Best Coding Practices in Java and C++
Download as pptx, pdf1 like879 views
The document provides guidelines for various naming conventions including: - Standards for naming variables, member functions, local variables, and method arguments. - Standards for naming classes, interfaces and packages. - Guidelines related to code documentation, comments and indentation. - Common coding errors and best practices to avoid them.
1 of 21
Downloaded 29 times



















Ad
Recommended
Pt permissão de trabalho
Pt permissão de trabalhofabricioalvesalmeida85 Este documento é uma permissão de trabalho que descreve as atividades, equipamentos de proteção individual necessários e medidas preventivas para um trabalho. Ele lista os possíveis perigos como quedas, choques elétricos e exposição a produtos químicos. Também especifica os EPIs necessários como capacetes, luvas e óculos de segurança.
Epi para trabalho em altura NR 35
Epi para trabalho em altura NR 35DiegoAugusto86 O documento discute a Norma Regulamentadora NR-35, que especifica medidas de segurança para trabalho em altura. A norma estabelece a correta seleção e uso de equipamentos de proteção individual para garantir a saúde e segurança dos trabalhadores. A aplicação da NR-35 protege trabalhadores e beneficia empregadores ao reduzir acidentes e custos.
Permissão de Trabalho - PT 0001
Permissão de Trabalho - PT 0001IZAIAS DE SOUZA AGUIAR Este documento descreve os procedimentos de segurança obrigatórios para escavações e outros tipos de trabalho, incluindo equipamentos de proteção, permissões de trabalho e precauções específicas. É necessária a inspeção prévia dos riscos e equipamentos, além da declaração de que a equipe recebeu todas as informações de segurança.
Questionário de Consulta aosTrabalhadores Grupo Consulgal 2009
Questionário de Consulta aosTrabalhadores Grupo Consulgal 2009Marta Silva Este questionário busca avaliar o conhecimento dos trabalhadores sobre segurança no trabalho e gestão de riscos na empresa. Ele contém perguntas sobre o conhecimento dos trabalhadores sobre avaliação de riscos, medidas de segurança, treinamentos, acidentes ocorridos e sistema integrado de gestão da empresa.
DDS ENEVA.ppt
DDS ENEVA.pptDavidWill25 O documento discute a diferença entre riscos e perigos, definindo perigo como qualquer fonte que pode causar dano e risco como a exposição a esses perigos. Ele enfatiza a importância da prevenção para reduzir riscos, como adotar atitudes positivas e estar ciente dos perigos ao nosso redor.
Check list espaço-confinado
Check list espaço-confinadoTst Eliana Gil Este documento é uma lista de verificação para trabalhos em espaços confinados. Contém 41 itens relacionados à segurança que devem ser verificados antes da entrada no espaço confinado, como isolamento de energia, remoção de fontes de ignição, ventilação adequada, uso correto de EPIs e treinamento dos trabalhadores. A lista deve ser assinada pelo supervisor, fiscal e encarregado para autorizar o trabalho.
Trabalho a quente modulo II
Trabalho a quente modulo IIemanueltstegeon O documento fornece diretrizes sobre segurança para trabalhos a quente, incluindo requisitos para proteção contra incêndios, inspeções prévias dos equipamentos, monitoramento da área durante e após o trabalho, e responsabilidades dos envolvidos.
0051 travamento seguran%e7a-92sld
0051 travamento seguran%e7a-92sldSávio Gomes O documento descreve procedimentos de lockout-tagout para garantir a segurança durante serviços em máquinas e equipamentos. Estabelece definições de termos como energia, bloqueio e isolamento. Detalha etapas como desligamento, bloqueio, verificação de isolamento e remoção após serviço. A norma objetiva proteger trabalhadores durante intervenções em fontes de energia.
Nbr 12962 inspecao manut. recarga de extintores (2)
Nbr 12962 inspecao manut. recarga de extintores (2)cristiano Santos Este documento estabelece as condições mínimas para a inspeção, manutenção e recarga de extintores de incêndio no Brasil. Ele define os níveis de manutenção recomendados, a frequência de inspeção, os procedimentos para recarga e os requisitos específicos para diferentes tipos de extintores.
11 proteção e combate a incêndio 05102005
11 proteção e combate a incêndio 05102005Shirlene Maciel Rafino O documento descreve conceitos básicos de fogo, seus elementos constituintes e métodos de combate e prevenção de incêndios. Aborda combustíveis, comburente, calor, propagação do fogo, classes de incêndio, métodos de extinção, extintores e agentes extintores.
Guia para analise de risco - NR 35
Guia para analise de risco - NR 35Fabiano Micaella O documento fornece diretrizes para análise de risco de trabalho em altura, incluindo dispositivos de proteção coletiva e equipamentos de proteção individual. Ele descreve sistemas de guarda-corpo, redes de segurança, escadas e rampas seguras, além de equipamentos como cinturão paraquedista e sistemas de retenção de queda.
NR 35 - Capacitação no trabalho em altura.pptx
NR 35 - Capacitação no trabalho em altura.pptxMelquiadesAlmeida2 A norma NR-35 estabelece requisitos e medidas de proteção para trabalho em altura, visando a segurança e saúde dos trabalhadores. Define responsabilidades para empregadores e trabalhadores, capacitação obrigatória, planejamento e execução adequados, além da utilização de Equipamentos de Proteção Individual (EPI). A norma também exige que todo trabalho em altura seja precedido de análise de risco e supervisão apropriada.
TRABALHO EM ALTURA - Treinamento (SENAI).ppt
TRABALHO EM ALTURA - Treinamento (SENAI).pptPalomaRibeirodeOlive O documento discute os procedimentos de segurança para trabalhos em altura de acordo com a NR-35, enfatizando a importância do uso correto de equipamentos de proteção individual, como capacetes e cintos de segurança, e a necessidade de pontos de ancoragem adequados e testados para suportar mais de 1500kg.
Atestado brigada
Atestado brigadacondmarenmaral Este documento é um atestado de treinamento de brigada de incêndio realizado em 13 de agosto de 2019 para funcionários de um prédio localizado em São Vicente, SP. Nele consta a lista de 24 pessoas que participaram com sucesso da capacitação de 4 horas sobre combate a incêndios e manuseio de equipamentos de segurança. O documento é assinado por um sargento do Corpo de Bombeiros que atesta o treinamento.
NR34 - TRABALHO A QUENTE.pptx
NR34 - TRABALHO A QUENTE.pptxDaniloMartinsdossant2 O documento discute os riscos e formas de prevenção da atividade com maçarico, abordando: 1) os riscos associados aos gases, equipamentos e instalações elétricas; 2) recomendações como inspeções prévias e cuidados com espaços confinados; 3) práticas de segurança como não usar oxigênio para limpeza e não conduzir com isqueiros.
APOSTILA TRABALHO ALTURA NR 35.pdf
APOSTILA TRABALHO ALTURA NR 35.pdfssuser22319e Este documento estabelece os requisitos mínimos e medidas de proteção para trabalho em altura, definindo como tal toda atividade acima de 2m do nível inferior com risco de queda. Ele aborda equipamentos de proteção individual, sistemas de ancoragem, planejamento e procedimentos de emergência para garantir a segurança dos trabalhadores.
01 c ce-–-andaime-fachadeiro-–-manual-de-montagem
01 c ce-–-andaime-fachadeiro-–-manual-de-montagemJanaina Xavier O documento fornece instruções sobre a montagem e desmontagem de andaimes fachadeiros da marca Tuper, descrevendo seus principais componentes, como quadros laterais, sapatas e plataformas. Inclui detalhes sobre a instalação correta de guarda-corpos simples e duplos de acordo com normas técnicas e fornece orientações gerais sobre segurança na montagem e inspeção dos equipamentos.
