Chapter09 -- networking with unix and linux
Download as ppt, pdf1 like1,784 views
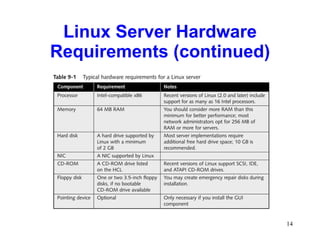
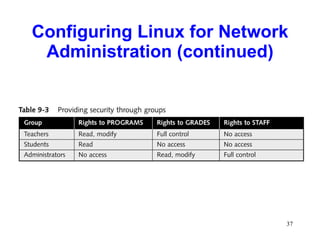
This chapter discusses the history and varieties of UNIX and Linux operating systems. It describes how to install Linux, configure users and permissions, and interconnect Linux with other network operating systems using tools like Samba, WINE, VMware and Telnet. The chapter also provides examples of basic Linux commands and how to set up a Linux server with the required hardware specifications.
1 of 51
Downloaded 142 times

















































Ad
Recommended
Ch01
Ch01Mike Qaissaunee This document provides an introduction to Linux, including its history from Unix and the GNU project. It describes the roles and responsibilities of a Linux system administrator, such as creating user accounts, maintaining systems, and recovering from emergencies. Tips are provided for working at the Linux command line and finding documentation. Key features of Linux include stability, security, flexibility and low cost.
Linux administration classes in mumbai
Linux administration classes in mumbaiVibrant Technologies & Computers Here are the steps to complete the assignment:
1. Logged in as guest user
2. Present working directory is /home/guest
3. Wrote the structure of root directory /
4. A few commands in /bin are ls, cp, mv. A few in /sbin are ifconfig, route
5. Guest directory is /home/guest
6. Permissions of /home/guest are drwxr-xr-x
7. Created directory test in /home/guest
8. Copied /etc/resolv.conf to /home/guest/test
9. Renamed /home/guest/test to /home/guest/testing
10. Deleted
Introduction to linux
Introduction to linuxnanocdac The document provides an overview of the Linux operating system, highlighting its history, advantages, and differences from Windows. Key benefits include low cost, high security, stability, performance, and flexibility, making it popular for servers and supercomputers. It also explains the directory structure, file permissions, and customization possibilities for users.
Gnu study guide linux admin 1 (lab work lpi 101) v 0.2
Gnu study guide linux admin 1 (lab work lpi 101) v 0.2Acácio Oliveira This document is a study guide for the Linux Professional Institute's (LPI) Linux System Administration 1 certification (exam 101). It provides an introduction, goals, intended audience, and table of contents for the guide. The introduction acknowledges contributions from various individuals and organizations. It also outlines the guide's primary aims of explaining concepts, examples, and exercises to help students prepare for the LPI 101 exam. The intended audience is assumed to have extensive computer and Linux experience. The guide is designed to accompany a 24-32 hour training course but can also be used more flexibly.
01 t1 s2_linux_lesson1
01 t1 s2_linux_lesson1Niit Care This document introduces the Linux operating system. It outlines objectives of the lesson which include identifying functions of an operating system, differentiating between single-user and multi-user systems, and learning Linux features and commands. The document describes operating system functions, types of systems, shells available in Linux, and commands for starting sessions, changing passwords, logging out, and managing files and directories.
Linux practicals T.Y.B.ScIT
Linux practicals T.Y.B.ScITvignesh0009 This document provides guidance for Linux administration practicals, including:
- An index of 17 practical topics ranging from basic Linux commands to configuring mail services.
- Detailed instructions for Practical 1 on basic commands like cat, mkdir, cp, and editors like vi. It provides an example directory and file structure to create.
- An overview of Practical 2 on installing Red Hat Linux, including selecting installation options and partitioning the hard drive to make space.
- Descriptions of changing file permissions using both binary and symbolic modes with chmod, and decoding permission codes from the ls command.
- An explanation of the different modes in the vi editor like command, insert, and ex modes,
Linux fundamentals
Linux fundamentalsRaghu nath This document provides an overview of Linux fundamentals, including:
- The kernel acts as an interface between hardware and software, handling processes and resource allocation.
- The userland includes standard libraries that allow programs to communicate with the kernel.
- Files are organized in a hierarchy with directories like /home for user files, /etc for configurations, and /var for variable files.
- Commands like ls, grep, and find allow viewing and searching files, while pipes, redirection, and compression utilities manage file input/output.
Red hat linux essentials
Red hat linux essentialsHaitham Raik This document provides an overview of Red Hat Linux and Linux fundamentals. It discusses Linux origins with the GNU project and Linus Torvalds' creation of the Linux kernel. It also describes open source software, different Red Hat distributions like Red Hat Enterprise Linux and Fedora, Linux principles like treating everything as a file, and basic Linux commands. The document is divided into units covering Linux usage basics, running commands and getting help, and browsing the filesystem.
basic linux command (questions)
basic linux command (questions)Sukhraj Singh This document contains instructions for 9 Linux lab practical assignments covering basic Linux commands, utilities, file attributes, redirection/pipes, processes, environment configuration, and basic system administration. The practicals include commands to find file locations, view process information, set user account attributes, and manage files and folders. Students are to complete the tasks listed in each practical and document their responses.
Linux fundamentals Training
Linux fundamentals TrainingLove Steven The document summarizes a presentation on the history and usage of Linux. It discusses:
- The dominance of proprietary operating systems in the 1960s-1970s and the motivation to create a free and open-source alternative called UNIX.
- How Linus Torvalds began developing Linux in 1991 based on UNIX to create a free academic version, gradually adding features over several years.
- Key advantages of Linux including being free, portable, scalable, and having short debug times. Some perceived disadvantages are too many distributions and being difficult to learn for newcomers.
- An overview of common Linux installation methods, partitioning disks, hardware configuration, and bootloaders like LILO that help Linux systems start
Ch02
Ch02Mike Qaissaunee The document discusses the graphical desktop environment in Linux. It describes the X Window System and its components including the X server, X clients, window managers and graphical libraries. It discusses the KDE and GNOME desktop interfaces, their components like panels and taskbars, and how to configure features. It also summarizes popular graphical utilities for file management, text editing, web browsing, productivity apps like OpenOffice, and email clients.
Introduction to linux at Introductory Bioinformatics Workshop
Introduction to linux at Introductory Bioinformatics WorkshopSetor Amuzu The document is an introduction to Linux, covering its definition, structure, and various distributions. It explores command-line interfaces, popular commands, file permissions, program installation, scripting, and common applications in bioinformatics. The conclusion emphasizes the advantages of mastering Linux for bioinformatics research despite the initial learning curve.
Introduction to unix
Introduction to unixsudheer yathagiri Unix is a multi-user, multi-tasking operating system developed since the 1960s, featuring a graphical user interface and requiring user knowledge for non-GUI operations. It consists of three main parts: the kernel, the shell, and programs, with the shell serving as the command line interface for users. The directory structure organizes files hierarchically, and users interact with the system through commands entered into a terminal.
Linux Administrator - The Linux Course on Eduonix
Linux Administrator - The Linux Course on EduonixPaddy Lock Daily tasks of a Linux administrator include package management, ensuring system security through regular backups and updating of software and patches, and monitoring system performance and anticipating potential issues. When issues do arise, Linux administrators must be able to effectively use documentation like man pages to troubleshoot problems. Choosing an appropriate Linux distribution depends on factors such as software compatibility, vendor support policies, and patch release schedules.
Linux: Basics OF Linux
Linux: Basics OF LinuxOmkar Walavalkar The document provides an overview of Unix basics, including the structure of the Unix file system, user shells, and essential utilities. It explains the functionality of shells, file hierarchy, common commands for managing files and directories, and file permissions. The summary emphasizes the similarity of Unix file systems and the use of special device files for communication with devices.
Introduction to Linux
Introduction to Linux Harish R This document provides an overview of a presentation on Linux programming and administration. It covers the history of Unix and Linux, files and directories in Linux, Linux installation, basic Linux commands, user and group administration, and LILO (Linux Loader). The document introduces key topics like Unix flavors, Linux distributions, partitioning and formatting disks for Linux installation, the file system hierarchy standard, and access permissions in Linux.
Presentation on nfs,afs,vfs
Presentation on nfs,afs,vfsPrakriti Dubey The document provides an overview of distributed file systems, specifically focusing on NFS (Network File System), AFS (Andrew File System), and VFS (Virtual File System). It covers their architectures, advantages, disadvantages, and key components such as caching mechanisms and security protocols. Additionally, the document discusses the differences between stateless and stateful servers in these systems and highlights the implementation and features of AFS as influenced by NFS.
