Implementation of energy efficient coverage aware routing protocol for wireless sensor network using genetic algorithm
- 1. International Journal in Foundations of Computer Science & Technology (IJFCST), Vol.5, No.1, January 2015 DOI:10.5121/ijfcst.2015.5103 23 IMPLEMENTATION OF ENERGY EFFICIENT COVERAGE AWARE ROUTING PROTOCOL FOR WIRELESS SENSOR NETWORK USING GENETIC ALGORITHM Khushbu Babbar1 , Kusum Lata Jain2 and G.N. Purohit3 Department of Computer Engineering, Banasthali University, Jaipur, Rajasthan ABSTRACT In recent years, wireless sensor network have been used in many application such as disaster reservation, agriculture, environmental observation and forecasting .Coverage preservation and energy consumption are two most important issues in wireless sensor networks. To increase the network lifetime, we propose an energy efficient coverage aware routing protocol for wireless sensor network for randomly deployed sensor nodes. Some of the routing protocol is based on energy efficiency and some are based on coverage aware. The proposed routing protocol is based on both the issues i.e. coverage and energy, in which we first find the k-mean i.e. the degree of coverage, so that we can use this in the selection of cluster heads in wireless sensor network by using Genetic Algorithm for increasing network lifetime and coverage. For cluster head selection each node evaluates its k-mean and energy by internal function which used as fitness function in genetic algorithm. The proposed algorithm “Implementation of energy efficient coverage aware routing protocol for Wireless Sensor Network” is designed for homogeneous wireless sensor network. Simulations results show that proposed algorithm increases the network lifetime by reduce the energy consumption and preserve coverage. Simulation is done with MATLAB and a comparison of algorithm with benchmark algorithms is also performed. KEYWORDS Wireless Sensor Network, Genetic Algorithm, Coverage, Single hop Communication, K-mean, Cluster. 1. INTRODUCTION Wireless sensor network (WSN) has emerged as an important area for research and development. Wireless sensor networks are found suitable for applications such a surveillance, agriculture, smart homes, traffic management, disaster detection etc. The key constraints in the development of WSNs are cost, limited energy, limited memory, limited computational capability, and the memory size of the sensor nodes. Many routing protocols for WSNs have been developed. The major routing challenges and design issues that affect routing process in WSN are whether node deployment is defined or not, Energy consumption of node without losing accuracy of data, Data Reporting Model of node, Node Heterogeneity, Fault Tolerance, network support for Scalability, Network Dynamics, Transmission Media, Connectivity, Coverage, area of sensor network, Data Aggregation of repeated data packets, Quality of Service in data delivery. There are many aspects which affect the routing protocol design we consider only the limited computing power of nodes. Rather there are number of approaches for the WSN, the research is based on the Hierarchical approach. A critical aspect of applications in WSN is network lifetime. WSN are usable as long as they can communicate sensed data to processed node. Sensing and communication are important activities and they consume energy so power management and coverage preservation
- 2. International Journal in Foundations of Computer Science & Technology (IJFCST), Vol.5, No.1, January 2015 24 can effectively increase the network lifetime. In some protocols sensor nodes transmit their sensed data directly to a BS. Thus, the nodes located far from the BS will die quickly since they dissipate more energy in transmitting data packets. Clustering is used as a tool for the energy efficient coverage aware routing protocol, and in this protocol network is organized in clusters. Such a sensor network contains two types of nodes; cluster head and cluster members. All the data processing such as data fusion and aggregation are local to the cluster. Cluster heads changes over time in order to balance the energy dissipation of nodes. Cluster member sense the data and send it to cluster head and cluster head sends the data to BS. Many protocols are made which is based on energy efficiency and some are based on coverage. Thus, there is a need of a new protocol scheme, which is based on both energy efficiency and coverage to increase the network lifetime. In this paper, we analyze energy efficient coverage aware routing protocol for homogeneous wireless sensor network in which genetic algorithm used for cluster head selection for WSN. We first describe the protocol and then we provide simulation results in MATLAB and determine performance analysis of given protocol compared with benchmark clustering algorithm LEACH. The paper is organized as follows. In the Section -2, LEACH protocol and its limitations are discussed, Section -3 summarizes Genetic Algorithm, Section-4 summarizes network parameter Description of the proposed algorithm is included in Section – 5 and Section6 and 7 includes the network preliminaries and Section-8 includes the simulation results and the final discussion is concluded in Section-9. 