Applying Security Algorithms Using openSSL crypto library
20 likes5,890 views
The document discusses applying security algorithms using the OpenSSL crypto library. It provides an overview of common security algorithms like hash functions, authentication codes, symmetric and public key cryptography. It then describes how OpenSSL implements these algorithms via sub-libraries and provides command line tools to generate keys, encrypt/decrypt data, and sign/verify signatures. The last section discusses programming with the crypto library, showing examples of generating keys, encrypting/decrypting data with Blowfish, and establishing SSL/TLS connections.
1 of 46















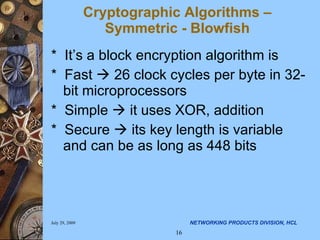




















![Programming using Crypto library – Blowfish – Create a key Step 2: Initialize key Read 16 bytes from /dev/random That gives 128-bit random symmetric key. Read 8 bytes to populate initialization vector. int bf_key[16]; int bf_vector[8]; if ((read (fd, bf_key, 16)) == -1) perror (“Could not read the key"); if ((read (fd, init_vector, 8)) == -1) perror ("read iv error");](https://image.slidesharecdn.com/applying-security-algorithms-using-openssl-crypto-library-4634/85/Applying-Security-Algorithms-Using-openSSL-crypto-library-38-320.jpg)






![Questions B.C. Sekar HCL Technologies Limited, 49-50, Nelson Manikkam Road, Chennai - 600026. Phone - +91-44-23750171 [email_address] http://www.hcltech.com](https://image.slidesharecdn.com/applying-security-algorithms-using-openssl-crypto-library-4634/85/Applying-Security-Algorithms-Using-openSSL-crypto-library-46-320.jpg)
Ad
Recommended
OpenSSL Basic Function Call Flow
OpenSSL Basic Function Call FlowWilliam Lee This document provides an overview of the basic function call flow for OpenSSL to establish a secure TCP connection. It discusses initializing the OpenSSL library, creating an SSL_CTX object, generating randomness, creating an SSL object for a connection, performing the TLS/SSL handshake, and reading and writing data over the encrypted connection. It also provides examples of OpenSSL code for a client application.
OpenSSL programming (still somewhat initial version)
OpenSSL programming (still somewhat initial version)Shteryana Shopova The document discusses programming with OpenSSL and libcrypto, emphasizing secured communications, cryptographic concepts, and implementation strategies. It covers SSL/TLS protocols, the architecture of OpenSSL, and best practices for coding, error handling, and security measures. Additionally, it highlights historical security issues like Apple's 'gotofail' and OpenSSL's 'Heartbleed' bug, along with various programming examples and testing recommendations.
Crypto With OpenSSL
Crypto With OpenSSLZhi Guan This document provides an overview and introduction to OpenSSL including its components, architecture, APIs and usage. It describes OpenSSL as an open source cryptography toolkit that implements SSL/TLS protocols as well as cryptographic functions for encryption, decryption, signatures, certificates etc. It outlines OpenSSL's command line interface, supported algorithms, license, source code organization, EVP crypto API and usage examples for symmetric encryption and hashing.
Openssl
Opensslpsychesnet Hsieh The document provides an overview of SSL and OpenSSL. It discusses generating keys and certificates, setting up SSL contexts, creating secure connections, reading/writing data, and handling errors. It also provides code snippets for an echo client and server. The echo server loads a certificate, sets up a listening BIO, accepts connections, and performs handshakes. The handshake process involves a client sending a "hello" message and the server responding with its own parameters to establish encryption.
Pgp smime
Pgp smimeTania Agni PGP and S/MIME are two standards for securing email. PGP uses asymmetric encryption and digital signatures to provide authentication, confidentiality, and compression of messages. It utilizes public/private key pairs and trust is established through signatures on public keys. S/MIME is an Internet standard that provides similar security services to MIME messages as PGP, using PKI/certificates and industry standard algorithms. Both standards encrypt messages and attach digital signatures to authenticate senders and guarantee message integrity.
Strong cryptography in PHP
Strong cryptography in PHPEnrico Zimuel The document discusses strong cryptography in PHP, highlighting its importance in secure data handling and various algorithms such as AES and RSA. It emphasizes that strong cryptography involves more than encryption, including hashing and secure password storage practices. Additionally, it outlines best practices, key generation techniques, and the use of libraries like OpenSSL and mcrypt in PHP applications.
Pkcs 5
Pkcs 5snakesv This document describes a password-based encryption standard (PKCS #5) that defines two key derivation algorithms combining message digest algorithms (MD2 and MD5) with DES encryption. The standard defines processes for encrypting and decrypting messages using a password, salt value, and iteration count to derive the encryption key. The encryption process formats the message and padding into a block, derives the key from the password/salt/count, and encrypts the block with DES-CBC. The decryption process reverses these steps to recover the original message.
securing_syslog_onFreeBSD
securing_syslog_onFreeBSDwebuploader The document discusses securing syslog logging on FreeBSD systems. It introduces syslog, its insecurities, and describes implementing digital signatures using an extension called syslog-sign. Syslog-sign calculates hashes of messages and stores signatures to assure integrity and detect any modifications. The implementation modifies the syslog daemon to generate signatures without other configuration. Verification can then validate log file contents offline.
Encryption
EncryptionMahmoud Abdeen The document discusses encryption methods, focusing on symmetric key cryptography, public key cryptography, and their applications. It explains various encryption standards such as DES and AES, and details the RSA algorithm for public key encryption, including key generation and the basis of its security. The text also highlights practical applications of these cryptographic methods in secure communication and digital signatures.
[BlackHat USA 2016] Nonce-Disrespecting Adversaries: Practical Forgery Attack...
[BlackHat USA 2016] Nonce-Disrespecting Adversaries: Practical Forgery Attack...Aaron Zauner GCM mode in TLS is vulnerable if nonces are not unique per message. The document describes scanning the internet and finding implementations that reuse nonces, allowing an attacker to recover the authentication key and manipulate messages. It proposes a man-in-the-middle attack where an attacker collects nonces from a server, waits for a repeat, recovers the key, and modifies encrypted content served to a victim. While TLS 1.2 specifies nonces, implementations sometimes fail to generate unique nonces correctly. Better guidance and testing tools are needed to prevent such vulnerabilities.
6.hash mac
6.hash macVirendrakumar Dhotre Cryptographic hash functions, message authentication codes (MACs), and digital signatures are discussed.
HMAC and CBC-MAC are introduced as methods to construct MACs from hash functions. HMAC incorporates a secret key into a hash function to provide message authentication. CBC-MAC uses a block cipher like DES in CBC mode.
Digital signatures are similar to MACs but use public-key cryptography like RSA. A digital signature provides both message authentication and non-repudiation. RSA can be used to generate signatures by signing a hash of the message with the private key.
Hash function
Hash functionHarry Potter The document discusses hash functions and message authentication codes (MACs). It begins by defining hash functions and MACs, noting that hash functions generate a fingerprint for a message without a key while MACs use a keyed hash function. It then covers security requirements for hash functions like one-wayness and collision resistance. Popular hash functions are described like MD5, SHA-1, and the SHA-2 family. Constructions for hash functions based on block ciphers and iterated hash functions are also outlined. The document concludes by comparing hash functions and MACs and describing common MAC constructions.
Cs8792 cns - unit iv
Cs8792 cns - unit ivArthyR3 This document provides an overview of message authentication and integrity. It discusses the need for authentication in network security and outlines different authentication functions including message encryption, message authentication codes (MACs), and hash functions. It describes how MACs are generated using a secret key and message and provides the requirements for MACs. The document also discusses the MD5 and SHA hash algorithms, explaining their processes and analyzing their security strengths and weaknesses.
Message Authentication using Message Digests and the MD5 Algorithm
Message Authentication using Message Digests and the MD5 AlgorithmAjay Karri Message authentication is important to prevent undetected manipulation of messages, which can have disastrous effects. Examples where message authentication is crucial include internet commerce and network management. Cryptographic hash functions are often used to authenticate messages by providing a digital fingerprint of the message contents.
MD5Algorithm
MD5AlgorithmMirza Tarannum MD5 & Hash Encryption provides an overview of MD5 and hash encryption algorithms. It discusses the purpose and examples of MD5, how the MD5 algorithm works, potential security risks like collisions, and practical applications through code. It also covers how difficult MD5 is to crack through brute force, though flaws in the algorithm allow for exploits, and discusses how MD5 is used for digital signatures, certificates, and one-way encryption storage.
Encryption
EncryptionIGZ Software house Encryption techniques like AES and Triple DES are used to secure data transmission over networks. AES encrypts data in blocks using symmetric encryption with variable key lengths up to 256 bits, making it more secure than older standards like DES with only a 56-bit key. Triple DES applies the DES algorithm three times with two or three keys, strengthening security compared to single DES. Stream and block ciphers differ in whether they encrypt data bits or blocks at a time.
