Building Secure Open & Distributed Social Networks
38 likes8,186 views
The document discusses the challenges of social networking, particularly the issues of data silos and the difficulty in linking multiple social networks. It proposes a solution involving a global namespace and universal identifiers (URIs) to facilitate better data portability and integration across platforms. Additionally, the document touches on security measures such as OpenID and SSL to protect user information within these decentralized networks.
1 of 45
Downloaded 691 times












































Ad
Recommended
Oscon 2008 Open Micro Blogging Presentation
Oscon 2008 Open Micro Blogging PresentationEvan Prodromou The document discusses Evan Prodromou's open source microblogging project Identi.ca. It summarizes the goals of making microblogging free and distributed through open standards, while also providing an alternative to the popular but closed Twitter platform. It outlines features already implemented in Identi.ca like federation and discusses future plans and opportunities for others to get involved through contributing code, translations, or spreading awareness of the project.
OSINT for Attack and Defense
OSINT for Attack and DefenseAndrew McNicol This document provides an overview of how open-source intelligence (OSINT) techniques can be used both offensively and defensively. It discusses tools like Shodan, Maltego, Google searches, and malware sandboxes that can be leveraged to gather technical information about targets, infrastructure, and indicators of compromise. The document also emphasizes the importance of automation and privacy when conducting OSINT research to enhance attacks or strengthen defenses.
Connect the Dots: Bridging Silos of Information (WPCampus 2019)
Connect the Dots: Bridging Silos of Information (WPCampus 2019)Elaine Shannon Elaine Shannon discusses strategies for integrating various information silos at St. Mary's University, focusing on the use of WordPress and APIs to improve data accessibility and user experience. Key tips include avoiding duplicate content, identifying common data keys, and maintaining good relationships with system administrators. The presentation provides practical examples and encourages attendees to consider user needs while connecting disparate information sources.
OSINT Tool - Reconnaissance with Maltego
OSINT Tool - Reconnaissance with MaltegoRaghav Bisht This document provides an overview of the open source intelligence (OSINT) tool Maltego. It describes what Maltego is, how it works, and how to install it. Maltego allows users to map relationships between entities like people, organizations, websites, domains, and IP addresses through the use of transforms. It gathers information from online sources and users can write their own transforms and machines. The document provides details on features of Maltego and how to download the commercial or community editions.
Semantic Social Network
Semantic Social NetworkHaklae Kim This document discusses linking data on the web through semantic technologies like linked data and social tagging. It describes how social networks can be built by connecting people, tags, and resources through common relationships. It advocates applying semantic web principles to integrate heterogeneous web data and user-generated content across different sites and applications.
(Re-) Discovering Lost Web Pages
(Re-) Discovering Lost Web PagesMichael Nelson This document summarizes research into discovering lost web pages using techniques from digital preservation and information retrieval. Key points include:
- Web pages are frequently lost due to broken links or content being moved/removed, but copies may still exist in search engine caches or archives.
- Techniques like lexical signatures (representing a page's content in a few keywords) and analyzing page titles, tags and link neighborhoods can help characterize lost pages and find similar replacement content.
- Experiments showed that lexical signatures degrade over time but page titles are more stable, and combining techniques improves performance in locating replacement content. The goal is to develop a browser extension to help users find lost web pages.
Web application penetration testing lab setup guide
Web application penetration testing lab setup guideSudhanshu Chauhan This document provides guidance on setting up a basic environment for conducting web application penetration testing. It outlines both hardware and software requirements, including recommended tools. It then walks through installing a base OS, browsers, programming languages, web servers, and various security tools. It also provides an overview of the testing process, including information gathering, automated scanning, manual testing, and reporting.
InfoSec World 2013 – W4 – Using Google to Find Vulnerabilities in Your IT Env...
InfoSec World 2013 – W4 – Using Google to Find Vulnerabilities in Your IT Env...Bishop Fox The document discusses Google hacking and its application in identifying vulnerabilities within IT environments, emphasizing the use of open source intelligence (OSINT) to gather information from publicly available sources. It introduces various hacking tools, such as Diggity tools, which are designed for advanced attacks and vulnerabilities, particularly in Google and Bing. The document also highlights real-world threats and examples of data breaches related to public cloud storage and sensitive information exposure.
Hacking with Semantic Web
Hacking with Semantic WebTom Praison Praison This document discusses semantic web technologies including linked data and how they can help solve information needs on the current web. It provides an overview of semantic web standards like RDF and SPARQL and examples of datasets like DBPedia that publish structured data on the web in RDF format and link to each other. It also demonstrates tools for extracting structured data from websites and a mobile app built using open linked data.
NISO/DCMI Webinar: Schema.org and Linked Data: Complementary Approaches to Pu...
NISO/DCMI Webinar: Schema.org and Linked Data: Complementary Approaches to Pu...National Information Standards Organization (NISO) The document discusses a webinar presented by NISO and DCMI on Schema.org and Linked Data. The webinar provides an overview of Schema.org and Linked Data, examines the advantages and challenges of using RDF and Linked Data, looks at Schema.org in more detail, and discusses how Schema.org and Linked Data can be combined. The goals of the webinar are to illustrate the different design choices for identifying entities and describing structured data, integrating vocabularies, and incentives for publishing accurate data, as well as to help guide adoption of Schema.org and Linked Data approaches.
Publishing data on the Semantic Web
Publishing data on the Semantic WebPeter Mika The document discusses several options for publishing data on the Semantic Web. It describes Linked Data as the preferred approach, which involves using URIs to identify things and including links between related data to improve discovery. It also outlines publishing metadata in HTML documents using standards like RDFa and Microdata, as well as exposing SPARQL endpoints and data feeds.
