Learning by hacking - android application hacking tutorial
18 likes5,514 views
The document is a tutorial on Android application hacking by Landice Fu, covering concepts such as Java knowledge, Android app design, and using tools like apktool and smali. It emphasizes responsible usage for educational purposes and includes techniques for localization, decompiling, and reverse engineering. The content also highlights strategies for protecting applications against hacking and provides insights into modifying applications.
1 of 29








![xxxxx!Free
Localization Demo
❖ You don’t even need to know how to
write android app or JAVA!
!
❖ Android multi-language support
mechanism [1][2]!
!
[1] http://developer.android.com/training/basics/supporting-devices/languages.html! !
[2] http://jjnnykimo.pixnet.net/blog/post/37831205-android%E5%A4%9A%E5%9C%8B%E8%AA
%9E%E8%A8%80%E8%B3%87%E6%96%99%E5%A4%BE%E5%91%BD%E5%90%8D
%E6%96%B9%E5%BC%8F](https://image.slidesharecdn.com/learningbyhacking-androidapplicationhackingtutorial-141214092757-conversion-gate02/85/Learning-by-hacking-android-application-hacking-tutorial-10-320.jpg)


















Recommended
Hacking your Android (slides)
Hacking your Android (slides)Justin Hoang This document provides an overview of Android malware. It begins with background on Android architecture, including that Android applications are packaged in APK files which contain code, resources, and an AndroidManifest file. It discusses Android application components like Activities and Services. It then covers the Android security model, permissions, and the Dalvik virtual machine. The document demonstrates reversing an APK file and outlines steps for creating a basic malware. It concludes with discussions of notable Android malware examples and opportunities for mobile application penetration testing.
The art of android hacking
The art of android hackingAbhinav Mishra This document discusses Android application security and provides an overview of assessing Android applications for vulnerabilities. It covers Android architecture, application structure, tools for analysis including emulators and Drozer, and demonstrates reversing an APK file. The document also lists examples of vulnerabilities the presenter has found in Android apps with associated bounty amounts, and how to detect each one. It proposes using a virtual machine called Droider for Android application assessments.
[Wroclaw #2] iOS Security - 101
[Wroclaw #2] iOS Security - 101OWASP This document summarizes iOS security features and risks for mobile applications. It outlines the typical architecture of an iOS app, including protection features like ASLR, non-executable memory, ARC, code signing, and sandboxing. It also discusses tools for analyzing iOS apps and potential risks like insecure data storage, lack of transport layer protection, unintended data leakage, poor authentication, and lack of binary protections. The document demonstrates examples of using tools like Cycript, Clutch, and Class-dump to inspect apps and decrypt or dump classes from binaries.
Hacker Halted 2014 - Reverse Engineering the Android OS
Hacker Halted 2014 - Reverse Engineering the Android OSEC-Council The document is a comprehensive overview of reverse engineering the Android OS, detailing its architecture, security features, potential vulnerabilities, and historical malware evolution. It discusses the implications of rooting devices, managing permissions, and the importance of understanding app functionalities to mitigate risks associated with mobile hacking. Additionally, it covers development tools, techniques for analysis, and best practices for maintaining security on Android devices.
Android Hacking
Android Hackingantitree The document discusses tools and techniques related to analyzing Android applications. It provides an overview of the Android operating system architecture and outlines various static and dynamic analysis methods. These include decompiling applications with Apktool and Dex2jar, reviewing manifest files, monitoring network traffic with Wireshark, and using tools like Burp Suite and Mallory. The document also highlights common mobile security issues discovered through analysis and provides recommendations for securing Android devices and applications.
My Null Android Penetration Session
My Null Android Penetration Session Avinash Sinha The document summarizes a session on Android penetration testing organized by Null Bangalore, documenting step-by-step instructions on tools and processes for testing vulnerabilities in Android applications. It covers installation, configuration, capturing HTTPS traffic, and details about specific vulnerable apps like FourGoat and Herd Financial. The notes aim to aid both attendees and those who could not participate in the session by providing comprehensive guidance and troubleshooting tips.
Dark Side of iOS [SmartDevCon 2013]
Dark Side of iOS [SmartDevCon 2013]Kuba Břečka This document discusses security and privacy considerations for iOS application development. It describes how jailbreaking an iOS device removes restrictions like sandboxing and allows access to the entire filesystem. It also explains how private APIs, encrypted binaries, and app review processes can be bypassed to extract information from iOS apps and modify their behavior. While modification is difficult, metadata can be easily extracted from iOS and Android apps. The document encourages developers to understand platform internals and take a reasonable approach to security rather than a paranoid one.
The Hookshot: Runtime Exploitation
The Hookshot: Runtime ExploitationPrathan Phongthiproek The document discusses dynamic binary instrumentation (DBI) and the use of the Frida toolkit for runtime exploitation without the need for rooting or jailbreaking devices. It highlights methods to bypass security measures such as root detection and SSL pinning, along with case studies and countermeasures for mobile banking applications. Additionally, it provides references and automation scripts for injecting libraries into apps for security analysis.
Android security and penetration testing | DIVA | Yogesh Ojha
Android security and penetration testing | DIVA | Yogesh OjhaYogesh Ojha This document provides an overview of Android security and penetration testing. It discusses the Android runtime environment and application fundamentals. It then examines the contents of an Android APK file, including the AndroidManifest.xml and code files. The document outlines the Android sandbox security model and various tools for decompiling and analyzing APKs. It introduces the DIVA vulnerable Android app and demonstrates several common security issues like insecure data storage, input validation problems, and ways to capture network traffic.
Android App Hacking - Erez Metula, AppSec
Android App Hacking - Erez Metula, AppSecDroidConTLV This document summarizes an expert presentation on hacking Android apps. It discusses the top 10 most common Android app vulnerabilities according to OWASP, including weak server-side controls, insecure data storage, lack of transport layer security, unintended data leakage, poor authorization and authentication, broken cryptography, client-side injections, making security decisions via untrusted inputs, improper session handling, and lack of binary protections. Specific attack examples for each vulnerability are provided.
[Wroclaw #1] Android Security Workshop
[Wroclaw #1] Android Security WorkshopOWASP The document summarizes an Android security workshop that took place on February 24th, 2016 in Poland. The workshop included sessions on Android fundamentals, application component security, and the OWASP top 10 mobile risks. It also covered reverse engineering and malware analysis. The document provides an agenda and summaries of the topics discussed in each session, including details on Android architecture, security features in Android 6.0, application permissions and components, and common mobile risks. It aims to provide attendees with a basic understanding of Android security concepts and methodologies for analyzing mobile applications for security issues.
Mobile Application Pentest [Fast-Track]
Mobile Application Pentest [Fast-Track]Prathan Phongthiproek The document discusses security issues related to mobile applications. It describes how mobile apps now offer many more services than basic phone calls and texts. This expanded functionality introduces new attack surfaces, including the client software on the device, the communication channel between the app and server, and server-side infrastructure. Some common vulnerabilities discussed are insecure data storage on the device, weaknesses in data encryption, SQL injection, and insecure transmission of sensitive data like credentials over the network. The document also provides examples of techniques for analyzing app security like reverse engineering the app code and using a proxy like Burp Suite to intercept network traffic.
Droidcon it-2014-marco-grassi-viaforensics
Droidcon it-2014-marco-grassi-viaforensicsviaForensics Marco Grassi gives a presentation on reverse engineering, penetration testing, and hardening Android apps. The presentation covers techniques for reverse engineering APKs, dealing with obfuscation, tamper detection, securing network communications, attacks on IPC, and more advanced topics like runtime manipulation. Real-world examples are provided to demonstrate vulnerabilities found in apps and how they can be exploited.
