Linux Binary Exploitation - Heap Exploitation
- 1. Linux binary Exploitation Heap exploitation - Glibc [email protected]
- 2. Outline • Glibc memory allocator Overview • Use After Free • Heap Overflow • Appendix - Detection in Glibc
- 3. Outline • Glibc memory allocator Overview • Use After Free • Heap Overflow • Appendix - Detection in Glibc
- 4. Memory allocator • dlmalloc – General purpose allocator • ptmalloc2 – glibc • jemalloc – Firefox • tcmalloc – chrome • …..
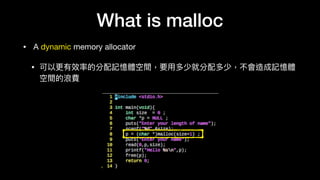
- 5. What is malloc • A dynamic memory allocator • 可以更更有效率的分配記憶體空間,要⽤用多少就分配多少,不會造成記憶體 空間的浪費
- 6. The workflow of malloc • 第⼀一次執⾏行行 malloc malloc mmap sys_mmap brk sys_brk size >= 128 KB size < 128 KB trap to kernel
- 7. The workflow of malloc • 無論⼀一開始 malloc 多少空間 < 128 KB 都會 kernel 都會給 132 KB 的 heap segment (rw) 這個部分稱為 main arena kernel space CODE VMA DATA VMA HEAP STACK kernel space CODE VMA DATA VMA STACK brk start_brk 132 KB brk
- 8. The workflow of malloc • 第⼆二次執⾏行行 malloc 時,只要分配出去的總記憶體空間⼤大⼩小不超過 128 KB ,則不會再執⾏行行 system call 跟系統要空間,超過⼤大⼩小才會⽤用 brk 來來跟 kernel 要記憶體空間 • 即使將所有 main arena 所分配出去的記憶體 free 完,也不會立即還給 kernel • 這時的記憶體空間將由 glibc 來來管理理 • 本投影片如未特別註明都以 64 位元電腦 glibc-2.23 為主,換到 32 位元則 ⼤大多數的欄欄位⼤大⼩小都須除⼆二
- 9. Mechanism of glibc malloc • Chunk • glibc 在實作記憶體管理理時的 data structure • 在 malloc 時所分配出去的空間即為⼀一個 chunk (最⼩小為 SIZE_T*4) • SIZE_T = unsigned long int • chunk header (prev_size + size) + user data • 如果該 chunk 被 free 則會將 chunk 加入名為 bin 的 linked list • 分為 • Allocated chunk • Free chunk • Top chunk
- 10. Mechanism of glibc malloc • heap data chunk header chunk header data chunk header top chunk chunk malloc return value
- 11. Mechanism of glibc malloc • Allocated chunk • prev_size • 如果上⼀一塊的 chunk 是 free 的狀狀態,則該欄欄位則會存有上⼀一塊 chunk 的 size (包括 header) • 這裏指的上⼀一塊是在連續記憶體中的上⼀一塊 • size • 該 chunk 的⼤大⼩小,其中有三個 flag • PREV_INUSE (bit 0) : 上⼀一塊 chunk 是否不是 freed • IS_MMAPPED (bit 1) : 該 chunk 是不是由 mmap 所分配的 • NON_MAIN_ARENA (bit 2):是否不屬於 main arena
- 12. Mechanism of glibc malloc • Allocated chunk DATA prev_size size N M P P:PREV_INUSED M:IS_MMAPPED N:NON_MAIN_ARENA
- 13. Mechanism of glibc malloc • freed chunk • prev_size • size • fd : point to next chunk ( 包含 bin ) • 這邊指的是 linked list 中的 next chunk,⽽而非連續記憶體中的 chunk • bk : point to last chunk ( 包含 bin ) • 這邊指的是 linked list 中的 last chunk,⽽而非連續記憶體中的 chunk • fd_nextsize : point to next large chunk(不包含 bin) • bk_nextsize : point to last large chunk (不包含 bin)
- 14. Mechanism of glibc malloc • freed chunk DATA prev_size size N M P P:PREV_INUSED M:IS_MMAPPED N:NON_MAIN_ARENA fd bk
- 15. Mechanism of glibc malloc • top chunk • 第⼀一次 malloc 時就會將 heap 切成兩兩塊 chunk,第⼀一塊 chunk 就是分配出 去的 chunk ,剩下的空間視為 top chunk,之後要是分配空間不⾜足時將會由 top chunk 切出去 • prev_size • size • 顯⽰示 top chunk 還剩下多少空間
- 16. Mechanism of glibc malloc • bin • linked list • 為了了讓 malloc 可以更更快找到適合⼤大⼩小的 chunk,因此在 free 掉⼀一個 chunk 時,會把該 chunk 根 據⼤大⼩小加入適合的 bin 中 • 根據⼤大⼩小⼀一共會分為 • fast bin • small bin • large bin • unsorted bin
- 17. Mechanism of glibc malloc • fast bin • a singly linked list • chunk size < 144 byte • 不取消 inuse flag • 依據 bin 中所存的 chunk ⼤大⼩小,在分為 10 個 fast bin 分別為 size 0x20,0x30,0x40… • LIFO • 當下次 malloc ⼤大⼩小與這次 free ⼤大⼩小相同時,會從相同的 bin 取出,也就是會取到相 同位置的 chunk
- 18. • fast bin Mechanism of glibc malloc 0x128 0 0xddaa …… 0 ….. 0x20size 0x30 0x40 …. 0x70 …. prev_size size = 0x20 fd = null bk = null data data prev_size size = 0x40 fd = null bk = null data data 0x128 0xddaa fast bin array
- 19. • fast bin Mechanism of glibc malloc 0x20size 0x30 0x40 …. 0x70 …. prev_size size = 0x20 fd = null bk = null data data prev_size size = 0x40 fd = null bk = null data data 0x128 0xddaa free(0x466) fast bin array 0x128 0 0xddaa …… 0 …..
