JavaOne 2014 - Securing RESTful Resources with OAuth2
- 1. Securing RESTful Resources with OAuth2 Rodrigo Cândido da Silva @rcandidosilva JavaOne 2014 CON4990
- 2. About Me • Brazilian guy ;) • Software Architect • Java Platform • Work for Integritas Tech • http://integritastech.com • JUG Leader of GUJavaSC • http://gujavasc.org • Twitter • @rcandidosilva • Personal • http://rodrigocandido.me
- 3. Agenda • Why use OAuth2? • OAuth2 concepts • Grant types • OAuth2 Tokens • Java Implementations • Demo
- 4. Public Web Service API’s
- 5. Security Closed Closed Open Authentication Authorization
- 6. Securing APIs • Securing resources strategies • Basic Auth (HTTP Basic) • Sending user credentials in http authentication header • Mutual Authentication (HTTP Digest) • Based on certificates, server authenticate to client, client to server • RESTful architecture not defines security procedures • HTTP methods: GET, POST, PUT, DELETE • REST API’s are equal vulnerable as standard web apps • Injection attacks, replay attacks, cross-site scripting, etc.
- 8. With OAuth
- 9. Why OAuth • Open standard protocol specification defined by IETF • Enables applications to access each other’s data without sharing credentials • Avoid password issues • User and password authentication is fine, but what if your API needs to be used by other apps? • Required for delegating access • Third party applications • For specified resource • For limited time • Can be selectively be revoked
- 10. Who is using OAuth
- 11. OAuth Timeline • OAuth 1.0 • Core specification published in Dec 2007 • OAuth 1.0a • Revised specification published in June 2009 • Related to fix a security issue • OAuth 2.0 • Standardized since Oct-2012 • Be more secure, simple, and standard • Additional RFCs are still being worked on
- 12. OAuth2 • No username or passwords (only tokens) • Protocol for authorization – not authentication • Delegated model • Fix the password anti-pattern • Trust relationship between resource, identity server and client app • Goal was simplicity • Relies heavily on TLS/SSL • Not backwards compatible • Easily to revoke
- 13. OAuth2 Roles • Resource Owner • Entity capable of granting access to a protected resource • Client Application • Application making protected resource requests on behalf of the resource owner • Resource Server • The server hosting the protected resources • Authorization Server • The server issuing access tokens to the clients
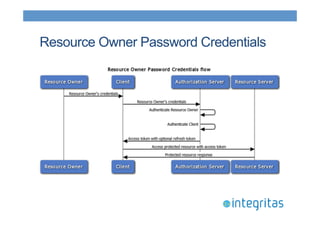
- 15. OAuth2 Grant Types • Authorization Code (web apps) • Optimized for confidential clients • Uses a authorization code from the server • Implicit (browser-based and mobile apps) • Optimized for script heavy web apps • User can see the access token • Resource Owner Password Credentials (user / password) • Used in cases where the user trusts the client • Exposes user credentials to the client • Client Credentials (application) • Clients gets an access token based on client credentials only
- 17. Implicit
- 18. Resource Owner Password Credentials
- 20. OAuth2 Tokens • Types • Bearer • Large random token • Need SSL to protect it in transit • Server needs to store it securely hashed like a user password • Mac • Uses a nonce to prevent replay • Does not required SSL • OAuth 1.0 only supported • Access Token • Short-lived token • Refresh Token • Long-lived token { "access_token":"2YotnFZFEjr1zCsicMWpAA", "token_type":“bearer", "expires_in":3600, "refresh_token":"tGzv3JOkF0XG5Qx2TlKWIA", }
- 21. OAuth2 Pros & Cons • Pros • Integration of third party apps to any sites • Access can be granted for limited scope or duration • No need for users to give password on third party site • Cons • Writing an authorization server is somewhat complex • Interoperability issues • Bad implementations can be security issues
- 22. OAuth2 Java Implementations • Some Java implementations available • Jersey • Apache Oltu • Spring Security OAuth2 • And others: CXF, Google OAuth2 API, etc • Not available as Java EE standard yet
- 23. Jersey • Open source RESTful Web services framework • The JAX-RS reference implementation • Integrates with the Java EE standard security • @RolesAllowed • @PermitAll • @DenyAll • Supports entity filtering features • @EntityFiltering • Only supports OAuth2 at client side :/
- 24. Jersey Java EE security integration @Path("restricted-resource") @Produces("application/json") public class RestrictedResource { @GET @Path(”denyAll") @DenyAll public RestrictedEntity denyAll() { ... } @GET @Path("rolesAllowed") @RolesAllowed({"manager"}) public RestrictedEntity rolesAllowed() { ... } }
- 25. Jersey OAuth2 client support OAuth2CodeGrantFlow.Builder builder = OAuth2ClientSupport .authorizationCodeGrantFlowBuilder( clientId, "https://example.com/oauth/authorization", "https://example.com/oauth/token"); OAuth2CodeGrantFlow flow = builder.property( OAuth2CodeGrantFlow.Phase.AUTHORIZATION, "readOnly", "true") .scope("contact") .build(); String authorizationUri = flow.start(); ... final TokenResult result = flow.finish(code, state); ...
