Java Database Connectivity
Download as ppt, pdf1 like4,036 views
The document discusses Java Database Connectivity (JDBC) API which defines how Java programs can communicate with databases. It describes key JDBC concepts like drivers, packages, and products. It also covers JDBC design considerations like different types of drivers and client-server models. Basic steps to use JDBC include loading drivers, establishing connections, executing statements, and closing connections.
1 of 35
Downloaded 440 times


































Ad
Recommended
Oracle SQL Basics



Oracle SQL BasicsDhananjay Goel This document provides an overview and introduction to Oracle SQL basics. It covers topics such as installing Oracle software like the database, Java SDK, and SQL Developer tool. It then discusses database concepts like what a database and table are. It also covers database fundamentals including SQL queries, functions, joins, constraints, views and other database objects. The document provides examples and explanations of SQL statements and database components.
Servlets



ServletsAkshay Ballarpure This document provides information on Java servlets including: what servlets are and their advantages; the servlet architecture and lifecycle including initialization, processing requests via doGet and doPost methods, and destruction; how to deploy servlets in an application server; and how servlets handle form data submission. Servlets act as a middle layer between web requests and applications/databases, and allow dynamically generating web pages.
Javascript



Javascriptmussawir20 JavaScript is a client-side scripting language that can be inserted into HTML pages to make them interactive. It allows dynamic validation of forms, changing HTML element properties like visibility, and reacting to user events like clicks or form submissions. The Document Object Model (DOM) represents an HTML or XML document as a tree structure, allowing JavaScript to programmatically access and modify the content, structure, and styling of the document. Common built-in JavaScript objects include String, Date, Array, Math, and Boolean, which provide properties and methods for manipulating text, dates, lists of values, numbers, and true/false values.
javaScript.ppt



javaScript.pptsentayehu This document provides an overview of JavaScript and the DOM (Document Object Model) for a web programming course. It introduces JavaScript as a scripting language used to add interactivity to HTML pages. It describes what JavaScript can do, such as dynamically updating text and reacting to events. It also covers JavaScript syntax, variables, operators, functions, and objects. A significant portion of the document is devoted to explaining the DOM and how it allows JavaScript to access and modify HTML elements and structure programmatically.
Jsp ppt



Jsp pptVikas Jagtap This document provides an overview of Java Server Pages (JSP) technology. Some key points:
- JSP allows separation of work between web designers and developers by allowing HTML/CSS design and Java code to be placed in the same file.
- A JSP page is compiled into a servlet, so it can take advantage of servlet features like platform independence and database-driven applications.
- JSP pages use tags like <jsp:include> and <jsp:useBean> to include content and access JavaBeans. Scriptlets, expressions, declarations, and directives are also used.
- Implicit objects like request, response, out, and session are automatically available in JSP pages
Spring Framework - Core



Spring Framework - CoreDzmitry Naskou Introduction to the Spring Framework:
Generar description
IoC container
Dependency Injection
Beans scope and lifecycle
Autowiring
XML and annotation based configuration
Additional features
Introduction to SQL



Introduction to SQLAmin Choroomi An introduction to SQL standard language for beginners and non-technical information people. Mostly covers SELECT statement using standard clauses, Joins, Sub-Queries and ...
Jdbc ppt



Jdbc pptsandeep54552 This document discusses Java Database Connectivity (JDBC) and the steps to connect to a database using JDBC. It provides an overview of JDBC architecture and its main components. It then outlines the key steps to connect to a database which include: 1) driver registration where the appropriate JDBC driver class is loaded, 2) defining the connection URL, 3) establishing a connection, 4) creating SQL statements, 5) executing queries and processing result sets, and 6) closing the connection. Examples are provided for connecting to MySQL and Derby databases using JDBC.
JDBC



JDBCPeople Strategists The document discusses Java Database Connectivity (JDBC) and how it allows Java programs to connect to databases. It describes the four types of JDBC drivers, the core JDBC interfaces like Driver, Connection, and Statement, and how to use JDBC to perform CRUD operations. The key interfaces allow establishing a database connection and executing SQL statements to retrieve and manipulate data.
Javascript basics



Javascript basicsshreesenthil This document provides an overview of JavaScript basics including variables, data types, operators, conditional statements, loops, functions, arrays, and error handling. It explains JavaScript syntax, how to include JavaScript code in HTML pages, and commonly used statements like if/else, switch case, while and for loops. It also covers JavaScript functions, returning values from functions, and printing pages. The document describes JavaScript strings and array objects, and their associated methods. Finally, it discusses different types of errors in JavaScript like syntax errors, runtime errors, and logical errors.
SQL Complete Tutorial. All Topics Covered



SQL Complete Tutorial. All Topics CoveredDanish Mehraj You can read SQL completely here . This file covers all SQL topics. Read and rate my work! Thanks
01) SQL Overview
02) RDBMS Concepts
03) Data Constraints
04) RDBMS Databases
05) Datatypes
06) Operators
07) Expressions
08) Creating Database
09) DDL
10) DML
11) DCL
12) Clauses
12) Joins
13) Synonyms
14) Index
15) Sequences
16) Clone Tables
17) Temporary Tables
18) Injections
Read and rate my work. Thanks
ASP.NET Page Life Cycle



ASP.NET Page Life CycleAbhishek Sur The document discusses the ASP.NET page lifecycle, which begins when a client requests a page from the server. It goes through initialization, loading, validation, event handling, and rendering steps. Key parts of the lifecycle include initializing controls and themes, loading view state and postback data, validating controls, firing server-side events, and rendering the output. Master pages and user controls follow the same lifecycle but are initialized differently and have their events called at different times in the process. The full lifecycle ensures the correct processing and output of the requested page.
Spring Boot



Spring BootHongSeong Jeon Spring Boot is a framework for creating stand-alone, production-grade Spring based applications that can be "just run". It aims to provide a radically faster and widely accessible starting experience for developing Spring applications. Spring Boot applications can be started using java -jar or traditional WAR deployments and require very little Spring configuration. The document then discusses system requirements, development environment, creating a simple Hello World application, using Spring Boot Admin to monitor applications, configuring databases, Spring Data JPA, REST controllers, caching with EhCache, building web applications with Thymeleaf, and project structure.
Spring Framework 



Spring Framework tola99 The document discusses Spring Boot, a framework from the Spring Team that aims to ease the bootstrapping and development of new Spring applications. Spring Boot allows applications to start quickly with very little Spring configuration. It provides some sensible defaults to help developers get started quickly on new projects.
Hibernate in Action



Hibernate in ActionAkshay Ballarpure This document provides an overview of Hibernate, an object-relational mapping tool for Java. It begins with a list of topics covered and then defines what Hibernate and JDBC are. It describes the Hibernate architecture including configuration, sessions, and mapping. It also discusses annotations, HQL, caching and batch processing. The document provides details on configuring Hibernate with different databases as well as mapping files and object-relational mappings. It explains the use of annotations, HQL, criteria queries, and native SQL with Hibernate.
Abstract class in java



Abstract class in javaLovely Professional University An abstract class is a class that is declared abstract —it may or may not include abstract methods. Abstract classes cannot be instantiated, but they can be subclassed. When an abstract class is subclassed, the subclass usually provides implementations for all of the abstract methods in its parent class.
Asp.net state management



Asp.net state managementpriya Nithya The document discusses different state management techniques in ASP.NET. It describes client-side techniques like hidden fields, view state, cookies, query strings, and control state. It also describes server-side techniques like session state and application state. Session state stores and retrieves data for each user session while application state stores data accessible to all users. Examples are provided for hidden fields, view state, cookies, query strings, session state, and application state.
MySQL Performance Schema in MySQL 8.0



MySQL Performance Schema in MySQL 8.0Mayank Prasad An overview of MySQL Performance Schema in 8.0
Few use cases to utilize Performance Schema.
A glimpse of new features in MySQL 8.0 with examples
SQL Queries



SQL QueriesNilt1234 This document provides an introduction to SQL and database systems. It begins with example tables to demonstrate SQL concepts. It then covers the objectives of SQL, including allowing users to create database structures, manipulate data, and perform queries. Various SQL concepts are introduced such as data types, comparison operators, logical operators, and arithmetic operators. The document also discusses SQL statements for schema and catalog definitions, data definition, data manipulation, and other operators. Example SQL queries are provided to illustrate concepts around selecting columns, rows, sorting, aggregation, grouping, and more.
Cookies and sessions



