)
Conclusion
Convolutional Neural Network (CNN) is a multi-layer neural network
Computer Security Lecture 7: RSA



Computer Security Lecture 7: RSAMohamed Loey We will discuss the following: RSA Key generation , RSA Encryption , RSA Decryption , A Real World Example, RSA Security.
https://www.youtube.com/watch?v=x7QWJ13dgGs&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf&index=7
PMP Lecture 1: Introduction to Project Management



PMP Lecture 1: Introduction to Project ManagementMohamed Loey https://mloey.github.io/courses/pmp2017.html
https://www.youtube.com/watch?v=XUoEr6kee6k&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf&index=1&t=2s
We will discuss the following: History of Project Management, Project Management, Program Management, Portfolio Management, Project Management Office, PMBOK, PMI.
Computer Security Lecture 5: Simplified Advanced Encryption Standard



Computer Security Lecture 5: Simplified Advanced Encryption StandardMohamed Loey Simplified Advanced Encryption Standard, S-AES Encryption and Decryption, S-AES Key Generation, S-AES Encryption, S-AES Decryption
https://www.youtube.com/watch?v=pa7s442lRL0&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf&index=6
Deep Learning - Overview of my work II



Deep Learning - Overview of my work IIMohamed Loey Deep Learning Machine Learning MNIST CIFAR 10 Residual Network AlexNet VGGNet GoogleNet Nvidia Deep learning (DL) is a hierarchical structure network which through simulates the human brain’s structure to extract the internal and external input data’s features
C++ Programming Language 



C++ Programming Language Mohamed Loey Basic Information
Expressions
Statements IF Else Switch While Do While
Arrays and Strings
Functions
Ad
Similar to Algorithms Lecture 4: Sorting Algorithms I (20)
UNEC__1683196273.pptx



UNEC__1683196273.pptxhuseynmusayev2 The document discusses several searching algorithms: linear search, binary search, jump search, and interpolation search. Linear search sequentially checks each element to find a match. Binary search repeatedly halves the search interval. Jump search checks elements by jumping ahead fixed steps. Interpolation search uses the position formula to calculate locations to search. The time complexities are O(n) for linear search, O(log n) for binary search, O(√n) for jump search, and O(log(log n)) or O(n) for interpolation search depending on element distribution.
chapter 1



chapter 1yatheesha This document provides an overview of a lecture on designing and analyzing computer algorithms. It discusses key concepts like what an algorithm and program are, common algorithm design techniques like divide-and-conquer and greedy methods, and how to analyze algorithms' time and space complexity. The goals of analyzing algorithms are to understand their behavior, improve efficiency, and determine whether problems can be solved within a reasonable time frame.
Data Structure (MC501)



Data Structure (MC501)Kamal Singh Lodhi The document provides an overview of several sorting algorithms, including insertion sort, bubble sort, selection sort, and radix sort. It describes the basic approach for each algorithm through examples and pseudocode. Analysis of the time complexity is also provided, with insertion sort, bubble sort, and selection sort having worst-case performance of O(n^2) and radix sort having performance of O(nk) where k is the number of passes.
Lecture 1.pptx



Lecture 1.pptxALIZAIB KHAN This document provides an introduction to algorithms and their design and analysis. It defines an algorithm as a well-defined set of steps to solve a problem and notes they must be unambiguous and produce the same output each time. Examples are given of finding the largest number in a list and sorting algorithms. The use of algorithms in computer systems is discussed as well as why their design and analysis is important for problem solving and programming.
Lecture 01-2.ppt



Lecture 01-2.pptRaoHamza24 This document discusses the objectives and topics of the CS-311 Design and Analysis of Algorithms course. The objectives are to design algorithms using techniques like divide and conquer, develop problem solving skills, and analyze algorithms to compare efficiencies. An algorithm is defined as a sequence of unambiguous instructions to solve a problem. Sorting algorithms like selection sort and merge sort are presented as examples and analyzed based on time complexity. The process of solving a problem with algorithms includes understanding the problem, designing a solution, implementing and testing code, and analyzing performance. Key constructs like sequences, selections, iterations, and recursion are discussed for analyzing time complexity of algorithms.
01-Slides.pdf



01-Slides.pdfemo1421 This document outlines the goals and techniques of a course on designing and analyzing algorithms, including how to devise, express, validate, analyze, and test algorithms. It provides insertion sort as an example, walking through how to develop, represent, prove correctness, determine time complexity, and test the algorithm. The course aims to teach techniques like divide and conquer, dynamic programming, greedy algorithms, backtracking, and branch and bound.
Cis435 week01



Cis435 week01ashish bansal This document provides an introduction to algorithms and algorithm analysis. It defines what an algorithm is, provides examples, and discusses analyzing algorithms to determine their efficiency. Insertion sort and merge sort are presented as examples and their time complexities are analyzed. Asymptotic notation is introduced to describe an algorithm's order of growth and provide bounds on its running time. Key points covered include analyzing best-case and worst-case time complexities, using recurrences to model algorithms, and the properties of asymptotic notation. Homework problems are assigned from the textbook chapters.
Unit 1 chapter 1 Design and Analysis of Algorithms



Unit 1 chapter 1 Design and Analysis of AlgorithmsP. Subathra Kishore, KAMARAJ College of Engineering and Technology, Madurai Anna University Regulation 2017
Design and Analysis of Algorithms
Text : Introduction to Design and Analysis of Algorithms by Anany Levitin
Sorting techniques



