Algorithms Lecture 8: Pattern Algorithms
3 likes699 views
We will discuss the following: Pattern searching, Naive Pattern Searching, Regular Expression. Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression
1 of 68
Downloaded 73 times





![Analysis and Design of Algorithms
Example 1:
Input: txt[] = "THIS IS A TEST TEXT"
pat[] = "TEST"
Output: Pattern found at index 10](https://image.slidesharecdn.com/algorithms-lecture8-171202163400/85/Algorithms-Lecture-8-Pattern-Algorithms-6-320.jpg)
![Analysis and Design of Algorithms
Example 2:
Input: txt[] = "AABAACAADAABAABA"
pat[] = "AABA"
Output: Pattern found at index 0
Pattern found at index 9
Pattern found at index 12](https://image.slidesharecdn.com/algorithms-lecture8-171202163400/85/Algorithms-Lecture-8-Pattern-Algorithms-7-320.jpg)


















![Analysis and Design of Algorithms
Input: txt[] = "AABAACAADAABAABA"
pat[] = "AABA"
Output: Pattern found at index 0
Pattern found at index 9
Pattern found at index 12](https://image.slidesharecdn.com/algorithms-lecture8-171202163400/85/Algorithms-Lecture-8-Pattern-Algorithms-27-320.jpg)


![Analysis and Design of Algorithms
What is the best case?
The best case occurs when the first character of the pattern
is not present in text at all.
txt[] = "AABCCAADDEE"
pat[] = "FAA"](https://image.slidesharecdn.com/algorithms-lecture8-171202163400/85/Algorithms-Lecture-8-Pattern-Algorithms-30-320.jpg)
![Analysis and Design of Algorithms
What is the worst case ?
1) When all characters of the text and pattern are same.
txt[] = "AAAAAAAAAAAAAAAAAA"
pat[] = "AAAAA"](https://image.slidesharecdn.com/algorithms-lecture8-171202163400/85/Algorithms-Lecture-8-Pattern-Algorithms-31-320.jpg)
![Analysis and Design of Algorithms
2) Worst case also occurs when only the last character is
different.
txt[] = "AAAAAAAAAAAAAAAAAB"
pat[] = "AAAAB"](https://image.slidesharecdn.com/algorithms-lecture8-171202163400/85/Algorithms-Lecture-8-Pattern-Algorithms-32-320.jpg)







![Analysis and Design of Algorithms
w (lowercase w): matches a "word" character:
a letter or digit or underbar [a-z A-Z 0-9 _].](https://image.slidesharecdn.com/algorithms-lecture8-171202163400/85/Algorithms-Lecture-8-Pattern-Algorithms-40-320.jpg)

![Analysis and Design of Algorithms
d (lowercase d): decimal digit [0-9]](https://image.slidesharecdn.com/algorithms-lecture8-171202163400/85/Algorithms-Lecture-8-Pattern-Algorithms-42-320.jpg)
![Analysis and Design of Algorithms
s (lowercase s): matches a single whitespace
character -- space, newline, return, tab, form [
nrtf].](https://image.slidesharecdn.com/algorithms-lecture8-171202163400/85/Algorithms-Lecture-8-Pattern-Algorithms-43-320.jpg)


![Analysis and Design of Algorithms
[ ] : a range of characters can be
indicated by giving two characters and
separating them by a “-”.](https://image.slidesharecdn.com/algorithms-lecture8-171202163400/85/Algorithms-Lecture-8-Pattern-Algorithms-47-320.jpg)
![Analysis and Design of Algorithms
[ ]](https://image.slidesharecdn.com/algorithms-lecture8-171202163400/85/Algorithms-Lecture-8-Pattern-Algorithms-48-320.jpg)
![Analysis and Design of Algorithms
[^ ] : will match any character except this.](https://image.slidesharecdn.com/algorithms-lecture8-171202163400/85/Algorithms-Lecture-8-Pattern-Algorithms-49-320.jpg)


![Analysis and Design of Algorithms
Syntax Description Equivalent
d Matches any decimal digit [0-9]
D Matches any non-digit character [^0-9]
s Matches any whitespace character [ tnrfv]
S Matches any non-whitespace character [^ tnrfv]
w Matches any alphanumeric character [a-zA-Z0-9_]
W Matches any non-alphanumeric character [^a-zA-Z0-9_]](https://image.slidesharecdn.com/algorithms-lecture8-171202163400/85/Algorithms-Lecture-8-Pattern-Algorithms-52-320.jpg)




![Analysis and Design of Algorithms
Emails:
Square brackets can be used to indicate a set of chars, so [abc]
matches 'a' or 'b' or 'c'.](https://image.slidesharecdn.com/algorithms-lecture8-171202163400/85/Algorithms-Lecture-8-Pattern-Algorithms-57-320.jpg)


![Analysis and Design of Algorithms
Operators Description
. Matches with any single character except newline ‘n’
? Match 0 or 1 occurrence of the pattern to its left
+ Match 1 or more occurrences of the pattern to its left
* Match 0 or more occurrences of the pattern to its left
w Matches with a alphanumeric character
W Matches non alphanumeric character
d Matches with digits [0-9]
D Matches with non-digits](https://image.slidesharecdn.com/algorithms-lecture8-171202163400/85/Algorithms-Lecture-8-Pattern-Algorithms-60-320.jpg)
![Analysis and Design of Algorithms
Operators Description
s Matches with a single white space character (space, newline, tab)
S Matches any non-white space character
[..] Matches any single character in a square bracket
[^..] Matches any single character not in square bracket
It is used for special meaning characters
^ and $ ^ and $ match the start or end of the string respectively
{n,m} Matches at least n and at most m occurrences of expression
a| b Matches either a or b](https://image.slidesharecdn.com/algorithms-lecture8-171202163400/85/Algorithms-Lecture-8-Pattern-Algorithms-61-320.jpg)






Ad
Recommended
Algorithms Lecture 5: Sorting Algorithms II



Algorithms Lecture 5: Sorting Algorithms IIMohamed Loey We will discuss the following: Sorting Algorithms, Counting Sort, Radix Sort, Merge Sort.Algorithms, Time Complexity & Space Complexity, Algorithm vs Pseudocode, Some Algorithm Types, Programming Languages, Python, Anaconda.
Algorithms Lecture 3: Analysis of Algorithms II



Algorithms Lecture 3: Analysis of Algorithms IIMohamed Loey We will discuss the following: Maximum Pairwise Product, Fibonacci, Greatest Common Divisors, Naive algorithm is too slow. The Efficient algorithm is much better. Finding the correct algorithm requires knowing something interesting about the problem
Algorithms Lecture 4: Sorting Algorithms I



Algorithms Lecture 4: Sorting Algorithms IMohamed Loey The document discusses three sorting algorithms: bubble sort, selection sort, and insertion sort. Bubble sort works by repeatedly swapping adjacent elements that are in the wrong order. Selection sort finds the minimum element and swaps it into the sorted portion of the array. Insertion sort inserts elements into the sorted portion of the array, swapping as needed to put the element in the correct position. Both selection sort and insertion sort have a time complexity of O(n^2) in the worst case.
Algorithms Lecture 2: Analysis of Algorithms I



Algorithms Lecture 2: Analysis of Algorithms IMohamed Loey This document discusses analysis of algorithms and time complexity. It explains that analysis of algorithms determines the resources needed to execute algorithms. The time complexity of an algorithm quantifies how long it takes. There are three cases to analyze - worst case, average case, and best case. Common notations for time complexity include O(1), O(n), O(n^2), O(log n), and O(n!). The document provides examples of algorithms and determines their time complexity in different cases. It also discusses how to combine complexities of nested loops and loops in algorithms.
Algorithms Lecture 7: Graph Algorithms