Android pen test basics
Android pen test basicsOWASPKerala The document covers topics related to Android penetration testing including the Android security model, software stack, content providers, and secure coding practices. The Android security model uses app isolation and each app runs in its own Dalvik Virtual Machine. Content providers manage access to structured app data and enable inter-process communication. Reverse engineering the APK file by extracting and decompiling it is demonstrated as part of the app security testing process. Common insecure practices like hardcoding sensitive data and lack of encryption are also discussed.
Drozer - An Android Application Security Tool
Drozer - An Android Application Security Tool nullowaspmumbai The document discusses the Android application security tool Drozer. It provides an overview of Drozer's capabilities including leaking content providers, attacking broadcast receivers, and abusing application permissions. The document then demonstrates Drozer's usage through several examples analyzing vulnerable Android applications and exploiting issues like content provider leakage, insecure broadcast receivers, and permission abuse.
Null Mumbai Meet_Android Reverse Engineering by Samrat Das
Null Mumbai Meet_Android Reverse Engineering by Samrat Dasnullowaspmumbai The document provides a comprehensive guide on reverse engineering and penetration testing for Android applications, covering fundamentals, tools, and methodologies involved in the analysis. It details the process of reverse engineering APK files, from extraction to packing, and outlines various security concerns and exploitation techniques for mobile applications. Additionally, it discusses common tools like Apktool, Drozer, and Java decompilers, as well as the importance of secure coding practices in Android development.
Pentesting Mobile Applications (Prashant Verma)
Pentesting Mobile Applications (Prashant Verma)ClubHack The document discusses penetration testing (pentesting) for mobile applications, covering both Android and iOS architectures, data storage, traffic capturing, and application reversal techniques. It highlights critical vulnerabilities and risks in mobile applications, including malware threats and insecure data handling practices. Best practices for securing mobile applications are also provided, such as encrypting data and avoiding hardcoding sensitive information.
BlackHat 2014 Briefings - Exploiting Fundamental Weaknesses in Botnet C&C Pan...
BlackHat 2014 Briefings - Exploiting Fundamental Weaknesses in Botnet C&C Pan...Aditya K Sood The document details a research presentation by Dr. Aditya K. Sood focused on exploiting vulnerabilities in command-and-control (C&C) panels used by botnets like Zeus and Citadel. It covers the architecture of C&C systems, methods for bypassing defenses, and the use of tools like Google dorks to locate exposed panels. Additionally, it emphasizes the importance of penetration testing and malware analysis in combating cybercrime and outlines future research directions in botnet detection.
Null 14 may_lesser_known_attacks_by_ninadsarang
Null 14 may_lesser_known_attacks_by_ninadsarangNinad Sarang The document summarizes several lesser-known web application attacks. It discusses mutation cross-site scripting (XSS), relative path overwrite XSS, zombie XSS, remote command execution, carriage return line feed (CRLF) attacks, and homograph attacks. For each attack, it provides examples of how the attack works and potential mitigations. The overall document serves as a guide to understanding and defending against these more obscure web application vulnerabilities.
Android Security & Penetration Testing
Android Security & Penetration TestingSubho Halder The document is a presentation by Subho Halder on Android security and penetration testing. It covers topics such as Android internals, the security model, best coding practices, and common malware techniques, highlighting vulnerabilities and exploitation methods using the Android Framework for Exploitation (AFE). Additionally, it emphasizes the importance of security measures and dynamic analysis to protect against malware threats.
Consulthink @ GDG Meets U - L'Aquila2014 - Codelab: Android Security -Il ke...
Consulthink @ GDG Meets U - L'Aquila2014 - Codelab: Android Security -Il ke...Consulthinkspa This document discusses Android key management and cryptography. It covers symmetric and asymmetric encryption algorithms like AES and RSA. It describes using the Android Keystore to securely store cryptographic keys and how PBKDF2 can be used to derive keys from passwords. It also demonstrates how apps can be reversed to extract hardcoded keys and discusses more secure alternatives like storing keys on a server.
Andriod Pentesting and Malware Analysis
Andriod Pentesting and Malware Analysisn|u - The Open Security Community The document provides an overview of Android OS basics, including its history and key components. It discusses understanding APKs, Android's security model, and includes a brief look at popular Android malware. It also covers reversing Android malware and pentesting the Android platform, with demos. The speaker will discuss Android OS, APKs, the security model, rooting, malware, and reversing tools.
iOS Application Security
iOS Application SecurityEgor Tolstoy This document provides an agenda for a training on iOS application penetration testing. It covers topics such as setting up an iOS pen testing environment, understanding the iOS filesystem and Objective-C runtime, runtime analysis and manipulation, insecure data storage, analyzing network traffic, jailbreak detection, secure coding guidelines, and automated testing. Tools discussed include class-dump-z, cycript, clutch, and gdb for analyzing iOS applications.
Pentesting iOS Apps - Runtime Analysis and Manipulation
Pentesting iOS Apps - Runtime Analysis and ManipulationAndreas Kurtz The document discusses runtime analysis and manipulation of iOS apps, highlighting techniques for dynamic analysis using Objective-C. It emphasizes the need for better tools to assess mobile applications and introduces the Snoop-it tool, which enhances security assessments by monitoring and manipulating app behavior. Furthermore, it addresses jailbreak detection and how its bypassing is crucial for robust security evaluations.
OWASP Melbourne - Introduction to iOS Application Penetration Testing
OWASP Melbourne - Introduction to iOS Application Penetration Testingeightbit This document provides an introduction to iOS application penetration testing. It discusses setting up an iOS penetration testing environment, including jailbreaking a test device and installing necessary software tools. It also provides an overview of iOS and Objective-C, covering key security features of iOS like sandboxing, ASLR, code signing, and data encryption. Topics to be covered include assessing data security, binary analysis, runtime manipulation, and evaluating authentication, session management, and transport security.
Fuzzing | Null OWASP Mumbai | 2016 June
Fuzzing | Null OWASP Mumbai | 2016 Junenullowaspmumbai The document outlines a training session on fuzzing, buffer overflow exploitation, and shellcode execution, focusing on the Minishare 1.4.1 application. It explains fuzzing as a technique for discovering exploitable software bugs, buffer overflows as vulnerabilities allowing memory overwrite, and the use of shellcode during exploitation. The session requires tools such as a VM platform, Windows XP, Kali Linux, and OllyDbg debugger.
Hacking android apps by srini0x00
Hacking android apps by srini0x00srini0x00 This document summarizes an agenda for a workshop on hacking and securing Android apps. The agenda includes topics like Android basics, the Android security model, building a "Hello World" app, reverse engineering apps, traffic analysis using Burp Suite and tcpdump, insecure data storage, attacking app authentication, exploiting app components, unintended data leakage, client-side injection, and securing Android apps. The workshop provides demonstrations for many of these topics and discusses penetration testing methodology for finding and exploiting vulnerabilities in Android apps.
Making Enterprise-Ready Plugins - Kaj Kandler JUC West 2015
Making Enterprise-Ready Plugins - Kaj Kandler JUC West 2015Black Duck by Synopsys The presentation discusses the development of enterprise-ready plugins by Black Duck Software for Jenkins, focusing on issues such as credential management and integration challenges. It highlights different plugins, including a security vulnerability report plugin and an update site manager for internal distribution of plugins. The emphasis is on the importance of continuous automation, governance in code, and ensuring security in open-source components.
How to reverse engineer Android applications—using a popular word game as an ...
How to reverse engineer Android applications—using a popular word game as an ...Christoph Matthies The document outlines a comprehensive guide on reverse engineering Android applications to identify vulnerabilities, using a popular word game as a case study. It details the steps to obtain and decompile APK files, manipulate resources, debug code, and automate gameplay through methods like proxy traffic interception and dictionary extraction. The guide emphasizes techniques for modifying application behavior and unlocking premium features while discussing both smali and Java code decompilation processes.