Sorting techniquesLovely Professional University This document discusses sorting algorithms. It explains that sorting refers to arranging data in a specified order like numerical or alphabetical. Selection sort is described as finding the minimum element and swapping it into the correct position in each pass through the array until sorted. An example of selection sort is provided, showing the steps and swaps to sort an array of numbers.
l01-intro (3).ppt



l01-intro (3).pptssuser15a62a This document discusses algorithms and their design. It defines an algorithm as a sequence of unambiguous instructions to solve a problem within a finite time. The key steps in designing algorithms are: understanding the problem, choosing appropriate data structures and computational means, designing and proving the algorithm, analyzing its efficiency, and coding it. Important problem types include sorting, searching, graphs, and numerical problems. Fundamental data structures include arrays, linked lists, stacks, queues, trees, graphs, sets, bags and dictionaries.
Lect01



Lect01yatheesha This document provides an overview of an algorithms course. It discusses analyzing and designing efficient algorithms to solve problems like finding the closest pair of points or solving the traveling salesman problem. The course will cover general algorithmic techniques like divide-and-conquer, greedy algorithms, and dynamic programming. It will also discuss analyzing algorithms' computational complexity and running time. Students will complete homework problem sets, programming assignments, quizzes and a final project over the course of the semester.
Data structure using c module 3



Data structure using c module 3smruti sarangi This slides contains the descriptions of Searching Techniques, Sorting Techniques and Hashing Techniques
Algorithm analysis (All in one)



Algorithm analysis (All in one)jehan1987 Algorithm analysis (All in one): Algorithm, Algoritthm Analysis, data structure, algorithm, algorithm Complexity, Floyd Algorithm, Kruskel Algorithm, Pakistan, Sorting Complexity, Big O notations, Time Complexity, Computational Complexity, Bubble Sort Complexity, Best case, Worst Case, Inversion in Algorithm, Traveling Salesperson Problem.
Lecture 13 data structures and algorithms



Lecture 13 data structures and algorithmsAakash deep Singhal The document discusses various sorting algorithms and their complexity. It begins by defining sorting as arranging data in increasing or decreasing order. It then discusses the complexity of sorting algorithms in terms of comparisons, swaps, and assignments needed. Sorting algorithms are divided into internal sorts, which use only main memory, and external sorts, which use external storage like disks. Popular internal sorting algorithms discussed in detail include bubble sort, selection sort, insertion sort, and merge sort. Bubble sort has a time complexity of O(n2) while merge sort and quicksort have better time complexities of O(nlogn).
Different Searching and Sorting Methods.pptx



Different Searching and Sorting Methods.pptxMinakshee Patil Linear Search, Binary Search
Bubble Sort, Merge Sort
Quick Sort, Selection Sort
Insertion Sort, Radix Sort, Bucket Sort
Complexity Issues of algorithms
Linear Search is defined as a sequential search algorithm that starts at one end and goes through each element of a list until the desired element is found, otherwise the search continues till the end of the data set. It is the easiest searching algorithm.
In Binary search, best case occurs when the element to search is found in first comparison, i.e., when the first middle element itself is the element to be searched. The best-case time complexity of Binary search is O(1).
Average Case :
The average case time complexity of Binary search is O(logn)
Worst Case:
In Binary search, the worst case occurs, when we have to keep reducing the search space till it has only one element. The worst-case time complexity of Binary search is O(logn).
Traverse a collection of elements
Move from the front to the end
“Bubble” the largest value to the end using pair-wise comparisons and swapping
Algorithm Bubble_Sort(a, n)
{
for i := 1 to n – 1 do
{
// to keep track of the number of iterations
for j := 0 to n –i-1
{
// to compare the elements inside the particular iteration
if (a[j] > a[j + 1]) then
swap(a[j], a[j + 1]); // swap if any element is greater than its adjacent element
}
}
}
Best Case: The best case occurs when the array is already sorted. So the number of comparisons required is N-1 and the number of swaps required = 0. Hence the best case complexity is O(N).
Worst Case: The worst-case condition for bubble sort occurs when elements of the array are arranged in decreasing order.
In the worst case, the total number of iterations or passes required to sort a given array is (N-1). where ‘N’ is the number of elements present in the array.
In each iteration Total number of swaps = Total number of comparison
Total number of comparison (Worst case) = N(N-1)/2
Total number of swaps (Worst case) = N(N-1)/2
So worst case and average case time complexity is O(N2) as N2 is the highest order term.
Partitioning a[1:n] into two subarrays in such a way that sorted subarrays do not need to be merged later.
This is accomplished by rearranging the elements in a[1:n] such that a[i] <= a[j] for all i between 1 to m, and for all j between m+1 to n where 1<=m<=n.
Thus, the elements in a[1:m] and a[m+1:n] can be sorted independently
No need for merging
The rearrangement of the elements is accomplished by picking some element of a[],say t = a[s],and then reordering the other elements so that all elements appearing before t in a[1:n] are less than or equal to t and all elements appearing after t are greater than or equal to t.
This rearranging is referred to as partitioning.
In selection sort, the smallest value among the unsorted elements of the array is selected in every pass and inserted to its appropriate position into the array.
In this algorithm, the array is divided into two parts, first is sorted part, and ano
Lec1.ppt



Lec1.pptssuser8bddb2 This course introduces students to analyzing and designing computer algorithms. The course objectives are to analyze asymptotic performance, demonstrate familiarity with major algorithms and data structures, apply algorithm design paradigms and analysis methods, and synthesize efficient algorithms for engineering problems. Topics covered include foundations of algorithms, accuracy, efficiency, comparing efficiencies, and understanding various algorithm variants and their design and analysis.
Sorting



SortingGopi Saiteja The document discusses sorting algorithms. It begins by defining the sorting problem as taking an unsorted sequence of numbers and outputting a permutation of the numbers in ascending order. It then discusses different types of sorts like internal versus external sorts and stable versus unstable sorts. Specific algorithms covered include insertion sort, bubble sort, and selection sort. Analysis is provided on the best, average, and worst case time complexity of insertion sort.
Insertion sort bubble sort selection sort



