Modified aes algorithm using multiple s boxes
1 like399 views
The document proposes a modified AES algorithm using multiple substitution boxes (S-Boxes) to improve performance. It describes the standard AES algorithm and then proposes modifications. Specifically, it suggests using two S-Boxes - the original Rijndael S-Box along with a new S-Box constructed by XORing each value of the original S-Box with 7F and applying an affine transformation. Evaluation results showed that the modified algorithm with two S-Boxes improved speed performance compared to standard AES, while slightly weakening security. The modified algorithm is also more efficient to implement using low-cost processors and minimal memory.
1 of 48
Download to read offline



























![AES -Key Expansion submodule
• RotWord performs a one byte circular left shift on a word
For example:
RotWord[b0,b1,b2,b3] = [b1,b2,b3,b0]
• SubWord performs a byte substitution on each byte of
input word using the S-box
• SubWord(RotWord(temp)) is XORed with RCon[j] – the
round constant](https://image.slidesharecdn.com/modifiedaesalgorithmusingmultiples-boxes-190630144613/85/Modified-aes-algorithm-using-multiple-s-boxes-34-320.jpg)



![AES - CONSTRUCTION OF THE NEW S-BOX
vThe second S-Box is derived from the
original S- Box as designed in the AES
ØExclusive OR Operation
§ each cell in the AES-Rijndael will be
XORed with 7F
AES-Rijndael[x,y] XOR (7F)
§ The Key[i] shall be any hexadecimal value
between 00 to FF (Table 1. AES-
2SboxXOR7F)](https://image.slidesharecdn.com/modifiedaesalgorithmusingmultiples-boxes-190630144613/85/Modified-aes-algorithm-using-multiple-s-boxes-38-320.jpg)







![Referents
• [1] National Institute of Standards and
Technology, Advanced Encryption Standard,
FIPS 197 (2011).
• [2] Paper “Modified AES Algorithm Using
Multiple S-Boxes”
• [3] Wiki & slide & Internet.
50](https://image.slidesharecdn.com/modifiedaesalgorithmusingmultiples-boxes-190630144613/85/Modified-aes-algorithm-using-multiple-s-boxes-47-320.jpg)

Ad
Recommended
AES effecitve software implementation
AES effecitve software implementationRoman Oliynykov The document discusses effective software implementation of the Advanced Encryption Standard (AES), developed from the Rijndael cipher and selected in a cryptographic competition between 1997 and 2000. It covers AES properties, direct implementation challenges, optimization methods, and its efficiency on 32-bit platforms. The text concludes that effective AES implementation can significantly reduce processing time through look-up table accesses while maintaining cryptographic security.
Pwning in c++ (basic)
Pwning in c++ (basic)Angel Boy The document discusses C++ exploitation techniques including name mangling, virtual function tables, vtable hijacking, vectors, strings, and memory allocation/deallocation functions like new and delete. It provides details on how virtual function tables are used to implement polymorphism in C++ and how vtable hijacking can be used to exploit vulnerabilities by forcing a vtable and hijacking the virtual function pointer to call shellcode. It also explains how vectors and strings are implemented dynamically in memory and their memory layout.
Aquamacs Manual
Aquamacs Manualroblingelbach This document is the manual for Aquamacs Emacs, a user-friendly distribution of the GNU Emacs text editor customized for macOS. It introduces Aquamacs' features like its Aqua-native interface with standard keyboard shortcuts. The manual covers using Aquamacs for both beginners, focusing on the interface and basics, and experienced Emacs users, discussing customization options and how it differs from standard Emacs. It aims to help users harness Emacs' power in a familiar way for the Mac environment.
AES KEY EXPANSION .pptx
AES KEY EXPANSION .pptxAhmudulHassan The document describes the AES key expansion process. The AES algorithm takes a 128-bit key as input and expands it into a linear array of 44 words using a key schedule. The key schedule applies the key expansion function g, which performs byte substitutions and XOR operations with round constants, to generate a key for each round. The initial key is added to the first four words of the expanded key schedule.
Information and data security cryptographic hash functions
Information and data security cryptographic hash functionsMazin Alwaaly This document discusses hash functions and their cryptographic applications. It begins by defining hash functions and their properties like one-wayness and collision resistance. It then discusses various applications of cryptographic hash functions like message authentication codes, digital signatures, password files, and more. It provides details on how hash functions are used for message authentication and digital signatures. It also describes the Secure Hash Algorithm family of hash functions like SHA-1, SHA-2, and the NIST competition for the SHA-3 standard.
AMBA AHB Protocols
AMBA AHB ProtocolsJoe Andelija This document describes the design and implementation of diagnostic access for AMBA AHB communication protocols between a master and slave device. A core was designed using a master-slave topology to perform efficient write operations. The process involved designing master and slave units and a test bench to simulate communication. VHDL and XILINX were used to generate a synthesis report. The 32-bit address and data bus protocol supports high-bandwidth communication between processors and low-bandwidth peripherals. Features like burst transfers and wider data buses were implemented to support high performance systems.
Memory model
Memory modelYi-Hsiu Hsu This document discusses memory ordering and synchronization in multithreaded programs. It begins with background on mutexes, semaphores, and their differences. It then discusses problems that can occur with locking-based synchronization methods like mutexes, such as deadlocks, priority inversion, and performance issues. Alternative lock-free programming techniques using atomic operations are presented as a way to synchronize access without locks. Finally, memory ordering, consistency models, barriers, and their implementations in compilers, Linux kernels, and ARM architectures are covered in detail.
Room 3 - 7 - Nguyễn Như Phúc Huy - Vitastor: a fast and simple Ceph-like bloc...
Room 3 - 7 - Nguyễn Như Phúc Huy - Vitastor: a fast and simple Ceph-like bloc...Vietnam Open Infrastructure User Group Vitastor is a fast and simple Ceph-like block storage solution that aims to maximize performance for SSDs and NVMEs. It focuses on block storage with fixed-size blocks rather than Ceph's object storage model. Vitastor uses a monitor, Etcd, and OSDs like Ceph but without a separate CRUSH layer and with monitors that do not store data. It supports technologies like RDMA for low latency and high throughput. The presenter's experiments showed Vitastor had improved performance over Ceph in some tests but also experienced some integration and operational issues.