A beginners introduction to unix
A beginners introduction to unixzafarali1981 This document provides an introduction to using UNIX. It outlines the course aims of explaining what UNIX is used for and how to navigate files and directories. The agenda covers a brief history of UNIX, logging on, working with files and directories, commands like vi editor, and customizing the login environment. It describes the kernel, commands/utilities, and shell that make up the UNIX operating system model. It also explains the file structure, special characters, and transferring files between Windows and UNIX.
Introduction about linux
Introduction about linuxABHISHEK KUMAR The document outlines the development and architecture of the Linux operating system, beginning with its origins in the 1980s as a free alternative to proprietary systems like DOS, Mac, and Unix. Key developments included Richard Stallman's GNU project and Linus Torvalds' creation of the Linux kernel, which received significant contributions from the global software community. The document also describes the Linux file management, process management, and system architecture, highlighting its advantages, such as stability and multi-user capabilities, as well as challenges like complexity and lower popularity compared to Windows.
Linux course details
Linux course detailscisco training This course covers all aspects of RHCE certification and Linux administration skills. It will teach students to administer a Linux system through topics like user management, filesystems, backups, networking services and security tools. The course is taught by experienced system engineers and includes hands-on training on a live domain with public IP addresses.
Unix ppt
Unix pptDr Rajiv Srivastava The Unix operating system, developed in 1969, serves as an interface between users and computer hardware, with communication facilitated through the shell, a command line interpreter. Its architecture comprises a kernel, shell, commands and utilities, and a structured file system, allowing multiuser and multitasking capabilities. Various Unix variants exist, and it supports numerous commands for file management, printing, compression, and searching, making it versatile for user needs.
Unix features, posix and single unix specification
Unix features, posix and single unix specificationsudha rani The document outlines various features of Unix, including its multiuser capability, multitasking, security, and portability. It explains the POSIX standard, which facilitates software portability across Unix systems, and describes how to utilize the Unix manual (man) for command documentation. Additionally, it details the structure of man pages, including essential sections such as name, synopsis, and description.
UNIX Operating System ppt
UNIX Operating System pptOECLIB Odisha Electronics Control Library The document provides an overview of the UNIX operating system through a seminar presentation. It discusses the history of UNIX from the 1970s to the 2000s, defines what UNIX is, describes common UNIX commands and the file system structure, and covers topics like memory management, interrupts, reasons for using UNIX, and some applications of UNIX like storage consulting and middleware/database administration. The presentation is intended to educate about the key aspects and functionality of the UNIX operating system.
Linux administration
Linux administrationYogesh Ks The document outlines a technical seminar on Linux administration presented by Yogesh K S. It discusses key topics like installing Linux, user and group management, security features like firewalls and SELinux, managing services, backups, and package management. The seminar covered essential admin tasks, tools, and commands for system installation, configuration, maintenance and security.
Linux administration training from hyderabad
Linux administration training from hyderabadFuturePoint Technologies The document provides an overview of a Linux Administration training program that covers topics such as Linux history, basics, file systems, users and permissions, processes, shells, text processing tools, and package management. It also lists various courses offered in areas like databases, networking, servers, and programming languages.
Unix fundamentals
Unix fundamentalsDima Gomaa Unix is an operating system that provides an interface between users and hardware. It manages storage, I/O devices, and allows for multi-tasking and multi-user access. The Unix operating system originated in 1969 and has evolved over time with contributions from various universities and companies. It uses a kernel to manage interactions between users, applications, and hardware. The shell is the interface that users interact with to run commands and programs on the system.
Chapter 21 - The Linux System
Chapter 21 - The Linux SystemWayne Jones Jnr Linux is an open-source operating system based on UNIX with a modular kernel. It uses processes, memory management and file systems similar to UNIX. The Linux kernel supports features like symmetric multiprocessing, virtual memory and loading of kernel modules. Popular Linux distributions package and distribute the Linux system along with utilities and applications.
Presentation1 linux os
Presentation1 linux osjoycoronado Linux is a freely distributed open source operating system based on Unix. It was developed in 1991 by Linus Torvalds and has gained popularity as a free alternative to proprietary operating systems. There are several popular Linux distributions including Red Hat Linux, Linux Mandrake, Debian/GNU, and SuSE Linux. These distributions bundle Linux with common software like the X Window System, KDE, and GNOME desktop environments. Hardware compatibility has improved with Linux supporting many modern components, though some proprietary drivers may need to be obtained from manufacturers.
The prophet's wives
The prophet's wivesRaja Waseem Akhtar The document discusses reasons why the Prophet Muhammad had multiple wives. It states that he had 12 wives total, with 10 being with him when he passed away. It argues that lust was not the reason, pointing out that he married his first wife Khadijah at age 25 and stayed with her alone for 25 years until her death when he was 52. It says the marriages were for political, social and religious reasons like spreading Islamic culture, strengthening bonds with companions, and having ties with other nations.
Chapter07 -- wa ns and remote connectivity
Chapter07 -- wa ns and remote connectivityRaja Waseem Akhtar The document discusses wide area networks (WANs) and remote connectivity. It defines WANs and their essential components. It describes various WAN topologies including bus, ring, star, mesh and tiered. It also discusses several WAN transmission methods like PSTN, ISDN, T-carriers, DSL, cable, and SONET. The document concludes with an overview of remote connectivity options like dial-up networking, remote control, terminal services, web portals and virtual private networks.
More Related Content
What's hot (20)
basic linux command (questions)
basic linux command (questions)Sukhraj Singh This document contains instructions for 9 Linux lab practical assignments covering basic Linux commands, utilities, file attributes, redirection/pipes, processes, environment configuration, and basic system administration. The practicals include commands to find file locations, view process information, set user account attributes, and manage files and folders. Students are to complete the tasks listed in each practical and document their responses.
Linux fundamentals Training
Linux fundamentals TrainingLove Steven The document summarizes a presentation on the history and usage of Linux. It discusses:
- The dominance of proprietary operating systems in the 1960s-1970s and the motivation to create a free and open-source alternative called UNIX.
- How Linus Torvalds began developing Linux in 1991 based on UNIX to create a free academic version, gradually adding features over several years.
- Key advantages of Linux including being free, portable, scalable, and having short debug times. Some perceived disadvantages are too many distributions and being difficult to learn for newcomers.
- An overview of common Linux installation methods, partitioning disks, hardware configuration, and bootloaders like LILO that help Linux systems start
Ch02
Ch02Mike Qaissaunee The document discusses the graphical desktop environment in Linux. It describes the X Window System and its components including the X server, X clients, window managers and graphical libraries. It discusses the KDE and GNOME desktop interfaces, their components like panels and taskbars, and how to configure features. It also summarizes popular graphical utilities for file management, text editing, web browsing, productivity apps like OpenOffice, and email clients.
Introduction to linux at Introductory Bioinformatics Workshop
Introduction to linux at Introductory Bioinformatics WorkshopSetor Amuzu The document is an introduction to Linux, covering its definition, structure, and various distributions. It explores command-line interfaces, popular commands, file permissions, program installation, scripting, and common applications in bioinformatics. The conclusion emphasizes the advantages of mastering Linux for bioinformatics research despite the initial learning curve.
Introduction to unix
Introduction to unixsudheer yathagiri Unix is a multi-user, multi-tasking operating system developed since the 1960s, featuring a graphical user interface and requiring user knowledge for non-GUI operations. It consists of three main parts: the kernel, the shell, and programs, with the shell serving as the command line interface for users. The directory structure organizes files hierarchically, and users interact with the system through commands entered into a terminal.
Linux Administrator - The Linux Course on Eduonix
Linux Administrator - The Linux Course on EduonixPaddy Lock Daily tasks of a Linux administrator include package management, ensuring system security through regular backups and updating of software and patches, and monitoring system performance and anticipating potential issues. When issues do arise, Linux administrators must be able to effectively use documentation like man pages to troubleshoot problems. Choosing an appropriate Linux distribution depends on factors such as software compatibility, vendor support policies, and patch release schedules.
Linux: Basics OF Linux
Linux: Basics OF LinuxOmkar Walavalkar The document provides an overview of Unix basics, including the structure of the Unix file system, user shells, and essential utilities. It explains the functionality of shells, file hierarchy, common commands for managing files and directories, and file permissions. The summary emphasizes the similarity of Unix file systems and the use of special device files for communication with devices.
Introduction to Linux
Introduction to Linux Harish R This document provides an overview of a presentation on Linux programming and administration. It covers the history of Unix and Linux, files and directories in Linux, Linux installation, basic Linux commands, user and group administration, and LILO (Linux Loader). The document introduces key topics like Unix flavors, Linux distributions, partitioning and formatting disks for Linux installation, the file system hierarchy standard, and access permissions in Linux.
Presentation on nfs,afs,vfs
Presentation on nfs,afs,vfsPrakriti Dubey The document provides an overview of distributed file systems, specifically focusing on NFS (Network File System), AFS (Andrew File System), and VFS (Virtual File System). It covers their architectures, advantages, disadvantages, and key components such as caching mechanisms and security protocols. Additionally, the document discusses the differences between stateless and stateful servers in these systems and highlights the implementation and features of AFS as influenced by NFS.