Laminacao powerpoint 3 d3b
Laminacao powerpoint 3 d3bMateushis O documento descreve o processo de laminação, incluindo sua história, tipos de laminadores, laminação a quente e a frio. Detalha os principais equipamentos como laminadores duo, trio e quadruo, assim como os processos de laminação a quente e a frio, incluindo suas vantagens e desvantagens. Apresenta também defeitos comuns na laminação e normas técnicas aplicadas.
Uso e Conservação EPIs NR6_2023.pptx
Uso e Conservação EPIs NR6_2023.pptxHailtonJose1 O documento resume os principais pontos da Norma Regulamentadora NR-6, que trata do treinamento em uso e conservação de Equipamentos de Proteção Individual (EPIs). A NR-6 estabelece as responsabilidades dos empregadores, empregados e fabricantes no fornecimento, uso e manutenção correta dos EPIs. Além disso, destaca os riscos do não uso ou uso indevido dos EPIs tanto para as empresas quanto para os trabalhadores.
NR12
NR12 Rafael Rocha O documento discute tipos de máquinas e equipamentos industriais como prensas, guilhotinas e dobradeiras. Ele descreve os principais tipos de prensas, como prensas de engate por chaveta, prensas hidráulicas e prensas mecânicas com freio pneumático, e destaca a necessidade de proteções de segurança nestas máquinas. O documento também menciona outros equipamentos como guilhotinas, dobradeiras e suas respectivas proteções de segurança.
Capacitação Brigada de Emergência
Capacitação Brigada de Emergência José Valfrido O documento aborda a capacitação da brigada de emergência, liderada por José Valfrido da Silva, e estabelece diretrizes de formação em diversas normas regulamentadoras, como NR-23 e NPT-16, enfatizando a importância da preparação para situações de incêndio. Ele detalha as funções dos membros da brigada, técnicas de combate ao incêndio, métodos de extinção e classes de incêndio, além de ressaltar a necessidade de um treinamento contínuo e regras de segurança. O documento também descreve os procedimentos para utilizar extintores e sistemas de hidrantes no combate a incêndios.
MODELO DE TREINAMENTO NR12 VOLTADO A FRENTES DE SERVIÇO EM OBRAS
MODELO DE TREINAMENTO NR12 VOLTADO A FRENTES DE SERVIÇO EM OBRASMateus Borges O documento discute treinamento em segurança no trabalho, com foco na Norma Regulamentadora NR-12. O objetivo do treinamento é capacitar colaboradores sobre segurança na operação de máquinas e equipamentos comuns em obras e grandes empreendimentos. A NR-12 estabelece requisitos mínimos de segurança para máquinas e equipamentos. Diversos equipamentos são descritos, com orientações sobre operação segura.
Apresentação nr 26 sinalização de segurança
Apresentação nr 26 sinalização de segurança João Vitor Rocha A norma NR-26 aborda a sinalização de segurança através de cores e emplacamentos. As cores têm objetivos específicos, como identificar equipamentos, delimitar áreas e advertir sobre riscos, enquanto os emplacamentos incluem sinais de proibição, obrigação, perigo, emergência e incêndio. A norma define cada cor e seu uso apropriado, destacando a importância da sinalização adequada para a segurança no ambiente de trabalho.
Trabalho em altura FI ENGENHARIA
Trabalho em altura FI ENGENHARIARenan Biscaglia O documento discute conceitos e medidas de segurança para trabalho em altura, definindo como tal qualquer atividade acima de 2m de altura com risco de queda. Apresenta riscos comuns como rompimento de telhados, equipamentos defeituosos e condições adversas, e responsabilidades de empregadores em treinar funcionários, fornecer EPI e realizar análises de risco.
Treinamento NR12 - Maquinas e Equipamentos Roçadeira Costal
Treinamento NR12 - Maquinas e Equipamentos Roçadeira Costalleonardocasoconsulto O documento fornece instruções sobre procedimentos de segurança para operar roçadeiras. Ele destaca a importância de usar equipamentos de proteção como óculos, luvas e protetores auriculares, e alerta sobre riscos de lesões por esforço repetitivo. O documento também aborda inspeção de lâminas, armazenamento seguro de combustível e precauções durante soldagens a quente.
TREINAMENTO NR-33 ESPACO CONFINADO.pptx
TREINAMENTO NR-33 ESPACO CONFINADO.pptxJoyceMarina2 O documento discute as normas de segurança e saúde para trabalhos em espaços confinados. Define o que são espaços confinados e onde eles podem ser encontrados. Detalha os riscos associados a trabalhar nesses espaços e as medidas de segurança que devem ser tomadas, incluindo testes do ar, equipamentos de proteção, treinamento dos trabalhadores e supervisão.
Nr 12 (anexo i)
Nr 12 (anexo i)JAIME NOVOA Este documento estabelece requisitos de segurança para máquinas e equipamentos, incluindo distâncias mínimas de segurança para impedir o acesso a zonas de perigo e requisitos para o uso de detectores de presença optoeletrônicos. Ele especifica como calcular distâncias de segurança usando barreiras físicas e detectores, e requisitos específicos para dobradeiras hidráulicas equipadas com detectores laser.
PT - Permissão de Trabalho - Trabalho em Altura
PT - Permissão de Trabalho - Trabalho em Alturaproftstsergioetm Este documento é uma permissão de trabalho em altura que requer detalhes sobre a localização, atividades, equipamentos de proteção individual, análise de riscos e autorização da supervisão para garantir a segurança da equipe durante o trabalho.
Coding standards for java
Coding standards for javamaheshm1206 This document provides an introduction to coding standards for Java. It discusses why coding standards are important for consistency, readability, and maintainability. It outlines the key components of a Java source file and comments. It also covers naming conventions, formatting, and best practices for variables, methods, classes, and comments. Finally, it introduces static code analysis tools like PMD and AppPerfect that can analyze Java code and enforce coding standards and best practices.
Coding standards and guidelines
Coding standards and guidelinesbrijraj_singh The document discusses coding standards and guidelines for developers to follow. It recommends limiting lines of code to 20 lines per function, writing comments before code, using PascalCase for class and method names and camelCase for variables, and giving functions, classes and variables meaningful names. Developers should not use single character variable names or underscores for local variables, and should prefix boolean variables with "is". Namespace names should follow a standard pattern of company, product, top and bottom level modules. Formatting and readability of code is also important. Future sessions will cover additional coding standards, tools to improve practices, and packaging programs.
More Related Content
What's hot (20)
Nbr 12962 inspecao manut. recarga de extintores (2)
Nbr 12962 inspecao manut. recarga de extintores (2)cristiano Santos Este documento estabelece as condições mínimas para a inspeção, manutenção e recarga de extintores de incêndio no Brasil. Ele define os níveis de manutenção recomendados, a frequência de inspeção, os procedimentos para recarga e os requisitos específicos para diferentes tipos de extintores.
11 proteção e combate a incêndio 05102005
11 proteção e combate a incêndio 05102005Shirlene Maciel Rafino O documento descreve conceitos básicos de fogo, seus elementos constituintes e métodos de combate e prevenção de incêndios. Aborda combustíveis, comburente, calor, propagação do fogo, classes de incêndio, métodos de extinção, extintores e agentes extintores.
Guia para analise de risco - NR 35
Guia para analise de risco - NR 35Fabiano Micaella O documento fornece diretrizes para análise de risco de trabalho em altura, incluindo dispositivos de proteção coletiva e equipamentos de proteção individual. Ele descreve sistemas de guarda-corpo, redes de segurança, escadas e rampas seguras, além de equipamentos como cinturão paraquedista e sistemas de retenção de queda.