Webofdata
WebofdataBill Roberts The document introduces the concept of the 'web of data', emphasizing its significance in exposing and connecting data via linked data principles set by Tim Berners-Lee. It discusses the importance of publishing linked data for various purposes, such as enhancing visibility and academic service. The document also outlines foundational steps for implementing linked data, including using URIs, RDF representations, and relevant tools and platforms.
Data Portability with SIOC and FOAF
Data Portability with SIOC and FOAFUldis Bojars The document discusses the challenges of data portability in social networks, highlighting the need for users to merge their online identities and content across different platforms. It introduces the Semantic Web concept and tools like FOAF and SIOC that facilitate data interoperability and user control over their online information. The authors emphasize that by adopting open standards, users can better manage their social media contributions and connections across various services.
From the Semantic Web to the Web of Data: ten years of linking up
From the Semantic Web to the Web of Data: ten years of linking upDavide Palmisano This document discusses the concepts and technologies behind the Semantic Web. It describes how RDF, RDF Schema, and OWL allow structured data and relationships to be represented and shared across the web. It also discusses tools for working with semantic data in Java, such as Jena, Sesame, and Any23 for extracting and working with RDF. The document provides examples of representing data and relationships in RDF and querying semantic data with SPARQL.
moscow_developer_day
moscow_developer_dayxlight - The document discusses the current state of the social graph and challenges around interoperability between social networks and applications. It proposes using open standards and protocols like OpenID, OAuth, FOAF and XFN to help connect the "Giant Global Graph" and enable applications to access social data across platforms.
- Issues around privacy, personas and syncing social data between sites are examined. The ideal is described as a world where applications can easily access the social graph while respecting user privacy and control over their data.
- Small steps are being taken using these open standards to work towards the ideal of a fully interoperable social graph not controlled by any single company.
Modeling and Representing Trust Relations in Semantic Web-Driven Social Networks
Modeling and Representing Trust Relations in Semantic Web-Driven Social NetworksNima Dokoohaki The document discusses the modeling and representation of trust in semantic web-driven social networks using ontologies, highlighting the importance of trust in such environments. It presents various properties of trust, modeling approaches, and the potential integration of social networks through frameworks like FOAF (Friend-of-a-Friend). It concludes that utilizing ontologies offers a promising methodology for enhancing trust relationships in social networks on the semantic web.
A Semantic Multimedia Web (Part 2)
A Semantic Multimedia Web (Part 2)Raphael Troncy The document outlines semantic multimedia web technologies, focusing on RDF as a triple model for information modeling, and discusses RDFS and OWL for representing ontologies. It emphasizes the importance of linked data, its principles, and various methodologies for building and publishing ontologies and vocabularies. Additionally, it addresses the challenges and current trends in linked data applications and resources.
Using MongoDB as a high performance graph database
Using MongoDB as a high performance graph databaseChris Clarke This document provides a summary of a presentation on using MongoDB as a high performance graph database. The presentation discusses:
1) The speaker's company Talis Education using MongoDB for 8 months to store and query graph data, and implementing a software wrapper on top of MongoDB to improve scalability and performance.
2) Common graph data models using nodes and edges or resources and properties. Basic graph concepts like undirected vs directed graphs are explained.
3) Storing graph data as RDF triples, with the standard subject-predicate-object structure. Benefits of RDF such as reusing common schemas and easy data merging are highlighted.
4) SPARQL, the query language for RDF,
Foaf Openid Milan
Foaf Openid MilanDan Brickley This document discusses the convergence of social networks and semantic web technologies like FOAF, OpenID, and OAuth. It provides a brief history of semantic web projects and social networking sites. It then explains how standards like FOAF, OpenID, and OAuth allow for decentralized social applications and a unified social graph by describing identities, connections between people, and permissions for sharing data across sites. The document suggests the emerging social web will focus more on groups than individuals and leverage evidence-based friend lists identified by OpenID and described by FOAF across multiple sites using OAuth.
RDF: what and why plus a SPARQL tutorial
RDF: what and why plus a SPARQL tutorialJerven Bolleman The document introduces RDF (Resource Description Framework), a technology used to describe web resources through statements called triples. It highlights the advantages of RDF, such as avoiding name clashes and enabling distributed data annotation, while explaining various serialization formats like RDF/XML, Turtle, and JSON-LD. Additionally, it discusses the integration and querying of RDF data using SPARQL, emphasizing the importance of accessibility in life sciences research.
When?
When?Dan Brickley 1. The document discusses the history and future of semantic web technologies, including lessons learned and trends. It notes that semantic web's strength is in data aggregation rather than data management.
2. Two scenarios involving expressing claims in RDFa and linking from a homepage are presented, showing how trust can come from linked information.
3. Recent and emerging trends in user interfaces, search engines, and services are moving towards a more machine-readable web where pages make claims and datasets are interconnected.
Linked Data Basics
Linked Data BasicsAnja Jentzsch The document discusses linked data and its principles, emphasizing the importance of using URIs, RDF, and HTTP to create a global data space on the web. It outlines the advantages of linked data over traditional web structures, including interconnectivity and ease of data integration. The growth of linked data is highlighted, showing increasing datasets and applications in various domains like government, libraries, and media.
Hack U Barcelona 2011
Hack U Barcelona 2011Peter Mika This document discusses the Semantic Web and Linked Data. It provides an overview of key Semantic Web technologies like RDF, URIs, and SPARQL. It also describes several popular Linked Data datasets including DBpedia, Freebase, Geonames, and government open data. Finally, it discusses the Yahoo BOSS search API and WebScope data for building search applications.