Reverse Engineering Android Application
Reverse Engineering Android Applicationn|u - The Open Security Community This document discusses reverse engineering of Android applications. It provides an overview of Android, noting that it is an open source platform based on Linux and uses Java and the Dalvik Virtual Machine. It lists the tools needed for reverse engineering like JRE, Apktools, SignApk, Dex2jar, and JD-GUI. It outlines two approaches - using Apktool to convert the DEX to SMALI or using Dex2jar to convert to a JAR and then Java. The document concludes by mentioning a live demo will be provided.
More Related Content
What's hot (20)
Android security and penetration testing | DIVA | Yogesh Ojha
Android security and penetration testing | DIVA | Yogesh OjhaYogesh Ojha This document provides an overview of Android security and penetration testing. It discusses the Android runtime environment and application fundamentals. It then examines the contents of an Android APK file, including the AndroidManifest.xml and code files. The document outlines the Android sandbox security model and various tools for decompiling and analyzing APKs. It introduces the DIVA vulnerable Android app and demonstrates several common security issues like insecure data storage, input validation problems, and ways to capture network traffic.
Android App Hacking - Erez Metula, AppSec
Android App Hacking - Erez Metula, AppSecDroidConTLV This document summarizes an expert presentation on hacking Android apps. It discusses the top 10 most common Android app vulnerabilities according to OWASP, including weak server-side controls, insecure data storage, lack of transport layer security, unintended data leakage, poor authorization and authentication, broken cryptography, client-side injections, making security decisions via untrusted inputs, improper session handling, and lack of binary protections. Specific attack examples for each vulnerability are provided.
[Wroclaw #1] Android Security Workshop
[Wroclaw #1] Android Security WorkshopOWASP The document summarizes an Android security workshop that took place on February 24th, 2016 in Poland. The workshop included sessions on Android fundamentals, application component security, and the OWASP top 10 mobile risks. It also covered reverse engineering and malware analysis. The document provides an agenda and summaries of the topics discussed in each session, including details on Android architecture, security features in Android 6.0, application permissions and components, and common mobile risks. It aims to provide attendees with a basic understanding of Android security concepts and methodologies for analyzing mobile applications for security issues.
Mobile Application Pentest [Fast-Track]
Mobile Application Pentest [Fast-Track]Prathan Phongthiproek The document discusses security issues related to mobile applications. It describes how mobile apps now offer many more services than basic phone calls and texts. This expanded functionality introduces new attack surfaces, including the client software on the device, the communication channel between the app and server, and server-side infrastructure. Some common vulnerabilities discussed are insecure data storage on the device, weaknesses in data encryption, SQL injection, and insecure transmission of sensitive data like credentials over the network. The document also provides examples of techniques for analyzing app security like reverse engineering the app code and using a proxy like Burp Suite to intercept network traffic.
Droidcon it-2014-marco-grassi-viaforensics
Droidcon it-2014-marco-grassi-viaforensicsviaForensics Marco Grassi gives a presentation on reverse engineering, penetration testing, and hardening Android apps. The presentation covers techniques for reverse engineering APKs, dealing with obfuscation, tamper detection, securing network communications, attacks on IPC, and more advanced topics like runtime manipulation. Real-world examples are provided to demonstrate vulnerabilities found in apps and how they can be exploited.
Android pen test basics
Android pen test basicsOWASPKerala The document covers topics related to Android penetration testing including the Android security model, software stack, content providers, and secure coding practices. The Android security model uses app isolation and each app runs in its own Dalvik Virtual Machine. Content providers manage access to structured app data and enable inter-process communication. Reverse engineering the APK file by extracting and decompiling it is demonstrated as part of the app security testing process. Common insecure practices like hardcoding sensitive data and lack of encryption are also discussed.
Drozer - An Android Application Security Tool
Drozer - An Android Application Security Tool nullowaspmumbai The document discusses the Android application security tool Drozer. It provides an overview of Drozer's capabilities including leaking content providers, attacking broadcast receivers, and abusing application permissions. The document then demonstrates Drozer's usage through several examples analyzing vulnerable Android applications and exploiting issues like content provider leakage, insecure broadcast receivers, and permission abuse.
Null Mumbai Meet_Android Reverse Engineering by Samrat Das
Null Mumbai Meet_Android Reverse Engineering by Samrat Dasnullowaspmumbai The document provides a comprehensive guide on reverse engineering and penetration testing for Android applications, covering fundamentals, tools, and methodologies involved in the analysis. It details the process of reverse engineering APK files, from extraction to packing, and outlines various security concerns and exploitation techniques for mobile applications. Additionally, it discusses common tools like Apktool, Drozer, and Java decompilers, as well as the importance of secure coding practices in Android development.
Pentesting Mobile Applications (Prashant Verma)
Pentesting Mobile Applications (Prashant Verma)ClubHack The document discusses penetration testing (pentesting) for mobile applications, covering both Android and iOS architectures, data storage, traffic capturing, and application reversal techniques. It highlights critical vulnerabilities and risks in mobile applications, including malware threats and insecure data handling practices. Best practices for securing mobile applications are also provided, such as encrypting data and avoiding hardcoding sensitive information.
BlackHat 2014 Briefings - Exploiting Fundamental Weaknesses in Botnet C&C Pan...
BlackHat 2014 Briefings - Exploiting Fundamental Weaknesses in Botnet C&C Pan...Aditya K Sood The document details a research presentation by Dr. Aditya K. Sood focused on exploiting vulnerabilities in command-and-control (C&C) panels used by botnets like Zeus and Citadel. It covers the architecture of C&C systems, methods for bypassing defenses, and the use of tools like Google dorks to locate exposed panels. Additionally, it emphasizes the importance of penetration testing and malware analysis in combating cybercrime and outlines future research directions in botnet detection.
Null 14 may_lesser_known_attacks_by_ninadsarang
Null 14 may_lesser_known_attacks_by_ninadsarangNinad Sarang The document summarizes several lesser-known web application attacks. It discusses mutation cross-site scripting (XSS), relative path overwrite XSS, zombie XSS, remote command execution, carriage return line feed (CRLF) attacks, and homograph attacks. For each attack, it provides examples of how the attack works and potential mitigations. The overall document serves as a guide to understanding and defending against these more obscure web application vulnerabilities.
Android Security & Penetration Testing
Android Security & Penetration TestingSubho Halder The document is a presentation by Subho Halder on Android security and penetration testing. It covers topics such as Android internals, the security model, best coding practices, and common malware techniques, highlighting vulnerabilities and exploitation methods using the Android Framework for Exploitation (AFE). Additionally, it emphasizes the importance of security measures and dynamic analysis to protect against malware threats.
Consulthink @ GDG Meets U - L'Aquila2014 - Codelab: Android Security -Il ke...
Consulthink @ GDG Meets U - L'Aquila2014 - Codelab: Android Security -Il ke...Consulthinkspa This document discusses Android key management and cryptography. It covers symmetric and asymmetric encryption algorithms like AES and RSA. It describes using the Android Keystore to securely store cryptographic keys and how PBKDF2 can be used to derive keys from passwords. It also demonstrates how apps can be reversed to extract hardcoded keys and discusses more secure alternatives like storing keys on a server.
Andriod Pentesting and Malware Analysis
Andriod Pentesting and Malware Analysisn|u - The Open Security Community The document provides an overview of Android OS basics, including its history and key components. It discusses understanding APKs, Android's security model, and includes a brief look at popular Android malware. It also covers reversing Android malware and pentesting the Android platform, with demos. The speaker will discuss Android OS, APKs, the security model, rooting, malware, and reversing tools.
iOS Application Security
iOS Application SecurityEgor Tolstoy This document provides an agenda for a training on iOS application penetration testing. It covers topics such as setting up an iOS pen testing environment, understanding the iOS filesystem and Objective-C runtime, runtime analysis and manipulation, insecure data storage, analyzing network traffic, jailbreak detection, secure coding guidelines, and automated testing. Tools discussed include class-dump-z, cycript, clutch, and gdb for analyzing iOS applications.