- 20. Mechanism of glibc malloc • fast bin 0x20size 0x30 0x40 …. 0x70 …. prev_size size = 0x20 fd = null bk = null data data prev_size size = 0x40 fd = ddaa bk = null data data prev_size size = 0x40 fd = null bk = null data data 0x128 0x456 0xddaa fast bin array 0x128 0 0x456 …… 0 …..
- 21. Mechanism of glibc malloc • fast bin 0x20size 0x30 0x40 …. 0x70 …. prev_size size = 0x20 fd = null bk = null data data prev_size size = 0x40 fd = ddaa bk = null data data prev_size size = 0x40 fd = null bk = null data data 0x128 0x456 0xddaa malloc(0x30) fast bin array 0x30 為使⽤用這所需⼤大⼩小,分配需加上 chunk header 所以分配到 0x40 的 chunk 0x128 0 0x456 …… 0 …..
- 22. • fast bin Mechanism of glibc malloc 0x20size 0x30 0x40 …. 0x70 …. prev_size size = 0x20 fd = null bk = null data data prev_size size = 0x40 fd = null bk = null data data 0x128 0xddaa fast bin array 0x128 0 0xddaa …… 0 …..
- 23. Mechanism of glibc malloc • unsorted bin • circular doubly linked list • 當 free 的 chunk ⼤大⼩小⼤大於等於 144 byte 時,為了了效率,glibc 並不會⾺馬 上將 chunk 放到相對應的 bin 中,就會先放到 unsorted bin • ⽽而下次 malloc 時將會先找找看 unsorted bin 中是否有適合的 chunk , 找不到才會去對應得 bin 中尋找, 此時會順便便把 unsorted bin 的 chunk 放到對應的 bin 中,但 small bin 除外,為了了效率,反⽽而先從 small bin 找
- 24. Mechanism of glibc malloc • small bin • circular doubly linked list • chunk size < 1024 byte • FIFO • 根據⼤大⼩小在分成 62 個⼤大⼩小不同的 bin • 0x20,0x30…0x60,0x70,0x90,……1008
- 25. Mechanism of glibc malloc • large bin • circular doubly linked list (sorted list) • chunk size >= 1024 • freed chunk 多兩兩個欄欄位 fd_nextsize 、bk_nextsize 指向前⼀一塊跟後⼀一塊 large chunk • 根據⼤大⼩小在分成 63 個 bin 但⼤大⼩小不再是⼀一固定⼤大⼩小增加 • 前 32 個 bin 為 0x400+64*i • 32 - 48 bin 為 0x1380 + 512*j • ....依此類推 • 不再是每個 bin 中的 chunk ⼤大⼩小都固定,每個 bin 中存著該範圍內不同⼤大⼩小的 bin 並在存的過程中進⾏行行 sort ⽤用來來加快 search 的 速度,⼤大的 chunk 會放在前⾯面,⼩小的 chunk 會放在後⾯面 • FIFO
- 26. Mechanism of glibc malloc • last remainder chunk • 在 malloc ⼀一塊 chunk 時,如果有找到比較⼤大的 chunk 可以給 user 會做 split 將 chunk 切成兩兩部分,多的那⼀一部分會成為⼀一塊 chunk 放到 last remander 中,unsortbin 也會存這⼀一塊 • 當下次 malloc 時,如果 last remainder chunk 夠⼤大,則會繼續從 last remainder 切出來來分配給 user
- 27. Mechanism of glibc malloc • unsorted bin, small bin , large bin (chunk array) 0x123 &bin2 &bin14 …… &bin64 0xdead …… 1bin_index 2 14 63 64 …. fd 126…. …. ….73 0x789 &bin2 &bin14 …… &bin64 0xbeef ……bk prev_size size = 144 fd = 0x789 bk = &bin1 data data prev_size size = 196 fd = &bin1 bk = 0x123 data data 0x123 0x789 prev_size size = 1152 fd = 0xbeef bk = &bin73 fd_nextsize bk_nextsize data prev_size size = 1140 fd = &bin73 bk = 0xdead fd_nextsize bk_nextsize data 0xdead 0xbeef
- 28. Mechanism of glibc malloc • main arena header • malloc_state • 存有所有的 bin 、 top chunk 等資訊 • 位於 libc 的 bss 段中
- 29. Mechanism of glibc malloc • Merge freed chunk • 為了了避免 heap 中存在太多⽀支離破碎的 chunk ,在 free 的時候會檢查周 圍 chunk 是否為 free 並進⾏行行合併 • 合併後會進⾏行行 unlink 去除 bin 中重複的 chunk
- 30. Mechanism of glibc malloc • Merge freed chunk • 執⾏行行 free 後 unlink 的條件,再 chunk 為非 mmaped 出來來的 chunk 時 • 如果連續記憶體中下⼀一塊是 top chunk,且上⼀一塊是 free chunk • 最後合併到 top chunk • 如果連續記憶體中下⼀一塊不是 top chunk • 上⼀一塊是 free chunk • 下⼀一塊是 free chunk
- 31. Mechanism of glibc malloc • Merge freed chunk • 合併流程 • 如果上⼀一塊是 freed • 合併上⼀一塊 chunk ,並對上⼀一塊做 unlink • 如果下⼀一塊是 • top : 合併到 top • ⼀一般 chunk : • freed : 合併下⼀一塊 chunk ,並對下⼀一塊做 unlink ,最後加入 unsortbin • inuse : 加入 unsortbin