NR 35 - Capacitação no trabalho em altura.pptx
NR 35 - Capacitação no trabalho em altura.pptxMelquiadesAlmeida2 A norma NR-35 estabelece requisitos e medidas de proteção para trabalho em altura, visando a segurança e saúde dos trabalhadores. Define responsabilidades para empregadores e trabalhadores, capacitação obrigatória, planejamento e execução adequados, além da utilização de Equipamentos de Proteção Individual (EPI). A norma também exige que todo trabalho em altura seja precedido de análise de risco e supervisão apropriada.
TRABALHO EM ALTURA - Treinamento (SENAI).ppt
TRABALHO EM ALTURA - Treinamento (SENAI).pptPalomaRibeirodeOlive O documento discute os procedimentos de segurança para trabalhos em altura de acordo com a NR-35, enfatizando a importância do uso correto de equipamentos de proteção individual, como capacetes e cintos de segurança, e a necessidade de pontos de ancoragem adequados e testados para suportar mais de 1500kg.
Atestado brigada
Atestado brigadacondmarenmaral Este documento é um atestado de treinamento de brigada de incêndio realizado em 13 de agosto de 2019 para funcionários de um prédio localizado em São Vicente, SP. Nele consta a lista de 24 pessoas que participaram com sucesso da capacitação de 4 horas sobre combate a incêndios e manuseio de equipamentos de segurança. O documento é assinado por um sargento do Corpo de Bombeiros que atesta o treinamento.
NR34 - TRABALHO A QUENTE.pptx
NR34 - TRABALHO A QUENTE.pptxDaniloMartinsdossant2 O documento discute os riscos e formas de prevenção da atividade com maçarico, abordando: 1) os riscos associados aos gases, equipamentos e instalações elétricas; 2) recomendações como inspeções prévias e cuidados com espaços confinados; 3) práticas de segurança como não usar oxigênio para limpeza e não conduzir com isqueiros.
APOSTILA TRABALHO ALTURA NR 35.pdf
APOSTILA TRABALHO ALTURA NR 35.pdfssuser22319e Este documento estabelece os requisitos mínimos e medidas de proteção para trabalho em altura, definindo como tal toda atividade acima de 2m do nível inferior com risco de queda. Ele aborda equipamentos de proteção individual, sistemas de ancoragem, planejamento e procedimentos de emergência para garantir a segurança dos trabalhadores.
01 c ce-–-andaime-fachadeiro-–-manual-de-montagem
01 c ce-–-andaime-fachadeiro-–-manual-de-montagemJanaina Xavier O documento fornece instruções sobre a montagem e desmontagem de andaimes fachadeiros da marca Tuper, descrevendo seus principais componentes, como quadros laterais, sapatas e plataformas. Inclui detalhes sobre a instalação correta de guarda-corpos simples e duplos de acordo com normas técnicas e fornece orientações gerais sobre segurança na montagem e inspeção dos equipamentos.
Laminacao powerpoint 3 d3b
Laminacao powerpoint 3 d3bMateushis O documento descreve o processo de laminação, incluindo sua história, tipos de laminadores, laminação a quente e a frio. Detalha os principais equipamentos como laminadores duo, trio e quadruo, assim como os processos de laminação a quente e a frio, incluindo suas vantagens e desvantagens. Apresenta também defeitos comuns na laminação e normas técnicas aplicadas.
Uso e Conservação EPIs NR6_2023.pptx
Uso e Conservação EPIs NR6_2023.pptxHailtonJose1 O documento resume os principais pontos da Norma Regulamentadora NR-6, que trata do treinamento em uso e conservação de Equipamentos de Proteção Individual (EPIs). A NR-6 estabelece as responsabilidades dos empregadores, empregados e fabricantes no fornecimento, uso e manutenção correta dos EPIs. Além disso, destaca os riscos do não uso ou uso indevido dos EPIs tanto para as empresas quanto para os trabalhadores.
NR12
NR12 Rafael Rocha O documento discute tipos de máquinas e equipamentos industriais como prensas, guilhotinas e dobradeiras. Ele descreve os principais tipos de prensas, como prensas de engate por chaveta, prensas hidráulicas e prensas mecânicas com freio pneumático, e destaca a necessidade de proteções de segurança nestas máquinas. O documento também menciona outros equipamentos como guilhotinas, dobradeiras e suas respectivas proteções de segurança.
Capacitação Brigada de Emergência
Capacitação Brigada de Emergência José Valfrido O documento aborda a capacitação da brigada de emergência, liderada por José Valfrido da Silva, e estabelece diretrizes de formação em diversas normas regulamentadoras, como NR-23 e NPT-16, enfatizando a importância da preparação para situações de incêndio. Ele detalha as funções dos membros da brigada, técnicas de combate ao incêndio, métodos de extinção e classes de incêndio, além de ressaltar a necessidade de um treinamento contínuo e regras de segurança. O documento também descreve os procedimentos para utilizar extintores e sistemas de hidrantes no combate a incêndios.
MODELO DE TREINAMENTO NR12 VOLTADO A FRENTES DE SERVIÇO EM OBRAS
MODELO DE TREINAMENTO NR12 VOLTADO A FRENTES DE SERVIÇO EM OBRASMateus Borges O documento discute treinamento em segurança no trabalho, com foco na Norma Regulamentadora NR-12. O objetivo do treinamento é capacitar colaboradores sobre segurança na operação de máquinas e equipamentos comuns em obras e grandes empreendimentos. A NR-12 estabelece requisitos mínimos de segurança para máquinas e equipamentos. Diversos equipamentos são descritos, com orientações sobre operação segura.
Apresentação nr 26 sinalização de segurança
Apresentação nr 26 sinalização de segurança João Vitor Rocha A norma NR-26 aborda a sinalização de segurança através de cores e emplacamentos. As cores têm objetivos específicos, como identificar equipamentos, delimitar áreas e advertir sobre riscos, enquanto os emplacamentos incluem sinais de proibição, obrigação, perigo, emergência e incêndio. A norma define cada cor e seu uso apropriado, destacando a importância da sinalização adequada para a segurança no ambiente de trabalho.
Trabalho em altura FI ENGENHARIA
Trabalho em altura FI ENGENHARIARenan Biscaglia O documento discute conceitos e medidas de segurança para trabalho em altura, definindo como tal qualquer atividade acima de 2m de altura com risco de queda. Apresenta riscos comuns como rompimento de telhados, equipamentos defeituosos e condições adversas, e responsabilidades de empregadores em treinar funcionários, fornecer EPI e realizar análises de risco.
Treinamento NR12 - Maquinas e Equipamentos Roçadeira Costal
Treinamento NR12 - Maquinas e Equipamentos Roçadeira Costalleonardocasoconsulto O documento fornece instruções sobre procedimentos de segurança para operar roçadeiras. Ele destaca a importância de usar equipamentos de proteção como óculos, luvas e protetores auriculares, e alerta sobre riscos de lesões por esforço repetitivo. O documento também aborda inspeção de lâminas, armazenamento seguro de combustível e precauções durante soldagens a quente.
TREINAMENTO NR-33 ESPACO CONFINADO.pptx
TREINAMENTO NR-33 ESPACO CONFINADO.pptxJoyceMarina2 O documento discute as normas de segurança e saúde para trabalhos em espaços confinados. Define o que são espaços confinados e onde eles podem ser encontrados. Detalha os riscos associados a trabalhar nesses espaços e as medidas de segurança que devem ser tomadas, incluindo testes do ar, equipamentos de proteção, treinamento dos trabalhadores e supervisão.