AES Encryption
AES EncryptionRahul Marwaha The document provides an introduction to the Advanced Encryption Standard (AES), developed by NIST as a successor to the Data Encryption Standard (DES). AES is a symmetric block cipher that uses key sizes of 128, 192, or 256 bits, and is known for its speed and security. The encryption process involves key generation and multiple rounds of transformation, including operations like substitution, permutation, and mixing of columns.
Qemu Introduction
Qemu IntroductionChiawei Wang QEMU is an emulator that uses dynamic translation to emulate one instruction set architecture (ISA) on another host ISA. It translates guest instructions to an intermediate representation (TCG IR) code, and then compiles the IR code to native host instructions. QEMU employs techniques like translation block caching and chaining to improve the performance of dynamic translation. It also uses helper functions to offload complex operations during translation to improve efficiency.
Windows 10 Nt Heap Exploitation (English version)
Windows 10 Nt Heap Exploitation (English version)Angel Boy The document discusses the Windows memory allocator and heap exploitation. It describes the core components and data structures of the NT heap, including the _HEAP structure, _HEAP_ENTRY chunks, BlocksIndex structure, and FreeLists. It also explains the differences between the backend and frontend allocators as well as how chunks of different sizes are managed.
Exploitation of counter overflows in the Linux kernel
Exploitation of counter overflows in the Linux kernelVitaly Nikolenko This document summarizes an exploit talk on counter overflows in the Linux kernel. It discusses how counter overflows can be used to exploit vulnerabilities by overflowing reference counters and triggering object deallocation. It provides examples of real counter overflow vulnerabilities in Linux, such as CVE-2014-2851 and CVE-2016-0728, and outlines the general exploitation procedure, including overflowing the counter, triggering object freeing, overwriting data, and executing code. It also discusses challenges like integer overflow times and techniques like using RCU calls to bypass checks.
Chacha ppt
Chacha pptVikramSingh1378 The document summarizes a seminar presentation on ChaCha, a variant of the Salsa20 stream cipher. It defines encryption and ciphers, describes types of ciphers like stream and block ciphers. It then explains Salsa20/20, how ChaCha is based on but improves Salsa20, details the ChaCha quarter round operation, and concludes with references used in the presentation.
Random Oracle Model & Hashing - Cryptography & Network Security
Random Oracle Model & Hashing - Cryptography & Network SecurityMahbubur Rahman This document discusses hashing and the random oracle model. It defines cryptographic hash functions as deterministic functions that map arbitrary strings to fixed-length outputs in a way that appears random. The random oracle model assumes an ideal hash function that behaves like a random function. The document discusses collision resistance, preimage resistance, and birthday attacks as they relate to finding collisions or preimages with a given hash function. It provides examples of calculating the number of messages an attacker would need to find collisions or preimages with different probabilities. The document concludes by listing some applications of cryptographic hash functions like password storage, file authenticity, and digital signatures.
Linux Binary Exploitation - Stack buffer overflow
Linux Binary Exploitation - Stack buffer overflowAngel Boy 该文档讨论了Linux下的二进制漏洞利用,尤其是缓冲区溢出和返回到文本攻击等技术。文中还介绍了多种保护机制,如ASLR、DEP和Stack Guard,并解释了延迟绑定如何影响函数调用的定位。总体上,文档为理解如何进行以及防止缓冲区溢出攻击提供了详尽的知识基础。
Salvatore Sanfilippo – How Redis Cluster works, and why - NoSQL matters Barce...
Salvatore Sanfilippo – How Redis Cluster works, and why - NoSQL matters Barce...NoSQLmatters The document discusses design tradeoffs for Redis cluster performance, addressing concepts like latency, consistency, and replication models. It details failure detection processes, configuration management using techniques from the Raft consensus algorithm, and strategies to ensure data safety during failovers. The document also outlines operational constraints during resharding and mentions an upcoming stable release for Redis cluster expected in Q1 2015.
Proxmox for DevOps
Proxmox for DevOpsJorge Moratilla Porras Proxmox VE is an open-source virtualization management solution that utilizes KVM and OpenVZ for efficient server virtualization. It offers features such as a rich web client, command line interface, role-based administration, live snapshots, and resource management for various storage types. While it has limitations regarding older kernels and lacks certain features like built-in firewalling, it remains a flexible option for both Linux and other operating systems.
Twofish
Twofishghanbarianm Twofish is a symmetric block cipher that uses a 16-round Feistel network with a block size of 128 bits and key sizes up to 256 bits. It was one of the five finalists in the AES competition. Twofish's building blocks include S-boxes, MDS matrices, and a key schedule. Differential cryptanalysis is the most successful attack against Twofish but requires a large number of chosen plaintexts and computational resources beyond what is practical. Twofish has efficient performance across many platforms and competitive speeds compared to other AES finalists.
Monoalphabetic Substitution Cipher
Monoalphabetic Substitution CipherSHUBHA CHATURVEDI Here is the cipher text using the Vigenere cipher with the given key and plaintext:
Ciphertext: "Sbkbtibn"
Q2. Decrypt the above cipher text:
CRYPTOGRAPHY AND NETWORK SECURITY- Transport-level Security
CRYPTOGRAPHY AND NETWORK SECURITY- Transport-level SecurityJyothishmathi Institute of Technology and Science Karimnagar The document discusses transport-level security, focusing on protocols like TLS and SSL, outlining their purpose in ensuring privacy and data integrity during internet communication. It details the TLS handshake and record protocols, highlighting how they authenticate parties and encrypt messages. Additionally, the document covers wireless network security concerns, vulnerabilities, and standards like IEEE 802.11i, recommending improvements for secure wireless communications.
Accelerating Virtual Machine Access with the Storage Performance Development ...
Accelerating Virtual Machine Access with the Storage Performance Development ...Michelle Holley The document discusses Intel's storage software products and highlights the performance of their technologies, including the Storage Performance Development Kit (SPDK). It notes that performance can vary based on system configurations and emphasizes the importance of consulting additional benchmarks and sources for accurate performance evaluation. Additionally, it outlines the benefits of using SPDK for maximizing IOPS and reducing latency in various storage applications.