2. LEACH PROTOCOL The LEACH protocol is one of the bench-mark protocols in the Wireless Sensor Networks. LEACH protocol has two phases: Setup phase and Steady state phase. In the setup phase, nodes are organized into clusters and in the steady state phase data is transferred from cluster head to sink via single-hop method. In each cluster a node is selected as a cluster head and the remaining nodes are called cluster-members. Data collected by the member nodes, locally processed by the cluster head. Due to local data processing and data transmission from cluster head to base station, cluster heads consume more energy than energy consumed by member nodes. Our paper has highlighted the practical implementation of protocol in MATLAB and determines network lifetime. 2.1. Limitations In LEACH location of the cluster head is on random basis. This is also true for the number of cluster member in a cluster. An optimum solution for both of above mentioned issues is always required. Establish control over location of cluster heads and size of the clusters in terms of number of members always has been considered as a challenge and solving this problem requires efficient clustering algorithms in energy consumption and network load balancing. In the following section, a new approach is suggested for the optimal selection of cluster head using genetic algorithm. The approach is based in the density of nodes in the network. Following figures express the effect of density in nodes organization. Figure 1(a), shows the nodes organization just according to nodes energy and regardless of density that is not optimal in number of nodes. Figure (b), express the nodes organization according to nodes density that is more optimum location for the cluster head. 3. GENETIC ALGORITHM Genetic algorithms are randomized search and optimization techniques guided by the principles of evolution and natural genetics. GAs perform search in complex, large landscapes, and provide
- 3. International Journal in Foundations of Computer Science & Technology (IJFCST), Vol.5, No.1, January 2015 25 near-optimal solutions for objective. Initially, the genetic algorithm begins with a primary population including random chromosomes that consist of genes. In the next step, the algorithm biases individuals toward the optimum solution through repetitive processes such as crossover and selection operators. A new population can be produced by two methods: steady-state GA and generational GA. In the first case, one or two members of population are replaced, while the generational GA replaces all the produced individuals at each generation. Proposed algorithm uses the second method so that the GA keeps the specified qualified individuals from the current generation and copies them into the new generation as part of the solution. Other individuals of the new population are obtained by crossover and mutation functions. Following steps are used in proposed genetic algorithm [Start] Generate random population of n chromosomes (suitable solutions for the problem) [Fitness] Evaluate the fitness f(x) of each chromosome x in the population [New population] Create a new population by repeating following steps until the new population is complete [Selection] Select two parent chromosomes from a population according to their fitness (the better fitness, the bigger chance to be selected) [Crossover] With a crossover probability cross over the parents to form a new offspring (children). If no crossover was performed, offspring is an exact copy of parents. [Mutation] With a mutation probability mutate new offspring at each locus (position in chromosome). [Accepting] Place new offspring in a new population [Replace] Use new generated population for a further run of algorithm [Test] If the end condition is satisfied, stop, and return the best solution in current population [Loop] Go to step 2 4. NETWORK AND ENERGY PARAMETERS Network Lifetime: Network Lifetime is the number of rounds in which the first node dies in round based routing protocol. In the random selection method cluster head selection in each round is done on the basis of 1/p and residual energy. When a node becomes dead in the network, it will not be the part of the network. Coverage: A point in network considered as covered if it is in sensing range of node. In proposed work Coverage is calculated percentage as number of points in the network is covered by sensing range of at least one node at a given time. Coverage= Number of point of network covered by sensing range of at least one node/ total number of points in the network* 100. The main contribution of my work is the design, implementation and verification of a new protocol using k-mean and genetic algorithm. The proposed algorithm “Energy Efficient Coverage Aware Routing Protocol for Wireless Sensor Network” is designed for homogeneous wireless sensor network. Proposed algorithm is based on both critical issue energy and coverage. Simulations results show that proposed algorithm increases the network lifetime by reduce the energy consumption and preserve coverage. Simulation is done with MATLAB and a comparison of algorithm with benchmark algorithms is also performed. 5. PROPOSED APPROACH FOR CLUSTERING USING GENETIC ALGORITHM Proposed algorithm works in rounds. Each round consists of Initial phase and Steady phase. In this study, single-hop communication is used within the normal nodes and from cluster head to BS. Network administrator selects a threshold value for the cluster head selection process. In