- 32. Mechanism of glibc malloc prev_size = 0x90 size = 0x90 prev_size = 0 size = 0x91 prev_size = 0 size = 0x90 fd = &small bin bk = &small bin p 0x4b000 0x4b000 0x4b000 small bin unsorted bin free(p) &unsortbin &unsortbin
- 33. Mechanism of glibc malloc prev_size = 0x90 size = 0x90 prev_size = 0 size = 0x91 prev_size = 0 size = 0x90 fd = &small bin bk = &small bin p 0x4b000 unsorted bin 先利利⽤用 size 找到下 ⼀一塊 chunk p - 0x10 + 0x90 0x4b000 0x4b000 &unsortbin &unsortbin small bin
- 34. Mechanism of glibc malloc prev_size = 0x90 size = 0x90 prev_size = 0 size = 0x91 prev_size = 0 size = 0x90 fd = &small bin bk = &small bin p 0x4b000 unsorted bin 利利⽤用 inuse bit 檢查是否有被 free 過 0x4b000 0x4b000 &unsortbin &unsortbin small bin
- 35. Mechanism of glibc malloc prev_size = 0x90 size = 0x90 prev_size = 0 size = 0x91 prev_size = 0 size = 0x90 fd = &small bin bk = &small bin p 0x4b000 unsorted bin 檢查上⼀一塊 是否為 freed 0x4b000 0x4b000 &unsortbin &unsortbin small bin
- 36. Mechanism of glibc malloc prev_size = 0x90 size = 0x90 prev_size = 0 size = 0x91 prev_size = 0 size = 0x90 fd = &small bin bk = &small bin p 0x4b000 unsorted bin 利利⽤用 prev_size 找到上⼀一塊 chunk p - 0x10 - 0x90 0x4b000 0x4b000 &unsortbin &unsortbin small bin
- 37. Mechanism of glibc malloc prev_size = 0x90 size = 0x90 prev_size = 0 size = 0x91 prev_size = 0 size = 0x90 fd = null bk = null p &smallbin &smallbinm 0x4b000 small bin &unsortbin &unsortbin unsorted bin 進⾏行行 unlink 將上⼀一塊 chunk 從 bin 中移除
- 38. Mechanism of glibc malloc prev_size = 0x120 size = 0x90 prev_size = 0 size = 0x120 fd = null bk = null p 0x4b000 small bin unsorted bin merge &smallbin &smallbinm &unsortbin &unsortbin
- 39. Mechanism of glibc malloc prev_size = 0x120 size = 0x90 prev_size = 0 size = 0x120 fd = &unsorted bin bk = &unsorted bin p 0x4b000 small bin unsorted bin 加入 unsorted bin 中 &smallbin &smallbinm 0x4b000 0x4b000
- 40. Practice • Pwngdb • https://github.com/scwuaptx/Pwngdb • 觀察不同 malloc ⼤大⼩小時 chunk 被放入的位置 • 觀察 merge 的現象
- 41. Outline • Glibc memory allocator Overview • Use After Free • Heap Overflow • Appendix - Detection in Glibc
- 42. Use after free • 當 free 完之後,並未將 pointer 設成 null ⽽而繼續使⽤用該 pointer 該 pointer 稱為 dangling pointer • 根據 use ⽅方式不同⽽而有不同的⾏行行為,可能造成任意位置讀取或是任意位置寫 入,進⼀一步造成控制程式流程
- 43. Use after free
- 44. Use after free • Assume there exists a dangling ptr • p is a pointer of movement • free(p)
- 45. Use after free • Assume there exists a dangling ptr • p is a pointer of movement • free(p) // p is dangling ptr • q = (*struct stu)malloc(sizeof(stu)) • 此時因為 fast bin 的關係使 p == q
- 46. Use after free • Assume there exists a dangling ptr • p is a pointer of movement • free(p) // p is dangling ptr • q = (*struct stu)malloc(sizeof(stu)) • 此時因為 fast bin 的關係使 p == q • set id = 0x616161616161
- 47. Use after free • Assume there exists a dangling ptr • p is a pointer of movement • free(p) // p is dangling ptr • q = (*struct stu)malloc(sizeof(stu)) • 此時因為 fast bin 的關係使 p == q • set id = 0x616161616161 • p.playctf()
- 48. Use after free • Assume there exists a dangling ptr • p is a pointer of movement • free(p) // p is dangling ptr • q = (*struct stu)malloc(sizeof(stu)) • 此時因為 fast bin 的關係使 p == q • set id = 0x616161616161 • p.playctf() rip = 0x616161616161
- 49. Outline • Glibc memory allocator Overview • Use After Free • Heap Overflow • Appendix - Detection in Glibc