Andes RISC-V vector extension demystified-tutorial
Andes RISC-V vector extension demystified-tutorialRISC-V International The document provides an overview of vector technology and the RISC-V Vector extension. It discusses SIMD and vector processor concepts, the evolution of vector instruction sets from Intel MMX/SSE/AVX to the RISC-V Vector specification. It also covers vector register file organization, instruction chaining, applications of vector processing, and challenges in implementing vector architectures. Andes Technology is introducing the AndesCoreTM NX27V processor core which implements the RISC-V Vector extension.
"Building Complete Embedded Vision Systems on Linux—From Camera to Display," ...
"Building Complete Embedded Vision Systems on Linux—From Camera to Display," ...Edge AI and Vision Alliance The document outlines a detailed approach to developing embedded computer vision systems on Linux using tools like OpenCV, Yocto, and various ARM SoC boards. It emphasizes the importance of selecting appropriate hardware, utilizing open-source libraries, and implementing video pipelines via V4L2 and GStreamer. Furthermore, it discusses potential challenges and solutions related to camera interfacing, video processing, and performance acceleration using different components.
U-Boot presentation 2013
U-Boot presentation 2013Wave Digitech U-Boot is an open source boot loader that initializes hardware and loads operating systems. It supports many CPUs and boards. The boot process involves a pre-relocation phase where U-Boot initializes hardware and copies itself to RAM, and a post-relocation phase where it finishes hardware initialization and loads the kernel or operating system. Debugging can be done before and after relocation by setting breakpoints and examining memory.
Qemu JIT Code Generator and System Emulation
Qemu JIT Code Generator and System EmulationNational Cheng Kung University QEMU is an open source system emulator that uses just-in-time (JIT) compilation to achieve high performance system emulation. It works by translating target CPU instructions to simple host CPU micro-operations at runtime. These micro-operations are cached and chained together into basic blocks to reduce overhead. This approach avoids the performance issues of traditional emulators by removing interpretation overhead and leveraging CPU parallelism through pipelining of basic blocks.
Nginx cheat sheet
Nginx cheat sheetLam Hoang This document provides a cheat sheet on how to configure the Nginx web server for common use cases such as setting ports and domain names, serving static files, redirects, reverse proxying, TLS/SSL encryption, load balancing, and access logging. It includes configuration examples for listening on ports, setting server names, serving static assets, 301 and 302 redirects, basic and upgraded reverse proxying, HTTPS setup, and load balancing multiple servers.
Message Authentication
Message Authenticationchauhankapil The document discusses message authentication, focusing on protecting message integrity, validating origin identity, and ensuring non-repudiation. It elaborates on three key methods: message encryption, message authentication codes (MAC), and hash functions, detailing their security requirements and properties. The document emphasizes the need for robust cryptographic functions to prevent various attacks and ensure reliable message authentication.
itlchn 20 - Kien truc he thong chung khoan - Phan 2
itlchn 20 - Kien truc he thong chung khoan - Phan 2IT Expert Club Đây là một công ty môi giới chính tại Việt Nam với khoảng 100.000 tài khoản khách hàng, đứng thứ 4 trên sàn HSX và thứ 2 trên sàn HNX. Hệ thống giao dịch có khả năng xử lý ổn định khoảng 5000-10000 lệnh mỗi giây nhưng gặp phải một số vấn đề như dead locking trong cơ sở dữ liệu và tần suất lệnh gửi cao, đặc biệt là vào ngày thị trường biến động mạnh. Công ty đang phát triển một hệ thống xử lý lệnh độc lập nhằm nâng hiệu năng và giảm độ trễ hệ thống.
AES.ppt
AES.pptBincySam2 The document discusses the Advanced Encryption Standard (AES). It describes AES as a symmetric block cipher selected by the U.S. National Institute of Standards and Technology (NIST) in 2001 to replace the Data Encryption Standard (DES). AES uses a variable block size of 128 bits and a key size of 128, 192, or 256 bits. The cipher operates on a 4x4 column-byte state and has 10, 12, or 14 rounds depending on the key size. Each round consists of byte substitution, shift rows, mix columns, and add round key transformations.
CR 05 - Advanced Encryption Standard.ppt
CR 05 - Advanced Encryption Standard.pptssuseraaf866 The document summarizes the Advanced Encryption Standard (AES) cipher. It describes AES's origins as a replacement for DES, outlines the structure and steps of AES including substitution bytes, shift rows, mix columns, and add round key. It also covers AES's key expansion process and notes AES can be efficiently implemented using table lookups and operations on 32-bit words.
More Related Content
What's hot (20)
AES Encryption
AES EncryptionRahul Marwaha The document provides an introduction to the Advanced Encryption Standard (AES), developed by NIST as a successor to the Data Encryption Standard (DES). AES is a symmetric block cipher that uses key sizes of 128, 192, or 256 bits, and is known for its speed and security. The encryption process involves key generation and multiple rounds of transformation, including operations like substitution, permutation, and mixing of columns.
Qemu Introduction
Qemu IntroductionChiawei Wang QEMU is an emulator that uses dynamic translation to emulate one instruction set architecture (ISA) on another host ISA. It translates guest instructions to an intermediate representation (TCG IR) code, and then compiles the IR code to native host instructions. QEMU employs techniques like translation block caching and chaining to improve the performance of dynamic translation. It also uses helper functions to offload complex operations during translation to improve efficiency.
Windows 10 Nt Heap Exploitation (English version)
Windows 10 Nt Heap Exploitation (English version)Angel Boy The document discusses the Windows memory allocator and heap exploitation. It describes the core components and data structures of the NT heap, including the _HEAP structure, _HEAP_ENTRY chunks, BlocksIndex structure, and FreeLists. It also explains the differences between the backend and frontend allocators as well as how chunks of different sizes are managed.
Exploitation of counter overflows in the Linux kernel
Exploitation of counter overflows in the Linux kernelVitaly Nikolenko This document summarizes an exploit talk on counter overflows in the Linux kernel. It discusses how counter overflows can be used to exploit vulnerabilities by overflowing reference counters and triggering object deallocation. It provides examples of real counter overflow vulnerabilities in Linux, such as CVE-2014-2851 and CVE-2016-0728, and outlines the general exploitation procedure, including overflowing the counter, triggering object freeing, overwriting data, and executing code. It also discusses challenges like integer overflow times and techniques like using RCU calls to bypass checks.