Algorithms Lecture 7: Graph AlgorithmsMohamed Loey We will discuss the following: Graph, Directed vs Undirected Graph, Acyclic vs Cyclic Graph, Backedge, Search vs Traversal, Breadth First Traversal, Depth First Traversal, Detect Cycle in a Directed Graph.
Algorithms Lecture 1: Introduction to Algorithms



Algorithms Lecture 1: Introduction to AlgorithmsMohamed Loey We will discuss the following: Algorithms, Time Complexity & Space Complexity, Algorithm vs Pseudo code, Some Algorithm Types, Programming Languages, Python, Anaconda.
Chapter1.1 Introduction to design and analysis of algorithm.ppt



Chapter1.1 Introduction to design and analysis of algorithm.pptTekle12 This document discusses the design and analysis of algorithms. It begins with defining what an algorithm is - a well-defined computational procedure that takes inputs and produces outputs. It describes analyzing algorithms to determine their efficiency and comparing different algorithms that solve the same problem. The document outlines steps for designing algorithms, including understanding the problem, deciding a solution approach, designing the algorithm, proving correctness, and analyzing and coding it. It discusses using mathematical techniques like asymptotic analysis and Big O notation to analyze algorithms independently of implementations or inputs. The importance of analysis is also covered.
Hash table



Hash tableRajendran This document discusses hashing techniques for implementing symbol tables. It begins by reviewing the motivation for symbol tables in compilers and describing the basic operations of search, insertion and deletion that a hash table aims to support efficiently. It then discusses direct addressing and its limitations when key ranges are large. The concept of a hash function is introduced to map keys to a smaller range to enable direct addressing. Collision resolution techniques of chaining and open addressing are covered. Analysis of expected costs for different operations on chaining hash tables is provided. Various hash functions are described including division and multiplication methods, and the importance of choosing a hash function to distribute keys uniformly is discussed. The document concludes by mentioning universal hashing as a technique to randomize the hash function
Introduction to algorithms



Introduction to algorithmssubhashchandra197 The document provides an introduction to algorithms through a lecture on fundamentals of algorithm analysis. It defines an algorithm as a finite sequence of unambiguous instructions to solve a problem. Characteristics of algorithms like inputs, outputs, definiteness and finiteness are discussed. The document also describes various algorithm design techniques like brute force, divide and conquer and greedy algorithms. It explains steps to write algorithms using pseudo code and discusses validating, analyzing, testing programs and specifying algorithms through pseudo code and flowcharts.
Divide and conquer - Quick sort



Divide and conquer - Quick sortMadhu Bala divide and conquer , Example , benefits, Quick sort algorithm, complexity of quick sort, merits of quick sort
Hashing



HashingAmar Jukuntla Hashing is a technique used to uniquely identify objects by assigning each object a key, such as a student ID or book ID number. A hash function converts large keys into smaller keys that are used as indices in a hash table, allowing for fast lookup of objects in O(1) time. Collisions, where two different keys hash to the same index, are resolved using techniques like separate chaining or linear probing. Common applications of hashing include databases, caches, and object representation in programming languages.
Stuart russell and peter norvig artificial intelligence - a modern approach...



Stuart russell and peter norvig artificial intelligence - a modern approach...Lê Anh Đạt This document provides publishing information for the book "Artificial Intelligence: A Modern Approach". It lists the editorial staff and production team, including the Vice President and Editorial Director, Editor-in-Chief, Executive Editor, and others. It also provides copyright information, acknowledging that the content is protected and requires permission for reproduction. Finally, it is dedicated to the authors' families and includes a preface giving an overview of the book.
Heaps



HeapsHafiz Atif Amin This document provides information about priority queues and binary heaps. It defines a binary heap as a nearly complete binary tree where the root node has the maximum/minimum value. It describes heap operations like insertion, deletion of max/min, and increasing/decreasing keys. The time complexity of these operations is O(log n). Heapsort, which uses a heap data structure, is also covered and has overall time complexity of O(n log n). Binary heaps are often used to implement priority queues and for algorithms like Dijkstra's and Prim's.
K-Nearest Neighbor(KNN)



K-Nearest Neighbor(KNN)Abdullah al Mamun The K-Nearest Neighbors (KNN) algorithm is a robust and intuitive machine learning method employed to tackle classification and regression problems. By capitalizing on the concept of similarity, KNN predicts the label or value of a new data point by considering its K closest neighbours in the training dataset. In this article, we will learn about a supervised learning algorithm (KNN) or the k – Nearest Neighbours, highlighting it’s user-friendly nature.
What is the K-Nearest Neighbors Algorithm?
K-Nearest Neighbours is one of the most basic yet essential classification algorithms in Machine Learning. It belongs to the supervised learning domain and finds intense application in pattern recognition, data mining, and intrusion detection.
It is widely disposable in real-life scenarios since it is non-parametric, meaning, it does not make any underlying assumptions about the distribution of data (as opposed to other algorithms such as GMM, which assume a Gaussian distribution of the given data). We are given some prior data (also called training data), which classifies coordinates into groups identified by an attribute.
SEARCHING AND SORTING ALGORITHMS



SEARCHING AND SORTING ALGORITHMSGokul Hari The document discusses various searching and sorting algorithms. It describes linear search, binary search, and interpolation search for searching unsorted and sorted lists. It also explains different sorting algorithms like bubble sort, selection sort, insertion sort, quicksort, shellsort, heap sort, and merge sort. Linear search searches sequentially while binary search uses divide and conquer. Sorting algorithms like bubble sort, selection sort, and insertion sort are in-place and have quadratic time complexity in the worst case. Quicksort, mergesort, and heapsort generally have better performance.
Time complexity



Time complexityKatang Isip Basic info about how to use time complexity and how to get the time of each program to solve the problem.
Strassen's matrix multiplication



Strassen's matrix multiplicationMegha V The document discusses Strassen's algorithm for matrix multiplication. It begins by explaining traditional matrix multiplication that has a time complexity of O(n3). It then explains how the divide and conquer strategy can be applied by dividing the matrices into smaller square sub-matrices. Strassen improved upon this by reducing the number of multiplications from 8 to 7 terms, obtaining a time complexity of O(n2.81). His key insight was applying different equations on the sub-matrix multiplication formulas to minimize operations.
Graph coloring using backtracking

Graph coloring using backtrackingshashidharPapishetty This document summarizes graph coloring using backtracking. It defines graph coloring as minimizing the number of colors used to color a graph. The chromatic number is the fewest colors needed. Graph coloring is NP-complete. The document outlines a backtracking algorithm that tries assigning colors to vertices, checks if the assignment is valid (no adjacent vertices have the same color), and backtracks if not. It provides pseudocode for the algorithm and lists applications like scheduling, Sudoku, and map coloring.
Radix sort presentation



Radix sort presentationRatul Hasan This document provides an overview of the Radix Sort algorithm presented by Ratul Hasan Shaon, Mostofa Rahat, and Jannatul Ferdaous. It begins by explaining that Radix Sort is a non-comparative sorting algorithm that groups keys based on their individual digit values at specific positions. The document then provides an example of Radix Sort using a 4 pass Least Significant Digit approach to sort a list of numbers. It analyzes the time complexity of Radix Sort and notes its applications in parallel computing.
Divide and Conquer