Web Topics
Web TopicsPraveen AP The document discusses the history and architecture of the World Wide Web and semantic web. It describes how Tim Berners-Lee created the World Wide Web in 1989 at CERN. It outlines the key components of the web including URIs, URLs, HTTP, HTML, and web browsers. It then discusses the evolution of the semantic web and linked data, including the use of XML, RDF, RDFS, and OWL to represent metadata and link data on the web.
Linked data HHS 2015
Linked data HHS 2015Cason Snow Linked Data, the Semantic Web, and You discusses key concepts related to Linked Data and the Semantic Web. It defines Linked Data as a set of best practices for publishing and connecting structured data on the web using URIs, HTTP, RDF, and other standards. It also explains semantic web technologies like RDF, ontologies, SKOS, and SPARQL that enable representing and querying structured data on the web. Finally, it discusses how libraries are applying these concepts through projects like BIBFRAME, FAST, library linked data platforms, and the LD4L project to represent bibliographic data as linked open data.
Facebook ( Open ) Graph and the Semantic Web
Facebook ( Open ) Graph and the Semantic WebMatteo Brunati The document discusses the integration of Facebook's Open Graph and RDFa within the context of the semantic web, highlighting the significance of social objects and their impact on web interactions. It contrasts Facebook's minimal implementation of RDFa with traditional W3C standards, advocating for the use of URIs to facilitate a more interconnected web. Future directions are proposed around personal data control and the potential shift towards a more user-centered digital marketplace enabled by semantic web technologies.
Year of the Monkey: Lessons from the first year of SearchMonkey
Year of the Monkey: Lessons from the first year of SearchMonkeyPeter Mika This document discusses publishing content on the Semantic Web. It introduces basic concepts of RDF and the Semantic Web like resources, literals, and triples. It then describes six main ways to publish RDF data on the web: 1) standalone RDF documents, 2) metadata inside webpages using techniques like RDFa, 3) SPARQL endpoints, 4) feeds, 5) XSLT transformations, and 6) automatic markup tools. Finally, it briefly discusses the history of embedding metadata in HTML and examples of metadata standards.
Semantic Web Austin Yahoo
Semantic Web Austin YahooPeter Mika This document discusses publishing content on the Semantic Web. It introduces basic concepts of RDF and the Semantic Web like resources, literals, and triples. It then describes six main ways to publish RDF data on the web: 1) standalone RDF documents, 2) metadata inside webpages using formats like RDFa, 3) SPARQL endpoints, 4) feeds, 5) XSLT transformations, and 6) automatic markup tools. Finally, it briefly reviews the history of embedding metadata in HTML and examples of formats used.
The Future of Product Management in AI ERA.pdf
The Future of Product Management in AI ERA.pdfAlyona Owens Hi, I’m Aly Owens, I have a special pleasure to stand here as over a decade ago I graduated from CityU as an international student with an MBA program. I enjoyed the diversity of the school, ability to work and study, the network that came with being here, and of course the price tag for students here has always been more affordable than most around.
Since then I have worked for major corporations like T-Mobile and Microsoft and many more, and I have founded a startup. I've also been teaching product management to ensure my students save time and money to get to the same level as me faster avoiding popular mistakes. Today as I’ve transitioned to teaching and focusing on the startup, I hear everybody being concerned about Ai stealing their jobs… We’ll talk about it shortly.
But before that, I want to take you back to 1997. One of my favorite movies is “Fifth Element”. It wowed me with futuristic predictions when I was a kid and I’m impressed by the number of these predictions that have already come true. Self-driving cars, video calls and smart TV, personalized ads and identity scanning. Sci-fi movies and books gave us many ideas and some are being implemented as we speak. But we often get ahead of ourselves:
Flying cars,Colonized planets, Human-like AI: not yet, Time travel, Mind-machine neural interfaces for everyone: Only in experimental stages (e.g. Neuralink).
Cyberpunk dystopias: Some vibes (neon signs + inequality + surveillance), but not total dystopia (thankfully).
On the bright side, we predict that the working hours should drop as Ai becomes our helper and there shouldn’t be a need to work 8 hours/day. Nobody knows for sure but we can require that from legislation. Instead of waiting to see what the government and billionaires come up with, I say we should design our own future.
So, we as humans, when we don’t know something - fear takes over. The same thing happened during the industrial revolution. In the Industrial Era, machines didn’t steal jobs—they transformed them but people were scared about their jobs. The AI era is making similar changes except it feels like robots will take the center stage instead of a human. First off, even when it comes to the hottest space in the military - drones, Ai does a fraction of work. AI algorithms enable real-time decision-making, obstacle avoidance, and mission optimization making drones far more autonomous and capable than traditional remote-controlled aircraft. Key technologies include computer vision for object detection, GPS-enhanced navigation, and neural networks for learning and adaptation. But guess what? There are only 2 companies right now that utilize Ai in drones to make autonomous decisions - Skydio and DJI.
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdf
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdfEarley Information Science As AI reshapes expectations in retail and B2B commerce, organizations are recognizing a critical reality: meaningful AI outcomes depend on well-structured, adaptable infrastructure. In this session, Seth Earley is joined by Phil Ryan - AI strategist, search technologist, and founder of Glass Leopard Technologies - for a candid conversation on what it truly means to engineer systems for scale, agility, and intelligence.
Phil draws on more than two decades of experience leading search and AI initiatives for enterprise organizations. Together, he and Seth explore the challenges businesses face when legacy architectures limit personalization, agility, and real-time decisioning - and what needs to change to support agentic technologies and next-best-action capabilities.
Key themes from the webinar include:
Composability as a prerequisite for AI - Why modular, loosely coupled systems are essential for adapting to rapid innovation and evolving business needs
Search and relevance as foundational to AI - How techniques honed-in enterprise search have laid the groundwork for more responsive and intelligent customer experiences
From MDM and CDP to agentic systems - How data platforms are evolving to support richer customer context and dynamic orchestration
Engineering for business alignment - Why successful AI programs require architectural decisions grounded in measurable outcomes
The conversation is practical and forward-looking, connecting deep technical understanding with real-world business needs. Whether you’re modernizing your commerce stack or exploring how AI can enhance product discovery, personalization, or customer journeys, this session provides a clear-eyed view of the capabilities, constraints, and priorities that matter most.