Cookies and sessionsLena Petsenchuk This document provides an overview of cookies and sessions. It defines cookies as small text files stored on a user's computer that contain information about a website visit. Sessions are a combination of a server-side cookie containing a unique session token and client-side cookie. The document discusses setting, retrieving, and deleting cookies using JavaScript, as well as the advantages of storing session data on the server rather than in client-side cookies.
C# Exceptions Handling 



C# Exceptions Handling sharqiyem The document discusses exceptions handling in .NET. It defines exceptions as objects that deliver a powerful mechanism for centralized handling of errors and unusual events. It describes how exceptions can be handled using try-catch blocks, and how finally blocks ensure code execution regardless of exceptions. It also covers the Exception class hierarchy, throwing exceptions with the throw keyword, and best practices like ordering catch blocks and avoiding exceptions for normal flow control.
Javascript essentials



Javascript essentialsBedis ElAchèche Things you should know about Javascript ES5. A programming language that enables you to create dynamically updating content, control multimedia, animate images, and pretty much everything else
Javascript



JavascriptRajavel Dhandabani The document discusses JavaScript, including that it is a lightweight scripting language embedded directly into HTML pages and executed without compilation. It describes common uses like client-side validation, reacting to HTML events, and dynamically updating content. Examples are provided of displaying the date, validating form fields, and using cookies. The document also covers JavaScript objects, events, functions, and manipulating the document object and CSS styles dynamically with JavaScript.
Constructor in java



Constructor in javaHitesh Kumar Constructor is a special member method which will be called automatically when you create an object of any class.
The main purpose of using constructor is to initialize an object.
http://www.tutorial4us.com/java/java-constructor
Introduction to Javascript



Introduction to JavascriptAmit Tyagi Video links: Part 1 : http://www.youtube.com/watch?v=lWSV4JLLJ8E Part2 : http://www.youtube.com/watch?v=-MvSBqPlMdY
HTML5: features with examples



HTML5: features with examplesAlfredo Torre This presentation is an introduction to the new features of
HTML5. The main elements of this document are:
* Brief history of HTML5
*The improvements
* Browser support
* Semantic elements
* Content Editable on pages
* Video Tag
* Canvas tag
* Local storage
* Geolocation API
* Offline applications
* Microdata
* Use cases
JDBC – Java Database Connectivity



JDBC – Java Database ConnectivityInformation Technology The document discusses Java Database Connectivity (JDBC) which allows Java applications to connect to databases. It describes the JDBC architecture including drivers, loading drivers, connecting to databases, executing queries and updates using Statement and PreparedStatement objects, processing result sets, and handling exceptions. It also covers transactions, result set metadata, and cleaning up resources.
MYSQL - PHP Database Connectivity



MYSQL - PHP Database ConnectivityV.V.Vanniaperumal College for Women This document discusses MySQL databases and how to interact with them using PHP. It begins by introducing MySQL as the world's most popular open source database and describes some basic database server concepts. It then provides code examples for how to connect to a MySQL database from PHP, select a database, perform queries to read, insert, update, and delete records, and more. The document is intended as a tutorial for learning the basic functions and syntax for accessing and manipulating data in a MySQL database with PHP.
JDBC Java Database Connectivity



JDBC Java Database ConnectivityRanjan Kumar There are 4 types of JDBC drivers. Database connections can be obtained using the DriverManager or a DataSource. Statements are used to execute SQL queries and updates. PreparedStatements are useful for executing the same statement multiple times with different parameter values. Joins allow querying data from multiple tables.
JDBC: java DataBase connectivity



JDBC: java DataBase connectivityTanmoy Barman how to make connection to database using jdbc, step by step connection, types of driver available, jdbc data source.
More Related Content
What's hot (20)
JDBC



JDBCPeople Strategists The document discusses Java Database Connectivity (JDBC) and how it allows Java programs to connect to databases. It describes the four types of JDBC drivers, the core JDBC interfaces like Driver, Connection, and Statement, and how to use JDBC to perform CRUD operations. The key interfaces allow establishing a database connection and executing SQL statements to retrieve and manipulate data.
Javascript basics



Javascript basicsshreesenthil This document provides an overview of JavaScript basics including variables, data types, operators, conditional statements, loops, functions, arrays, and error handling. It explains JavaScript syntax, how to include JavaScript code in HTML pages, and commonly used statements like if/else, switch case, while and for loops. It also covers JavaScript functions, returning values from functions, and printing pages. The document describes JavaScript strings and array objects, and their associated methods. Finally, it discusses different types of errors in JavaScript like syntax errors, runtime errors, and logical errors.
SQL Complete Tutorial. All Topics Covered



SQL Complete Tutorial. All Topics CoveredDanish Mehraj You can read SQL completely here . This file covers all SQL topics. Read and rate my work! Thanks
01) SQL Overview
02) RDBMS Concepts
03) Data Constraints
04) RDBMS Databases
05) Datatypes
06) Operators
07) Expressions
08) Creating Database
09) DDL
10) DML
11) DCL
12) Clauses
12) Joins
13) Synonyms
14) Index
15) Sequences
16) Clone Tables
17) Temporary Tables
18) Injections
Read and rate my work. Thanks
ASP.NET Page Life Cycle



ASP.NET Page Life CycleAbhishek Sur The document discusses the ASP.NET page lifecycle, which begins when a client requests a page from the server. It goes through initialization, loading, validation, event handling, and rendering steps. Key parts of the lifecycle include initializing controls and themes, loading view state and postback data, validating controls, firing server-side events, and rendering the output. Master pages and user controls follow the same lifecycle but are initialized differently and have their events called at different times in the process. The full lifecycle ensures the correct processing and output of the requested page.
Spring Boot



Spring BootHongSeong Jeon Spring Boot is a framework for creating stand-alone, production-grade Spring based applications that can be "just run". It aims to provide a radically faster and widely accessible starting experience for developing Spring applications. Spring Boot applications can be started using java -jar or traditional WAR deployments and require very little Spring configuration. The document then discusses system requirements, development environment, creating a simple Hello World application, using Spring Boot Admin to monitor applications, configuring databases, Spring Data JPA, REST controllers, caching with EhCache, building web applications with Thymeleaf, and project structure.
Spring Framework 



Spring Framework tola99 The document discusses Spring Boot, a framework from the Spring Team that aims to ease the bootstrapping and development of new Spring applications. Spring Boot allows applications to start quickly with very little Spring configuration. It provides some sensible defaults to help developers get started quickly on new projects.
Hibernate in Action



Hibernate in ActionAkshay Ballarpure This document provides an overview of Hibernate, an object-relational mapping tool for Java. It begins with a list of topics covered and then defines what Hibernate and JDBC are. It describes the Hibernate architecture including configuration, sessions, and mapping. It also discusses annotations, HQL, caching and batch processing. The document provides details on configuring Hibernate with different databases as well as mapping files and object-relational mappings. It explains the use of annotations, HQL, criteria queries, and native SQL with Hibernate.
Abstract class in java



Abstract class in javaLovely Professional University An abstract class is a class that is declared abstract —it may or may not include abstract methods. Abstract classes cannot be instantiated, but they can be subclassed. When an abstract class is subclassed, the subclass usually provides implementations for all of the abstract methods in its parent class.
Asp.net state management



Asp.net state managementpriya Nithya The document discusses different state management techniques in ASP.NET. It describes client-side techniques like hidden fields, view state, cookies, query strings, and control state. It also describes server-side techniques like session state and application state. Session state stores and retrieves data for each user session while application state stores data accessible to all users. Examples are provided for hidden fields, view state, cookies, query strings, session state, and application state.
MySQL Performance Schema in MySQL 8.0



MySQL Performance Schema in MySQL 8.0Mayank Prasad An overview of MySQL Performance Schema in 8.0
Few use cases to utilize Performance Schema.
A glimpse of new features in MySQL 8.0 with examples
SQL Queries