Pentesting iOS Apps - Runtime Analysis and Manipulation
Pentesting iOS Apps - Runtime Analysis and ManipulationAndreas Kurtz The document discusses runtime analysis and manipulation of iOS apps, highlighting techniques for dynamic analysis using Objective-C. It emphasizes the need for better tools to assess mobile applications and introduces the Snoop-it tool, which enhances security assessments by monitoring and manipulating app behavior. Furthermore, it addresses jailbreak detection and how its bypassing is crucial for robust security evaluations.
OWASP Melbourne - Introduction to iOS Application Penetration Testing
OWASP Melbourne - Introduction to iOS Application Penetration Testingeightbit This document provides an introduction to iOS application penetration testing. It discusses setting up an iOS penetration testing environment, including jailbreaking a test device and installing necessary software tools. It also provides an overview of iOS and Objective-C, covering key security features of iOS like sandboxing, ASLR, code signing, and data encryption. Topics to be covered include assessing data security, binary analysis, runtime manipulation, and evaluating authentication, session management, and transport security.
Fuzzing | Null OWASP Mumbai | 2016 June
Fuzzing | Null OWASP Mumbai | 2016 Junenullowaspmumbai The document outlines a training session on fuzzing, buffer overflow exploitation, and shellcode execution, focusing on the Minishare 1.4.1 application. It explains fuzzing as a technique for discovering exploitable software bugs, buffer overflows as vulnerabilities allowing memory overwrite, and the use of shellcode during exploitation. The session requires tools such as a VM platform, Windows XP, Kali Linux, and OllyDbg debugger.
Hacking android apps by srini0x00
Hacking android apps by srini0x00srini0x00 This document summarizes an agenda for a workshop on hacking and securing Android apps. The agenda includes topics like Android basics, the Android security model, building a "Hello World" app, reverse engineering apps, traffic analysis using Burp Suite and tcpdump, insecure data storage, attacking app authentication, exploiting app components, unintended data leakage, client-side injection, and securing Android apps. The workshop provides demonstrations for many of these topics and discusses penetration testing methodology for finding and exploiting vulnerabilities in Android apps.
Making Enterprise-Ready Plugins - Kaj Kandler JUC West 2015
Making Enterprise-Ready Plugins - Kaj Kandler JUC West 2015Black Duck by Synopsys The presentation discusses the development of enterprise-ready plugins by Black Duck Software for Jenkins, focusing on issues such as credential management and integration challenges. It highlights different plugins, including a security vulnerability report plugin and an update site manager for internal distribution of plugins. The emphasis is on the importance of continuous automation, governance in code, and ensuring security in open-source components.
Viewers also liked (20)
How to reverse engineer Android applications—using a popular word game as an ...
How to reverse engineer Android applications—using a popular word game as an ...Christoph Matthies The document outlines a comprehensive guide on reverse engineering Android applications to identify vulnerabilities, using a popular word game as a case study. It details the steps to obtain and decompile APK files, manipulate resources, debug code, and automate gameplay through methods like proxy traffic interception and dictionary extraction. The guide emphasizes techniques for modifying application behavior and unlocking premium features while discussing both smali and Java code decompilation processes.
Reverse Engineering Android Application
Reverse Engineering Android Applicationn|u - The Open Security Community This document discusses reverse engineering of Android applications. It provides an overview of Android, noting that it is an open source platform based on Linux and uses Java and the Dalvik Virtual Machine. It lists the tools needed for reverse engineering like JRE, Apktools, SignApk, Dex2jar, and JD-GUI. It outlines two approaches - using Apktool to convert the DEX to SMALI or using Dex2jar to convert to a JAR and then Java. The document concludes by mentioning a live demo will be provided.
Attacking and Defending Mobile Applications
Attacking and Defending Mobile ApplicationsJerod Brennen The document discusses mobile application security, focusing on both offensive and defensive strategies within the software development lifecycle (SDLC). It addresses different mobile platforms such as iOS, Android, and Windows, detailing security frameworks, analysis techniques, and defensive tools. Additionally, it emphasizes the importance of developer training and provides a variety of resources for secure app development and vulnerability testing.
Understanding the Dalvik bytecode with the Dedexer tool
Understanding the Dalvik bytecode with the Dedexer toolGabor Paller This document discusses the Dalvik virtual machine used in Android and how to decompile Dalvik bytecode using the Dedexer tool. It provides background on Android's use of Java and the Dalvik VM. Key points include: Dalvik uses its own bytecode format rather than Java bytecode and executes applications; the Dedexer tool can be used to disassemble DEX files back into Dalvik bytecode; and differences in Dalvik like its register-based rather than stack-based design are explained. Examples of Dalvik bytecode instructions and register usage are also provided.
Hacking Mobile Apps
Hacking Mobile AppsSophos Benelux The document presents insights from a 2016 presentation by Erwin Geirnaert on mobile app security, focusing on various vulnerabilities and risks associated with Android, iOS, and Windows apps. It discusses the OWASP Top 10 mobile risks, the significance of weak server-side controls, and the impact of insecure data storage and transport layer protection. Additionally, the document highlights real-world examples of security flaws and emphasizes the importance of secure coding practices and access controls in mobile applications.
Mobile Hacking
Mobile HackingNovizul Evendi The document discusses mobile hacking and identification techniques for encrypted data. It covers mobile technology threats like Bluetooth, WiFi, cracked apps, and data storage. It then describes mobile hacking tools like PWN PAD, PWN Phone, and Linux chroot that can be used for wireless attacks, networking, and Android hacking. The conclusion recommends using firewalls, antivirus software, keeping apps up to date, avoiding cracked apps, and using security locks to help defend against these mobile threats.
Reverse engineering android apps
Reverse engineering android appsPranay Airan This document discusses ways to secure Android applications against threats such as unauthorized code access and malware. It covers tools for code protection, including ProGuard and DexGuard, as well as methods for disassembling apps and implementing API protections. The author emphasizes that while various techniques can enhance security, no method is entirely foolproof.
Practice of Android Reverse Engineering
Practice of Android Reverse EngineeringNational Cheng Kung University The document focuses on the practice of Android reverse engineering, outlining the development flow of Android applications and the process of APK installation. It provides insights into code injection, data protection, and techniques for disassembling and analyzing Android APK files using tools like APKTool and dex2jar. Additionally, it includes real-world tasks aimed at enhancing practical understanding for beginners in reverse engineering Android applications.
Dancing with dalvik
Dancing with dalvikThomas Richards The document provides an overview of Dalvik, the virtual machine used in Android, detailing its architecture, optimizations, and bytecode structure. It illustrates the process of disassembling and rebuilding Android applications, including the tools and techniques involved, as well as examples of modifying application code to remove ads. Additionally, it examines case studies demonstrating practical applications of these techniques within Android apps.
Understanding the Dalvik Virtual Machine
Understanding the Dalvik Virtual MachineNational Cheng Kung University The document provides an overview of the Dalvik Virtual Machine (VM), its architecture, and its functionality as a software implementation executing programs similarly to a physical machine. It details the setup for building the Dalvik VM from source using CyanogenMod on specific hardware, and explains the differences between Java and Dalvik bytecode, emphasizing Dalvik's register-based design. Additionally, the presentation covers VM instruction execution and optimization techniques for efficient dispatching of operations.
