Introduction to tcp ip linux networking
8 likes1,566 views
The document discusses network layering models and TCP/IP fundamentals. It describes: 1. Networking problems are divided into layers for easier understanding and standardization, with the two main models being OSI and TCP/IP. 2. The TCP/IP model has four or five layers - process, host-to-host transport, internet, network access, and sometimes physical. 3. Packets are encapsulated as they leave a machine and decapsulated on the receiving host, with each layer adding headers.
1 of 36



![OSI
Conceptual model composed of seven layers,
developed by the International Organization for
Standardization (ISO) in 1984.
Layer 7 – Application (servers and clients etc web browsers, httpd)
Layer 6 – Presentation (file formats e.g pdf, ASCII, jpeg etc)
Layer 5 – Session (conversation initialisation, termination, )
Layer 4 – Transport (inter host comm – error correction, QOS)
Layer 3 – Network (routing – path determination, IP[x] addresses etc)
Layer 2 – Data link (switching – media acces, MAC addresses etc)
Layer 1 – Physical (signalling – representation of binary digits)
Acronym: All People Seem To Need Data
Processing](https://image.slidesharecdn.com/introductiontotcpip-linuxnetworking-170304132420/85/Introduction-to-tcp-ip-linux-networking-4-320.jpg)































Ad
Recommended
The TCP/IP Stack in the Linux Kernel
The TCP/IP Stack in the Linux KernelDivye Kapoor The document discusses various data structures and functions related to network packet processing in the Linux kernel socket layer. It describes the sk_buff structure that is used to pass packets between layers. It also explains the net_device structure that represents a network interface in the kernel. When a packet is received, the interrupt handler will raise a soft IRQ for processing. The packet will then traverse various protocol layers like IP and TCP to be eventually delivered to a socket and read by a userspace application.
Cisco CCNA- NAT Configuration
Cisco CCNA- NAT ConfigurationHamed Moghaddam The document provides a detailed guide on Cisco CCNA Network Address Translation (NAT) configuration, explaining both dynamic and static NAT. It includes step-by-step instructions to configure a NAT with examples of commands and IP addresses, emphasizing the setup of access lists and defining inside and outside interfaces. Additional notes clarify when to use NAT pools and the importance of ensuring the ISP is aware of the network's public address.
Wireshark ppt
Wireshark pptbala150985 Wireshark is a GUI tool that can be used to analyze network traffic on many operating systems. It allows users to apply filters to network packets using parameters like IP addresses, ports, and protocols. The document provides examples of Wireshark filters and links to sample network capture files that can be used for practice analyzing network traffic using different filters.
Configuracion dns ipv6
Configuracion dns ipv6Yerlin Delgado Este documento proporciona 10 pasos para configurar el servicio DNS e IPv6 en un equipo servidor. Estos pasos incluyen configurar los adaptadores de red, instalar y configurar el servicio DNS bind9, crear y editar archivos de zona, y reiniciar el servicio DNS para actualizar los cambios.
How to configure dns server(2)
How to configure dns server(2)Amandeep Kaur The document provides instructions on how to configure a DNS server. It begins by explaining what a DNS server is and its purpose of translating domain names to IP addresses. It then discusses IP addresses and the differences between dynamic and static IP addresses. Finally, it provides the steps to install and configure a Microsoft DNS server using DNS Manager. These include adding the DNS component in Windows and using DNS Manager to configure the server.
CCNA v6.0 ITN - Chapter 01
CCNA v6.0 ITN - Chapter 01Irsandi Hasan The document provides an overview of chapter 1 from the CCNA Routing and Switching Introduction to Networks course. It discusses how networks are used in everyday life and how they have changed the way people interact, learn, work and play. It also describes the basic components of networks, including end devices, intermediary devices, network media, and topologies. Additionally, it differentiates between local area networks (LANs), which span a small geographic area, and wide area networks (WANs), which interconnect LANs over a wider geographical area.
DevConf 2014 Kernel Networking Walkthrough
DevConf 2014 Kernel Networking WalkthroughThomas Graf The document is a walkthrough of kernel networking presented by Thomas Graf, focusing on the flow of packets through the network stack and various processing mechanisms like receive side scaling and socket buffers. It covers topics including TCP processing, memory accounting, and flow control, explaining methods for packet transmission and reception in the system. The agenda includes Q&A and future topics, showcasing key networking concepts relevant to Linux networking services.
BITS: Introduction to linux, distributions and installation
BITS: Introduction to linux, distributions and installationBITS The document is an introduction to Linux, covering its origins, distributions, and installation processes. It explains the significance of Linux in bioinformatics and provides a guide on obtaining installation media for various distributions like Fedora and Ubuntu. The document also touches on dual-booting Linux with Windows and running Linux in a virtual machine.
JSON Web Tokens
JSON Web TokensIvan Rosolen - JSON Web Tokens (JWTs) are a compact and self-contained way for securely transmitting information between parties as JSON objects. JWTs can be signed using a secret or public/private key pair to provide verification of the token.
- JWTs contain encoded JSON objects comprising three parts - a header, claims, and signature. The header describes the token type and signing algorithm. Claims contain the user identity and other data. The signature ensures the token hasn't been altered.
- JWTs provide a number of advantages over traditional session cookies, including being more leightweight, easier to pass across domains, and not requiring server-side storage. They can also be used to implement stateless authentication for APIs.
The linux networking architecture
The linux networking architecturehugo lu The document discusses Linux networking architecture and covers several key topics in 3 paragraphs or less:
It first describes the basic structure and layers of the Linux networking stack including the network device interface, network layer protocols like IP, transport layer, and sockets. It then discusses how network packets are managed in Linux through the use of socket buffers and associated functions. The document also provides an overview of the data link layer and protocols like Ethernet, PPP, and how they are implemented in Linux.
Domain name system
Domain name systemfordcoppenz The document provides an overview of the Domain Name System (DNS). It explains that DNS translates human-friendly domain names to IP addresses, allowing computers to communicate over the internet. The summary describes DNS's evolution from its early use on ARPANET to support email to its current global role translating domain names to IP addresses for websites, emails, and other internet services and applications.
IP Addressing (Subnetting, VLSM, Supernetting)
IP Addressing (Subnetting, VLSM, Supernetting)cuetcse The document discusses various IP addressing concepts including IP addresses, subnet masks, CIDR notation, private and public IP addresses, subnetting using both fixed length and variable length subnet masks, and supernetting. IP addresses have a network portion and host portion that can be varied using subnet masks to create multiple logical subnets from one physical network. Subnetting and VLSM allow for more efficient use of IP address space, while supernetting reduces routing table sizes.
Networking in linux
Networking in linuxVarnnit Jain The document provides an overview of networking in Linux, explaining basic concepts such as network devices, interfaces, and essential configuration commands. It details how to manage network interfaces, check connectivity, configure IP addresses, and troubleshoot network issues using various command-line tools. Additionally, it includes a practical scenario for setting up networking between two systems with specific IP addresses.
Introduction to ns3
Introduction to ns3Shahid Beheshti University This document provides an overview of NS-3, an open-source discrete event network simulator. It describes what NS-3 is, how to install it, and some of its key components and functionality. NS-3 allows modeling of network elements like nodes, devices, channels, and protocols. It has a collection of C++ libraries rather than a single program. Topologies can be built by configuring nodes, applications, and network elements like channels and devices. The simulator can be used to analyze network performance through tracing and logging functions.
VirtualBox networking explained
VirtualBox networking explainedMaarten Smeets The document discusses various VirtualBox networking options, including internal network, NAT, NAT network, host-only, and bridged modes, detailing their configurations, benefits, and drawbacks. Each option has specific use cases, such as ease of use, internet access, guest isolation, and access between host and guest systems. Practical cases are provided to illustrate suitable networking solutions for different scenarios.
Introduction to ansible
Introduction to ansibleOmid Vahdaty Ansible is an automation platform that allows users to configure, deploy, and manage applications on servers. It combines multi-node software deployment, configuration management, and task execution. Ansible works by provisioning machines using SSH and executing commands via modules. Playbooks allow users to automate complex deployment workflows through YAML scripts. Roles in Ansible allow for reusable and modular components.
Basic command to configure mikrotik
Basic command to configure mikrotikTola LENG The document provides instructions for configuring a Mikrotik router, including setting up interfaces and network cards, assigning IP addresses, creating NAT and DHCP rules, configuring DNS and gateway settings, and setting up a basic hotspot with user authentication. It also describes how to change the ISP connection and switch between Radius and local authentication for the hotspot.
IP Addressing
IP AddressingKishore Kumar The document provides an overview of IP addressing, detailing both IPv4 and IPv6, their structure, and the different classes of IP addresses (A, B, C, D, E). It explains the concept of subnetting, subnet masks, and their usages within local area networks, as well as private address ranges for home and office use. Additionally, it discusses practical scenarios for implementing these concepts effectively.
