Function-and-prototype defined classes in JavaScript
Download as pptx, pdf1 like92 views
Objects and prototypes; Student-Grade example; this keyword; Constructor function; How does the new operator work in JavaScript; Inheritance with the prototype chain; The instanceof operator in JavaScript
1 of 19
Download to read offline





![Student-Grade Example
function Student(x) {
this.name = x;
this.grade = [];
}
Student.prototype = {
addGrade: function(x) {
this.grade.push(x);
}
};
var Tom = new Student("Tom");
Tom.addGrade(82);
Tom.addGrade(75);
Tom.addGrade(70);](https://image.slidesharecdn.com/function-and-prototypedefinedclassesinjavascript-170624230641/85/Function-and-prototype-defined-classes-in-JavaScript-7-320.jpg)



![How does the new operator work in
JavaScript?
• The new operator uses the
internal [[Construct]] method, and it basically
does the following:
– Initializes a new object
– Sets the internal [[Prototype]] of this object, pointing
to the constructor function prototype property.
– If the constructor function's prototype property is
not an object (but a primitive value, such as a
Number, String, Boolean, Undefined or
Null), Object.prototype is used instead.](https://image.slidesharecdn.com/function-and-prototypedefinedclassesinjavascript-170624230641/85/Function-and-prototype-defined-classes-in-JavaScript-11-320.jpg)

![• { name: 'Tom', grade: [ 82, 75, 70 ] } { name:
'Sarah', grade: [ 83, 88, 91 ] } { name: 'Vu',
grade: [ 85, 79, 84 ] }](https://image.slidesharecdn.com/function-and-prototypedefinedclassesinjavascript-170624230641/85/Function-and-prototype-defined-classes-in-JavaScript-13-320.jpg)
![Inheritance with the Prototype Chain
• When it comes to inheritance, JavaScript only has
one construct: objects. Each object has a private
property (referred to as [[Prototype]] ) which
holds a link to another object called
its prototype. That prototype object has a
prototype of its own, and so on until an object is
reached with null as its prototype. By
definition, null has no prototype, and acts as the
final link in this prototype chain.](https://image.slidesharecdn.com/function-and-prototypedefinedclassesinjavascript-170624230641/85/Function-and-prototype-defined-classes-in-JavaScript-15-320.jpg)




Ad
Recommended
Best practices in Java



Best practices in JavaMudit Gupta - Best Practices in Java
- Avoiding garbage collection
- Loop Optimizaiton
- Exception Handling
- Object Oriented Design Principles
- Avoiding null pointer exception
Introduction to Scala



Introduction to ScalaRahul Jain A Short presentation on Scala for beginners with Introduction to Functional Programming, Basics of Scala, Use-casses and Examples
String interpolation



String interpolationKnoldus Inc. It is a mechanism that enables us to sew/embed/bind WORDS in between a processed/unprocessed string literal.
Here by the processed string literal we mean processing of meta-characters like escape sequences(\n, \t, \r etc.) in the string.
Simplicitly



SimplicitlyMartin Odersky This document discusses implicit function types as a way to abstract over context in programming. It proposes implicit function types as a lighter-weight alternative to type classes and the reader monad for passing implicit context parameters. Implicit function types allow context to be provided implicitly based on the expected type rather than requiring it to be passed explicitly. The document outlines the typing rules and translation to the lambda calculus for implicit function types and provides examples of their use in a conference management system and the builder pattern.
Ruby object model



Ruby object modelChamnap Chhorn This document provides an overview of key concepts in Ruby including variables, methods, classes, modules, inheritance and scope. It discusses local variables, instance variables, class variables and global variables. It explains how methods are defined and called in Ruby. It describes classes and modules, and how modules can be mixed into classes. The document also covers inheritance, constants, self, and singleton methods. It provides details on variable scope and how Ruby determines an identifier is a variable, keyword or method call.
How Green are Java Best Coding Practices? - GreenDays @ Rennes - 2014-07-01



How Green are Java Best Coding Practices? - GreenDays @ Rennes - 2014-07-01Jérôme Rocheteau This work investigates if best coding practices in Java can stand for eco-design rules as they deal with software performance. It focuses on how validating such an hypothesis for consumed energy, spent execution time and peak allocated memory. It leads to this silent feedback: no need to carry on many measures.
Lesson3



Lesson3Arpan91 This document provides an overview and examples of Java arrays, strings, parameter passing, object constructors, and modifiers like static and final. It discusses declaring and using arrays, bounds checking, copying and sorting arrays. It also covers string and StringBuffer objects, passing parameters by value and reference, using constructors to initialize objects, and static and final modifiers to define constants and class methods.
Shapeless- Generic programming for Scala



Shapeless- Generic programming for ScalaKnoldus Inc. "Introduction to Shapeless- Generic programming for Scala !". Broadly speaking, shapeless is about programming with types. Doing things at compile-time that would more commonly be done at runtime to ensure type-safety. A long list of features provided by Shapeless are explained in the enclosed presentation.
Small Lambda Talk @Booster2015



Small Lambda Talk @Booster2015Martin (高馬丁) Skarsaune You have probably noticed the excitement regarding functional programming and the new lambda expression in Java 8. But did you know that this also brings Java back to its object-oriented roots?
The Smalltalk programming language shows how virtually any task can be achieved through good old object orientation. Everything is built with the basic ingredients of objects, messages and blocks (lambda).
Smalltalk uses lambda expressions for conditional processing, iteration and exception handling. We will look at some fascinating examples, and discuss if and how to apply them in Java.
We Java programmers now find ourselves with a brand new lambda tool in our toolbox. Lets take the time to learn from the past about the power of object orientation and lambdas.
4. Classes and Methods



4. Classes and MethodsNilesh Dalvi The document discusses classes and methods in Java. It defines that a class is a user-defined data type that serves as a template to define properties. A class contains fields to store data and methods to perform actions. Methods are declared inside the class and can access and modify the class fields. The document also discusses creating objects from classes using the new keyword, using constructors to initialize objects, using this keyword to refer to class fields from methods, method overloading and static methods.
Java keywords