Hacking Tutorial for Apps
Hacking Tutorial for AppsGrant Eaton This document provides a guide for hacking apps through various methods ranging from basic to advanced. It begins by explaining how to find and install pre-made hacks from online sources. Then it discusses basic text editing of files like .plist and .xml to modify values like scores or currencies. More advanced methods covered include Mobile Substrate hacking, decrypting encrypted files, and hex editing files using a hex editor. Precautions are given that hacking should only be done for educational purposes and not for illegal acts.
CyberLab CCEH Session -13 Hacking Web Applications
CyberLab CCEH Session -13 Hacking Web ApplicationsCyberLab This document appears to be the title slide for a presentation on hacking web applications. The main title is "Hacking Web Applications" and the subtitle provides the website "www.CyberLabZone.com" where additional information can be found. The document also includes session information for session 13.
FIDO, PKI & beyond: Where Authentication Meets Identification
FIDO, PKI & beyond: Where Authentication Meets IdentificationFIDO Alliance The document discusses the establishment of a trusted ecosystem for FIDO (Fast Identity Online) authentication, highlighting the integration of asymmetric cryptography and mechanisms similar to conventional PKI (Public Key Infrastructure) systems. It emphasizes the importance of trusted protocols, key storage, personalization, and the ecosystem itself in building trust, and proposes a layered approach to authentication and identification. Additionally, it suggests that FIDO can complement existing PKI methods, allowing flexibility in both identification and authentication processes.
Web Application Hacking
Web Application HackingSensePost The document discusses vulnerabilities in web applications and the importance of securing them, highlighting various attack methods such as directory traversal, SQL injection, and cross-site scripting. It emphasizes the necessity of proper input sanitization and the complexities involved in web application testing and automation. SensePost, the company mentioned, focuses on information security and aims to improve web application security practices.
FIDO Webinar – A New Model for Online Authentication: Implications for Policy...
FIDO Webinar – A New Model for Online Authentication: Implications for Policy...FIDO Alliance The FIDO Alliance outlines a new model for online authentication, emphasizing the need for enhanced security and privacy in government services through strong authentication methods like public key cryptography and biometrics. The document highlights the importance of evolving policies to adapt to technological advancements and the necessity for governments to recognize and support modern authentication standards. Additionally, it stresses FIDO's commitment to user privacy by ensuring data remains secure and under user control, while promoting interoperability and usability.
Hacking your Droid (Aditya Gupta)
Hacking your Droid (Aditya Gupta)ClubHack This document provides an overview of malware on Android systems. It discusses the Android architecture and security model, how to analyze Android application packages (APKs), and techniques for reverse engineering and creating Android malware. Specific malware examples like Trojan-SMS.FakePlayer.a and Geinimi are described. The document also covers tools for mobile application penetration testing and discusses both legal and illegal ways that Android malware can generate money.
Smali语法
Smali语法xiaoshan8743 1. Dalvik bytecode represents types as either primitive types represented by single letters (e.g. I for int) or reference types in the form of Lpackage/name/ObjectName;.
2. Methods are specified in a verbose form including the containing type, name, parameter types, and return type (e.g. Lpackage/name/ObjectName;->MethodName(III)Z).
3. Fields are also specified verbosely including the containing type, name, and field type (e.g. Lpackage/name/ObjectName;->FieldName:Ljava/lang/String;).
RoR Workshop - Web applications hacking - Ruby on Rails example
RoR Workshop - Web applications hacking - Ruby on Rails exampleRailwaymen The document discusses web application security, specifically focusing on Ruby on Rails vulnerabilities like SQL injection and XSS attacks, along with best practices for prevention. It emphasizes the importance of sanitizing user inputs, securing APIs, and obtaining code reviews to mitigate risks. Furthermore, it outlines common pitfalls related to CSRF attacks and sensitive data exposure, providing strategies to enhance application security.
Hacking ingress
Hacking ingressEran Goldstein The document discusses reverse engineering the Android application Ingress in order to modify its functionality. It describes extracting the application code from the APK file. The analysis aims to disable detection of mock locations, allowing fake GPS signals to be used. It also aims to remove the "Scanner Disabled" message that appears when using fake GPS. The analysis identifies specific code sections to modify to achieve these goals.
Toward Reverse Engineering of VBA Based Excel Spreadsheets Applications
Toward Reverse Engineering of VBA Based Excel Spreadsheets ApplicationsREvERSE University of Naples Federico II The document outlines a proposed approach for reverse engineering VBA-based Excel spreadsheet applications to enhance comprehension and maintenance. It discusses the widespread use of spreadsheets across various domains, the challenges posed by their complexity, and introduces a heuristic-based method for reconstructing data models and understanding user interfaces. The authors also present a tool called 'Exact' designed to extract and visualize the structure and dependencies of spreadsheet applications.
Toward Reverse Engineering of VBA Based Excel Spreadsheets Applications
Toward Reverse Engineering of VBA Based Excel Spreadsheets ApplicationsREvERSE University of Naples Federico II
Similar to Learning by hacking - android application hacking tutorial (20)
hashdays 2011: Tobias Ospelt - Reversing Android Apps - Hacking and cracking ...
hashdays 2011: Tobias Ospelt - Reversing Android Apps - Hacking and cracking ...Area41 The document discusses the vulnerabilities and security issues related to Android app development, primarily focusing on reverse engineering techniques for pentesters. It highlights past issues with lock screen circumvention, malware presence in the Google Market, and the ease of decompiling Android applications. Additionally, it provides an overview of techniques for downloading, disassembling, and analyzing Android apps, as well as recommendations for improving security practices.
2013 Toorcon San Diego Building Custom Android Malware for Penetration Testing
2013 Toorcon San Diego Building Custom Android Malware for Penetration TestingStephan Chenette This presentation by Stephan Chenette outlines methodologies for developing custom Android malware intended for penetration testing of security controls. It covers the Android operating system, malware techniques, and defensive technologies, while emphasizing the importance of understanding in-the-wild malware to improve security measures. The document also discusses categories of Android malware, infection vectors, and provides a systematic approach for testing and bypassing security controls.
ethical hacking-mobile hacking methods.ppt
ethical hacking-mobile hacking methods.pptJayaprasanna4 Mobile hacking poses significant threats, particularly for the dominant Android OS, which constitutes 84.1% of the global market. Given its widespread use, Android is a prime target for hackers employing various methods such as social engineering and exploitation of vulnerabilities. To mitigate risks, users are advised to keep their OS and applications updated, avoid untrusted installations, and practice general security precautions.
Who Needs Thumbs? Reverse Engineering Scramble with Friends v1.1
Who Needs Thumbs? Reverse Engineering Scramble with Friends v1.1Apkudo This document discusses reverse engineering an Android application (Scramble With Friends) through APK hacking. It provides a step-by-step approach to extract resources from an APK, inject code to transmit resources to another application, and repackage the modified APK. The key steps are: 1) Disassembling the APK using baksmali, 2) Isolating target resources like word lists, 3) Patching the APK to transmit resources to Romain Guy's ViewServer app, 4) Reassembling the patched APK using smali. The goal is to extract application content programmatically using these techniques.
Decompiling Android
Decompiling AndroidGodfrey Nolan The document discusses decompiling Android applications. It defines decompilers as tools that reverse engineer applications into source code. Specifically, Java and .NET applications are at high risk of being decompiled due to the design of the JVM and CLR. The document explains that decompiling Android applications is easy because the code is easily accessible in APK files, few developers use obfuscation, and dex files have a simpler structure than native code. It provides recommendations for protecting code such as using ProGuard, DashO, native code, and avoiding sensitive strings and keys in APKs.
LinkedIn - Disassembling Dalvik Bytecode
LinkedIn - Disassembling Dalvik BytecodeAlain Leon The document discusses disassembling Dalvik bytecode on Android. It begins by providing background on Android, Dalvik VM, APK files, DEX files, and JIT compilation. It then discusses ways to hack at different levels: using macros to automate games, intercepting REST traffic, analyzing APK/DEX files by decompiling them and modifying bytecode, analyzing and modifying shared object libraries, and disassembling machine code. The key steps outlined are decompiling DEX to Smali bytecode, applying changes, recompiling to an APK, installing on a device, and analyzing shared object libraries by disassembling to machine code.