Chacha ppt
Chacha pptVikramSingh1378 The document summarizes a seminar presentation on ChaCha, a variant of the Salsa20 stream cipher. It defines encryption and ciphers, describes types of ciphers like stream and block ciphers. It then explains Salsa20/20, how ChaCha is based on but improves Salsa20, details the ChaCha quarter round operation, and concludes with references used in the presentation.
Random Oracle Model & Hashing - Cryptography & Network Security
Random Oracle Model & Hashing - Cryptography & Network SecurityMahbubur Rahman This document discusses hashing and the random oracle model. It defines cryptographic hash functions as deterministic functions that map arbitrary strings to fixed-length outputs in a way that appears random. The random oracle model assumes an ideal hash function that behaves like a random function. The document discusses collision resistance, preimage resistance, and birthday attacks as they relate to finding collisions or preimages with a given hash function. It provides examples of calculating the number of messages an attacker would need to find collisions or preimages with different probabilities. The document concludes by listing some applications of cryptographic hash functions like password storage, file authenticity, and digital signatures.
Linux Binary Exploitation - Stack buffer overflow
Linux Binary Exploitation - Stack buffer overflowAngel Boy 该文档讨论了Linux下的二进制漏洞利用,尤其是缓冲区溢出和返回到文本攻击等技术。文中还介绍了多种保护机制,如ASLR、DEP和Stack Guard,并解释了延迟绑定如何影响函数调用的定位。总体上,文档为理解如何进行以及防止缓冲区溢出攻击提供了详尽的知识基础。
Salvatore Sanfilippo – How Redis Cluster works, and why - NoSQL matters Barce...
Salvatore Sanfilippo – How Redis Cluster works, and why - NoSQL matters Barce...NoSQLmatters The document discusses design tradeoffs for Redis cluster performance, addressing concepts like latency, consistency, and replication models. It details failure detection processes, configuration management using techniques from the Raft consensus algorithm, and strategies to ensure data safety during failovers. The document also outlines operational constraints during resharding and mentions an upcoming stable release for Redis cluster expected in Q1 2015.
Proxmox for DevOps
Proxmox for DevOpsJorge Moratilla Porras Proxmox VE is an open-source virtualization management solution that utilizes KVM and OpenVZ for efficient server virtualization. It offers features such as a rich web client, command line interface, role-based administration, live snapshots, and resource management for various storage types. While it has limitations regarding older kernels and lacks certain features like built-in firewalling, it remains a flexible option for both Linux and other operating systems.
Twofish
Twofishghanbarianm Twofish is a symmetric block cipher that uses a 16-round Feistel network with a block size of 128 bits and key sizes up to 256 bits. It was one of the five finalists in the AES competition. Twofish's building blocks include S-boxes, MDS matrices, and a key schedule. Differential cryptanalysis is the most successful attack against Twofish but requires a large number of chosen plaintexts and computational resources beyond what is practical. Twofish has efficient performance across many platforms and competitive speeds compared to other AES finalists.
Monoalphabetic Substitution Cipher
Monoalphabetic Substitution CipherSHUBHA CHATURVEDI Here is the cipher text using the Vigenere cipher with the given key and plaintext:
Ciphertext: "Sbkbtibn"
Q2. Decrypt the above cipher text:
CRYPTOGRAPHY AND NETWORK SECURITY- Transport-level Security
CRYPTOGRAPHY AND NETWORK SECURITY- Transport-level SecurityJyothishmathi Institute of Technology and Science Karimnagar The document discusses transport-level security, focusing on protocols like TLS and SSL, outlining their purpose in ensuring privacy and data integrity during internet communication. It details the TLS handshake and record protocols, highlighting how they authenticate parties and encrypt messages. Additionally, the document covers wireless network security concerns, vulnerabilities, and standards like IEEE 802.11i, recommending improvements for secure wireless communications.
Accelerating Virtual Machine Access with the Storage Performance Development ...
Accelerating Virtual Machine Access with the Storage Performance Development ...Michelle Holley The document discusses Intel's storage software products and highlights the performance of their technologies, including the Storage Performance Development Kit (SPDK). It notes that performance can vary based on system configurations and emphasizes the importance of consulting additional benchmarks and sources for accurate performance evaluation. Additionally, it outlines the benefits of using SPDK for maximizing IOPS and reducing latency in various storage applications.
Andes RISC-V vector extension demystified-tutorial
Andes RISC-V vector extension demystified-tutorialRISC-V International The document provides an overview of vector technology and the RISC-V Vector extension. It discusses SIMD and vector processor concepts, the evolution of vector instruction sets from Intel MMX/SSE/AVX to the RISC-V Vector specification. It also covers vector register file organization, instruction chaining, applications of vector processing, and challenges in implementing vector architectures. Andes Technology is introducing the AndesCoreTM NX27V processor core which implements the RISC-V Vector extension.
"Building Complete Embedded Vision Systems on Linux—From Camera to Display," ...
"Building Complete Embedded Vision Systems on Linux—From Camera to Display," ...Edge AI and Vision Alliance The document outlines a detailed approach to developing embedded computer vision systems on Linux using tools like OpenCV, Yocto, and various ARM SoC boards. It emphasizes the importance of selecting appropriate hardware, utilizing open-source libraries, and implementing video pipelines via V4L2 and GStreamer. Furthermore, it discusses potential challenges and solutions related to camera interfacing, video processing, and performance acceleration using different components.
U-Boot presentation 2013
U-Boot presentation 2013Wave Digitech U-Boot is an open source boot loader that initializes hardware and loads operating systems. It supports many CPUs and boards. The boot process involves a pre-relocation phase where U-Boot initializes hardware and copies itself to RAM, and a post-relocation phase where it finishes hardware initialization and loads the kernel or operating system. Debugging can be done before and after relocation by setting breakpoints and examining memory.
Qemu JIT Code Generator and System Emulation
Qemu JIT Code Generator and System EmulationNational Cheng Kung University QEMU is an open source system emulator that uses just-in-time (JIT) compilation to achieve high performance system emulation. It works by translating target CPU instructions to simple host CPU micro-operations at runtime. These micro-operations are cached and chained together into basic blocks to reduce overhead. This approach avoids the performance issues of traditional emulators by removing interpretation overhead and leveraging CPU parallelism through pipelining of basic blocks.