Block Ciphers Modes of Operation
Block Ciphers Modes of OperationRoman Oliynykov The document discusses various block cipher modes of operation, detailing their properties, advantages, and disadvantages, and highlighting the need for specific modes to enhance encryption security. It covers well-known standard modes like ECB, CBC, CFB, OFB, and CTR, as well as newly developed NIST-adopted modes tailored for different applications including network protection and key management. The conclusion emphasizes the importance of careful mode selection to ensure strong cryptographic security in practical applications.
Hash Function
Hash FunctionSiddharth Srivastava This document discusses message authentication techniques including message encryption, message authentication codes (MACs), and hash functions. It describes how each technique can be used to authenticate messages and protect against various security threats. It also covers how symmetric and asymmetric encryption can provide authentication when used with MACs or digital signatures. Specific MAC and hash functions are examined like HMAC, SHA-1, and SHA-2. X.509 is introduced as a standard for digital certificates.
Reverse shell
Reverse shellIlan Mindel A shell is a user interface for accessing an operating system's services, either through a command-line interface or graphical user interface. A bind shell opens a listener port on the target machine and waits for an incoming connection from the attacker. A reverse shell is when the target machine connects back to the attacking machine. Netcat and PowerShell can be used to create bind and reverse shells for command execution on remote systems. Examples show how netcat can be used to establish each type of shell connection between an attacker and victim machine.
Hash crypto
Hash cryptoHarry Potter The document discusses cryptographic hash functions, including an overview of their usage, properties, structures, attacks, and the need for a new secure hash standard. It describes how hash functions work by condensing arbitrary messages into fixed-size message digests. The properties of preimage resistance, second preimage resistance, and collision resistance are explained. Common hashing algorithms like MD5, SHA-1, and SHA-2 are outlined along with vulnerabilities like birthday attacks. The document concludes by noting the need to replace standards like MD5 and SHA-1 due to successful cryptanalysis attacks.
Cryptography and Message Authentication NS3
Cryptography and Message Authentication NS3koolkampus This document provides an overview of approaches to message authentication and public-key cryptography. It discusses secure hash functions like SHA-1 and HMAC for message authentication codes. For public-key cryptography, it describes the principles including key distribution and encryption/decryption with public/private key pairs. Specific public-key algorithms covered are RSA, Diffie-Hellman key exchange, and their applications for encryption, digital signatures, and key exchange. Requirements and examples of the RSA algorithm are also summarized.
Ch11
Ch11Joe Christensen This document summarizes message authentication techniques including message encryption, message authentication codes (MACs), and hash functions. It discusses the security requirements of message authentication such as integrity, authentication, and non-repudiation. It then describes how message encryption, MACs, and hash functions provide message authentication and their properties and security considerations.
Computer network (3)
Computer network (3)NYversity This document discusses cryptography and how it can be used to secure communication. It covers symmetric and public key encryption, digital signatures, hashes, and authentication. Symmetric encryption uses a shared secret key for both encryption and decryption, while public key encryption uses different keys for encryption and decryption. Cryptographic hashes provide integrity for messages, and message authentication codes (MACs) also provide integrity and authentication. Digital signatures provide authentication and integrity using public key cryptography. The document discusses encryption modes like CBC and stream ciphers like RC4. It also covers key distribution challenges and how certificate authorities can help authenticate servers.
CNS - Unit v
CNS - Unit vArthyR3 This document discusses electronic mail security and web security. It covers Pretty Good Privacy (PGP) and S/MIME for securing email, describing their encryption, authentication, and key management functions. For web security, it outlines threats like eavesdropping, impersonation, and denial of service attacks. It also explains how Secure Sockets Layer (SSL) and Transport Layer Security (TLS) establish encrypted connections between web browsers and servers to protect data confidentiality and integrity during transmission. Cryptographic algorithms like SHA-1, MD5, DES, and RSA are used to authenticate, encrypt, and digitally sign messages.
Blockchain Cryptography for Developers (Nakov @ BGWebSummit 2018)
Blockchain Cryptography for Developers (Nakov @ BGWebSummit 2018)Svetlin Nakov The document provides an extensive overview of blockchain cryptography, focusing on elliptic curve cryptography (ECC), its associated key algorithms like ECDSA, and the implementation details of secp256k1 used in Bitcoin and Ethereum. It also covers the construction and management of wallets through BIP39 and BIP44 standards, as well as techniques for private key encryption using algorithms such as AES and HMAC. Additionally, it explores hashing functions and key derivation methods like PBKDF2 and Scrypt, illustrating key concepts through Python code examples.
Cns
CnsArthyR3 This document discusses message authentication and hash functions. It begins by defining message authentication and its security requirements. It then describes three approaches to message authentication: message encryption, message authentication codes (MACs), and hash functions. It provides details on how MACs and hash functions work, including properties and requirements. Specific algorithms like MD5 are also covered. The document aims to explain the concepts and tradeoffs between different message authentication techniques.
Tecnologias Free e Open Source na Plataforma Microsoft
Tecnologias Free e Open Source na Plataforma MicrosoftGustavo Malheiros The document outlines the professional background and expertise of an individual involved in software development and consulting, highlighting their experience with Microsoft technologies and the .NET ecosystem. It provides insights into various tools, frameworks, and methodologies used in application lifecycle management, cloud computing, and open-source development. Additionally, it discusses the establishment of the Pantanet community aimed at fostering connections among tech professionals and students while promoting training and job opportunities.
What you Need to Know about FHA Upfront Mortgage Insurance
What you Need to Know about FHA Upfront Mortgage InsuranceMortgage Commentator The document explains the differences between upfront mortgage insurance and annual mortgage insurance associated with FHA loans. Upfront mortgage insurance is a one-time fee paid at closing unless financed, while annual mortgage insurance is paid monthly throughout the loan term. Borrowers can get the upfront premium back only when refinancing into a streamline FHA loan, but it applies to all FHA loans regardless of refinancing.
Types of ssl commands and keytool
Types of ssl commands and keytoolCheapSSLsecurity The document provides an overview of SSL commands and the OpenSSL and Java Keytool utilities for managing SSL/TLS protocols. It lists common OpenSSL commands for generating certificate signing requests (CSRs), self-signed certificates, and checking SSL certificates, as well as similar functionalities for Java Keytool. Additionally, it outlines commands for creating, importing, and managing keystores and certificates within the Java environment.
OpenSSL
OpenSSLSafwane Madjeri OpenSSL est une boîte à outils cryptographiques open source, développée par une communauté mondiale, qui implémente les protocoles SSL et TLS pour sécuriser les communications client/serveur. Elle comprend une bibliothèque robuste de cryptographie, et bien qu'elle présente des avantages comme sa puissance et sa portabilité, elle souffre également de certaines limites telles que des problèmes de compatibilité et des failles de sécurité. Malgré cela, OpenSSL reste un outil largement utilisé pour le chiffrement et le hachage dans diverses applications.
More Related Content
What's hot (18)
Encryption
EncryptionMahmoud Abdeen The document discusses encryption methods, focusing on symmetric key cryptography, public key cryptography, and their applications. It explains various encryption standards such as DES and AES, and details the RSA algorithm for public key encryption, including key generation and the basis of its security. The text also highlights practical applications of these cryptographic methods in secure communication and digital signatures.
[BlackHat USA 2016] Nonce-Disrespecting Adversaries: Practical Forgery Attack...
[BlackHat USA 2016] Nonce-Disrespecting Adversaries: Practical Forgery Attack...Aaron Zauner GCM mode in TLS is vulnerable if nonces are not unique per message. The document describes scanning the internet and finding implementations that reuse nonces, allowing an attacker to recover the authentication key and manipulate messages. It proposes a man-in-the-middle attack where an attacker collects nonces from a server, waits for a repeat, recovers the key, and modifies encrypted content served to a victim. While TLS 1.2 specifies nonces, implementations sometimes fail to generate unique nonces correctly. Better guidance and testing tools are needed to prevent such vulnerabilities.
6.hash mac
6.hash macVirendrakumar Dhotre Cryptographic hash functions, message authentication codes (MACs), and digital signatures are discussed.
HMAC and CBC-MAC are introduced as methods to construct MACs from hash functions. HMAC incorporates a secret key into a hash function to provide message authentication. CBC-MAC uses a block cipher like DES in CBC mode.
Digital signatures are similar to MACs but use public-key cryptography like RSA. A digital signature provides both message authentication and non-repudiation. RSA can be used to generate signatures by signing a hash of the message with the private key.
Hash function
Hash functionHarry Potter The document discusses hash functions and message authentication codes (MACs). It begins by defining hash functions and MACs, noting that hash functions generate a fingerprint for a message without a key while MACs use a keyed hash function. It then covers security requirements for hash functions like one-wayness and collision resistance. Popular hash functions are described like MD5, SHA-1, and the SHA-2 family. Constructions for hash functions based on block ciphers and iterated hash functions are also outlined. The document concludes by comparing hash functions and MACs and describing common MAC constructions.