Divide and ConquerDr Shashikant Athawale The document discusses the divide and conquer algorithm design paradigm. It begins by defining divide and conquer as recursively breaking down a problem into smaller sub-problems, solving the sub-problems, and then combining the solutions to solve the original problem. Some examples of problems that can be solved using divide and conquer include binary search, quicksort, merge sort, and the fast Fourier transform algorithm. The document then discusses control abstraction, efficiency analysis, and uses divide and conquer to provide algorithms for large integer multiplication and merge sort. It concludes by defining the convex hull problem and providing an example input and output.
Brute force-algorithm



Brute force-algorithm9854098540 The brute force algorithm finds the maximum subarray of a given array by calculating the sum of all possible contiguous subarrays. It has a time complexity of O(n^2) as it calculates the sum in two nested loops from index 1 to n. While simple to implement, the brute force approach is only efficient for small problem sizes due to its quadratic time complexity. More optimized algorithms are needed for large arrays.
b+ tree



b+ treebitistu The document discusses B+ trees, which are self-balancing search trees used to store data in databases. It defines B+ trees, provides examples, and explains how to perform common operations like searching, insertion, and deletion on B+ trees in a way that maintains the tree's balanced structure. Key aspects are that B+ trees allow fast searching, maintain balance during operations, and improve performance over other tree structures for large databases.
Turing Machine



Turing MachineRajendran The document discusses Turing machines and their properties. It introduces the Church-Turing thesis that any problem that can be solved by an algorithm can be modeled by a Turing machine. It then describes different types of Turing machines, such as multi-track, nondeterministic, two-way, multi-tape, and multidimensional Turing machines. The document provides examples of Turing machines that accept specific languages and evaluate mathematical functions through their transition tables and diagrams.
Natural Language Processing (NLP) - Introduction



Natural Language Processing (NLP) - IntroductionAritra Mukherjee This presentation provides a beginner-friendly introduction towards Natural Language Processing in a way that arouses interest in the field. I have made the effort to include as many easy to understand examples as possible.
Merge sort algorithm power point presentation



Merge sort algorithm power point presentationUniversity of Science and Technology Chitttagong This is a merge sort algorithm presentation. Those are want to learn merge sort by a simple example , he/she can watch to understand easily
Divide and Conquer - Part 1



Divide and Conquer - Part 1Amrinder Arora Divide and Conquer Algorithms - D&C forms a distinct algorithm design technique in computer science, wherein a problem is solved by repeatedly invoking the algorithm on smaller occurrences of the same problem. Binary search, merge sort, Euclid's algorithm can all be formulated as examples of divide and conquer algorithms. Strassen's algorithm and Nearest Neighbor algorithm are two other examples.
15. Transactions in DBMS



15. Transactions in DBMSkoolkampus Transactions are units of program execution that access and update database items. A transaction must preserve database consistency. Concurrent transactions are allowed for increased throughput but can result in inconsistent views. Serializability ensures transactions appear to execute serially in some order. Conflict serializability compares transaction instruction orderings while view serializability compares transaction views. Concurrency control protocols enforce serializability without examining schedules after execution.
linked list in data structure 



linked list in data structure shameen khan This document discusses data structures and linked lists. It provides definitions and examples of different types of linked lists, including:
- Single linked lists, which contain nodes with a data field and a link to the next node.
- Circular linked lists, where the last node links back to the first node, forming a loop.
- Doubly linked lists, where each node contains links to both the previous and next nodes.
- Operations on linked lists such as insertion, deletion, traversal, and searching are also described.
Python (regular expression)



Python (regular expression)Chirag Shetty Regular expressions (RegEx) allow defining search patterns to match strings. RegEx use metacharacters like ^, $, *, ?, etc. to specify patterns. The re module in Python provides functions like search(), match(), sub(), split() to work with RegEx patterns. These functions take a pattern and string, and return matches or modified strings. Common tasks like finding, replacing, extracting substrings can be performed using RegEx in Python.
Project



ProjectGuilherme Torres This document describes Project 4 for CMPSC 201, which involves writing a C++ program to perform linear regression on a set of (x,y) coordinate data to find the line of best fit. The program must read in the data from a file, calculate statistics like the mean, standard deviation, and correlation coefficient, then use those values to compute the slope and y-intercept of the regression line. It also provides specifications on the required functions and expected inputs/outputs of the program.
More Related Content
What's hot (20)
Introduction to algorithms



Introduction to algorithmssubhashchandra197 The document provides an introduction to algorithms through a lecture on fundamentals of algorithm analysis. It defines an algorithm as a finite sequence of unambiguous instructions to solve a problem. Characteristics of algorithms like inputs, outputs, definiteness and finiteness are discussed. The document also describes various algorithm design techniques like brute force, divide and conquer and greedy algorithms. It explains steps to write algorithms using pseudo code and discusses validating, analyzing, testing programs and specifying algorithms through pseudo code and flowcharts.
Divide and conquer - Quick sort



Divide and conquer - Quick sortMadhu Bala divide and conquer , Example , benefits, Quick sort algorithm, complexity of quick sort, merits of quick sort
Hashing



HashingAmar Jukuntla Hashing is a technique used to uniquely identify objects by assigning each object a key, such as a student ID or book ID number. A hash function converts large keys into smaller keys that are used as indices in a hash table, allowing for fast lookup of objects in O(1) time. Collisions, where two different keys hash to the same index, are resolved using techniques like separate chaining or linear probing. Common applications of hashing include databases, caches, and object representation in programming languages.
Stuart russell and peter norvig artificial intelligence - a modern approach...



Stuart russell and peter norvig artificial intelligence - a modern approach...Lê Anh Đạt This document provides publishing information for the book "Artificial Intelligence: A Modern Approach". It lists the editorial staff and production team, including the Vice President and Editorial Director, Editor-in-Chief, Executive Editor, and others. It also provides copyright information, acknowledging that the content is protected and requires permission for reproduction. Finally, it is dedicated to the authors' families and includes a preface giving an overview of the book.
Heaps



HeapsHafiz Atif Amin This document provides information about priority queues and binary heaps. It defines a binary heap as a nearly complete binary tree where the root node has the maximum/minimum value. It describes heap operations like insertion, deletion of max/min, and increasing/decreasing keys. The time complexity of these operations is O(log n). Heapsort, which uses a heap data structure, is also covered and has overall time complexity of O(n log n). Binary heaps are often used to implement priority queues and for algorithms like Dijkstra's and Prim's.
K-Nearest Neighbor(KNN)



K-Nearest Neighbor(KNN)Abdullah al Mamun The K-Nearest Neighbors (KNN) algorithm is a robust and intuitive machine learning method employed to tackle classification and regression problems. By capitalizing on the concept of similarity, KNN predicts the label or value of a new data point by considering its K closest neighbours in the training dataset. In this article, we will learn about a supervised learning algorithm (KNN) or the k – Nearest Neighbours, highlighting it’s user-friendly nature.
What is the K-Nearest Neighbors Algorithm?
K-Nearest Neighbours is one of the most basic yet essential classification algorithms in Machine Learning. It belongs to the supervised learning domain and finds intense application in pattern recognition, data mining, and intrusion detection.
It is widely disposable in real-life scenarios since it is non-parametric, meaning, it does not make any underlying assumptions about the distribution of data (as opposed to other algorithms such as GMM, which assume a Gaussian distribution of the given data). We are given some prior data (also called training data), which classifies coordinates into groups identified by an attribute.
SEARCHING AND SORTING ALGORITHMS



SEARCHING AND SORTING ALGORITHMSGokul Hari The document discusses various searching and sorting algorithms. It describes linear search, binary search, and interpolation search for searching unsorted and sorted lists. It also explains different sorting algorithms like bubble sort, selection sort, insertion sort, quicksort, shellsort, heap sort, and merge sort. Linear search searches sequentially while binary search uses divide and conquer. Sorting algorithms like bubble sort, selection sort, and insertion sort are in-place and have quadratic time complexity in the worst case. Quicksort, mergesort, and heapsort generally have better performance.
Time complexity