Java keywordsRavi_Kant_Sahu This document discusses keywords in Java including this, super, and final. It explains that this refers to the current object instance and is used to call methods or access fields of the current class. Super is used to call methods or access fields of the parent class. Final is used to declare variables that cannot be reassigned, prevent method overriding, and prevent class inheritance. The document also covers static keywords and how static methods can be called on a class without creating an instance.
Strings in Java 



Strings in Java Hitesh-Java In this core java training session, you will learn Handling Strings in Java. Topics covered in this session are:
• Memory Allocation & Garbage Collection
• Strings in Java
For more information about this course visit on this link: https://www.mindsmapped.com/courses/software-development/learn-java-fundamentals-hands-on-training-on-core-java-concepts/
What To Leave Implicit



What To Leave ImplicitMartin Odersky This document summarizes Martin Odersky's talk on implicits in Scala. The key points are:
1. Implicits allow certain values or functions to be passed implicitly rather than explicitly as parameters. This can avoid tedious repetition when many parameters rarely change.
2. Implicits are commonly used to establish context, inject dependencies, implement type classes, and prove theorems by modeling types as theorems and programs as proofs.
3. Future changes to implicits in Scala 3 include allowing multiple implicit parameter lists, implicit by-name parameters, and implicit function types which avoid wrapping implicits in monads.
What To Leave Implicit



What To Leave ImplicitMartin Odersky - Implicit function types are a powerful way to abstract over contexts by defining types that inject implicit values into a scope. This can fundamentally change the code we write by removing boilerplate around passing implicit parameters and configurations.
- Implicit parameters are a core Scala feature that allow removing repetition through parameterization while enabling use cases like proving theorems, establishing context, and implementing type classes. Their scope may be expanded through implicit function types.
- Future Scala versions aim to tighten rules for implicit conversions while introducing features like lazy implicits, multiple implicit parameter lists, and coherence to improve the discoverability and reasoning around implicits.
Wrapper classes



Wrapper classesRavi_Kant_Sahu This document discusses Java wrapper classes. It explains that wrapper classes allow primitive types to be used as objects. Each primitive type has a corresponding wrapper class (e.g. Integer for int). Wrapper classes provide methods to convert between primitive types and their object equivalents. They allow primitives to be used in contexts that require objects, like collections, and provide additional functionality like constants and parsing/formatting methods.
Java 101 Intro to Java Programming - Exercises



Java 101 Intro to Java Programming - Exercisesagorolabs This document outlines several hands-on exercises for learning Java fundamentals. It describes exercises to create basic Java programs, programs that take command line arguments, programs for integer operations, finding leap years, and printing powers of two. It also includes bonus exercises for random number generation, arrays of days, printing personal details, and calculating sales discounts.
3. Data types and Variables



3. Data types and VariablesNilesh Dalvi This document discusses Java data types and variables. It begins by defining data types as sets of values with predefined characteristics. It then lists the default Java primitive data types (boolean, char, byte, short, int, long, float, double) along with their default sizes and values. Examples are provided to demonstrate the double and char data types. The document then discusses variables, describing how to declare them and the three types: local, instance, and static variables. It also covers dynamic initialization, default values, and visibility/scope. Finally, the document discusses type conversion and casting between incompatible types in Java.
What is String in Java?



What is String in Java?RAKESH P String is a sequence of characters represented by the java.lang.String class. Strings can be created using string literals or the new keyword. When using string literals, the JVM checks if an identical string exists in the string constant pool first before creating a new string object. Using the new keyword always creates a new string object in heap memory. This difference is important for memory efficiency as string literals avoid duplicating identical string objects in memory.
Preparing for Scala 3



Preparing for Scala 3Martin Odersky This document outlines the roadmap for Scala 3 and the Dotty compiler. It discusses the goals of improving type safety, ergonomics and performance while simplifying the language. Key points include incorporating learnings from Haskell for purity without sacrificing simplicity. The roadmap aims for a 2020 release of Scala 3 with stabilization in 2019. It emphasizes the importance of community contributions and getting early feedback on Dotty releases.
Introduction to JavaScript



Introduction to JavaScriptRangana Sampath Introduction to JavaScript for a set of people with previous programming experience, emphasizing on key parts that defer from other languages
String handling(string class)



String handling(string class)Ravi Kant Sahu This document discusses string handling in Java. It begins by explaining that strings are immutable objects of type String. It then discusses why strings are immutable and the security implications if they were mutable. The document also introduces the main string classes in Java and some common string operations like concatenation, comparison, searching and modifying strings. It provides examples for many string methods like length(), charAt(), equals(), indexOf() etc.
String Interpolation in Scala



String Interpolation in ScalaKnoldus Inc. This presentation describes the String Interpolation in scala and its different interpolator (s, f, and raw) to fomat the string in various way. String interpolation is the replacement of defined character sequences in the string by values or variable values. String interpolation was introduced by SIP-11, which contains all details of the implementation. String Interpolation allows users to embed variable references directly in processed string literals.
Core java concepts



Core java conceptsChikugehlot This document provides an overview of core Java concepts including comments, classes, objects, scoping, static methods and fields, arrays, and constructors. It discusses how comments in Java are similar to C++, the fundamentals of classes and objects, variable scoping determined by curly braces, how static methods and fields belong to the class rather than instances, and how arrays are objects allocated dynamically. It also covers how constructors are used to create class instances and automatically invoke superclass constructors.
2CPP04 - Objects and Classes



2CPP04 - Objects and ClassesMichael Heron This is an intermediate conversion course for C++, suitable for second year computing students who may have learned Java or another language in first year.
6. Exception Handling