QEMU - Binary Translation
QEMU - Binary Translation Jiann-Fuh Liaw This document provides an overview of QEMU, including its use of dynamic translation and Tiny Code Generator (TCG) to emulate target CPUs on the host system. It discusses how QEMU translates target instructions into a RISC-like intermediate representation (TCG ops), optimizes and converts them to host instructions. The document also mentions Linaro's work with QEMU and a QEMU monitor tool for debugging ARM systems emulated by QEMU.
Static NAT
Static NATNetProtocol Xpert Static NAT maps a private IP address to a public IP address in a 1:1 ratio, requiring a separate public IP for each private IP. It is configured by specifying the private to public IP mapping, marking the inside and outside interfaces, and can be verified with NAT translation commands.
Sockets
SocketsIndrasena Reddy Socket programming allows processes to communicate over a network. Key aspects include:
- Demultiplexing packets into processes using port numbers
- Converting between host and network byte order
- Sockets representing an endpoint for communication and identified by address/port pairs
- Functions for binding addresses, listening for connections, accepting connections, and sending/receiving data over established sockets.
Linux Networking Commands
Linux Networking Commandstmavroidis This document provides an overview of common Linux networking commands such as ifconfig, route, traceroute, nslookup, arp, dig, and netstat that are used to configure network interfaces, display routing tables, trace network routes, lookup domain names, manage address resolution, query DNS servers, and view network statistics. It also discusses how to use ifconfig to assign IP addresses to interfaces, route to view routing tables, arp to manage the address resolution cache, and dig for more powerful DNS lookups than nslookup.
IPv4 addressing and subnetting
IPv4 addressing and subnettingShashank Asthana This document provides an overview of IPv4 addressing and subnetting. It discusses hardware addressing using MAC addresses, logical addressing using network IDs and host IDs, and the Internet Protocol (IP). IP uses 32-bit addresses and provides logical addressing and routing. Subnet masks distinguish the network and host portions of an IP address. CIDR notation compactly represents subnet masks. Address classes and subnetting create networks and hosts. Private IP addresses are used internally while public addresses can route on the internet.
Fun with Network Interfaces
Fun with Network InterfacesKernel TLV The document provides an overview of the Linux network stack, including its components and programming interfaces. It elaborates on the structure and functionalities of the net_device abstraction, along with various logical network interfaces such as VLANs, virtual Ethernet pairs, and bonding. Additionally, it aims to strengthen foundational knowledge while easing future research in networking.
DHCP & DNS
DHCP & DNSNetProtocol Xpert DHCP is a client-server protocol that assigns network parameters like IP addresses to devices from a server's address pool. A DHCP client broadcasts a request and the DHCP server responds with an offered address via acknowledgement packets. DNS translates human-friendly hostnames to IP addresses by querying a DNS server's address records, allowing users to access resources by name instead of numeric address. Together, DHCP and DNS simplify network configuration and access.
Iptables Configuration
Iptables Configurationstom123 This document discusses the configuration and implementation of iptables on Linux. It provides instructions on installing iptables, starting and checking the status of iptables, and describes how packets are processed through the different iptables tables and chains. Key aspects covered include the three main tables - filter, nat, and mangle - and how each table contains built-in chains that rules can be applied to for packet filtering, network address translation, and modification of packet headers.
DNS - Domain Name System
DNS - Domain Name SystemPeter R. Egli The document is an in-depth overview of the Domain Name System (DNS), detailing its purpose as a distributed system that maps symbolic names to IP addresses. It covers DNS elements, hierarchy, operational mechanisms, and various terms associated with DNS, such as authoritative records and resource records. Additionally, it addresses dynamic DNS, international domain names, and the technical specifications of DNS packets and queries.
Network address translation
Network address translationKarppinen Ngoc Anh Network Address Translation (NAT) allows multiple devices on a private network to share a single public IP address to connect to the internet. It works by translating the private IP addresses and port numbers in data packets into public IP addresses and port numbers before being sent out to the internet, and vice versa for incoming packets. Dynamic NAT assigns public IP addresses and port numbers from a pool to private addresses and ports on demand. Overloading allows multiple connections from the same private IP by using different port numbers. Proxies provide additional benefits like caching but require explicit client support. NAT can improve security, administration and fault tolerance but causes issues for some network games without workarounds.
Linux commands and file structure
Linux commands and file structureSreenatha Reddy K R The document discusses Linux commands for file management, viewing and shell programming. It describes common commands like ls, cd, cp, mv, rm, mkdir which allow navigating and manipulating files and directories. It also covers commands for viewing file contents like cat, head, tail, grep. Commands for compression like tar, gzip, zip and decompression like gunzip, unzip are mentioned. The document also has a section on shell programming which explains how to write shell scripts using commands and variables. It provides examples of using pipes, redirections and command options.
Linux booting process - Linux System Administration
Linux booting process - Linux System AdministrationSreenatha Reddy K R The document discusses the Linux booting process. It begins with the BIOS loading the master boot record (MBR) from the hard disk. The MBR then loads the boot loader like GRUB or LILO. The boot loader loads the Linux kernel into memory and passes control to it. The kernel initializes hardware and loads drivers. It then launches the init process which starts essential system processes and moves the system to the default runlevel based on the /etc/inittab file.
More Related Content
What's hot (20)
JSON Web Tokens
JSON Web TokensIvan Rosolen - JSON Web Tokens (JWTs) are a compact and self-contained way for securely transmitting information between parties as JSON objects. JWTs can be signed using a secret or public/private key pair to provide verification of the token.
- JWTs contain encoded JSON objects comprising three parts - a header, claims, and signature. The header describes the token type and signing algorithm. Claims contain the user identity and other data. The signature ensures the token hasn't been altered.
- JWTs provide a number of advantages over traditional session cookies, including being more leightweight, easier to pass across domains, and not requiring server-side storage. They can also be used to implement stateless authentication for APIs.
The linux networking architecture
The linux networking architecturehugo lu The document discusses Linux networking architecture and covers several key topics in 3 paragraphs or less:
It first describes the basic structure and layers of the Linux networking stack including the network device interface, network layer protocols like IP, transport layer, and sockets. It then discusses how network packets are managed in Linux through the use of socket buffers and associated functions. The document also provides an overview of the data link layer and protocols like Ethernet, PPP, and how they are implemented in Linux.
Domain name system
Domain name systemfordcoppenz The document provides an overview of the Domain Name System (DNS). It explains that DNS translates human-friendly domain names to IP addresses, allowing computers to communicate over the internet. The summary describes DNS's evolution from its early use on ARPANET to support email to its current global role translating domain names to IP addresses for websites, emails, and other internet services and applications.
IP Addressing (Subnetting, VLSM, Supernetting)
IP Addressing (Subnetting, VLSM, Supernetting)cuetcse The document discusses various IP addressing concepts including IP addresses, subnet masks, CIDR notation, private and public IP addresses, subnetting using both fixed length and variable length subnet masks, and supernetting. IP addresses have a network portion and host portion that can be varied using subnet masks to create multiple logical subnets from one physical network. Subnetting and VLSM allow for more efficient use of IP address space, while supernetting reduces routing table sizes.
Networking in linux
Networking in linuxVarnnit Jain The document provides an overview of networking in Linux, explaining basic concepts such as network devices, interfaces, and essential configuration commands. It details how to manage network interfaces, check connectivity, configure IP addresses, and troubleshoot network issues using various command-line tools. Additionally, it includes a practical scenario for setting up networking between two systems with specific IP addresses.
Introduction to ns3
Introduction to ns3Shahid Beheshti University This document provides an overview of NS-3, an open-source discrete event network simulator. It describes what NS-3 is, how to install it, and some of its key components and functionality. NS-3 allows modeling of network elements like nodes, devices, channels, and protocols. It has a collection of C++ libraries rather than a single program. Topologies can be built by configuring nodes, applications, and network elements like channels and devices. The simulator can be used to analyze network performance through tracing and logging functions.
VirtualBox networking explained
VirtualBox networking explainedMaarten Smeets The document discusses various VirtualBox networking options, including internal network, NAT, NAT network, host-only, and bridged modes, detailing their configurations, benefits, and drawbacks. Each option has specific use cases, such as ease of use, internet access, guest isolation, and access between host and guest systems. Practical cases are provided to illustrate suitable networking solutions for different scenarios.
Introduction to ansible
Introduction to ansibleOmid Vahdaty Ansible is an automation platform that allows users to configure, deploy, and manage applications on servers. It combines multi-node software deployment, configuration management, and task execution. Ansible works by provisioning machines using SSH and executing commands via modules. Playbooks allow users to automate complex deployment workflows through YAML scripts. Roles in Ansible allow for reusable and modular components.