SQL QueriesNilt1234 This document provides an introduction to SQL and database systems. It begins with example tables to demonstrate SQL concepts. It then covers the objectives of SQL, including allowing users to create database structures, manipulate data, and perform queries. Various SQL concepts are introduced such as data types, comparison operators, logical operators, and arithmetic operators. The document also discusses SQL statements for schema and catalog definitions, data definition, data manipulation, and other operators. Example SQL queries are provided to illustrate concepts around selecting columns, rows, sorting, aggregation, grouping, and more.
Cookies and sessions



Cookies and sessionsLena Petsenchuk This document provides an overview of cookies and sessions. It defines cookies as small text files stored on a user's computer that contain information about a website visit. Sessions are a combination of a server-side cookie containing a unique session token and client-side cookie. The document discusses setting, retrieving, and deleting cookies using JavaScript, as well as the advantages of storing session data on the server rather than in client-side cookies.
C# Exceptions Handling 



C# Exceptions Handling sharqiyem The document discusses exceptions handling in .NET. It defines exceptions as objects that deliver a powerful mechanism for centralized handling of errors and unusual events. It describes how exceptions can be handled using try-catch blocks, and how finally blocks ensure code execution regardless of exceptions. It also covers the Exception class hierarchy, throwing exceptions with the throw keyword, and best practices like ordering catch blocks and avoiding exceptions for normal flow control.
Javascript essentials



Javascript essentialsBedis ElAchèche Things you should know about Javascript ES5. A programming language that enables you to create dynamically updating content, control multimedia, animate images, and pretty much everything else
Javascript



JavascriptRajavel Dhandabani The document discusses JavaScript, including that it is a lightweight scripting language embedded directly into HTML pages and executed without compilation. It describes common uses like client-side validation, reacting to HTML events, and dynamically updating content. Examples are provided of displaying the date, validating form fields, and using cookies. The document also covers JavaScript objects, events, functions, and manipulating the document object and CSS styles dynamically with JavaScript.
Constructor in java



Constructor in javaHitesh Kumar Constructor is a special member method which will be called automatically when you create an object of any class.
The main purpose of using constructor is to initialize an object.
http://www.tutorial4us.com/java/java-constructor
Introduction to Javascript



Introduction to JavascriptAmit Tyagi Video links: Part 1 : http://www.youtube.com/watch?v=lWSV4JLLJ8E Part2 : http://www.youtube.com/watch?v=-MvSBqPlMdY
HTML5: features with examples



HTML5: features with examplesAlfredo Torre This presentation is an introduction to the new features of
HTML5. The main elements of this document are:
* Brief history of HTML5
*The improvements
* Browser support
* Semantic elements
* Content Editable on pages
* Video Tag
* Canvas tag
* Local storage
* Geolocation API
* Offline applications
* Microdata
* Use cases
JDBC – Java Database Connectivity



JDBC – Java Database ConnectivityInformation Technology The document discusses Java Database Connectivity (JDBC) which allows Java applications to connect to databases. It describes the JDBC architecture including drivers, loading drivers, connecting to databases, executing queries and updates using Statement and PreparedStatement objects, processing result sets, and handling exceptions. It also covers transactions, result set metadata, and cleaning up resources.
MYSQL - PHP Database Connectivity



MYSQL - PHP Database ConnectivityV.V.Vanniaperumal College for Women This document discusses MySQL databases and how to interact with them using PHP. It begins by introducing MySQL as the world's most popular open source database and describes some basic database server concepts. It then provides code examples for how to connect to a MySQL database from PHP, select a database, perform queries to read, insert, update, and delete records, and more. The document is intended as a tutorial for learning the basic functions and syntax for accessing and manipulating data in a MySQL database with PHP.
Viewers also liked (20)
JDBC Java Database Connectivity



JDBC Java Database ConnectivityRanjan Kumar There are 4 types of JDBC drivers. Database connections can be obtained using the DriverManager or a DataSource. Statements are used to execute SQL queries and updates. PreparedStatements are useful for executing the same statement multiple times with different parameter values. Joins allow querying data from multiple tables.
JDBC: java DataBase connectivity



JDBC: java DataBase connectivityTanmoy Barman how to make connection to database using jdbc, step by step connection, types of driver available, jdbc data source.
How to Backdoor Diffie-Hellman



How to Backdoor Diffie-HellmanDavid Wong Lately, several backdoors in cryptographic constructions, protocols and implementations have been surfacing in the wild: Dual-EC in RSA's B-Safe product, a modified Dual-EC in Juniper's operating system ScreenOS and a non-prime modulus in the open-source tool socat. Many papers have already discussed the fragility of cryptographic constructions not using nothing-up-my-sleeve numbers, as well as how such numbers can be safely picked. However, the question of how to introduce a backdoor in an already secure, safe and easy to audit implementation has so far rarely been researched (in the public). We present two ways of building a Nobody-But-Us (NOBUS) Diffie-Hellman backdoor: a composite modulus with a hidden subgroup (CMHS) and a composite modulus with a smooth order (CMSO). We then explain how we were able to subtly implement and exploit it in a local copy of an open source library using the TLS protocol.
BackDoors Seminar



BackDoors SeminarChaitali Patel This document discusses backdoors and how they can bypass normal authentication to gain access to systems. It defines different types of backdoors like hard-wired backdoors and Rakshasa backdoors, which are difficult to detect. Rakshasa backdoors can compromise BIOS and infect over 100 motherboards. The document also covers vulnerabilities like buffer overflows that can introduce backdoors. It lists the main motivations for backdoor attacks as hardware cloning and information leakage. Finally, it provides recommendations for preventing backdoors, such as installing security updates, scanning for backdoors, and updating anti-spyware software definitions regularly.
Jdbc ppt



Jdbc pptVikas Jagtap Java applications cannot directly communicate with a database to submit data and retrieve the results of queries.
This is because a database can interpret only SQL statements and not Java language statements.
For this reason, you need a mechanism to translate Java statements into SQL statements.
The JDBC architecture provides the mechanism for this kind of translation.
The JDBC architecture can be classified into two layers :
JDBC application layer.
JDBC driver layer.
JDBC application layer : Signifies a Java application that uses the JDBC API to interact with the JDBC drivers. A JDBC driver is software that a Java application uses to access a database. The JDBC driver manager of JDBC API connects the Java application to the driver.
JDBC driver layer : Acts as an interface between a Java applications and a database. This layer contains a driver , such as a SQL server driver or an Oracle driver , which enables connectivity to a database.
A driver sends the request of a Java application to the database. After processing the request, the database sends the response back to the driver. The driver translates and sends the response to the JDBC API. The JDBC API forwards it to the Java application.
Trojans and backdoors



Trojans and backdoorsGaurav Dalvi This document discusses Trojans, backdoors, and other malware. It begins by explaining the origin of the term "Trojan" from the story of the Trojan horse in Greek mythology. It then defines Trojans and different types like destructive, denial of service, and remote access Trojans. The document also covers how systems can become infected, techniques for detecting and hiding malware like Trojans and backdoors, and discusses the historical Back Orifice 2000 backdoor as a case study. It concludes with recommendations for protecting against malware.
Jdbc architecture and driver types ppt



Jdbc architecture and driver types pptkamal kotecha JDBC provides a standard interface for connecting to and working with databases in Java applications. There are four main types of JDBC drivers: Type 1 drivers use ODBC to connect to databases but are only compatible with Windows. Type 2 drivers use native database client libraries but require the libraries to be installed. Type 3 drivers use a middleware layer to support multiple database types without native libraries. Type 4 drivers connect directly to databases using a pure Java implementation, providing cross-platform compatibility without additional layers.
Jdbc Ppt



Jdbc PptCentre for Budget and Governance Accountability (CBGA) This document summarizes the history and concepts of database connectivity prior to and with the introduction of JDBC and ODBC. It discusses how database connectivity was previously vendor-specific and difficult, and how JDBC and ODBC standardized connectivity through open APIs. It then covers the key aspects of JDBC including its definition, tasks, support for different architectures, and types of JDBC drivers.
Penetración con una Backdoor



Penetración con una BackdoorNEGOCIOS PROPIOS El documento describe cómo realizar un ataque a través de una backdoor usando Kali Linux y una máquina virtual de Windows XP. Primero se instala Kali Linux y se obtiene la dirección IP. Luego se inicia Metasploit y se crea un archivo ejecutable crack.exe que actuará como backdoor. Este archivo se descarga en la máquina XP objetivo a través de una conexión inalámbrica. Una vez ejecutado, permite tomar capturas de pantalla de la máquina objetivo y apagarla a distancia.
Backdoor