A beginners introduction to unix
A beginners introduction to unixzafarali1981 This document provides an introduction to using UNIX. It outlines the course aims of explaining what UNIX is used for and how to navigate files and directories. The agenda covers a brief history of UNIX, logging on, working with files and directories, commands like vi editor, and customizing the login environment. It describes the kernel, commands/utilities, and shell that make up the UNIX operating system model. It also explains the file structure, special characters, and transferring files between Windows and UNIX.
Introduction about linux
Introduction about linuxABHISHEK KUMAR The document outlines the development and architecture of the Linux operating system, beginning with its origins in the 1980s as a free alternative to proprietary systems like DOS, Mac, and Unix. Key developments included Richard Stallman's GNU project and Linus Torvalds' creation of the Linux kernel, which received significant contributions from the global software community. The document also describes the Linux file management, process management, and system architecture, highlighting its advantages, such as stability and multi-user capabilities, as well as challenges like complexity and lower popularity compared to Windows.
Linux course details
Linux course detailscisco training This course covers all aspects of RHCE certification and Linux administration skills. It will teach students to administer a Linux system through topics like user management, filesystems, backups, networking services and security tools. The course is taught by experienced system engineers and includes hands-on training on a live domain with public IP addresses.
Unix ppt
Unix pptDr Rajiv Srivastava The Unix operating system, developed in 1969, serves as an interface between users and computer hardware, with communication facilitated through the shell, a command line interpreter. Its architecture comprises a kernel, shell, commands and utilities, and a structured file system, allowing multiuser and multitasking capabilities. Various Unix variants exist, and it supports numerous commands for file management, printing, compression, and searching, making it versatile for user needs.
Unix features, posix and single unix specification
Unix features, posix and single unix specificationsudha rani The document outlines various features of Unix, including its multiuser capability, multitasking, security, and portability. It explains the POSIX standard, which facilitates software portability across Unix systems, and describes how to utilize the Unix manual (man) for command documentation. Additionally, it details the structure of man pages, including essential sections such as name, synopsis, and description.
UNIX Operating System ppt
UNIX Operating System pptOECLIB Odisha Electronics Control Library The document provides an overview of the UNIX operating system through a seminar presentation. It discusses the history of UNIX from the 1970s to the 2000s, defines what UNIX is, describes common UNIX commands and the file system structure, and covers topics like memory management, interrupts, reasons for using UNIX, and some applications of UNIX like storage consulting and middleware/database administration. The presentation is intended to educate about the key aspects and functionality of the UNIX operating system.
Linux administration
Linux administrationYogesh Ks The document outlines a technical seminar on Linux administration presented by Yogesh K S. It discusses key topics like installing Linux, user and group management, security features like firewalls and SELinux, managing services, backups, and package management. The seminar covered essential admin tasks, tools, and commands for system installation, configuration, maintenance and security.
Linux administration training from hyderabad
Linux administration training from hyderabadFuturePoint Technologies The document provides an overview of a Linux Administration training program that covers topics such as Linux history, basics, file systems, users and permissions, processes, shells, text processing tools, and package management. It also lists various courses offered in areas like databases, networking, servers, and programming languages.
Unix fundamentals
Unix fundamentalsDima Gomaa Unix is an operating system that provides an interface between users and hardware. It manages storage, I/O devices, and allows for multi-tasking and multi-user access. The Unix operating system originated in 1969 and has evolved over time with contributions from various universities and companies. It uses a kernel to manage interactions between users, applications, and hardware. The shell is the interface that users interact with to run commands and programs on the system.
Chapter 21 - The Linux System
Chapter 21 - The Linux SystemWayne Jones Jnr Linux is an open-source operating system based on UNIX with a modular kernel. It uses processes, memory management and file systems similar to UNIX. The Linux kernel supports features like symmetric multiprocessing, virtual memory and loading of kernel modules. Popular Linux distributions package and distribute the Linux system along with utilities and applications.
Presentation1 linux os
Presentation1 linux osjoycoronado Linux is a freely distributed open source operating system based on Unix. It was developed in 1991 by Linus Torvalds and has gained popularity as a free alternative to proprietary operating systems. There are several popular Linux distributions including Red Hat Linux, Linux Mandrake, Debian/GNU, and SuSE Linux. These distributions bundle Linux with common software like the X Window System, KDE, and GNOME desktop environments. Hardware compatibility has improved with Linux supporting many modern components, though some proprietary drivers may need to be obtained from manufacturers.
Viewers also liked (20)
The prophet's wives
The prophet's wivesRaja Waseem Akhtar The document discusses reasons why the Prophet Muhammad had multiple wives. It states that he had 12 wives total, with 10 being with him when he passed away. It argues that lust was not the reason, pointing out that he married his first wife Khadijah at age 25 and stayed with her alone for 25 years until her death when he was 52. It says the marriages were for political, social and religious reasons like spreading Islamic culture, strengthening bonds with companions, and having ties with other nations.
Chapter07 -- wa ns and remote connectivity
Chapter07 -- wa ns and remote connectivityRaja Waseem Akhtar The document discusses wide area networks (WANs) and remote connectivity. It defines WANs and their essential components. It describes various WAN topologies including bus, ring, star, mesh and tiered. It also discusses several WAN transmission methods like PSTN, ISDN, T-carriers, DSL, cable, and SONET. The document concludes with an overview of remote connectivity options like dial-up networking, remote control, terminal services, web portals and virtual private networks.
Chapter04 -- network protocols
Chapter04 -- network protocolsRaja Waseem Akhtar The document summarizes key network protocols including TCP/IP, IPX/SPX, NetBIOS, and AppleTalk. It describes the layers of the TCP/IP protocol suite and how they correspond to the OSI model. It also discusses important TCP/IP protocols like TCP, IP, UDP, ICMP, and ARP as well as addressing schemes, dynamic host configuration protocol (DHCP), and port numbers.
Sol linux cmg-t_1_1.pptx
Sol linux cmg-t_1_1.pptxBob Sneed The document provides an overview of a 3-part training session on Unix/Linux performance and capacity management. It introduces the presenters, Adrian Cockcroft and Bob Sneed, and outlines the topics to be covered in each session. Session 1 will cover key definitions and concepts in capacity planning as well as important laws like Little's Law, Amdahl's Law, and Moore's Law. It will also discuss workload characterization and the importance of understanding application workloads.
Hands-on ethernet driver
Hands-on ethernet driverSUSE Labs Taipei This document provides an overview of the data structures and functions used to implement ethernet drivers in the Linux kernel. It discusses the net_device and sk_buff structures that represent network interfaces and packets. It also describes how the driver interacts with the kernel via polling, interrupts, and NAPI to handle reception and transmission of frames. Finally, it provides an example of the key components needed for a simple ethernet driver, including initialization, setup, open/close, transmission, and reception functions.
Linux or unix interview questions
Linux or unix interview questionsTeja Bheemanapally The document discusses Linux/Unix interview questions and answers. It covers topics such as the GRUB bootloader, the Linux boot process, user profile files, changing the default runlevel, displaying user information with the finger command, inode numbers, increasing disk read performance, password expiration times, locking user passwords, default shells, user attributes defined in /etc/login.defs, changing the system's authentication method, modifying file attributes with chattr, network interface configuration files, changing network interface settings, the DNS configuration file, exporting NFS directories, checking open ports, soft vs hard links, setting expired passwords, restricting file insertion, displaying or killing processes accessing files/folders, killing all processes for a user, daily system analysis reports
Linux Ethernet device driver
Linux Ethernet device driver艾鍗科技 The document discusses Ethernet device drivers in Linux. It describes the driver architecture, Ethernet packet format, driver development process, and important data structures like net_device and sk_buff. It provides examples of initializing a driver, probing hardware, uploading/downloading data using callbacks, interrupt handling, and buffer management. The key steps are registering the driver, allocating network devices, setting callbacks, and using sk_buff objects to transfer packets between layers.
Networking in linux
Networking in linuxVarnnit Jain The document provides an overview of networking in Linux, explaining basic concepts such as network devices, interfaces, and essential configuration commands. It details how to manage network interfaces, check connectivity, configure IP addresses, and troubleshoot network issues using various command-line tools. Additionally, it includes a practical scenario for setting up networking between two systems with specific IP addresses.
Chapter11 -- networking with tcpip and the internet
Chapter11 -- networking with tcpip and the internetRaja Waseem Akhtar This chapter discusses TCP/IP network design including subnetting, CIDR, and NAT. It describes protocols for email delivery and access like SMTP, POP, and IMAP. It also explains using TCP/IP networks for voice transmission (VoIP) and provides details on TCP/IP utilities like netstat, nslookup, traceroute, and ifconfig that can be used for network discovery and troubleshooting.