6. Exception HandlingNilesh Dalvi Exception handling in Java allows programs to gracefully deal with errors and unexpected conditions. There are two types of exceptions: checked exceptions which must be explicitly caught, and unchecked exceptions which do not need to be caught. The try-catch block is used to catch exceptions, where code that might throw an exception is placed in the try block and catch blocks handle specific exceptions. Finally blocks are always executed and can be used to perform cleanup tasks. Exceptions can also be explicitly thrown using the throw keyword or declared as thrown from methods using the throws clause.
Scala basic



Scala basicNguyen Tuan The document summarizes the agenda and content of a Scala training workshop. The agenda includes functions and evaluations, higher order functions, data and abstraction, and exercises. Key points from the document include:
- Functions can be defined conditionally and with value definitions. Blocks allow grouping of definitions and expressions. Tail recursion optimizes recursion by reusing the call stack.
- Higher order functions allow functions to be passed as parameters or returned as results. Currying transforms functions that take multiple parameters into chains of functions that each take a single parameter.
- Classes define hierarchies and traits provide flexibility for code reuse like interfaces while abstract classes are used for base classes requiring constructor arguments.
- Exercises include implementing
9. Input Output in java



9. Input Output in javaNilesh Dalvi - Java uses streams to perform input and output operations which allow for fast processing. Streams are sequences of data composed of bytes.
- The main stream classes in Java are InputStream for reading data and OutputStream for writing data. These classes handle byte-oriented input/output.
- FileInputStream and FileOutputStream classes allow reading and writing of data to files by extending InputStream and OutputStream respectively. They are used for file handling operations in Java.
7. Multithreading



7. MultithreadingNilesh Dalvi The document discusses multithreading in Java. It defines a thread as the smallest unit of processing and describes how Java allows executing multiple threads simultaneously. It outlines the five states in a thread's lifecycle and how threads transition between these states. It also discusses how to create threads by extending the Thread class or implementing the Runnable interface. Additionally, it covers common thread methods like sleep(), join(), getName(), currentThread(), and setting priority. The document concludes with a brief overview of synchronization in Java.
Prototype 120102020133-phpapp02



Prototype 120102020133-phpapp02plutoone TestTwo this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality scor
Advanced Javascript



Advanced Javascriptrelay12 The document discusses different approaches to object-oriented programming in JavaScript, including classical and prototypal inheritance, constructor functions, and the prototype property. It also covers topics like pseudoclassical patterns, parasitic inheritance, private methods, and debugging and performance techniques.
More Related Content
What's hot (20)
Small Lambda Talk @Booster2015



Small Lambda Talk @Booster2015Martin (高馬丁) Skarsaune You have probably noticed the excitement regarding functional programming and the new lambda expression in Java 8. But did you know that this also brings Java back to its object-oriented roots?
The Smalltalk programming language shows how virtually any task can be achieved through good old object orientation. Everything is built with the basic ingredients of objects, messages and blocks (lambda).
Smalltalk uses lambda expressions for conditional processing, iteration and exception handling. We will look at some fascinating examples, and discuss if and how to apply them in Java.
We Java programmers now find ourselves with a brand new lambda tool in our toolbox. Lets take the time to learn from the past about the power of object orientation and lambdas.
4. Classes and Methods



4. Classes and MethodsNilesh Dalvi The document discusses classes and methods in Java. It defines that a class is a user-defined data type that serves as a template to define properties. A class contains fields to store data and methods to perform actions. Methods are declared inside the class and can access and modify the class fields. The document also discusses creating objects from classes using the new keyword, using constructors to initialize objects, using this keyword to refer to class fields from methods, method overloading and static methods.
Java keywords



Java keywordsRavi_Kant_Sahu This document discusses keywords in Java including this, super, and final. It explains that this refers to the current object instance and is used to call methods or access fields of the current class. Super is used to call methods or access fields of the parent class. Final is used to declare variables that cannot be reassigned, prevent method overriding, and prevent class inheritance. The document also covers static keywords and how static methods can be called on a class without creating an instance.
Strings in Java 



Strings in Java Hitesh-Java In this core java training session, you will learn Handling Strings in Java. Topics covered in this session are:
• Memory Allocation & Garbage Collection
• Strings in Java
For more information about this course visit on this link: https://www.mindsmapped.com/courses/software-development/learn-java-fundamentals-hands-on-training-on-core-java-concepts/
What To Leave Implicit



What To Leave ImplicitMartin Odersky This document summarizes Martin Odersky's talk on implicits in Scala. The key points are:
1. Implicits allow certain values or functions to be passed implicitly rather than explicitly as parameters. This can avoid tedious repetition when many parameters rarely change.
2. Implicits are commonly used to establish context, inject dependencies, implement type classes, and prove theorems by modeling types as theorems and programs as proofs.
3. Future changes to implicits in Scala 3 include allowing multiple implicit parameter lists, implicit by-name parameters, and implicit function types which avoid wrapping implicits in monads.
What To Leave Implicit



What To Leave ImplicitMartin Odersky - Implicit function types are a powerful way to abstract over contexts by defining types that inject implicit values into a scope. This can fundamentally change the code we write by removing boilerplate around passing implicit parameters and configurations.
- Implicit parameters are a core Scala feature that allow removing repetition through parameterization while enabling use cases like proving theorems, establishing context, and implementing type classes. Their scope may be expanded through implicit function types.
- Future Scala versions aim to tighten rules for implicit conversions while introducing features like lazy implicits, multiple implicit parameter lists, and coherence to improve the discoverability and reasoning around implicits.
Wrapper classes



Wrapper classesRavi_Kant_Sahu This document discusses Java wrapper classes. It explains that wrapper classes allow primitive types to be used as objects. Each primitive type has a corresponding wrapper class (e.g. Integer for int). Wrapper classes provide methods to convert between primitive types and their object equivalents. They allow primitives to be used in contexts that require objects, like collections, and provide additional functionality like constants and parsing/formatting methods.
Java 101 Intro to Java Programming - Exercises



Java 101 Intro to Java Programming - Exercisesagorolabs This document outlines several hands-on exercises for learning Java fundamentals. It describes exercises to create basic Java programs, programs that take command line arguments, programs for integer operations, finding leap years, and printing powers of two. It also includes bonus exercises for random number generation, arrays of days, printing personal details, and calculating sales discounts.
3. Data types and Variables



3. Data types and VariablesNilesh Dalvi This document discusses Java data types and variables. It begins by defining data types as sets of values with predefined characteristics. It then lists the default Java primitive data types (boolean, char, byte, short, int, long, float, double) along with their default sizes and values. Examples are provided to demonstrate the double and char data types. The document then discusses variables, describing how to declare them and the three types: local, instance, and static variables. It also covers dynamic initialization, default values, and visibility/scope. Finally, the document discusses type conversion and casting between incompatible types in Java.
What is String in Java?