Basic command to configure mikrotik
Basic command to configure mikrotikTola LENG The document provides instructions for configuring a Mikrotik router, including setting up interfaces and network cards, assigning IP addresses, creating NAT and DHCP rules, configuring DNS and gateway settings, and setting up a basic hotspot with user authentication. It also describes how to change the ISP connection and switch between Radius and local authentication for the hotspot.
IP Addressing
IP AddressingKishore Kumar The document provides an overview of IP addressing, detailing both IPv4 and IPv6, their structure, and the different classes of IP addresses (A, B, C, D, E). It explains the concept of subnetting, subnet masks, and their usages within local area networks, as well as private address ranges for home and office use. Additionally, it discusses practical scenarios for implementing these concepts effectively.
QEMU - Binary Translation
QEMU - Binary Translation Jiann-Fuh Liaw This document provides an overview of QEMU, including its use of dynamic translation and Tiny Code Generator (TCG) to emulate target CPUs on the host system. It discusses how QEMU translates target instructions into a RISC-like intermediate representation (TCG ops), optimizes and converts them to host instructions. The document also mentions Linaro's work with QEMU and a QEMU monitor tool for debugging ARM systems emulated by QEMU.
Static NAT
Static NATNetProtocol Xpert Static NAT maps a private IP address to a public IP address in a 1:1 ratio, requiring a separate public IP for each private IP. It is configured by specifying the private to public IP mapping, marking the inside and outside interfaces, and can be verified with NAT translation commands.
Sockets
SocketsIndrasena Reddy Socket programming allows processes to communicate over a network. Key aspects include:
- Demultiplexing packets into processes using port numbers
- Converting between host and network byte order
- Sockets representing an endpoint for communication and identified by address/port pairs
- Functions for binding addresses, listening for connections, accepting connections, and sending/receiving data over established sockets.
Linux Networking Commands
Linux Networking Commandstmavroidis This document provides an overview of common Linux networking commands such as ifconfig, route, traceroute, nslookup, arp, dig, and netstat that are used to configure network interfaces, display routing tables, trace network routes, lookup domain names, manage address resolution, query DNS servers, and view network statistics. It also discusses how to use ifconfig to assign IP addresses to interfaces, route to view routing tables, arp to manage the address resolution cache, and dig for more powerful DNS lookups than nslookup.
IPv4 addressing and subnetting
IPv4 addressing and subnettingShashank Asthana This document provides an overview of IPv4 addressing and subnetting. It discusses hardware addressing using MAC addresses, logical addressing using network IDs and host IDs, and the Internet Protocol (IP). IP uses 32-bit addresses and provides logical addressing and routing. Subnet masks distinguish the network and host portions of an IP address. CIDR notation compactly represents subnet masks. Address classes and subnetting create networks and hosts. Private IP addresses are used internally while public addresses can route on the internet.
Fun with Network Interfaces
Fun with Network InterfacesKernel TLV The document provides an overview of the Linux network stack, including its components and programming interfaces. It elaborates on the structure and functionalities of the net_device abstraction, along with various logical network interfaces such as VLANs, virtual Ethernet pairs, and bonding. Additionally, it aims to strengthen foundational knowledge while easing future research in networking.
DHCP & DNS
DHCP & DNSNetProtocol Xpert DHCP is a client-server protocol that assigns network parameters like IP addresses to devices from a server's address pool. A DHCP client broadcasts a request and the DHCP server responds with an offered address via acknowledgement packets. DNS translates human-friendly hostnames to IP addresses by querying a DNS server's address records, allowing users to access resources by name instead of numeric address. Together, DHCP and DNS simplify network configuration and access.
Iptables Configuration
Iptables Configurationstom123 This document discusses the configuration and implementation of iptables on Linux. It provides instructions on installing iptables, starting and checking the status of iptables, and describes how packets are processed through the different iptables tables and chains. Key aspects covered include the three main tables - filter, nat, and mangle - and how each table contains built-in chains that rules can be applied to for packet filtering, network address translation, and modification of packet headers.
DNS - Domain Name System
DNS - Domain Name SystemPeter R. Egli The document is an in-depth overview of the Domain Name System (DNS), detailing its purpose as a distributed system that maps symbolic names to IP addresses. It covers DNS elements, hierarchy, operational mechanisms, and various terms associated with DNS, such as authoritative records and resource records. Additionally, it addresses dynamic DNS, international domain names, and the technical specifications of DNS packets and queries.
Network address translation
Network address translationKarppinen Ngoc Anh Network Address Translation (NAT) allows multiple devices on a private network to share a single public IP address to connect to the internet. It works by translating the private IP addresses and port numbers in data packets into public IP addresses and port numbers before being sent out to the internet, and vice versa for incoming packets. Dynamic NAT assigns public IP addresses and port numbers from a pool to private addresses and ports on demand. Overloading allows multiple connections from the same private IP by using different port numbers. Proxies provide additional benefits like caching but require explicit client support. NAT can improve security, administration and fault tolerance but causes issues for some network games without workarounds.
Viewers also liked (20)
Linux commands and file structure
Linux commands and file structureSreenatha Reddy K R The document discusses Linux commands for file management, viewing and shell programming. It describes common commands like ls, cd, cp, mv, rm, mkdir which allow navigating and manipulating files and directories. It also covers commands for viewing file contents like cat, head, tail, grep. Commands for compression like tar, gzip, zip and decompression like gunzip, unzip are mentioned. The document also has a section on shell programming which explains how to write shell scripts using commands and variables. It provides examples of using pipes, redirections and command options.
Linux booting process - Linux System Administration
Linux booting process - Linux System AdministrationSreenatha Reddy K R The document discusses the Linux booting process. It begins with the BIOS loading the master boot record (MBR) from the hard disk. The MBR then loads the boot loader like GRUB or LILO. The boot loader loads the Linux kernel into memory and passes control to it. The kernel initializes hardware and loads drivers. It then launches the init process which starts essential system processes and moves the system to the default runlevel based on the /etc/inittab file.
Hacking for Dummies 2
Hacking for Dummies 2Chandra Pr. Singh This document provides an introduction to hacking and the internet. It discusses topics like Linux, TCP/IP, and gaining unauthorized access to computers. The author acknowledges the legal issues with hacking but provides tips and resources anyway. They aim to introduce hacking basics and explain the anarchic nature of the internet in a mostly harmless way.
101 4.7 find system files and place files in the correct location
101 4.7 find system files and place files in the correct locationAcácio Oliveira This document discusses locating files on a Linux system. It describes the find, locate, which, and whereis commands and their syntax and options for finding files and their locations. The key utilities covered are find, which searches for files matching expressions; locate, which searches a database index for file locations; which, which finds the location of executables; and whereis, which finds the location of binaries, manuals, and sources of commands. It also discusses the Filesystem Hierarchy Standard for placement of files on Linux systems.
Session Hijacking
Session Hijackingn|u - The Open Security Community Session hijacking involves an attacker stealing a valid user session ID to gain access to a system and retrieve data. There are several types of session hijacking such as predictable session tokens, session sniffing, and man-in-the-middle attacks. To perform session hijacking, an attacker places themselves between the victim and target server, monitors packet flows, and predicts sequence numbers to take over the user's session and inject packets to the target server. Mitigations include using HTTPS, a VPN, limiting exposure to untrusted networks, and educating employees. Tools that can be used for session hijacking include Firesheep and other programs.
Presentation on rhce
Presentation on rhceG Raveena Nair This document outlines a seminar presentation on Linux system administration certification (RHCSA/RHCE). The presentation covers topics such as what Linux is, features of Red Hat Enterprise Linux 6.4, user and file system management, logical volume management, server configuration, shell scripting, and text user interfaces. It provides an introduction to the RHCSA/RHCE certification and its focus on competencies for senior Linux system administrators. An agenda with timing is included, as well as conclusions about the benefits of Linux being an open source, customizable, portable, and stable operating system.
Access control list acl - permissions in linux
Access control list acl - permissions in linuxSreenatha Reddy K R The document outlines key concepts related to Linux system administration, particularly focusing on user and group permissions, file ownership, and the Linux security model. It describes how programs run and the significance of file permissions, including the various modes for setting them with the chmod command. The document also highlights the differences in access rights, including the meanings of file permission indicators and the implications for directory visibility and file editing capabilities.
Palo alto networks
Palo alto networksJonathanMarinFlores5565 Este documento describe la plataforma de seguridad de Palo Alto Networks. Explica que los firewalls tradicionales solo ofrecen dos opciones: bloquear todo o permitir todo. Sin embargo, la plataforma de Palo Alto Networks inspecciona todo el tráfico de red, incluidas las aplicaciones, usuarios y contenido, y permite habilitar aplicaciones de forma segura mediante la clasificación y asignación de políticas selectivas. Esto permite a las empresas protegerse contra amenazas sin comprometer el acceso a aplicaciones necesarias.