Insertion sort bubble sort selection sortUmmar Hayat The document discusses three sorting algorithms: insertion sort, bubble sort, and selection sort. Insertion sort has best-case linear time but worst-case quadratic time, sorting elements in place. Bubble sort repeatedly compares and swaps adjacent elements, having quadratic time in all cases. Selection sort finds the minimum element and exchanges it into the sorted portion of the array in each pass, with quadratic time.
Sorting algorithums > Data Structures & Algorithums



Sorting algorithums > Data Structures & AlgorithumsAin-ul-Moiz Khawaja The document discusses sorting algorithms including bubble sort, selection sort, insertion sort, and merge sort. It provides pseudocode and explanations of how each algorithm works. Bubble sort, selection sort, and insertion sort have O(n2) runtime and are best for small datasets, while merge sort uses a divide-and-conquer approach to sort arrays with O(n log n) runtime, making it more efficient for large datasets. Radix sort is also discussed as an alternative sorting method that is optimized for certain data types.
Unit 1 chapter 1 Design and Analysis of Algorithms



Unit 1 chapter 1 Design and Analysis of AlgorithmsP. Subathra Kishore, KAMARAJ College of Engineering and Technology, Madurai
Ad
More from Mohamed Loey (19)
Lecture 6: Deep Learning Applications



Lecture 6: Deep Learning ApplicationsMohamed Loey We will discuss the following: Deep Learning Applications, Image Processing, Video Processing, Medical, Computer Network, Big Data, Bioinformatics.
Lecture 5: Convolutional Neural Network Models



Lecture 5: Convolutional Neural Network ModelsMohamed Loey We will discuss the following: Convolutional Neural Network, AlexNet, ZFNet, VGGNet, GoogleNet, ResNet, DenseNet.
Lecture 4: Deep Learning Frameworks



Lecture 4: Deep Learning FrameworksMohamed Loey The document provides information on several popular deep learning frameworks: TensorFlow, Caffe, Theano, Torch, CNTK, and Keras. It describes each framework's creator, license, programming languages supported, and brief purpose or use. TensorFlow is noted as the most popular framework, created by Google for machine learning research. Caffe is described as the fastest, Theano as most efficient, Torch is used by Facebook AI, CNTK for high scalability, and Keras for easy experimentation across frameworks. The document also provides examples of building and running computational graphs in TensorFlow.
Lecture 4: How it Works: Convolutional Neural Networks



Lecture 4: How it Works: Convolutional Neural NetworksMohamed Loey We will discuss the following: Filtering, Convolution, Convolution layer, Normalization, Rectified Linear Units, Pooling, Pooling layer, ReLU layer, Deep stacking, Fully connected layer.
Lecture 3: Convolutional Neural Networks



Lecture 3: Convolutional Neural NetworksMohamed Loey We will discuss the following: Deep vs Machine Learning, Superstar Researchers, Superstar Companies, Deep Learning, Deep Learning Requirements, Deep Learning Architectures, Convolution Neural Network, Case studies, LeNet,AlexNet, ZFNet, GoogLeNet, VGGNet, ResNet, ILSVRC, MNIST, CIFAR-10, CNN Optimization , NVIDIA TITAN X.
Lecture 2: Artificial Neural Network



Lecture 2: Artificial Neural NetworkMohamed Loey We will discuss the following: Artificial Neural Network, Perceptron Learning Example, Artificial Neural Network Training Process, Forward propagation, Backpropagation, Classification of Handwritten Digits, Neural Network Zoo.
Lecture 1: Deep Learning for Computer Vision



Lecture 1: Deep Learning for Computer VisionMohamed Loey This document discusses how deep learning has helped advance computer vision capabilities. It notes that deep learning can help bridge the gap between pixels and meaning by allowing computers to recognize complex patterns in images. It provides an overview of related fields like image processing, machine learning, artificial intelligence, and computer graphics. It also lists some specific applications of deep learning like object detection, image classification, and generating descriptive text. Students are then assigned a task to research how deep learning has improved one particular topic and submit a two-page summary.
Design of an Intelligent System for Improving Classification of Cancer Diseases



Design of an Intelligent System for Improving Classification of Cancer DiseasesMohamed Loey The methodologies that depend on gene expression profile have been able to detect cancer since its inception. The previous works have spent great efforts to reach the best results. Some researchers have achieved excellent results in the classification process of cancer based on the gene expression profile using different gene selection approaches and different classifiers
Early detection of cancer increases the probability of recovery. This thesis presents an intelligent decision support system (IDSS) for early diagnosis of cancer-based on the microarray of gene expression profiles. The problem of this dataset is the little number of examples (not exceed hundreds) comparing to a large number of genes (in thousands). So, it became necessary to find out a method for reducing the features (genes) that are not relevant to the investigated disease to avoid overfitting. The proposed methodology used information gain (IG) for selecting the most important features from the input patterns. Then, the selected features (genes) are reduced by applying the Gray Wolf Optimization algorithm (GWO). Finally, the methodology exercises support vector machine (SVM) for cancer type classification. The proposed methodology was applied to three data sets (breast, colon, and CNS) and was evaluated by the classification accuracy performance measurement, which is most important in the diagnosis of diseases. The best results were gotten when integrating IG with GWO and SVM rating accuracy improved to 96.67% and the number of features was reduced to 32 feature of the CNS dataset.
This thesis investigates several classification algorithms and their suitability to the biological domain. For applications that suffer from high dimensionality, different feature selection methods are considered for illustration and analysis. Moreover, an effective system is proposed. In addition, Experiments were conducted on three benchmark gene expression datasets. The proposed system is assessed and compared with related work performance.
Computer Security - CCNA Security - Lecture 2