More Related Content
Similar to Building Secure Open & Distributed Social Networks (20)
Hacking with Semantic Web
Hacking with Semantic WebTom Praison Praison This document discusses semantic web technologies including linked data and how they can help solve information needs on the current web. It provides an overview of semantic web standards like RDF and SPARQL and examples of datasets like DBPedia that publish structured data on the web in RDF format and link to each other. It also demonstrates tools for extracting structured data from websites and a mobile app built using open linked data.
NISO/DCMI Webinar: Schema.org and Linked Data: Complementary Approaches to Pu...
NISO/DCMI Webinar: Schema.org and Linked Data: Complementary Approaches to Pu...National Information Standards Organization (NISO) The document discusses a webinar presented by NISO and DCMI on Schema.org and Linked Data. The webinar provides an overview of Schema.org and Linked Data, examines the advantages and challenges of using RDF and Linked Data, looks at Schema.org in more detail, and discusses how Schema.org and Linked Data can be combined. The goals of the webinar are to illustrate the different design choices for identifying entities and describing structured data, integrating vocabularies, and incentives for publishing accurate data, as well as to help guide adoption of Schema.org and Linked Data approaches.
Publishing data on the Semantic Web
Publishing data on the Semantic WebPeter Mika The document discusses several options for publishing data on the Semantic Web. It describes Linked Data as the preferred approach, which involves using URIs to identify things and including links between related data to improve discovery. It also outlines publishing metadata in HTML documents using standards like RDFa and Microdata, as well as exposing SPARQL endpoints and data feeds.
Webofdata
WebofdataBill Roberts The document introduces the concept of the 'web of data', emphasizing its significance in exposing and connecting data via linked data principles set by Tim Berners-Lee. It discusses the importance of publishing linked data for various purposes, such as enhancing visibility and academic service. The document also outlines foundational steps for implementing linked data, including using URIs, RDF representations, and relevant tools and platforms.
Data Portability with SIOC and FOAF
Data Portability with SIOC and FOAFUldis Bojars The document discusses the challenges of data portability in social networks, highlighting the need for users to merge their online identities and content across different platforms. It introduces the Semantic Web concept and tools like FOAF and SIOC that facilitate data interoperability and user control over their online information. The authors emphasize that by adopting open standards, users can better manage their social media contributions and connections across various services.
From the Semantic Web to the Web of Data: ten years of linking up
From the Semantic Web to the Web of Data: ten years of linking upDavide Palmisano This document discusses the concepts and technologies behind the Semantic Web. It describes how RDF, RDF Schema, and OWL allow structured data and relationships to be represented and shared across the web. It also discusses tools for working with semantic data in Java, such as Jena, Sesame, and Any23 for extracting and working with RDF. The document provides examples of representing data and relationships in RDF and querying semantic data with SPARQL.
moscow_developer_day
moscow_developer_dayxlight - The document discusses the current state of the social graph and challenges around interoperability between social networks and applications. It proposes using open standards and protocols like OpenID, OAuth, FOAF and XFN to help connect the "Giant Global Graph" and enable applications to access social data across platforms.
- Issues around privacy, personas and syncing social data between sites are examined. The ideal is described as a world where applications can easily access the social graph while respecting user privacy and control over their data.
- Small steps are being taken using these open standards to work towards the ideal of a fully interoperable social graph not controlled by any single company.
Modeling and Representing Trust Relations in Semantic Web-Driven Social Networks
Modeling and Representing Trust Relations in Semantic Web-Driven Social NetworksNima Dokoohaki The document discusses the modeling and representation of trust in semantic web-driven social networks using ontologies, highlighting the importance of trust in such environments. It presents various properties of trust, modeling approaches, and the potential integration of social networks through frameworks like FOAF (Friend-of-a-Friend). It concludes that utilizing ontologies offers a promising methodology for enhancing trust relationships in social networks on the semantic web.
A Semantic Multimedia Web (Part 2)
A Semantic Multimedia Web (Part 2)Raphael Troncy The document outlines semantic multimedia web technologies, focusing on RDF as a triple model for information modeling, and discusses RDFS and OWL for representing ontologies. It emphasizes the importance of linked data, its principles, and various methodologies for building and publishing ontologies and vocabularies. Additionally, it addresses the challenges and current trends in linked data applications and resources.
Using MongoDB as a high performance graph database
Using MongoDB as a high performance graph databaseChris Clarke This document provides a summary of a presentation on using MongoDB as a high performance graph database. The presentation discusses:
1) The speaker's company Talis Education using MongoDB for 8 months to store and query graph data, and implementing a software wrapper on top of MongoDB to improve scalability and performance.
2) Common graph data models using nodes and edges or resources and properties. Basic graph concepts like undirected vs directed graphs are explained.
3) Storing graph data as RDF triples, with the standard subject-predicate-object structure. Benefits of RDF such as reusing common schemas and easy data merging are highlighted.
4) SPARQL, the query language for RDF,
Foaf Openid Milan
Foaf Openid MilanDan Brickley This document discusses the convergence of social networks and semantic web technologies like FOAF, OpenID, and OAuth. It provides a brief history of semantic web projects and social networking sites. It then explains how standards like FOAF, OpenID, and OAuth allow for decentralized social applications and a unified social graph by describing identities, connections between people, and permissions for sharing data across sites. The document suggests the emerging social web will focus more on groups than individuals and leverage evidence-based friend lists identified by OpenID and described by FOAF across multiple sites using OAuth.