Nginx cheat sheet
Nginx cheat sheetLam Hoang This document provides a cheat sheet on how to configure the Nginx web server for common use cases such as setting ports and domain names, serving static files, redirects, reverse proxying, TLS/SSL encryption, load balancing, and access logging. It includes configuration examples for listening on ports, setting server names, serving static assets, 301 and 302 redirects, basic and upgraded reverse proxying, HTTPS setup, and load balancing multiple servers.
Message Authentication
Message Authenticationchauhankapil The document discusses message authentication, focusing on protecting message integrity, validating origin identity, and ensuring non-repudiation. It elaborates on three key methods: message encryption, message authentication codes (MAC), and hash functions, detailing their security requirements and properties. The document emphasizes the need for robust cryptographic functions to prevent various attacks and ensure reliable message authentication.
itlchn 20 - Kien truc he thong chung khoan - Phan 2
itlchn 20 - Kien truc he thong chung khoan - Phan 2IT Expert Club Đây là một công ty môi giới chính tại Việt Nam với khoảng 100.000 tài khoản khách hàng, đứng thứ 4 trên sàn HSX và thứ 2 trên sàn HNX. Hệ thống giao dịch có khả năng xử lý ổn định khoảng 5000-10000 lệnh mỗi giây nhưng gặp phải một số vấn đề như dead locking trong cơ sở dữ liệu và tần suất lệnh gửi cao, đặc biệt là vào ngày thị trường biến động mạnh. Công ty đang phát triển một hệ thống xử lý lệnh độc lập nhằm nâng hiệu năng và giảm độ trễ hệ thống.
CRYPTOGRAPHY AND NETWORK SECURITY- Transport-level Security
CRYPTOGRAPHY AND NETWORK SECURITY- Transport-level SecurityJyothishmathi Institute of Technology and Science Karimnagar
"Building Complete Embedded Vision Systems on Linux—From Camera to Display," ...
"Building Complete Embedded Vision Systems on Linux—From Camera to Display," ...Edge AI and Vision Alliance
Similar to Modified aes algorithm using multiple s boxes (20)
AES.ppt
AES.pptBincySam2 The document discusses the Advanced Encryption Standard (AES). It describes AES as a symmetric block cipher selected by the U.S. National Institute of Standards and Technology (NIST) in 2001 to replace the Data Encryption Standard (DES). AES uses a variable block size of 128 bits and a key size of 128, 192, or 256 bits. The cipher operates on a 4x4 column-byte state and has 10, 12, or 14 rounds depending on the key size. Each round consists of byte substitution, shift rows, mix columns, and add round key transformations.
CR 05 - Advanced Encryption Standard.ppt
CR 05 - Advanced Encryption Standard.pptssuseraaf866 The document summarizes the Advanced Encryption Standard (AES) cipher. It describes AES's origins as a replacement for DES, outlines the structure and steps of AES including substitution bytes, shift rows, mix columns, and add round key. It also covers AES's key expansion process and notes AES can be efficiently implemented using table lookups and operations on 32-bit words.
AES.ppt
AES.pptssuser6602e0 The document summarizes the Advanced Encryption Standard (AES) cipher. It describes AES's origins as a replacement for DES, outlines the structure and steps of AES including substitution bytes, shift rows, mix columns, and add round key. It also covers AES's key expansion process and notes AES can be efficiently implemented using table lookups and byte operations.
Information and data security advanced encryption standard (aes)
Information and data security advanced encryption standard (aes)Mazin Alwaaly The Advanced Encryption Standard (AES) is a block cipher algorithm developed by Dr. Joan Daemen and Dr. Vincent Rijmen, designed to be secure, efficient, and easy to implement, featuring a block length of 128 bits and key lengths of 128, 192, or 256 bits. It employs a series of processes including byte substitution, shifting rows, mixing columns, and adding round keys in multiple rounds depending on the key size, ensuring robust data protection. AES is widely used for secure communications across various applications, including internet protocols like TLS and IPSec, due to its resistance to known attacks.
Cryptography
CryptographyMannat Gill 1. The document discusses the Advanced Encryption Standard (AES) cipher, which was selected from the Rijndael algorithm in 2000 to replace the Data Encryption Standard (DES).
2. AES has a block size of 128 bits, with key sizes of 128, 192, or 256 bits. It operates on a 4x4 column-byte state and consists of 10-14 rounds depending on the key size.
3. Each round performs byte substitution, shifting rows of the state, mixing columns using matrix multiplication, and adding the round key using XOR. The key is expanded using XOR and S-boxes to generate round keys.
advance encryption standard chapter 5.ppt
advance encryption standard chapter 5.pptroueida mohammed 1. AES was developed as a replacement for DES and published by NIST in 2001 to be more secure against attacks.
2. AES uses a block size of 128 bits and a key size of 128, 192, or 256 bits. Each round consists of four functions: byte substitution, shifting rows, mixing columns, and adding the round key.
3. The Rijndael cipher was selected as the basis for AES due to its resistance to attacks, efficient implementation on CPUs, and simple design.
694 lecture1aes
694 lecture1aesAnkur Human The document summarizes the Advanced Encryption Standard (AES) cipher. It describes AES as an iterative block cipher based on Rijndael that was selected through a competition in 2000 to replace the aging Data Encryption Standard (DES). The AES cipher uses 10 rounds of processing for 128-bit keys consisting of byte substitution, shifting rows of the internal block representation, mixing columns, and XORing with a round key. Keys are expanded using a key schedule to generate round keys.
Lecture # 007 AES.pptx
Lecture # 007 AES.pptxMuhammadJavedNaro The document provides information about the Advanced Encryption Standard (AES) encryption algorithm. It describes AES as a symmetric block cipher chosen by the U.S. government to protect classified information. The document outlines the development and selection process for AES, describing how it was intended to replace the aging Data Encryption Standard (DES). It also provides details about the AES algorithm, including that it uses 128, 192, or 256-bit keys and encryption is performed through 10-14 rounds of processing involving byte substitution, shifting rows of data, mixing columns, and combining with the encryption key.
Advanced Encryption System - Network and Security.ppt
Advanced Encryption System - Network and Security.pptVimalAadhithan The Advanced Encryption Standard (AES) was established to replace the outdated Data Encryption Standard (DES) due to its smaller key size and slow processing. The AES cipher, specifically the Rijndael algorithm, was selected in October 2000 for its speed, security, and efficiency, and it processes data in 128-bit blocks with key sizes of 128, 192, or 256 bits. The design features include multiple rounds of transformations involving substitution, permutation, mixing, and key addition, offering strong resistance against known cryptanalysis attacks.