Cs8792 cns - unit iv
Cs8792 cns - unit ivArthyR3 This document provides an overview of message authentication and integrity. It discusses the need for authentication in network security and outlines different authentication functions including message encryption, message authentication codes (MACs), and hash functions. It describes how MACs are generated using a secret key and message and provides the requirements for MACs. The document also discusses the MD5 and SHA hash algorithms, explaining their processes and analyzing their security strengths and weaknesses.
Message Authentication using Message Digests and the MD5 Algorithm
Message Authentication using Message Digests and the MD5 AlgorithmAjay Karri Message authentication is important to prevent undetected manipulation of messages, which can have disastrous effects. Examples where message authentication is crucial include internet commerce and network management. Cryptographic hash functions are often used to authenticate messages by providing a digital fingerprint of the message contents.
MD5Algorithm
MD5AlgorithmMirza Tarannum MD5 & Hash Encryption provides an overview of MD5 and hash encryption algorithms. It discusses the purpose and examples of MD5, how the MD5 algorithm works, potential security risks like collisions, and practical applications through code. It also covers how difficult MD5 is to crack through brute force, though flaws in the algorithm allow for exploits, and discusses how MD5 is used for digital signatures, certificates, and one-way encryption storage.
Encryption
EncryptionIGZ Software house Encryption techniques like AES and Triple DES are used to secure data transmission over networks. AES encrypts data in blocks using symmetric encryption with variable key lengths up to 256 bits, making it more secure than older standards like DES with only a 56-bit key. Triple DES applies the DES algorithm three times with two or three keys, strengthening security compared to single DES. Stream and block ciphers differ in whether they encrypt data bits or blocks at a time.
Block Ciphers Modes of Operation
Block Ciphers Modes of OperationRoman Oliynykov The document discusses various block cipher modes of operation, detailing their properties, advantages, and disadvantages, and highlighting the need for specific modes to enhance encryption security. It covers well-known standard modes like ECB, CBC, CFB, OFB, and CTR, as well as newly developed NIST-adopted modes tailored for different applications including network protection and key management. The conclusion emphasizes the importance of careful mode selection to ensure strong cryptographic security in practical applications.
Hash Function
Hash FunctionSiddharth Srivastava This document discusses message authentication techniques including message encryption, message authentication codes (MACs), and hash functions. It describes how each technique can be used to authenticate messages and protect against various security threats. It also covers how symmetric and asymmetric encryption can provide authentication when used with MACs or digital signatures. Specific MAC and hash functions are examined like HMAC, SHA-1, and SHA-2. X.509 is introduced as a standard for digital certificates.
Reverse shell
Reverse shellIlan Mindel A shell is a user interface for accessing an operating system's services, either through a command-line interface or graphical user interface. A bind shell opens a listener port on the target machine and waits for an incoming connection from the attacker. A reverse shell is when the target machine connects back to the attacking machine. Netcat and PowerShell can be used to create bind and reverse shells for command execution on remote systems. Examples show how netcat can be used to establish each type of shell connection between an attacker and victim machine.
Hash crypto
Hash cryptoHarry Potter The document discusses cryptographic hash functions, including an overview of their usage, properties, structures, attacks, and the need for a new secure hash standard. It describes how hash functions work by condensing arbitrary messages into fixed-size message digests. The properties of preimage resistance, second preimage resistance, and collision resistance are explained. Common hashing algorithms like MD5, SHA-1, and SHA-2 are outlined along with vulnerabilities like birthday attacks. The document concludes by noting the need to replace standards like MD5 and SHA-1 due to successful cryptanalysis attacks.
Cryptography and Message Authentication NS3
Cryptography and Message Authentication NS3koolkampus This document provides an overview of approaches to message authentication and public-key cryptography. It discusses secure hash functions like SHA-1 and HMAC for message authentication codes. For public-key cryptography, it describes the principles including key distribution and encryption/decryption with public/private key pairs. Specific public-key algorithms covered are RSA, Diffie-Hellman key exchange, and their applications for encryption, digital signatures, and key exchange. Requirements and examples of the RSA algorithm are also summarized.
Ch11
Ch11Joe Christensen This document summarizes message authentication techniques including message encryption, message authentication codes (MACs), and hash functions. It discusses the security requirements of message authentication such as integrity, authentication, and non-repudiation. It then describes how message encryption, MACs, and hash functions provide message authentication and their properties and security considerations.
Computer network (3)
Computer network (3)NYversity This document discusses cryptography and how it can be used to secure communication. It covers symmetric and public key encryption, digital signatures, hashes, and authentication. Symmetric encryption uses a shared secret key for both encryption and decryption, while public key encryption uses different keys for encryption and decryption. Cryptographic hashes provide integrity for messages, and message authentication codes (MACs) also provide integrity and authentication. Digital signatures provide authentication and integrity using public key cryptography. The document discusses encryption modes like CBC and stream ciphers like RC4. It also covers key distribution challenges and how certificate authorities can help authenticate servers.
CNS - Unit v
CNS - Unit vArthyR3 This document discusses electronic mail security and web security. It covers Pretty Good Privacy (PGP) and S/MIME for securing email, describing their encryption, authentication, and key management functions. For web security, it outlines threats like eavesdropping, impersonation, and denial of service attacks. It also explains how Secure Sockets Layer (SSL) and Transport Layer Security (TLS) establish encrypted connections between web browsers and servers to protect data confidentiality and integrity during transmission. Cryptographic algorithms like SHA-1, MD5, DES, and RSA are used to authenticate, encrypt, and digitally sign messages.
Blockchain Cryptography for Developers (Nakov @ BGWebSummit 2018)
Blockchain Cryptography for Developers (Nakov @ BGWebSummit 2018)Svetlin Nakov The document provides an extensive overview of blockchain cryptography, focusing on elliptic curve cryptography (ECC), its associated key algorithms like ECDSA, and the implementation details of secp256k1 used in Bitcoin and Ethereum. It also covers the construction and management of wallets through BIP39 and BIP44 standards, as well as techniques for private key encryption using algorithms such as AES and HMAC. Additionally, it explores hashing functions and key derivation methods like PBKDF2 and Scrypt, illustrating key concepts through Python code examples.
Cns
CnsArthyR3 This document discusses message authentication and hash functions. It begins by defining message authentication and its security requirements. It then describes three approaches to message authentication: message encryption, message authentication codes (MACs), and hash functions. It provides details on how MACs and hash functions work, including properties and requirements. Specific algorithms like MD5 are also covered. The document aims to explain the concepts and tradeoffs between different message authentication techniques.
Viewers also liked (20)
Tecnologias Free e Open Source na Plataforma Microsoft
Tecnologias Free e Open Source na Plataforma MicrosoftGustavo Malheiros The document outlines the professional background and expertise of an individual involved in software development and consulting, highlighting their experience with Microsoft technologies and the .NET ecosystem. It provides insights into various tools, frameworks, and methodologies used in application lifecycle management, cloud computing, and open-source development. Additionally, it discusses the establishment of the Pantanet community aimed at fostering connections among tech professionals and students while promoting training and job opportunities.
What you Need to Know about FHA Upfront Mortgage Insurance
What you Need to Know about FHA Upfront Mortgage InsuranceMortgage Commentator The document explains the differences between upfront mortgage insurance and annual mortgage insurance associated with FHA loans. Upfront mortgage insurance is a one-time fee paid at closing unless financed, while annual mortgage insurance is paid monthly throughout the loan term. Borrowers can get the upfront premium back only when refinancing into a streamline FHA loan, but it applies to all FHA loans regardless of refinancing.
Types of ssl commands and keytool
Types of ssl commands and keytoolCheapSSLsecurity The document provides an overview of SSL commands and the OpenSSL and Java Keytool utilities for managing SSL/TLS protocols. It lists common OpenSSL commands for generating certificate signing requests (CSRs), self-signed certificates, and checking SSL certificates, as well as similar functionalities for Java Keytool. Additionally, it outlines commands for creating, importing, and managing keystores and certificates within the Java environment.
OpenSSL
OpenSSLSafwane Madjeri OpenSSL est une boîte à outils cryptographiques open source, développée par une communauté mondiale, qui implémente les protocoles SSL et TLS pour sécuriser les communications client/serveur. Elle comprend une bibliothèque robuste de cryptographie, et bien qu'elle présente des avantages comme sa puissance et sa portabilité, elle souffre également de certaines limites telles que des problèmes de compatibilité et des failles de sécurité. Malgré cela, OpenSSL reste un outil largement utilisé pour le chiffrement et le hachage dans diverses applications.
b
bBalaji Ravi This document provides an overview of cryptography from classical to modern times. It discusses the history and evolution of cryptographic techniques including substitution ciphers, transposition ciphers, codes, public key cryptography, digital signatures, and key distribution problems. The document also summarizes the four main topics that will be covered in the course: the history and foundations of modern cryptography, using cryptography in practice, the theory of cryptography including proofs and definitions, and a special topic in cryptography.