Computer Security - CCNA Security - Lecture 2Mohamed Loey We will discuss the following: Classical Security Methods, AAA, Authentication, Authorization, Accounting, AAA Characteristic, Local Based AAA, Server Based AAA, TACACS+ and RADIUS.
Computer Security - CCNA Security - Lecture 1



Computer Security - CCNA Security - Lecture 1Mohamed Loey We will discuss the following: CCNAS Overview, Threats Landscape, Hackers Tools, Tools. Kali Linux Parrot Linux Cisco Packet Tracer Wireshark Denial of Service
Distributed DoS
Man In The Middle
Phishing
Vishing
Smishing
Pharming
Sniffer
Password Attack
Algorithms Lecture 8: Pattern Algorithms



Algorithms Lecture 8: Pattern AlgorithmsMohamed Loey We will discuss the following: Pattern searching, Naive Pattern Searching, Regular Expression.
Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression
Computer Security Lecture 4.1: DES Supplementary Material



Computer Security Lecture 4.1: DES Supplementary MaterialMohamed Loey We will discuss the following: Data Encryption Standard, DES Algorithm, DES Key Creation
https://www.youtube.com/watch?v=1-lF4dePpts&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf
PMP Lecture 4: Project Integration Management



PMP Lecture 4: Project Integration ManagementMohamed Loey https://mloey.github.io/
We will discuss the following: Develop Project Charter, Develop Project Management Plan, Direct and Manage Project Work, Monitor and Control Project Work, Perform Integrated Change Control, Close Project or Phase.
Computer Security Lecture 4: Block Ciphers and the Data Encryption Standard



Computer Security Lecture 4: Block Ciphers and the Data Encryption StandardMohamed Loey We will discuss the following: Stream Ciphers and Block Ciphers, Data Encryption Standard, DES Algorithm, DES Key Creation, DES Encryption, The Strength Of DES.
https://www.youtube.com/watch?v=1-lF4dePpts&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf
Computer Security Lecture 3: Classical Encryption Techniques 2



Computer Security Lecture 3: Classical Encryption Techniques 2Mohamed Loey https://mloey.github.io/courses/security2017.html
https://www.youtube.com/watch?v=eGGnjwpaOIo&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf&index=3&t=584s
We will discuss the following: Polyalphabetic Ciphers, Vigenère Cipher, Autokey Cipher, Vernam Cipher, Transposition Techniques, Rail Fence Cipher, Row Transposition Cipher
Computer Security Lecture 2: Classical Encryption Techniques 1



Computer Security Lecture 2: Classical Encryption Techniques 1Mohamed Loey https://mloey.github.io/courses/security2017.html
https://www.youtube.com/watch?v=td_8AM80DUA&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf&index=2&t=37s
We will discuss the following: Symmetric Encryption, Substitution Techniques, Caesar Cipher, Monoalphabetic Cipher, Playfair Cipher, Hill Cipher
Computer Security Lecture 1: Overview



Computer Security Lecture 1: OverviewMohamed Loey https://mloey.github.io/courses/security2017.html
We will discuss the following: Cryptography, Computer Security, OSI Security Architecture, Security Structure Scheme, Key Properties, Symmetric Encryption, Asymmetric Encryption, finally Our Book
PMP Lecture 3: Project Management Processes



PMP Lecture 3: Project Management ProcessesMohamed Loey https://mloey.github.io/courses/pmp2017.html
We will discuss the following: Project Management Processes, Initiating Process, Planning Process, Executing Process, Monitoring and controlling Process, Closing Process, Knowledge Areas, Project Management Process and Knowledge Area Mapping
PMP Lecture 2: Project Management Framework



PMP Lecture 2: Project Management FrameworkMohamed Loey https://mloey.github.io/courses/pmp2017.html
We will discuss the following: Organization, Organizational Structures, Functional Organization, Projectized Organization, Matrix Organization, Influence of Organizational Structures on Projects.
Recently uploaded (20)
TV Shows and web-series quiz | QUIZ CLUB OF PSGCAS | 13TH MARCH 2025



TV Shows and web-series quiz | QUIZ CLUB OF PSGCAS | 13TH MARCH 2025Quiz Club of PSG College of Arts & Science HOW YOU DOIN'?
Cool, cool, cool...
Because that's what she said after THE QUIZ CLUB OF PSGCAS' TV SHOW quiz.
Grab your popcorn and be seated.
QM: THARUN S A
BCom Accounting and Finance (2023-26)
THE QUIZ CLUB OF PSGCAS.
Pfeiffer "Secrets to Changing Behavior in Scholarly Communication: A 2025 NIS...



Pfeiffer "Secrets to Changing Behavior in Scholarly Communication: A 2025 NIS...National Information Standards Organization (NISO) This presentation was provided by Nicole 'Nici" Pfeiffer of the Center for Open Science (COS), during the first session of our 2025 NISO training series "Secrets to Changing Behavior in Scholarly Communications." Session One was held June 5, 2025.
Final Sketch Designs for poster production.pptx



Final Sketch Designs for poster production.pptxbobby205207 Final Sketch Designs for poster production.
Artificial intelligence Presented by JM.