Nr 12 (anexo i)
Nr 12 (anexo i)JAIME NOVOA Este documento estabelece requisitos de segurança para máquinas e equipamentos, incluindo distâncias mínimas de segurança para impedir o acesso a zonas de perigo e requisitos para o uso de detectores de presença optoeletrônicos. Ele especifica como calcular distâncias de segurança usando barreiras físicas e detectores, e requisitos específicos para dobradeiras hidráulicas equipadas com detectores laser.
PT - Permissão de Trabalho - Trabalho em Altura
PT - Permissão de Trabalho - Trabalho em Alturaproftstsergioetm Este documento é uma permissão de trabalho em altura que requer detalhes sobre a localização, atividades, equipamentos de proteção individual, análise de riscos e autorização da supervisão para garantir a segurança da equipe durante o trabalho.
Viewers also liked (20)
Coding standards for java
Coding standards for javamaheshm1206 This document provides an introduction to coding standards for Java. It discusses why coding standards are important for consistency, readability, and maintainability. It outlines the key components of a Java source file and comments. It also covers naming conventions, formatting, and best practices for variables, methods, classes, and comments. Finally, it introduces static code analysis tools like PMD and AppPerfect that can analyze Java code and enforce coding standards and best practices.
Coding standards and guidelines
Coding standards and guidelinesbrijraj_singh The document discusses coding standards and guidelines for developers to follow. It recommends limiting lines of code to 20 lines per function, writing comments before code, using PascalCase for class and method names and camelCase for variables, and giving functions, classes and variables meaningful names. Developers should not use single character variable names or underscores for local variables, and should prefix boolean variables with "is". Namespace names should follow a standard pattern of company, product, top and bottom level modules. Formatting and readability of code is also important. Future sessions will cover additional coding standards, tools to improve practices, and packaging programs.
Standards For Java Coding
Standards For Java CodingRahul Bhutkar This document outlines coding style guidelines for various aspects of Ruby code including indentation, whitespace, naming conventions, comments, and other stylistic elements. It discusses formatting recommendations for indentation, line lengths, alignment, blank lines and spaces, trailing whitespace, declarations, dead code, and use of parentheses. It also provides tips for commit messages, and style guidelines for models, views, and controllers in Ruby on Rails. The document is intended as a reference for writing clean, readable Ruby code.
12 multi-threading
12 multi-threadingAPU This document introduces multi-threading in Java. It discusses that threads allow a program to have multiple paths of execution. Threads can be created by extending the Thread class or implementing the Runnable interface. The key method for threads is run, which contains the logic to be executed. The document covers starting threads, potential problems with threads accessing shared resources, and techniques for thread synchronization like synchronized methods, waits and notifies.
Alternate concurrency models
Alternate concurrency modelsAbid Khan This document discusses alternate concurrency models including the actor model and software transactional memory (STM). It provides overviews of common problems with multi-threading like atomicity, visibility and race conditions. The actor model is described as involving autonomous units that communicate asynchronously via message passing without shared state. STM is analogous to database transactions for controlling concurrency in shared memory through atomic reads and writes. Examples of actor model applications and STM implementations in Java are also mentioned.
Developer Friendly API Design
Developer Friendly API Designtheamiableapi The document discusses best practices for API design. It covers topics such as considering the perspective of the caller, keeping APIs simple, striving for consistency, choosing memorable names, specifying behavior, making APIs safe, anticipating evolution, and writing helpful documentation. The overall message is that API design has a significant impact and requires careful consideration to create interfaces that are intuitive, easy to use, and stand the test of time.
Multi threading
Multi threadingMavoori Soshmitha This document discusses multi-threaded programming in Java. It covers key concepts like synchronized blocks, static synchronization, deadlocks, inter-thread communication, thread states (new, runnable, running, non-runnable, terminated), creating threads by extending Thread class and implementing Runnable interface, starting threads using start() vs calling run() directly, joining threads, naming threads, setting thread priority, and using methods like sleep(), yield(), currentThread() etc. It provides examples to explain these concepts.
null Bachaav Session | Secure Coding in Java
null Bachaav Session | Secure Coding in Javan|u - The Open Security Community The document discusses various techniques for writing secure Java code. It covers topics like ensuring classes are final by default to prevent breaking invariants, declaring data members as private and providing accessible wrapper methods, not using public static nonfinal variables, being wary of constructors that throw exceptions, not signing code that only performs unprivileged operations, placing all security sensitive code in a single signed JAR file, not trusting environment variable values, avoiding granting dangerous permission combinations, not disabling bytecode verification, and not deploying remotely monitorable applications.
Standards For Java Coding
Standards For Java CodingRahul Bhutkar This document provides a Java coding standard for code structure, documentation, naming conventions, and recommendations. It outlines how to structure packages, program files, classes, methods, and code layout. It provides conventions for naming packages, files, classes, variables, methods and other identifiers. It gives recommendations for classes, exception handling, variables, methods, technical points and applying common sense. Code examples are provided to demonstrate the conventions.
(Ebook resume) job interview - 101 dynamite answers to interview questions ...
(Ebook resume) job interview - 101 dynamite answers to interview questions ...Farahaa Based on your responses, here are a few things you can focus on to better nail the interview:
- Practice answering common questions like "Tell me about yourself" so you have clear, concise responses prepared. Have specific examples from your background to draw from.
- Research the company and position thoroughly so you understand what skills and experience they are looking for. Connect your background to their needs.
- Anticipate questions that may be asked and have well-thought out, positive responses prepared. Practice your delivery.
- Ask insightful questions yourself to demonstrate your interest and qualifications for the role. Follow up after the interview as well.
Preparing thoroughly, anticipating questions, connecting your background to their needs
Java best practices
Java best practicesRay Toal This document provides an overview of best practices for writing Java code. It discusses topics like immutability, using libraries like Guava and Joda-Time, avoiding nulls, closing resources properly, using prepared statements to prevent SQL injection, and many other practices. The document emphasizes writing code that is readable, maintainable, efficient and avoids common pitfalls. It also provides resources for tools that can analyze code and help identify areas that don't follow best practices.
Concurrency and Multithreading Demistified - Reversim Summit 2014
Concurrency and Multithreading Demistified - Reversim Summit 2014Haim Yadid The document discusses concurrency and multi-threading concepts in software development, emphasizing the importance of architecture over coding in handling parallel tasks. It covers various challenges such as deadlock, data races, and state management, while providing examples in Java and Go. The presentation also touches on immutability and its benefits in avoiding concurrency issues, alongside techniques like Software Transactional Memory (STM).
Inner Classes & Multi Threading in JAVA
Inner Classes & Multi Threading in JAVATech_MX The document discusses inner classes, static classes, and multithreading in Java. It defines inner classes as classes defined within other classes. There are four types of inner classes: non-static, static, local, and anonymous. Static inner classes are similar to top-level classes but are declared within another class. They can be accessed without creating an instance of the outer class. Multithreading allows multiple parts of a program to run concurrently by using threads.
Data Structures- Part7 linked lists
Data Structures- Part7 linked listsAbdullah Al-hazmy The document discusses different types of linked lists including singly linked lists, doubly linked lists, and circularly linked lists. Singly linked lists contain nodes that point to the next node in the list, while doubly linked lists contain nodes that point to both the next and previous nodes. Circularly linked lists form a circle with the last node pointing back to the first node. The document provides code examples for common linked list operations like insertion, removal and traversal for each of the linked list types.
Advanced Introduction to Java Multi-Threading - Full (chok)
Advanced Introduction to Java Multi-Threading - Full (chok)choksheak The document is an advanced introduction to Java multi-threading, aimed at developers of all skill levels, detailing the Java Memory Model (JMM) and concurrent utilities. It explains critical concepts like visibility, ordering, and atomicity in thread interactions, along with practical examples of multi-threading issues. Additionally, it covers available tools in the java.util.concurrent package, including lock objects, executors, and concurrent collections, to assist in writing efficient multi-threaded code.