- 4. International Journal in Foundations of Computer Science & Technology (IJFCST), Vol.5, No.1, January 2015 26 Initial phase all nodes send the residual energy, k-mean and probability parameters to the own internal function to calculate fitness function. K-mean i.e. degree of coverage means sensor node covered by k nodes which are in its sensing range. According to the result of internal function, the node starts a counter. The nodes with high result of internal function are selected by the network administrator and notify its candidacy as cluster head to the base station. The objective of the process to find the cluster heads with higher capabilities and distribute them in the network so that the total network energy consumption is minimized and coverage get preserved. 5.1. Details of algorithm 5.1.1. Initial phase: In initial phase of each round a population and fitness function is be used to select cluster head and cluster member. In first round of algorithm choose K initial cluster heads z1, z2……, zK from the n nodes {x1, x2,……,xn}. Than cluster member will be selected for each cluster head. Step1: Initially all nodes have same probability to become a cluster head. Step2: F(t) is the fitness function used to select the cluster head and defined as F(t)=(Er * T(n) * Kmean)) where Er=Residual energy of the node T(n)= probability of node to become cluster head as given by LEACH Kmean= Degree of coverage In this equation the energy, kmean and probability have a direct relationship with the output of function, so increased value of inputs will produce a larger output the optimal value obtained for a particular node will be eligible to be a cluster node. Step 3: After calculating this built in F(t) function. All nodes sort in descending order. For each network, network administrator decides number of cluster heads. Candidate nodes send their information to the sink for cluster head selection. Step 4: Selection of Cluster Head BS selects the cluster head and the result is sent to the network. At the BS a predefined number of nodes introduced themselves as the candidate of cluster head will determine the length of the chromosome. Each of the genes in this chromosome is identifier of number of network nodes. Single-point crossover is performed on chromosome which is selected and mutation is performed, that may change a bit by leap or jump a bit state to generate one or more new chromosomes. After this base station selects a chromosome that has minimum difference of energy from last round and with best probability and high distribution function as cluster head to network. Other nodes bind to the nearest cluster head. Step 5: BS will send the information to selected cluster head Step 6: Cluster Formation Selected cluster head send advertisement to normal nodes. Non cluster head nodes join to closest CH to form cluster Step 7: Sensing unneeded node to sleep state
- 5. International Journal in Foundations of Computer Science & Technology (IJFCST), Vol.5, No.1, January 2015 27 If k-coverage of area>2 then node deployed in that area will goes into sleep mode. Selection of node will be done by round robin algorithm. 5.1.2. Steady State Phase After initial state each node knows its cluster head. In each period a cluster head only receive one package form each member nodes of the cluster. Cluster head aggregate the data and send to it BS 5.2 Pseudo-code of the Proposed Approach: BEGIN 1: Specify the probability (p), number of nodes (n); 2: Einit(s)=E0, s=1,2, …, n; 5.2.1 Initial Phase 1: Each node calculate Fitness Function F(t) 2: Start Counter 4: CCH{s}=TRUE; //node s be a candidate CH 3: SendToBS(IDx,) (Xx,Yx) // The first predefine number of node reaches at threshold value will sends their candidacy to the sink for cluster head selection. 5: GAinBS //BS perform the GA on the node which sends their candidacy for cluster and select cluster head for the network. 6: SendToCH ← BS send message to selected cluster head. 7: if (CH{s}=TRUE) then 8: BC (ADV) ← broadcast an advertisement message; 9: Join(IDi); //non-cluster head node i join into the closest CH 10: K-coverage of area> 2 then node in that area will goes into sleep mode //Selection of node will be done by round robin algorithm 11: Cluster(c); //form a cluster c; 12: end if 5.2.2 STEADY-STATE PHASE 1: If (CH(s)=TRUE) then 2: Receive(IDi, Data) //receive data from members; 3: Aggregate(IDi, Data) //aggregate received data; 4: TansToBS(IDi, Data); //transmit received data; 5: else 6: TansToCH(IDi, Data); //transmit sensed data; 7: end if 8: end if 9: } // round is completed END 6. NETWORK PRELIMINARIES Simulation is done with MATLAB. A network with 100 nodes deployed over an area of size 100 x 100 m2 . All nodes are of same specification. All nodes in the network are having the same