Linux basics part 1
Linux basics part 1Lilesh Pathe The document provides a comprehensive overview of the Linux operating system, covering its origins, structure, basic commands, and components such as the shell, text editors, user and group management, permissions, GRUB, and networking. It outlines essential commands for file management, user account administration, and network configuration. Additionally, it explains the functionality of RPM for package management and highlights hard disk management commands.
Vi editor in linux
Vi editor in linuxBhumivaghasiya This document provides an overview of the vi text editor in Linux. It discusses what vi is, its history and key characteristics. It describes the different modes in vi - command mode, input mode, and last line mode. It then covers how to start vi, common commands for navigating and editing text like moving the cursor, deleting text, and copying/pasting. Finally, it explains how to exit vi by saving changes with ZZ or quit without saving changes using :q.
Linux System Administration Crash Course
Linux System Administration Crash CourseJason Cannon This document provides an overview of a Linux administration crash course that covers key system administration concepts. The course is intended for anyone interested in learning Linux administration, from beginners to experienced professionals. It covers topics such as the Linux boot process, system logging, disk management, user and group management, networking, processes and jobs, scheduling jobs with cron, and managing software. The document promotes enrolling in an in-depth Linux administration course for live instruction and assistance with shell scripting.
Data security in local network using distributed firewall ppt
Data security in local network using distributed firewall ppt Sabreen Irfana Distributed firewalls provide data security in LANs by enforcing security policies at network endpoints rather than a single centralized firewall. This overcomes issues with traditional firewalls like single points of failure, restricted topologies, and an assumption that inside users are trusted. A distributed firewall uses a central management system to define security policies which are then enforced by policy agents on endpoints using public key certificates for authentication. This allows filtering of both internal and external traffic according to the security policy.
Shell scripting
Shell scriptingsimha.dev.lin This document provides an overview of shell scripting in 3 paragraphs or less:
The document discusses Linux shell scripting, including that a shell is a user program that provides an environment for user interaction by reading commands from standard input and executing them. It mentions common shell types like BASH, CSH, and KSH, and that shell scripts allow storing sequences of commands in a file to execute them instead of entering each command individually. The document provides basic information on writing, executing, and using variables and input/output redirection in shell scripts.
Introduction to DNS
Introduction to DNSJonathan Oxer The document provides an extensive overview of the Domain Name System (DNS), describing its functions such as directory services, identity mechanisms, and mapping hostnames to IP addresses. It discusses the structure of DNS, including zones and record types, as well as security issues such as DNS cache poisoning and various attack vectors. Additionally, it covers the roles of registries, registrars, and the management of domain names under ICANN's oversight.
Intro to Linux Shell Scripting
Intro to Linux Shell Scriptingvceder This document is a presentation on introducing Linux shell scripting. It begins by stating that the talk is aimed at those who can open a terminal and type commands. It then outlines what will be covered, including basic shell commands, combining commands, creating simple scripts, and using cron for automation. The document provides examples of commands for files, disks, processes, and networks. It also demonstrates how to combine commands using pipes and redirection. Finally, it shows how to create simple scripts and discusses using cron for automation.
Unix Shell Scripting Basics
Unix Shell Scripting BasicsDr.Ravi The document provides an introduction to UNIX shell scripting basics. It discusses what a shell and shell script are, how to run commands and write simple shell scripts using bash. It covers basics like variables, conditionals, loops, pipes and redirection to process inputs, outputs and errors when running programs from shell scripts.
tybsc it sem 5 Linux administration notes of unit 1,2,3,4,5,6 version 3
tybsc it sem 5 Linux administration notes of unit 1,2,3,4,5,6 version 3WE-IT TUTORIALS The document is a comprehensive guide on Linux administration, covering various topics such as system configuration, TCP/IP networking, and internet services. It elaborates on Linux's architecture, components like kernel and shell, and includes practical instructions for tasks like configuring servers and managing mail services. Additionally, it discusses different Linux distributions and their features, tailored for diverse user needs.
Linux commands
Linux commandsBalakumaran Arunachalam Linux is an open-source operating system developed by Linus Torvalds in 1991. It has a reputation for being efficient and fast-performing. The document then lists and describes 50 common Linux commands, including their syntax and usage. Examples include commands for changing directories, copying files, displaying the date/time, searching files with grep, and more.
Shell programming
Shell programmingMoayad Moawiah The document provides information about shells in Linux operating systems. It defines what a kernel and shell are, explains why shells are used, describes different types of shells, and provides examples of shell scripting. The key points are:
- The kernel manages system resources and acts as an intermediary between hardware and software. A shell is a program that takes commands and runs them, providing an interface between the user and operating system.
- Shells are useful for automating tasks, combining commands to create new ones, and adding functionality to the operating system. Common shells include Bash, Bourne, C, Korn, and Tcsh.
- Shell scripts allow storing commands in files to automate tasks.
Ad
Similar to Introduction to tcp ip linux networking (20)
Intro tcp-ip
Intro tcp-ipZoulou Adams Networking is divided into layers for modularity and standardization. The OSI model has 7 layers, while TCP/IP typically uses a 4 layer model. Each layer encapsulates the packet from the previous layer, adding a header. Packets are called frames, datagrams or segments depending on the layer. IP addresses are 32-bit numbers that specify networks and hosts. Subnet masks define the network and host portions. Routers use route tables to determine the next hop for packets based on the destination address.
CCNA Exam by [email protected] - for CCNA test
CCNA Exam by [email protected] - for CCNA testepro2k71 The document provides an extensive overview of networking concepts, focusing on layered models like OSI and TCP/IP, encapsulation, and the roles of different network layers such as the application, transport, network, and data link layers. It details protocols, addressing, routing, subnetting, and the transition to IPv6, including address representation and autoconfiguration mechanisms. Additionally, it highlights the importance of reliable communication, error checking, and flow control, while explaining concepts such as unicast, multicast, private and public IP addresses.
Mod6
Mod6Alam Garcia The document discusses IP addressing concepts including:
1. IP addresses are represented in binary and decimal, and methods to convert between the two. IPv4 addresses are 32-bit numbers that are commonly shown in dotted decimal notation.
2. IP networks are divided into a network portion and host portion using subnet masks. Common subnet masks like /24, /16, and /8 define the traditional IP address classes. More flexible classless addressing allows any prefix length.
3. Key addressing concepts include private vs public IP addresses, network vs broadcast addresses, subnetting to create more networks from an existing range, and utilities like ping and traceroute.
Your app lives on the network - networking for web developers
Your app lives on the network - networking for web developersWim Godden The document outlines foundational concepts of networking, including the roles of TCP/IP, packet structures, IP addressing (both IPv4 and IPv6), and routing mechanisms. It emphasizes the importance of understanding how data is transmitted over networks, with practical considerations for developers and system engineers. Technical details include packet headers, subnetting, and brief overviews of protocols such as DNS, TCP, and UDP.
7-Lect_7 .pptxNetwork LayerNetwork Layer
7-Lect_7 .pptxNetwork LayerNetwork LayerZahouAmel1 The document discusses the fundamentals of computer networks, focusing on the network layer, addressing, subnetting, and routing. It explains classful IP addressing, including default subnet masks for different classes (A, B, C), and how to calculate subnet addresses and host ranges using binary methods. Additionally, it outlines static and dynamic routing, including examples of routing protocols and how routers manage routing tables and determine optimal paths based on hop counts.
7-Lect_7 .pptxNetwork Layer. Addressing Subnetting Mask (default and subnet) ...
7-Lect_7 .pptxNetwork Layer. Addressing Subnetting Mask (default and subnet) ...ZahouAmel1 The document covers the fundamentals of computer networks, focusing on the concepts of the network layer, classful IP addressing, subnetting, and routing. It explains network classes (A, B, C), default subnet masks, the process of subnetting, and the calculation of usable host addresses. Additionally, it outlines static and dynamic routing processes, including routing protocols and how to manage routing tables effectively.
Course 102: Lecture 20: Networking In Linux (Basic Concepts)
Course 102: Lecture 20: Networking In Linux (Basic Concepts) Ahmed El-Arabawy Linux networking concepts allow machines to connect and communicate over a network. This includes identifying interfaces, IP addresses, subnet masks, default gateways, DNS servers, and network protocols like ARP and NAT. Networking is essential for tasks like accessing the internet, copying files remotely, and debugging embedded systems that typically lack local interfaces. Core networking commands like ifconfig, route, arp, and resolv.conf are used to configure and view network settings and operations.
TCP/IP Basics
TCP/IP BasicsSMC Networks Europe The document discusses TCP/IP networking fundamentals including:
- The TCP/IP protocol suite model with layers for internet, transport, and applications.
- Key protocols like IP, TCP, UDP that operate at each layer.
- IP addressing and routing protocols like RIP and OSPF.
- Network applications that use TCP/IP like HTTP, FTP, SMTP, and DNS.