What is String in Java?RAKESH P String is a sequence of characters represented by the java.lang.String class. Strings can be created using string literals or the new keyword. When using string literals, the JVM checks if an identical string exists in the string constant pool first before creating a new string object. Using the new keyword always creates a new string object in heap memory. This difference is important for memory efficiency as string literals avoid duplicating identical string objects in memory.
Preparing for Scala 3



Preparing for Scala 3Martin Odersky This document outlines the roadmap for Scala 3 and the Dotty compiler. It discusses the goals of improving type safety, ergonomics and performance while simplifying the language. Key points include incorporating learnings from Haskell for purity without sacrificing simplicity. The roadmap aims for a 2020 release of Scala 3 with stabilization in 2019. It emphasizes the importance of community contributions and getting early feedback on Dotty releases.
Introduction to JavaScript



Introduction to JavaScriptRangana Sampath Introduction to JavaScript for a set of people with previous programming experience, emphasizing on key parts that defer from other languages
String handling(string class)



String handling(string class)Ravi Kant Sahu This document discusses string handling in Java. It begins by explaining that strings are immutable objects of type String. It then discusses why strings are immutable and the security implications if they were mutable. The document also introduces the main string classes in Java and some common string operations like concatenation, comparison, searching and modifying strings. It provides examples for many string methods like length(), charAt(), equals(), indexOf() etc.
String Interpolation in Scala



String Interpolation in ScalaKnoldus Inc. This presentation describes the String Interpolation in scala and its different interpolator (s, f, and raw) to fomat the string in various way. String interpolation is the replacement of defined character sequences in the string by values or variable values. String interpolation was introduced by SIP-11, which contains all details of the implementation. String Interpolation allows users to embed variable references directly in processed string literals.
Core java concepts



Core java conceptsChikugehlot This document provides an overview of core Java concepts including comments, classes, objects, scoping, static methods and fields, arrays, and constructors. It discusses how comments in Java are similar to C++, the fundamentals of classes and objects, variable scoping determined by curly braces, how static methods and fields belong to the class rather than instances, and how arrays are objects allocated dynamically. It also covers how constructors are used to create class instances and automatically invoke superclass constructors.
2CPP04 - Objects and Classes



2CPP04 - Objects and ClassesMichael Heron This is an intermediate conversion course for C++, suitable for second year computing students who may have learned Java or another language in first year.
6. Exception Handling



6. Exception HandlingNilesh Dalvi Exception handling in Java allows programs to gracefully deal with errors and unexpected conditions. There are two types of exceptions: checked exceptions which must be explicitly caught, and unchecked exceptions which do not need to be caught. The try-catch block is used to catch exceptions, where code that might throw an exception is placed in the try block and catch blocks handle specific exceptions. Finally blocks are always executed and can be used to perform cleanup tasks. Exceptions can also be explicitly thrown using the throw keyword or declared as thrown from methods using the throws clause.
Scala basic



Scala basicNguyen Tuan The document summarizes the agenda and content of a Scala training workshop. The agenda includes functions and evaluations, higher order functions, data and abstraction, and exercises. Key points from the document include:
- Functions can be defined conditionally and with value definitions. Blocks allow grouping of definitions and expressions. Tail recursion optimizes recursion by reusing the call stack.
- Higher order functions allow functions to be passed as parameters or returned as results. Currying transforms functions that take multiple parameters into chains of functions that each take a single parameter.
- Classes define hierarchies and traits provide flexibility for code reuse like interfaces while abstract classes are used for base classes requiring constructor arguments.
- Exercises include implementing
9. Input Output in java



9. Input Output in javaNilesh Dalvi - Java uses streams to perform input and output operations which allow for fast processing. Streams are sequences of data composed of bytes.
- The main stream classes in Java are InputStream for reading data and OutputStream for writing data. These classes handle byte-oriented input/output.
- FileInputStream and FileOutputStream classes allow reading and writing of data to files by extending InputStream and OutputStream respectively. They are used for file handling operations in Java.
7. Multithreading



7. MultithreadingNilesh Dalvi The document discusses multithreading in Java. It defines a thread as the smallest unit of processing and describes how Java allows executing multiple threads simultaneously. It outlines the five states in a thread's lifecycle and how threads transition between these states. It also discusses how to create threads by extending the Thread class or implementing the Runnable interface. Additionally, it covers common thread methods like sleep(), join(), getName(), currentThread(), and setting priority. The document concludes with a brief overview of synchronization in Java.
Similar to Function-and-prototype defined classes in JavaScript (20)
Prototype 120102020133-phpapp02



Prototype 120102020133-phpapp02plutoone TestTwo this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality score, this is to check virality scor
Advanced Javascript



Advanced Javascriptrelay12 The document discusses different approaches to object-oriented programming in JavaScript, including classical and prototypal inheritance, constructor functions, and the prototype property. It also covers topics like pseudoclassical patterns, parasitic inheritance, private methods, and debugging and performance techniques.
Advanced Javascript



Advanced JavascriptManikanda kumar The document discusses different approaches to object-oriented programming in JavaScript, including classical and prototypal inheritance, constructor functions, and the prototype property. It also covers topics like pseudoclassical patterns, parasitic inheritance, private methods, and debugging and performance techniques.
Advanced Javascript