320.1-Cryptography
320.1-Cryptographybehrad eslamifar This document discusses security concepts like minimizing risk, managing vulnerabilities, and monitoring logs. It then focuses on OpenSSL and cryptography, explaining how to set up an OpenSSL certificate authority (CA) to generate and sign certificates. It covers generating keys, creating certificate signing requests, signing certificates, managing certificate revocation lists, and configuring applications to use the CRL for validation.
Evaluating Open Source Security Software
Evaluating Open Source Security SoftwareJohn ILIADIS The SECRETS project evaluates open source security protocols, specifically OpenSSL and FreeS/WAN, through experiments assessing their efficiency, performance, and interoperability in various applications. The evaluation framework includes assessments of the developing organizations' capabilities, support services, product evaluation, and specific application experiments. Conclusions indicate that while OpenSSL generally performs well in capability and stability, FreeS/WAN shows mixed results in support services and maintainability.
LibreSSL, one year later
LibreSSL, one year laterGiovanni Bechis This document discusses the Heartbleed bug in OpenSSL and the creation of LibreSSL as a more secure alternative. It notes that 17% of HTTPS servers were vulnerable to Heartbleed, which allowed attackers to steal passwords, credit cards, and other private data from server memory. LibreSSL was created to have fewer lines of code, modern coding practices, and fewer portability workarounds than OpenSSL to address bugs like Heartbleed. The document emphasizes fixing bugs quickly and not reinventing standard library functions.
OpenSSL User Manual and Data Format
OpenSSL User Manual and Data FormatVittorio Giovara The OpenSSL user manual provides comprehensive information on various functions including benchmark, certificates, digital signature, and encryption/decryption. It explains symmetric encryption, key and initialization vector details, password security, and provides command line examples for encryption tasks. Key concepts such as salt, cipher types, and hash functions are also discussed to enhance security.
[CB16] (物理的に分離された)エアギャップのセキュリティ:最先端の攻撃、分析、および軽減 by Mordechai Guri, Yisroel Mi...
[CB16] (物理的に分離された)エアギャップのセキュリティ:最先端の攻撃、分析、および軽減 by Mordechai Guri, Yisroel Mi...CODE BLUE エアギャップなネットワークとは物理的および論理的にパブリックなネットワークから隔離され、分離されているネットワークである。例えば軍事、(高機密を有する)産業、金融などのネットワークがあげられる。そのようなシステムへ侵入することの事項可能性が近年実演されているが、エアギャップなネットワーク(からの/への)通信は、攻撃者にとってチャレンジングなものであり、また、守る側に対してもより(攻撃が発生すれば)難しい脅威となる。エアギャップなネットワークと通信を行うあらたな手法が近年現れており、いくぶんか高度なものになっており、対応が難しいものとなっている。新たに顕在化した脆弱性は、物理環境やネットワークセキュリティを考えるうえで必要かつ、広く影響を与えるものである。
しかしながら、エアギャップなネットワーク(からの/への)情報を密かに盗み出そうとする試みは休みなく行われ続けている。よって、そららの攻撃手法を公表するだけでなく対応策と実行可能性の検証を行うことは重要なことである。
本講演では、攻撃者がエアギャップなネットワークにアクセスするために必要なステップについての概略をのべる。熱、無線、音響などを活用した最先端の攻撃手法をレビューするとともに、その対応策と検証を行う。本講演における多くの攻撃手法はユバル・イロビィチ教授の監督のもと、当ラボの研究員であるモルデチャイ・グリによって発見されている。
--- モルデチャイ・グリ Mordechai Guri
モルデチャイ・グリはコンピュータ科学者ならびにセキュリティ専門家として二十年以上の実践的な経験を有している。エルサレムのヘブライ大学コンピューターサイエンス学科にて学士及び修士号を得た。その後、ベングリオン大学(BGU)サイバーリサーチセンターにおける主任研究員およびラボ部長をつとめるともに、IBMのPhDインターナショナルフェローシップ (2015-2016)を獲得している。官民の様々な機関に対してサイバーセキュリティに関する多様な面からの学術的な研究を指導している。過去数年間にわたり多くの革新的なサイバーセキュリティ研究に従事し、(関連したいくつかの論文は)世界中で出版されている。研究分野はサイバーアタックおよびサイバー防御における最先端の手法に焦点をあてている。そして、現在の枠組みを深く調べ、最近のサイバー環境におけるセキュリティ問題への対処方法を改善するための新しい手法を開発し�
SSLCertificate101
SSLCertificate101Teerayut Hiruntaraporn The document provides a detailed guide on SSL certificate management, including the use of OpenSSL for generating RSA key pairs, creating certificate requests, and installing certificates. It covers validation of certificates, connection to LDAPS, and troubleshooting common issues, alongside examples of commands and expected outputs. Key steps involve generating keys, creating self-signed certificates, and validating the certificate and key pairs.
Attack presentation
Attack presentationFrikha Nour This document discusses attacks on wireless networks. It begins with an introduction to wireless technologies like WiFi that operate using IEEE 802.11 standards and components like wireless clients, access points, and antennas. It then explains how hackers can attack wireless networks by first finding the network, studying its traffic and security mechanisms, and then launching attacks like denial-of-service (DOS) attacks, man-in-the-middle attacks (MITM) using ARP poisoning/spoofing, and DNS spoofing attacks. The document concludes by stating that a demonstration of these attacks will be shown.
即時影像傳輸探測車 20121023
即時影像傳輸探測車 20121023艾鍗科技 即時影像傳輸探測車是基於嵌入式 Linux 系統設計的,結合伺服馬達、webcam、wifi 和超音波感測器,實現即時影像傳輸和自主行駛。該系統可通過網頁和手機應用程序進行控制和監視,是自走車技術的一部分。文檔包括技術簡介、系統架構、各組員介紹及相關參考文獻。
Sécurité des bd
Sécurité des bd Badr Hirchoua Ce document traite de la sécurité des bases de données, en abordant des sujets clés tels que la gestion des privilèges, les transactions, le cryptage d'informations et l'audit. Il présente des méthodes pour assurer l'intégrité et la confidentialité des données, ainsi que des recommandations pratiques pour sécuriser les bases de données. La conclusion fournit des conseils sur des mesures essentielles comme le changement de mots de passe par défaut et le chiffrement des données.
How to create Self-Sign Certificate by using OpenSSL
How to create Self-Sign Certificate by using OpenSSLMehdi Poustchi Amin This document provides instructions for creating a self-signed certificate using OpenSSL. It outlines downloading and installing OpenSSL and Visual C++ 2008, changing environment variables, downloading an OpenSSL configuration file, making directories, creating required files, entering a password and information, generating a server certificate, and copying and installing the certificate.
How to use OpenPGP for Email Encryption & Signing
How to use OpenPGP for Email Encryption & SigningMehdi Poustchi Amin OpenPGP is a standard for encrypting and digitally signing emails. It allows users to encrypt emails to ensure only the intended recipient can read the message. Digital signatures authenticate who sent the email and confirm the message contents were not altered. OpenPGP provides security and privacy for email communication.
Computer and internet security
Computer and internet securityhoshmand kareem This document discusses computer and internet security. It begins by defining malware and listing common types like viruses, worms, spyware, Trojan horses, scareware, and ransomware. It then describes how worms, viruses, spyware, and Trojan horses operate and their purposes. The document further discusses hackers and crackers, firewalls, reasons for writing malware, and ways to protect computers from malware like using antivirus software, firewalls, and updating operating systems. It concludes with references used to create the presentation.
[CB16] IoTとしての自動車とセキュリティ: リモートサービスのセキュリティ評価とその対策の検討 - by 和栗直英
[CB16] IoTとしての自動車とセキュリティ: リモートサービスのセキュリティ評価とその対策の検討 - by 和栗直英CODE BLUE 近年、電気自動車を筆頭にリモートから自動車の位置情報(GPS)の取得や制御を提供するサービスが増えている。
こうしたサービスは自動車OEMにとっては自動車に対するより高い付加価値となる可能性のある挑戦的なサービスである。
その一方で、今までインターネットを初めとした不特定多数の機器と相互通信するネットワークとの繋がりを持たなかった自動車にとってこうしたサービスの登場は新たな脅威に晒されることで新しいリスクを生み出すとも言える。
事実、2015年から今までの僅かな期間でこうしたサービスに対する問題点がいくつも報告されている。
こうした問題はいずれも国外で指摘されたものだが、日本市場ではどうだろうか?