Time complexityKatang Isip Basic info about how to use time complexity and how to get the time of each program to solve the problem.
Strassen's matrix multiplication



Strassen's matrix multiplicationMegha V The document discusses Strassen's algorithm for matrix multiplication. It begins by explaining traditional matrix multiplication that has a time complexity of O(n3). It then explains how the divide and conquer strategy can be applied by dividing the matrices into smaller square sub-matrices. Strassen improved upon this by reducing the number of multiplications from 8 to 7 terms, obtaining a time complexity of O(n2.81). His key insight was applying different equations on the sub-matrix multiplication formulas to minimize operations.
Graph coloring using backtracking

Graph coloring using backtrackingshashidharPapishetty This document summarizes graph coloring using backtracking. It defines graph coloring as minimizing the number of colors used to color a graph. The chromatic number is the fewest colors needed. Graph coloring is NP-complete. The document outlines a backtracking algorithm that tries assigning colors to vertices, checks if the assignment is valid (no adjacent vertices have the same color), and backtracks if not. It provides pseudocode for the algorithm and lists applications like scheduling, Sudoku, and map coloring.
Radix sort presentation



Radix sort presentationRatul Hasan This document provides an overview of the Radix Sort algorithm presented by Ratul Hasan Shaon, Mostofa Rahat, and Jannatul Ferdaous. It begins by explaining that Radix Sort is a non-comparative sorting algorithm that groups keys based on their individual digit values at specific positions. The document then provides an example of Radix Sort using a 4 pass Least Significant Digit approach to sort a list of numbers. It analyzes the time complexity of Radix Sort and notes its applications in parallel computing.
Divide and Conquer



Divide and ConquerDr Shashikant Athawale The document discusses the divide and conquer algorithm design paradigm. It begins by defining divide and conquer as recursively breaking down a problem into smaller sub-problems, solving the sub-problems, and then combining the solutions to solve the original problem. Some examples of problems that can be solved using divide and conquer include binary search, quicksort, merge sort, and the fast Fourier transform algorithm. The document then discusses control abstraction, efficiency analysis, and uses divide and conquer to provide algorithms for large integer multiplication and merge sort. It concludes by defining the convex hull problem and providing an example input and output.
Brute force-algorithm



Brute force-algorithm9854098540 The brute force algorithm finds the maximum subarray of a given array by calculating the sum of all possible contiguous subarrays. It has a time complexity of O(n^2) as it calculates the sum in two nested loops from index 1 to n. While simple to implement, the brute force approach is only efficient for small problem sizes due to its quadratic time complexity. More optimized algorithms are needed for large arrays.
b+ tree



b+ treebitistu The document discusses B+ trees, which are self-balancing search trees used to store data in databases. It defines B+ trees, provides examples, and explains how to perform common operations like searching, insertion, and deletion on B+ trees in a way that maintains the tree's balanced structure. Key aspects are that B+ trees allow fast searching, maintain balance during operations, and improve performance over other tree structures for large databases.
Turing Machine



Turing MachineRajendran The document discusses Turing machines and their properties. It introduces the Church-Turing thesis that any problem that can be solved by an algorithm can be modeled by a Turing machine. It then describes different types of Turing machines, such as multi-track, nondeterministic, two-way, multi-tape, and multidimensional Turing machines. The document provides examples of Turing machines that accept specific languages and evaluate mathematical functions through their transition tables and diagrams.
Natural Language Processing (NLP) - Introduction



Natural Language Processing (NLP) - IntroductionAritra Mukherjee This presentation provides a beginner-friendly introduction towards Natural Language Processing in a way that arouses interest in the field. I have made the effort to include as many easy to understand examples as possible.
Merge sort algorithm power point presentation



Merge sort algorithm power point presentationUniversity of Science and Technology Chitttagong This is a merge sort algorithm presentation. Those are want to learn merge sort by a simple example , he/she can watch to understand easily
Divide and Conquer - Part 1



Divide and Conquer - Part 1Amrinder Arora Divide and Conquer Algorithms - D&C forms a distinct algorithm design technique in computer science, wherein a problem is solved by repeatedly invoking the algorithm on smaller occurrences of the same problem. Binary search, merge sort, Euclid's algorithm can all be formulated as examples of divide and conquer algorithms. Strassen's algorithm and Nearest Neighbor algorithm are two other examples.
15. Transactions in DBMS



15. Transactions in DBMSkoolkampus Transactions are units of program execution that access and update database items. A transaction must preserve database consistency. Concurrent transactions are allowed for increased throughput but can result in inconsistent views. Serializability ensures transactions appear to execute serially in some order. Conflict serializability compares transaction instruction orderings while view serializability compares transaction views. Concurrency control protocols enforce serializability without examining schedules after execution.
linked list in data structure 



linked list in data structure shameen khan This document discusses data structures and linked lists. It provides definitions and examples of different types of linked lists, including:
- Single linked lists, which contain nodes with a data field and a link to the next node.
- Circular linked lists, where the last node links back to the first node, forming a loop.
- Doubly linked lists, where each node contains links to both the previous and next nodes.
- Operations on linked lists such as insertion, deletion, traversal, and searching are also described.
Similar to Algorithms Lecture 8: Pattern Algorithms (20)
Python (regular expression)



Python (regular expression)Chirag Shetty Regular expressions (RegEx) allow defining search patterns to match strings. RegEx use metacharacters like ^, $, *, ?, etc. to specify patterns. The re module in Python provides functions like search(), match(), sub(), split() to work with RegEx patterns. These functions take a pattern and string, and return matches or modified strings. Common tasks like finding, replacing, extracting substrings can be performed using RegEx in Python.
Project



ProjectGuilherme Torres This document describes Project 4 for CMPSC 201, which involves writing a C++ program to perform linear regression on a set of (x,y) coordinate data to find the line of best fit. The program must read in the data from a file, calculate statistics like the mean, standard deviation, and correlation coefficient, then use those values to compute the slope and y-intercept of the regression line. It also provides specifications on the required functions and expected inputs/outputs of the program.
String



StringDr. Abhineet Anand This document discusses strings and string handling functions in C programming. It introduces strings as arrays of characters, and describes how to read and write strings using input/output functions. Examples are provided for programs that count characters in a string and reverse a string. Common string handling functions are explained, including strcmp(), strcpy(), strcat(), strlen(), and others. The document concludes with assignments for students to write programs implementing these string functions.
Quick start reg ex



Quick start reg exV krishnamoorthy The document provides a quick reference guide and cheat sheet for basic regular expressions (regex). It includes tables that list common regex syntax elements, with examples and explanations. The tables are meant to serve as an accelerated course for regex beginners to have as a reference. They cover basic characters, quantifiers, character classes, anchors and other syntax. The full document encourages printing the tables for easy reference when working with regex.
Python - Regular Expressions



Python - Regular ExpressionsMukesh Tekwani The document discusses regular expressions (regexes) in Python. It defines regexes as sequences of characters used to match patterns in strings. The re module provides full support for regexes. It describes various regex patterns like literals, concatenation, alternation, repetition. It also covers metacharacters like brackets, caret, backslash, dot and special sequences. Finally, it explains the search() and match() methods to perform regex queries on strings, with search() finding matches anywhere and match() only at the start.
Regular expressions



Regular expressionsEran Zimbler Regular expressions provide a concise way to match patterns in text. They work by converting the regex into a state machine that can efficiently search a string to find matches. Important regex syntax includes quantifiers like *, +, ?, character classes like [a-z], and anchors like ^ and $. Regular expression engines turn the regex pattern into a program that can search strings. Thompson's NFA construction algorithm is commonly used to build the state machine from a regex for efficient matching.
Array and string