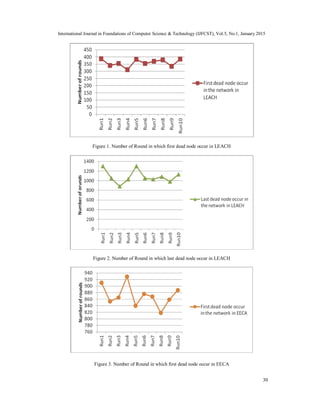
- 6. International Journal in Foundations of Computer Science & Technology (IJFCST), Vol.5, No.1, January 2015 28 energy at starting point and having maximum energy. All nodes consume same energy for transmission and reception Sensor nodes have three states –In the active mode, a sensor observes the environment and communicates with other sensors. In the sleep mode, a sensor cannot sense or transmit data .In off mode, the nodes are completely turned off .A sensor can change to active mode from sleep mode to active mode whenever it receives appropriate signal from base station. In this proposed algorithm, sleep and active mode are used. The nodes are randomly deployed. Simulations performed for performance analysis of proposed algorithm. The simulation result gives in terms of the coverage percentage of network area. The coverage percentage is calculated on the basis of percentage of X, Y point covered by sensing range of at least one node in the network and a comparison of algorithm with benchmark algorithms is also performed. 7. SIMULATION PARAMETERS Simulation Parameters : following simulation parameters are used to perform simulation. Table1: Simulation parameters Table 2: The values of genetic algorithm 8. SIMULATION RESULTS The comparison is done between the LEACH and CPCP protocol with the new technique under the same simulation condition and values. Table 3 lists the obtained simulation results using LEACH, CPCP and EECA. Table 4 shows the comparison and the number of rounds after which first dead node and last dead node occur in the network when all nodes are active using LEACH and EECA. As results shows that the number of round in which first round dead is 322 from 10 simulations with LEACH protocol is increased to 870 rounds with proposed algorithm. The Parameter Values Simulation Round 8000 Number of rounds 100+1(Node+BS) Topology Size 100 X 100 CH probability 0.05 Initial Node Power 0.5 Joule Nodes Distribution Nodes are Randomly Distributed Energy for Transmission (ETX) 50*0.000000001 Energy for Reception (ERX) 50*0.000000001 Energy for Data Aggregation (EDA) 5*0.000000001 Parameter Value Initial population 100 Crossover rate 0.5 Mutation rate 0.5
- 7. International Journal in Foundations of Computer Science & Technology (IJFCST), Vol.5, No.1, January 2015 29 proposed technique has improved the performance in terms of increasing the network lifetime by comparing with LEACH. Table 5 shows the comparison and the number of rounds after which first dead node occur in the network when all nodes and selected nodes are active according to k- mean using CPCP and EECA. As a results shows that that the number of round in which first dead nodes when all nodes are active is 788 and selected nodes are active is 876 from 10 simulation with CPCP protocol is increased to 858 and 1509 respectively The proposed technique has improved the performance in terms of coverage by comparing with CPCP protocol. The results show that the proposed approach outperforms LEACH and CPCP in terms of lifetime of network and coverage. Table 3. Number of round in which first dead node and last dead node occur in the network for CPCP and LEACH Routing Protocols Round number in which first dead node occur Round number in which last dead node occur EECA 1701 7414 LEACH 387 1302 CPCP 903 6051 Table 1. Comparison of LEACH and EECA Simulation Run LEACH EECA Round number in which first dead node occur when all nodes are active Round number in which last dead node occur when all nodes are active Round number in which first dead node occur when all nodes are active Round number in which last dead node occur when all nodes are active Simulation Run1 387 1302 910 2701 Simulation Run2 340 1049 853 2281 Simulation Run3 355 885 865 3060 Simulation Run4 312 1029 929 3240 Simulation Run5 383 1301 840 2640 Simulation Run6 354 1051 876 3380 Simulation Run7 370 1030 868 3080 Simulation Run8 380 1084 818 3540 Simulation Run9 335 982 859 2321 Simulation Run10 386 1127 888 2633
- 8. International Journal in Foundations of Computer Science & Technology (IJFCST), Vol.5, No.1, January 2015 30 Figure 1. Number of Round in which first dead node occur in LEACH Figure 2. Number of Round in which last dead node occur in LEACH Figure 3. Number of Round in which first dead node occur in EECA