Droidcon Greece '15 - Reverse Engineering in Android: Countermeasures and Tools
Droidcon Greece '15 - Reverse Engineering in Android: Countermeasures and ToolsDario Incalza The document outlines strategies and tools for reverse engineering Android applications, emphasizing the motivations behind reverse engineering, such as understanding malware and improving security. It also discusses the anatomy of Android apps, the building process, and various countermeasures like tamper detection, dynamic bytecode loading, and obfuscation to protect applications. Key reverse engineering tools and use cases, such as analyzing the Anserverbot trojan, are highlighted to demonstrate practical applications of these techniques.
Introduction to Android Development and Security
Introduction to Android Development and SecurityKelwin Yang This document provides an introduction to Android development and security. It begins with a brief history of Android and overview of its architecture. It then discusses the Android development environment and process, including key tools and frameworks. It also outlines Android security features like application sandboxing, permissions, and encryption. Finally, it introduces a series of Android security labs that demonstrate exploits like parameter manipulation, insecure storage, and memory attacks. The goal is to provide hands-on examples of common Android vulnerabilities.
Android village @nullcon 2012
Android village @nullcon 2012 hakersinfo This document provides an overview of a two-day training on Android hacking and security. Day 1 covers Android architecture basics, development, and penetration testing fundamentals. Topics include the operating system, file system, security model, application components, and setting up a penetration testing lab. Day 2 covers more advanced topics like malware analysis, common exploits, custom ROM development, and forensics. The document outlines the agenda and key learning points for each topic.
Android tutorial
Android tutorialAvinash Nandakumar This document provides an overview of the tools and steps needed to develop Android applications in Eclipse. It describes how to install the Android SDK and set up an Android project in Eclipse. It also explains key Android concepts like activities, services, and the manifest file. The document demonstrates how to add a MapView to an app and get an API key for Google Maps. It provides guidance on running apps in the emulator or on a device, as well as debugging techniques.
Android-Tutorial.ppt
Android-Tutorial.pptsiddharthsingh496426 This document provides an overview of setting up and developing Android applications using Eclipse. It describes downloading and installing the necessary tools like the Android SDK, Eclipse plugin, and creating an Android virtual device. It explains creating an Android project in Eclipse and the typical project components. The document also covers key Android concepts like activities, services, and the manifest file. It includes an example of adding a map to an app using the Google Maps API.
Android
AndroidJesus_Aguirre This document provides an overview of developing Android applications. It discusses installing the necessary tools like the Android SDK and Eclipse plugin. It describes creating an Android project in Eclipse, including specifying the SDK location. It explains app components like activities and services. It provides an example of adding maps functionality by configuring the manifest file and getting an API key. The document is a tutorial that introduces major Android development concepts in a brief and high-level manner.
Null Dubai Humla_Romansh_Yadav_Android_app_pentesting
Null Dubai Humla_Romansh_Yadav_Android_app_pentestingRomansh Yadav The document provides a comprehensive overview of Android application penetration testing, discussing the setup of testing environments, reverse engineering, and runtime manipulation techniques. Key concepts include the Android permission model, common security issues, and various tools for static and dynamic analysis. It emphasizes the importance of protecting applications from vulnerabilities such as insecure data storage, code obfuscation, and ensuring secure network connections.
Android tutorial
Android tutorialTechacademy Software This document provides an overview of key concepts for developing Android applications. It discusses installing the necessary tools like Eclipse, the Android SDK, and configuring the ADT plugin. It also covers creating Android projects, using layouts and resources, adding activities and services to the manifest, and debugging apps. The document demonstrates how to display maps using the Google Maps API, including getting an API key and adding the MapView to an app's layout.
Android tutorial
Android tutorialEd Zel This document provides an overview of the steps to create an Android application using Eclipse that incorporates Google Maps. It describes downloading the necessary tools like the Android SDK and Eclipse plugin. It explains how to set up a project, configure the manifest file to include the maps library and internet permission. It also covers getting an API key for maps by obtaining the fingerprint of the debug certificate. The document then gives examples of basic maps functionality like adding a MapView to a layout.
Android tutorial
Android tutorialkatayoon_bz This document provides an overview of key concepts for developing Android applications. It discusses installing the necessary tools like Eclipse, the Android SDK, and configuring the ADT plugin. It also covers creating Android projects, using layouts and resources, adding activities and services to the manifest, and debugging apps. The document demonstrates how to display maps using the Google Maps API, including getting an API key and adding the MapView to layouts.
Android tutorial
Android tutorialKeshav Chauhan This document is an introductory tutorial for Android development, covering essential components like the Android SDK, project creation, activity management, and service life cycle. It provides guidance on using Eclipse as an IDE, configuring Google Maps API, and debugging techniques using Android Debug Bridge (ADB). Additional resources and references for further learning are also included.
Introduction to mobile reversing
Introduction to mobile reversingjduart This document provides an introduction to mobile application reversing. It discusses reversing apps for Windows Mobile, Android, and iPhone operating systems. For Windows Mobile, it analyzes a Spanish banking app called BBVA. For Android, it analyzes a US banking app called Wells Fargo. For iPhone, it analyzes a Korean banking app called HanaBank. The document discusses the file formats, architectures, languages, and tools used for reversing apps on each mobile platform.
Introduction to mobile reversing
Introduction to mobile reversingzynamics GmbH This document provides an introduction to mobile application reversing. It discusses reversing applications on Windows Mobile, Android, and iPhone platforms. For Windows Mobile, it analyzes a Spanish banking app called BBVA. For Android, it analyzes a US banking app called Wells Fargo. For iPhone, it analyzes a Korean banking app called HanaBank. The document discusses the file formats, architectures, languages, and tools used for reversing apps on each mobile platform.
Android tutorial
Android tutorialAlberto Jr Gaudicos This document provides an overview of key concepts for developing Android applications. It discusses tools like Eclipse, the Android SDK, and Android Virtual Devices. It also covers important app components like activities, services, and the manifest file. The document demonstrates how to set up a basic maps application using the Google Maps API, including getting an API key. It recommends several Android developer resources and forums for additional information.
Recently uploaded (20)
362 Alec Data Center Solutions-Slysium Data Center-AUH-Glands & Lugs, Simplex...
362 Alec Data Center Solutions-Slysium Data Center-AUH-Glands & Lugs, Simplex...djiceramil submittal
Machine Learning - Classification Algorithms
Machine Learning - Classification Algorithmsresming1 This covers traditional machine learning algorithms for classification. It includes Support vector machines, decision trees, Naive Bayes classifier , neural networks, etc.
It also discusses about model evaluation and selection. It discusses ID3 and C4.5 algorithms. It also describes k-nearest neighbor classifer.
Impurities of Water and their Significance.pptx
Impurities of Water and their Significance.pptxdhanashree78 Impart Taste, Odour, Colour, and Turbidity to water.
Presence of organic matter or industrial wastes or microorganisms (algae) imparts taste and odour to water.
Presence of suspended and colloidal matter imparts turbidity to water.
Structural Design for Residential-to-Restaurant Conversion
Structural Design for Residential-to-Restaurant ConversionDanielRoman285499 Overview of a 4-month project working on designing the structural components of a residential building to meet new code
IntroSlides-June-GDG-Cloud-Munich community [email protected]
IntroSlides-June-GDG-Cloud-Munich community [email protected]Luiz Carneiro Introduction slides for starting the June GDG Cloud Munich community gathering in Munich, Germany.