RDF: what and why plus a SPARQL tutorial
RDF: what and why plus a SPARQL tutorialJerven Bolleman The document introduces RDF (Resource Description Framework), a technology used to describe web resources through statements called triples. It highlights the advantages of RDF, such as avoiding name clashes and enabling distributed data annotation, while explaining various serialization formats like RDF/XML, Turtle, and JSON-LD. Additionally, it discusses the integration and querying of RDF data using SPARQL, emphasizing the importance of accessibility in life sciences research.
When?
When?Dan Brickley 1. The document discusses the history and future of semantic web technologies, including lessons learned and trends. It notes that semantic web's strength is in data aggregation rather than data management.
2. Two scenarios involving expressing claims in RDFa and linking from a homepage are presented, showing how trust can come from linked information.
3. Recent and emerging trends in user interfaces, search engines, and services are moving towards a more machine-readable web where pages make claims and datasets are interconnected.
Linked Data Basics
Linked Data BasicsAnja Jentzsch The document discusses linked data and its principles, emphasizing the importance of using URIs, RDF, and HTTP to create a global data space on the web. It outlines the advantages of linked data over traditional web structures, including interconnectivity and ease of data integration. The growth of linked data is highlighted, showing increasing datasets and applications in various domains like government, libraries, and media.
Hack U Barcelona 2011
Hack U Barcelona 2011Peter Mika This document discusses the Semantic Web and Linked Data. It provides an overview of key Semantic Web technologies like RDF, URIs, and SPARQL. It also describes several popular Linked Data datasets including DBpedia, Freebase, Geonames, and government open data. Finally, it discusses the Yahoo BOSS search API and WebScope data for building search applications.
Web Topics
Web TopicsPraveen AP The document discusses the history and architecture of the World Wide Web and semantic web. It describes how Tim Berners-Lee created the World Wide Web in 1989 at CERN. It outlines the key components of the web including URIs, URLs, HTTP, HTML, and web browsers. It then discusses the evolution of the semantic web and linked data, including the use of XML, RDF, RDFS, and OWL to represent metadata and link data on the web.
Linked data HHS 2015
Linked data HHS 2015Cason Snow Linked Data, the Semantic Web, and You discusses key concepts related to Linked Data and the Semantic Web. It defines Linked Data as a set of best practices for publishing and connecting structured data on the web using URIs, HTTP, RDF, and other standards. It also explains semantic web technologies like RDF, ontologies, SKOS, and SPARQL that enable representing and querying structured data on the web. Finally, it discusses how libraries are applying these concepts through projects like BIBFRAME, FAST, library linked data platforms, and the LD4L project to represent bibliographic data as linked open data.
Facebook ( Open ) Graph and the Semantic Web
Facebook ( Open ) Graph and the Semantic WebMatteo Brunati The document discusses the integration of Facebook's Open Graph and RDFa within the context of the semantic web, highlighting the significance of social objects and their impact on web interactions. It contrasts Facebook's minimal implementation of RDFa with traditional W3C standards, advocating for the use of URIs to facilitate a more interconnected web. Future directions are proposed around personal data control and the potential shift towards a more user-centered digital marketplace enabled by semantic web technologies.
Year of the Monkey: Lessons from the first year of SearchMonkey
Year of the Monkey: Lessons from the first year of SearchMonkeyPeter Mika This document discusses publishing content on the Semantic Web. It introduces basic concepts of RDF and the Semantic Web like resources, literals, and triples. It then describes six main ways to publish RDF data on the web: 1) standalone RDF documents, 2) metadata inside webpages using techniques like RDFa, 3) SPARQL endpoints, 4) feeds, 5) XSLT transformations, and 6) automatic markup tools. Finally, it briefly discusses the history of embedding metadata in HTML and examples of metadata standards.
Semantic Web Austin Yahoo
Semantic Web Austin YahooPeter Mika This document discusses publishing content on the Semantic Web. It introduces basic concepts of RDF and the Semantic Web like resources, literals, and triples. It then describes six main ways to publish RDF data on the web: 1) standalone RDF documents, 2) metadata inside webpages using formats like RDFa, 3) SPARQL endpoints, 4) feeds, 5) XSLT transformations, and 6) automatic markup tools. Finally, it briefly reviews the history of embedding metadata in HTML and examples of formats used.
NISO/DCMI Webinar: Schema.org and Linked Data: Complementary Approaches to Pu...
NISO/DCMI Webinar: Schema.org and Linked Data: Complementary Approaches to Pu...National Information Standards Organization (NISO)
Recently uploaded (20)
The Future of Product Management in AI ERA.pdf
The Future of Product Management in AI ERA.pdfAlyona Owens Hi, I’m Aly Owens, I have a special pleasure to stand here as over a decade ago I graduated from CityU as an international student with an MBA program. I enjoyed the diversity of the school, ability to work and study, the network that came with being here, and of course the price tag for students here has always been more affordable than most around.
Since then I have worked for major corporations like T-Mobile and Microsoft and many more, and I have founded a startup. I've also been teaching product management to ensure my students save time and money to get to the same level as me faster avoiding popular mistakes. Today as I’ve transitioned to teaching and focusing on the startup, I hear everybody being concerned about Ai stealing their jobs… We’ll talk about it shortly.
But before that, I want to take you back to 1997. One of my favorite movies is “Fifth Element”. It wowed me with futuristic predictions when I was a kid and I’m impressed by the number of these predictions that have already come true. Self-driving cars, video calls and smart TV, personalized ads and identity scanning. Sci-fi movies and books gave us many ideas and some are being implemented as we speak. But we often get ahead of ourselves:
Flying cars,Colonized planets, Human-like AI: not yet, Time travel, Mind-machine neural interfaces for everyone: Only in experimental stages (e.g. Neuralink).