Backdoorphanleson The document discusses Trojans and backdoors. It defines a Trojan as a hidden program that runs on an infected computer and a backdoor as a program that allows hackers to connect without normal authentication. It describes how they are used to gain remote access or disable protections. The document outlines Trojan types and infection mechanisms like wrapper programs and autorun files. It provides examples of hacking tools and recommendations for detection and prevention like using antivirus software and educating users.
Finding the back door to people’s hearts



Finding the back door to people’s heartsThird Column Ministries Guest Brooke Butler with CRU at UC Berkeley
Ravi Zacharias said, “We have to find the back door to peoples’ hearts because the front door is heavily guarded.” Arguing on the basis of facts, reason and rationality can often lead to mere debate and sharp exchanges of opinions rather than any significant discussion and dialogue. Using cultural “tools” such as films, art, stories and music, we can more readily access the deeper thoughts and feelings of the people who we are trying to reach with the Gospel. Two interesting outreaches we have developed are; a Renaissance dinner that employs the food, story and art of Rembrandt; and Story of the Soul that employs a combination of short presentations and discussion in small groups.
Expert System MYCIN



Expert System MYCINRached Krim MYCIN was an early expert system developed in the 1970s and 1980s to diagnose bacterial infections and recommend antibiotics. It used a production rule-based approach with a static knowledge base of rules and a dynamic knowledge base to represent patient-specific information. MYCIN could explain its reasoning and allow knowledge engineers to update its rules through an interactive dialogue interface. The system demonstrated competence comparable to human experts in bacterial infection diagnosis and treatment selection.
JDBC Basics (In 20 Minutes Flat)



JDBC Basics (In 20 Minutes Flat)Craig Dickson The document discusses JDBC (Java Database Connectivity) basics including connecting to a database, executing SQL statements to create, update, query, and delete data. It covers establishing a connection using the DriverManager, executing SQL using Statement objects, and includes examples for creating a table, inserting rows, updating rows, selecting rows, and deleting rows. The document is intended as a 20 minute introduction to JDBC fundamentals.
Trojan virus & backdoors



Trojan virus & backdoorsShrey Vyas This document discusses trojans and backdoors. It defines a trojan as a malicious program that misrepresents itself as useful to install itself on a victim's computer. Trojans are used for destructive purposes like crashing systems or stealing data, or for using the computer's resources. Examples of trojans provided include Netbus and Back Orifice. Backdoors are methods of bypassing authentication to gain unauthorized access. They work by installing hidden server software that listens for connections from client software controlled by attackers. Known backdoors discussed include Back Orifice and a possible NSA backdoor in a cryptographic standard.
SOAR!!!



SOAR!!!roopakdesai The document provides tips for success as an executive. It recommends deeply understanding your areas of responsibility and the company, developing knowledge of your industry and trends, being authentic and leveraging your strengths as a leader. Additionally, it suggests finding a work-life balance, caring about the company and associates, and building a team. The overarching message is to stand out as an outstanding, approachable and respectful executive in order to feel successful.
Olms ppt



Olms pptsaritabhateja The document discusses an online library management system that was proposed to address drawbacks of the current manual system. The current system is run by a librarian and small staff during limited hours, with all record keeping done by hand. This makes maintenance difficult and does not make efficient use of resources. The proposed online system would allow library members to login to borrow, return, and search for books anytime. It would also automate all transaction recording to make maintenance easier. Entities, relationships, and data flows were modeled to design the new system, which was outlined as having advantages like 24/7 access and easier book tracking for staff.
.NET Code Examples



.NET Code ExamplesGaryB47 The document outlines the requirements for 3 phases of a library management system project. Phase 1 involves developing a Windows desktop application for basic functionality. Phase 2 replaces the data access and entity layers with SQL stored procedures and custom entities. Phase 3 creates a web application to replace the Windows frontend. Code samples are provided for the Windows application and web forms.
.NET Portfolio



.NET PortfolioCRD Alternatives, Inc. Portfolio includes 2 projects completed at SetFocus. First is .NET Framework project and the second is an n-tiered Library application project that includes 4 phases. Responsibility includes developing a Windows Forms phase, Data Access (ADO.NET) phase utilizing SQL Server (T-SQL), Web Application (ASP.NET) phase, and Web Services (WSE) phase.
Framework Project



Framework ProjectMauro_Sist The document describes a business tier framework for a retail company. It includes:
1. Two class libraries - a Foundation library with base classes/interfaces and an AppTypes library with entity/exception classes for business processes.
2. A custom Suppliers collection class that implements the ICustomCollection interface to provide a strongly typed collection of Supplier objects while ensuring type safety and uniqueness.
3. The Suppliers class uses an ArrayList internally and provides various methods like adding, removing, and iterating over suppliers as well as serialization/deserialization functionality.
Java Intro



Java Introbackdoor The document outlines the topics covered in an advanced Java programming course, including object-oriented programming concepts, Java programming fundamentals, GUI programming, networking, and server-side programming. It also provides examples of Java code demonstrating basic syntax, methods, classes, strings, and math functions.
Ad
Similar to Java Database Connectivity (20)
Java Database Connectivity (JDBC)



Java Database Connectivity (JDBC)Pooja Talreja This will give a brief idea about JDBC architecture and how database connectivity can be done in java.
Rajesh jdbc



Rajesh jdbcAditya Sharma This document discusses JDBC (Java Database Connectivity) which provides a uniform interface for connecting to and operating on relational databases from Java code. It describes how JDBC works by establishing a connection between a Java application and database using a JDBC driver, allowing SQL statements to be executed and results processed. Key components of JDBC including the driver manager, drivers, statements, metadata, and result sets are defined. Different architectures for JDBC connections like direct, middle-tier, and use of ODBC bridges are presented along with their pros and cons. The mapping between SQL and Java data types is shown and basic steps for a JDBC program are outlined.
Jdbc 1



Jdbc 1Mukesh Tekwani JDBC allows Java programs to execute SQL statements. It includes interfaces and classes that provide methods for connecting to a database, executing queries, processing result sets, and managing transactions. The key components of JDBC are the JDBC API, driver manager, drivers, and Java SQL package. There are four types of JDBC drivers: Type 1 uses JDBC-ODBC bridge, Type 2 uses a native database API, Type 3 uses a network protocol, and Type 4 communicates directly with a database via its network protocol. Creating a database connection in JDBC involves loading the driver, getting a connection, creating statements, executing queries, and closing resources.
java.pptx



java.pptxbfgd1 The document discusses Java Database Connectivity (JDBC) which provides a standard interface for connecting Java applications to various databases. It describes the JDBC architecture including common components like DriverManager, Connection, Statement, and ResultSet. It also explains the four types of JDBC drivers and how to register drivers, establish a connection, execute queries, and extract result sets in a JDBC application. Key classes like Connection, Statement, PreparedStatement, and ResultSet and their common methods are outlined.
Core jdbc basics



Core jdbc basicsSourabrata Mukherjee The document provides an overview of Core JDBC basics, including:
- JDBC defines interfaces and classes for connecting to databases and executing SQL statements from Java code. It standardizes connecting to databases, executing queries, navigating results, and updates.
- There are four main types of JDBC drivers: JDBC-ODBC bridge, native API, network protocol, and thin drivers. Thin drivers provide the best performance by directly converting JDBC calls to database protocols.
- The basic steps to connect using JDBC are: register the driver, get a connection, create statements to execute queries and updates, handle result sets, and close the connection. Transactions allow grouping statements
Jdbc



JdbcMumbai Academisc JDBC provides a standard Java API for connecting Java applications to relational databases. It defines interfaces for establishing a connection to a database, sending SQL statements, processing results, and handling errors. There are four types of JDBC drivers that implement the API in different ways, including bridge drivers, native drivers, network protocol drivers, and pure Java drivers.
4-INTERDUCATION TO JDBC-2019.ppt



4-INTERDUCATION TO JDBC-2019.pptNaveenKumar648465 JDBC provides a standard interface for connecting Java applications to different database systems. It allows Java programs to contain database-independent code. The key steps in a basic JDBC program are: 1) importing JDBC packages, 2) loading and registering the JDBC driver, 3) connecting to the database, 4) creating statements to execute queries, 5) executing queries and processing result sets, and 6) closing connections. JDBC supports different types of drivers including JDBC-ODBC bridge drivers, native API drivers, and pure Java drivers that communicate directly with databases.
Jdbc