Information and network security 25 algorithmic steps of aes
Information and network security 25 algorithmic steps of aesVaibhav Khanna The document outlines the Advanced Encryption Standard (AES) algorithm, detailing its structure and operations, including iterative processes, key expansion, and four main stages: substitution, shifting, mixing, and adding the round key. Each stage is designed to enhance security and is reversible for decryption, involving arithmetic in the finite field GF(2^8). It emphasizes the importance of diffusion and confusion in data encryption to protect against attacks.
AES.pptx
AES.pptxRizwanBasha12 The document describes the Advanced Encryption Standard (AES) algorithm. AES is a symmetric block cipher that encrypts data blocks of 128 bits using a key of 128, 192, or 256 bits. It operates on a 4x4 matrix through a series of transformations including byte substitution, shifting rows, mixing columns, and adding a round key. The algorithm consists of 10, 12, or 14 rounds depending on the key size. AES provides security, efficiency, and flexibility for encryption.
Aes
AesAravindharamanan S The document discusses the Advanced Encryption Standard (AES), which was selected by the U.S. National Institute of Standards and Technology in 2000 to replace the older Data Encryption Standard (DES). It describes the origins and development of AES, including the evaluation process where Rijndael was selected as the winning algorithm. The summary also provides a high-level overview of how AES works, including its conceptual scheme, encryption rounds, key scheduling, and security against known attacks.
Aes128 bit project_report
Aes128 bit project_reportNikhil Gupta The document discusses the Advanced Encryption Standard (AES) algorithm, which is used for encryption and involves several processes applied to a rectangular array called the state. AES uses a variable number of rounds depending on the key size, with each round consisting of sub bytes, shift rows, mix columns, and add round key transformations except for the last round which excludes mix columns. The Rijndael cipher which was selected as the AES algorithm operates on a 4x4 byte state and supports key sizes of 128, 192, and 256 bits.
Aes
AesMuhammad Asif The document summarizes the Advanced Encryption Standard (AES). It describes how AES was selected by NIST as a replacement for DES. AES (Rijndael cipher) uses a block size of 128 bits, with key sizes of 128, 192, or 256 bits. It operates on data in rounds that include byte substitution, shifting rows, mixing columns, and adding the round key. The key is expanded into an array of words used for each round.
“Optimized AES Algorithm Core Using FeedBack Architecture”
“Optimized AES Algorithm Core Using FeedBack Architecture” Nirav Desai This document describes an optimized AES algorithm core using a feedback architecture. It proposes a new design scheme for the AES-128 encryption algorithm that applies feedback technology to maintain encryption speed while modifying the data transmission mode to reduce chip size. The key details are dividing the 128-bit plaintext, key, and ciphertext into four 32-bit units controlled by a clock. This allows significantly decreasing the number of chip pins and optimizing the chip area.
Paper on Optimized AES Algorithm Core Using FeedBack Architecture
Paper on Optimized AES Algorithm Core Using FeedBack Architecture Dhaval Kaneria The document presents a novel feedback architecture-based design for the AES-128 encryption algorithm aimed at optimizing chip size and enhancing encryption speed. The proposed solution simplifies the chip pin count and effectively reduces the overall area through a modified data transmission mode. The paper compares this feedback architecture to a traditional pipeline approach, demonstrating significant performance improvements and applications for high-speed data encryption in various fields.
AES-Advanced Encryption Standard
AES-Advanced Encryption StandardPrince Rachit The Advanced Encryption Standard (AES) is a widely accepted encryption algorithm established by NIST to secure classified information and operates on 128-bit blocks. AES uses a series of repeated functions - including substitution, shifting, mixing, and key addition - with the number of rounds varying based on key size (10, 12, or 14 rounds). Despite its robustness, there are advanced attacks like the related key attack which attempt to weaken AES, though these remain impractical with current technology for key sizes of 128 bits and above.
Unit -2.ppt
Unit -2.pptDHANABALSUBRAMANIAN The document discusses the Advanced Encryption Standard (AES) which was selected by the U.S. government to encrypt sensitive data. It describes the requirements for AES, the evaluation criteria used in selecting it, and the five algorithm finalists. Rijndael, designed by Belgian cryptographers, was ultimately chosen as the AES cipher due to its security, performance, and simplicity. The summary provides an overview of the AES selection process and key aspects of the Rijndael cipher, including its round structure and efficient software implementations.
Chapter 5 module 3
Chapter 5 module 3daneshwarihatti The document discusses the Advanced Encryption Standard (AES), which was selected by the US National Institute of Standards and Technology (NIST) in 2000 to replace the Data Encryption Standard (DES). AES uses 128-bit blocks and supports key sizes of 128, 192, and 256 bits. It is based on the Rijndael cipher designed by Vincent Rijmen and Joan Daemen. AES operates on a 4x4 column-major order matrix of bytes and uses substitutions, transpositions, and mixing operations along with adding a round key to transform the input, with decryption being the inverse process using the round keys in reverse order.
Advance Encryption Standard-AES Cryptosystem
Advance Encryption Standard-AES CryptosystemFacelessVoid6 The document discusses the development and characteristics of the Advanced Encryption Standard (AES), which was selected as the successor to the Data Encryption Standard (DES) due to vulnerabilities found in DES and the need for a more secure encryption algorithm. AES emphasizes security, cost, and implementation flexibility and operates on 128-bit blocks using multiple transformation rounds, including substitutions, permutations, and mixing operations. AES is highly secure against known attacks and is designed for efficient implementation across various platforms.
Ad
Recently uploaded (20)
Tanja Vujicic - PISA for Schools contact Info
Tanja Vujicic - PISA for Schools contact InfoEduSkills OECD Tanja Vujicic, Senior Analyst and PISA for School’s Project Manager at the OECD spoke at the OECD webinar 'Turning insights into impact: What do early case studies reveal about the power of PISA for Schools?' on 20 June 2025
PISA for Schools is an OECD assessment that evaluates 15-year-old performance on reading, mathematics, and science. It also gathers insights into students’ learning environment, engagement and well-being, offering schools valuable data that help them benchmark performance internationally and improve education outcomes. A central ambition, and ongoing challenge, has been translating these insights into meaningful actions that drives lasting school improvement.