そこで、我々は国内外のOEM各社が日本向けに提供しているクライアントアプリを解析、これらのアプリに対するアプリ間連携や通信に利用する証明書検証などの脆弱性の有無に加えて、攻撃者のリバースエンジニアリングによってこうした問題が発見され、悪用されることを防ぐ難読化などの耐解析技術の適用状況について評価を行った。
なお、現状日本国内において問題が指摘されているようなリモートから車両の一部機能を制御可能なサービスを提供しているOEMは限られている。
そのため、本講演では日本向けのアプリだけではなく米国向けのアプリも対象として、現時点におけるアプリのセキュリティ対策状況の評価結果およびその結果に基づいた将来的にエクスプロイトされる可能性と今後必要な対策について解説する。
--- 和栗 直英Naohide Waguri
ネットワークエンジニアとしてネットワーク機器(ギガビットイーサネットやマルチレイヤスイッチ)のソフトウェア品質評価やテスト自動化の推進、開発業務を経て、2013年に株式会社FFRIに入社。 FFRIではセキュリティテストやサイバー攻撃動向の調査、分析業務に従事し、現在はリサーチャーとして自動車を中心とした組み込み機器に対する脅威分析やペネトレーションテスト手法の研究を行っている。 CODE BLUE 2015で講演。
Blue ocean strategy ( IPL example )
Blue ocean strategy ( IPL example ) IMM Graduate School The Blue Ocean Strategy posits that companies can achieve success by creating uncontested market spaces, termed 'blue oceans,' rather than competing in saturated markets. Key principles include focusing on value innovation, which integrates differentiation and low cost, and overcoming organizational hurdles for effective implementation. The strategy emphasizes creating new demand and rendering competition irrelevant through innovative products and services, as illustrated by examples such as the nano car and the IPL.
成果展簡報-Zigbee無線自動燈光及溫度調控系統
成果展簡報-Zigbee無線自動燈光及溫度調控系統艾鍗科技 該文檔介紹了一個基於嵌入式Linux的智慧家庭系統整合平台,結合了Zigbee無線通信、燈光控制及遙感控制等技術。系統架構包括多種硬體元件,如燈光控制器和紅外線遙控設備,並具備良好的擴展性與智能應用潛力。文檔還詳述了Zigbee的工作原理、優勢以及在智慧家庭中的應用,並展望了未來的擴展機會。
Ad
Similar to Applying Security Algorithms Using openSSL crypto library (20)
Cryptography and network security
Cryptography and network securityNagendra Um The document provides an overview of cryptography and network security, covering topics including symmetric and asymmetric cryptography, key management, hashing algorithms, and digital signatures. It discusses various encryption algorithms such as DES, AES, RSA, and the principles of secure communications and authentication protocols. Key security trends and challenges, including key distribution and digital signatures, as well as real-world applications like SSL/TLS and PKI are also addressed.
Introduction to Cryptography
Introduction to CryptographySeema Goel The document provides a comprehensive overview of cryptography, covering key concepts such as encryption, decryption, and various types of cryptographic techniques including symmetric and asymmetric algorithms, as well as hashing and digital signatures. It details the general goals of cryptography such as confidentiality, integrity, authentication, and nonrepudiation, along with common types of attacks against cryptographic systems. Furthermore, the document discusses important protocols like Transport Layer Security (TLS) and Public Key Infrastructure (PKI), highlighting their roles in secure communication.
Crypt
CryptMir Majid The document discusses cryptography and the RSA encryption algorithm. It begins with an introduction to cryptography and its uses. It then covers the history of cryptography, common security issues, and different cryptographic techniques like symmetric and asymmetric encryption. The document focuses on explaining the RSA algorithm, how it works using public and private keys, and why factoring large numbers makes RSA secure. It provides an overview of the key aspects of cryptography and the RSA algorithm.
Basic Cryptography unit 4 CSS
Basic Cryptography unit 4 CSSDr. SURBHI SAROHA The document discusses various topics related to public key cryptography including:
1) Public key cryptography uses key pairs (public/private keys) to encrypt and decrypt messages securely. Private keys are kept secret while public keys can be openly distributed.
2) RSA is a commonly used public key cryptosystem that uses large prime numbers to encrypt data. It is considered secure if a large enough key is used.
3) Digital signatures authenticate messages by encrypting a hash of the message with the sender's private key, allowing verification with their public key.
ch09_rsa_nemo.ppt
ch09_rsa_nemo.pptChandraB15 Public-key cryptography uses two keys: a public key for encryption and digital signatures, and a private key for decryption and signature verification. RSA is the most widely used public-key cryptosystem, using large prime factorization and modular exponentiation. It allows secure communication without prior key exchange. While brute force attacks on RSA are infeasible due to large key sizes, its security relies on the difficulty of factoring large numbers.
Security
Security Saqib Shehzad 1. The document discusses principles of secure communication including secrecy, authentication, and message integrity. It describes passive and active intrusion types.
2. Symmetric and public key cryptography methods are covered, including AES, RSA, digital signatures, hashes, and their use for encryption, authentication, and ensuring message integrity.
3. Secure email is discussed as an application, where a symmetric session key is used to encrypt messages and that key is encrypted with the recipient's public key for delivery.
RSA
RSAbansidhar11 This document provides a summary of public key encryption and digital signatures. It begins by reviewing symmetric cryptography and its limitations in key distribution. It then introduces public key encryption, where each party has a public and private key pair. The document outlines the RSA algorithm and how it uses large prime number factorization problems to encrypt and decrypt messages. It also discusses how digital signatures can provide authentication, integrity, and non-repudiation for electronic messages and contracts using public key techniques like RSA.
Rsa
Rsamagentie Public key cryptography uses two keys - a public key that can encrypt messages but not decrypt them, and a private key that can decrypt messages but not encrypt them. The RSA algorithm is a commonly used public key cryptosystem. It works by having users generate a public/private key pair using large prime numbers, then messages can be encrypted with the public key and decrypted with the private key. The security of RSA relies on the difficulty of factoring large numbers.
Cryptography 101
Cryptography 101Aditya Kamat The document provides an extensive overview of cryptography, including definitions, key concepts, and various encryption techniques such as hashing, symmetric and asymmetric key encryption, and digital signatures. It also discusses real-world applications, mathematical foundations, and best practices for secure communication, particularly emphasizing the importance of confidentiality, integrity, and availability of data. Additionally, it highlights tools like PGP for email security and common pitfalls to avoid in cryptographic implementations.
international security system data threats
international security system data threatsgacop74666 1. Principle of Least Privilege (POLP) This principle states that every user and program on the system should be granted only the specific rights and permissions needed to perform their tasks, with no more.
PRINCIPLES OF INFORMATION SYSTEM SECURITY
PRINCIPLES OF INFORMATION SYSTEM SECURITYgacop74666 Introduction: Information security is more and more important every day in the workplace. If we want to improve our information security, we need a solid understanding of the principles that will help us do that. This guide explores those principles and will guide you to building a more secure environment.
Information Security Principles: There are three basic principles of information security, and all other practices are based on these three:
* Confidentiality: Confidentiality is the basic tenet of information security. Confidentiality means that you don't share private or confidential information with anyone who shouldn't know it. As the name implies, you don't give out confidential information.
* Availability: Availability means that you can access the information you need when you need it. You may not need access to everything all the time, but when you do, you want access quickly. You may need access to your bank account when you pay a bill. This is availability.
* Integrity: If you make a change to something, it should be tracked and logged in a journal or log. That way, you can verify that no unauthorized changes were made to the original information, so we know that the information is genuine. In short, integrity means you can verify that the information hasn't been altered in any way.
There are four key concepts that underpin the practice of information security. These concepts, when integrated and applied appropriately, enable security managers and practitioners to defend against and recover from attacks. The four key concepts are:
* Confidentiality: Confidentiality refers to protecting information from unauthorized access, use, or disclosure. This includes both internal and external threats. Data encryption or access control lists are examples of confidentiality controls.
* Integrity: Integrity refers to protecting the accuracy, completeness, and validity of information. This includes protecting data from being modified without authorization. Data hashing algorithms or message authentication codes are examples of integrity controls.
* Availability: Availability refers to ensuring that information and systems are accessible to authorized users when they need them. This includes measures to prevent service outages or data loss due to natural disasters or accidental or intentional malicious activity. Redundant systems, data backups, and disaster recovery plans are examples of availability controls.
* Accountability: Accountability involves tracing user actions to the identity of the user. If the user's identity is associated with a group, then the actions of the user are also associated with the group. Accountability mechanisms typically involve the use of logs, audit trails, and other monitoring techniques. Accountability controls are also used to identify and fix system weaknesses that could lead to unauthorized access or changes to data and systems.
By following these basic principles, we can help protect our information fro
KEY MGMT.ppt
KEY MGMT.pptRizwanBasha12 The document discusses key management and the Diffie-Hellman key exchange protocol. It begins by explaining public-key encryption helps address key distribution problems. It then describes different methods for distributing public keys including public announcement, publicly available directories, public-key authorities, and public-key certificates. It also explains how public-key encryption can be used to distribute secret keys, including Diffie-Hellman key exchange and hybrid key distribution. The document concludes by discussing elliptic curve cryptography as an alternative to methods using large integer arithmetic.
Unit --3.ppt
Unit --3.pptDHANABALSUBRAMANIAN Public-key cryptography uses two keys: a public key to encrypt messages and verify signatures, and a private key for decryption and signing. RSA is the most widely used public-key cryptosystem, using large prime factorization and exponentiation modulo n for encryption and decryption. While faster than brute-force, breaking RSA remains computationally infeasible with sufficiently large key sizes over 1024 bits.