Cyberpunk dystopias: Some vibes (neon signs + inequality + surveillance), but not total dystopia (thankfully).
On the bright side, we predict that the working hours should drop as Ai becomes our helper and there shouldn’t be a need to work 8 hours/day. Nobody knows for sure but we can require that from legislation. Instead of waiting to see what the government and billionaires come up with, I say we should design our own future.
So, we as humans, when we don’t know something - fear takes over. The same thing happened during the industrial revolution. In the Industrial Era, machines didn’t steal jobs—they transformed them but people were scared about their jobs. The AI era is making similar changes except it feels like robots will take the center stage instead of a human. First off, even when it comes to the hottest space in the military - drones, Ai does a fraction of work. AI algorithms enable real-time decision-making, obstacle avoidance, and mission optimization making drones far more autonomous and capable than traditional remote-controlled aircraft. Key technologies include computer vision for object detection, GPS-enhanced navigation, and neural networks for learning and adaptation. But guess what? There are only 2 companies right now that utilize Ai in drones to make autonomous decisions - Skydio and DJI.
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdf
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdfEarley Information Science As AI reshapes expectations in retail and B2B commerce, organizations are recognizing a critical reality: meaningful AI outcomes depend on well-structured, adaptable infrastructure. In this session, Seth Earley is joined by Phil Ryan - AI strategist, search technologist, and founder of Glass Leopard Technologies - for a candid conversation on what it truly means to engineer systems for scale, agility, and intelligence.
Phil draws on more than two decades of experience leading search and AI initiatives for enterprise organizations. Together, he and Seth explore the challenges businesses face when legacy architectures limit personalization, agility, and real-time decisioning - and what needs to change to support agentic technologies and next-best-action capabilities.
Key themes from the webinar include:
Composability as a prerequisite for AI - Why modular, loosely coupled systems are essential for adapting to rapid innovation and evolving business needs
Search and relevance as foundational to AI - How techniques honed-in enterprise search have laid the groundwork for more responsive and intelligent customer experiences
From MDM and CDP to agentic systems - How data platforms are evolving to support richer customer context and dynamic orchestration
Engineering for business alignment - Why successful AI programs require architectural decisions grounded in measurable outcomes
The conversation is practical and forward-looking, connecting deep technical understanding with real-world business needs. Whether you’re modernizing your commerce stack or exploring how AI can enhance product discovery, personalization, or customer journeys, this session provides a clear-eyed view of the capabilities, constraints, and priorities that matter most.
Coordinated Disclosure for ML - What's Different and What's the Same.pdf
Coordinated Disclosure for ML - What's Different and What's the Same.pdfPriyanka Aash Coordinated Disclosure for ML - What's Different and What's the Same
"Scaling in space and time with Temporal", Andriy Lupa.pdf
"Scaling in space and time with Temporal", Andriy Lupa.pdfFwdays Design patterns like Event Sourcing and Event Streaming have long become standards for building real-time analytics systems. However, when the system load becomes nonlinear with fast and often unpredictable spikes, it's crucial to respond quickly in order not to lose real-time operating itself.
In this talk, I’ll share my experience implementing and using a tool like Temporal.io. We'll explore the evolution of our system for maintaining real-time report generation and discuss how we use Temporal both for short-lived pipelines and long-running background tasks.
10 Key Challenges for AI within the EU Data Protection Framework.pdf
10 Key Challenges for AI within the EU Data Protection Framework.pdfPriyanka Aash 10 Key Challenges for AI within the EU Data Protection Framework
AI vs Human Writing: Can You Tell the Difference?
AI vs Human Writing: Can You Tell the Difference?Shashi Sathyanarayana, Ph.D This slide illustrates a side-by-side comparison between human-written, AI-written, and ambiguous content. It highlights subtle cues that help readers assess authenticity, raising essential questions about the future of communication, trust, and thought leadership in the age of generative AI.
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...Fwdays We will explore how e-commerce projects prepare for the busiest time of the year, which key aspects to focus on, and what to expect. We’ll share our experience in setting up auto-scaling, load balancing, and discuss the loads that Silpo handles, as well as the solutions that help us navigate this season without failures.
Mastering AI Workflows with FME by Mark Döring
Mastering AI Workflows with FME by Mark DöringSafe Software Harness the full potential of AI with FME: From creating high-quality training data to optimizing models and utilizing results, FME supports every step of your AI workflow. Seamlessly integrate a wide range of models, including those for data enhancement, forecasting, image and object recognition, and large language models. Customize AI models to meet your exact needs with FME’s powerful tools for training, optimization, and seamless integration
Enhance GitHub Copilot using MCP - Enterprise version.pdf
Enhance GitHub Copilot using MCP - Enterprise version.pdfNilesh Gule Slide deck related to the GitHub Copilot Bootcamp in Melbourne on 17 June 2025
Wenn alles versagt - IBM Tape schützt, was zählt! Und besonders mit dem neust...
Wenn alles versagt - IBM Tape schützt, was zählt! Und besonders mit dem neust...Josef Weingand IBM LTO10
“MPU+: A Transformative Solution for Next-Gen AI at the Edge,” a Presentation...
“MPU+: A Transformative Solution for Next-Gen AI at the Edge,” a Presentation...Edge AI and Vision Alliance For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2025/06/mpu-a-transformative-solution-for-next-gen-ai-at-the-edge-a-presentation-from-fotonation/
Petronel Bigioi, CEO of FotoNation, presents the “MPU+: A Transformative Solution for Next-Gen AI at the Edge” tutorial at the May 2025 Embedded Vision Summit.
In this talk, Bigioi introduces MPU+, a novel programmable, customizable low-power platform for real-time, localized intelligence at the edge. The platform includes an AI-augmented image signal processor that enables leading image and video quality.