Java Performance, Threading and Concurrent Data Structures
Java Performance, Threading and Concurrent Data StructuresHitendra Kumar The document discusses Java performance and threading. It provides an overview of performance concepts, the performance process, and measurement techniques like benchmarking and profiling. It also covers key threading concepts like thread states, synchronization, and how to share data across threads using synchronized methods, objects, and wait/notify.
Data Structures- Part5 recursion
Data Structures- Part5 recursionAbdullah Al-hazmy The document discusses recursion, including:
1) Recursion involves breaking a problem down into smaller subproblems until a base case is reached, then building up the solution to the overall problem from the solutions to the subproblems.
2) A recursive function is one that calls itself, with each call typically moving closer to a base case where the problem can be solved without recursion.
3) Recursion can be linear, involving one recursive call, or binary, involving two recursive calls to solve similar subproblems.
Best Practices of Software Development
Best Practices of Software DevelopmentFolio3 Software Folio3 is a software development company that focuses on designing custom enterprise, mobile, and social media applications. They have over 200 employees across offices in the US, Canada, Bulgaria, and Pakistan. The document outlines Folio3's areas of expertise and best practices for software development and databases, including using consistent naming conventions, short methods, clear comments, specific exceptions, and avoiding wildcard queries.
Top 10 Java Interview Questions and Answers 2014
Top 10 Java Interview Questions and Answers 2014 iimjobs and hirist The document presents the top 10 Java interview questions and answers as cited from hirist.com, addressing key Java concepts such as the Java Virtual Machine (JVM), differences between JDK and JRE, and the nature of immutable objects. It also covers Java data types, autoboxing and unboxing, function overriding and overloading, and differences between ArrayList and LinkedList. Additional topics include using SimpleDateFormat and the distinctions between CyclicBarrier and CountDownLatch.
Standard java coding convention
Standard java coding conventionTam Thanh This document provides coding standards and conventions for Java programming. It covers topics such as program structure, file organization, indentation, comments, declarations, statements, naming conventions, and programming practices. The goal is to improve code readability, understandability, and maintainability. Projects may customize the standards as needed based on customer requirements.
Ad
Similar to Best Coding Practices in Java and C++ (20)
76829060 java-coding-conventions
76829060 java-coding-conventionsslavicp This document provides coding standards and guidelines for writing clean, readable, and maintainable Java code. It outlines standards for naming conventions, documentation, member functions, fields, and other elements. The goal is to promote consistency and best practices to improve productivity, maintainability, and scalability. Key aspects include using descriptive names, commenting code clearly, and encapsulating fields with accessors.
Clean code
Clean codeAlvaro García Loaisa The document outlines principles of clean code as articulated by Robert C. Martin, emphasizing the importance of clear names, small functions, and effective error handling. It insists that code should be simple, direct, and elegantly written, highlighting that meaningful names and a commitment to high-quality code are essential for better programming. Additionally, the document discusses the impact of code quality on productivity and the necessity of refactoring poor code instead of commenting on it.
What's in a name
What's in a nameKoby Fruchtnis The document discusses best practices for naming variables, functions, classes and other code elements. It recommends using intention-revealing names that are pronounceable, searchable and avoid encodings or abbreviations. Names should clearly convey what each element represents without need for comments. Context and consistency in naming conventions helps readers understand the code more easily. Overall, taking time to thoughtfully name elements improves code quality, readability and maintainability.
Writing Good Code
Writing Good CodeLeo Liang This document discusses principles and best practices for writing good code, including:
1. Code should be simple, clean, readable, maintainable, testable, secure, and extensible.
2. Code style is important for readability and maintainability, though performance depends more on design.
3. Guidelines help improve readability, eliminate bugs, and unify conventions within a team.
Coding standards
Coding standardsMimoh Ojha The document discusses the importance of writing 'good code' that is reliable, maintainable, and efficient, emphasizing the need for coding standards and conventions to reduce software maintenance costs. It outlines characteristics of good code, standard practices for file organization, naming conventions, and the significance of code reviews. Additionally, it provides specific guidelines and principles to enhance code readability and maintainability, arguing that effective coding practices contribute to long-term success in software development.
Clean Code
Clean CodeChris Farrell The document discusses principles for writing clean code, including:
- Functions should do one thing and be small, with descriptive names.
- Code should be organized in a way that reads like well-written prose from top-level functions down.
- Comments are usually a code smell and cleaning up code is preferable to adding comments.
- Overall the goal is for code to be easy to read and understand at a glance.
UNIT I cloud computing ppt cloud ccd all about the cloud computing
UNIT I cloud computing ppt cloud ccd all about the cloud computingvishnubala78900 It is about the cloud computing ppt and it is very useful to cloud computing
Clean code
Clean codeUday Pratap Singh The document discusses the principles of clean code, emphasizing readability, maintainability, and meaningful naming conventions. It highlights the importance of writing code that is concise, understandable, and free from duplication, using clear naming for variables and functions. Additionally, it cautions against writing bad code due to haste or external pressures and provides detailed rules for function design and structure.
Crafting high quality code
Crafting high quality code Allan Mangune The document provides guidance on writing high-quality code and functions. It recommends that functions should have a single well-described purpose, use meaningful naming conventions, limit their size and number of parameters, and handle errors. It also emphasizes the importance of testing code through test cases to ensure it works as intended.
Clean code
Clean codeHenrique Smoco This document discusses principles and best practices for writing clean code. It defines clean code as code that works, is easy to read, understand and extend. It emphasizes writing code for other developers who will maintain it. Some key points include writing small, focused methods with meaningful names; avoiding duplicated code; using exceptions appropriately; formatting code consistently; and writing thorough automated tests. The overall goal is to communicate intent in the code as clearly as possible through these practices.
Naming guidelines for professional programmers
Naming guidelines for professional programmersPeter Hilton The document outlines comprehensive naming guidelines for professional programmers, emphasizing the importance of naming in code clarity, maintainability, and bug prevention. It includes detailed suggestions, such as using descriptive names, adhering to programming conventions, and avoiding ambiguous or overly complex identifiers. Additionally, it poses research questions regarding the impact of naming on code quality and maintainability.
Perfect Code
Perfect CodeArtem Tabalin The document discusses principles and best practices for writing high-quality code, including keeping code simple, avoiding duplication, using object-oriented design principles like SOLID, giving variables and methods meaningful names, properly structuring classes, methods and variables, and applying principles of encapsulation and inheritance. It emphasizes that code quality is important to reduce development costs and improve productivity.
Variables
VariablesMaha Saad The document discusses best practices for naming variables. It recommends initializing variables as they are declared, giving variables descriptive names to indicate their purpose, and adopting naming conventions to make code more consistent and readable for multiple programmers. Standardized prefixes and abbreviations can make long names more compact while retaining clarity. Overall, the goal is to use variable names that are meaningful, unambiguous, and help convey the essential logic of the code at a glance.
Android course session 3 ( OOP ) part 1
Android course session 3 ( OOP ) part 1Keroles M.Yakoub The document outlines an Android course using Java, covering key concepts such as exceptions, classes and objects, naming conventions, access modifiers, and encapsulation. It explains exception handling with 'try...catch...finally' blocks, how to define classes and methods, and the importance of proper naming conventions for code readability. Additionally, it details access and non-access modifiers along with encapsulation principles to manage access to class members.