Artificial intelligence Presented by JM.jmansha170 AI (Artificial Intelligence) :
"AI is the ability of machines to mimic human intelligence, such as learning, decision-making, and problem-solving."
Important Points about AI:
1. Learning – AI can learn from data (Machine Learning).
2. Automation – It helps automate repetitive tasks.
3. Decision Making – AI can analyze and make decisions faster than humans.
4. Natural Language Processing (NLP) – AI can understand and generate human language.
5. Vision & Recognition – AI can recognize images, faces, and patterns.
6. Used In – Healthcare, finance, robotics, education, and more.
Owner By:
Name : Junaid Mansha
Work : Web Developer and Graphics Designer
Contact us : +92 322 2291672
Email : [email protected]
Rai dyansty Chach or Brahamn dynasty, History of Dahir History of Sindh NEP.pptx



Rai dyansty Chach or Brahamn dynasty, History of Dahir History of Sindh NEP.pptxDr. Ravi Shankar Arya Mahila P. G. College, Banaras Hindu University, Varanasi, India. This presentation has been made keeping in mind the students of undergraduate and postgraduate level. To keep the facts in a natural form and to display the material in more detail, the help of various books, websites and online medium has been taken. Whatever medium the material or facts have been taken from, an attempt has been made by the presenter to give their reference at the end.
In the seventh century, the rule of Sindh state was in the hands of Rai dynasty. We know the names of five kings of this dynasty- Rai Divji, Rai Singhras, Rai Sahasi, Rai Sihras II and Rai Sahasi II. During the time of Rai Sihras II, Nimruz of Persia attacked Sindh and killed him. After the return of the Persians, Rai Sahasi II became the king. After killing him, one of his Brahmin ministers named Chach took over the throne. He married the widow of Rai Sahasi and became the ruler of entire Sindh by suppressing the rebellions of the governors.
Strengthened Senior High School - Landas Tool Kit.pptx



Strengthened Senior High School - Landas Tool Kit.pptxSteffMusniQuiballo Landas Tool Kit is a very helpful guide in guiding the Senior High School students on their SHS academic journey. It will pave the way on what curriculum exits will they choose and fit in.
Webcrawler_Mule_AIChain_MuleSoft_Meetup_Hyderabad



Webcrawler_Mule_AIChain_MuleSoft_Meetup_HyderabadVeera Pallapu 1. MuleSoft AI Chain Concept Introduction
2. Demo on Mule AI Chain Connector
3. Q/A
4. Wrap up
Parenting Teens: Supporting Trust, resilience and independence



Parenting Teens: Supporting Trust, resilience and independencePooky Knightsmith For more information about my speaking and training work, visit: https://www.pookyknightsmith.com/speaking/
SESSION OVERVIEW:
Parenting Teens: Supporting Trust, Resilience & Independence
The teenage years bring new challenges—for teens and for you. In this practical session, we’ll explore how to support your teen through emotional ups and downs, growing independence, and the pressures of school and social life.
You’ll gain insights into the teenage brain and why boundary-pushing is part of healthy development, along with tools to keep communication open, build trust, and support emotional resilience. Expect honest ideas, relatable examples, and space to connect with other parents.
By the end of this session, you will:
• Understand how teenage brain development affects behaviour and emotions
• Learn ways to keep communication open and supportive
• Explore tools to help your teen manage stress and bounce back from setbacks
• Reflect on how to encourage independence while staying connected
• Discover simple strategies to support emotional wellbeing
• Share experiences and ideas with other parents
Ray Dalio How Countries go Broke the Big Cycle



Ray Dalio How Countries go Broke the Big CycleDadang Solihin A complete and practical understanding of the Big Debt Cycle. A much more practical understanding of how supply and demand really work compared to the conventional economic thinking. A complete and practical understanding of the Overall Big Cycle, which is driven by the Big Debt Cycle and the other major cycles, including the big political cycle within countries that changes political orders and the big geopolitical cycle that changes world orders.
Unit- 4 Biostatistics & Research Methodology.pdf



Unit- 4 Biostatistics & Research Methodology.pdfKRUTIKA CHANNE Blocking and confounding (when a third variable, or confounder, influences both the exposure and the outcome) system for Two-level factorials (a type of experimental design where each factor (independent variable) is investigated at only two levels, typically denoted as "high" and "low" or "+1" and "-1")
Regression modeling (statistical model that estimates the relationship between one dependent variable and one or more independent variables using a line): Hypothesis testing in Simple and Multiple regression models
Introduction to Practical components of Industrial and Clinical Trials Problems: Statistical Analysis Using Excel, SPSS, MINITAB®️, DESIGN OF EXPERIMENTS, R - Online Statistical Software to Industrial and Clinical trial approach
SEXUALITY , UNWANTED PREGANCY AND SEXUAL ASSAULT .pptx



SEXUALITY , UNWANTED PREGANCY AND SEXUAL ASSAULT .pptxPoojaSen20 SEXUALITY AND ITS TYPES , UNWANTED PREGANCY AND SEXUAL ASSAULT
Energy Balances Of Oecd Countries 2011 Iea Statistics 1st Edition Oecd



Energy Balances Of Oecd Countries 2011 Iea Statistics 1st Edition Oecdrazelitouali Energy Balances Of Oecd Countries 2011 Iea Statistics 1st Edition Oecd
Energy Balances Of Oecd Countries 2011 Iea Statistics 1st Edition Oecd
Energy Balances Of Oecd Countries 2011 Iea Statistics 1st Edition Oecd
Respiratory System , Urinary System



Respiratory System , Urinary SystemRushiMandali Human Anatomy and Physiology II Unit 3 B pharm Sem 2
Respiratory system
Anatomy of respiratory system with special reference to anatomy
of lungs, mechanism of respiration, regulation of respiration
Lung Volumes and capacities transport of respiratory gases,
artificial respiration, and resuscitation methods
Urinary system
Anatomy of urinary tract with special reference to anatomy of
kidney and nephrons, functions of kidney and urinary tract,
physiology of urine formation, micturition reflex and role of
kidneys in acid base balance, role of RAS in kidney and
disorders of kidney
Diptera: The Two-Winged Wonders, The Fly Squad: Order Diptera.pptx