In addition, it integrates ultra-low-power object and motion detection capabilities to enable always-on computer vision. A programmable neural processor provides flexibility to efficiently implement new neural networks. And additional specialized engines facilitate image stabilization and audio enhancements.
Oh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdf
Oh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdfPriyanka Aash Oh, the Possibilities - Balancing Innovation and Risk with Generative AI
Agentic AI for Developers and Data Scientists Build an AI Agent in 10 Lines o...
Agentic AI for Developers and Data Scientists Build an AI Agent in 10 Lines o...All Things Open Presented at All Things Open RTP Meetup
Presented by William Hill - Developer Advocate, NVIDIA
Title: Agentic AI for Developers and Data Scientists
Build an AI Agent in 10 Lines of Code and the Concepts Behind the Code
Abstract: In this talk we will demonstrate building a working data science AI agent in 10 lines of basic Python code in a Colab notebook. Our AI Agent will perform LLM prompt-driven visual analysis using open-source libraries. In this session we will show how to develop an AI Agent using GPUs through NVIDIA’s developer program and Google Colab notebooks. After coding our AI Agent, we will break down the 10 lines of code. We will show the key components and open source library integrations that enable the agent's functionality, focusing on practical implementation details and then the theoretical concepts. The presentation concludes with a survey of current LLM technologies and the latest trends in developing AI applications for enthusiasts and enterprises
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdf
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdfPriyanka Aash A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy
9-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection.
Cracking the Code - Unveiling Synergies Between Open Source Security and AI.pdf
Cracking the Code - Unveiling Synergies Between Open Source Security and AI.pdfPriyanka Aash Cracking the Code - Unveiling Synergies Between Open Source Security and AI
From Manual to Auto Searching- FME in the Driver's Seat
From Manual to Auto Searching- FME in the Driver's SeatSafe Software Finding a specific car online can be a time-consuming task, especially when checking multiple dealer websites. A few years ago, I faced this exact problem while searching for a particular vehicle in New Zealand. The local classified platform, Trade Me (similar to eBay), wasn’t yielding any results, so I expanded my search to second-hand dealer sites—only to realise that periodically checking each one was going to be tedious. That’s when I noticed something interesting: many of these websites used the same platform to manage their inventories. Recognising this, I reverse-engineered the platform’s structure and built an FME workspace that automated the search process for me. By integrating API calls and setting up periodic checks, I received real-time email alerts when matching cars were listed. In this presentation, I’ll walk through how I used FME to save hours of manual searching by creating a custom car-finding automation system. While FME can’t buy a car for you—yet—it can certainly help you find the one you’re after!
"Database isolation: how we deal with hundreds of direct connections to the d...
"Database isolation: how we deal with hundreds of direct connections to the d...Fwdays What can go wrong if you allow each service to access the database directly? In a startup, this seems like a quick and easy solution, but as the system scales, problems appear that no one could have guessed.
In my talk, I'll share Solidgate's experience in transforming its architecture: from the chaos of direct connections to a service-based data access model. I will talk about the transition stages, bottlenecks, and how isolation affected infrastructure support. I will honestly show what worked and what didn't. In short, we will analyze the controversy of this talk.
Securing Account Lifecycles in the Age of Deepfakes.pptx
Securing Account Lifecycles in the Age of Deepfakes.pptxFIDO Alliance Securing Account Lifecycles in the Age of Deepfakes
“MPU+: A Transformative Solution for Next-Gen AI at the Edge,” a Presentation...
“MPU+: A Transformative Solution for Next-Gen AI at the Edge,” a Presentation...Edge AI and Vision Alliance
Ad
Building Secure Open & Distributed Social Networks
- 1. Secure Distributed Open Social Networks Henry Story Senior Staff Engineer Semantic Web Evangelist http://blogs.sun.com/bblfish Sun Microsystem photo by prakharevich
- 2. Overview Description of the Social Networking problem Why this is no longer “ somebody else's problem ”: a hyper address book The functioning of the Address Book How to add distributed decentralized security A final thought: how this changes the desktop paradigm
- 3. Too many Social Networks? ...are there too many web servers?
- 4. The Problem: data silos SN don't link up: Information can't be moved easily (see: Data Portability the video ) Users have to create and maintain accounts on each SN they have friends on, or loose contacts Growing number of social networks (SN) because there are a lot of $$$ to be made because there are many needs there will never be one SN to rule them all.
- 5. Scoble gets thrown off Facebook! In early January 2008 Scoble, the developer who got blogging going at Microsoft, got thrown off Facebook for extracting information too agressively from his social network on Facebook. This is the Facebook who asked users for their gmail password to extract all their contacts from their email! see his video
- 6. An (evolving) Social Graph relates many different things people to information about them name address phone number relations between people: who knows who who worked with who relations with external things blogs companies
- 7. Two social Networks how can Tim and Henry link up ?
- 8. Solution 1: minimal naïve approach but within each SN queries are very limited: e.g.: in Network A, nobody can query for Tim's address
- 9. Solution 2: copy some information how to copy the data? Data Portability? (DRY principle?) how to keep the relations up to date?! Twice as much work. queries still limited: what are the friends of Tim's friends?
- 10. Solution 3: copy all technically impossible: does not scale as networks grow in size and number: how to keep information up to date? amount of synchronization grows exponentially politically impossible: S.N. are very protective of their data + privacy issues + oligopoly issues
- 11. The pull to one network Due to Metcalf's law : the larger the network the more valuable it becomes. But why does it have to be in one database? Because each database has its own LOCAL POINTER mechanism, just like every Java virtual Machine has a local pointer mechanism. You cannot easily point from one JVM/DB into another. What if we had one big world wide database? we would need universal names for things. URIs?