- Networking services like DHCP, NAT, and firewalls.
- Emerging technologies like IPv6 that expand addressing and add new features.
Ip Addressing Basics
Ip Addressing Basicstmavroidis The document discusses IP addressing basics including MAC addresses, IP addresses, private and public IP addresses, and subnetting. It provides examples of MAC addresses, ifconfig output showing MAC and IP addresses, private IP address ranges, and how to break up a Class C network into multiple subnets using subnet masks.
CCNA
CCNAAbhishek Parihari The document provides an overview of the CCNA certification and covers topics like internetworking, IP addressing, routing protocols, Cisco IOS, and more. It begins with an introduction to computer networks and protocols. Then it discusses the OSI reference model, IP addressing fundamentals, routing protocols like RIP, IGRP, EIGRP and OSPF, Cisco IOS configuration, and IP routing. The document serves as a study guide for CCNA exam topics at a high level.
tcpip.ppt
tcpip.pptGreenSignal This document provides an overview of how the TCP/IP protocol works by describing its core components:
- IP handles addressing, routing, and fragmentation of packets into smaller pieces if needed
- ICMP provides control and error messages between devices
- UDP and TCP provide transport layer services, with TCP adding reliability via flow control and error recovery
- Addressing uses IP addresses to identify interfaces, along with subnet masks to divide networks into smaller subnets
- ARP maps IP addresses to MAC addresses within a local network, and routing selects the next hop for packets between networks.
Networking basics
Networking basicsSridhar Baithi This document provides an overview of networking concepts including network components, layers of the OSI model, network structures, IP addressing, subnetting, routing, and TCP/IP protocols. Key points covered include the core, distribution, and access layers of a network hierarchy; functions of the physical, data link, network, and transport layers; MAC addressing; IP addressing classes and subnetting; TCP and port numbers; and routing protocols.
gofortution
gofortutiongofortution The document provides an overview of IP addressing and routing, explaining concepts such as internet topology, addressing types, routing protocols, and special address conventions. It differentiates between classful and classless addressing, elaborates on subnetting, and identifies different types of routers and protocols used in routing information exchange. The document also discusses the significance of routing tables, metrics, and automatic vs. manual configuration in network routing.
Free CCNA workbook by networkers home pdf
Free CCNA workbook by networkers home pdfNetworkershome The document explains IP addressing rules, including the uniqueness of IP addresses and the significance of subnet masks, along with various classes of IP addresses (A, B, C, D, and E). It outlines subnetting procedures and provides exercises for subnetting calculations, followed by details on the OSI model layers, their functions, and associated protocols. Additionally, it covers router configuration, command interfaces, and user instructions for managing router settings effectively.
TCP/IP basics
TCP/IP basicsSecurityTube.Net This document provides an overview of TCP/IP concepts and networking fundamentals, including:
- The TCP/IP protocol stack consists of 4 layers: application, transport, internet, and network. The transport layer uses TCP and UDP to encapsulate data into segments.
- TCP uses a 3-way handshake to establish a connection and its header includes fields like source/destination ports and sequence numbers. Common TCP ports like 80 and 443 are used for web traffic.
- IP addresses are made of a network and host portion and are classified into classes A, B, and C. Subnet masks determine the network vs host portions.
- UDP is a simpler connectionless protocol. ICMP and protocols like ping
Ch02 TCP/IP Concepts Review
Ch02 TCP/IP Concepts Reviewphanleson The document provides an overview of TCP/IP concepts including:
1. It describes the four layers of the TCP/IP protocol stack - application, transport, internet, and link layer.
2. It explains TCP and UDP protocols operate at the transport layer, and how TCP establishes reliable connections using a three-way handshake.
3. It discusses IP addressing and how networks, subnets, and hosts are identified using IP addresses and subnet masks.
CCNA 200-120 Exam Quick Notes
CCNA 200-120 Exam Quick NotesEng. Emad Al-Atoum The document provides an overview of key networking concepts, including the OSI model, TCP/IP protocols, and Cisco IOS commands. It details the seven layers of the OSI model, explains various networking protocols and subnetting techniques, and covers basic Cisco router configuration and operational modes. Additionally, it discusses the roles of different types of memory in Cisco routers and outlines how to manage network configurations.
Ccna pres
Ccna presDanish Nauman This document provides information about networking concepts for the CCNA exam, including transmission media, network interface cards, protocols, addresses, hubs, switches, routers, and the OSI model. It defines common networking cable types and standards like Ethernet and their associated bandwidths. It also covers IP addressing schemes including public/private IP ranges, subnetting of IP classes A, B and C, and default subnet masks. Network communication methods like unicast, broadcast and multicast are defined.
Linux Systems Prograramming: Unix Domain, Internet Domain (TCP, UDP) Socket P...
Linux Systems Prograramming: Unix Domain, Internet Domain (TCP, UDP) Socket P...RashidFaridChishti The document provides an overview of socket programming in Linux, explaining the fundamental concepts including socket types, communication domains, and the client/server model. It covers network addressing specifics for both MAC and IP addresses, as well as details about IPv4 addressing and subnetting. Additionally, it presents examples of socket programming through client and server code, illustrating the functionality of TCP and UDP protocols in network communications.
Ccna1v3 mod10
Ccna1v3 mod10igede tirtanata This document provides an overview of routing fundamentals and subnetting in CCNA version 3.0. It discusses routed and routing protocols, how IP acts as a routed protocol, routing tables, routing algorithms and metrics, and the mechanics of subnetting including establishing subnet masks and calculating subnetworks through ANDing. The objectives are to understand routed protocols, IP routing protocols, and the mechanics of subnetting.
Ad
More from Sreenatha Reddy K R (7)
Data science applications and usecases
Data science applications and usecasesSreenatha Reddy K R The document provides an overview of data science applications and use cases. It defines data science as using computer science, statistics, machine learning and other techniques to analyze data and create data products to help businesses make better decisions. It discusses big data challenges, the differences between data science and software engineering, and key areas of data science competence including data analytics, engineering, domain expertise and data management. Finally, it outlines several common data science applications and use cases such as recommender systems, credit scoring, dynamic pricing, customer churn analysis and fraud detection with examples of how each works and real world cases.
Linux security firewall and SELinux
Linux security firewall and SELinuxSreenatha Reddy K R The document discusses Linux system administration and security, focusing on firewalls and SELinux. It explains how to activate and configure the firewall and SELinux through the GUI, emphasizing the importance of restricting permissions to minimize security risks. SELinux can operate in three modes: enforcing, permissive, and disabled, each serving different security needs.
Mail server setup
Mail server setupSreenatha Reddy K R The document outlines the setup process for a Linux mail server, specifying the use of protocols like SMTP for mail transfer and POP/IMAP for retrieving emails. It includes configuration instructions for Sendmail and Dovecot, along with specific commands to edit configuration files and restart services. The author, Sreenatha Reddy, provides links to their social media for further contact.
Linux System Administration - Web Server and squid setup
Linux System Administration - Web Server and squid setupSreenatha Reddy K R This document provides information on setting up an Apache web server and Squid proxy server on Linux. It discusses installing and configuring Apache, including the configuration file location and directives. It also covers installing Squid from source or binaries, editing the Squid configuration file to set the cache size and location, enable authentication, and restrict access. Virtual hosting with Apache and example Squid configuration options are also summarized.
Linux System Administration - NFS Server
Linux System Administration - NFS ServerSreenatha Reddy K R This document discusses how to set up NFS and Samba servers. It explains that NFS allows sharing directories between UNIX systems using daemons like nfs, nfslock, and portmap. It describes configuring the /etc/exports file to define exported filesystems and configuring clients via /etc/fstab. For Samba, it discusses using smbd to share files and printers from UNIX to Windows via the smb.conf configuration file. Authentication can be done using local Unix usernames and passwords stored in /etc/samba/smbpasswd.
Linux System Administration - DNS
Linux System Administration - DNSSreenatha Reddy K R This document provides an overview of DNS (Domain Name System) and its role in translating names to IP addresses. It details the setup and configuration of a DNS server, including the use of zone files, named daemon, and access control lists for managing domain queries and transfers. Additionally, it covers advanced features such as dynamic DNS updates and load balancing through round robin techniques.
DHCP and NIS
DHCP and NISSreenatha Reddy K R The document covers Linux system administration focusing on Dynamic Host Configuration Protocol (DHCP) and Network Information Service (NIS). It details DHCP server and client configuration processes, including specific files and commands needed for setup. Additionally, it outlines NIS setup for centralized authentication and troubleshooting techniques for verifying server connections and data availability.
Recently uploaded (20)
Humans vs AI Call Agents - Qcall.ai's Special Report
Humans vs AI Call Agents - Qcall.ai's Special ReportUdit Goenka Humans vs Agentic AI Cost Comparison: Cut 85% Support Costs
TL;DR: Agentic AI crushes human costs in L1/L2 support with 85% savings, 300% efficiency gains, and 90%+ success rates.