Array and stringprashant chelani The document discusses arrays and strings in C programming. It defines arrays as groups of data items of the same type that share a common name. One-dimensional arrays are declared with a datatype and size, and can be initialized. Multi-dimensional arrays have multiple subscripts. Strings are arrays of characters that are null-terminated. Strings can be initialized and manipulated using functions like strcpy(), strlen(), strcmp(). Examples are provided to demonstrate array and string declarations, initialization, manipulation and differences between the two data structures.
regular-expression.pdf



regular-expression.pdfDarellMuchoko The document discusses regular expressions (regex) in Python. It explains that regex is a sequence of characters that defines a search pattern. It provides examples of regex patterns using metacharacters like ^, $, [], etc. It also discusses various regex methods in Python like re.findall(), re.split(), re.sub(), re.search() and attributes of match objects returned like group(), start(), end() to extract matched patterns from strings.
Php String And Regular Expressions



Php String And Regular Expressionsmussawir20 The document discusses string manipulation and regular expressions. It provides explanations of regular expression syntax including brackets, quantifiers, predefined character ranges, and flags. It also summarizes PHP functions for regular expressions like ereg(), eregi(), ereg_replace(), split(), and sql_regcase(). Practical examples of using these functions are shown.
9781285852744 ppt ch08



9781285852744 ppt ch08Terry Yoast This chapter discusses arrays and strings in C++. It covers topics such as declaring and initializing one-dimensional and multi-dimensional arrays, accessing array elements, passing arrays to functions, and built-in functions for manipulating C-strings. The chapter also introduces parallel arrays, arrays of strings, and common array processing tasks like searching, sorting, summing elements, and finding maximum/minimum values.
Ch09



Ch09Arriz San Juan The document discusses strings and character arrays in C, including defining and initializing string literals, input and output of strings, common string processing and library functions, validating user input, and formatting output strings. Key topics covered include using gets(), scanf(), and printf() for I/O, comparing and concatenating strings, counting characters and words in a string, and avoiding common errors when working with strings.
string in C



string in CCGC Technical campus,Mohali The document discusses strings in C programming. It explains that strings are arrays of characters terminated by a null character. Strings can be declared as character arrays or using string pointers. It then provides examples of declaring and initializing strings. The document also discusses various string functions in C like strlen(), strcpy(), strcat(), gets(), puts() and how to perform operations on strings like reversing them, finding length, concatenating, copying and manipulating strings.
0-Slot21-22-Strings.pdf



0-Slot21-22-Strings.pdfssusere19c741 The document discusses strings in C including how to declare, initialize, input, output, and manipulate strings using standard library functions as well as how to manage arrays of strings. It provides examples of declaring and initializing strings, using scanf and gets to input strings, common string manipulation functions like strlen and strcpy, and demonstrates how to work with arrays of strings such as storing and sorting a list of names.
Matlab: Procedures And Functions



Matlab: Procedures And Functionsmatlab Content Script files, also called M-files, make MATLAB programming more efficient than entering individual commands. M-files are text files that contain MATLAB commands to perform specific tasks. They can be created and edited in any plain text editor or the built-in MATLAB editor. User defined functions are a special type of M-file that take inputs and produce outputs, with the function name and arguments specified in the first line. Strings in MATLAB are matrices of character elements that can be manipulated using various functions like converting between data types and extracting substrings.
Procedures And Functions in Matlab



Procedures And Functions in MatlabDataminingTools Inc Script files, also called M-files, make MATLAB programming more efficient than entering individual commands. M-files are text files that contain MATLAB commands to perform specific tasks. They can be created and edited in any plain text editor or the built-in MATLAB editor. User defined functions are a special type of M-file that take inputs and produce outputs, with the function name and arguments specified in the first line. Strings in MATLAB are matrices of character elements that can be manipulated using various functions like converting between data types and extracting substrings.
Introduction To Regex in Lasso 8.5



Introduction To Regex in Lasso 8.5bilcorry Regular expressions (regex) allow users to search for patterns in text. The document provides an introduction to regex, including its basic components: a regex engine, text to search, and a regular expression pattern. It then covers various regex patterns such as literals, character classes, quantifiers, and grouping. Examples are provided to illustrate how different regex patterns can be used to extract or match text.
C-Pubb-TestingExperience_Issue_08_2008



C-Pubb-TestingExperience_Issue_08_2008Berta Danilo The document describes a method for reducing generic software routines that accept alphanumeric inputs and outputs into mathematical functions. It presents a simple example of a routine that reverses a string input. To model this as a function, it introduces a method to assign unique numbers to strings using a dictionary of allowed characters and representing strings as numeric expressions in a given base. It then proves this method mathematically. The goal is to enable testing software routines using standard mathematical testing techniques by mapping routines to well-defined functions.
Adv. python regular expression by Rj



Adv. python regular expression by RjShree M.L.Kakadiya MCA mahila college, Amreli The document discusses regular expressions and text processing in Python. It covers various components of regular expressions like literals, escape sequences, character classes, and metacharacters. It also discusses different regular expression methods in Python like match, search, split, sub, findall, finditer, compile and groupdict. The document provides examples of using these regular expression methods to search, find, replace and extract patterns from text.
Exploratory data analysis project 



Exploratory data analysis project BabatundeSogunro This document summarizes an exploratory data analysis project on a credit card application dataset. The analysis involved examining relationships between variables, identifying variables that best distinguish between positive and negative application outcomes, and calculating statistical metrics. Key variables like A2, A3, A8, and A14 showed differences in distributions between positive and negative classes. Correlation and R-squared analyses revealed that variables A2, A3, A8, and A11 explained the most variance in the classification variable. The analysis uncovered useful insights that will help build an effective predictive model.
Ad
More from Mohamed Loey (20)
Lecture 6: Deep Learning Applications



Lecture 6: Deep Learning ApplicationsMohamed Loey We will discuss the following: Deep Learning Applications, Image Processing, Video Processing, Medical, Computer Network, Big Data, Bioinformatics.
Lecture 5: Convolutional Neural Network Models



Lecture 5: Convolutional Neural Network ModelsMohamed Loey We will discuss the following: Convolutional Neural Network, AlexNet, ZFNet, VGGNet, GoogleNet, ResNet, DenseNet.
Lecture 4: Deep Learning Frameworks



Lecture 4: Deep Learning FrameworksMohamed Loey The document provides information on several popular deep learning frameworks: TensorFlow, Caffe, Theano, Torch, CNTK, and Keras. It describes each framework's creator, license, programming languages supported, and brief purpose or use. TensorFlow is noted as the most popular framework, created by Google for machine learning research. Caffe is described as the fastest, Theano as most efficient, Torch is used by Facebook AI, CNTK for high scalability, and Keras for easy experimentation across frameworks. The document also provides examples of building and running computational graphs in TensorFlow.
Lecture 4: How it Works: Convolutional Neural Networks



Lecture 4: How it Works: Convolutional Neural NetworksMohamed Loey We will discuss the following: Filtering, Convolution, Convolution layer, Normalization, Rectified Linear Units, Pooling, Pooling layer, ReLU layer, Deep stacking, Fully connected layer.
Lecture 3: Convolutional Neural Networks



Lecture 3: Convolutional Neural NetworksMohamed Loey We will discuss the following: Deep vs Machine Learning, Superstar Researchers, Superstar Companies, Deep Learning, Deep Learning Requirements, Deep Learning Architectures, Convolution Neural Network, Case studies, LeNet,AlexNet, ZFNet, GoogLeNet, VGGNet, ResNet, ILSVRC, MNIST, CIFAR-10, CNN Optimization , NVIDIA TITAN X.
Lecture 2: Artificial Neural Network