- 9. International Journal in Foundations of Computer Science & Technology (IJFCST), Vol.5, No.1, January 2015 31 Figure 4. Number of Round in which last dead node occur in EECA Table 1. Comparison of CPCP and EECA Simulation Run CPCP EECA Round number in which first dead node occur when all nodes are active Round number in which first dead node occur when selected nodes are active Round number in which first dead node occur when all nodes are active Round number in which last dead node occur when selected nodes are active Simulation Run1 801 840 840 1714 Simulation Run2 790 890 810 1660 Simulation Run3 808 912 876 1552 Simulation Run4 789 899 818 1767 Simulation Run5 779 801 859 1195 Simulation Run6 806 812 828 1785 Simulation Run7 803 913 929 1719 Simulation Run8 781 905 888 1498 Simulation Run9 768 892 870 1096 Simulation Run10 760 902 868 1105
- 10. International Journal in Foundations of Computer Science & Technology (IJFCST), Vol.5, No.1, January 2015 32 Figure 5. Number of Round in which first dead node occur when all nodes are active in CPCP Figure 6. Number of Round in which first dead node occur when all nodes are active in EECA Figure 7. Number of Round in which first dead node occur when selected nodes are active in CPCP
- 11. International Journal in Foundations of Computer Science & Technology (IJFCST), Vol.5, No.1, January 2015 33 Figure 8. Number of Round in which first dead node occur when selected nodes are active In EECA 9. CONCLUSIONS In this paper, new approach Energy Efficient Coverage Aware routing protocol architecture, reduce energy consumption by using clustering technique, therefore increase system lifetime, and increase coverage of network by turning off some redundant nodes. The performance evaluation in terms of network lifetime and coverage was conducted using MATLAB. This work proposed a genetic algorithm based new approach for clustering for wireless sensor network. The LEACH protocol does not consider k-mean of the node in cluster head selection. Proposed algorithm is for the homogeneous network which uses k-mean method for cluster head selection and in this BS selects the cluster head from the candidate cluster head using genetic algorithm. The proposed technique has improved the performance in terms of network lifetime and coverage by comparing with LEACH and CPCP protocol. The simulation result also shows that 95% of network area gets covered. Hence proposed routing protocol work for both important issues of the wireless sensor network i.e. network lifetime and coverage. REFERENCES [1] A.Mainwaring, D.Culler, J.Polastre, RSzewczyk and J.Anderson, “Wireless Sensor networks for habitat monitoring “International Workshop on Wireless Sensor networks and Applications,ACM,pp.88-97,2002 [2] Zude Zhou, Zheng Huang, Quan Liu,Ying Zhou “A Study on the Coverage Problem in Wireless Sensor Network.” International Conference on Wireless Mobile and Multimedia Network (ICWMMN),PP.1-3,2006. [3] M.Cardei and D.Du, “Improving Wireless Sensor Network Lifetime through Power Aware Organization”, Wireless Networks, Vol 11, Issue 3.May 2005 [4] Dantu,K., Rahimi, M.,Shah, H., Babel, S., Dhariwal, A., and Sukhatme,G. “Robomote: Enabling Mobility In Sensor Networks” IEEE/ACM International Conference Information Processing in Sensor Networks(ISPN’05), Apr. 2005 [5] Mihaela Cardei and Jie Wu “Coverage in Wireless Sensor Networks” lorida Atlantic University Boca Raton, FL 33431 [6] Raymond Mulligan” Network Protocols and Algorithms” ISSN 1943-35812010, Vol. 2, No. 2
- 12. International Journal in Foundations of Computer Science & Technology (IJFCST), Vol.5, No.1, January 2015 34 [7] Sunita Gupta, Dr.K.C.Roy”Energy Efficient Target Coverage Issues in Wireless Sensor Network” International Journal of Computer& Organization Trends ,Volume1 Issue3,2011 [8] Jiwan N.Dehankar Pragati Patil Girish Agarwal” Energy Consumption in Wireless sensor Network” International Journal of Engineering Research & Technology, ISSN: 2278-0181, Vol. 2 Issue 1, January- 2013 [9] Rathna .R,Siva Subarmanian. A” Improving Energy Efficiency in Wireless sensor networks” International Journal Of Advanced Smart Sensor Network Systems ( IJASSN ), Vol 2, No.1, January 2012 [10] Bang Wang,Hock Beng Lim, Di Ma, “A coverage-aware clustering protocol for wireless sensor networks”, Computer Networks 56 (2012) 1599-1611 [11] Jiguo Yu, Yingying Qi, Guanghui Wang, Xin Gu, “A cluster-based routing protocol for wireless sensor networks with non uniform node distribution”, International Journal of Electronics and Communications (AEU) 66 (2012) 54-61 [12] Nauman Aslam, William Phillips, William Robertson, Shyamala Sivakumar, “A multi-criterion optimization technique for energy Efficient cluster formation in wireless sensor networks”, Information Fusion 12 (2011) 202-212. [13] Stanislva Soro,Wendi B.Heinzelman,”Cluster head election techniques for coverage preservation in wireless sensor networks”, Ad Hoc Networks 7 (2009) 955-972. [14] Sudip Misra, Manikonda Pavan Kumar, Mohammad S. Obaidat, “Connectivity preserving localized coverage algorithm for area monitoring using wireless sensor networks”, Computer Communications 34 (2011) 1484-1496. [15] Yaling Tao, Yongbing Zhang, Yusheng Ji, “Flow-balanced routing for multi-hop clustered wireless sensor networks”, Ad Hoc Networks 11 (2013) 541-554. [16] Miao Peng, Hui Chen, Yang Xiao, Suat Ozdemir, Athanasios V.Vasilakos, Jie Wu, “Impacts of sensor