Advanced JavascriptAdieu The document discusses different approaches to object-oriented programming in JavaScript, including classical and prototypal inheritance, constructor functions, and the prototype property. It explains how prototypal inheritance works by linking objects together through their internal prototype properties. Constructor functions and the new operator allow simulating classical inheritance by establishing prototype links. Various design patterns are also covered, such as public/privileged methods, singletons, modules, and parasitic inheritance.
Javascript Prototypal Inheritance - Big Picture



Javascript Prototypal Inheritance - Big PictureManish Jangir Are you still confused about what the prototypes really are in Javascript. Read the slides from the very begining, you will have a very clear picture about inheritance in Javascript. If you have any questions, please leave a comment. I will try to clarify that thing.
JS Level Up: Prototypes



JS Level Up: PrototypesVernon Kesner Take a dive into JavaScript prototypes from the perspective of constructor functions. Originally given at Charlotte JS on June 18, 2015.
Prototype



PrototypeAditya Gaur Javascript uses prototypal inheritance rather than classical inheritance. In prototypal inheritance, objects inherit directly from other objects by using the object's prototype property. The prototype property allows objects to inherit methods and properties from other objects. When accessing a property on an object, Javascript will search the prototype chain to find the property if it is not present on the object itself. This allows code reuse through prototype chaining. The prototype property of a function sets the prototype of objects created with that function.
The prototype property



The prototype propertyHernan Mammana functions, constructor functions, this keyword, instances, prototype, own properties, prototype properties
Spanish video: https://www.youtube.com/watch?v=oq-6rGZkogY
Javascript Prototype Visualized



Javascript Prototype Visualized军 沈 This document discusses JavaScript prototypes and how they work. It explains that every function has a prototype property that is shared among objects created with that function. It also explains that every object has a hidden __proto__ property that links it to a prototype object. It provides examples of how prototype inheritance works for both classical and prototypal inheritance in JavaScript. Key points covered include how the new operator works, property lookup via the prototype chain, and the relationships between functions, prototypes, and objects in JavaScript.
JavaScript Essentials



JavaScript EssentialsTriphon Statkov This document provides an overview of a JavaScript training presentation. It discusses:
- The presenter and their background in software development and TV apps.
- What topics will be covered, including JavaScript principles, vanilla JS, becoming JS ninjas, and specific concepts like prototypes, types, scope, and patterns.
- Benefits of learning JavaScript like it being the language of the web and used for both frontend and backend development.
- Interesting facts about the history and creation of JavaScript.
- Primitive types like strings, numbers, booleans being similar to pizza ingredients, and object types being able to contain other values.
- Syntax for objects, properties, methods, and the prototype
Js: master prototypes



Js: master prototypesBarak Drechsler Practical and conceptual overview of Javascript prototype paradigm, how to use prototypes, how do they work, and how do they differ from classes, and why there are no real classes in Javascript.
Advanced JavaScript



Advanced JavaScriptStoyan Stefanov This document provides a summary of an introductory presentation on advanced JavaScript concepts including closures, prototypes, inheritance, and more. The presentation covers object literals and arrays, functions as objects, constructors and the this keyword, prototypes and the prototype chain, classical and prototypal inheritance, scope, and closures. Examples are provided to demonstrate each concept.
Ian 20150116 java script oop



Ian 20150116 java script oopLearningTech The document discusses JavaScript objects and functions. It explains that JavaScript objects are collections of name-value pairs similar to dictionaries. Functions in JavaScript are objects that support function call operations. The document also covers constructor functions, prototypes, closures, and namespaces in JavaScript.
How prototype works in java script?



How prototype works in java script?InnovationM By default, every function has a property called prototype this property by default is empty and you can add properties and methods to it and when you create an object from this function. The object inherits its properties and methods.
JavaScript Inheritance



JavaScript InheritanceJussi Pohjolainen The document discusses JavaScript inheritance. It explains that JavaScript uses prototype-based inheritance rather than class-based inheritance. It provides examples of how to implement inheritance by linking object prototypes together through the __proto__ property or Object.create method. Functions in JavaScript have a prototype property that is used to inherit properties and methods onto objects created with new.
JavaScript In Object Oriented Way



JavaScript In Object Oriented WayBorey Lim 1. The document summarizes JavaScript concepts like objects, data types, constructors, prototypes and inheritance.
2. It explains that in JavaScript, objects are collections of key-value pairs known as hashes, and that arrays are also objects.
3. The document also discusses how inheritance is achieved in JavaScript through prototypes - an internal property of functions that is used to provide methods and properties to objects created with a constructor.
Java script unleashed



Java script unleashedDibyendu Tiwary The document provides an overview of key JavaScript concepts including objects, functions, prototypes, inheritance, closures, namespaces and classes. It discusses JavaScript as a prototype-based language and how concepts like inheritance are simulated rather than being true classes. Code examples are provided to demonstrate various JavaScript programming techniques.
Beginning Object-Oriented JavaScript



Beginning Object-Oriented JavaScriptStoyan Stefanov Slides from my "Object-oriented JavaScript" presentation at CSDN (China Software Developers Network), Beijing, December 2008
Object oriented javascript



Object oriented javascriptUsman Mehmood The document provides an overview of object-oriented programming concepts in JavaScript including classes, objects, properties, methods, constructors, inheritance, encapsulation, and abstraction. It discusses defining classes and custom objects, creating instances of classes, adding and calling methods and properties, implementing inheritance between classes, and other core OOP principles in JavaScript.
Javascript



JavascriptAditya Gaur The document discusses JavaScript and some of its key features:
- JavaScript is the programming language of the web browser and was originally developed by Netscape under different names before being standardized.
- JavaScript uses a prototypal object model instead of classes, with objects inheriting directly from other objects via prototypal inheritance chains rather than from classes.
- The "new" keyword is used to create objects but can give the misleading impression of classes; functions can also be used to create objects without "new" by returning the object.
Ad
Recently uploaded (20)
TimeSeries Machine Learning - PyData London 2025



TimeSeries Machine Learning - PyData London 2025Suyash Joshi Timeseries Machine Learning - forecasting and anomaly detection with InfluxDB
Azure vs AWS Which Cloud Platform Is Best for Your Business in 2025



Azure vs AWS Which Cloud Platform Is Best for Your Business in 2025Infrassist Technologies Pvt. Ltd. Azure vs. AWS is a common comparison when businesses evaluate cloud platforms for performance, flexibility, and cost-efficiency.
National Fuels Treatments Initiative: Building a Seamless Map of Hazardous Fu...