1329 n 9460
1329 n 9460kicknit123 The document discusses various topics related to network security including encryption, authentication, and protocols. It provides an overview of symmetric and public key cryptography, algorithms like DES and RSA, digital signatures, protocols like SSL and IPsec, and applications like PGP. Common security threats like packet sniffing, IP spoofing, and denial of service attacks are also summarized.
needed.ppt
needed.pptfaizalkhan673954 This document provides an introduction to cryptography. It defines key terms like cryptography, cryptanalysis, and cryptology. It describes the goals of encryption and authentication. It explains symmetric key cryptography where a shared secret key is used for both encryption and decryption. It also covers public key cryptography using key pairs, digital signatures to provide authentication, and how public key encryption and signatures can be combined. It discusses cryptographic attacks and the importance of Kerckhoffs' principle. It provides an overview of common cryptographic algorithms like block ciphers, stream ciphers, hash functions, and key exchange methods. It also discusses concepts like encryption modes, password hashing, random number generation, and the security of algorithms like RSA and Diffie-
introduction to cryptography (basics of it)
introduction to cryptography (basics of it)neonaveen This document provides an introduction to cryptography. It defines key terms like cryptography, cryptanalysis, and cryptology. It describes the goals of encryption and authentication. It explains symmetric key cryptography where a shared secret key is used for both encryption and decryption. It also covers public key cryptography using key pairs, digital signatures to provide authentication, and how public key encryption and signatures can be combined. It discusses cryptographic attacks and the importance of Kerckhoffs' principle. It provides an overview of common cryptographic algorithms like block ciphers, stream ciphers, hash functions, and key exchange methods. It also discusses concepts like encryption modes, password hashing, random number generation, and the security of algorithms like RSA and Diffie-
crypto.ppt
crypto.pptGanesh Chavan The document provides an introduction to cryptography, including definitions of key terms, goals of cryptography like encryption and authentication, and descriptions of common cryptographic techniques. It summarizes symmetric key encryption where a shared secret key is used for both encryption and decryption, public key encryption using key pairs, digital signatures to authenticate messages, and how public key encryption and signatures can be combined. It also discusses cryptographic attacks, Kerckhoffs' principle of secrecy depending on the key not the algorithm, provable security, block ciphers like AES and DES, encryption modes, stream ciphers, hash functions, message authentication codes, key exchange methods like Diffie-Hellman, and public key cryptosystems like RSA and ElGamal
crypto1.ppt
crypto1.ppttommychauhan The document provides an introduction to cryptography, including definitions of key terms, goals of cryptography like encryption and authentication, and descriptions of common cryptographic techniques. It summarizes symmetric key encryption where a shared secret key is used for both encryption and decryption, public key encryption using key pairs, digital signatures to authenticate messages, and how public key encryption and signatures can be combined. It also discusses cryptographic attacks, Kerckhoffs' principle of secrecy depending on the key not the algorithm, provable security, block ciphers like AES and DES, encryption modes, stream ciphers, hash functions, message authentication codes, key exchange methods like Diffie-Hellman, and public key cryptosystems like RSA and ElGamal
CNS 3RD UNIT PPT.pptx
CNS 3RD UNIT PPT.pptxpjeraids 1. Public key cryptography uses asymmetric key encryption where each user has a public key for encryption and a private key for decryption.
2. The RSA algorithm is an example of public key encryption that uses modular exponentiation with large prime numbers to encrypt plaintext and decrypt ciphertext.
3. Diffie-Hellman key exchange allows two users to securely exchange a secret key over an insecure channel without any prior secrets.
18CS2005 Cryptography and Network Security
18CS2005 Cryptography and Network SecurityKathirvel Ayyaswamy The document covers public-key cryptography, detailing its principles, including algorithms like RSA, Diffie-Hellman key exchange, and ElGamal cryptosystem. Public-key cryptography uses two keys for encryption and decryption, addressing issues of key distribution and digital signatures. It also discusses the security mechanisms and challenges associated with these cryptosystems, such as brute force attacks and timing attacks.
Ad
More from Priyank Kapadia (15)
Ubuntu, Canonical and the release of Feisty
Ubuntu, Canonical and the release of FeistyPriyank Kapadia The document summarizes Ubuntu, an open-source Linux distribution developed by Canonical. It discusses Ubuntu's goals of bringing free software to common platforms and providing an out-of-box experience. It also outlines Canonical's business model of offering commercial support and engineering services to support Ubuntu's development. Finally, it previews new features for the upcoming Feisty Fawn release, including improved wireless networking, printing support, and automated testing.
How to start an Open Source Project
How to start an Open Source ProjectPriyank Kapadia This document provides guidance on starting an open source project. It outlines common pitfalls like underestimating resources and having an unclear vision. The key first steps are to learn from other projects, define goals and build a community. Successful projects have active management, coordination of tasks, and processes for decision making and releases. While many are volunteer efforts, large projects often rely on funding and paid contributors to coordinate activities. Managing volunteers is challenging and requires finding roles that motivate contributors.
Developing Multilingual Applications
Developing Multilingual ApplicationsPriyank Kapadia The document discusses developing multilingual apps and localization. It covers internationalization (i18n) and localization (l10n) basics like handling different languages and encodings. It demonstrates marking translatable strings in code and the process of building locales. Localization is defined as implementing a specific language for an already internationalized software by adapting it to a given culture. Steps for localizing free and open source software like building the environment and merging translations are outlined. The document also briefly mentions opportunities for contributing to localization efforts.
Open Solaris
Open SolarisPriyank Kapadia The document discusses the benefits of exercise for mental health. Regular physical activity can help reduce anxiety and depression and improve mood and cognitive functioning. Exercise causes chemical changes in the brain that may help protect against mental illness and improve symptoms.
How to build Debian packages
How to build Debian packages Priyank Kapadia The document discusses how to build Debian packages. It covers the basics of Debian packaging including what packages are, why the Debian distribution uses the .deb package format, and the basic components of a Debian package. It then outlines the steps for building a package, including using tools like dh_make and cdbs to generate the package files and structure, and dpkg-buildpackage to build the binary package. It emphasizes quality control and following Debian policies. It concludes with information on contributing packages to Debian through mentors.debian.net and becoming a Debian Developer.
AMANDA
AMANDAPriyank Kapadia Amanda is an open source network backup and recovery software that provides client-server backup functionality across multiple operating systems in a robust and scalable manner. It uses native backup tools and standard data formats to provide functionality similar to proprietary solutions. Amanda features include automatic backup level selection, backup to disk and tape, intelligent scheduling, compression, encryption and fault tolerance. Data recovery with Amanda is simple through browsing backup information and restoring data using operating system tools.
C Types - Extending Python
C Types - Extending PythonPriyank Kapadia Ctypes provides an easy way to extend Python with functions from C libraries without needing to write C code or dependencies like SWIG. It works by dynamically loading shared libraries and allowing Python functions to call C functions. Ctypes abstracts away the complexities of type conversions and memory management to make the process simple. Developers can write Python callback functions, define C structures and unions in Python, and interface with C libraries using just a few lines of Python code. This makes ctypes a popular modern alternative for creating Python bindings for C code.
Google Web toolkit
Google Web toolkitPriyank Kapadia The document discusses the Google Web Toolkit (GWT), which allows developers to build Ajax applications in Java that are compiled into JavaScript for cross-browser support. It addresses some common architectural issues with Ajax apps that GWT handles, such as back button support, session state, and UI event handling. The author provides an overview of GWT features and demos building widgets and applications. Gotchas discussed include RPC only working with GWT clients and needing to replace hibernated objects before serialization to avoid memory leaks.
Debugging Applications with GNU Debugger
Debugging Applications with GNU DebuggerPriyank Kapadia The document discusses using the GNU Debugger (gdb) to debug applications. It covers when to use a debugger, invoking and configuring gdb, setting breakpoints, examining stack frames and data, disassembling code, and viewing registers. Gdb allows stepping through code, viewing variables and memory, and setting conditional breakpoints to debug programs.
Storage Management using LVM
Storage Management using LVMPriyank Kapadia The document provides an overview of Logical Volume Management (LVM) in Linux. It discusses what LVM is, its main components like physical volumes, volume groups, logical volumes, and how they relate. It then gives steps to use LVM by creating a physical volume, volume group and logical volume. It also discusses how LVM allows expanding logical volumes and live resizing of file systems.
Linux Kernel Development
Linux Kernel DevelopmentPriyank Kapadia The document provides an overview of device driver development in Linux, including character device drivers. It discusses topics such as device driver types, kernel subsystems, compiling and loading kernel modules, the __init and __exit macros, character device registration, and issues around reference counting when removing modules. It also provides sample code for a basic character device driver that prints information to the kernel log.
Recently uploaded (20)
2025_06_18 - OpenMetadata Community Meeting.pdf
2025_06_18 - OpenMetadata Community Meeting.pdfOpenMetadata The community meetup was held Wednesday June 18, 2025 @ 9:00 AM PST.