LDMMIA Shop & Student News Summer Solstice 25
LDMMIA Shop & Student News Summer Solstice 25LDM & Mia eStudios 6/18/25
Shop, Upcoming: Final Notes to Review as we Close Level One. Make sure to review the orientation and videos as well. There’s more to come and material to cover in Levels 2-3. The content will be a combination of Reiki and Yoga. Also energy topics of our spiritual collective.
Thanks again all future Practitioner Level Students. Our Levels so far are: Guest, Grad, and Practitioner. We have had over 5k Spring Views.
https://ldm-mia.creator-spring.com
Plate Tectonic Boundaries and Continental Drift Theory
Plate Tectonic Boundaries and Continental Drift TheoryMarie This 28 slide presentation covers the basics of plate tectonics and continental drift theory. It is an effective introduction into a full plate tectonics unit study, but does not cover faults, stress, seismic waves, or seafloor spreading.
To download PDF, visit The Homeschool Daily. We will be uploading more slideshows to follow this one. Blessings, Marie
A Visual Introduction to the Prophet Jeremiah
A Visual Introduction to the Prophet JeremiahSteve Thomason These images will give you a visual guide to both the context and the flow of the story of the prophet Jeremiah. Feel free to use these in your study, preaching, and teaching.
Romanticism in Love and Sacrifice An Analysis of Oscar Wilde’s The Nightingal...
Romanticism in Love and Sacrifice An Analysis of Oscar Wilde’s The Nightingal...KaryanaTantri21 The story revolves around a college student who despairs not having a red rose as a condition for dancing with the girl he loves. The nightingale hears his complaint and offers to create the red rose at the cost of his life. He sang a love song all night with his chest stuck to the thorns of the rose tree. Finally, the red rose grew, but his sacrifice was in vain. The girl rejected the flower because it didn’t match her outfit and preferred a jewellery gift. The student threw the flower on the street and returned to studying philosophy
Paper 107 | From Watchdog to Lapdog: Ishiguro’s Fiction and the Rise of “Godi...
Paper 107 | From Watchdog to Lapdog: Ishiguro’s Fiction and the Rise of “Godi...Rajdeep Bavaliya Dive into a captivating analysis where Kazuo Ishiguro’s nuanced fiction meets the stark realities of post‑2014 Indian journalism. Uncover how “Godi Media” turned from watchdog to lapdog, echoing the moral compromises of Ishiguro’s protagonists. We’ll draw parallels between restrained narrative silences and sensationalist headlines—are our media heroes or traitors? Don’t forget to follow for more deep dives!
M.A. Sem - 2 | Presentation
Presentation Season - 2
Paper - 107: The Twentieth Century Literature: From World War II to the End of the Century
Submitted Date: April 4, 2025
Paper Name: The Twentieth Century Literature: From World War II to the End of the Century
Topic: From Watchdog to Lapdog: Ishiguro’s Fiction and the Rise of “Godi Media” in Post-2014 Indian Journalism
[Please copy the link and paste it into any web browser to access the content.]
Video Link: https://youtu.be/kIEqwzhHJ54
For a more in-depth discussion of this presentation, please visit the full blog post at the following link: https://rajdeepbavaliya2.blogspot.com/2025/04/from-watchdog-to-lapdog-ishiguro-s-fiction-and-the-rise-of-godi-media-in-post-2014-indian-journalism.html
Please visit this blog to explore additional presentations from this season:
Hashtags:
#GodiMedia #Ishiguro #MediaEthics #WatchdogVsLapdog #IndianJournalism #PressFreedom #LiteraryCritique #AnArtistOfTheFloatingWorld #MediaCapture #KazuoIshiguro
Keyword Tags:
Godi Media, Ishiguro fiction, post-2014 Indian journalism, media capture, Kazuo Ishiguro analysis, watchdog to lapdog, press freedom India, media ethics, literature and media, An Artist of the Floating World
K12 Tableau User Group virtual event June 18, 2025
K12 Tableau User Group virtual event June 18, 2025dogden2 National K12 Tableau User Group: June 2025 meeting slides
Sustainable Innovation with Immersive Learning
Sustainable Innovation with Immersive LearningLeonel Morgado Prof. Leonel and Prof. Dennis approached educational uses, practices, and strategies of using immersion as a lens to interpret, design, and planning educational activities in a sustainable way. Rather than one-off gimmicks, the intent is to enable instructors (and institutions) to be able to include them in their regular activities, including the ability to evaluate and redesign them.
Immersion as a phenomenon enables interpreting pedagogical activities in a learning-agnostic way: you take a stance on the learning theory to follow, and leverage immersion to envision and guide your practice.
VCE Literature Section A Exam Response Guide
VCE Literature Section A Exam Response Guidejpinnuck This practical guide shows students of Unit 3&4 VCE Literature how to write responses to Section A of the exam. Including a range of examples writing about different types of texts, this guide:
*Breaks down and explains what Q1 and Q2 tasks involve and expect
*Breaks down example responses for each question
*Explains and scaffolds students to write responses for each question
*Includes a comprehensive range of sentence starters and vocabulary for responding to each question
*Includes critical theory vocabulary lists to support Q2 responses
Aprendendo Arquitetura Framework Salesforce - Dia 02
Aprendendo Arquitetura Framework Salesforce - Dia 02Mauricio Alexandre Silva Aprendendo Arquitetura Framework Salesforce - Dia 02
INDUCTIVE EFFECT slide for first prof pharamacy students
INDUCTIVE EFFECT slide for first prof pharamacy studentsSHABNAM FAIZ The inductive effect is the electron-withdrawing or electron-donating effect transmitted through sigma (σ) bonds in a molecule due to differences in electronegativity between atoms.
---
🔹 Definition:
The inductive effect is the permanent shifting of electrons in a sigma bond caused by the electronegativity difference of atoms, resulting in partial charges within the molecule.
Great Governors' Send-Off Quiz 2025 Prelims IIT KGP
Great Governors' Send-Off Quiz 2025 Prelims IIT KGPIIT Kharagpur Quiz Club Prelims of the Great Governors' Send-Off Quiz 2025 hosted by the outgoing governors.