Ch20 system administration
Ch20 system administration Raja Waseem Akhtar The document discusses name resolution services including NIS, DNS, and how they work together. NIS is a local name service, while DNS is global and hierarchical. It describes the components and configuration of DNS, including root, top-level, and subordinate domains as well as master, slave and caching nameservers. The document then provides an example of the name resolution process between a client, local nameserver, and external domain.
Ch05 system administration
Ch05 system administration Raja Waseem Akhtar The document discusses various methods for installing operating systems. It covers hardware requirements, preparing for installation, different installation types including desktop, server and dual-boot installations. It also discusses Windows, Linux, Solaris and BSD installations and outlines unattended network installations using answer files.
Ch04 system administration
Ch04 system administration Raja Waseem Akhtar The document discusses the boot sequence of a computer system. It examines each step including the PROM monitor, boot block, secondary boot loader, the OS kernel, and start-up scripts. The administrator should understand this boot process as well as how to modify the boot sequence, select alternate devices, and properly shut down the system.
Ch08 system administration
Ch08 system administration Raja Waseem Akhtar The document discusses disk drives and file systems. It provides an overview of disk components like platters, heads, and sectors. It explains disk geometry including cylinders, tracks, and how addressing schemes allow unique identification of each sector. Different disk interfaces like SCSI, IDE, and Fibre Channel are covered. The document also discusses disk formatting, partitioning, and techniques for optimizing performance like load balancing and RAID.
Ch10
Ch10Raja Waseem Akhtar The document discusses user account management tasks for system administrators, including creating login names, assigning home directories and user IDs, setting passwords and shells, and formatting the password file. It describes challenges around reusable passwords and methods to improve security such as password aging, lockouts for failed attempts, and one-time password tokens.
Ch12
Ch12Raja Waseem Akhtar This document discusses disk and file system concepts including:
- Creating file systems using newfs and how it connects to mkfs
- Mounting file systems manually, via fstab, and using volume manager
- Identifying mounted file systems using mount, df, and mnttab
- Repairing file systems using fsck and handling recoverable vs unrecoverable damage
- Benefits of journaling file systems like reduced reboot time and data retention
Chapter10 -- netware-based networking
Chapter10 -- netware-based networkingRaja Waseem Akhtar The document discusses NetWare, a network operating system developed by Novell. It provides an overview of NetWare's history and versions. The key advantages of NetWare include centralized management, support for multiple protocols, and integration with other network operating systems. The document also describes planning and installing a NetWare server, including hardware requirements, the installation process, establishing user accounts and groups, and providing client access and interoperability with other operating systems.
Ch24 system administration
Ch24 system administration Raja Waseem Akhtar The document discusses performance analysis and tuning. It provides terminology related to performance monitoring and discusses general rules for performance tuning. It recommends right-sizing systems, determining hardware requirements, monitoring systems to establish baselines, and making one change at a time while monitoring the impact. It also discusses tools for monitoring CPU, memory, disk, and network performance on Unix and Windows systems.
Ch23 system administration
Ch23 system administration Raja Waseem Akhtar This document discusses automating system administration tasks through shell scripting. It begins by outlining common tasks that can be automated, such as installing patches, managing accounts and configuration files. It then covers tools for automation like cron, find, and rdist. The rest of the document discusses different methods for distributing system information, such as the push and pull methods, and provides examples of rdist and package files used for automation.
Ch11
Ch11Raja Waseem Akhtar The document discusses system security and provides seven common sense rules for security. It covers account security, file permissions, data encryption, single user security, dialup modems, security tools, and an overview of viruses, trojans, and worms. Monitoring logs, using security scanning tools, and educating yourself on security best practices are emphasized as important ways to help secure systems.
Chapter12 Managing And Implementing Backups And Disaster Recovery
Chapter12 Managing And Implementing Backups And Disaster RecoveryRaja Waseem Akhtar The document discusses various methods for managing backups and disaster recovery in a Microsoft Windows Server 2003 environment. It covers planning backups, using the backup utility to perform different types of backups including system state backups, configuring shadow copies and previous versions, setting up automated system recovery backups, using advanced startup options like safe mode and last known good configuration, and installing/using the recovery console for system recovery tasks. Activities are provided to demonstrate configuring and testing many of these backup and disaster recovery features.
Ad
Similar to Chapter09 -- networking with unix and linux (20)
Linux.ppt
Linux.ppt onu9 This document provides an overview of Linux including:
- Different pronunciations of Linux and the origins of each pronunciation.
- A definition of Linux as a generic term for Unix-like operating systems with graphical user interfaces.
- Why Linux is significant as a powerful, free, and customizable operating system that runs on multiple hardware platforms.
- An introduction to key Linux concepts like multi-user systems, multiprocessing, multitasking and open source software.
- Examples of common Linux commands for file handling, text processing, and system administration.
Linux Systems Programming: Ubuntu Installation and Configuration
Linux Systems Programming: Ubuntu Installation and ConfigurationRashidFaridChishti The document outlines a comprehensive course on Linux system programming, detailing prerequisites, recommended virtual machines, and various programming topics including file structures, process management, and user management commands. It also discusses the history and evolution of Unix and Linux, as well as specific commands and configurations for different tasks such as file editing, software installation, and managing system services. Additionally, it provides practical commands for working with Linux environments, including user creation, process control, and setting up network services.
Unix_Introduction_BCA.pptx the very basi
Unix_Introduction_BCA.pptx the very basiPriyadarshini648418 This document provides an introduction and overview of the UNIX operating system. It discusses that UNIX is an operating system, like Windows, that manages communication between software and hardware. Popular versions of UNIX include Linux and Android. The document outlines reasons for using UNIX such as reliability, low/no cost, and open source access. It describes the core components of UNIX including the kernel, bootloader, daemons, and shells. Key features like being portable, multi-user, and providing security are highlighted. Common UNIX commands and utilities are listed along with file permissions, redirection, pipes, and filters.
Unix/Linux Basic Commands and Shell Script
Unix/Linux Basic Commands and Shell Scriptsbmguys - Linux originated as a clone of the UNIX operating system. Key developers included Linus Torvalds and developers from the GNU project.
- Linux is open source, multi-user, and can run on a variety of hardware. It includes components like the Linux kernel, shell, terminal emulator, and desktop environments.
- The document provides information on common Linux commands, files, users/groups, permissions, and startup scripts. It describes the Linux file system and compression/archiving utilities.
prateekporwal
prateekporwalprateekporwal This document provides an overview of network management with Linux. It discusses key topics such as:
- Why Linux is significant, including its growing popularity, power, ability to run on multiple hardware platforms, and speed and stability.
- The basic Linux system structure including user commands, the shell for interpreting commands, and the kernel for managing hardware resources.
- Common shells like Bash used for calling commands and programming.
- Basic Linux file system organization with directories, pathnames, and special filenames.
- File permissions including read, write, and execute permissions for owners, groups and others.
- Virtual file systems and how they provide a consistent view of data storage.
- User management with tools like useradd
Linux introductory-course-day-1
Linux introductory-course-day-1Julio Pulido This document provides an overview of file administration in Linux. It describes the three types of files in Linux - ordinary disk files which contain user data, special files which represent devices, and directory files which contain other files and directories. It outlines guidelines for naming files and directories, explaining which characters to avoid. It also introduces the file command for determining a file's type and describes the basic Linux directory structure with files and directories organized in a tree format.
Basics of Linux Commands, Git and Github
Basics of Linux Commands, Git and GithubDevang Garach The document provides an overview of Linux commands, Git, and GitHub, covering the history, file system structure, and basic commands for Linux and Git. It explains Linux as an open-source operating system with two main components: the kernel and the shell, as well as essential commands for file management and system administration. Additionally, it outlines Git as a version control system developed by Linus Torvalds, detailing commands for creating and managing repositories.
cisco
ciscoedomaldo Linux is a fully-featured open source operating system based on Unix. It was created by Linus Torvalds in 1991 and has since grown in popularity. Linux uses a kernel to manage hardware resources and runs on multiple hardware platforms. Users interact with Linux through a shell and can execute commands, manage files and directories, and perform other tasks. Common Linux commands include ls, cd, pwd, cp, and more.
3. intro
3. introHarsh Shrimal Linux is a fully-networked, multi-user, multitasking operating system similar to Unix. It was created in 1991 by Linus Torvalds and is now used widely due to its low cost, stability, and ability to run on different hardware platforms. Linux uses a command line interface where users log in and issue commands to perform tasks like copying files, installing software, and checking system resources. Common commands include ls to list files, cd to change directories, and man to view manuals.