- 50. Heap overflow • 在 heap 段中發⽣生的 buffer overflow • 通常無法直接控制 eip 但可以利利⽤用蓋下⼀一個 chunk header ,並利利⽤用 malloc 時或 free 的造成的⾏行行為來來間接達成任意位置寫入,進⽽而控制 eip
- 51. Heap overflow data chunk header chunk header data chunk header data chunk header chunk header data chunk header aaaaaaaaaaaaaaaaaaaaa aaaaaaaaaaaaaaaaaaaaa aaaaaaaaaaaaaaaaaaaaa aaaaaaaaaaaaaaaaaaaaa aaaaaaaaaaaaaaaaaaaaa aaaaaaaaaaaaaaaaaaaaa aaaaaaaaaaaaaaaaaaaaa aaaaaaaaaaaaaaa overflow
- 52. Heap overflow • Unlink • Malloc maleficarum • Overwrite Fastbin
- 53. Heap overflow • using unlink • 透過 overflow 蓋掉 freed chunk 中的, fd 及 bk ,再利利⽤用 unlink 中 FD- >bk = BK 及 BK->fd = FD 來來更更改任意記憶體位置
- 54. Heap overflow • 複習⼀一下 doubly linked list 中, delete ⼀一個 node 時的過程 fd bk fd bk fd bk P unlink(P,BK,FD)
- 55. Heap overflow • 複習⼀一下 doubly linked list 中, delete ⼀一個 node 時的過程 P FD = P->fd FD fd bk fd bk fd bk
- 56. Heap overflow • 複習⼀一下 doubly linked list 中, delete ⼀一個 node 時的過程 P BK = P->bk FDBK fd bk fd bk fd bk
- 57. Heap overflow • 複習⼀一下 doubly linked list 中, delete ⼀一個 node 時的過程 P FD->bk = BK FDBK fd bk fd bk fd bk
- 58. Heap overflow • 複習⼀一下 doubly linked list 中, delete ⼀一個 node 時的過程 P BK->fd = FD FDBK fd bk fd bk fd bk
- 59. Heap overflow • 複習⼀一下 doubly linked list 中, delete ⼀一個 node 時的過程 P FDBK fd bk fd bk fd bk
- 60. Heap overflow • using unlink prev_size = 0 size = 0x90 prev_size = 0 size = 0x90 prev_size = 0 size = 0x91 fd = &bin bk = &bin overflow prev_size = 0x90 size = 0x90 prev_size = 0 size = 0x90 prev_size = 0 size = 0x81 fd = &bin bk = &bin prev_size = 0 size = 0x91 fd = got entry - 24 bk = shellcode addr
- 61. Heap overflow • using unlink • free(q) prev_size = 0x90 size = 0x90 prev_size = 0 size = 0x90 prev_size = 0 size = 0x81 fd = &bin bk = &bin prev_size = 0 size = 0x91 fd = got entry - 24 bk = shellcode addr q
- 62. Heap overflow • using unlink • free(q) • FD = P->fd = got entry - 24 • BK = P->bk = sc addr prev_size = 0x90 size = 0x90 prev_size = 0 size = 0x90 prev_size = 0 size = 0x81 fd = &bin bk = &bin prev_size = 0 size = 0x91 fd = got entry - 24 bk = shellcode addr q P
- 63. Heap overflow • using unlink • free(q) • FD = P->fd = got entry - 24 • BK = P->bk = sc addr • FD->bk = BK • got entry - 24 + 24 = sc addr • BK->fd = FD • sc addr + 16 = got entry - 24 prev_size = 0x90 size = 0x90 prev_size = 0 size = 0x90 prev_size = 0 size = 0x81 fd = &bin bk = &bin prev_size = 0 size = 0x91 fd = got entry - 24 bk = shellcode addr q P
- 64. Heap overflow • using unlink • free(q) • FD = P->fd = got entry - 24 • BK = P->bk = sc addr • FD->bk = BK • got entry - 24 + 24 = sc addr • BK->fd = FD • sc addr + 16 = got entry - 24 prev_size = 0x90 size = 0x90 prev_size = 0 size = 0x90 prev_size = 0 size = 0x81 fd = &bin bk = &bin prev_size = 0 size = 0x91 fd = got entry - 24 bk = shellcode addr q P GOT hijacking
- 65. Heap overflow • using unlink • 不過 shellcode 的第16 到第 24 個 byte 會因為 sc addr + 16 = got entry - 24 ⽽而被破壞 • 需修正為 shellcode 改為 jmp 的⽅方式跳到後⾯面去執⾏行行 • 當下次 call 到 got entry 時便便會跳到 shellcode 去執⾏行行了了
- 66. Heap overflow • using unlink (modern) • 但現實是殘酷的,現代 glibc 中有各種針對 chunk 的檢查及其他保護機制 (DEP),使 得該⽅方法無法使⽤用 • Double free detect • Invalid next size • Corrupted double linked list • Corrupted size vs. prev_size • ……