- 26. Apache Oltu • Apache OAuth protocol implementation • It also covers others related implementations • JSON Web Token (JWT) • JSON Web Signature (JWS) • OpenID Connect • Supports the full OAuth2 features • Authorization Server • Resource Server • Client • Provides predefined OAuth2 client types • Facebook, Foursquare, Github, Google, etc • Still being improved…
- 27. Apache Oltu Authorization endpoint protected void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { //dynamically recognize an OAuth profile and perform validation OAuthAuthzRequest oauthRequest = new OAuthAuthzRequest(request); validateRedirectionURI(oauthRequest) //build OAuth response OAuthResponse resp = OAuthASResponse .authorizationResponse(HttpServletResponse.SC_FOUND) .setCode(oauthIssuerImpl.authorizationCode()) .location(ex.getRedirectUri()) .buildQueryMessage(); response.sendRedirect(resp.getLocationUri()); }
- 28. Apache Oltu Token endpoint protected void doPost(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { OAuthIssuer oauthIssuerImpl = new OAuthIssuerImpl(new MD5Generator()); OAuthTokenRequest oauthRequest = new OAuthTokenRequest(request); validateClient(oauthRequest); String authzCode = oauthRequest.getCode(); String accessToken = oauthIssuerImpl.accessToken(); String refreshToken = oauthIssuerImpl.refreshToken(); OAuthResponse r = OAuthASResponse(...); }
- 29. Apache Oltu Protecting the resources protected void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { // Make the OAuth Request and validate it OAuthAccessResourceRequest oauthRequest = new OAuthAccessResourceRequest(request, ParameterStyle.BODY); // Get the access token String accessToken = oauthRequest.getAccessToken(); //... validate access token }
- 30. Apache Oltu OAuth2 client OAuthClientRequest request = OAuthClientRequest .tokenProvider(OAuthProviderType.FACEBOOK) .setGrantType(GrantType.AUTHORIZATION_CODE) .setClientId("your-facebook-application-client-id") .setClientSecret("your-facebook-application-client-secret") .setRedirectURI("http://www.example.com/redirect") .setCode(code) .buildQueryMessage(); //create OAuth client that uses custom http client under the hood OAuthClient oAuthClient = new OAuthClient(new URLConnectionClient()); OAuthAccessTokenResponse oAuthResponse = oAuthClient.accessToken(request); String accessToken = oAuthResponse.getAccessToken(); String expiresIn = oAuthResponse.getExpiresIn();
- 31. Spring Security OAuth • Provides OAuth (1a) and OAuth2 support • Implements 4 types of authorization grants • Supports the OAuth2 full features • Authorization Server • Resources Server • Client • Good integration with JAX-RS and Spring MVC • Configuration using annotation support • Integrates with the Spring ecosystem
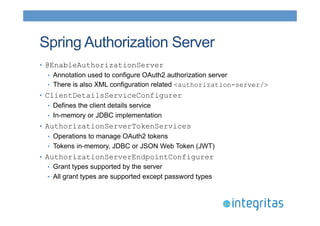
- 32. Spring Authorization Server • @EnableAuthorizationServer • Annotation used to configure OAuth2 authorization server • There is also XML configuration related <authorization-server/> • ClientDetailsServiceConfigurer • Defines the client details service • In-memory or JDBC implementation • AuthorizationServerTokenServices • Operations to manage OAuth2 tokens • Tokens in-memory, JDBC or JSON Web Token (JWT) • AuthorizationServerEndpointConfigurer • Grant types supported by the server • All grant types are supported except password types
- 33. Spring Resource Server • Can be the same as Authorization Server • Or deployed in a separate application • Provides a authentication filter for web protection • @EnableResourceServer • Annotation used to configure OAuth2 resource server • There is also XML configuration related <resource-server/> • Supports expression-based access control • #oauth2.clientHasRole • #oauth2.clientHasAnyRole • #oauth2.denyClient
- 34. Spring OAuth2 Client • Creates a filter to store the current request and context • Manages the redirection to and from the OAuth authentication URI • @EnableOAuth2Client • Annotation used to configure OAuth2 client • There is also XML configuration related <client/> • OAuth2RestTemplate • Wrapper client object to access the resources
- 35. Demo • OAuth2 Use Case • Conference application sharing resources with different clients • http://github.com/rcandidosilva/rest-oauth2-sample
- 36. Questions ?
- 37. References • http://oauth.net/2/ • http://tools.ietf.org/html/rfc6749 • http://projects.spring.io/spring-security-oauth/ • https://github.com/spring-projects/spring-security-oauth • http://cxf.apache.org/docs/jax-rs-oauth2.html • https://jersey.java.net/documentation/latest/security.html#d0e10940 • https://oltu.apache.org
- 38. Thank you! @rcandidosilva rodrigocandido.me