JdbcMumbai Academisc Mumbai Academics is Mumbai’s first dedicated Professional Training Center for Training with Spoke and hub model with Multiple verticles . The strong foundation of Mumbai Academics is laid by highly skilled and trained Professionals, carrying mission to provide industry level input to the freshers and highly skilled and trained Software Professionals/other professional to IT companies.
JDBC Presentation with JAVA code Examples.pdf



JDBC Presentation with JAVA code Examples.pdfssuser8878c1 JDBC provides an interface between Java programs and databases. It allows Java programs to send SQL statements to a database and retrieve the results. There are different types of JDBC drivers that allow communication with databases using different methods, such as via ODBC or directly using the database's native APIs. The basic steps to use JDBC include loading the appropriate driver, establishing a connection, creating statements to execute queries and updates, processing result sets, and closing connections.
Unit 5.pdf



Unit 5.pdfsaturo3011 This document discusses various ways to interact with databases from Java programs using JDBC. It covers the main JDBC components like DriverManager, Connection, Statement, and ResultSet. It also describes the different types of JDBC drivers and their characteristics. The key steps to connect a Java application to a database are outlined as registering the driver, getting a connection, creating statements, executing queries, and closing the connection. Sample code is provided to demonstrate connecting to MySQL.
JDBC java for learning java for learn.ppt



JDBC java for learning java for learn.pptkingkolju The document discusses the common JDBC components used to connect to and interact with databases from Java programs. It describes the key interfaces and classes in JDBC including DriverManager, Driver, Connection, Statement, ResultSet, and SQLException. It provides an overview of how to establish a connection, execute SQL statements, and process the results using these JDBC components.
Jdbc introduction



Jdbc introductionRakesh Kumar Ray The document discusses Java Database Connectivity (JDBC), which provides a standard interface for connecting to relational databases from Java applications. It describes the JDBC model and programming steps, which include loading a JDBC driver, connecting to a database, executing SQL statements via a Statement object, processing query results stored in a ResultSet, and closing connections. It also covers JDBC driver types, the roles of core classes like Connection and Statement, and transaction handling with JDBC.
jdbc



jdbcGayatri Patel This document discusses Java Database Connectivity (JDBC) and its components. It begins with an introduction to JDBC, explaining that JDBC is a Java API that allows Java programs to execute SQL statements and interact with multiple database sources. It then discusses the four types of JDBC drivers - JDBC-ODBC bridge drivers, native-API partly Java drivers, network protocol all-Java drivers, and native protocol all-Java drivers - and their characteristics. The document proceeds to explain the standard seven steps to querying databases using JDBC: loading the driver, defining the connection URL, establishing the connection, creating a statement object, executing a query or update, processing results, and closing the connection.
JDBC-Introduction



JDBC-IntroductionMythili Shankar JDBC is a Java API that allows Java programs to connect to databases. It provides standard methods for querying and updating data and includes drivers specific to different database systems. The key components of JDBC include the JDBC API, driver manager, drivers, and architecture. The architecture supports both two-tier and three-tier models for connecting Java applications to databases.
jdbc document



jdbc documentYamuna Devi The document discusses Java Database Connectivity (JDBC). It describes JDBC as a Java API that allows Java programs to execute SQL statements. It provides methods for querying and updating data within a database. The document outlines the different components and specifications of JDBC, including the JDBC driver manager, JDBC drivers, and JDBC APIs. It also discusses the different types of JDBC drivers and their architectures.
Java and Database - Interacting with database



Java and Database - Interacting with databaseAmol Gaikwad This files explains java and database connectivity concepts.
Jdbc 1



Jdbc 1Tuan Ngo JDBC is a Java API that provides interfaces for connecting to and working with databases. It allows Java applications to execute SQL statements and process the results by providing a standard interface for database access that is independent of database vendors. The key classes and interfaces in JDBC include Connection, Statement, PreparedStatement, CallableStatement, and ResultSet. JDBC drivers convert JDBC calls into database-specific protocols to communicate with the database.
What is JDBC



What is JDBCuniversity of education,Lahore JDBC (Java Database Connectivity) is a standard Java API that allows Java programs to connect to and interact with various database systems in a database-independent way. It provides interfaces for querying and updating data in a database, as well as interfaces for executing SQL statements. The JDBC architecture consists of the JDBC API layer and the JDBC driver API layer. Common JDBC components include the DriverManager, Drivers, Connections, Statements, ResultSets, and SQLExceptions.
Java database connectivity



Java database connectivityVaishali Modi JDBC (Java Database Connectivity) is a standard Java API for connecting to databases. It provides interfaces for tasks like making database connections, executing SQL statements, and retrieving results. There are 4 types of JDBC drivers that implement the JDBC interfaces in different ways. A basic JDBC program imports SQL packages, registers the JDBC driver, gets a database connection, executes SQL statements using a Statement object, extracts result data, and closes resources.
Ad
More from backdoor (20)
Distributed Programming using RMI



Distributed Programming using RMIbackdoor This document discusses distributed programming with Java RMI. It explains the key components of client-server systems and different distributed computing models like DCE, DCOM, CORBA, and Java RMI. It then describes how Java RMI works, the packages involved, and provides steps to implement a basic RMI application with a remote interface, server implementation, and client.
Programming Server side with Sevlet 



Programming Server side with Sevlet backdoor The document provides an overview of servlets, including:
- What servlets are and how they work
- The lifecycle of a servlet from initialization to handling requests to destruction
- Options for server-side development like CGI, FastCGI, PHP
- Advantages of using servlets like performance, portability, and security
Distributed Programming using RMI



Distributed Programming using RMIbackdoor This document discusses distributed programming with Java RMI. It explains the key components of client-server systems and different distributed computing models like DCE, DCOM, CORBA, and Java RMI. It then describes how Java RMI works, the packages involved, and provides steps to implement a basic RMI application with a remote interface, server implementation, and client.
Client Side Programming with Applet



Client Side Programming with Appletbackdoor - Java applets allow Java programs to run within web browsers. All applets extend the Applet class and override lifecycle methods like init(), start(), stop(), and destroy().
- To create an applet, you define its structure using these lifecycle methods and draw to the screen using the Graphics object's drawing methods. Applets are compiled and run within HTML using the <applet> tag.
- Applets differ from standalone Java applications in that they have security restrictions and run within a web browser rather than having their own execution environment. The Graphics class provides methods for drawing various shapes, text, and images to the applet display area.
Java Network Programming



Java Network Programmingbackdoor This document provides an introduction to networking and internet concepts like protocols, TCP, UDP and client-server computing. It explains key classes in the java.net package used for network programming like InetAddress, Socket, ServerSocket, DatagramSocket, DatagramPacket, URL, URLConnection and ContentHandler. The classes help establish connections, send/receive data and interact with resources on the web. Common port numbers and their associated protocols are also listed. TCP establishes links between source and destination ports while UDP is connectionless and sends data in datagrams without delivery assurance.
Windows Programming with Swing



Windows Programming with Swingbackdoor The document discusses Java Swing, which provides GUI components for building desktop applications. It describes key Swing concepts like the MVC architecture, event handling, look and feel, and core Swing components like windows, menus, buttons, panels and tables. It also lists various Swing packages and example programs to demonstrate different Swing features.
Windows Programming with AWT



Windows Programming with AWTbackdoor The document provides an overview of the Abstract Windowing Toolkit (AWT) in Java, including:
1. AWT allows the creation of graphical user interfaces and provides containers, components, layout managers, graphics capabilities, and event handling.
2. Common containers include frames, panels, dialogs. Common components include labels, text fields, text areas, buttons, checkboxes, lists.
3. Layout managers like flow, border, grid, card and gridbag layouts are used to position components in containers.
4. Events in AWT are handled through interfaces like action listener, item listener and mouse listener. Programmers implement the appropriate listener interface.
Multithreading