- 67. Heap overflow • detection in unlink • corrupted double linked list • 檢查 circular doubly linked list 的完整性,指出去在指回來來必須指回⾃自 ⼰己,否則就會顯⽰示 corrupted double-linked list 並中斷程式 • P->bk->fd == P • P->fd->bk == P
- 68. Heap overflow • detection in unlink • Corrupted size vs. prev_size • 預防 size 或 prev_size 被竄改 • chunksize(P) == next_chunk(P)->prev_size • glibc 2.26 後新增的檢查,ubuntu 16.04 glibc 有 update 所以也會有 這樣檢查
- 69. Heap overflow • using unlink (modern) • bypass the detection • 必須偽造 chunk 結構 • 必須找到指向偽造 chunk 的 pointer 及該 pointer 的 address • 因此能直接改的地⽅方有限,通常要間接去讀取或寫入任意位置 • chunk size 及 next_chunk->prev_szie 要⼀一起偽造
- 70. Heap overflow • using unlink (modern) • bypass the detection • there’re a pointer r point to data of the second chunk. prev_size = 0 size = 0x91 prev_size = 0 size = 0x80 prev_size = 0 size = 0x91 q r
- 71. Heap overflow • using unlink (modern) • bypass the detection • there’re a pointer r point to data of the second chunk. • overflow and forge chunks. prev_size = 0 size = 0x80 prev_size = 0 size = 0x80 prev_size = 0 size = 0x81 fd = &bin bk = &bin q rfake prev_size = 0x90 fake size = 0x80 fake fd = &r-0x18 fake bk = &r-0x10 fake prev_size2=0x80 size = 0x90 fake chunk
- 72. Heap overflow • using unlink (modern) • bypass the detection • there’re a pointer r point to data of the second chunk. • overflow and forge chunks. • you can see the pointer r is point to the fake chunk prev_size = 0 size = 0x80 prev_size = 0 size = 0x80 prev_size = 0 size = 0x81 fd = &bin bk = &bin fake prev_size = 0x90 fake size = 0x80 fake fd = &r-0x18 fake bk = &r-0x10 fake prev_size2=0x80 size = 0x90 r q
- 73. Heap overflow • using unlink (modern) • bypass the detection • free(q) prev_size = 0 size = 0x80 prev_size = 0 size = 0x80 prev_size = 0 size = 0x81 fd = &bin bk = &bin fake prev_size = 0x90 fake size = 0x80 fake fd = &r-0x18 fake bk = &r-0x10 fake prev_size2=0x80 fake prev_size = 0x90 fake size = 0x80 fake fd = &r-0x18 fake bk = &r-0x10 fake prev_size2=0x80 size = 0x90 r q
- 74. Heap overflow • using unlink (modern) • bypass the detection • free(q) • check q & r is freed prev_size = 0 size = 0x80 prev_size = 0 size = 0x80 fake prev_size = 0x90 fake size = 0x80 fake fd = &r-0x18 fake bk = &r-0x10 fake prev_size2=0x80 fake prev_size = 0x90 fake size = 0x80 fake fd = &r-0x18 fake bk = &r-0x10 fake prev_size2=0x80 size = 0x90 r q
- 75. Heap overflow • using unlink (modern) • bypass the detection • free(q) • check q & r is freed • find the last chunk of q • q - 0x10 - prev_size2 = r prev_size = 0 size = 0x80 prev_size = 0 size = 0x80 fake prev_size = 0x90 fake size = 0x80 fake fd = &r-0x18 fake bk = &r-0x10 fake prev_size2=0x80 q rfake prev_size = 0x90 fake size = 0x80 fake fd = &r-0x18 fake bk = &r-0x10 fake prev_size2=0x80 size = 0x90
- 76. Heap overflow • using unlink (modern) • bypass the detection • unlink(r,FD,BK) • FD = r->fd = &r - 0x18 • BK = r->bk = &r - 0x10 prev_size = 0 size = 0x80 prev_size = 0 size = 0x80 fake prev_size = 0x90 fake size = 0x80 fake fd = &r-0x18 fake bk = &r-0x10 fake prev_size2=0x80 fake prev_size = 0x90 fake size = 0x80 fake fd = &r-0x18 fake bk = &r-0x10 fake prev_size2=0x80 size = 0x90 r q