Diptera: The Two-Winged Wonders, The Fly Squad: Order Diptera.pptxArshad Shaikh Diptera, commonly known as flies, is a large and diverse order of insects that includes mosquitoes, midges, gnats, and horseflies. Characterized by a single pair of wings (hindwings are modified into balancing organs called halteres), Diptera are found in almost every environment and play important roles in ecosystems as pollinators, decomposers, and food sources. Some species, however, are significant pests and disease vectors, transmitting diseases like malaria, dengue, and Zika virus.
LDMMIA Free Reiki Yoga S9 Grad Level Intuition II



LDMMIA Free Reiki Yoga S9 Grad Level Intuition IILDM & Mia eStudios Completed Sunday 6/8. For Weekend 6/14 & 15th. (Fathers Day Weekend US.) These workshops are also timeless for future students TY. No admissions needed.
A 9th FREE WORKSHOP
Reiki - Yoga
“Intuition-II, The Chakras”
Your Attendance is valued.
We hit over 5k views for Spring Workshops and Updates-TY.
Thank you for attending our workshops.
If you are new, do welcome.
Grad Students: I am planning a Reiki-Yoga Master Course (As a package). I’m Fusing both together.
This will include the foundation of each practice. Our Free Workshops can be used with any Reiki Yoga training package. Traditional Reiki does host rules and ethics. Its silent and within the JP Culture/Area/Training/Word of Mouth. It allows remote healing but there’s limits As practitioners and masters, we are not allowed to share certain secrets/tools. Some content is designed only for “Masters”. Some yoga are similar like the Kriya Yoga-Church (Vowed Lessons). We will review both Reiki and Yoga (Master tools) in the Course upcoming.
S9/This Week’s Focus:
* A continuation of Intuition-2 Development. We will review the Chakra System - Our temple. A misguided, misused situation lol. This will also serve Attunement later.
Thx for tuning in. Your time investment is valued. I do select topics related to our timeline and community. For those seeking upgrades or Reiki Levels. Stay tuned for our June packages. It’s for self employed/Practitioners/Coaches…
Review & Topics:
* Reiki Is Japanese Energy Healing used Globally.
* Yoga is over 5k years old from India. It hosts many styles, teacher versions, and it’s Mainstream now vs decades ago.
* Anything of the Holistic, Wellness Department can be fused together. My origins are Alternative, Complementary Medicine. In short, I call this ND. I am also a metaphysician. I learnt during the 90s New Age Era. I forget we just hit another wavy. It’s GenZ word of Mouth, their New Age Era. WHOA, History Repeats lol. We are fusing together.
* So, most of you have experienced your Spiritual Awakening. However; The journey wont be perfect. There will be some roller coaster events. The perks are: We are in a faster Spiritual Zone than the 90s. There’s more support and information available.
(See Presentation for all sections, THX AGAIN.)
Adam Grant: Transforming Work Culture Through Organizational Psychology



Adam Grant: Transforming Work Culture Through Organizational PsychologyPrachi Shah This presentation explores the groundbreaking work of Adam Grant, renowned organizational psychologist and bestselling author. It highlights his key theories on giving, motivation, leadership, and workplace dynamics that have revolutionized how organizations think about productivity, collaboration, and employee well-being. Ideal for students, HR professionals, and leadership enthusiasts, this deck includes insights from his major works like Give and Take, Originals, and Think Again, along with interactive elements for enhanced engagement.
How to Manage Upselling of Subscriptions in Odoo 18



How to Manage Upselling of Subscriptions in Odoo 18Celine George Subscriptions in Odoo 18 are designed to auto-renew indefinitely, ensuring continuous service for customers. However, businesses often need flexibility to adjust pricing or quantities based on evolving customer needs.
TV Shows and web-series quiz | QUIZ CLUB OF PSGCAS | 13TH MARCH 2025



TV Shows and web-series quiz | QUIZ CLUB OF PSGCAS | 13TH MARCH 2025Quiz Club of PSG College of Arts & Science
Pfeiffer "Secrets to Changing Behavior in Scholarly Communication: A 2025 NIS...



Pfeiffer "Secrets to Changing Behavior in Scholarly Communication: A 2025 NIS...National Information Standards Organization (NISO)
Rai dyansty Chach or Brahamn dynasty, History of Dahir History of Sindh NEP.pptx