最新版美国圣莫尼卡学院毕业证(SMC毕业证书)原版定制
最新版美国圣莫尼卡学院毕业证(SMC毕业证书)原版定制Taqyea 鉴于此,定制圣莫尼卡学院学位证书提升履历【q薇1954292140】原版高仿圣莫尼卡学院毕业证(SMC毕业证书)可先看成品样本【q薇1954292140】帮您解决在美国圣莫尼卡学院未毕业难题,美国毕业证购买,美国文凭购买,【q微1954292140】美国文凭购买,美国文凭定制,美国文凭补办。专业在线定制美国大学文凭,定做美国本科文凭,【q微1954292140】复制美国Santa Monica College completion letter。在线快速补办美国本科毕业证、硕士文凭证书,购买美国学位证、圣莫尼卡学院Offer,美国大学文凭在线购买。
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
【复刻一套圣莫尼卡学院毕业证成绩单信封等材料最强攻略,Buy Santa Monica College Transcripts】
购买日韩成绩单、英国大学成绩单、美国大学成绩单、澳洲大学成绩单、加拿大大学成绩单(q微1954292140)新加坡大学成绩单、新西兰大学成绩单、爱尔兰成绩单、西班牙成绩单、德国成绩单。成绩单的意义主要体现在证明学习能力、评估学术背景、展示综合素质、提高录取率,以及是作为留信认证申请材料的一部分。
圣莫尼卡学院成绩单能够体现您的的学习能力,包括圣莫尼卡学院课程成绩、专业能力、研究能力。(q微1954292140)具体来说,成绩报告单通常包含学生的学习技能与习惯、各科成绩以及老师评语等部分,因此,成绩单不仅是学生学术能力的证明,也是评估学生是否适合某个教育项目的重要依据!
WIRELESS COMMUNICATION SECURITY AND IT’S PROTECTION METHODS
WIRELESS COMMUNICATION SECURITY AND IT’S PROTECTION METHODSsamueljackson3773 In this paper, the author discusses the concerns of using various wireless communications and how to use
them safely. The author also discusses the future of the wireless industry, wireless communication
security, protection methods, and techniques that could help organizations establish a secure wireless
connection with their employees. The author also discusses other essential factors to learn and note when
manufacturing, selling, or using wireless networks and wireless communication systems.
OCS Group SG - HPHT Well Design and Operation - SN.pdf
OCS Group SG - HPHT Well Design and Operation - SN.pdfMuanisa Waras This course is delivered as a scenario-based course to
provide knowledge of High Pressure and High-Temperature (HPHT) well design, drilling and completion operations. The course is specifically designed to provide an
understanding of the challenges associated with the design
and construction of HPHT wells. The course guides the
participants to work through the various well design
aspects starting from a geological well proposal with an
estimated formation pressure and temperature profile.
Working with real well data allows the participants to learn
not only theory, technicalities and practicalities of drilling
and completing HPHT wells but it also ensures that participants gain real experience in understanding the HPHT issues.
NALCO Green Anode Plant,Compositions of CPC,Pitch
NALCO Green Anode Plant,Compositions of CPC,Pitcharpitprachi123 Its a pdf about all the process involving in the green anode production
社内勉強会資料_Chain of Thought .
社内勉強会資料_Chain of Thought .NABLAS株式会社 本資料「To CoT or not to CoT?」では、大規模言語モデルにおけるChain of Thought(CoT)プロンプトの効果について詳しく解説しています。
CoTはあらゆるタスクに効く万能な手法ではなく、特に数学的・論理的・アルゴリズム的な推論を伴う課題で高い効果を発揮することが実験から示されています。
一方で、常識や一般知識を問う問題に対しては効果が限定的であることも明らかになりました。
複雑な問題を段階的に分解・実行する「計画と実行」のプロセスにおいて、CoTの強みが活かされる点も注目ポイントです。
This presentation explores when Chain of Thought (CoT) prompting is truly effective in large language models.
The findings show that CoT significantly improves performance on tasks involving mathematical or logical reasoning, while its impact is limited on general knowledge or commonsense tasks.
20CE601- DESIGN OF STEEL STRUCTURES ,INTRODUCTION AND ALLOWABLE STRESS DESIGN
20CE601- DESIGN OF STEEL STRUCTURES ,INTRODUCTION AND ALLOWABLE STRESS DESIGNgowthamvicky1 • Understand concepts of limit state and working stress method of design of structural steel members and various types of connections.
• Determine net area and effective sections in tension members, tension splices, lug angles and gussets.
• Execute design of compression members as per IS codal practice.
• Analyze concepts of design of flexural members.
• Design structural systems such as roof trusses, gantry girders as per provisions of IS 800 – 2007 of practice for limit state method.
OUTCOMES:
On successful completion of this course, the students will be able to,
• Analyze different types of bolted and welded connections.
• Develop skills to design tension members, splices, lug angles and gussets.
• Elaborate IS Code design practice of various compression members.
• Design laterally supported and unsupported beams, built-up beams, plate girders and stiffeners.
• Acquire knowledge about components of industrial structures, Gantry girders and roof trusses.
TEXT BOOKS:
1. Bhavikatti S S, “Design of Steel Structures”, By Limit State Method as per IS: 800 – 2007, IK International Publishing House Pvt. Ltd., 2019.
2. Subramanian N, “Design of Steel Structures”, Oxford University Press 2011.
REFERENCE BOOKS:
1. Duggal S K, “Limit State Design of Steel Structures”, Tata, McGraw Hill Education Pvt. Ltd., New Delhi, 2017.
2. Shiyekar M R, “Limit State Design in Structural Steel”, PHI Learning Private Limited, New Delhi, 2013.
3. IS: 800 – 2007, IS: 800 – 1984, General Construction in Steel – Code of Practice, BIS, New Delhi.
Structural steel types – Mechanical Properties of structural steel- Indian structural steel products- Steps involved in the Deign Process -Steel Structural systems and their Elements- -Type of Loads on Structures and Load combinations- Code of practices, Loading standards and Specifications - Concept of Allowable Stress Method, and Limit State Design Methods for Steel structures-Relative advantages and Limitations-Strengths and Serviceability Limit states.
Allowable stresses as per IS 800 section 11 -Concepts of Allowable stress design for bending and Shear –Check for Elastic deflection-Calculation of moment carrying capacity –Design of Laterally supported Solid Hot Rolled section beams-Allowable stress deign of Angle Tension and Compression Members and estimation of axial load carrying capacity.
Type of Fasteners- Bolts Pins and welds- Types of simple bolted and welded connections Relative advantages and Limitations-Modes of failure-the concept of Shear lag-efficiency of joints- Axially loaded bolted connections for Plates and Angle Members using bearing type bolts –Prying forces and Hanger connection– Design of Slip critical connections with High strength Friction Grip bolts.- Design of joints for combined shear and Tension- Eccentrically Loaded Bolted Bracket Connections- Welds-symbols and specifications- Effective area of welds-Fillet and but Welded connections-Axially Loaded connections for Plate and angle truss members and
Microwatt: Open Tiny Core, Big Possibilities
Microwatt: Open Tiny Core, Big PossibilitiesIBM Microwatt is a lightweight, open-source core based on the OpenPOWER ISA.
It’s designed for FPGAs and easy experimentation in chip design.
Ideal for education, prototyping, and custom silicon development.
Fully open, it empowers developers to learn, modify, and innovate.