- 77. Heap overflow • using unlink (modern) • bypass the detection • unlink(r,FD,BK) • check • prev_size2 == fake_size == 0x80 • r->fd->bk == r = *(&r-0x18+0x18) = r • r->bk->fd == r = *(&r-0x10+0x10) = r prev_size = 0 size = 0x80 prev_size = 0 size = 0x80 fake prev_size = 0x90 fake size = 0x80 fake fd = &r-0x18 fake bk = &r-0x10 fake prev_size2=0x80 fake prev_size = 0x90 fake size = 0x80 fake fd = &r-0x18 fake bk = &r-0x10 fake prev_size2=0x80 size = 0x90 r q
- 78. Heap overflow • using unlink (modern) • bypass the detection • FD->bk = BK • *(&r-0x18+0x18) = &r-0x10 • BK->fd = FD • *(&r-0x10+0x10) = &r-0x18 prev_size = 0 size = 0x80 prev_size = 0 size = 0x80 fake prev_size = 0x90 fake size = 0x80 fake fd = &r-0x18 fake bk = &r-0x10 fake prev_size2=0x80 fake prev_size = 0x90 fake size = 0x80 fake fd = &r-0x18 fake bk = &r-0x10 fake prev_size2=0x80 size = 0x90 r q
- 79. Heap overflow • using unlink (modern) • bypass the detection • FD->bk = BK • *(&r-0x18+0x18) = &r-0x10 • BK->fd = FD • *(&r - 0x10 + 0x10) = &r-0x18 • We change the value of &r successful then we may change other thing in mem. prev_size = 0 size = 0x80 prev_size = 0 size = 0x80 fake prev_size = 0x90 fake size = 0x80 fake fd = &r-0x18 fake bk = &r-0x10 fake prev_size2=0x80 fake prev_size = 0x90 fake size = 0x80 fake fd = &r-0x18 fake bk = &r-0x10 fake prev_size2=0x80 size = 0x80 fake prev_size = 0x90 fake size = 0x80 fake fd = &r-0x18 fake bk = &r-0x10 fake prev_size2=0x80 size = 0x90 r q
- 80. Heap overflow • using unlink (modern) • bypass the detection • 通常 r 會是個 data pointer • 可以利利⽤用他再去改變其他存在 &r 附近的 pointer 然後再利利⽤用這些 pointer 去造成任意位置讀取及寫入,如果存在 function pointer 更更可直 接控制 eip
- 83. Heap overflow BSS P R Q unlink *(&R-0x18+0x18) = &R-0x10 *(&R-0x10+0x10) = &R-0x18
- 84. Heap overflow BSS P &R - 0x18 Q Write data to R
- 87. Heap overflow • Using malloc maleficarum • The House of Mind • The House of Prime • The House of Spirit • The House of Force • The House of Lore
- 88. The House of Spirit • stack overflow • 當 stack overflow 不夠蓋到 ret 時 • 利利⽤用 stack overflow 蓋過要 free 的 ptr 並偽造 chunk • 須針對 prev_size 及 size 做處理理,通過檢查 • using fastbin • 當下次 malloc 時 就會取得偽造的 chunk
- 89. The House of Spirit • 可以做 information leak • 也可加⼤大 stack overflow 的距離 • 要先算算看在 stack 中取下⼀一塊 chunk 的 size 是否合法為 0x10 的倍數, size 的取決是很重要的 • 32 bit 為 0x8 倍數
- 90. The House of Spirit • Assume exist free(p) • read(0,buf,size) • read 不夠長到可以蓋 ret fake_size_2 … ret ebp … … *p dddd eeee buf q size
- 91. The House of Spirit • overflow *p fake chunk fake_size_2 … ret ebp … … *q fake_size fake prev_size buf q
- 92. The House of Spirit • overflow *p • free(p) -> free(q) fake chunk fake_size_2 … ret ebp … … *q fake_size fake prev_size buf q
- 93. The House of Spirit • overflow *p • free(q) • 下⼀一塊 size 要合法 fake_size_2 … ret ebp … … *q fake_size fake prev_size buf q
- 94. The House of Spirit • overflow *p • free(q) • malloc(fake_size-16) • it will return q fake_size fake_size_2 … ret ebp … … *q fake_size fake prev_size buf q
- 95. The House of Spirit • overflow *p • free(q) • malloc(fake_size-16) • it will return q • read(0,q,fake_size-16) fake_size_2 … ret ebp … … *q fake_size fake prev_size buf q
- 96. The House of Spirit • overflow *p • free(q) • malloc(fake_size-16) • it will return q • read(0,q,fake_size-16) overflow fake_size_2 … aaaa aaaa aaaa aaaa aaaa fake_size fake prev_size buf q
- 97. The House of Force • malloc 從 top 分配空間時,top 位置會以當前位置+分配 chunk ⼤大⼩小,作為 新的 top 位置 • nb = malloc 時 user 所需⼤大⼩小 • new top = old top + nb + sizeof(chunk header)