National Fuels Treatments Initiative: Building a Seamless Map of Hazardous Fu...Safe Software The National Fuels Treatments Initiative (NFT) is transforming wildfire mitigation by creating a standardized map of nationwide fuels treatment locations across all land ownerships in the United States. While existing state and federal systems capture this data in diverse formats, NFT bridges these gaps, delivering the first truly integrated national view. This dataset will be used to measure the implementation of the National Cohesive Wildland Strategy and demonstrate the positive impact of collective investments in hazardous fuels reduction nationwide. In Phase 1, we developed an ETL pipeline template in FME Form, leveraging a schema-agnostic workflow with dynamic feature handling intended for fast roll-out and light maintenance. This was key as the initiative scaled from a few to over fifty contributors nationwide. By directly pulling from agency data stores, oftentimes ArcGIS Feature Services, NFT preserves existing structures, minimizing preparation needs. External mapping tables ensure consistent attribute and domain alignment, while robust change detection processes keep data current and actionable. Now in Phase 2, we’re migrating pipelines to FME Flow to take advantage of advanced scheduling, monitoring dashboards, and automated notifications to streamline operations. Join us to explore how this initiative exemplifies the power of technology, blending FME, ArcGIS Online, and AWS to solve a national business problem with a scalable, automated solution.
Domino IQ – Was Sie erwartet, erste Schritte und Anwendungsfälle



Domino IQ – Was Sie erwartet, erste Schritte und Anwendungsfällepanagenda Webinar Recording: https://www.panagenda.com/webinars/domino-iq-was-sie-erwartet-erste-schritte-und-anwendungsfalle/
HCL Domino iQ Server – Vom Ideenportal zur implementierten Funktion. Entdecken Sie, was es ist, was es nicht ist, und erkunden Sie die Chancen und Herausforderungen, die es bietet.
Wichtige Erkenntnisse
- Was sind Large Language Models (LLMs) und wie stehen sie im Zusammenhang mit Domino iQ
- Wesentliche Voraussetzungen für die Bereitstellung des Domino iQ Servers
- Schritt-für-Schritt-Anleitung zur Einrichtung Ihres Domino iQ Servers
- Teilen und diskutieren Sie Gedanken und Ideen, um das Potenzial von Domino iQ zu maximieren
Establish Visibility and Manage Risk in the Supply Chain with Anchore SBOM



Establish Visibility and Manage Risk in the Supply Chain with Anchore SBOMAnchore Over 70% of any given software application consumes open source software (most likely not even from the original source) and only 15% of organizations feel confident in their risk management practices.
With the newly announced Anchore SBOM feature, teams can start safely consuming OSS while mitigating security and compliance risks. Learn how to import SBOMs in industry-standard formats (SPDX, CycloneDX, Syft), validate their integrity, and proactively address vulnerabilities within your software ecosystem.
June Patch Tuesday



June Patch TuesdayIvanti Ivanti’s Patch Tuesday breakdown goes beyond patching your applications and brings you the intelligence and guidance needed to prioritize where to focus your attention first. Catch early analysis on our Ivanti blog, then join industry expert Chris Goettl for the Patch Tuesday Webinar Event. There we’ll do a deep dive into each of the bulletins and give guidance on the risks associated with the newly-identified vulnerabilities.
Artificial Intelligence in the Nonprofit Boardroom.pdf



Artificial Intelligence in the Nonprofit Boardroom.pdfOnBoard OnBoard recently partnered with Microsoft Tech for Social Impact on the AI in the Nonprofit Boardroom Survey, an initiative designed to uncover the current and future role of artificial intelligence in nonprofit governance.
PyData - Graph Theory for Multi-Agent Integration



PyData - Graph Theory for Multi-Agent Integrationbarqawicloud Graph theory is a well-known concept for algorithms and can be used to orchestrate the building of multi-model pipelines. By translating tasks and dependencies into a Directed Acyclic Graph, we can orchestrate diverse AI models, including NLP, vision, and recommendation capabilities. This tutorial provides a step-by-step approach to designing graph-based AI model pipelines, focusing on clinical use cases from the field.
Cisco ISE Performance, Scalability and Best Practices.pdf



Cisco ISE Performance, Scalability and Best Practices.pdfsuperdpz Cisco ISE Performance, Scalability and Best Practices
Ben Blair - Operating Safely in a Vibe Coding World



Ben Blair - Operating Safely in a Vibe Coding WorldAWS Chicago AWS Community Day Midwest 2025
Ben Blair
Operating Safely in a Vibe Coding World
Kubernetes Security Act Now Before It’s Too Late



Kubernetes Security Act Now Before It’s Too LateMichael Furman In today's cloud-native landscape, Kubernetes has become the de facto standard for orchestrating containerized applications, but its inherent complexity introduces unique security challenges. Are you one YAML away from disaster?
This presentation, "Kubernetes Security: Act Now Before It’s Too Late," is your essential guide to understanding and mitigating the critical security risks within your Kubernetes environments. This presentation dives deep into the OWASP Kubernetes Top Ten, providing actionable insights to harden your clusters.
We will cover:
The fundamental architecture of Kubernetes and why its security is paramount.
In-depth strategies for protecting your Kubernetes Control Plane, including kube-apiserver and etcd.
Crucial best practices for securing your workloads and nodes, covering topics like privileged containers, root filesystem security, and the essential role of Pod Security Admission.
Don't wait for a breach. Learn how to identify, prevent, and respond to Kubernetes security threats effectively.
It's time to act now before it's too late!
vertical-cnc-processing-centers-drillteq-v-200-en.pdf



vertical-cnc-processing-centers-drillteq-v-200-en.pdfAmirStern2 מכונות CNC קידוח אנכיות הן הבחירה הנכונה והטובה ביותר לקידוח ארונות וארגזים לייצור רהיטים. החלק נוסע לאורך ציר ה-x באמצעות ציר דיגיטלי מדויק, ותפוס ע"י צבת מכנית, כך שאין צורך לבצע setup (התאמות) לגדלים שונים של חלקים.
Bridging the divide: A conversation on tariffs today in the book industry - T...