Coding Standards & Best Practices for iOS/C#
Coding Standards & Best Practices for iOS/C#Asim Rais Siddiqui The document provides guidelines for coding standards and best practices to develop reliable and maintainable applications. It discusses topics like naming conventions, indentation and spacing, commenting code, avoiding bugs, and organizing code logically. The goal is to outline a standard approach for an entire team to follow to make the code easy to understand, modify and prevent errors. Key recommendations include using meaningful names, consistent indentation, separating concerns in methods, adding descriptive comments, handling errors gracefully and using source control.
clean code book summary - uncle bob - English version
clean code book summary - uncle bob - English versionsaber tabatabaee The document provides guidance on writing clean code based on the book "Clean Code" by Robert Cecil Martin. Some of the key points discussed include:
- Functions should do one thing and do it well, with a single level of abstraction and no side effects. They should fit on a screen.
- Names should be meaningful, avoid abbreviations, and use consistent vocabulary. Class names should be nouns and method names should be verbs.
- Code formatting is important for readability. Classes should not exceed 200 lines, functions a single screen. Variables should be declared near use.
- Comments should only explain why unusual decisions were made, not what the code does. Avoid commented out code or redundant comments
Lecture No 13.ppt
Lecture No 13.pptAhmadNaeem59 The document discusses guidelines for writing maintainable and self-documenting code. It emphasizes that code should be simple, clear, and flexible to be easy to understand and modify. Self-documenting code can be achieved through use of descriptive names, consistent style, and limiting function size. The document also provides specific naming conventions for variables, methods, and other programming elements in languages like Java and C++.
Clean code - DSC DYPCOE
Clean code - DSC DYPCOEPatil Shreyas The document discusses the principles of writing clean code, emphasizing readability, maintainability, and proper naming conventions. It introduces the S.O.L.I.D. principles for object-oriented design and provides guidelines for naming variables, functions, and classes effectively. Additionally, it highlights the importance of error handling, comments, and code refactoring to improve code quality.
Writing High Quality Code in C#
Writing High Quality Code in C#Svetlin Nakov The document outlines principles for writing high-quality programming code, focusing on aspects such as naming conventions, code formatting, and the importance of self-documenting code. It emphasizes that good code should be easy to read, modify, and maintain, while also conforming to established coding standards. Detailed guidelines on naming identifiers, methods, and variables are provided to promote clarity and consistency in code development.
R. herves. clean code (theme)2
R. herves. clean code (theme)2saber tabatabaee This document discusses principles of writing clean code for readability and maintainability. It defines clean code as code that is simple, direct and reads like well-written prose. Clean code should have meaningful names, small and focused functions, minimal comments, and use exceptions for error handling rather than return codes. Classes should also have a single well-described responsibility and follow the single responsibility principle. Overall, writing clean code produces benefits during development and makes the code easier to maintain going forward.
Ad
Recently uploaded (20)
Techniques for Automatic Device Identification and Network Assignment.pdf
Techniques for Automatic Device Identification and Network Assignment.pdfPriyanka Aash Techniques for Automatic Device Identification and Network Assignment
“MPU+: A Transformative Solution for Next-Gen AI at the Edge,” a Presentation...
“MPU+: A Transformative Solution for Next-Gen AI at the Edge,” a Presentation...Edge AI and Vision Alliance For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2025/06/mpu-a-transformative-solution-for-next-gen-ai-at-the-edge-a-presentation-from-fotonation/
Petronel Bigioi, CEO of FotoNation, presents the “MPU+: A Transformative Solution for Next-Gen AI at the Edge” tutorial at the May 2025 Embedded Vision Summit.
In this talk, Bigioi introduces MPU+, a novel programmable, customizable low-power platform for real-time, localized intelligence at the edge. The platform includes an AI-augmented image signal processor that enables leading image and video quality.
In addition, it integrates ultra-low-power object and motion detection capabilities to enable always-on computer vision. A programmable neural processor provides flexibility to efficiently implement new neural networks. And additional specialized engines facilitate image stabilization and audio enhancements.
From Manual to Auto Searching- FME in the Driver's Seat
From Manual to Auto Searching- FME in the Driver's SeatSafe Software Finding a specific car online can be a time-consuming task, especially when checking multiple dealer websites. A few years ago, I faced this exact problem while searching for a particular vehicle in New Zealand. The local classified platform, Trade Me (similar to eBay), wasn’t yielding any results, so I expanded my search to second-hand dealer sites—only to realise that periodically checking each one was going to be tedious. That’s when I noticed something interesting: many of these websites used the same platform to manage their inventories. Recognising this, I reverse-engineered the platform’s structure and built an FME workspace that automated the search process for me. By integrating API calls and setting up periodic checks, I received real-time email alerts when matching cars were listed. In this presentation, I’ll walk through how I used FME to save hours of manual searching by creating a custom car-finding automation system. While FME can’t buy a car for you—yet—it can certainly help you find the one you’re after!
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...Fwdays We will explore how e-commerce projects prepare for the busiest time of the year, which key aspects to focus on, and what to expect. We’ll share our experience in setting up auto-scaling, load balancing, and discuss the loads that Silpo handles, as well as the solutions that help us navigate this season without failures.
Agentic AI for Developers and Data Scientists Build an AI Agent in 10 Lines o...
Agentic AI for Developers and Data Scientists Build an AI Agent in 10 Lines o...All Things Open Presented at All Things Open RTP Meetup
Presented by William Hill - Developer Advocate, NVIDIA
Title: Agentic AI for Developers and Data Scientists
Build an AI Agent in 10 Lines of Code and the Concepts Behind the Code
Abstract: In this talk we will demonstrate building a working data science AI agent in 10 lines of basic Python code in a Colab notebook. Our AI Agent will perform LLM prompt-driven visual analysis using open-source libraries. In this session we will show how to develop an AI Agent using GPUs through NVIDIA’s developer program and Google Colab notebooks. After coding our AI Agent, we will break down the 10 lines of code. We will show the key components and open source library integrations that enable the agent's functionality, focusing on practical implementation details and then the theoretical concepts. The presentation concludes with a survey of current LLM technologies and the latest trends in developing AI applications for enthusiasts and enterprises
AI vs Human Writing: Can You Tell the Difference?
AI vs Human Writing: Can You Tell the Difference?Shashi Sathyanarayana, Ph.D This slide illustrates a side-by-side comparison between human-written, AI-written, and ambiguous content. It highlights subtle cues that help readers assess authenticity, raising essential questions about the future of communication, trust, and thought leadership in the age of generative AI.
OpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.
Database Benchmarking for Performance Masterclass: Session 2 - Data Modeling ...
Database Benchmarking for Performance Masterclass: Session 2 - Data Modeling ...ScyllaDB Specific best practices and pitfalls for benchmarking popular high-performance databases.
WebdriverIO & JavaScript: The Perfect Duo for Web Automation
WebdriverIO & JavaScript: The Perfect Duo for Web Automationdigitaljignect In today’s dynamic digital landscape, ensuring the quality and dependability of web applications is essential. While Selenium has been a longstanding solution for automating browser tasks, the integration of WebdriverIO (WDIO) with Selenium and JavaScript marks a significant advancement in automation testing. WDIO enhances the testing process by offering a robust interface that improves test creation, execution, and management. This amalgamation capitalizes on the strengths of both tools, leveraging Selenium’s broad browser support and WDIO’s modern, efficient approach to test automation. As automation testing becomes increasingly vital for faster development cycles and superior software releases, WDIO emerges as a versatile framework, particularly potent when paired with JavaScript, making it a preferred choice for contemporary testing teams.
10 Key Challenges for AI within the EU Data Protection Framework.pdf
10 Key Challenges for AI within the EU Data Protection Framework.pdfPriyanka Aash 10 Key Challenges for AI within the EU Data Protection Framework
Tech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdf
Tech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdfcaoyixuan2019 A presentation at Internetware 2025.