Your CFO just asked: "Why spend $2.3M annually on L1 support when competitors automated 80% for under $200K?" The humans vs agentic AI cost debate isn't theoretical - it's happening now.
Real Cost Breakdown:
- India L1/L2 Agent: ₹6,64,379 ($8,000) annually (full cost)
- US L1/L2 Agent: $70,000 annually (loaded cost)
- Qcall.ai Agentic AI: ₹6/min ($0.07/min) = 85% savings
Game-Changing Results:
- 47 human agents → 8 agents + AI system
- Operating costs: $2.8M → $420K (85% reduction)
- Customer satisfaction: 78% → 91%
- First call resolution: 72% → 94%
- Languages: 2-3 → 15+ fluently
Why Agentic AI Wins:
- Human Limitations: 8hrs/day, 1-2 languages, 30-45% attrition, mood-dependent, 6-12 weeks training
- Qcall.ai Advantages: 24/7 availability, 97% humanized voice, <60 second response, intelligent qualification, seamless handoff
Industry Impact:
- E-commerce: 82% cost reduction
- Healthcare: 90% appointment automation
- SaaS: 23% satisfaction improvement
- Financial: 95% inquiry automation
Implementation:
- Setup: 2-5 days vs 6-12 weeks hiring
- ROI: Break-even in 3 months
- Scaling: Instant global expansion
Competitive Gap:
- Early Adopters: 85% cost advantage, superior metrics, faster expansion
Late Adopters: Higher costs, limited scalability, compounding disadvantage
Similar automation patterns emerge across industries.
Marketing teams use autoposting.ai for social media automation - same human-AI collaboration model driving L1/L2 transformation.
"We reduced support costs by 78% while improving satisfaction by 31%. ROI was immediate and keeps compounding." - COO, Global SaaS Company
Getting Started:
Calculate current L1/L2 costs
Assess repetitive tasks
Request Qcall.ai demo
Plan 20% pilot
Bottom Line: Companies avoiding this shift hemorrhage millions while competitors scale globally with fraction of costs. The question isn't whether agentic AI will replace routine tasks - it's whether you'll implement before competitors gain insurmountable advantage.
Ready to transform operations? This reveals complete cost analysis, implementation strategy, and competitive advantages.
IDM Crack with Internet Download Manager 6.42 Build 41 [Latest 2025]
IDM Crack with Internet Download Manager 6.42 Build 41 [Latest 2025]pcprocore 👉Copy link &paste Google new tab > https://pcprocore.com/ 👈✅
IDM Crack with Internet Download Manager (IDM) is a tool to increase download speeds, resume, and schedule downloads.Comprehensive error recovery and resume capability will restart broken or interrupted downloads due to lost connections, network problems, computer shutdowns, or unexpected power outages. The simple graphic user interface makes IDM user-friendly and easy to use. Internet Download Manager has a smart download logic accelerator with intelligent dynamic file segmentation and safe multipart downloading technology to accelerate your downloads. Unlike other download managers and accelerators, Internet Download Manager segments downloaded files dynamically during the download process and reuses available connections without additional connect and login stages to achieve the best acceleration performance for IDM users.
System Requirements of IDM:
Operating System: Windows XP, NT, 2000, Vista, 7, 8, 8.1, 10 & 11 (32bit and 64bit)
Memory (RAM): 512 MB of RAM required
Hard Disk Space: 25 MB of free space required for full installation
Processor: Intel Pentium 4 Dual Core GHz or higher. Ensure your system meets these requirements for the IDM Crack to function properly.
How to Install and Crack:
Temporarily disable the antivirus until the IDM Crack process
Install “idman642build41.exe”
Extract “IDM 6.42.41 Patch.rar” (Password is: 123)
Install “IDM 6.42.41 Patch.exe”
Done!!! Enjoy!!!
Threat Modeling a Batch Job Framework - Teri Radichel - AWS re:Inforce 2025
Threat Modeling a Batch Job Framework - Teri Radichel - AWS re:Inforce 20252nd Sight Lab This presentation is similar to another presentation I gave earlier in the year at the AWS Community Security Day, except that I had less time to present and incorporated some AI slides into the presentation. In this presentation I explain what batch jobs are, how to use them, and that AI Agents are essentially batch jobs. All the same security controls that apply to batch jobs also apply to AI agents. In addition, we have more concerns with AI agents because AI is based on a statistical model. That means that depending on where and how AI is used we lose some of the reliability that we would get from a traditional batch job. That needs to be taken into consideration when selecting how and when to use AI Agents as batch jobs and whether we should use AI to trigger an Agent. As I mention on one side - I don't want you to predict what my bank statement should look like. I want it to be right! By looking at various data breaches we can determine how those attacks worked and whether the system we are building is susceptible to a similar attack or not.
CodeCleaner: Mitigating Data Contamination for LLM Benchmarking
CodeCleaner: Mitigating Data Contamination for LLM Benchmarkingarabelatso This is the pdf-version slides for the presentation "CodeCleaner: Mitigating Data Contamination for LLM Benchmarking" in Internetware 2025.
CodeCleaner: Mitigating Data Contamination for LLM Benchmarking
CodeCleaner: Mitigating Data Contamination for LLM Benchmarkingarabelatso The pdf version of "CodeCleaner: Mitigating Data Contamination for LLM Benchmarking" presented in Internetware 2025.
Heat Treatment Process Automation in India
Heat Treatment Process Automation in IndiaReckers Mechatronics Automate your heat treatment processes for superior precision, consistency, and cost savings. Explore solutions for furnaces, quench systems. Heat treatment is a critical manufacturing process that alters the microstructure and properties of materials, typically metals, to achieve desired characteristics such as hardness, strength, ductility, and wear resistance.
Digital Transformation: Automating the Placement of Medical Interns
Digital Transformation: Automating the Placement of Medical InternsSafe Software Discover how the Health Service Executive (HSE) in Ireland has leveraged FME to implement an automated solution for its “Order of Merit” process, which assigns medical interns to their preferred placements based on applications and academic performance. This presentation will showcase how FME validates applicant data, including placement preferences and academic results, ensuring both accuracy and eligibility. It will also explore how FME automates the matching process, efficiently assigning placements to interns and distributing offer letters. Beyond this, FME actively monitors responses and dynamically reallocates placements in line with the order of merit when offers are accepted or declined. The solution also features a self-service portal (FME Flow Gallery App), enabling administrators to manage the entire process seamlessly, make adjustments, generate reports, and maintain audit logs. Additionally, the system upholds strict data security and governance, utilising FME to encrypt data both at rest and in transit.
AI for PV: Development and Governance for a Regulated Industry
AI for PV: Development and Governance for a Regulated IndustryBiologit AI for pharmacovigilance: Development and Governance for a Regulated Industry.
A survey of regulatory guidance for the use of artificial intelligence in pharmacovigilance and best practices for its safe implementation with the Biologit literature platform as case study.
How Automation in Claims Handling Streamlined Operations
How Automation in Claims Handling Streamlined OperationsInsurance Tech Services Claims processing automation reduces manual work, cuts errors, and speeds up resolutions. Using AI, RPA, and OCR, it enables faster data handling and smoother workflows—boosting efficiency and customer satisfaction. Visit https://www.damcogroup.com/insurance/claims-processing-automation for more details!
From Code to Commerce, a Backend Java Developer's Galactic Journey into Ecomm...
From Code to Commerce, a Backend Java Developer's Galactic Journey into Ecomm...Jamie Coleman In a galaxy not so far away, a Java developer advocate embarks on an epic quest into the vast universe of e-commerce. Armed with backend languages and the wisdom of microservice architectures, set out with us to learn the ways of the Force. Navigate the asteroid fields of available tools and platforms; tackle the challenge of integrating location-based technologies into open-source projects; placate the Sith Lords by enabling great customer experiences.
Follow me on this journey from humble Java coder to digital marketplace expert. Through tales of triumph and tribulation, gain valuable insights into conquering the e-commerce frontier - such as the different open-source solutions available - and learn how technology can bring balance to the business Force, large or small. May the code be with you.
Automated Testing and Safety Analysis of Deep Neural Networks
Automated Testing and Safety Analysis of Deep Neural NetworksLionel Briand Keynote address at Internetware 2025, co-located with FSE 2025
Folding Cheat Sheet # 9 - List Unfolding 𝑢𝑛𝑓𝑜𝑙𝑑 as the Computational Dual of ...
Folding Cheat Sheet # 9 - List Unfolding 𝑢𝑛𝑓𝑜𝑙𝑑 as the Computational Dual of ...Philip Schwarz For newer version see https://fpilluminated.org/deck/264
In this deck we look at the following:
* How unfolding lists is the computational dual of folding lists
* Different variants of the function for unfolding lists
* How they relate to the iterate function
On-Device AI: Is It Time to Go All-In, or Do We Still Need the Cloud?