Rai dyansty Chach or Brahamn dynasty, History of Dahir History of Sindh NEP.pptxDr. Ravi Shankar Arya Mahila P. G. College, Banaras Hindu University, Varanasi, India.
Algorithms Lecture 4: Sorting Algorithms I
- 1. Analysis and Design of Algorithms Sorting Algorithms I
- 2. Analysis and Design of Algorithms Sorting Algorithms Bubble Sort Selection Sort Insertion Sort
- 3. Analysis and Design of Algorithms Sorting Algorithm is an algorithm made up of a series of instructions that takes an array as input, and outputs a sorted array. There are many sorting algorithms, such as: Selection Sort, Bubble Sort, Insertion Sort, Merge Sort, Heap Sort, QuickSort, Radix Sort, Counting Sort, Bucket Sort, ShellSort, Comb Sort, Pigeonhole Sort, Cycle Sort
- 4. Analysis and Design of Algorithms Bubble Sort
- 5. Analysis and Design of Algorithms Bubble Sort is the simplest sorting algorithm that works by repeatedly swapping the adjacent elements if they are in wrong order.
- 6. Analysis and Design of Algorithms Algorithm: Step1: Compare each pair of adjacent elements in the list Step2: Swap two element if necessary Step3: Repeat this process for all the elements until the entire array is sorted
- 7. Analysis and Design of Algorithms Example 1 Assume the following Array: 5 1 4 2
- 8. Analysis and Design of Algorithms First Iteration: Compare 5 1 4 2 j j+1
- 9. Analysis and Design of Algorithms First Iteration: Swap 1 5 4 2 j j+1
- 10. Analysis and Design of Algorithms First Iteration: Compare 1 5 4 2 j j+1
- 11. Analysis and Design of Algorithms First Iteration: Swap 1 4 5 2 j j+1
- 12. Analysis and Design of Algorithms First Iteration: Compare 1 4 5 2 j j+1
- 13. Analysis and Design of Algorithms First Iteration: Swap 1 4 2 5 j j+1
- 14. Analysis and Design of Algorithms 1 4 2 5
- 15. Analysis and Design of Algorithms Second Iteration: Compare 1 4 2 5 j j+1
- 16. Analysis and Design of Algorithms Second Iteration: Compare 1 4 2 5 j j+1
- 17. Analysis and Design of Algorithms Second Iteration: Swap 1 2 4 5 j j+1
- 18. Analysis and Design of Algorithms 1 2 4 5
- 19. Analysis and Design of Algorithms Third Iteration: Compare 1 2 4 5 j j+1
- 20. Analysis and Design of Algorithms 1 2 4 5
- 21. Analysis and Design of Algorithms Array is now sorted 1 2 3 4
- 22. Analysis and Design of Algorithms 5 4 2 1 3 4 5 2 1 3 4 2 5 1 3 4 2 1 5 3 4 2 1 3 5 4 2 1 3 5 2 4 1 3 5 2 1 4 3 5 2 1 3 4 5 2 1 3 4 5 1 2 3 4 5 1 2 3 4 5 Example 2:
- 23. Analysis and Design of Algorithms What is the output of bubble sort after the 1st iteration given the following sequence of numbers: 13 2 9 4 18 45 37 63 a) 2 4 9 13 18 37 45 63 b) 2 9 4 13 18 37 45 63 c) 13 2 4 9 18 45 37 63 d) 2 4 9 13 18 45 37 63
- 24. Analysis and Design of Algorithms What is the output of bubble sort after the 1st iteration given the following sequence of numbers: 13 2 9 4 18 45 37 63 a) 2 4 9 13 18 37 45 63 b) 2 9 4 13 18 37 45 63 c) 13 2 4 9 18 45 37 63 d) 2 4 9 13 18 45 37 63
- 25. Analysis and Design of Algorithms Python Code
- 26. Analysis and Design of Algorithms
- 27. Analysis and Design of Algorithms Time Complexity: O(n2) as there are two nested loops Example of worst case 5 4 3 2 1
- 28. Analysis and Design of Algorithms Selection Sort
- 29. Analysis and Design of Algorithms The selection sort algorithm sorts an array by repeatedly finding the minimum element (considering ascending order) from unsorted part and putting it at the beginning.
- 30. Analysis and Design of Algorithms Algorithm: Step1: Find the minimum value in the list Step2: Swap it with the value in the current position Step3: Repeat this process for all the elements until the entire array is sorted
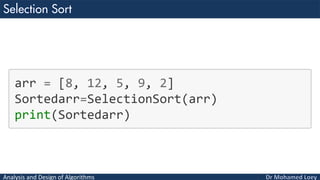
- 31. Analysis and Design of Algorithms Example 1 Assume the following Array: 8 12 5 9 2
- 32. Analysis and Design of Algorithms Compare 8 12 5 9 2 i j min
- 33. Analysis and Design of Algorithms Compare 8 12 5 9 2 i j min
- 34. Analysis and Design of Algorithms Move 8 12 5 9 2 j i min
- 35. Analysis and Design of Algorithms Compare 8 12 5 9 2 i min j
- 36. Analysis and Design of Algorithms Compare 8 12 5 9 2 i min j
- 37. Analysis and Design of Algorithms Move 8 12 5 9 2 i j min
- 38. Analysis and Design of Algorithms Smallest 8 12 5 9 2 i min
- 39. Analysis and Design of Algorithms Swap 8 12 5 9 2 min i
- 40. Analysis and Design of Algorithms Sorted Un Sorted 2 12 5 9 8 Sorted Un Sorted
- 41. Analysis and Design of Algorithms Compare 2 12 5 9 8 i min j Sorted
- 42. Analysis and Design of Algorithms Move 2 12 5 9 8 i min j Sorted
- 43. Analysis and Design of Algorithms Compare 2 12 5 9 8 Sorted i j min
- 44. Analysis and Design of Algorithms Compare 2 12 5 9 8 Sorted i j min
- 45. Analysis and Design of Algorithms Smallest 2 12 5 9 8 Sorted i min
- 46. Analysis and Design of Algorithms Swap 2 12 5 9 8 Sorted i min
- 47. Analysis and Design of Algorithms Sorted Un Sorted 2 5 12 9 8 Sorted Un Sorted