Catch the next OpenMetadata Community Meetup @ https://www.meetup.com/openmetadata-meetup-group/
In this month's OpenMetadata Community Meetup, "Enforcing Quality & SLAs with OpenMetadata Data Contracts," we covered data contracts, why they matter, and how to implement them in OpenMetadata to increase the quality of your data assets!
Agenda Highlights:
👋 Introducing Data Contracts: An agreement between data producers and consumers
📝 Data Contracts key components: Understanding a contract and its purpose
🧑🎨 Writing your first contract: How to create your own contracts in OpenMetadata
🦾 An OpenMetadata MCP Server update!
➕ And More!
Coordinated Disclosure for ML - What's Different and What's the Same.pdf
Coordinated Disclosure for ML - What's Different and What's the Same.pdfPriyanka Aash Coordinated Disclosure for ML - What's Different and What's the Same
OWASP Barcelona 2025 Threat Model Library
OWASP Barcelona 2025 Threat Model LibraryPetraVukmirovic Threat Model Library Launch at OWASP Barcelona 2025
https://owasp.org/www-project-threat-model-library/
OpenPOWER Foundation & Open-Source Core Innovations
OpenPOWER Foundation & Open-Source Core InnovationsIBM penPOWER offers a fully open, royalty-free CPU architecture for custom chip design.
It enables both lightweight FPGA cores (like Microwatt) and high-performance processors (like POWER10).
Developers have full access to source code, specs, and tools for end-to-end chip creation.
It supports AI, HPC, cloud, and embedded workloads with proven performance.
Backed by a global community, it fosters innovation, education, and collaboration.
Creating Inclusive Digital Learning with AI: A Smarter, Fairer Future
Creating Inclusive Digital Learning with AI: A Smarter, Fairer FutureImpelsys Inc. Have you ever struggled to read a tiny label on a medicine box or tried to navigate a confusing website? Now imagine if every learning experience felt that way—every single day.
For millions of people living with disabilities, poorly designed content isn’t just frustrating. It’s a barrier to growth. Inclusive learning is about fixing that. And today, AI is helping us build digital learning that’s smarter, kinder, and accessible to everyone.
Accessible learning increases engagement, retention, performance, and inclusivity for everyone. Inclusive design is simply better design.
Smarter Aviation Data Management: Lessons from Swedavia Airports and Sweco
Smarter Aviation Data Management: Lessons from Swedavia Airports and SwecoSafe Software Managing airport and airspace data is no small task, especially when you’re expected to deliver it in AIXM format without spending a fortune on specialized tools. But what if there was a smarter, more affordable way?
Join us for a behind-the-scenes look at how Sweco partnered with Swedavia, the Swedish airport operator, to solve this challenge using FME and Esri.
Learn how they built automated workflows to manage periodic updates, merge airspace data, and support data extracts – all while meeting strict government reporting requirements to the Civil Aviation Administration of Sweden.
Even better? Swedavia built custom services and applications that use the FME Flow REST API to trigger jobs and retrieve results – streamlining tasks like securing the quality of new surveyor data, creating permdelta and baseline representations in the AIS schema, and generating AIXM extracts from their AIS data.
To conclude, FME expert Dean Hintz will walk through a GeoBorders reading workflow and highlight recent enhancements to FME’s AIXM (Aeronautical Information Exchange Model) processing and interpretation capabilities.
Discover how airports like Swedavia are harnessing the power of FME to simplify aviation data management, and how you can too.
The Future of AI Agent Development Trends to Watch.pptx
The Future of AI Agent Development Trends to Watch.pptxLisa ward The Future of AI Agent Development: Trends to Watch explores emerging innovations shaping smarter, more autonomous AI solutions for businesses and technology.
Enhance GitHub Copilot using MCP - Enterprise version.pdf
Enhance GitHub Copilot using MCP - Enterprise version.pdfNilesh Gule Slide deck related to the GitHub Copilot Bootcamp in Melbourne on 17 June 2025
Lessons Learned from Developing Secure AI Workflows.pdf
Lessons Learned from Developing Secure AI Workflows.pdfPriyanka Aash Lessons Learned from Developing Secure AI Workflows
You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante We live in an ever evolving landscape for cyber threats creating security risk for your production systems. Mitigating these risks requires participation throughout all stages from development through production delivery - and by every role including architects, developers QA and DevOps engineers, product owners and leadership. No one is excused! This session will cover examples of common mistakes or missed opportunities that can lead to vulnerabilities in production - and ways to do better throughout the development lifecycle.
The Future of Data, AI, and AR: Innovation Inspired by You.pdf
The Future of Data, AI, and AR: Innovation Inspired by You.pdfSafe Software The future of FME is inspired by you. We can't wait to show you what's ahead for FME and Safe Software.
CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025
CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025pcprocore 👉𝗡𝗼𝘁𝗲:𝗖𝗼𝗽𝘆 𝗹𝗶𝗻𝗸 & 𝗽𝗮𝘀𝘁𝗲 𝗶𝗻𝘁𝗼 𝗚𝗼𝗼𝗴𝗹𝗲 𝗻𝗲𝘄 𝘁𝗮𝗯> https://pcprocore.com/ 👈◀
CapCut Pro Crack is a powerful tool that has taken the digital world by storm, offering users a fully unlocked experience that unleashes their creativity. With its user-friendly interface and advanced features, it’s no wonder why aspiring videographers are turning to this software for their projects.
Wenn alles versagt - IBM Tape schützt, was zählt! Und besonders mit dem neust...
Wenn alles versagt - IBM Tape schützt, was zählt! Und besonders mit dem neust...Josef Weingand IBM LTO10
From Manual to Auto Searching- FME in the Driver's Seat
From Manual to Auto Searching- FME in the Driver's SeatSafe Software Finding a specific car online can be a time-consuming task, especially when checking multiple dealer websites. A few years ago, I faced this exact problem while searching for a particular vehicle in New Zealand. The local classified platform, Trade Me (similar to eBay), wasn’t yielding any results, so I expanded my search to second-hand dealer sites—only to realise that periodically checking each one was going to be tedious. That’s when I noticed something interesting: many of these websites used the same platform to manage their inventories. Recognising this, I reverse-engineered the platform’s structure and built an FME workspace that automated the search process for me. By integrating API calls and setting up periodic checks, I received real-time email alerts when matching cars were listed. In this presentation, I’ll walk through how I used FME to save hours of manual searching by creating a custom car-finding automation system. While FME can’t buy a car for you—yet—it can certainly help you find the one you’re after!
9-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection.
"Database isolation: how we deal with hundreds of direct connections to the d...
"Database isolation: how we deal with hundreds of direct connections to the d...Fwdays What can go wrong if you allow each service to access the database directly? In a startup, this seems like a quick and easy solution, but as the system scales, problems appear that no one could have guessed.
In my talk, I'll share Solidgate's experience in transforming its architecture: from the chaos of direct connections to a service-based data access model. I will talk about the transition stages, bottlenecks, and how isolation affected infrastructure support. I will honestly show what worked and what didn't. In short, we will analyze the controversy of this talk.
FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptx
FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptxFIDO Alliance FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography
You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
Applying Security Algorithms Using openSSL crypto library
- 1. Applying security algorithms using openssl crypto library B.C. Sekar HCL Technologies Limited NETWORKING PRODUCTS DIVISION, HCL
- 2. Agenda * Introduction * Overview of related security concepts. * Types of security algorithms * Overview of openssl crypto library * Using the security algorithms * Programming using crypto library. * Conclusion
- 3. Introduction * Security Algorithms form the basis of many security systems like SSH, HTTPS etc., * Growing use of web applications for e-commerce, banking and other security sensitive apps. * There is a clear need for securing communication. * Applying security algorithms is essential - if you are building or enhancing your security system
- 4. Agenda * Introduction * Overview of related security concepts . * Types of security algorithms * Overview of openssl crypto library * Using the security algorithms * Programming using crypto library. * Conclusion
- 5. Block Ciphers * Messages are broken down into blocks * Each of these are then encrypted M1 M2 M3 M4 Mn Plain Message (M) E E E E E C1 C2 C3 C4 Cn Cipher Message (C)
- 6. Symmetric cryptography It uses the same key for encryption and decryption. E.g. DES, 3DES, Blowfish Encrypt using key K Cipher text Sender Decrypt using key K Cipher text Plain text Receiver Send from Sender to Receiver Plain Text
- 7. Public key cryptography Public key is distributed whereas private key is kept secret. E.g. RSA, DSA Encrypt using B’s public key Cipher text A Decrypt using B’s private key Cipher text Plain text B Send from Sender to Receiver Plain Text
- 8. Hashing Function Hash Function Message digest Message Eg. a word “Linux conference” becomes EFDD2356. Typical Hash functions have an infinite domain, such as byte streams of arbitrary length and a finite range such as bit sequences of some fixed length.
- 9. Digital Signatures Hash Function Message digest Encrypt using Sender’s private key Digital Signature Message The message digest which is the hash value is Encrypted and anybody can check the signature using the public key.