node distributions on coverage in sensor networks”, Journal of Parallel and Distributed Computing 71 (2011) 1578-1591. [17] GUO Jian, SUN Lijuan, WANG Rachuan, XIAO Fu, “A low coverage first classifying algorithm for wireless sensor networks”, Procedia Engineering 15 (2011) 3825-3830. [18] H.Hwa-Chun Ma, Prasan Kumar Sahoo, Yen-Wen Chen, “Computational geometry based distributed coverage hole detection protocol for the wireless sensor networks”, Journal of Network and Computer Applications 34 (2011) 1743-1756. [19] Bang Wang, Cheng Fu,Hock Beng Lim,”Layered Diffusion based coverage control in wireless sensor networks,” Computer Networks 53(2009) 1114-1124 [20] Yan Jin, Ju-Yeon Jo, Ling Wang, Yoohwan Kim, Xiaozong Yang, “ECCRA:An energy-efficient coverage and connectivity preserving routing algorithm under border effects in wireless sensor networks, Computer Communications 31 (2008) 2398-2407. [21] S.Hussain, A.Matin and O.Islam, “Genetic Algorithm for Hierarchical Wireless Sensor Network,” Journal of Networks, Vol. 2, No. 5, 2007, pp. 87-97. [22] A.P.Bhondekar, R.Vig, M.L.Singla, C. Ghanshyam and P. Kapur, “Genetic Algorithm Based Node Placement Methodology for Wireless Sensor Networks,” Proceeding of the International Multi- Conference of Engineering and Computer Science, Hong Kong, 18-20 March 2009, pp. 106-112. [23] S.Ghiasi, A.Srivastava, X.Yang and M. Sarrafzadeh, “Optimal Energy Aware Clustering in Sensor Networks,” Sensors, vol. 2, No. 7, 2002, pp. 258–259. [24] K.Kalpakis, K.Dasgupta and P. Namjoshi, “Maximum Lifetime Data Gathering and Aggregation in Wireless Sensor Networks,” In IEEE International Conference on Networking, Atlanta, 26-29 August 2002, pp. 685-696. [25] S.Bandyopadhyay and E.J.Coyle, “An Energy Efficient Hierarchical Clustering Algorithm for Wireless Sensor Networks.” In Proceedings of the IEEE Conference on Computer Communications (INFOCOM), San Francisco, 30 March-3 April 2003, pp. 1713-1723. [26] J.Jabari Lotf, S.H.Hosseini Nazhad Ghazani and R. M. Alguliev, “A New Cluster-Based Routing Protocol with Maximum Lifetime for Wireless Sensor Networks,” In International Journal of Computer and Network Security, vol. 2, No. 6, 2010, pp. 133-137. [27] D.Turgut, S.K.Das, R.Elmasri and B. Turgut, “Opti-mizing Clustering Algorithm in Mobile Ad Hoc Net-works Using Genetic Algorithmic Approach,” In Pro-ceedings of the Global Telecommunications Conference (GLOBECOM), Taibei, November 2002, pp. 62-66.



![International Journal in Foundations of Computer Science & Technology (IJFCST), Vol.5, No.1, January 2015
25
near-optimal solutions for objective. Initially, the genetic algorithm begins with a primary
population including random chromosomes that consist of genes. In the next step, the algorithm
biases individuals toward the optimum solution through repetitive processes such as crossover
and selection operators. A new population can be produced by two methods: steady-state GA and
generational GA. In the first case, one or two members of population are replaced, while the
generational GA replaces all the produced individuals at each generation. Proposed algorithm
uses the second method so that the GA keeps the specified qualified individuals from the current
generation and copies them into the new generation as part of the solution. Other individuals of
the new population are obtained by crossover and mutation functions. Following steps are used in
proposed genetic algorithm
[Start] Generate random population of n chromosomes (suitable solutions for the problem)
[Fitness] Evaluate the fitness f(x) of each chromosome x in the population
[New population] Create a new population by repeating following steps until the new
population is complete
[Selection] Select two parent chromosomes from a population according to their fitness (the
better fitness, the bigger chance to be selected)
[Crossover] With a crossover probability cross over the parents to form a new offspring
(children). If no crossover was performed, offspring is an exact copy of parents.
[Mutation] With a mutation probability mutate new offspring at each locus (position in
chromosome).
[Accepting] Place new offspring in a new population
[Replace] Use new generated population for a further run of algorithm
[Test] If the end condition is satisfied, stop, and return the best solution in current population
[Loop] Go to step 2
4. NETWORK AND ENERGY PARAMETERS
Network Lifetime: Network Lifetime is the number of rounds in which the first node dies in
round based routing protocol. In the random selection method cluster head selection in each round
is done on the basis of 1/p and residual energy. When a node becomes dead in the network, it will
not be the part of the network.
Coverage: A point in network considered as covered if it is in sensing range of node. In proposed
work Coverage is calculated percentage as number of points in the network is covered by sensing
range of at least one node at a given time.
Coverage= Number of point of network covered by sensing range of at least one node/ total
number of points in the network* 100.