Bridging the divide: A conversation on tariffs today in the book industry - T...BookNet Canada A collaboration-focused conversation on the recently imposed US and Canadian tariffs where speakers shared insights into the current legislative landscape, ongoing advocacy efforts, and recommended next steps. This event was presented in partnership with the Book Industry Study Group.
Link to accompanying resource: https://bnctechforum.ca/sessions/bridging-the-divide-a-conversation-on-tariffs-today-in-the-book-industry/
Presented by BookNet Canada and the Book Industry Study Group on May 29, 2025 with support from the Department of Canadian Heritage.
Crypto Super 500 - 14th Report - June2025.pdf



Crypto Super 500 - 14th Report - June2025.pdfStephen Perrenod This OrionX's 14th semi-annual report on the state of the cryptocurrency mining market. The report focuses on Proof-of-Work cryptocurrencies since those use substantial supercomputer power to mint new coins and encode transactions on their blockchains. Only two make the cut this time, Bitcoin with $18 billion of annual economic value produced and Dogecoin with $1 billion. Bitcoin has now reached the Zettascale with typical hash rates of 0.9 Zettahashes per second. Bitcoin is powered by the world's largest decentralized supercomputer in a continuous winner take all lottery incentive network.
How Advanced Environmental Detection Is Revolutionizing Oil & Gas Safety.pdf



How Advanced Environmental Detection Is Revolutionizing Oil & Gas Safety.pdfRejig Digital Unlock the future of oil & gas safety with advanced environmental detection technologies that transform hazard monitoring and risk management. This presentation explores cutting-edge innovations that enhance workplace safety, protect critical assets, and ensure regulatory compliance in high-risk environments.
🔍 What You’ll Learn:
✅ How advanced sensors detect environmental threats in real-time for proactive hazard prevention
🔧 Integration of IoT and AI to enable rapid response and minimize incident impact
📡 Enhancing workforce protection through continuous monitoring and data-driven safety protocols
💡 Case studies highlighting successful deployment of environmental detection systems in oil & gas operations
Ideal for safety managers, operations leaders, and technology innovators in the oil & gas industry, this presentation offers practical insights and strategies to revolutionize safety standards and boost operational resilience.
👉 Learn more: https://www.rejigdigital.com/blog/continuous-monitoring-prevent-blowouts-well-control-issues/
Your startup on AWS - How to architect and maintain a Lean and Mean account J...



Your startup on AWS - How to architect and maintain a Lean and Mean account J...angelo60207 Prevent infrastructure costs from becoming a significant line item on your startup’s budget! Serial entrepreneur and software architect Angelo Mandato will share his experience with AWS Activate (startup credits from AWS) and knowledge on how to architect a lean and mean AWS account ideal for budget minded and bootstrapped startups. In this session you will learn how to manage a production ready AWS account capable of scaling as your startup grows for less than $100/month before credits. We will discuss AWS Budgets, Cost Explorer, architect priorities, and the importance of having flexible, optimized Infrastructure as Code. We will wrap everything up discussing opportunities where to save with AWS services such as S3, EC2, Load Balancers, Lambda Functions, RDS, and many others.
TrustArc Webinar - 2025 Global Privacy Survey



TrustArc Webinar - 2025 Global Privacy SurveyTrustArc How does your privacy program compare to your peers? What challenges are privacy teams tackling and prioritizing in 2025?
In the sixth annual Global Privacy Benchmarks Survey, we asked global privacy professionals and business executives to share their perspectives on privacy inside and outside their organizations. The annual report provides a 360-degree view of various industries' priorities, attitudes, and trends. See how organizational priorities and strategic approaches to data security and privacy are evolving around the globe.
This webinar features an expert panel discussion and data-driven insights to help you navigate the shifting privacy landscape. Whether you are a privacy officer, legal professional, compliance specialist, or security expert, this session will provide actionable takeaways to strengthen your privacy strategy.
This webinar will review:
- The emerging trends in data protection, compliance, and risk
- The top challenges for privacy leaders, practitioners, and organizations in 2025
- The impact of evolving regulations and the crossroads with new technology, like AI
Predictions for the future of privacy in 2025 and beyond
If You Use Databricks, You Definitely Need FME



If You Use Databricks, You Definitely Need FMESafe Software DataBricks makes it easy to use Apache Spark. It provides a platform with the potential to analyze and process huge volumes of data. Sounds awesome. The sales brochure reads as if it is a can-do-all data integration platform. Does it replace our beloved FME platform or does it provide opportunities for FME to shine? Challenge accepted
Down the Rabbit Hole – Solving 5 Training Roadblocks



Down the Rabbit Hole – Solving 5 Training RoadblocksRustici Software Feeling stuck in the Matrix of your training technologies? You’re not alone. Managing your training catalog, wrangling LMSs and delivering content across different tools and audiences can feel like dodging digital bullets. At some point, you hit a fork in the road: Keep patching things up as issues pop up… or follow the rabbit hole to the root of the problems.
Good news, we’ve already been down that rabbit hole. Peter Overton and Cameron Gray of Rustici Software are here to share what we found. In this webinar, we’ll break down 5 training roadblocks in delivery and management and show you how they’re easier to fix than you might think.
Azure vs AWS Which Cloud Platform Is Best for Your Business in 2025