Lecture 2: Artificial Neural NetworkMohamed Loey We will discuss the following: Artificial Neural Network, Perceptron Learning Example, Artificial Neural Network Training Process, Forward propagation, Backpropagation, Classification of Handwritten Digits, Neural Network Zoo.
Lecture 1: Deep Learning for Computer Vision



Lecture 1: Deep Learning for Computer VisionMohamed Loey This document discusses how deep learning has helped advance computer vision capabilities. It notes that deep learning can help bridge the gap between pixels and meaning by allowing computers to recognize complex patterns in images. It provides an overview of related fields like image processing, machine learning, artificial intelligence, and computer graphics. It also lists some specific applications of deep learning like object detection, image classification, and generating descriptive text. Students are then assigned a task to research how deep learning has improved one particular topic and submit a two-page summary.
Design of an Intelligent System for Improving Classification of Cancer Diseases



Design of an Intelligent System for Improving Classification of Cancer DiseasesMohamed Loey The methodologies that depend on gene expression profile have been able to detect cancer since its inception. The previous works have spent great efforts to reach the best results. Some researchers have achieved excellent results in the classification process of cancer based on the gene expression profile using different gene selection approaches and different classifiers
Early detection of cancer increases the probability of recovery. This thesis presents an intelligent decision support system (IDSS) for early diagnosis of cancer-based on the microarray of gene expression profiles. The problem of this dataset is the little number of examples (not exceed hundreds) comparing to a large number of genes (in thousands). So, it became necessary to find out a method for reducing the features (genes) that are not relevant to the investigated disease to avoid overfitting. The proposed methodology used information gain (IG) for selecting the most important features from the input patterns. Then, the selected features (genes) are reduced by applying the Gray Wolf Optimization algorithm (GWO). Finally, the methodology exercises support vector machine (SVM) for cancer type classification. The proposed methodology was applied to three data sets (breast, colon, and CNS) and was evaluated by the classification accuracy performance measurement, which is most important in the diagnosis of diseases. The best results were gotten when integrating IG with GWO and SVM rating accuracy improved to 96.67% and the number of features was reduced to 32 feature of the CNS dataset.
This thesis investigates several classification algorithms and their suitability to the biological domain. For applications that suffer from high dimensionality, different feature selection methods are considered for illustration and analysis. Moreover, an effective system is proposed. In addition, Experiments were conducted on three benchmark gene expression datasets. The proposed system is assessed and compared with related work performance.
Computer Security - CCNA Security - Lecture 2



Computer Security - CCNA Security - Lecture 2Mohamed Loey We will discuss the following: Classical Security Methods, AAA, Authentication, Authorization, Accounting, AAA Characteristic, Local Based AAA, Server Based AAA, TACACS+ and RADIUS.
Computer Security - CCNA Security - Lecture 1



Computer Security - CCNA Security - Lecture 1Mohamed Loey We will discuss the following: CCNAS Overview, Threats Landscape, Hackers Tools, Tools. Kali Linux Parrot Linux Cisco Packet Tracer Wireshark Denial of Service
Distributed DoS
Man In The Middle
Phishing
Vishing
Smishing
Pharming
Sniffer
Password Attack
Algorithms Lecture 6: Searching Algorithms



Algorithms Lecture 6: Searching AlgorithmsMohamed Loey We will discuss the following: Search Algorithms, Linear Search, Binary Search, Jump Search, and Interpolation Search
Convolutional Neural Network Models - Deep Learning



Convolutional Neural Network Models - Deep LearningMohamed Loey Convolutional Neural Network Models - Deep Learning
Convolutional Neural Network
ILSVRC
AlexNet (2012)
ZFNet (2013)
VGGNet (2014)
GoogleNet 2014)
ResNet (2015)
Conclusion
Convolutional Neural Network (CNN) is a multi-layer neural network
Deep Learning - Overview of my work II



Deep Learning - Overview of my work IIMohamed Loey Deep Learning Machine Learning MNIST CIFAR 10 Residual Network AlexNet VGGNet GoogleNet Nvidia Deep learning (DL) is a hierarchical structure network which through simulates the human brain’s structure to extract the internal and external input data’s features
Computer Security Lecture 7: RSA



Computer Security Lecture 7: RSAMohamed Loey We will discuss the following: RSA Key generation , RSA Encryption , RSA Decryption , A Real World Example, RSA Security.
https://www.youtube.com/watch?v=x7QWJ13dgGs&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf&index=7
Computer Security Lecture 5: Simplified Advanced Encryption Standard



Computer Security Lecture 5: Simplified Advanced Encryption StandardMohamed Loey Simplified Advanced Encryption Standard, S-AES Encryption and Decryption, S-AES Key Generation, S-AES Encryption, S-AES Decryption
https://www.youtube.com/watch?v=pa7s442lRL0&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf&index=6
Computer Security Lecture 4.1: DES Supplementary Material



Computer Security Lecture 4.1: DES Supplementary MaterialMohamed Loey We will discuss the following: Data Encryption Standard, DES Algorithm, DES Key Creation
https://www.youtube.com/watch?v=1-lF4dePpts&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf
PMP Lecture 4: Project Integration Management



PMP Lecture 4: Project Integration ManagementMohamed Loey https://mloey.github.io/
We will discuss the following: Develop Project Charter, Develop Project Management Plan, Direct and Manage Project Work, Monitor and Control Project Work, Perform Integrated Change Control, Close Project or Phase.
Computer Security Lecture 4: Block Ciphers and the Data Encryption Standard



Computer Security Lecture 4: Block Ciphers and the Data Encryption StandardMohamed Loey We will discuss the following: Stream Ciphers and Block Ciphers, Data Encryption Standard, DES Algorithm, DES Key Creation, DES Encryption, The Strength Of DES.
https://www.youtube.com/watch?v=1-lF4dePpts&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf
Computer Security Lecture 3: Classical Encryption Techniques 2



Computer Security Lecture 3: Classical Encryption Techniques 2Mohamed Loey https://mloey.github.io/courses/security2017.html
https://www.youtube.com/watch?v=eGGnjwpaOIo&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf&index=3&t=584s
We will discuss the following: Polyalphabetic Ciphers, Vigenère Cipher, Autokey Cipher, Vernam Cipher, Transposition Techniques, Rail Fence Cipher, Row Transposition Cipher
Computer Security Lecture 2: Classical Encryption Techniques 1



Computer Security Lecture 2: Classical Encryption Techniques 1Mohamed Loey https://mloey.github.io/courses/security2017.html
https://www.youtube.com/watch?v=td_8AM80DUA&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf&index=2&t=37s
We will discuss the following: Symmetric Encryption, Substitution Techniques, Caesar Cipher, Monoalphabetic Cipher, Playfair Cipher, Hill Cipher
Ad
Recently uploaded (20)
How to Create Quotation Templates Sequence in Odoo 18 Sales



How to Create Quotation Templates Sequence in Odoo 18 SalesCeline George In this slide, we’ll discuss on how to create quotation templates sequence in Odoo 18 Sales. Odoo 18 Sales offers a variety of quotation templates that can be used to create different types of sales documents.
THERAPEUTIC COMMUNICATION included definition, characteristics, nurse patient...