- 10. The purpose of a Message authentication code is to authenticate a source of a message and and its integrity. MAC Hash Function Message digest Encrypt using symmetric key MAC Message
- 11. NETWORKING PRODUCTS DIVISION, HCL Digital Certificates Country Name: State: Locality: Organizational Name: Common Name: E-mail address: Public key Certificate Sign using private key of Self or trusted Certification Authority(CA).
- 12. Agenda * Introduction * Overview of related security concepts. * Types of security algorithms * Overview of openssl crypto library * Using the security algorithms * Programming using the crypto library. * Conclusion
- 13. Types of security Algorithms * Hash functions * Authentication codes * Cryptographic algorithms Symmetric Public key * Key agreement algorithms
- 14. Hash functions – SHA-1 * SHA-1 Secure Hash Function-1 * Its Secure They are one way and collision free. * SHA-1 produces a 160-bit hash. * Because the number of possible hashes are so large, the probability of getting the same hash for a different message is smaller 2 80 by brute force. * Some cryptanalysts were able to do it in 2 69 .
- 15. Authentication codes - HMAC * Keyed-Hash Message Authentication code is used by the sender to produce a value that is formed by condensing the secret key and the message input. * A hash function such as SHA-1 will be used. * HMAC depends on the size and quality of key and size and quality of hash output length in bits. * HMAC-SHA-1 and HMAC-MD5 are used with IPSec and TLS protocols.
- 16. * It’s a block encryption algorithm is * Fast 26 clock cycles per byte in 32-bit microprocessors * Simple it uses XOR, addition * Secure its key length is variable and can be as long as 448 bits Cryptographic Algorithms – Symmetric - Blowfish
- 17. Cryptographic Algorithms – Public key * Unlike private key cryptography there is no need to share keys. Instead a public key is available to any user and a private key is held as secret. * Public key cryptography is based on the idea of a trapdoor function. * f: X Y * f is one to one, f is public, f -1 is difficult to compute, f is easy to compute and f -1 is easy to compute if a trapdoor is known.
- 18. Public key cryptography - RSA * Rivest Shamir Adleman * Find P and Q, two large prime numbers, N=PQ * Choose E such that E and (P-1)(Q-1) are relatively prime, which means they have no common factors except 1 * Find another number such that ED-1 is divisible by (P-1)(Q-1). * The values E and D are called public and private components respectively.
- 19. Public key cryptography – RSA …contd * The public key is the pair (E,N) and private key is the pair (D,N). * It is currently difficult to obtain D from (E,N).
- 20. Public key cryptography – RSA …contd * Encryption * Suppose Alice wants to send a message m to Bob. * Alice creates the cipher text c by exponentiation: c = m^e mod n, where e and n are Bob's public key. She sends c to Bob. To decrypt, Bob also exponentiates: m = c^d mod n; the relationship between e and d ensures that Bob correctly recovers m. Since only Bob knows d, only Bob can decrypt this message.
- 21. * Message Digest is computed. * Alice creates a digital signature s by exponentiation: s = m^d mod n , where d and n are Alice's private key. She sends m and s to Bob. To verify the signature, Bob exponentiates and checks that the message digest m is recovered: m = s^e mod n , where e and n are Alice's public key. Public key cryptography – RSA …contd
- 22. * The obvious way to do this attack is to factor the public modulus, n, into its two prime factors, p and q. From p, q, and e, the public exponent, the attacker can easily get d, the private exponent. * The hard part is factoring n; the security of RSA depends on factoring being difficult. In fact, the task of recovering the private key is equivalent to the task of factoring the modulus: you can use d to factor n, as well as use the factorization of n to find d RSA – How safe?
- 23. * The protocol allows two users to exchange a secret key without the aid of another secret key in an insecure medium * The protocol has two public system variables p and g. p is a prime number. g which is less than p, n = g^k mod p Key agreement algorithms – Diffie Hellman
- 24. * Alice generates a random private key value a. Bob generates a random private key value b. * Alice public value is: pa = g^a mod p. * Bob’s public key value is: pb = g^b mod p. * They exchange their public key values * Alice computes g^ab = pb^a mod p = (g^b)^a mod p. * Bob computes g^ba = pa^b mod p = (g^a) ^b mod p. * K = g^ab = g^ba Key agreement algorithms – Diffie Hellman …contd
- 25. * It assumes that the given two public values g^a mod p and g^b mod p, its not feasible to calculate the shared secret key k = g^ab mod p. * There is Man in the middle attack vulnerability * The communicating parties are required to authenticate themselves by use of digital signatures and public key certificates. Key agreement algorithms – Diffie Hellman …contd
- 26. Agenda * Introduction * Overview of related security concepts. * Types of security algorithms * Overview of openssl crypto library * Using the security algorithms * Programming using crypto library * Conclusion
- 27. * The crypto library implements a wide variety of security algorithms. * Its used for implementation of SSL, TLS, SSH and OpenPGP and other standards. * Crypto library consists of many sub-libraries which implement the individual algorithms. OpenSSL crypto library
- 28. Crypto sub-libraries Sub-libraries Blowfish DES DH HMAC RSA SHA-1
- 29. OpenSSL CLIs * openssl is a CLI which has options to invoke the crypto subsystems and do the necessary security functionality. $ openssl list-cipher-commands base64 bf bf-cbc cast des
- 30. OpenSSL CLIs …contd $ openssl list-message-digest-commands md2 md4 md5 mdc2 rmd160 sha sha1
- 31. Agenda * Introduction * Overview of related security concepts. * Types of security algorithms * Overview of openssl crypto library * Using the security algorithms * Programming using crypto library. * Conclusion
- 32. Generating Authentication codes $ openssl dgst –sha1 args.c SHA1(args.c)= 7ee67eeb39f1ed1117855ca1986416d8052c9dcf $ openssl dgst -md5 args.c MD5(args.c)= 0e474915f4a0fb8af12594d11c2cf048
- 33. Using blowfish for file encryption/decryption $ openssl enc -bf -in test.txt -out test.enc enter bf-cbc encryption password: Verifying password - enter bf-cbc encryption password: $ openssl enc -d -bf -in test.enc -out test.txt enter bf-cbc decryption password:
- 34. Generate RSA keys Generating $ openssl genpkey -algorithm RSA -out key.pem Generating with protection $ openssl genpkey -algorithm RSA -out key.pem -bf -pass pass:hello The public key info is contained within the private key, so no separate public key is generated. Mainly used in web server cases.
- 35. Generate Diffie Hellman key * Generate 1024 bit DH parameters: openssl genpkey -genparam -algorithm DH -out dhp.pem -pkeyopt dh_paramgen_prime_len:1024 * Generate DH key from parameters: openssl genpkey -paramfile dhp.pem -out dhkey.pem
- 36. Agenda * Introduction * Overview of related security concepts. * Types of security Algorithms * Overview of openssl crypto library * Using the security Algorithms * Programming using crypto library. * Conclusion
- 37. Programming using Crypto library – Blowfish – Create a key * Step 1: Open /dev/random generate_symmetric_key() { if ((fd = open ( "/dev/random", O_RDONLY)) == -1) perror ("open error");
- 38. Programming using Crypto library – Blowfish – Create a key Step 2: Initialize key Read 16 bytes from /dev/random That gives 128-bit random symmetric key. Read 8 bytes to populate initialization vector. int bf_key[16]; int bf_vector[8]; if ((read (fd, bf_key, 16)) == -1) perror (“Could not read the key"); if ((read (fd, init_vector, 8)) == -1) perror ("read iv error");
- 39. Programming using Crypto library – Blowfish - Encrypt * Step 1: Create a cipher context EVP_CIPHER_CTX ctxt; EVP_CIPHER_CTX_init (&ctxt); * Step 2: Initialize encryption algorithm and key. EVP_EncryptInit ( &ctxt, EVP_bf_cbc (), bf_key, bf_vector); * Step 3: Read data in 1K size if ((n = read (infd, inbuff, 1024) == -1)
- 40. Programming using Crypto library – Blowfish - Encrypt * Step 4: Encrypt blocks of 1K size if (EVP_EncryptUpdate (&ctx, outbuf, &olen, inbuff, n) != 1) * Step 5: if (EVP_EncryptFinal (&ctx, outbuf + olen, &tlen) != 1) * Step 6: Write your encrypted buffer into a file. * Step 7: Cleanup context. EVP_CIPHER_CTX_cleanup (&ctx);
- 41. Programming using Crypto library – Blowfish - Decrypt * Likewise, use EVP_DecryptUpdate and EVP_DecryptFinal for decryption…
- 42. SSL/TLS Architecture Packet processing in SSL/TLS record protocol layer. Source: www.modssl.org
- 43. SSL/TLS connection establishment SSL/TLS Connection establishment. Source: www.modssl.org
- 44. Summary * We dealt with various security algorithms and how openssl CLI and crypto library provides a mechanism to apply those algorithms.
- 45. References http://www.openssl.org http://www.rsasecurity.com http://linuxgazette.net/issue87/vinayak.html
- 46. Questions B.C. Sekar HCL Technologies Limited, 49-50, Nelson Manikkam Road, Chennai - 600026. Phone - +91-44-23750171 [email_address] http://www.hcltech.com