Multithreadingbackdoor The document discusses threads and multithreading in Java. It defines a thread as a single sequential flow of control that runs within the address space of a process. It notes that threads allow programs to accomplish multiple simultaneous tasks. The document then covers thread states, priorities, synchronization, and provides examples of a producer-consumer problem implemented with and without synchronization.
Object and Classes in Java



Object and Classes in Javabackdoor This document discusses classes and objects in Java, including:
- Classes should implement object models and reflect real-world objects.
- Constructors prepare objects for use and finalizers perform cleanup before objects are discarded.
- Reference objects and the garbage collector determine how reachable objects are.
- Cloning objects allows copying but a deep copy duplicates contained objects.
- The Reflection API supports introspection to access class information at runtime.
- Nested and inner classes can be defined inside other classes.
IO and serialization



IO and serializationbackdoor The document discusses input/output (I/O) and serialization in Java. It covers the core I/O packages that support console and file I/O, as well as the new I/O package. It also describes object serialization which allows objects to be written to streams and read back without defining additional methods, enabling object transmission over networks. Key I/O classes include InputStream, OutputStream, Reader and Writer.
Exception Handling



Exception Handlingbackdoor Exception handling in Java involves using try, catch, and finally blocks to gracefully handle errors and unexpected conditions at runtime. The try block contains code that might throw exceptions, catch blocks specify how to handle specific exceptions, and finally ensures cleanup code runs regardless of exceptions. User-defined exceptions can be created by subclassing the Exception class and using throw to raise the exception which catch blocks can then handle.
Object Oriented Programming with Java



Object Oriented Programming with Javabackdoor The document discusses key concepts of object-oriented programming including objects, classes, inheritance, polymorphism, encapsulation, and abstraction. It provides examples of constructors, method overloading and overriding, interfaces, and packages in Java.
AWT Program output



AWT Program outputbackdoor This document provides output summaries for 14 Java AWT programs and exercises from an advanced Java course. It lists the program numbers and exercise numbers but does not include any details about the programs or what each output demonstrates.
Net Man



Net Manbackdoor The document discusses network management topics including the Network Availability Program (NAP) which predicts network availability and reliability, Simple Network Management Protocol (SNMP) which is used to monitor network devices, Abstract Syntax Notation One (ASN.1) which defines data structures for network communication, Management Information Base (MIB) which describes managed objects in a network, common network management protocols like CMIP and SNMP, and responsibilities of a Communication Systems Manager.
Data Security



Data Securitybackdoor The document discusses various topics related to data security including encryption, firewalls, virtual private networks (VPNs), authentication, digital certificates, digital signatures, internet viruses, and online data security tools. It provides details on how each of these topics work to secure data and protect against viruses. The document also lists some popular antivirus software and security websites for additional information.
Ne Course Part One



Ne Course Part Onebackdoor This document provides an overview of computer viruses and data security topics. It discusses different types of malware like viruses, worms, Trojan horses and hybrids. It also covers topics like encryption, firewalls, authentication, virtual private networks, digital certificates, digital signatures, certification authorities and online security assistants. The document aims to educate about computer viruses, data security issues and how to prevent and protect against malware.
Ne Course Part Two



Ne Course Part Twobackdoor The document discusses various aspects of information security and network security. It defines information security and describes different types including physical security, communication security, and network security. It then discusses several common security processes and tools used for protection, such as anti-virus software, access controls, firewalls, intrusion detection systems, policy management, and vulnerability scanning. However, it notes that no single security measure provides complete protection and that security is an ongoing process.
Net Sec



Net Secbackdoor The document discusses various topics related to practical network security including security threats, data security, private communication over public channels, security services, applications that provide security like VPNs and firewalls, types of intruders, intrusion detection, and references for further information. It addresses confidentiality, authenticity, integrity, and non-repudiation as security services and discusses tools like firewalls, intrusion detection, and spam filters that can help safeguard networks.
Security Policy Checklist



Security Policy Checklistbackdoor This document provides a comprehensive checklist to help create or audit an IT security policy. The checklist covers a wide variety of topics including web browsing, usernames/passwords, email, file access permissions, backups, disaster recovery, physical security, and security for PCs/laptops. For each topic, it lists key planning items and considerations to develop a thorough policy that protects organizational assets and data.
Bcis Csm Chapter Three



Bcis Csm Chapter Threebackdoor The document discusses network security and computer viruses. It defines network security and lists common types of computer viruses such as macro viruses, worms, and Trojan horses. It provides preventive actions against viruses like using antivirus software and security patches. Examples of antivirus software are also given along with their criteria. The document also defines disaster recovery plans and lists common network security threats such as malicious threats from spoofing, scanning and eavesdropping.
Recently uploaded (20)
Your startup on AWS - How to architect and maintain a Lean and Mean account J...



Your startup on AWS - How to architect and maintain a Lean and Mean account J...angelo60207 Prevent infrastructure costs from becoming a significant line item on your startup’s budget! Serial entrepreneur and software architect Angelo Mandato will share his experience with AWS Activate (startup credits from AWS) and knowledge on how to architect a lean and mean AWS account ideal for budget minded and bootstrapped startups. In this session you will learn how to manage a production ready AWS account capable of scaling as your startup grows for less than $100/month before credits. We will discuss AWS Budgets, Cost Explorer, architect priorities, and the importance of having flexible, optimized Infrastructure as Code. We will wrap everything up discussing opportunities where to save with AWS services such as S3, EC2, Load Balancers, Lambda Functions, RDS, and many others.
Oracle Cloud Infrastructure AI Foundations



Oracle Cloud Infrastructure AI FoundationsVICTOR MAESTRE RAMIREZ Oracle Cloud Infrastructure AI Foundations
Edge-banding-machines-edgeteq-s-200-en-.pdf



Edge-banding-machines-edgeteq-s-200-en-.pdfAmirStern2 מכונת קנטים המתאימה לנגריות קטנות או גדולות (כמכונת גיבוי).
מדביקה קנטים מגליל או פסים, עד עובי קנט – 3 מ"מ ועובי חומר עד 40 מ"מ. בקר ממוחשב המתריע על תקלות, ומנועים מאסיביים תעשייתיים כמו במכונות הגדולות.
Boosting MySQL with Vector Search -THE VECTOR SEARCH CONFERENCE 2025 .pdf



Boosting MySQL with Vector Search -THE VECTOR SEARCH CONFERENCE 2025 .pdfAlkin Tezuysal As the demand for vector databases and Generative AI continues to rise, integrating vector storage and search capabilities into traditional databases has become increasingly important. This session introduces the *MyVector Plugin*, a project that brings native vector storage and similarity search to MySQL. Unlike PostgreSQL, which offers interfaces for adding new data types and index methods, MySQL lacks such extensibility. However, by utilizing MySQL's server component plugin and UDF, the *MyVector Plugin* successfully adds a fully functional vector search feature within the existing MySQL + InnoDB infrastructure, eliminating the need for a separate vector database. The session explains the technical aspects of integrating vector support into MySQL, the challenges posed by its architecture, and real-world use cases that showcase the advantages of combining vector search with MySQL's robust features. Attendees will leave with practical insights on how to add vector search capabilities to their MySQL systems.
Floods in Valencia: Two FME-Powered Stories of Data Resilience



Floods in Valencia: Two FME-Powered Stories of Data ResilienceSafe Software In October 2024, the Spanish region of Valencia faced severe flooding that underscored the critical need for accessible and actionable data. This presentation will explore two innovative use cases where FME facilitated data integration and availability during the crisis. The first case demonstrates how FME was used to process and convert satellite imagery and other geospatial data into formats tailored for rapid analysis by emergency teams. The second case delves into making human mobility data—collected from mobile phone signals—accessible as source-destination matrices, offering key insights into population movements during and after the flooding. These stories highlight how FME's powerful capabilities can bridge the gap between raw data and decision-making, fostering resilience and preparedness in the face of natural disasters. Attendees will gain practical insights into how FME can support crisis management and urban planning in a changing climate.
Oracle Cloud and AI Specialization Program



Oracle Cloud and AI Specialization ProgramVICTOR MAESTRE RAMIREZ Oracle Cloud and AI Specialization Program
cnc-drilling-dowel-inserting-machine-drillteq-d-510-english.pdf



cnc-drilling-dowel-inserting-machine-drillteq-d-510-english.pdfAmirStern2 CNC מכונות קידוח drillteq d-510
Your startup on AWS - How to architect and maintain a Lean and Mean account