- 98. The House of Force • malloc(nb) prev_size data top chunk size prev_size top_size
- 99. The House of Force • malloc(nb) • 檢查 top_size 是否夠分配給使⽤用者 • top_size - nb > 0 ? • true : 從 top 分配 • false : 使⽤用 mmap or 擴⼤大 heap 空間 prev_size data top chunk size prev_size top_size
- 100. The House of Force • malloc(nb) • new top = old top + nb + sizeof(chunk header) prev_size data top chunk size prev_size top_size
- 101. The House of Force • malloc(nb) • new top = old top + nb + sizeof(chunk header) • new_top_size = top_size - (nb+sizeof(chunk header) prev_size data old top size prev_size nb + sizeof(header) new topprev_size new_top_size data nb + sizeof(header)
- 102. The House of Force • heap overflow 蓋過 top chunk 的 size,變成⼀一個很⼤大的值 • 下次 malloc 時,malloc ⼀一個很⼤大的數字(nb),然後 arena header 中的 top chunk 的位置會改變 • new top chunk = old top + nb + sizeof(header) • nb 可以是負的,因為傳進去會被⾃自動轉成很⼤大的數字,只要讓 fake size - nb > 0 就會讓 glibc 以為 top 還有空間可以給,因 nb 是負的,所以 top 會往前,造 成 overlap • 這樣下次 malloc 的位置將會是 new top chunk 的位置
- 103. The House of Force prev_size data prev_size top chunk size size data prev_size size
- 104. The House of Force 0 function ptr 0 top chunk 0x41 0x41 data 0 0x20f81
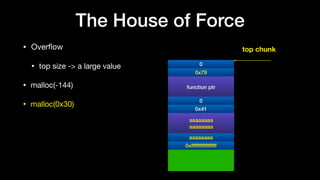
- 105. • Overflow • top size -> a large value The House of Force 0 function ptr 0 top chunk 0x41 0x41 aaaaaaaa aaaaaaaa aaaaaaaa 0xffffffffffffffff
- 106. • Overflow • top size -> a large value • malloc(nb) • new top chunk = old top + nb + 16 • nb = new top - old top - 16 The House of Force 0 function ptr 0 top chunk 0x41 0x41 aaaaaaaa aaaaaaaa aaaaaaaa 0xffffffffffffffff
- 107. • Overflow • top size -> a large value • malloc(nb) • new top chunk = old top + nb + 16 • nb = -(0x40+0x40) - 0x10 = -0x90 = - 144 The House of Force 0 function ptr 0 top chunk 0x41 0x41 aaaaaaaa aaaaaaaa aaaaaaaa 0xffffffffffffffff new top
- 108. • Overflow • top size -> a large value • malloc(-144) • check • 0xffffffffffffffff - (-144) > 0 The House of Force 0 function ptr 0 top chunk 0x41 0x41 aaaaaaaa aaaaaaaa aaaaaaaa 0xffffffffffffffff new top
- 109. • Overflow • top size -> a large value • malloc(-144) • malloc(0x30) The House of Force 0 function ptr 0 top chunk 0x79 0x41 aaaaaaaa aaaaaaaa aaaaaaaa 0xffffffffffffffff
- 110. • Overflow • top size -> a large value • malloc(-144) • malloc(0x30) • call function ptr The House of Force 0 aaaaaaaa 0 top chunk 0x41 0x79-0x41 aaaaaaaa aaaaaaaa aaaaaaaa 0xffffffffffffffff
- 111. • Overflow • top size -> a large value • malloc(-144) • malloc(0x30) • call function ptr The House of Force 0 aaaaaaaa 0 top chunk 0x79 0x41 aaaaaaaa aaaaaaaa aaaaaaaa 0xffffffffffffffff Control RIP
- 112. Overwrite Fastbin • 類似 House of Spirit • 如果可以改到 fastbin 的 free chunk 可以將 fd 改成 fake chunk 的位置,只 要符合 size 是屬於該 fastbin 就好,因為在下⼀一次 malloc 只會檢查這項 • 下下次 malloc(size-0x10) 時,就會取得該 fake chunk 的位置 • fake chunk 可以是任意記憶體位置
- 113. Overwrite Fastbin 0x128 0 0xddaa …… 0 ….. 0x20size 0x30 0x40 …. 0x70 …. prev_size size = 0x20 fd = null bk = null datadata prev_size size = 0x40 fd = null bk = null datadata 0x128 0xddaa fast bin array Overwrite fd
- 114. Overwrite Fastbin 0x20size 0x30 0x40 …. 0x70 …. prev_size size = 0x20 fd = 0xbeef bk = null datadata prev_size size = 0x40 fd = null bk = null data data 0x128 0xddaa fast bin array malloc(0x10) = 0x128+0x10 0x128 0 0xddaa …… 0 …..