Introduction 2 linux
Introduction 2 linuxPapu Kumar The document is an introduction to Linux, covering its definition, history, and many functionalities such as command-line interface, file permissions, and installing programs. It explains Linux distributions, popular commands, and their applications in bioinformatics, emphasizing the power of command-line tools. The conclusion encourages learning Linux for bioinformatics research, highlighting its open-source nature and flexibility.
linux-lecture1.ppt
linux-lecture1.pptNikhil Raut Here are the steps to complete the assignment:
1. Login as guest user (password is guest)
2. To find the present working directory: pwd
3. The root directory structure includes: /bin, /dev, /etc, /home, /lib, /root, /sbin, /tmp, /usr etc.
4. A few commands in /bin are: ls, cp, mv, rm, chmod. Commands in /sbin are: ifconfig, route, iptables etc.
5. The guest home directory is /home/guest
6. The permissions of the guest home directory are: drwxr-xr-x
7. To create a new
Linux: An Unbeaten Empire
Linux: An Unbeaten EmpireYogesh Sharma The document provides an overview of Red Hat Enterprise Linux Server, covering its history, comparison to UNIX, and key features. It details the UNIX and Linux file system structures, user permissions, and basic command-line commands. Additionally, it discusses various Linux services and servers such as DNS, DHCP, FTP, and more, highlighting the widespread use of Linux in banking and other industries.
LINUX
LINUXARJUN Linux is an open-source operating system that provides free and secure software. It allows applications and users to access computer devices and functions through the kernel, which manages communication between hardware, software, and processes. Files, directories, programs, and devices are all treated as files in the Linux file system hierarchy, accessed through commands like ls, mkdir, and rmdir.
Test Bank for Linux+ and LPIC-1 Guide to Linux Certification, 5th Edition Jas...
Test Bank for Linux+ and LPIC-1 Guide to Linux Certification, 5th Edition Jas...kuervoingvar25 Test Bank for Linux+ and LPIC-1 Guide to Linux Certification, 5th Edition Jason Eckert
Test Bank for Linux+ and LPIC-1 Guide to Linux Certification, 5th Edition Jason Eckert
Test Bank for Linux+ and LPIC-1 Guide to Linux Certification, 5th Edition Jason Eckert
Introduction to Unix
Introduction to UnixSudharsan S Linux is an open source operating system created by Linus Torvalds in 1991. It uses a Linux kernel and includes many common Unix tools. Linux is free to use and modify due to its open source licensing. It runs on many hardware platforms and is growing in popularity for servers, desktops, and embedded systems due to its low cost, stability, and security. Users can download Linux from distributions like Red Hat which package the Linux kernel with additional software and support.
Redhat Linux server administration industrial training report.
Redhat Linux server administration industrial training report.AlokGupta336 The document is a practical training report submitted by Alok Gupta to partial fulfillment of the degree of Bachelor of Technology in Computer Science & Engineering. It discusses Linux server administration and thanks those who provided guidance during the training period. It includes an abstract stating that Linux server administration is important to ensure proper functioning of servers to provide client services and deal with high traffic. It also lists various chapter titles that will be covered in the report related to Linux introduction, Red Hat installation, user and file management, disk partitioning, package management, server needs, and descriptions of specific server types.
Linux Administration
Linux AdministrationHarish1983 The document discusses various topics related to Linux administration. It covers Unix system architecture, the Linux command line, files and directories, running programs, wildcards, text editors, shells, command syntax, filenames, command history, paths, hidden files, home directories, making directories, copying and renaming files, and more. It provides an overview of key Linux concepts and commands for system administration.
Linux Administration
Linux Administrationharirxg The document provides a comprehensive overview of Linux administration, covering topics such as the Unix philosophy, Linux system architecture, and command line usage. It explains file management commands, process management, user permissions, file systems, and backup strategies, along with details about shell programming and text editors. Additionally, it addresses navigating the manual pages, managing cron jobs, and understanding graphical versus text interfaces in Linux environments.
Ad
More from Raja Waseem Akhtar (20)
God is Great
God is GreatRaja Waseem Akhtar This document takes the reader on a trip through scales of size from micro to macro, jumping distances by factors of 10. It starts at 1 meter and increases the scale up to 10 million light years, observing different objects that come into view like planets, galaxies, and nebulae. It then returns back down to the micro scale, decreasing distances by factors of 10 until it reaches the scale of femtometers, observing subatomic particles. The document emphasizes the constancy of natural laws across all scales and encourages contemplating humanity's place in the vast universe.
Namaz ka tareeqa
Namaz ka tareeqaRaja Waseem Akhtar 1) Salat Tasbeeh is a four rakat prayer where in each posture of the rakat (standing, bowing, prostrating, sitting), the phrase "Subhan Allah-e-Wal Hamd-o-lillah-e-Wala-Ilaha -Ilallaho-Wallaho-Akbar" is uttered a specified number of times.
2) In each rakat, the phrase must be uttered 75 times total across the seven postures - with 15 times while standing after recitation, 10 times while bowing, 10 times in each prostration, and 10 times while sitting between prostrations.
3) The specified numbers of times the phrase
Aayat ul qursi
Aayat ul qursiRaja Waseem Akhtar This document discusses the benefits of reciting Aayathul Qursi. It states that reciting it when leaving the house will result in 70,000 angels protecting from all sides. Reciting it 40 times daily at sunset earns the reward of 40 Hajj pilgrimages. Reciting it before bed will result in an angel guarding the person until morning. Reciting it after returning home and after ablution increases a person's rank with every word. Sharing it with others also provides reward from God.
Indiansoldiers
IndiansoldiersRaja Waseem Akhtar Indian soldiers who were wounded fighting in World War 1 on the Western Front were sent to England for treatment. Many towns on the south coast of England, including Brighton, Bournemouth, Brockenhurst and New Milton helped care for the large numbers of wounded Indian soldiers. It is estimated that over 64,000 Indian soldiers died or went missing and more than 65,000 were wounded by the end of the war.
2ªwwii how did it fought
2ªwwii how did it foughtRaja Waseem Akhtar World War II involved major battles in the European Theater between November 1942 and May 1945. Allied forces led by generals Montgomery, Clark, Alexander, Patton, Bradley, and Devers fought against Axis forces in campaigns across Western, Central, and Eastern areas of engagement. Through coordinated operations between multiple army groups consisting of airborne, armored, and infantry divisions, the Allies were ultimately able to defeat Nazi Germany.
Fun with EMC2
Fun with EMC2Raja Waseem Akhtar 1) A liter of water contains enough mass to produce 9 x 1016 Joules of energy if converted entirely, which could power a 1 Watt lightbulb for around 3 billion years.
2) The sun produces its energy through nuclear fusion, where hydrogen nuclei fuse into helium. A little bit of mass is lost in this process, appearing as energy according to E=mc2.
3) Scientists are trying to create controlled nuclear fusion on Earth for a sustainable energy source, but it requires maintaining temperatures over 15 million degrees, which is technically challenging.
Discover the discovery
Discover the discoveryRaja Waseem Akhtar This document provides a high-level overview of the shuttle processing steps before flight, including:
1) The external tank arrives by barge and is moved to the Vertical Assembly Building (VAB) for preparation.
2) Solid rocket boosters and shuttle engines are attached to the external tank in the VAB.
3) The shuttle is then lifted and attached to the external tank.
4) The payload is prepared separately in the Payload Preparation Room and then transported to the launch pad for insertion into the shuttle.
Solaris servers sec
Solaris servers secRaja Waseem Akhtar This document provides guidance on securing Solaris servers through hardening and configuration best practices. It recommends removing unnecessary software and services, enabling detailed system logging, installing the latest security patches regularly, and configuring services like sendmail securely based on checklists from SANS and CIS. Key steps include a minimal OS installation, removing unneeded packages and services, setting secure permissions and logging levels, and installing tools like Tripwire and SSH.
Chapter16 - the internet and its tools
Chapter16 - the internet and its toolsRaja Waseem Akhtar The document provides a history of the internet and explains how it works and some common tools used on it. It began as a US military network called ARPANET and later expanded. The Domain Name System translates website names to IP addresses. Web browsers allow viewing web pages while email and listservs allow communication. Search engines and portals help users find information and HTML defines webpage formatting.
Chapter15 -- implementing and managing networks
Chapter15 -- implementing and managing networksRaja Waseem Akhtar 1. Project management is important for network implementation projects and involves determining feasibility, assessing needs, setting goals, planning tasks and timelines, managing communication, and contingency planning.
2. Network management includes monitoring performance and faults, tracking assets, and regularly maintaining and upgrading both hardware and software.
3. Careful planning is required for any network changes, including software updates, client and server upgrades, and adding or replacing physical equipment. Changes must be thoroughly tested and plans should allow for reverting changes if needed.
Chapter14 -- networking security
Chapter14 -- networking securityRaja Waseem Akhtar This document summarizes security risks and mitigation techniques for computer networks. It discusses risks associated with people, transmission, hardware, protocols, software, and internet access. It also outlines the goals of an effective security policy and describes physical security, firewalls, proxy servers, remote access, network operating system security, encryption, and wireless security. Key risks include social engineering, unauthorized access, transmission interception, insecure protocols, denial-of-service attacks, and improper firewall/remote access configurations. The chapter recommends conducting security audits, restricting physical access, using firewalls/proxy servers for access control, enforcing secure authentication/access, and encrypting sensitive data and wireless transmissions.