Your startup on AWS - How to architect and maintain a Lean and Mean accountangelo60207 Prevent infrastructure costs from becoming a significant line item on your startup’s budget! Serial entrepreneur and software architect Angelo Mandato will share his experience with AWS Activate (startup credits from AWS) and knowledge on how to architect a lean and mean AWS account ideal for budget minded and bootstrapped startups. In this session you will learn how to manage a production ready AWS account capable of scaling as your startup grows for less than $100/month before credits. We will discuss AWS Budgets, Cost Explorer, architect priorities, and the importance of having flexible, optimized Infrastructure as Code. We will wrap everything up discussing opportunities where to save with AWS services such as S3, EC2, Load Balancers, Lambda Functions, RDS, and many others.
Agentic AI: Beyond the Buzz- LangGraph Studio V2



Agentic AI: Beyond the Buzz- LangGraph Studio V2Shashikant Jagtap Presentation given at the LangChain community meetup London
https://lu.ma/9d5fntgj
Coveres
Agentic AI: Beyond the Buzz
Introduction to AI Agent and Agentic AI
Agent Use case and stats
Introduction to LangGraph
Build agent with LangGraph Studio V2
How Advanced Environmental Detection Is Revolutionizing Oil & Gas Safety.pdf



How Advanced Environmental Detection Is Revolutionizing Oil & Gas Safety.pdfRejig Digital Unlock the future of oil & gas safety with advanced environmental detection technologies that transform hazard monitoring and risk management. This presentation explores cutting-edge innovations that enhance workplace safety, protect critical assets, and ensure regulatory compliance in high-risk environments.
🔍 What You’ll Learn:
✅ How advanced sensors detect environmental threats in real-time for proactive hazard prevention
🔧 Integration of IoT and AI to enable rapid response and minimize incident impact
📡 Enhancing workforce protection through continuous monitoring and data-driven safety protocols
💡 Case studies highlighting successful deployment of environmental detection systems in oil & gas operations
Ideal for safety managers, operations leaders, and technology innovators in the oil & gas industry, this presentation offers practical insights and strategies to revolutionize safety standards and boost operational resilience.
👉 Learn more: https://www.rejigdigital.com/blog/continuous-monitoring-prevent-blowouts-well-control-issues/
Can We Use Rust to Develop Extensions for PostgreSQL? (POSETTE: An Event for ...



Can We Use Rust to Develop Extensions for PostgreSQL? (POSETTE: An Event for ...NTT DATA Technology & Innovation Can We Use Rust to Develop Extensions for PostgreSQL?
(POSETTE: An Event for Postgres 2025)
June 11, 2025
Shinya Kato
NTT DATA Japan Corporation
The State of Web3 Industry- Industry Report



The State of Web3 Industry- Industry ReportLiveplex Web3 is poised for mainstream integration by 2030, with decentralized applications potentially reaching billions of users through improved scalability, user-friendly wallets, and regulatory clarity. Many forecasts project trillions of dollars in tokenized assets by 2030 , integration of AI, IoT, and Web3 (e.g. autonomous agents and decentralized physical infrastructure), and the possible emergence of global interoperability standards. Key challenges going forward include ensuring security at scale, preserving decentralization principles under regulatory oversight, and demonstrating tangible consumer value to sustain adoption beyond speculative cycles.
Scaling GenAI Inference From Prototype to Production: Real-World Lessons in S...



Scaling GenAI Inference From Prototype to Production: Real-World Lessons in S...Anish Kumar Presented by: Anish Kumar
LinkedIn: https://www.linkedin.com/in/anishkumar/
This lightning talk dives into real-world GenAI projects that scaled from prototype to production using Databricks’ fully managed tools. Facing cost and time constraints, we leveraged four key Databricks features—Workflows, Model Serving, Serverless Compute, and Notebooks—to build an AI inference pipeline processing millions of documents (text and audiobooks).
This approach enables rapid experimentation, easy tuning of GenAI prompts and compute settings, seamless data iteration and efficient quality testing—allowing Data Scientists and Engineers to collaborate effectively. Learn how to design modular, parameterized notebooks that run concurrently, manage dependencies and accelerate AI-driven insights.
Whether you're optimizing AI inference, automating complex data workflows or architecting next-gen serverless AI systems, this session delivers actionable strategies to maximize performance while keeping costs low.
Crypto Super 500 - 14th Report - June2025.pdf



Crypto Super 500 - 14th Report - June2025.pdfStephen Perrenod This OrionX's 14th semi-annual report on the state of the cryptocurrency mining market. The report focuses on Proof-of-Work cryptocurrencies since those use substantial supercomputer power to mint new coins and encode transactions on their blockchains. Only two make the cut this time, Bitcoin with $18 billion of annual economic value produced and Dogecoin with $1 billion. Bitcoin has now reached the Zettascale with typical hash rates of 0.9 Zettahashes per second. Bitcoin is powered by the world's largest decentralized supercomputer in a continuous winner take all lottery incentive network.
Establish Visibility and Manage Risk in the Supply Chain with Anchore SBOM



Establish Visibility and Manage Risk in the Supply Chain with Anchore SBOMAnchore Over 70% of any given software application consumes open source software (most likely not even from the original source) and only 15% of organizations feel confident in their risk management practices.
With the newly announced Anchore SBOM feature, teams can start safely consuming OSS while mitigating security and compliance risks. Learn how to import SBOMs in industry-standard formats (SPDX, CycloneDX, Syft), validate their integrity, and proactively address vulnerabilities within your software ecosystem.
Domino IQ – What to Expect, First Steps and Use Cases



Domino IQ – What to Expect, First Steps and Use Casespanagenda Webinar Recording: https://www.panagenda.com/webinars/domino-iq-what-to-expect-first-steps-and-use-cases/
HCL Domino iQ Server – From Ideas Portal to implemented Feature. Discover what it is, what it isn’t, and explore the opportunities and challenges it presents.
Key Takeaways
- What are Large Language Models (LLMs) and how do they relate to Domino iQ
- Essential prerequisites for deploying Domino iQ Server
- Step-by-step instructions on setting up your Domino iQ Server
- Share and discuss thoughts and ideas to maximize the potential of Domino iQ
Oracle Cloud Infrastructure Generative AI Professional



Oracle Cloud Infrastructure Generative AI ProfessionalVICTOR MAESTRE RAMIREZ Oracle Cloud Infrastructure Generative AI Professional
Enabling BIM / GIS integrations with Other Systems with FME



Enabling BIM / GIS integrations with Other Systems with FMESafe Software Jacobs has successfully utilized FME to tackle the complexities of integrating diverse data sources in a confidential $1 billion campus improvement project. The project aimed to create a comprehensive digital twin by merging Building Information Modeling (BIM) data, Construction Operations Building Information Exchange (COBie) data, and various other data sources into a unified Geographic Information System (GIS) platform. The challenge lay in the disparate nature of these data sources, which were siloed and incompatible with each other, hindering efficient data management and decision-making processes.
To address this, Jacobs leveraged FME to automate the extraction, transformation, and loading (ETL) of data between ArcGIS Indoors and IBM Maximo. This process ensured accurate transfer of maintainable asset and work order data, creating a comprehensive 2D and 3D representation of the campus for Facility Management. FME's server capabilities enabled real-time updates and synchronization between ArcGIS Indoors and Maximo, facilitating automatic updates of asset information and work orders. Additionally, Survey123 forms allowed field personnel to capture and submit data directly from their mobile devices, triggering FME workflows via webhooks for real-time data updates. This seamless integration has significantly enhanced data management, improved decision-making processes, and ensured data consistency across the project lifecycle.
Down the Rabbit Hole – Solving 5 Training Roadblocks



Down the Rabbit Hole – Solving 5 Training RoadblocksRustici Software Feeling stuck in the Matrix of your training technologies? You’re not alone. Managing your training catalog, wrangling LMSs and delivering content across different tools and audiences can feel like dodging digital bullets. At some point, you hit a fork in the road: Keep patching things up as issues pop up… or follow the rabbit hole to the root of the problems.
Good news, we’ve already been down that rabbit hole. Peter Overton and Cameron Gray of Rustici Software are here to share what we found. In this webinar, we’ll break down 5 training roadblocks in delivery and management and show you how they’re easier to fix than you might think.
Can We Use Rust to Develop Extensions for PostgreSQL? (POSETTE: An Event for ...