- 12. The Solution: linking across social networks requires a global namespace
- 13. The Solution: a closer look objects and documents have URLs Relations also have URLs: foaf:knows , foaf:name The Self Describing Web
- 14. A hyperdata Address Book
- 15. 1. first launch of jnlp
- 16. 2. drag and drop a foaf file url
- 17. 3. click on the first name in the first column
- 18. 4. explore the second column
- 19. 5. press the space bar on the keyboard...
- 20. 6. positioning with NASA's World Wind
- 21. 7. Sun Intranet Foaf experiment
- 22. Foaf: Friend of a Friend
- 23. Advantages Open Social Network – no data silos Information about people is always up to date (an HTTP GET away) this could be used to keep up to date on where friends are It is easy to publish a foaf file: one click away Drag and drop friends security: some ideas at the end of the talk
- 24. Two foaf files on the internet
- 25. Well, what we really have is
- 26. Well, what we really have is in graph view
- 27. The graphs inside the Beatnik Database
- 28. Networked graphs: A merged view
- 29. SPARQL: semantic query lang PREFIX foaf: <http://xmlns.com/foaf/0.1/> SELECT ?p WHERE { ?p foaf:knows ?q . }
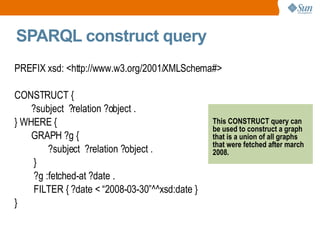
- 30. SPARQL construct query PREFIX xsd: <http://www.w3.org/2001/XMLSchema#> CONSTRUCT { ?subject ?relation ?object . } WHERE { GRAPH ?g { ?subject ?relation ?object . } ?g :fetched-at ?date . FILTER { ?date < “2008-03-30”^^xsd:date } } This CONSTRUCT query can be used to construct a graph that is a union of all graphs that were fetched after march 2008.
- 31. Networked Graphs: SPARQL Rules PREFIX owl: < http://www.w3.org/2002/07/owl #> CONSTRUCT { ?b owl:sameAs ?a . } WHERE { ?a owl:sameAs ?b . FILTER ( ! SAMETERM(?a , ?b) ) } CONSTRUCT queries can also be thought of as rules. Here is the well known rule of symmetry of identity. Simon Schenk's Networked Graphs can have a number of rules expressed as SPARQL CONSTRUCT queries, which works nicely with the Sesame semantic engine.
- 32. merging identities PREFIX owl: < http://www.w3.org/2002/07/owl #> PREFIX foaf: < http://xmlns.com/foaf/0.1/ > CONSTRUCT { ?a owl:sameAs ?b . } WHERE { ?a foaf:homepage ?pg . ?b foaf:homepage ?pg . FILTER ( ! SAMETERM (?a , ?b)) } The rule that if we have two names for people that have the same homepage, then the two names refer to the same person. There are more general ways of stating this btw.
- 33. Security: 3 approaches Simple Firewall based security OpenId based Security Even simpler SSL based security
- 35. Protecting resources with OpenId
- 36. Protected Resources :me a foaf:Person; foaf:name “Henry Story”; rdfs:seeAlso </protected/henry> . </protected/henry> openid:login </openidAuth.cgi> . This is trying to say that in order to access the protected resource one needs to login with openid first. This is a sketch of such a vocabulary
- 37. OpenId continued
- 39. Protected Resources :me a foaf:Person; foaf:name “Henry Story”; rdfs:seeAlso <https://.../protected/henry> . notice the seeAlso is now an https url
- 41. X509 certificate Certificate: Data: Version: 3 (0x2) Serial Number: 1 (0x1) Signature Algorithm: dsaWithSHA1 Issuer: O=OpenPGP to X.509 Bridge, OU=RDFauth Test, CN=Henry Story <[email protected]> Validity Not Before: Dec 12 21:49:50 2007 GMT Not After : Dec 6 21:49:50 2008 GMT Subject: O=OpenPGP to X.509 Bridge, OU=RDFauth Test, CN=Henry Story <[email protected]> Subject Public Key Info: Public Key Algorithm: dsaEncryption DSA Public Key: pub: 33:41:...
- 42. X509 certificate with id X509v3 extensions: X509v3 Basic Constraints: critical CA:TRUE X509v3 Key Usage: critical Digital Signature, Non Repudiation, Key Encipherment, Key Agreement, Certificate Sign Netscape Cert Type: SSL Client, S/MIME X509v3 Subject Key Identifier: 45:DC:F9:10:33:C0:45:28:EA:90:6E:83:73:06:6F:51:21:89:13:DD X509v3 Authority Key Identifier: keyid:45:DC:F9:10:33:C0:45:28:EA:90:6E:83:73:06:6F:51:21:89:13:DD X509v3 Subject Alternative Name: URI:http://bblfish.net/people/henry/card#me Signature Algorithm: dsaWithSHA1 30:2c:02:14:78:69:1e:4f:7d:37:36:a5:8f:37:30:58:18:5a: f6:10:e9:13:a4:ec:02:14:03:93:42:3b:c0:d4:33:63:ae:2f: eb:8c:11:08:1c:aa:93:7d:71:01
- 45. some references Getting Started With RDF The Semantic Address Book web site
Editor's Notes
- #2: Hello, my name is Henry Story. I work for Sun Microsystems where I research on the Semantic Web. I am tasked with finding ways to get people excited about what is happening in this space, which at first may seem very abstract. So I have been looking for problems that would affect people directly, have some real immediate business value, clearly demonstrate the power of the semantic web, and that is small enough that I don't need a big budget to get things done. After all I am in the business of convincing people. Once they are convinced I hope they will help out one way or another. Social Networking is big. It affects everyone in very personal ways. It is useful. It is what we are all about. Here I wish to show how one can build an secure, open, distributed global social network with no center of control. The only way to do this is using the semantic web....