Securing Account Lifecycles in the Age of Deepfakes.pptx
Securing Account Lifecycles in the Age of Deepfakes.pptxFIDO Alliance Securing Account Lifecycles in the Age of Deepfakes
Security Tips for Enterprise Azure Solutions
Security Tips for Enterprise Azure SolutionsMichele Leroux Bustamante Delivering solutions to Azure may involve a variety of architecture patterns involving your applications, APIs data and associated Azure resources that comprise the solution. This session will use reference architectures to illustrate the security considerations to protect your Azure resources and data, how to achieve Zero Trust, and why it matters. Topics covered will include specific security recommendations for types Azure resources and related network security practices. The goal is to give you a breadth of understanding as to typical security requirements to meet compliance and security controls in an enterprise solution.
Cracking the Code - Unveiling Synergies Between Open Source Security and AI.pdf
Cracking the Code - Unveiling Synergies Between Open Source Security and AI.pdfPriyanka Aash Cracking the Code - Unveiling Synergies Between Open Source Security and AI
The Future of Product Management in AI ERA.pdf
The Future of Product Management in AI ERA.pdfAlyona Owens Hi, I’m Aly Owens, I have a special pleasure to stand here as over a decade ago I graduated from CityU as an international student with an MBA program. I enjoyed the diversity of the school, ability to work and study, the network that came with being here, and of course the price tag for students here has always been more affordable than most around.
Since then I have worked for major corporations like T-Mobile and Microsoft and many more, and I have founded a startup. I've also been teaching product management to ensure my students save time and money to get to the same level as me faster avoiding popular mistakes. Today as I’ve transitioned to teaching and focusing on the startup, I hear everybody being concerned about Ai stealing their jobs… We’ll talk about it shortly.
But before that, I want to take you back to 1997. One of my favorite movies is “Fifth Element”. It wowed me with futuristic predictions when I was a kid and I’m impressed by the number of these predictions that have already come true. Self-driving cars, video calls and smart TV, personalized ads and identity scanning. Sci-fi movies and books gave us many ideas and some are being implemented as we speak. But we often get ahead of ourselves:
Flying cars,Colonized planets, Human-like AI: not yet, Time travel, Mind-machine neural interfaces for everyone: Only in experimental stages (e.g. Neuralink).
Cyberpunk dystopias: Some vibes (neon signs + inequality + surveillance), but not total dystopia (thankfully).
On the bright side, we predict that the working hours should drop as Ai becomes our helper and there shouldn’t be a need to work 8 hours/day. Nobody knows for sure but we can require that from legislation. Instead of waiting to see what the government and billionaires come up with, I say we should design our own future.
So, we as humans, when we don’t know something - fear takes over. The same thing happened during the industrial revolution. In the Industrial Era, machines didn’t steal jobs—they transformed them but people were scared about their jobs. The AI era is making similar changes except it feels like robots will take the center stage instead of a human. First off, even when it comes to the hottest space in the military - drones, Ai does a fraction of work. AI algorithms enable real-time decision-making, obstacle avoidance, and mission optimization making drones far more autonomous and capable than traditional remote-controlled aircraft. Key technologies include computer vision for object detection, GPS-enhanced navigation, and neural networks for learning and adaptation. But guess what? There are only 2 companies right now that utilize Ai in drones to make autonomous decisions - Skydio and DJI.
Curietech AI in action - Accelerate MuleSoft development
Curietech AI in action - Accelerate MuleSoft developmentshyamraj55 CurieTech AI in Action – Accelerate MuleSoft Development
Overview:
This presentation demonstrates how CurieTech AI’s purpose-built agents empower MuleSoft developers to create integration workflows faster, more accurately, and with less manual effort
linkedin.com
+12
curietech.ai
+12
meetups.mulesoft.com
+12
.
Key Highlights:
Dedicated AI agents for every stage: Coding, Testing (MUnit), Documentation, Code Review, and Migration
curietech.ai
+7
curietech.ai
+7
medium.com
+7
DataWeave automation: Generate mappings from tables or samples—95%+ complete within minutes
linkedin.com
+7
curietech.ai
+7
medium.com
+7
Integration flow generation: Auto-create Mule flows based on specifications—speeds up boilerplate development
curietech.ai
+1
medium.com
+1
Efficient code reviews: Gain intelligent feedback on flows, patterns, and error handling
youtube.com
+8
curietech.ai
+8
curietech.ai
+8
Test & documentation automation: Auto-generate MUnit test cases, sample data, and detailed docs from code
curietech.ai
+5
curietech.ai
+5
medium.com
+5
Why Now?
Achieve 10× productivity gains, slashing development time from hours to minutes
curietech.ai
+3
curietech.ai
+3
medium.com
+3
Maintain high accuracy with code quality matching or exceeding manual efforts
curietech.ai
+2
curietech.ai
+2
curietech.ai
+2
Ideal for developers, architects, and teams wanting to scale MuleSoft projects with AI efficiency
Conclusion:
CurieTech AI transforms MuleSoft development into an AI-accelerated workflow—letting you focus on innovation, not repetition.
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdf
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdfPriyanka Aash GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdf
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdfEarley Information Science As AI reshapes expectations in retail and B2B commerce, organizations are recognizing a critical reality: meaningful AI outcomes depend on well-structured, adaptable infrastructure. In this session, Seth Earley is joined by Phil Ryan - AI strategist, search technologist, and founder of Glass Leopard Technologies - for a candid conversation on what it truly means to engineer systems for scale, agility, and intelligence.
Phil draws on more than two decades of experience leading search and AI initiatives for enterprise organizations. Together, he and Seth explore the challenges businesses face when legacy architectures limit personalization, agility, and real-time decisioning - and what needs to change to support agentic technologies and next-best-action capabilities.
Key themes from the webinar include:
Composability as a prerequisite for AI - Why modular, loosely coupled systems are essential for adapting to rapid innovation and evolving business needs
Search and relevance as foundational to AI - How techniques honed-in enterprise search have laid the groundwork for more responsive and intelligent customer experiences
From MDM and CDP to agentic systems - How data platforms are evolving to support richer customer context and dynamic orchestration
Engineering for business alignment - Why successful AI programs require architectural decisions grounded in measurable outcomes
The conversation is practical and forward-looking, connecting deep technical understanding with real-world business needs. Whether you’re modernizing your commerce stack or exploring how AI can enhance product discovery, personalization, or customer journeys, this session provides a clear-eyed view of the capabilities, constraints, and priorities that matter most.
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdf
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdfPriyanka Aash A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy
Coordinated Disclosure for ML - What's Different and What's the Same.pdf
Coordinated Disclosure for ML - What's Different and What's the Same.pdfPriyanka Aash Coordinated Disclosure for ML - What's Different and What's the Same
“MPU+: A Transformative Solution for Next-Gen AI at the Edge,” a Presentation...
“MPU+: A Transformative Solution for Next-Gen AI at the Edge,” a Presentation...Edge AI and Vision Alliance
Best Coding Practices in Java and C++
- 2. • Guidelines regarding naming conventions: • Standards for naming variables. • Standards for naming member functions. • Standards for local variables. • Standards for naming method arguments. • Standards for classes, interfaces and packages. • Guidelines related to code documentation, comments and indentation. • Common coding errors (C++) and how to avoid them. • General security loopholes in code and tips to avoid them. • Some best coding practices to follow in java.
- 3. Standards for naming variables: • Use full English descriptors that accurately describe the variable/field/class/interface, for example: • use names like firstName, grandTotal, or CorporateCustomer. • Use terminology applicable to the domain like If the users of the system refer to their clients as Customer, then use the term Customer for the class, not client. • Use mixed case to make names readable. • Use abbreviations sparingly, but if you do so then use then intelligently and document it, for example: • to use a short form for the word “number”, choose one of nbr, no or num. • Avoid long names (<15 characters is a good tradeoff). • Avoid names that are similar or differ only in case.