- 48. Analysis and Design of Algorithms Compare 2 5 12 9 8 Sorted i j min
- 49. Analysis and Design of Algorithms Move 2 5 12 9 8 Sorted i j min
- 50. Analysis and Design of Algorithms Compare 2 5 12 9 8 Sorted i min j
- 51. Analysis and Design of Algorithms Move 2 5 12 9 8 Sorted i min j
- 52. Analysis and Design of Algorithms Smallest 2 5 12 9 8 Sorted i min
- 53. Analysis and Design of Algorithms Swap 2 5 12 9 8 Sorted i min
- 54. Analysis and Design of Algorithms Sorted Un Sorted 2 5 8 9 12 Sorted Un Sorted
- 55. Analysis and Design of Algorithms Compare 2 5 8 9 12 Sorted i min j
- 56. Analysis and Design of Algorithms Sorted Un Sorted 2 5 8 9 12 Sorted Un Sorted
- 57. Analysis and Design of Algorithms Sorted Un Sorted 2 5 8 9 12 Sorted i min
- 58. Analysis and Design of Algorithms Array is now sorted 2 5 8 9 12 Sorted
- 59. Analysis and Design of Algorithms 12 10 16 11 9 7 Example 2: 7 10 16 11 9 12 7 9 16 11 10 12 7 9 10 11 16 12 7 9 10 11 16 12 7 9 10 11 12 16 12 10 16 11 9 7
- 60. Analysis and Design of Algorithms What is the output of selection sort after the 2nd iteration given the following sequence of numbers: 13 2 9 4 18 45 37 63 a) 2 4 9 13 18 37 45 63 b) 2 9 4 13 18 37 45 63 c) 13 2 4 9 18 45 37 63 d) 2 4 9 13 18 45 37 63
- 61. Analysis and Design of Algorithms What is the output of selection sort after the 2nd iteration given the following sequence of numbers: 13 2 9 4 18 45 37 63 a) 2 4 9 13 18 37 45 63 b) 2 9 4 13 18 37 45 63 c) 13 2 4 9 18 45 37 63 d) 2 4 9 13 18 45 37 63
- 62. Analysis and Design of Algorithms Python Code
- 63. Analysis and Design of Algorithms
- 64. Analysis and Design of Algorithms Time Complexity: O(n2) as there are two nested loops Example of worst case 2 3 4 5 1
- 65. Analysis and Design of Algorithms Insertion Sort
- 66. Analysis and Design of Algorithms Insertion sort is a simple sorting algorithm that works the way we sort playing cards in our hands.
- 67. Analysis and Design of Algorithms Algorithm: Step1: Compare each pair of adjacent elements in the list Step2: Insert element into the sorted list, until it occupies correct position. Step3: Swap two element if necessary Step4: Repeat this process for all the elements until the entire array is sorted
- 68. Analysis and Design of Algorithms Assume the following Array: 5 1 4 2
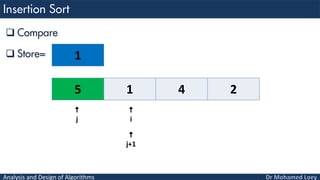
- 69. Analysis and Design of Algorithms Compare Store= 5 1 4 2 i j j+1 1
- 70. Analysis and Design of Algorithms Move Store= 5 4 2 i j j+1 1
- 71. Analysis and Design of Algorithms Move Store= 1 5 4 2 i j+1
- 72. Analysis and Design of Algorithms Compare Store= 1 5 4 2 i j 4 j+1
- 73. Analysis and Design of Algorithms Move Store= 1 5 2 i j 4 j+1
- 74. Analysis and Design of Algorithms Compare Store= 1 5 2 i j 4 j+1
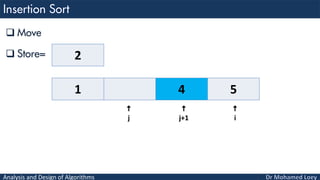
- 75. Analysis and Design of Algorithms Move Store= 1 4 5 2 i j j+1
- 76. Analysis and Design of Algorithms Compare Store= 1 4 5 2 i j 2 j+1
- 77. Analysis and Design of Algorithms Move Store= 1 4 5 i j 2 j+1
- 78. Analysis and Design of Algorithms Compare Store= 1 4 5 i j 2 j+1
- 79. Analysis and Design of Algorithms Move Store= 1 4 5 i j 2 j+1
- 80. Analysis and Design of Algorithms Compare Store= 1 4 5 i j 2 j+1
- 81. Analysis and Design of Algorithms Compare Store= 1 2 4 5 i j j+1
- 82. Analysis and Design of Algorithms Array is now sorted 1 2 4 5
- 83. Analysis and Design of Algorithms 5 1 8 3 9 2 Example 2: 1 5 8 3 9 2 1 5 8 3 9 2 1 3 5 8 9 2 1 3 5 8 9 2 1 2 3 5 8 9 5 1 8 3 9 2
- 84. Analysis and Design of Algorithms What is the output of insertion sort after the 1st iteration given the following sequence of numbers: 7 3 5 1 9 8 4 6 a) 3 7 5 1 9 8 4 6 b) 1 3 7 5 9 8 4 6 c) 3 4 1 5 6 8 7 9 d) 1 3 4 5 6 7 8 9
- 85. Analysis and Design of Algorithms What is the output of insertion sort after the 1st iteration given the following sequence of numbers: 7 3 5 1 9 8 4 6 a) 3 7 5 1 9 8 4 6 b) 1 3 7 5 9 8 4 6 c) 3 4 1 5 6 8 7 9 d) 1 3 4 5 6 7 8 9
- 86. Analysis and Design of Algorithms What is the output of insertion sort after the 2nd iteration given the following sequence of numbers: 7 3 5 1 9 8 4 6 a) 3 5 7 1 9 8 4 6 b) 1 3 7 5 9 8 4 6 c) 3 4 1 5 6 8 7 9 d) 1 3 4 5 6 7 8 9
- 87. Analysis and Design of Algorithms What is the output of insertion sort after the 2nd iteration given the following sequence of numbers: 7 3 5 1 9 8 4 6 a) 3 5 7 1 9 8 4 6 b) 1 3 7 5 9 8 4 6 c) 3 4 1 5 6 8 7 9 d) 1 3 4 5 6 7 8 9
- 88. Analysis and Design of Algorithms Python Code
- 89. Analysis and Design of Algorithms
- 90. Analysis and Design of Algorithms Time Complexity: O(n2) Example of worst case 5 4 3 2 1
- 91. Analysis and Design of Algorithms facebook.com/mloey [email protected] twitter.com/mloey linkedin.com/in/mloey [email protected] mloey.github.io
- 92. Analysis and Design of Algorithms www.YourCompany.com © 2020 Companyname PowerPoint Business Theme. All Rights Reserved. THANKS FOR YOUR TIME