The main contribution of my work is the design, implementation and verification of a new
protocol using k-mean and genetic algorithm. The proposed algorithm “Energy Efficient
Coverage Aware Routing Protocol for Wireless Sensor Network” is designed for homogeneous
wireless sensor network. Proposed algorithm is based on both critical issue energy and coverage.
Simulations results show that proposed algorithm increases the network lifetime by reduce the
energy consumption and preserve coverage. Simulation is done with MATLAB and a comparison
of algorithm with benchmark algorithms is also performed.
5. PROPOSED APPROACH FOR CLUSTERING USING GENETIC ALGORITHM
Proposed algorithm works in rounds. Each round consists of Initial phase and Steady phase. In
this study, single-hop communication is used within the normal nodes and from cluster head to
BS. Network administrator selects a threshold value for the cluster head selection process. In](https://image.slidesharecdn.com/implementationofenergyefficientcoverageawareroutingprotocolforwirelesssensornetworkusinggeneticalgor-150212233519-conversion-gate02/85/Implementation-of-energy-efficient-coverage-aware-routing-protocol-for-wireless-sensor-network-using-genetic-algorithm-3-320.jpg)






![International Journal in Foundations of Computer Science & Technology (IJFCST), Vol.5, No.1, January 2015
33
Figure 8. Number of Round in which first dead node occur when selected nodes are active
In EECA
9. CONCLUSIONS
In this paper, new approach Energy Efficient Coverage Aware routing protocol architecture,
reduce energy consumption by using clustering technique, therefore increase system lifetime, and
increase coverage of network by turning off some redundant nodes. The performance evaluation
in terms of network lifetime and coverage was conducted using MATLAB. This work proposed a
genetic algorithm based new approach for clustering for wireless sensor network. The LEACH
protocol does not consider k-mean of the node in cluster head selection. Proposed algorithm is for
the homogeneous network which uses k-mean method for cluster head selection and in this BS
selects the cluster head from the candidate cluster head using genetic algorithm. The proposed
technique has improved the performance in terms of network lifetime and coverage by comparing
with LEACH and CPCP protocol. The simulation result also shows that 95% of network area gets
covered. Hence proposed routing protocol work for both important issues of the wireless sensor
network i.e. network lifetime and coverage.
REFERENCES
[1] A.Mainwaring, D.Culler, J.Polastre, RSzewczyk and J.Anderson, “Wireless Sensor networks for
habitat monitoring “International Workshop on Wireless Sensor networks and
Applications,ACM,pp.88-97,2002
[2] Zude Zhou, Zheng Huang, Quan Liu,Ying Zhou “A Study on the Coverage Problem in Wireless
Sensor Network.” International Conference on Wireless Mobile and Multimedia Network
(ICWMMN),PP.1-3,2006.
[3] M.Cardei and D.Du, “Improving Wireless Sensor Network Lifetime through Power Aware
Organization”, Wireless Networks, Vol 11, Issue 3.May 2005
[4] Dantu,K., Rahimi, M.,Shah, H., Babel, S., Dhariwal, A., and Sukhatme,G. “Robomote: Enabling
Mobility In Sensor Networks” IEEE/ACM International Conference Information Processing in Sensor
Networks(ISPN’05), Apr. 2005
[5] Mihaela Cardei and Jie Wu “Coverage in Wireless Sensor Networks” lorida Atlantic University Boca
Raton, FL 33431
[6] Raymond Mulligan” Network Protocols and Algorithms” ISSN 1943-35812010, Vol. 2, No. 2](https://image.slidesharecdn.com/implementationofenergyefficientcoverageawareroutingprotocolforwirelesssensornetworkusinggeneticalgor-150212233519-conversion-gate02/85/Implementation-of-energy-efficient-coverage-aware-routing-protocol-for-wireless-sensor-network-using-genetic-algorithm-11-320.jpg)
![International Journal in Foundations of Computer Science & Technology (IJFCST), Vol.5, No.1, January 2015
34
[7] Sunita Gupta, Dr.K.C.Roy”Energy Efficient Target Coverage Issues in Wireless Sensor Network”
International Journal of Computer& Organization Trends ,Volume1 Issue3,2011
[8] Jiwan N.Dehankar Pragati Patil Girish Agarwal” Energy Consumption in Wireless sensor Network”
International Journal of Engineering Research & Technology, ISSN: 2278-0181, Vol. 2 Issue 1,
January- 2013
[9] Rathna .R,Siva Subarmanian. A” Improving Energy Efficiency in Wireless sensor networks”
International Journal Of Advanced Smart Sensor Network Systems ( IJASSN ), Vol 2, No.1, January
2012
[10] Bang Wang,Hock Beng Lim, Di Ma, “A coverage-aware clustering protocol for wireless sensor
networks”, Computer Networks 56 (2012) 1599-1611
[11] Jiguo Yu, Yingying Qi, Guanghui Wang, Xin Gu, “A cluster-based routing protocol for wireless
sensor networks with non uniform node distribution”, International Journal of Electronics and
Communications (AEU) 66 (2012) 54-61
[12] Nauman Aslam, William Phillips, William Robertson, Shyamala Sivakumar, “A multi-criterion
optimization technique for energy Efficient cluster formation in wireless sensor networks”,
Information Fusion 12 (2011) 202-212.