THERAPEUTIC COMMUNICATION included definition, characteristics, nurse patient...parmarjuli1412 The document provides an overview of therapeutic communication, emphasizing its importance in nursing to address patient needs and establish effective relationships. THERAPEUTIC COMMUNICATION included some topics like introduction of COMMUNICATION, definition, types, process of communication, definition therapeutic communication, goal, techniques of therapeutic communication, non-therapeutic communication, few ways to improved therapeutic communication, characteristics of therapeutic communication, barrier of THERAPEUTIC RELATIONSHIP, introduction of interpersonal relationship, types of IPR, elements/ dynamics of IPR, introduction of therapeutic nurse patient relationship, definition, purpose, elements/characteristics , and phases of therapeutic communication, definition of Johari window, uses, what actually model represent and its areas, THERAPEUTIC IMPASSES and its management in 5th semester Bsc. nursing and 2nd GNM students
Pests of Rice: Damage, Identification, Life history, and Management.pptx



Pests of Rice: Damage, Identification, Life history, and Management.pptxArshad Shaikh Rice pests can significantly impact crop yield and quality. Major pests include the brown plant hopper (Nilaparvata lugens), which transmits viruses like rice ragged stunt and grassy stunt; the yellow stem borer (Scirpophaga incertulas), whose larvae bore into stems causing deadhearts and whiteheads; and leaf folders (Cnaphalocrocis medinalis), which feed on leaves reducing photosynthetic area. Other pests include rice weevils (Sitophilus oryzae) and gall midges (Orseolia oryzae). Effective management strategies are crucial to minimize losses.
Exploring Ocean Floor Features for Middle School



Exploring Ocean Floor Features for Middle SchoolMarie This 16 slide science reader is all about ocean floor features. It was made to use with middle school students.
You can download the PDF at thehomeschooldaily.com
Thanks! Marie
Trends Spotting Strategic foresight for tomorrow’s education systems - Debora...



Trends Spotting Strategic foresight for tomorrow’s education systems - Debora...EduSkills OECD Deborah Nusche, Senior Analyst, OECD presents at the OECD webinar 'Trends Spotting: Strategic foresight for tomorrow’s education systems' on 5 June 2025. You can check out the webinar on the website https://oecdedutoday.com/webinars/ Other speakers included: Deborah Nusche, Senior Analyst, OECD
Sophie Howe, Future Governance Adviser at the School of International Futures, first Future Generations Commissioner for Wales (2016-2023)
Davina Marie, Interdisciplinary Lead, Queens College London
Thomas Jørgensen, Director for Policy Coordination and Foresight at European University Association
Respiratory System , Urinary System



Respiratory System , Urinary SystemRushiMandali Human Anatomy and Physiology II Unit 3 B pharm Sem 2
Respiratory system
Anatomy of respiratory system with special reference to anatomy
of lungs, mechanism of respiration, regulation of respiration
Lung Volumes and capacities transport of respiratory gases,
artificial respiration, and resuscitation methods
Urinary system
Anatomy of urinary tract with special reference to anatomy of
kidney and nephrons, functions of kidney and urinary tract,
physiology of urine formation, micturition reflex and role of
kidneys in acid base balance, role of RAS in kidney and
disorders of kidney
Strengthened Senior High School - Landas Tool Kit.pptx



Strengthened Senior High School - Landas Tool Kit.pptxSteffMusniQuiballo Landas Tool Kit is a very helpful guide in guiding the Senior High School students on their SHS academic journey. It will pave the way on what curriculum exits will they choose and fit in.
How to Configure Vendor Management in Lunch App of Odoo 18



How to Configure Vendor Management in Lunch App of Odoo 18Celine George The Vendor management in the Lunch app of Odoo 18 is the central hub for managing all aspects of the restaurants or caterers that provide food for your employees.
How to Manage & Create a New Department in Odoo 18 Employee



How to Manage & Create a New Department in Odoo 18 EmployeeCeline George In Odoo 18's Employee module, organizing your workforce into departments enhances management and reporting efficiency. Departments are a crucial organizational unit within the Employee module.
How to Manage Maintenance Request in Odoo 18



How to Manage Maintenance Request in Odoo 18Celine George Efficient maintenance management is crucial for keeping equipment and work centers running smoothly in any business. Odoo 18 provides a Maintenance module that helps track, schedule, and manage maintenance requests efficiently.
EUPHORIA GENERAL QUIZ FINALS | QUIZ CLUB OF PSGCAS | 21 MARCH 2025



EUPHORIA GENERAL QUIZ FINALS | QUIZ CLUB OF PSGCAS | 21 MARCH 2025Quiz Club of PSG College of Arts & Science RE-LIVE THE EUPHORIA!!!!
The Quiz club of PSGCAS brings to you a fun-filled breezy general quiz set from numismatics to sports to pop culture.
Re-live the Euphoria!!!
QM: Eiraiezhil R K,
BA Economics (2022-25),
The Quiz club of PSGCAS
Analysis of Quantitative Data Parametric and non-parametric tests.pptx



Analysis of Quantitative Data Parametric and non-parametric tests.pptxShrutidhara2 This presentation covers the following points--
Parametric Tests
• Testing the Significance of the Difference between Means
• Analysis of Variance (ANOVA) - One way and Two way
• Analysis of Co-variance (One-way)
Non-Parametric Tests:
• Chi-Square test
• Sign test
• Median test
• Sum of Rank test
• Mann-Whitney U-test
Moreover, it includes a comparison of parametric and non-parametric tests, a comparison of one-way ANOVA, two-way ANOVA, and one-way ANCOVA.
Black and White Illustrative Group Project Presentation.pdf (1).pdf



Black and White Illustrative Group Project Presentation.pdf (1).pdfAnnasofiaUrsini mmmmmmmmmmmmmmmmmmmmmmmmmmmmmmmmmm
Final Sketch Designs for poster production.pptx



Final Sketch Designs for poster production.pptxbobby205207 Final Sketch Designs for poster production.
Rose Cultivation Practices by Kushal Lamichhane.pdf



Rose Cultivation Practices by Kushal Lamichhane.pdfkushallamichhame This includes the overall cultivation practices of Rose prepared by:
Kushal Lamichhane (AKL)
Instructor
Shree Gandhi Adarsha Secondary School
Kageshowri Manohara-09, Kathmandu, Nepal
EUPHORIA GENERAL QUIZ FINALS | QUIZ CLUB OF PSGCAS | 21 MARCH 2025