Can We Use Rust to Develop Extensions for PostgreSQL? (POSETTE: An Event for ...NTT DATA Technology & Innovation
Java Database Connectivity
- 1. IADCS Diploma Course Java Database Connectivity U Nyein Oo COO/Director (IT) Myanma Computer Co., Ltd
- 2. JDBC API JDBC API stands for Java Database Connectivity Application Programming Interface It is a set of specifications that defines how a Java program can communicate with the database It defines how an application opens a connection, communicates with the database, executes SQL statements and retrieves the results Many of the JDBC API concepts are taken from other sources, particularly Microsoft’s ODBC (Open Database Connectivity)
- 3. JDBC API (Contd…) Figure below depicts the functioning of the JDBC API
- 4. JDBC Drivers It ensures that the application interacts with all databases in a standard and uniform manner It ensures that the requests made by the application are presented to the database in a language understood by the database It receives the requests from the client, converts it into the format understandable by the database and then presents it to the database It receives the response, translates it back to Java data format and presents it to the client application All databases follow SQL and hence there is only one JDBC Driver, that is, the Java-to-SQL translator
- 5. JDBC Drivers (Contd…) Figure below depicts the working of JDBC Driver
- 6. JDBC Products Three components of JDBC: java.sql package Test Suite JDBC-ODBC bridge
- 7. java.sql package It contains a set of interfaces and classes defined by JDBC API that are used for communicating with the database Interfaces of java.sql package: CallableStatement Connection DatabaseMetaData Driver PreparedStatement ResultSet ResultSetMetaData Statement
- 8. java.sql package (Contd…) Exceptions defined by java.sql package: DataTruncation SQLException SQLWarning
- 9. JDBC Driver Test Suite It tests the functionality of a JDBC Driver It ensures that all classes and methods defined in the JDBC API are implemented Once the driver passes through all the tests, the test suite can be designated as JDBC COMPLAINT
- 10. JDBC-ODBC Bridge It is a JDBC driver designed to allow Java applications to communicate with the database using ODBC driver It allows developers to begin writing JDBC applications without having to wait for a native driver for their database It is a part of the JDBC package
- 11. JDBC Products (Contd…) To work with JDBC API the following are required: Java Development ToolKit (JDK) SQL complaint database JDBC driver for database
- 12. JDBC Design Considerations JDBC driver fits into the architecture of various client/server models Four types of JDBC drivers: JDBC-ODBC Bridge Native API Java JDBC Network Native Protocol
- 13. JDBC-ODBC Bridge This driver is supplied by JavaSoft. It is the only driver that can be used with multiple databases. The ODBC interface remains constant no matter which database is used. Once the request is passed by the JDBC to the ODBC driver, it is the responsibility of the ODBC driver to communicate it with the database. An disadvantage of JDBC-ODBC bridge driver is that it adds one more layer of complexity to the program and can make software bugs more difficult to solve.
- 14. JDBC-ODBC Bridge (Contd...) Figure below depicts how JDBC-ODBC bridge driver is implemented
- 15. Native-API-Partly-Java Driver It makes use of local native libraries to communicate with the database It does this by calling to the local installed native call level interface (CLI) The CLI libraries are actually responsible for the communication with the database server When a client makes a request, the driver translates the JDBC request to the native method call and then passes the request to the native CLI
- 16. Native-API-Partly-Java Driver (Contd...) Figure below depicts how native driver is implemented
- 17. JDBC-Net-All-Java Driver The only difference between the previous two drivers is the placement of the native database access libraries The native CLI libraries are placed on the remote server and the driver uses a network protocol to communicate between the application and the driver The driver is split into two parts: one containing all Java portion that can be downloaded to the client and the server portion containing both Java and native methods
- 18. Native-Protocol-All-Java Driver These drivers are 100% Java and use no CLI libraries It is capable of communicating directly with the database without any need of translation
- 19. Two-Tier Client Server Model The architecture of any client-server environment is by default a two-tier system The client is the first tier and the server the second tier In a two-tier JDBC environment, the database application is the client and the DBMS is the server The client communicates directly with the server
- 20. Two-Tier Client Server Model (Contd...) Figure below depicts a two-tier client-server model
- 21. Advantages of using a two-tier database system: It is the least complicated system to implement This architecture maintains a constant connection between the client and the database This system is usually faster than a three-tier implementation Disadvantages of using this system: Most of the drivers require that native libraries be loaded on the client machine Local configuration has to be maintained for native code Applets can open up connection to the server from which they are downloaded Two-Tier Client Server Model (Contd...)
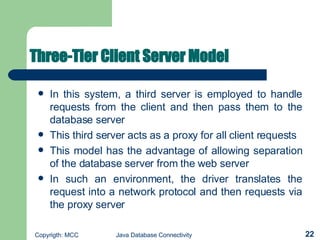
- 22. Three-Tier Client Server Model In this system, a third server is employed to handle requests from the client and then pass them to the database server This third server acts as a proxy for all client requests This model has the advantage of allowing separation of the database server from the web server In such an environment, the driver translates the request into a network protocol and then requests via the proxy server
- 23. Three-Tier Client Server Model (Contd...) Figure below depicts a three-tier client-server environment
- 24. Basic Steps to JDBC Seven steps in using JDBC to access a database: Importing java.sql package Loading and registering the driver Establishing a connection to the database server Creating a statement Executing the statement Retrieving the results Closing the statement and connection
- 25. Basic Steps to JDBC ( contd.. ) Figure below depicts the steps
- 26. Setting up a Connection to the Database java.sql package provides database programming capabilities to Java JDBC API is a programming interface for application developers doing development through database Another major component of JDBC is the JDBC Driver API A database server and database driver are required f or using JDBC
- 27. Setting up a Connection to the Database (Contd...) java.sql.DriverManager class provides methods to load drivers. It consists of the following methods: getDrivers( ) getConnection( ) registerDriver( ) deregisterDriver( ) getLoginTimeout( ) setLoginTimeout( ) getLogStream( ) setLogStream( )
- 28. Creating and Executing SQL Statements An SQL statement is at the center of any JDBC The SQL statement and the JDBC representation are the same The JDBC string needs to be modified to ensure that the database receives the intended SQL statement Any string that is identical to the SQL statement is referred to as simple SQL Statement and those requiring some modifications are considered complex Queries are one of the most important forms of SQL statements
- 29. Creating and Executing SQL Statements (Contd…) In JDBC, all queries return results in the form of ResultSet objects The most efficient way to execute a query is to use the Statement.executeQuery( ) method Time and Date Literals handling is also possible in JDBC Outer joins are also supported by JDBC
- 30. ResultSet and ResultSetMetaData Objects The result of the query is returned in the form of rows and columns The ResultSet interface is used to access this data The query results are returned as ResultSet objects that in turn provide access to the tabular data, one row at a time ResultSetMetaData interface provides constants and methods used to obtain information about the ResultSet object
- 31. Stored Procedures A stored procedure is a group of SQL statements that form a logical unit and perform a particular task They are used to encapsulate a set of operations or queries to execute on a database server They can be compiled and executed with different parameters and results They are supported by most DBMSs, but there is a fair amount of variation in their syntax and capabilities
- 32. Stored Procedures (Contd…) Syntax for creating a procedure create procedure <proc_name> as select <column_name/s> from <table name/s> where <query>
- 33. Calling Stored Procedures Syntax for calling a stored procedure CallableStatement cs = con.prepareCall("{call <Proc_name>}"); ResultSet rs = cs.executeQuery(); Note that the method used to execute ‘cs’ is executeQuery( ) because ‘cs’ calls a stored procedure that contains one query and thus produces one result set If the procedure had contained one update or one DDL statement, the method executeUpdate( ) would have been the one to use
- 34. Database Security Database security is of vital importance. The data contains sensitive and confidential information about the company and hence vital care has to be taken to see that no unauthorized users access it and thereby tamper with the data. Data availability is also of utmost importance. It should be available whenever required. JDBC depends on the database server for providing security.
- 35. Database Security (Contd…) The JDBC makes use of Secure Socket Layer (SSL) in their product lines t hat provides encrypted communication between database driver and server