On-Device AI: Is It Time to Go All-In, or Do We Still Need the Cloud?Hassan Abid As mobile hardware becomes more powerful, the promise of running advanced AI directly on-device is closer than ever. With Google’s latest on-device model Gemini Nano, accessible through the new ML Kit GenAI APIs and AI Edge SDK, alongside the open-source Gemma-3n models, developers can now integrate lightweight, multimodal intelligence that works even without an internet connection. But does this mean we no longer need cloud-based AI? This session explores the practical trade-offs between on-device and cloud AI for mobile apps.
Building Geospatial Data Warehouse for GIS by GIS with FME
Building Geospatial Data Warehouse for GIS by GIS with FMESafe Software Data warehouses are often considered the backbone of data-driven decision-making. However, traditional implementations can struggle to meet the iterative and dynamic demands of GIS operations, particularly for Iterative Cross-Division Data Integration (ICDI) processes. At WVDOT, we faced this challenge head-on by designing a Geospatial Data Warehouse (GDW) tailored to the needs of GIS. In this talk, we’ll share how WVDOT developed a metadata-driven, SESSI-based (Simplicity, Expandability, Spatiotemporality, Scalability, Inclusivity) GDW that transforms how we manage and leverage spatial data. Key highlights include: - Simplifying data management with a lean schema structure. - Supporting ad hoc source data variations using JSON for flexibility. - Scaling for performance with RDBMS partitioning and materialized views. - Empowering users with FME Flow-based self-service metadata tools.We’ll showcase real-world use cases, such as pavement condition data and LRS-based reporting, and discuss how this approach is elevating GIS as an integrative framework across divisions. Attendees will walk away with actionable insights on designing GIS-centric data systems that combine the best of GIS and data warehouse methodologies.
Key Challenges in Troubleshooting Customer On-Premise Applications
Key Challenges in Troubleshooting Customer On-Premise ApplicationsTier1 app When applications are deployed in customer-managed environments, resolving performance issues becomes a hidden battle. Limited access to logs, delayed responses, and vague problem descriptions make root cause analysis incredibly challenging.
In this presentation, we walk through:
The six most common hurdles faced in on-prem troubleshooting
A practical 360° artifact collection strategy using the open-source yc-360 script
Real-world case studies covering transaction timeouts, CPU spikes, and intermittent HTTP 502 errors
Benefits of structured data capture in reducing investigation time and improving communication with customers
✅ Whether you're supporting enterprise clients or building tools for distributed environments, this deck offers a practical roadmap to make on-prem issue resolution faster and less frustrating.
IObit Driver Booster Pro 12 Crack Latest Version Download
IObit Driver Booster Pro 12 Crack Latest Version Downloadpcprocore 👉𝗡𝗼𝘁𝗲:𝗖𝗼𝗽𝘆 𝗹𝗶𝗻𝗸 & 𝗽𝗮𝘀𝘁𝗲 𝗶𝗻𝘁𝗼 𝗚𝗼𝗼𝗴𝗹𝗲 𝗻𝗲𝘄 𝘁𝗮𝗯🔴▶ https://pcprocore.com/ ◀✅
IObit Driver Booster Pro is the solution. It automatically downloads and updates drivers with just one click, avoiding hardware failures, system instability, and security vulnerabilities.
NEW-IDM Crack with Internet Download Manager 6.42 Build 27 VERSION
NEW-IDM Crack with Internet Download Manager 6.42 Build 27 VERSIONgrete1122g 🌍📱👉COPY & PASTE LINK >> https://click4pc.com/after-verification-click-go-to-download-page/
IIDM is a powerful and safe file Downloader, it grabs the original Download link version 6.41 build 7 latest of a file, sends powerful ...
Sysinfo OST to PST Converter Infographic
Sysinfo OST to PST Converter InfographicSysInfo Tools The SysInfo OST to PST Converter is the most secure software to perform the OST to PST conversion. It converts OST files into various formats, including MBOX, EML, EMLX, HTML, and CSV, with 100% accuracy. Along with that, it imports OST files into different email clients like Office 365 and G Suite.
visit: https://www.sysinfotools.com/ost-to-pst-converter.php
Advance Doctor Appointment Booking App With Online Payment
Advance Doctor Appointment Booking App With Online PaymentAxisTechnolabs https://www.slideshare.net/slideshow/advance-doctor-appointment-booking-app-with-online-payment/280654375
Introduction to tcp ip linux networking
- 1. LINUX SYSTEM ADMINISTRATION TCP/IP Network Essentials
- 2. Layers Complex problems can be solved using the common divide and conquer principle. In this case the internals of the Internet are divided into separate layers. • Makes it easier to understand • Developments in one layer need not require changes in another layer • Easy formation (and quick testing of conformation to) standards Two main models of layers are used: • OSI (Open Systems Interconnection) • TCP/IP
- 3. OSI Model
- 4. OSI Conceptual model composed of seven layers, developed by the International Organization for Standardization (ISO) in 1984. Layer 7 – Application (servers and clients etc web browsers, httpd) Layer 6 – Presentation (file formats e.g pdf, ASCII, jpeg etc) Layer 5 – Session (conversation initialisation, termination, ) Layer 4 – Transport (inter host comm – error correction, QOS) Layer 3 – Network (routing – path determination, IP[x] addresses etc) Layer 2 – Data link (switching – media acces, MAC addresses etc) Layer 1 – Physical (signalling – representation of binary digits) Acronym: All People Seem To Need Data Processing
- 5. TCP/IP Generally, TCP/IP (Transmission Control Protocol/Internet Protocol) is described using three to five functional layers. We have chosen the common DoD reference model, which is also known as the Internet reference model. • Process/Application Layer consists of applications and processes that use the network. • Host-to-host transport layer provides end-to-end data delivery services. • Internetwork layer defines the datagram and handles the routing of data. • Network access layer consists of routines for accessing physical networks.
- 6. TCP/IP model – the “hourglass” Browser MUA HTTP SMTP TCP UDP DNS RTSP Video Player ICMP PING IP 802.11 WiFi Ethernet PPP Copper Fiber PigeonsAir :)
- 7. TCP/IP model – IPv4 and IPv6 Browser MUA HTTP SMTP TCP UDP DNS RTSP Video Player ICMP PING 802.11 WiFi Ethernet PPP Copper Fiber PigeonsAir :) IPv4 IPv6
- 10. Encapsulation & Decapsulation Lower layers add headers (and sometimes trailers) to upper layers packets Application Transport Network Data Link Data DataHeader Transport PacketHeader DataHeaderHeader Network Packet DataHeaderHeader Header Header Trailer Trailer
- 11. Frame, Datagram, Segment, Packet Different names for packets at different layers • Ethernet (link layer) frame • IP (network layer) datagram • TCP (transport layer) segment Terminology is not strictly followed • we often just use the term “packet” at any layer
- 12. Summary Networking is a problem approached in layers. • OSI Layers • TCP/IP Layers Each layer adds headers to the packet of the previous layer as the data leaves the machine (encapsulation) and the reverse occurs on the receiving host (decapsulation)
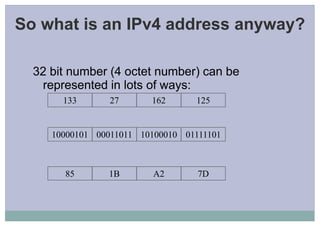
- 13. So what is an IPv4 address anyway? 32 bit number (4 octet number) can be represented in lots of ways: 133 27 162 125 10000101 00011011 10100010 01111101 85 1B A2 7D
- 14. Calculating dec, hex, bin ipcalc is your friend - try: $ ipcalc 41.93.45.1 linux command line is your friend - try: $ echo 'ibase=10;obase=16;27' | bc 1B $ echo 'ibase=10;obase=2;27' | bc 11011 $ echo 'ibase=16;obase=A;1B' | bc 27
- 15. More to the structure Hierarchical Division in IP Address: Network Part (Prefix) describes which network Host Part (Host Address) describes which host on that network Boundary can be anywhere used to be a multiple of 8 (/8, /16/, /24), but not usual today Network Hos t 205 . 154 . 8 1 11001101 10011010 00001000 00000001 Mask
- 16. Network Masks Network Masks help define which bits are used to describe the Network Part and which for hosts Different Representations: • decimal dot notation: 255.255.224.0 (128+64+32 in byte 3) • binary: 11111111 11111111 111 00000 00000000 • hexadecimal: 0xFFFFE000 • number of network bits: /19 (8 + 8 + 3) Binary AND of 32 bit IP address with 32 bit netmask yields network part of address
- 17. Sample Netmasks 137.158.128.0/17 (netmask 255.255.128.0) 1000 1001 1001 1110 1 000 0000 0000 0000 1111 1111 1111 1111 1 000 0000 0000 0000 1100 0110 1000 0110 0000 0000 0000 0000 1111 1111 1111 1111 0000 0000 0000 0000 1100 1101 0010 0101 1100 0001 10 00 0000 1111 1111 1111 1111 1111 1111 11 00 0000 198.134.0.0/16 (netmask 255.255.0.0) 205.37.193.128/26 (netmask 255.255.255.192)
- 18. Allocating IP addresses The subnet mask is used to define size of a network E.g a subnet mask of 255.255.255.0 or /24 implies 32-24=8 host bits 2^8 minus 2 = 254 possible hosts Similarly a subnet mask of 255.255.255.224 or /27 implies 32-27=5 host bits 2^5 minus 2 = 30 possible hosts
- 19. Special IP Addresses All 0’s in host part: Represents Network e.g. 193.0.0.0/24 e.g. 138.37.128.0/17 e.g. 192.168.2.128/25 (WHY?) All 1’s in host part: Broadcast (all hosts on net) e.g. 137.156.255.255 (137.156.0.0/16) e.g. 134.132.100.255 (134.132.100.0/24) e.g. 192.168.2.127/25 (192.168.2.0/25) (WHY?) 127.0.0.0/8: Loopback address (127.0.0.1) 0.0.0.0: Various special purposes (DHCP, etc.)