Chapter13 -- ensuring integrity and availability
Chapter13 -- ensuring integrity and availabilityRaja Waseem Akhtar The document discusses ensuring integrity and availability in networks. It covers viruses, fault tolerance techniques like redundant components and UPS systems, data backup strategies, and disaster recovery plans. Integrity ensures the soundness of network programs, data, services and connections, while availability refers to consistent access. General guidelines include limiting administrator access and regularly monitoring performance.
Chapter12 -- troubleshooting networking problems
Chapter12 -- troubleshooting networking problemsRaja Waseem Akhtar The document discusses a methodology for effectively troubleshooting networking problems which includes identifying symptoms, determining the scope of the problem, establishing what has changed, selecting the most probable cause, verifying physical and logical connectivity, recognizing potential solution effects, implementing and testing a solution, and documenting the problem and resolution. It also discusses various software and hardware tools that can be used to diagnose networking issues, including cable testers, network monitors, protocol analyzers, and wireless network testing tools.
Chapter08 -- network operating systems and windows server 2003-based networking
Chapter08 -- network operating systems and windows server 2003-based networkingRaja Waseem Akhtar This chapter discusses network operating systems and Windows Server 2003. It covers the functions of a network OS like managing resources and users. Windows Server 2003 editions are examined along with installation requirements. Features like Active Directory, file systems, and integration with other OSs are described. The chapter concludes with instructions for a basic Windows Server 2003 installation and configuration of users and groups.
Chapter06 -- topologies and access methods
Chapter06 -- topologies and access methodsRaja Waseem Akhtar This document provides an overview of network topologies and access methods. It describes physical topologies like bus, ring, and star, as well as hybrid topologies like star-wired ring and star-wired bus. It also covers backbone structures, switching methods, Ethernet, Token Ring, FDDI, ATM, and wireless networking standards like 802.11a, 802.11b, and 802.11g. Key aspects like frames, association, and quality of service are discussed for different network types.
Chapter05 -- networking hardware
Chapter05 -- networking hardwareRaja Waseem Akhtar This document provides an overview of various networking hardware components, including their functions and how they operate at different layers of the OSI model. It describes network adapters, repeaters, hubs, bridges, switches, routers, and gateways. It covers topics such as installing and configuring network adapters, choosing the right adapter, VLANs, and common routing protocols.
Chapter03 a - network media
Chapter03 a - network mediaRaja Waseem Akhtar This document discusses networking basics, including the two main types of networks (circuit-switched and packet-switched), how data is transmitted over networks using baseband and broadband signaling, common factors that can distort transmissions like attenuation and interference, different types of transmission media like copper cables, fiber optic, and wireless, and the function of the network interface card.
Recently uploaded (20)
Viral>Wondershare Filmora 14.5.18.12900 Crack Free Download
Viral>Wondershare Filmora 14.5.18.12900 Crack Free DownloadPuppy jhon ➡ 🌍📱👉COPY & PASTE LINK👉👉👉 ➤ ➤➤ https://drfiles.net/
Wondershare Filmora Crack is a user-friendly video editing software designed for both beginners and experienced users.
“Why It’s Critical to Have an Integrated Development Methodology for Edge AI,...
“Why It’s Critical to Have an Integrated Development Methodology for Edge AI,...Edge AI and Vision Alliance For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2025/06/why-its-critical-to-have-an-integrated-development-methodology-for-edge-ai-a-presentation-from-lattice-semiconductor/
Sreepada Hegade, Director of ML Systems and Software at Lattice Semiconductor, presents the “Why It’s Critical to Have an Integrated Development Methodology for Edge AI” tutorial at the May 2025 Embedded Vision Summit.
The deployment of neural networks near sensors brings well-known advantages such as lower latency, privacy and reduced overall system cost—but also brings significant challenges that complicate development. These challenges can be addressed effectively by choosing the right solution and design methodology. The low-power FPGAs from Lattice are well poised to enable efficient edge implementation of models, while Lattice’s proven development methodology helps to mitigate the challenges and risks associated with edge model deployment.
In this presentation, Hegade explains the importance of an integrated framework that tightly consolidates different aspects of edge AI development, including training, quantization of networks for edge deployment, integration with sensors and inferencing. He also illustrates how Lattice’s simplified tool flow helps to achieve the best trade-off between power, performance and efficiency using low-power FPGAs for edge deployment of various AI workloads.
Mastering AI Workflows with FME - Peak of Data & AI 2025
Mastering AI Workflows with FME - Peak of Data & AI 2025Safe Software Harness the full potential of AI with FME: From creating high-quality training data to optimizing models and utilizing results, FME supports every step of your AI workflow. Seamlessly integrate a wide range of models, including those for data enhancement, forecasting, image and object recognition, and large language models. Customize AI models to meet your exact needs with FME’s powerful tools for training, optimization, and seamless integration
“Addressing Evolving AI Model Challenges Through Memory and Storage,” a Prese...
“Addressing Evolving AI Model Challenges Through Memory and Storage,” a Prese...Edge AI and Vision Alliance For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2025/06/addressing-evolving-ai-model-challenges-through-memory-and-storage-a-presentation-from-micron/
Wil Florentino, Senior Segment Marketing Manager at Micron, presents the “Addressing Evolving AI Model Challenges Through Memory and Storage” tutorial at the May 2025 Embedded Vision Summit.
In the fast-changing world of artificial intelligence, the industry is deploying more AI compute at the edge. But the growing diversity and data footprint of transformers and models such as large language models and large multimodal models puts a spotlight on memory performance and data storage capacity as key bottlenecks. Enabling the full potential of AI in industries such as manufacturing, automotive, robotics and transportation will require us to find efficient ways to deploy this new generation of complex models.
In this presentation, Florentino explores how memory and storage are responding to this need and solving complex issues in the AI market. He examines the storage capacity and memory bandwidth requirements of edge AI use cases ranging from tiny devices with severe cost and power constraints to edge servers, and he explains how new memory technologies such as LPDDR5, LPCAMM2 and multi-port SSDs are helping system developers to meet these challenges.
Reducing Conflicts and Increasing Safety Along the Cycling Networks of East-F...
Reducing Conflicts and Increasing Safety Along the Cycling Networks of East-F...Safe Software In partnership with the Belgian Province of East-Flanders this project aimed to reduce conflicts and increase safety along a cycling route between the cities of Oudenaarde and Ghent. To achieve this goal, the current cycling network data needed some extra key information, including: Speed limits for segments, Access restrictions for different users (pedestrians, cyclists, motor vehicles, etc.), Priority rules at intersections. Using a 360° camera and GPS mounted on a measuring bicycle, we collected images of traffic signs and ground markings along the cycling lanes building up mobile mapping data. Image recognition technologies identified the road signs, creating a dataset with their locations and codes. The data processing entailed three FME workspaces. These included identifying valid intersections with other networks (e.g., roads, railways), creating a topological network between segments and intersections and linking road signs to segments and intersections based on proximity and orientation. Additional features, such as speed zones, inheritance of speed and access to neighbouring segments were also implemented to further enhance the data. The final results were visualized in ArcGIS, enabling analysis for the end users. The project provided them with key insights, including statistics on accessible road segments, speed limits, and intersection priorities. These will make the cycling paths more safe and uniform, by reducing conflicts between users.
OWASP Barcelona 2025 Threat Model Library
OWASP Barcelona 2025 Threat Model LibraryPetraVukmirovic Threat Model Library Launch at OWASP Barcelona 2025
https://owasp.org/www-project-threat-model-library/
Data Validation and System Interoperability
Data Validation and System InteroperabilitySafe Software A non-profit human services agency with specialized health record and billing systems. Challenges solved include access control integrations from employee electronic HR records, multiple regulations compliance, data migrations, benefits enrollments, payroll processing, and automated reporting for business intelligence and analysis.
Bridging the divide: A conversation on tariffs today in the book industry - T...
Bridging the divide: A conversation on tariffs today in the book industry - T...BookNet Canada A collaboration-focused conversation on the recently imposed US and Canadian tariffs where speakers shared insights into the current legislative landscape, ongoing advocacy efforts, and recommended next steps. This event was presented in partnership with the Book Industry Study Group.
Link to accompanying resource: https://bnctechforum.ca/sessions/bridging-the-divide-a-conversation-on-tariffs-today-in-the-book-industry/
Presented by BookNet Canada and the Book Industry Study Group on May 29, 2025 with support from the Department of Canadian Heritage.
“Key Requirements to Successfully Implement Generative AI in Edge Devices—Opt...
“Key Requirements to Successfully Implement Generative AI in Edge Devices—Opt...Edge AI and Vision Alliance For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2025/06/key-requirements-to-successfully-implement-generative-ai-in-edge-devices-optimized-mapping-to-the-enhanced-npx6-neural-processing-unit-ip-a-presentation-from-synopsys/
Gordon Cooper, Principal Product Manager at Synopsys, presents the “Key Requirements to Successfully Implement Generative AI in Edge Devices—Optimized Mapping to the Enhanced NPX6 Neural Processing Unit IP” tutorial at the May 2025 Embedded Vision Summit.