- 115. Overwrite Fastbin 0x20size 0x30 0x40 …. 0x70 …. prev_size size = 0x40 fd = null bk = null datadata 0xddaa fast bin array malloc(0x10) = Get the 0xbeef chunk 0xbeef 0 0xddaa …… 0 …..
- 116. Overwrite Fastbin 0xbeef 0 0xddaa …… 0 ….. 16size 24 32 …. 64 …. prev_size size = 32 fd = null bk = null datadata 0xddaa fast bin array malloc(0x10) = Get the 0xbeef chunk 可對 0xbeef 任意寫值
- 117. Outline • Glibc memory allocator Overview • Use After Free • Heap Overflow • Appendix - Detection in Glibc
- 118. Detection in Glibc • detection in malloc • size 是 fastbin 的情況 • memory corruption (fast) • 從 fastbin 取出的第⼀一塊 chunk 的 (unsigned long) size 不屬於該 fastbin 中的 • 主要檢查⽅方式是根據 malloc 的 bytes ⼤大⼩小取得 index 後,到對應的 fastbin 找,取 出第⼀一塊後後檢查該 chunk 的 (unsigned long) size 是否屬於該 fastbin • 但實際比較的時候是先以fastbin 中第⼀一塊 size 取得fastbin 的 index ,再去比 index 跟剛剛算的 index 是否相同,不過這取 index 的⽅方式是⽤用 unsigned int (4 byte)
- 119. Detection in Glibc • detection in malloc • size 是 smallbin 的情況 • smallbin double linked list corrupted • 從相對應的 smallbin 中拿最後⼀一個時,要符合 smallbin 是 double linked list • victim == smallbin 最後⼀一塊 chunk • bck = victim->bk • bck->fd == victim
- 120. Detection in Glibc • detection in malloc • unsortbin 中有 chunk • memory corruption • 取 unsortbin 的最後⼀一塊 chunk 作為 victim • victim->size 要符合規定 • size 必須⼤大於 2 x SIZE_SZ ( 0x10 ) • size 必須⼩小於 system_mem • system mem : heap 的⼤大⼩小通常為 132k
- 121. Detection in Glibc • detection in malloc • size 是 largebin 的情況 • corrupted unsorted chunks • 在找到適合的 chunk 切給 user 後,剩下的空間會放到 last remainder,然後加到 unsortbin 中 • 這時會取 unsortbin 的第⼀一個的 fd 是否等於 unsortbin 的位置
- 122. Detection in Glibc • detection in free • invalid pointer • 檢查 alignment • chunk address 是否為 0x10 的倍數 • 檢查 chunk address 是否⼩小於 - size
- 123. Detection in Glibc • detection in free • invalid size • 檢查 chunk size 是否合法 • size 必須為 0x10 的倍數 ( 不含最低 3 bit ) • 也就是是否有符合 alignment • size 必須⼤大於 MINSIZE ( 0x20 byte )
- 124. Detection in Glibc • detection in free • size 是 fastbin 的情況 • invalid next size (fast) • 檢查下⼀一塊 chunk size 是否合法 • size 必須⼤大於 MINSIZE ( 0x10 byte ) • size 必須⼩小於 system_mem • system mem : heap 的⼤大⼩小通常為 132k
- 125. Detection in Glibc • detection in free • size 是 fastbin 的情況 • double free or corruption (fasttop) • 檢查 fastbin 中的第⼀一塊 chunk 跟正要 free 的 chunk 是否不同 • 要是相同就會 abort
- 126. Detection in Glibc • detection in free • size 是 smallbin & largebin 的情況 (非 mmap) • double free or corruption (top) • 檢查正要 free 的 chunk 跟 top chunk 的位置是否不同 • 要是相同就會 abort
- 127. Detection in Glibc • detection in free • size 是 smallbin & largebin 的情況 (非 mmap) • double free or corruption (out) • 計算出來來下⼀一塊 chunk 的位置是否超出 heap 的邊界 • 超出 heap 邊界就會 abort
- 128. Detection in Glibc • detection in free • size 是 smallbin & largebin 的情況 (非 mmap) • double free or corruption (!prev) • 根據下⼀一塊 chunk 的 inuse bit 來來檢查正要 free 的 chunk 是否已 被 free 過
- 129. Detection in Glibc • detection in free • size 是 smallbin & largebin 的情況 (非 mmap) • invalid next size (normal) • 檢查下⼀一塊 chunk size 是否合法 • size 必須⼤大於 2 x SIZE_SZ (0x10) • size 必須⼩小於 system_mem • system mem : heap 的⼤大⼩小通常為 132k
- 130. Detection in Glibc • detection in free • size 是 smallbin & largebin 的情況 (非 mmap) • corrupted unsorted chunks • 在 unlink 後要放到 unsortbin 時,會先從 unsortbin 取第⼀一塊 chunk 出來來,然後檢查該 chunk 的 bk 是否等於 unsortbin
- 131. Reference • understanding-glibc-malloc • Modern Binary Exploitation - heap exploitation • MallocMaleficarum • glibc cross reference • SP heap exploitation by dada
- 132. Q & A