- 4. Standards for naming member function: • Member functions should be named using a full English description, using mixed case with the first letter of any non- initial word capitalized. The first word of the member function should be a verb, for example: • openAccount(), printMailingList(), save() etc. • Naming accessor member functions: • Getters: member functions that return the value of a field / attribute / property of an object. • Use prefix “get” to the name of the field / attribute / property if the field in not boolean, for example getFirstName(). • Use prefix “is” to the name of the field / attribute / property if the field is Boolean, for example isAvailable(). • A viable alternative is to use the prefix ‘has’ or ‘can’ instead of ‘is’ for boolean getters, for example canConsume().
- 5. Standards for naming member function (contd..): • Naming accessor member functions: • Setters: member functions that modify the values of a field. • Use prefix ‘set’ to the name of the field, for example: setFirstName() setLongCode() setMACAddr()
- 6. Standards for naming local variables: • Naming local variables: Use full English descriptors with the first letter of any non-initial word in uppercase, for example tempCounter. • Naming streams: When there is a single input and/or output stream being opened, used, and then closed within a member function the convention is to use in and out for the names of these streams, respectively. For example: FileInputStream fileIn = new FileInputStream(); FileOutputStream fileOut = new FileOutputStream(); • Naming loop counter: A common way is to use words like loopCounters or simply counter because it helps facilitate the search for the counters in the program. i, j, k can also be used as loop counters but the disadvantage is that search for i ,j and k in the code will result in many hits. • Naming exception objects: Use letter ‘e’ for generic exception, for example Catch (Exception e).
- 7. Standards for naming method arguements: • Naming parameters: Parameters should be named following the exact same conventions as for local variable. Name parameters the same as their corresponding fields (if any). • Example: If Account has an attribute called balance and you needed to pass a parameter representing a new value for it the parameter would be called balance. The field would be referred to as this.balance in the code and the parameter would be referred as balance.
- 8. Standards for classes, interfaces and packages: • Naming classes: Use full English descriptor starting with the first letter capitalized using mixed case for the rest of the name, for example class InterestCalculator. • Ordering member functions and fields: The order should as: • Constructors. • Private fields. • Public member functions. • Protected member functions. • Private member functions. • finalize(). • Naming interfaces: Name interfaces using mixed case with the first letter of each word capitalized. Prefix the letter “I” or “Ifc” to the interface name, for example interface IThirdPartyReqHandler. • Naming packages: Packages names should begin with an identifier that is not all upper case, for example safeword.jdbc.sql. Package name must be defined logically depending on the type of class it holds.
- 9. • Comment should add to clarity of code. Avoid decoration like comments. • Document why something is being done not just what. Comment Type Usage Example Documentation Starts with /** and ends with */ Used before declarations of interfaces, classes, member functions, and fields to document them. /** * Customer – a person or * organization */ C style Starts with /* and ends with */ Used to document out lines of code that are no longer applicable. It is helpful in debugging. /* This code was commented out by Ashish Sarin */ Single line Starts with // and go until the end of the line Used internally within member functions to document business logic, sections of code, and declarations of temporary variables. // If the amount is greater // than 10 multiply by 100
- 10. • Documentation related to member functions: • What and why the member function does than just what it does. • What member function must be passed as parameters. • What a member function returns. • Known bugs. • Any exception that a member function throws. • Visibility decisions (if questionable by other developers). • Applicable pre conditions and post conditions under which the function will work properly. These are the assumptions made during writing of the function. • Explanation of why keeping a function synchronized must be documented. • Use C style comments to document out lines of unneeded code (within member function). • Use single-line comments for business logic (within member function).
- 11. • Indentation: • Four spaces should be used as the unit of indentation or in eclipse IDE, use shortcut ctrl+I to indent complete code in one go. • When an expression will not fit on a single line, break it according to these general principles: • Break after a comma. • Break before an operator. • Prefer higher-level breaks to lower-level breaks. • Example: longName1 = longName2 * (longName3 + longName4 - longName5) + 4 * longname6; // PREFER longName1 = longName2 * (longName3 + longName4 - longName5) + 4 * longname6; // AVOID • One declaration per line is recommended since it encourages commenting. In other words, int level; int size; Is preferred over int level, size;
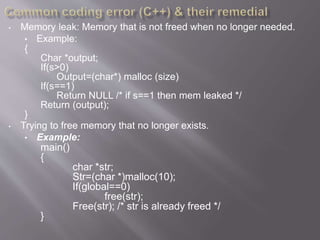
- 12. • Memory leak: Memory that is not freed when no longer needed. • Example: { Char *output; If(s>0) Output=(char*) malloc (size) If(s==1) Return NULL /* if s==1 then mem leaked */ Return (output); } • Trying to free memory that no longer exists. • Example: main() { char *str; Str=(char *)malloc(10); If(global==0) free(str); Free(str); /* str is already freed */ }
- 13. • NULL dereferencing: Trying to access an object which is pointing to NULL. • Example: if (x>0) { ch=‘c’; } printf(“%c”. *ch); /* ch may be NULL */ *ch=malloc(size) ch=‘c’; /* ch will be NULL if malloc returns NULL */ • Lack of unique addresses: Aliasing creates many problems among them is violation of unique addresses when we expect different addresses. • e.g in the string concatenation function, we expect source and destination addresses to be different. • strcat (src , destn ); if src and destn are same then runtime exeception will be thrown.
- 14. • Synchronization error: When multiple threads tries to acccess some common resources then deadlock may happen: • Example: Thread 1: synchronized (A){ synchronized (B){ } } Thread 2: synchronized (B){ synchronized (C){ } } Thread 3: synchronized (C){ synchronized (A){ } }
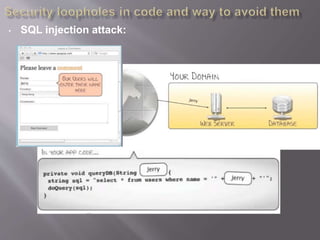
- 15. • SQL injection attack:
- 16. • SQL injection attack:
- 17. • SQL injection attack: Use parameterized sql queries to avoid SQL injection attack. • Expose of confidential information: Never print fileNotFoundException messages to console or log file or user prompt because these exceptions may show the exact path where file is present/what’s the file name and attacker may use this information for some malicious activities.
- 18. • Cross site scripting: Attacks involving embedding some malicious information and special characters in URLs and getting unauthorized information. To avoid this, always use url.encode method to encode the url and decode method to decode url and then use it. • Disable HTML rendering in swing components: Sometimes any adversar may inject some false information in html tag and display it on swing components. To avoid this always disable html in swing by calling html.disable client property. For example, label.putClientProperty("html.disable", true) • Always validate user input at server side and not on client side, as some malicious programs may bypass client and directly call server side application.
- 19. • Always use finally block with try-catch clause to ensure code execution. • Example: try { } catch(Exception e) {} finally { } • Replace Hashtable and Vector with Hashmap, ArrayList and LinkedList. • Use stringbuffer instead of stringbuilder and string concatenation. • Use lazy initialization to defer creation of objects until they are required.
- 20. • Always close DB resources in finally block in following order to avoid connection leak: • Connection open • Statement open • Resultset open (if required) • Resultset closed (if opened) • Statement closed • Connection closed • Always set session timeouts to kill idle sessions and avoid any security breach. • Always do session.invalidate() before calling session.close() to avoid security breach. • Always use string.length()==0 instead of string.equals(Null) to check null string.