[13] Stanislva Soro,Wendi B.Heinzelman,”Cluster head election techniques for coverage preservation in
wireless sensor networks”, Ad Hoc Networks 7 (2009) 955-972.
[14] Sudip Misra, Manikonda Pavan Kumar, Mohammad S. Obaidat, “Connectivity preserving localized
coverage algorithm for area monitoring using wireless sensor networks”, Computer Communications
34 (2011) 1484-1496.
[15] Yaling Tao, Yongbing Zhang, Yusheng Ji, “Flow-balanced routing for multi-hop clustered wireless
sensor networks”, Ad Hoc Networks 11 (2013) 541-554.
[16] Miao Peng, Hui Chen, Yang Xiao, Suat Ozdemir, Athanasios V.Vasilakos, Jie Wu, “Impacts of
sensor node distributions on coverage in sensor networks”, Journal of Parallel and Distributed
Computing 71 (2011) 1578-1591.
[17] GUO Jian, SUN Lijuan, WANG Rachuan, XIAO Fu, “A low coverage first classifying algorithm for
wireless sensor networks”, Procedia Engineering 15 (2011) 3825-3830.
[18] H.Hwa-Chun Ma, Prasan Kumar Sahoo, Yen-Wen Chen, “Computational geometry based distributed
coverage hole detection protocol for the wireless sensor networks”, Journal of Network and Computer
Applications 34 (2011) 1743-1756.
[19] Bang Wang, Cheng Fu,Hock Beng Lim,”Layered Diffusion based coverage control in wireless sensor
networks,” Computer Networks 53(2009) 1114-1124
[20] Yan Jin, Ju-Yeon Jo, Ling Wang, Yoohwan Kim, Xiaozong Yang, “ECCRA:An energy-efficient
coverage and connectivity preserving routing algorithm under border effects in wireless sensor
networks, Computer Communications 31 (2008) 2398-2407.
[21] S.Hussain, A.Matin and O.Islam, “Genetic Algorithm for Hierarchical Wireless Sensor Network,”
Journal of Networks, Vol. 2, No. 5, 2007, pp. 87-97.
[22] A.P.Bhondekar, R.Vig, M.L.Singla, C. Ghanshyam and P. Kapur, “Genetic Algorithm Based Node
Placement Methodology for Wireless Sensor Networks,” Proceeding of the International Multi-
Conference of Engineering and Computer Science, Hong Kong, 18-20 March 2009, pp. 106-112.
[23] S.Ghiasi, A.Srivastava, X.Yang and M. Sarrafzadeh, “Optimal Energy Aware Clustering in Sensor
Networks,” Sensors, vol. 2, No. 7, 2002, pp. 258–259.
[24] K.Kalpakis, K.Dasgupta and P. Namjoshi, “Maximum Lifetime Data Gathering and Aggregation in
Wireless Sensor Networks,” In IEEE International Conference on Networking, Atlanta, 26-29 August
2002, pp. 685-696.
[25] S.Bandyopadhyay and E.J.Coyle, “An Energy Efficient Hierarchical Clustering Algorithm for
Wireless Sensor Networks.” In Proceedings of the IEEE Conference on Computer Communications
(INFOCOM), San Francisco, 30 March-3 April 2003, pp. 1713-1723.
[26] J.Jabari Lotf, S.H.Hosseini Nazhad Ghazani and R. M. Alguliev, “A New Cluster-Based Routing
Protocol with Maximum Lifetime for Wireless Sensor Networks,” In International Journal of
Computer and Network Security, vol. 2, No. 6, 2010, pp. 133-137.
[27] D.Turgut, S.K.Das, R.Elmasri and B. Turgut, “Opti-mizing Clustering Algorithm in Mobile Ad Hoc
Net-works Using Genetic Algorithmic Approach,” In Pro-ceedings of the Global Telecommunications
Conference (GLOBECOM), Taibei, November 2002, pp. 62-66.](https://image.slidesharecdn.com/implementationofenergyefficientcoverageawareroutingprotocolforwirelesssensornetworkusinggeneticalgor-150212233519-conversion-gate02/85/Implementation-of-energy-efficient-coverage-aware-routing-protocol-for-wireless-sensor-network-using-genetic-algorithm-12-320.jpg)