- 20. Networks – super- and subnetting /24 /25 /27 .... By adding one bit to the netmask, we subdivide the network into two smaller networks. This is subnetting. i.e.: If one has a /26 network (32 – 26 = 6 => 2^6 => 64 addresses), that network can be subdivided into two subnets, using a /27 netmask, where the state of the last bit will determine which network we are addressing (32 – 27 = 5 => 2^5 => 32 addresses). This can be done recursively (/27 => 2 x /28 or 4 x /29, etc...). Example: 192.168.10.0/25 (.0 - .127) can be subnetted into 192.168.10.0 / 26 and 192.168.10.64 / 26 /27 /27 /27 /27 /27 /27 /27 /26 /26 /26 /26 /25
- 21. Networks – super- and subnetting /24 /25 /25 Inversely, if two networks can be “joined” together under the same netmask, which encompasses both networks, then we are supernetting. Example: Networks 10.254.4.0/24 and 10.254.5.0/24 can be “joined” together into one network expressed: 10.254.4.0/23. Note: for this to be possible, the networks must be contiguous, i.e. it is not possible to supernet 10.254.5.0/24 and 10.254.6.0/24 /26 /26 /26 /26
- 22. Numbering Rules Private IP address ranges (RFC 1918) • 10/8 (10.0.0.0 – 10.255.255.255) • 192.168/16 (192.168.0.0 – 192.168.255.255) • 172.16/12 (172.16.0.0 – 172.31.255.255) • Public Address space available from AfriNIC • Choose a small block from whatever range you have, and subnet your networks (to avoid problems with broadcasts, and implement segmentation policies – DMZ, internal, etc...)
- 23. Network related settings Files /etc/network/interfaces /etc/hosts /etc/resolv.conf Commands # ifconfig eth0 10.10.0.X/24 # route add default gw 10.10.0.254 # hostname pcX.ws.nsrc.org
- 24. Network related settings Files /etc/network/interfaces – excerpt: auto eth0 iface eth0 inet dhcp auto eth1 iface eth1 inet static address 41.93.45.101 gateway 41.93.45.1 netmask 255.255.255.0 /etc/resolv.conf - example: domain mydomain.org search mydomain.org nameserver 41.93.45.3
- 25. Network related settings Commands Modern Linux distributions are in the process of deprecating ifconfig and route – one new command does it all: #ip Try #ip addr show #ip route show #ip addr add 10.10.10.10 eth0 #ip route add default .... For details: #man ip
- 26. Routing Every host on the internet needs a way to get packets to other hosts outside its local network. This requires special hosts called routers that can move packets between networks. Packets may pass through many routers before they reach their destinations.
- 27. The route table All hosts (including routers) have a route table that specifies which networks it is connected to, and how to forward packets to a gateway router that can talk to other networks. Linux routing table from “netstat –rn46” Kernel IP routing table Destination Gateway Genmask Flags MSS Window irtt Iface 0.0.0.0 128.223.157.1 0.0.0.0 UG 0 0 0 eth0 128.223.157.0 0.0.0.0 255.255.255.128 U 0 0 0 eth0 Kernel IPv6 routing table Destination Next Hop Flag Met Ref Use If 2001:468:d01:103::/64 :: UAe 256 0 0 eth0 fe80::/64 :: U 256 0 0 eth0 ::/0 fe80::2d0:1ff:fe95:e000 UGDAe 1024 0 0 eth0 ::/0 :: !n -1 1 7 lo ::1/128 :: Un 0 1 1125 lo 2001:468:d01:103:3d8c:b867:f16d:efed/128 :: Un 0 1 0 lo 2001:468:d01:103:a800:ff:fe9c:4089/128 :: Un 0 1 0 lo fe80::a800:ff:fe9c:4089/128 :: Un 0 1 0 lo ff00::/8 :: U 256 0 0 eth0 ::/0 :: !n -1 1 7 lo
- 28. What do route table entries mean? Destination Gateway Genmask Flags MSS Window irtt Iface 0.0.0.0 128.223.157.1 0.0.0.0 UG 0 0 0 eth0 128.223.157.0 0.0.0.0 255.255.255.128* U 0 0 0 eth0 • The destination is a network address. • The gateway is an IP address of a router that can forward packets (or 0.0.0.0, if the packet doesn't need to be forwarded). • Flags indicate various attributes for each route: - U Up: The route is active. - H Host: The route destination is a single host. - G Gateway: Send anything for this destination on to this remote system, which will figure out from there where to send it. - D Dynamic: This route was dynamically created by something like gated or an ICMP redirect message. - M Modified: This route is set if the table entry was modified by an ICMP redirect message. - ! Reject: The route is a reject route and datagrams will be dropped. • MSS is the Maximum Segment Size. Largest datagram kernel will construct for transmission via this route. • Window is maximum data host will accept from a remote host. • irtt initial round trip time. • Iface the network inferface this route will use *What size network is 255.255.255.128?
- 29. How the route table is used A packet that needs to be sent has a destination IP address. For each entry in the route table (starting with the first): 1. Compute the logical AND of the destination IP and the genmask entry. 2. Compare that with the destination entry. 3. If those match, send the packet out the interface, and we're done. 4. If not, move on to the next entry in the table.
- 30. Reaching the local network Suppose we want to send a packet to 128.223.143.42 using this route table. Destination Gateway Genmask Flags Interface 128.223.142.0 0.0.0.0 255.255.254.0 U eth0 0.0.0.0 128.223.142.1 0.0.0.0 UG eth0 • In the first entry 128.223.143.42 AND 255.255.254.0 = 128.223.142.0 • This matches the destination of the first routing table entry, so send the packet out interface eth0. • That first entry is called a network route. Do you notice anything different about this routing table?
- 31. Reaching other networks Suppose we want to send a packet to 72.14.213.99 using this route table. Destination Gateway Genmask Flags Interface 128.223.142.0 0.0.0.0 255.255.254.0 U eth0 0.0.0.0 128.223.142.1 0.0.0.0 UG eth0 1. 72.14.213.99 AND 255.255.254.0 = 72.14.212.0 2. This does not match the first entry, so move on to the next entry. 3. 72.14.213.99 AND 0.0.0.0 = 0.0.0.0 4. This does match the second entry, so forward the packet to 128.223.142.1 via bge0.
- 32. The default route Note that this route table entry: Destination Gateway Genmask Flags Interface 0.0.0.0 128.223.142.1 0.0.0.0 UG eth0 matches every possible destination IP address. This is called the default route. The gateway has to be a router capable of forwarding traffic.
- 33. More complex routing Consider this route table: Destination Gateway Genmask Flags Interface 192.168.0.0 0.0.0.0 255.255.255.0 U eth0 192.168.1.0 0.0.0.0 255.255.255.0 U eth1 192.168.2.0 0.0.0.0 255.255.254.0 U eth2 192.168.4.0 0.0.0.0 255.255.252.0 U eth3 0.0.0.0 192.168.1.1 0.0.0.0 UG eth0 This is what a router's routing table might look like. Note that there are multiple interfaces for multiple local networks, and a gateway that can reach other networks.
- 34. Forwarding packets Any UNIX-like (and other) operating system can function as a gateway: In Ubuntu /etc/sysctl.conf set: # Uncomment the next line to enable # packet forwarding for IPv4 #net/ipv4/ip_forward=1 # Uncomment the next line to enable # packet forwarding for IPv6 #net/ipv6/ip_forward=1
- 35. Forwarding packets Important Without forwarding enabled, the box will not forward packets from one interface to another: it is simply a host with multiple interfaces.