Azure vs AWS Which Cloud Platform Is Best for Your Business in 2025Infrassist Technologies Pvt. Ltd.
Ad
Function-and-prototype defined classes in JavaScript
- 1. Function-and-Prototype Defined Classes in JavaScript Hong Langford June 24, 2017
- 2. Overview • Objects and prototypes • Student-Grade example • this keyword • Constructor function • How does the new operator work in JavaScript • Inheritance with the prototype chain • The instanceof operator in JavaScript • References
- 3. Objects and Prototypes • Objects are JavaScript’s fundamental data structure. Intuitively, an object represents a table relating strings to values. But when you dig deeper, there is a fair amount of machinery that goes into objects.
- 4. • Like many object-oriented languages, JavaScript provides support for implementation inheritance: the reuse of code or data through a dynamic delegation mechanism. But unlike many conventional languages, JavaScript’s inheritance mechanism is based on prototypes rather than classes. For many programmers, JavaScript is the first object-oriented language they encounter without classes.
- 5. • JavaScript classes introduced in ECMAScript 2015 (ES6) are primarily syntactical sugar over JavaScript's existing prototype-based inheritance. The class syntax is not introducing a new object-oriented inheritance model to JavaScript. JavaScript classes provide a much simpler and clearer syntax to create objects and deal with inheritance for programmers who are used to classes.
- 6. • In many languages, every object is an instance of an associated class, which provides code shared between all its instances. JavaScript, by contrast, has no built-in notion of classes. Instead, objects inherit from other objects. Every object is associated with some other object, known as its prototype. Working with prototypes can be different from classes, although many concepts from traditional object-oriented languages still carry over.
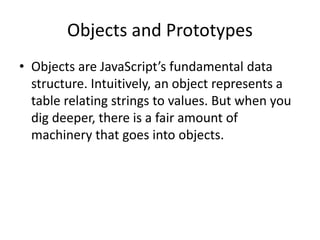
- 7. Student-Grade Example function Student(x) { this.name = x; this.grade = []; } Student.prototype = { addGrade: function(x) { this.grade.push(x); } }; var Tom = new Student("Tom"); Tom.addGrade(82); Tom.addGrade(75); Tom.addGrade(70);
- 8. var Sarah = new Student("Sarah"); Sarah.addGrade(83); Sarah.addGrade(88); Sarah.addGrade(91); var Vu = new Student("Vu"); Vu.addGrade(85); Vu.addGrade(79); Vu.addGrade(84); console.log(Tom, Sarah, Vu);
- 9. this keyword • A function's this keyword behaves a little differently in JavaScript compared to other languages. In most cases, the value of this is determined by how a function is called. It may be different each time the function is called.
- 10. Constructor Function • Constructor function – A "constructor" in JavaScript is "just" a function that happens to be called with the new operator.
- 11. How does the new operator work in JavaScript? • The new operator uses the internal [[Construct]] method, and it basically does the following: – Initializes a new object – Sets the internal [[Prototype]] of this object, pointing to the constructor function prototype property. – If the constructor function's prototype property is not an object (but a primitive value, such as a Number, String, Boolean, Undefined or Null), Object.prototype is used instead.
- 12. – After creating the object, it calls the function, providing the object as its this value. – If the return value of the called function, is a primitive, the object created internally is returned. – Otherwise, if an object is returned, the object created internally is lost.
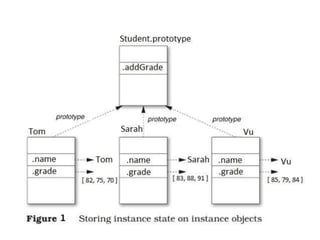
- 13. • { name: 'Tom', grade: [ 82, 75, 70 ] } { name: 'Sarah', grade: [ 83, 88, 91 ] } { name: 'Vu', grade: [ 85, 79, 84 ] }
- 15. Inheritance with the Prototype Chain • When it comes to inheritance, JavaScript only has one construct: objects. Each object has a private property (referred to as [[Prototype]] ) which holds a link to another object called its prototype. That prototype object has a prototype of its own, and so on until an object is reached with null as its prototype. By definition, null has no prototype, and acts as the final link in this prototype chain.
- 16. • Nearly all objects in JavaScript are instances of Object constructor which sits on the top of a prototype chain. And the prototype of Object’s prototype is not pointing anywhere but just null .
- 17. The instanceof operator in JavaScript • The instanceof operator tests presence of constructor.prototype in object's prototype chain.
- 18. References 1. David Herman, Effective JavaScript: 68 Specific Ways to Harness the Power of JavaScript (Effective Software Development Series), Addison-Wesley Professional, 1 edition (December 6, 2012). 2. https://stackoverflow.com/questions/6750880/ how-does-the-new-operator-work-in-javascript 3. https://developer.mozilla.org/en- US/docs/Web/JavaScript/Reference
- 19. Thank You!
Editor's Notes
- #8: C:\Users\Hong\WebstormProjects\studentgradeproj Question: what’s the result?
- #9: Question: what’s the result?
- #10: Later, we will see what the value of this is in our example.
- #13: So in our example, the value of this is Tom when executing var Tom = new Student("Tom"); Any questions? See Example 2 returnobject.js // defining constructors function C() { this.name = "Jack"; //return {a:1}; }; function D() { this.name = "Linda"; } var o = new C(); var o2 = new D(); console.log(o, o2); //C { name: 'Jack' } D { name: 'Linda' }
- #15: Question: Why use prototypes? Using prototypes can save memory. Any questions?
- #16: https://developer.mozilla.org/en-US/docs/Web/JavaScript/Inheritance_and_the_prototype_chain Mention example.
- #18: See Example 3 instanceof.js in webstorm. // defining constructors function C() {} function D() {} var o = new C(); // true, because: Object.getPrototypeOf(o) === C.prototype console.log(o instanceof C); // false, because D.prototype is nowhere in o's prototype chain console.log(o instanceof D); console.log(o instanceof Object); // true, because: console.log(C.prototype instanceof Object) // true