Cadastral Maps
Cadastral MapsGoogle Preparation of cadastral maps based by Engineer Dungo Tizazu from Dire Dawa University
Rigor, ethics, wellbeing and resilience in the ICT doctoral journey
Rigor, ethics, wellbeing and resilience in the ICT doctoral journeyYannis The doctoral thesis trajectory has been often characterized as a “long and windy road” or a journey to “Ithaka”, suggesting the promises and challenges of this journey of initiation to research. The doctoral candidates need to complete such journey (i) preserving and even enhancing their wellbeing, (ii) overcoming the many challenges through resilience, while keeping (iii) high standards of ethics and (iv) scientific rigor. This talk will provide a personal account of lessons learnt and recommendations from a senior researcher over his 30+ years of doctoral supervision and care for doctoral students. Specific attention will be paid on the special features of the (i) interdisciplinary doctoral research that involves Information and Communications Technologies (ICT) and other scientific traditions, and (ii) the challenges faced in the complex technological and research landscape dominated by Artificial Intelligence.
Modern multi-proposer consensus implementations
Modern multi-proposer consensus implementationsFrançois Garillot Multi-proposer consensus protocols let multiple validators propose blocks in parallel, breaking the single-leader throughput bottleneck of classic designs. Yet the modern multi-proposer consensus implementation has grown a lot since HotStuff. THisworkshop will explore the implementation details of recent advances – DAG-based approaches like Narwhal and Sui’s Mysticeti – and reveal how implementation details translate to real-world performance gains. We focus on the nitty-gritty: how network communication patterns and data handling affect throughput and latency. New techniques such as Turbine-like block propagation (inspired by Solana’s erasure-coded broadcast) and lazy push gossip broadcasting dramatically cut communication overhead. These optimizations aren’t just theoretical – they enable modern blockchains to process over 100,000 transactions per second with finality in mere milliseconds redefining what is possible in decentralized systems.
Montreal Dreamin' 25 - Introduction to the MuleSoft AI Chain (MAC) Project
Montreal Dreamin' 25 - Introduction to the MuleSoft AI Chain (MAC) ProjectAlexandra N. Martinez Montreal Dreamin' 25 - Introduction to the MuleSoft AI Chain (MAC) Project
Learning by hacking - android application hacking tutorial
- 1. Learning by Hacking Android application hacking tutorial Landice Fu! [email protected]
- 2. About me Landice Fu Android system developer at ASUS! ! FOSS user and promoter! ! Android app hacker! ! Ruby / JAVA / C / Qt
- 3. Android application hacking tutorial Background Knowledge ❖ Java! ❖ Android Application Design! ❖ Using Android Logcat with Android Debug Bridge (ADB)! ❖ Assembly syntax
- 4. My proclamation about this presentation ❖ The application binary and decompiled code I use in this presentation are only for teaching and learning! ! ❖ After the presentation, I would not provide or use them in ANY circumstances and I will immediately delete them
- 5. You must be really bad! ❖ Pirate! ❖ Stealing accounts and data! ❖ Mess up the device! ❖ BitCoin mining using others’ device
- 7. What about… ❖ UI Localization! ❖ Ad. removal! ❖ Resource extraction! ❖ Wow, that’s cool! How did you do that?! ❖ Fix the bug yourself! ❖ Get to know your enemy and how to better protect your product! ❖ Add some features to it Are you kidding?
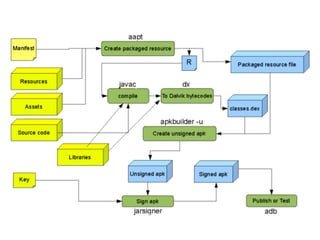
- 9. APKTOOL ❖ https://code.google.com/p/android-apktool/! ❖ Command line tool for disassembling/assembling APK! ❖ Decompile APK apktool d file_name.apk! ❖ Rebuild APK apktool b folder_name
- 10. xxxxx!Free Localization Demo ❖ You don’t even need to know how to write android app or JAVA! ! ❖ Android multi-language support mechanism [1][2]! ! [1] http://developer.android.com/training/basics/supporting-devices/languages.html! ! [2] http://jjnnykimo.pixnet.net/blog/post/37831205-android%E5%A4%9A%E5%9C%8B%E8%AA %9E%E8%A8%80%E8%B3%87%E6%96%99%E5%A4%BE%E5%91%BD%E5%90%8D %E6%96%B9%E5%BC%8F
- 11. Localization Demo ❖ Get the original APK! ❖ AndroidAssistant (backup)! ❖ /data/app/ (root access)! ❖ Copy values folder to values-zh-rTW! ❖ Localize the content of values-zh-rTW/strings.xml! ❖ Build and sign the APK
- 12. Smali/Baksmali ❖ Assembler/disassembler for the dex format used by Dalvik! ❖ The syntax is loosely based on Jasmin’s dedexer's syntax! ❖ Supports the full functionality of the dex format! ❖ Annotations (@Override, @SuppressWarnings …)! ❖ Debug Information! ❖ Line Information! ❖ Etc.! ❖ https://code.google.com/p/smali/
- 13. Dalvik opcodes ❖ Write a simple application and decompile it and see how it is turned into Dalvik operations! ❖ http://pallergabor.uw.hu/androidblog/dalvik_opcodes.html! ❖ http://www.netmite.com/android/mydroid/dalvik/docs/ dalvik-bytecode.html
- 14. Types in smali Smali JAVA Primitive Type V void - can only be used for return types Z boolean B byte S short C char I int J long (64 bits) F float D double Class Object Lcom/lansion/myapp/xxxparser;
- 15. Framework Resource ❖ Some code and resources that are built into the Android system on your device! ❖ /system/framework/framework-res.apk! ❖ Installing framework resource for apktool apktool if framework-res.apk
- 16. Integrated Development Hacking Environment
- 17. Virtuous Ten Studio (VTS) ❖ Integrated Reverse Engineering Environment for APK! ❖ Built-in ApkTool, ADB, Zipalign, Sign, dex2jar…! ❖ Support for APKs and framework JARs! ❖ Text editing of smali, xml files with syntax highlighting, live checking and code folding! ❖ M10 file editing (HTC Sense)! ❖ Unpack/ repack boot images! ❖ Generate JAVA sources using multiple libraries! ❖ http://virtuous-ten-studio.com/
- 18. Demo: Remove the ad. from xxxxx!free ❖ What you need! ❖ Know the API of libraries! ❖ Know the API of Android! ❖ Luck! ❖ Patience! ❖ Tip1 : When you don’t know how to do something in smali, just write it in JAVA and decompile it
- 19. Source Obfuscation ❖ Make it really difficult for human to understand and time consuming to hack! ❖ Make the names of variables, methods, classes and packages meaningless! ❖ Remove debug information! ❖ Complicated call flow! ❖ Redundant source code! ❖ …………..! ❖ Penalty of obfuscation Stop laughing…! This is you!!
- 22. Build your own crack tool ❖ Provide static functions! ❖ Add logcat logs with variable states! ❖ Add stack trace dump! ❖ Do the complicated tricks out side of the original program (much easier in JAVA)
- 23. A more difficult task - ??????? ❖ UI is always the key to find the starting point! ❖ Resource ID (name) turns into constant value map! ❖ Insert the snippets decompiled from your crack tool! ❖ Most of the local license checking is not too complicated! ❖ Altering one of the boolean-returning function does the trick in a majority of cases
- 25. Still a piece of cake ❖ Knowing the system API is very helpful! ❖ More complicated check might involve getting IMEI, MAC… from your device! ❖ You still can trick the application by replacing the system API call to your own function
- 26. What I did to Age of Empires on Android ❖ Modify the menu bar to provide control interface! ❖ TCP server to communication with another Android device with the same hacked APK! ❖ Add a robot state machine to get money, resource… from the other account without effort.
- 27. Protect your work ❖ Design with NDK! ❖ Using framework like cocos2d (generates native library)! ❖ Don’t just use one method for checking! ❖ Strong obfuscation! ❖ Provide the content using web! ❖ Find a way to mess up the decompiler
- 28. What you might be interested in ❖ You can use the decompiled code from other apps in your application! ❖ Embed a broadcast receiver to interact with external application
- 29. Thanks for your attention