In this talk, Cooper discusses emerging trends in generative AI for edge devices and the key role of transformer-based neural networks. He reviews the distinct attributes of transformers, their advantages over conventional convolutional neural networks and how they enable generative AI.
Cooper then covers key requirements that must be met for neural processing units (NPU) to support transformers and generative AI in edge device applications. He uses transformer-based generative AI examples to illustrate the efficient mapping of these workloads onto the enhanced Synopsys ARC NPX NPU IP family.
High Availability On-Premises FME Flow.pdf
High Availability On-Premises FME Flow.pdfSafe Software FME Flow is a highly robust tool for transforming data both automatically and by user-initiated workflows. At the Finnish telecommunications company Elisa, FME Flow serves processes and internal stakeholders that require 24/7 availability from underlying systems, while imposing limitations on the use of cloud based systems. In response to these business requirements, Elisa has implemented a high-availability on-premises setup of FME Flow, where all components of the system have been duplicated or clustered. The goal of the presentation is to provide insights into the architecture behind the high-availability functionality. The presentation will show in basic technical terms how the different parts of the system work together. Basic level understanding of IT technologies is required to understand the technical portion of the presentation, namely understanding the purpose of the following components: load balancer, FME Flow host nodes, FME Flow worker nodes, network file storage drives, databases, and external authentication services. The presentation will also outline our lessons learned from the high-availability project, both benefits and challenges to consider.
No-Code Workflows for CAD & 3D Data: Scaling AI-Driven Infrastructure
No-Code Workflows for CAD & 3D Data: Scaling AI-Driven InfrastructureSafe Software When projects depend on fast, reliable spatial data, every minute counts.
AI Clearing needed a faster way to handle complex spatial data from drone surveys, CAD designs and 3D project models across construction sites. With FME Form, they built no-code workflows to clean, convert, integrate, and validate dozens of data formats – cutting analysis time from 5 hours to just 30 minutes.
Join us, our partner Globema, and customer AI Clearing to see how they:
-Automate processing of 2D, 3D, drone, spatial, and non-spatial data
-Analyze construction progress 10x faster and with fewer errors
-Handle diverse formats like DWG, KML, SHP, and PDF with ease
-Scale their workflows for international projects in solar, roads, and pipelines
If you work with complex data, join us to learn how to optimize your own processes and transform your results with FME.
FME for Distribution & Transmission Integrity Management Program (DIMP & TIMP)
FME for Distribution & Transmission Integrity Management Program (DIMP & TIMP)Safe Software Peoples Gas in Chicago, IL has changed to a new Distribution & Transmission Integrity Management Program (DIMP & TIMP) software provider in recent years. In order to successfully deploy the new software we have created a series of ETL processes using FME Form to transform our gas facility data to meet the required DIMP & TIMP data specifications. This presentation will provide an overview of how we used FME to transform data from ESRI’s Utility Network and several other internal and external sources to meet the strict data specifications for the DIMP and TIMP software solutions.
Artificial Intelligence in the Nonprofit Boardroom.pdf
Artificial Intelligence in the Nonprofit Boardroom.pdfOnBoard OnBoard recently partnered with Microsoft Tech for Social Impact on the AI in the Nonprofit Boardroom Survey, an initiative designed to uncover the current and future role of artificial intelligence in nonprofit governance.
Kubernetes Security Act Now Before It’s Too Late
Kubernetes Security Act Now Before It’s Too LateMichael Furman In today's cloud-native landscape, Kubernetes has become the de facto standard for orchestrating containerized applications, but its inherent complexity introduces unique security challenges. Are you one YAML away from disaster?
This presentation, "Kubernetes Security: Act Now Before It’s Too Late," is your essential guide to understanding and mitigating the critical security risks within your Kubernetes environments. This presentation dives deep into the OWASP Kubernetes Top Ten, providing actionable insights to harden your clusters.
We will cover:
The fundamental architecture of Kubernetes and why its security is paramount.
In-depth strategies for protecting your Kubernetes Control Plane, including kube-apiserver and etcd.
Crucial best practices for securing your workloads and nodes, covering topics like privileged containers, root filesystem security, and the essential role of Pod Security Admission.
Don't wait for a breach. Learn how to identify, prevent, and respond to Kubernetes security threats effectively.
It's time to act now before it's too late!
FME for Good: Integrating Multiple Data Sources with APIs to Support Local Ch...
FME for Good: Integrating Multiple Data Sources with APIs to Support Local Ch...Safe Software Have-a-skate-with-Bob (HASB-KC) is a local charity that holds two Hockey Tournaments every year to raise money in the fight against Pancreatic Cancer. The FME Form software is used to integrate and exchange data via API, between Google Forms, Google Sheets, Stripe payments, SmartWaiver, and the GoDaddy email marketing tools to build a grass-roots Customer Relationship Management (CRM) system for the charity. The CRM is used to communicate effectively and readily with the participants of the hockey events and most importantly the local area sponsors of the event. Communication consists of a BLOG used to inform participants of event details including, the ever-important team rosters. Funds raised by these events are used to support families in the local area to fight cancer and support PanCan research efforts to find a cure against this insidious disease. FME Form removes the tedium and error-prone manual ETL processes against these systems into 1 or 2 workbenches that put the data needed at the fingertips of the event organizers daily freeing them to work on outreach and marketing of the events in the community.
Creating Inclusive Digital Learning with AI: A Smarter, Fairer Future
Creating Inclusive Digital Learning with AI: A Smarter, Fairer FutureImpelsys Inc. Have you ever struggled to read a tiny label on a medicine box or tried to navigate a confusing website? Now imagine if every learning experience felt that way—every single day.
For millions of people living with disabilities, poorly designed content isn’t just frustrating. It’s a barrier to growth. Inclusive learning is about fixing that. And today, AI is helping us build digital learning that’s smarter, kinder, and accessible to everyone.
Accessible learning increases engagement, retention, performance, and inclusivity for everyone. Inclusive design is simply better design.
AI vs Human Writing: Can You Tell the Difference?
AI vs Human Writing: Can You Tell the Difference?Shashi Sathyanarayana, Ph.D This slide illustrates a side-by-side comparison between human-written, AI-written, and ambiguous content. It highlights subtle cues that help readers assess authenticity, raising essential questions about the future of communication, trust, and thought leadership in the age of generative AI.
National Fuels Treatments Initiative: Building a Seamless Map of Hazardous Fu...
National Fuels Treatments Initiative: Building a Seamless Map of Hazardous Fu...Safe Software The National Fuels Treatments Initiative (NFT) is transforming wildfire mitigation by creating a standardized map of nationwide fuels treatment locations across all land ownerships in the United States. While existing state and federal systems capture this data in diverse formats, NFT bridges these gaps, delivering the first truly integrated national view. This dataset will be used to measure the implementation of the National Cohesive Wildland Strategy and demonstrate the positive impact of collective investments in hazardous fuels reduction nationwide. In Phase 1, we developed an ETL pipeline template in FME Form, leveraging a schema-agnostic workflow with dynamic feature handling intended for fast roll-out and light maintenance. This was key as the initiative scaled from a few to over fifty contributors nationwide. By directly pulling from agency data stores, oftentimes ArcGIS Feature Services, NFT preserves existing structures, minimizing preparation needs. External mapping tables ensure consistent attribute and domain alignment, while robust change detection processes keep data current and actionable. Now in Phase 2, we’re migrating pipelines to FME Flow to take advantage of advanced scheduling, monitoring dashboards, and automated notifications to streamline operations. Join us to explore how this initiative exemplifies the power of technology, blending FME, ArcGIS Online, and AWS to solve a national business problem with a scalable, automated solution.
MuleSoft for AgentForce : Topic Center and API Catalog
MuleSoft for AgentForce : Topic Center and API Catalogshyamraj55 This presentation dives into how MuleSoft empowers AgentForce with organized API discovery and streamlined integration using Topic Center and the API Catalog. Learn how these tools help structure APIs around business needs, improve reusability, and simplify collaboration across teams. Ideal for developers, architects, and business stakeholders looking to build a connected and scalable API ecosystem within AgentForce.
“Why It’s Critical to Have an Integrated Development Methodology for Edge AI,...
“Why It’s Critical to Have an Integrated Development Methodology for Edge AI,...Edge AI and Vision Alliance
“Addressing Evolving AI Model Challenges Through Memory and Storage,” a Prese...
“Addressing Evolving AI Model Challenges Through Memory and Storage,” a Prese...Edge AI and Vision Alliance
“Key Requirements to Successfully Implement Generative AI in Edge Devices—Opt...