EUPHORIA GENERAL QUIZ FINALS | QUIZ CLUB OF PSGCAS | 21 MARCH 2025Quiz Club of PSG College of Arts & Science
Algorithms Lecture 8: Pattern Algorithms
- 1. Analysis and Design of Algorithms Patterns Algorithms
- 2. Analysis and Design of Algorithms Pattern searching Naive Pattern Searching Regular Expression
- 3. Analysis and Design of Algorithms Pattern searching is an important problem in computer science. When we do search for a string in notepad/word file or browser or database, pattern searching algorithms are used to show the search results.
- 4. Analysis and Design of Algorithms Naive Pattern Searching
- 5. Analysis and Design of Algorithms Slide the pattern over text one by one and check for a match. If a match is found, then slides by 1 again to check for subsequent matches.
- 6. Analysis and Design of Algorithms Example 1: Input: txt[] = "THIS IS A TEST TEXT" pat[] = "TEST" Output: Pattern found at index 10
- 7. Analysis and Design of Algorithms Example 2: Input: txt[] = "AABAACAADAABAABA" pat[] = "AABA" Output: Pattern found at index 0 Pattern found at index 9 Pattern found at index 12
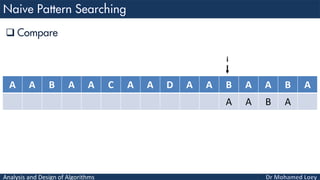
- 8. Analysis and Design of Algorithms Compare A A B A A C A A D A A B A A B A A A B A j i
- 9. Analysis and Design of Algorithms Compare A A B A A C A A D A A B A A B A A A B A j i i+j
- 10. Analysis and Design of Algorithms Compare A A B A A C A A D A A B A A B A A A B A j i i+j
- 11. Analysis and Design of Algorithms Compare A A B A A C A A D A A B A A B A A A B A j i i+j
- 12. Analysis and Design of Algorithms Pattern found at index 0 A A B A A C A A D A A B A A B A A A B A i
- 13. Analysis and Design of Algorithms Compare A A B A A C A A D A A B A A B A A A B A i
- 14. Analysis and Design of Algorithms Compare A A B A A C A A D A A B A A B A A A B A i
- 15. Analysis and Design of Algorithms Compare A A B A A C A A D A A B A A B A A A B A i
- 16. Analysis and Design of Algorithms Compare A A B A A C A A D A A B A A B A A A B A i
- 17. Analysis and Design of Algorithms Compare A A B A A C A A D A A B A A B A A A B A i
- 18. Analysis and Design of Algorithms Compare A A B A A C A A D A A B A A B A A A B A i
- 19. Analysis and Design of Algorithms Compare A A B A A C A A D A A B A A B A A A B A i
- 20. Analysis and Design of Algorithms Compare A A B A A C A A D A A B A A B A A A B A i
- 21. Analysis and Design of Algorithms Pattern found at index 9 A A B A A C A A D A A B A A B A A A B A i
- 22. Analysis and Design of Algorithms Compare A A B A A C A A D A A B A A B A A A B A i
- 23. Analysis and Design of Algorithms Compare A A B A A C A A D A A B A A B A A A B A i
- 24. Analysis and Design of Algorithms Pattern found at index 12 A A B A A C A A D A A B A A B A A A B A i
- 25. Analysis and Design of Algorithms Compare A A B A A C A A D A A B A A B A A A B i
- 26. Analysis and Design of Algorithms Compare A A B A A C A A D A A B A A B A A A i
- 27. Analysis and Design of Algorithms Input: txt[] = "AABAACAADAABAABA" pat[] = "AABA" Output: Pattern found at index 0 Pattern found at index 9 Pattern found at index 12
- 28. Analysis and Design of Algorithms Python Code:
- 29. Analysis and Design of Algorithms
- 30. Analysis and Design of Algorithms What is the best case? The best case occurs when the first character of the pattern is not present in text at all. txt[] = "AABCCAADDEE" pat[] = "FAA"
- 31. Analysis and Design of Algorithms What is the worst case ? 1) When all characters of the text and pattern are same. txt[] = "AAAAAAAAAAAAAAAAAA" pat[] = "AAAAA"
- 32. Analysis and Design of Algorithms 2) Worst case also occurs when only the last character is different. txt[] = "AAAAAAAAAAAAAAAAAB" pat[] = "AAAAB"
- 33. Analysis and Design of Algorithms The worst case is O(m*(n-m+1))
- 34. Analysis and Design of Algorithms Regular Expression
- 35. Analysis and Design of Algorithms Regular expressions are a powerful language for matching text patterns.
- 36. Analysis and Design of Algorithms re.match() checks for a match only at the beginning of the string. re.search() checks for a match anywhere in the string.
- 37. Analysis and Design of Algorithms Import Regular Expression (Python)
- 38. Analysis and Design of Algorithms In Python a regular expression search is typically written as: match = re.search(pat, str)
- 39. Analysis and Design of Algorithms Simple match
- 40. Analysis and Design of Algorithms w (lowercase w): matches a "word" character: a letter or digit or underbar [a-z A-Z 0-9 _].
- 41. Analysis and Design of Algorithms W (upper case W): matches any non-word character.
- 42. Analysis and Design of Algorithms d (lowercase d): decimal digit [0-9]
- 43. Analysis and Design of Algorithms s (lowercase s): matches a single whitespace character -- space, newline, return, tab, form [ nrtf].
- 44. Analysis and Design of Algorithms . (dot) : matches any single character except newline 'n'
- 45. Analysis and Design of Algorithms ^ = start : match the start Match is empty
- 46. Analysis and Design of Algorithms $ = end : match the end of the string Match is empty
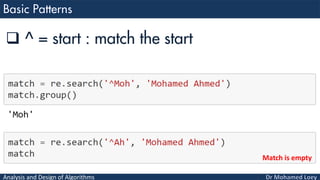
- 47. Analysis and Design of Algorithms [ ] : a range of characters can be indicated by giving two characters and separating them by a “-”.
- 48. Analysis and Design of Algorithms [ ]
- 49. Analysis and Design of Algorithms [^ ] : will match any character except this.
- 50. Analysis and Design of Algorithms {n} : match exactly with any number of n.
- 51. Analysis and Design of Algorithms {n,m} : match exactly with any number of n to m.
- 52. Analysis and Design of Algorithms Syntax Description Equivalent d Matches any decimal digit [0-9] D Matches any non-digit character [^0-9] s Matches any whitespace character [ tnrfv] S Matches any non-whitespace character [^ tnrfv] w Matches any alphanumeric character [a-zA-Z0-9_] W Matches any non-alphanumeric character [^a-zA-Z0-9_]
- 53. Analysis and Design of Algorithms + : 1 or more occurrences of the pattern
- 54. Analysis and Design of Algorithms * : 0 or more occurrences of the pattern
- 55. Analysis and Design of Algorithms ? : match 0 or 1 occurrences of the pattern
- 56. Analysis and Design of Algorithms Emails:
- 57. Analysis and Design of Algorithms Emails: Square brackets can be used to indicate a set of chars, so [abc] matches 'a' or 'b' or 'c'.
- 58. Analysis and Design of Algorithms Emails: findall() finds all the matches and returns them as a list of strings.
- 59. Analysis and Design of Algorithms ( ): match group of pattern
- 60. Analysis and Design of Algorithms Operators Description . Matches with any single character except newline ‘n’ ? Match 0 or 1 occurrence of the pattern to its left + Match 1 or more occurrences of the pattern to its left * Match 0 or more occurrences of the pattern to its left w Matches with a alphanumeric character W Matches non alphanumeric character d Matches with digits [0-9] D Matches with non-digits
- 61. Analysis and Design of Algorithms Operators Description s Matches with a single white space character (space, newline, tab) S Matches any non-white space character [..] Matches any single character in a square bracket [^..] Matches any single character not in square bracket It is used for special meaning characters ^ and $ ^ and $ match the start or end of the string respectively {n,m} Matches at least n and at most m occurrences of expression a| b Matches either a or b
- 62. Analysis and Design of Algorithms Operators Description ( ) Groups regular expressions and returns matched text t, n, r Matches tab, newline, return
- 63. Analysis and Design of Algorithms Validate a phone number (phone number must be of 10 digits and starts with 8 or 9)
- 64. Analysis and Design of Algorithms Solution
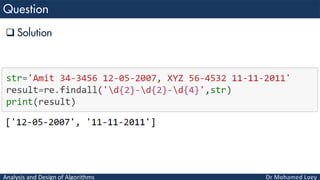
- 65. Analysis and Design of Algorithms Return date from given string str= Amit 34-3456 12-05-2007, XYZ 56-4532 11- 11-2011
- 66. Analysis and Design of Algorithms Solution
- 67. Analysis and Design of Algorithms facebook.com/mloey [email protected] twitter.com/mloey linkedin.com/in/mloey [email protected] mloey.github.io
- 68. Analysis and Design of Algorithms www.YourCompany.com © 2020 Companyname PowerPoint Business Theme. All Rights Reserved. THANKS FOR YOUR TIME