“Key Requirements to Successfully Implement Generative AI in Edge Devices—Opt...Edge AI and Vision Alliance
Chapter09 -- networking with unix and linux
- 1. Chapter 9: Networking with Unix and Linux Network+ Guide to Networks
- 2. Objectives: Describe the origins and history of the UNIX operating system Identify similarities and differences between popular implementations of UNIX Understand why you might choose a UNIX or Linux server for a corporate network
- 3. Objectives: (continued) Explain and execute basic UNIX and Linux commands Install Linux on an Intel-based PC Use Linux to add groups and users and to change file access permissions Explain how UNIX and Linux can be internetworked with other operating systems
- 4. A Brief History of UNIX AT&T Source code System V. BSD (Berkeley Software Distribution) The SCO Group The Open Group
- 5. Varieties of UNIX UNIX features: Multiple, simultaneously logged on users Multiple, simultaneously running tasks Mount disk partitions upon demand Permissions for file and directory access Uniform method of issuing or receiving data from hardware devices, files, and running programs
- 6. Varieties of UNIX (continued) UNIX features: The ability to start a program without interfering with a currently running program Hundreds of subsystems, including dozens of programming languages Source code portability Window interfaces that the user can configure, the most popular of which is the X Window system
- 7. Varieties of UNIX (continued) Proprietary UNIX Licensed copy from The SCO Group Popular Vendors Sun Microsystems--Solaris IBM--AIX HP--HP-UX,
- 8. Varieties of UNIX (continued) Proprietary UNIX Proprietary UNIX system advantages: Accountability and support Optimization of hardware and software Predictability and compatibility One drawback No access to the system’s source code
- 9. Open Source UNIX Open Source UNIX Open source software or Freely distributable software GNU BSD Linux
- 10. Open Source UNIX (continued) Open Source UNIX Primary advantage Cost Users can modify its code Freely distributable Run not only on Intel-based processors, but also on other processor brands
- 11. Why Choose Linux? What considerations: Is it compatible with my existing infrastructure? Will it provide the security required by my resources? Can my technical staff manage it effectively? Will my applications run smoothly on it? Will it accommodate future growth (is it scalable)?
- 12. Why Choose Linux? (continued) What considerations: (cont.) Does it support the additional services required by my users? Does it fit my budget? What additional training will it require? Can I count on competent and consistent support from its manufacturer?
- 13. Linux Server Hardware Requirements Table 9-1 shows the minimum hardware requirements for the various components of a Linux server. Hardware compatibility list (HCL) at www.tldp.org/HOWTO/Hardware-HOWTO/.
- 14. Linux Server Hardware Requirements (continued)
- 15. Linux Server Hardware Requirements (continued) What additional hardware your server may require: Which applications and services will run How many users How much random access memory (RAM) How much secondary storage (hard disk)
- 16. A Closer Look at Linux Linux Multiprocessing In addition to processes, Linux also supports threads Allocates separate resources (such as memory space) to each process as it is created Symmetric multiprocessing (SMP)
- 17. A Closer Look at Linux (continued) The Linux Memory Model Use both physical and virtual memory efficiently Allocates a memory area for each application Attempts to decrease the inefficiency of this practice, however, by sharing memory between programs wherever it can
- 18. A Closer Look at Linux (continued) The Linux Kernel Kernel Core of the Linux system Kernel module Instructions for performing a specific task
- 19. A Closer Look at Linux (continued) Linux File and Directory Structure Hierarchical file system UNIX system was one of the first to implement Method of organizing files and directories on a disk in which directories may contain files and other directories Most operating systems use hierarchical file systems
- 20. A Closer Look at Linux (continued)
- 21. A Closer Look at Linux (continued) Linux File Services Native file system type, called ext3 Allows you to access DOS FAT as well as NTFS Can both attach shared file systems and share local partitions with other users Windows or NetWare Network File System (NFS)
- 22. A Closer Look at Linux (continued) Linux Internet Services UNIX-based systems have deep roots in Internet services Leading Internet Web server is an open source software application called Apache Original Web tools—including the first browsers and servers—were developed on UNIX-based systems Full range of Internet services as standard components
- 23. A Linux Command Sampler The command line is the primary method of interacting with a Linux system Command interpreter Shell
- 24. A Linux Command Sampler (continued) Manual pages (Online documentation) Section 1 covers the commands that you most typically enter while typing in a command window. Sections 2 through 5 document the programmer’s interface to the Linux system. Section 6 documents some of the amusements and games that are included in the Linux system.
- 25. A Linux Command Sampler (continued) Manual pages (Online documentation) Section 7 describes the device drivers for the system. Section 8 covers the commands used by administrators to manage the system. Section 9 documents the Linux kernel functions programmers use when writing device drivers.
- 26. A Linux Command Sampler (continued)
- 27. A Linux Command Sampler (continued)
- 28. A Linux Command Sampler (continued) Command ls (with -l) Learn everything about a file except its contents: The filename The file size (in bytes) The date and time that the file was created The date and time that the file was last accessed (viewed or printed)
- 29. A Linux Command Sampler (continued) Command ls (with -l) (cont.) The date and time that the file contents were last modified The number of “aliases” or links to the file The numeric identifier of the user who owns the file The numeric identifier of the group to which the file belongs The access rights for the owner, the group, and all others
- 30. A Linux Command Sampler (continued)
- 31. A Linux Command Sampler (continued) Command ls (with -l) (cont.) Files with a type of “d” are directories “ -” are regular files such as word-processing files or spreadsheet files “ l” for symbolic link files “ b” for block device files “ c” for character device files
- 32. A Linux Command Sampler (continued)
- 33. Planning for Installation Answer the following questions: What is the new server’s name? What is the server’s IP address? What kind of video card is installed in the server? What do you want the administrative user’s password to be? How can I remember all of this information?
- 34. Installing and Configuring a Red Hat Linux Server Step by step Select the language the system will use Confirm the keyboard layout Confirm your mouse type Select disk drive partitioning options Choose booting options
- 35. Installing and Configuring a Red Hat Linux Server (continued) Step by step (cont.) Configure the network interface (or interfaces) Configure the network firewall options Add support for additional languages Set the time and time zone Enter (and confirm) the root (administrator) password
- 36. Configuring Linux for Network Administration The basics of adding users and groups The basics of modifying file access permissions Two commands: groupadd useradd.
- 37. Configuring Linux for Network Administration (continued)
- 38. Configuring Linux for Network Administration (continued) To add group IDs to your Linux system: Type groupadd instructors and then press Enter at the command prompt. The group instructors is added. Type groupadd students and then press Enter . The group students is added. Type groupadd administrators and then press Enter . The group administrators is added.
- 39. Configuring Linux for Network Administration (continued) To add a new user and assign the user a password: Type useradd –g users –G instructors thomas and then press Enter to add a new user account named thomas. Type passwd thomas and then press Enter.
- 40. Configuring Linux for Network Administration (continued) Linux prompts you to type the new password. Linux prompts you to retype your password. Enter the same password again; this confirmation helps ensure that you type your new password accurately.
- 41. Configuring Linux for Network Administration (continued) Changing File Access Permissions To create a directory and assign it to a group If you are still logged on to your Linux system, log off by typing exit and then pressing Enter. To log back on to your system as user thomas, type thomas at the login prompt and then press Enter .
- 42. Configuring Linux for Network Administration (continued) Type the password you assigned for thomas and then press Enter . You see a command window and a command prompt. To create the new directory, type mkdir PROGRAMS and then press Enter .
- 43. Configuring Linux for Network Administration (continued) Type ls -l and then press Enter . Notice that the directory belongs to the group users. That’s because the primary group to which the user thomas belongs is users. Type chgrp instructors PROGRAMS and then press Enter to assign ownership of the PROGRAMS directory to the group instructors.
- 44. Configuring Linux for Network Administration (continued) Type ls -l and then press Enter . Notice that the directory is now assigned to the group instructors.
- 45. Configuring Linux for Network Administration (continued) To change the access permissions for the PROGRAMS directory: Log on as the user thomas (whose primary directory is instructors ). Type chmod g+w PROGRAMS and then press Enter . This command adds write access for the instructors group to the directory PROGRAMS. Next, you will remove read and write access to the PROGRAMS directory for all others. To do so, type chmod o-rw PROGRAMS and then press Enter .
- 46. Configuring Linux for Network Administration (continued) Type ls -l and then press Enter to view the access permissions assigned to PROGRAMS.You should see a line for PROGRAMS that includes permissions of drwxrwx--x.
- 47. Internetworking with Other Network Operating Systems Samba Communicates with Windows servers WINE Enables Windows programs to run on Linux VMware Emulates a complete Intel-based computer Telnet
- 48. Internetworking with Other Network Operating Systems (continued)
- 49. Internetworking with Other Network Operating Systems (continued)
- 50. Chapter summary Describe the origins and history of the UNIX operating system Identify similarities and differences between popular implementations of UNIX Understand why you might choose a UNIX or Linux server for a corporate network
- 51. Chapter summary (continued) Explain and execute basic UNIX and Linux commands Install Linux on an Intel-based PC Use Linux to add groups and users and to change file access permissions Explain how UNIX and Linux can be internetworked with other operating systems