QMs: Aarushi, Aatir, Aditya, Arnav
Code Profiling in Odoo 18 - Odoo 18 Slides
Code Profiling in Odoo 18 - Odoo 18 SlidesCeline George Profiling in Odoo identifies slow code and resource-heavy processes, ensuring better system performance. Odoo code profiling detects bottlenecks in custom modules, making it easier to improve speed and scalability.
IIT KGP Quiz Week 2024 Sports Quiz (Prelims + Finals)
IIT KGP Quiz Week 2024 Sports Quiz (Prelims + Finals)IIT Kharagpur Quiz Club The document outlines the format for the Sports Quiz at Quiz Week 2024, covering various sports & games and requiring participants to Answer without external sources. It includes specific details about question types, scoring, and examples of quiz questions. The document emphasizes fair play and enjoyment of the quiz experience.
LAZY SUNDAY QUIZ "A GENERAL QUIZ" JUNE 2025 SMC QUIZ CLUB, SILCHAR MEDICAL CO...
LAZY SUNDAY QUIZ "A GENERAL QUIZ" JUNE 2025 SMC QUIZ CLUB, SILCHAR MEDICAL CO...Ultimatewinner0342 🧠 Lazy Sunday Quiz | General Knowledge Trivia by SMC Quiz Club – Silchar Medical College
Presenting the Lazy Sunday Quiz, a fun and thought-provoking general knowledge quiz created by the SMC Quiz Club of Silchar Medical College & Hospital (SMCH). This quiz is designed for casual learners, quiz enthusiasts, and competitive teams looking for a diverse, engaging set of questions with clean visuals and smart clues.
🎯 What is the Lazy Sunday Quiz?
The Lazy Sunday Quiz is a light-hearted yet intellectually rewarding quiz session held under the SMC Quiz Club banner. It’s a general quiz covering a mix of current affairs, pop culture, history, India, sports, medicine, science, and more.
Whether you’re hosting a quiz event, preparing a session for students, or just looking for quality trivia to enjoy with friends, this PowerPoint deck is perfect for you.
📋 Quiz Format & Structure
Total Questions: ~50
Types: MCQs, one-liners, image-based, visual connects, lateral thinking
Rounds: Warm-up, Main Quiz, Visual Round, Connects (optional bonus)
Design: Simple, clear slides with answer explanations included
Tools Needed: Just a projector or screen – ready to use!
🧠 Who Is It For?
College quiz clubs
School or medical students
Teachers or faculty for classroom engagement
Event organizers needing quiz content
Quizzers preparing for competitions
Freelancers building quiz portfolios
💡 Why Use This Quiz?
Ready-made, high-quality content
Curated with lateral thinking and storytelling in mind
Covers both academic and pop culture topics
Designed by a quizzer with real event experience
Usable in inter-college fests, informal quizzes, or Sunday brain workouts
📚 About the Creators
This quiz has been created by Rana Mayank Pratap, an MBBS student and quizmaster at SMC Quiz Club, Silchar Medical College. The club aims to promote a culture of curiosity and smart thinking through weekly and monthly quiz events.
🔍 SEO Tags:
quiz, general knowledge quiz, trivia quiz, SlideShare quiz, college quiz, fun quiz, medical college quiz, India quiz, pop culture quiz, visual quiz, MCQ quiz, connect quiz, science quiz, current affairs quiz, SMC Quiz Club, Silchar Medical College
📣 Reuse & Credit
You’re free to use or adapt this quiz for your own events or sessions with credit to:
SMC Quiz Club – Silchar Medical College & Hospital
Curated by: Rana Mayank Pratap
How to use search fetch method in Odoo 18
How to use search fetch method in Odoo 18Celine George The search_fetch is a powerful ORM method used in Odoo for some specific addons to combine the functionality of search and read for more efficient data fetching. It might be used to search for records and fetch specific fields in a single call. It stores the result in the cache memory.
THE PSYCHOANALYTIC OF THE BLACK CAT BY EDGAR ALLAN POE (1).pdf
THE PSYCHOANALYTIC OF THE BLACK CAT BY EDGAR ALLAN POE (1).pdfnabilahk908 Psychoanalytic Analysis of The Black Cat by Edgar Allan Poe explores the deep psychological dimensions of the narrator’s disturbed mind through the lens of Sigmund Freud’s psychoanalytic theory. According to Freud (1923), the human psyche is structured into three components: the Id, which contains primitive and unconscious desires; the Ego, which operates on the reality principle and mediates between the Id and the external world; and the Superego, which reflects internalized moral standards.
In this story, Poe presents a narrator who experiences a psychological breakdown triggered by repressed guilt, aggression, and internal conflict. This analysis focuses not only on the gothic horror elements of the narrative but also on the narrator’s mental instability and emotional repression, demonstrating how the imbalance of these three psychic forces contributes to his downfall.
Ad
Modified aes algorithm using multiple s boxes
- 1. 1 Modified AES Algorithm Using Multiple S-Boxes Instructor: Truong Tuan Anh, PhD S: Chu Xuân Tình - 1870583
- 2. 2 Modified AES Algorithm Using Multiple S-Boxes 1. Introduction 2. Advance Encryption Standard (AES) 3. Modified AES Algorithm 4. Avaluation AES - Modifier
- 3. 3 AES - introdution Ø In 2000, the NIST formally adopted the AES encryption algorithm and published it as a federal standard under the designation FIPS-197. Ø It was chosen because of its security, performance, efficiency, implement ability, and low memory requirements. • Rijndael was selected as the AES – Designed by Vincent Rijmen and Joan Daemen in Belgium
- 4. 4 AES - introdution Ø The AES Cipher - Rijndael • An iterative – processes data as block of 4 columns of 4 bytes (128 bits) – operates on entire data block in every round • Rijndael design: – simplicity – has 128/192/256 bit keys, 128 bits data – resistant against known attacks – speed and code compactness on many CPUs • The MixColumn function in the AES algorithm is an important property of the cipher
- 5. 5 AES - introdution Ø The MixColumn function in the AES algorithm is an important property of the cipher ü It provides strength against differential and linear attacks due to the complexity of its mathematical operations. ü Require computational resources in software implementation. ü Replacing the MixColumn function, the speed performance of the AES algorithm will be improved. ü Propose for a modified AES algorithm using multiple S-Boxes.
- 7. AES - Basic 7 AES Plaintext (128 bits) Ciphertext (128 bits) Key (128-256 bits) AES Conceptual Scheme
- 8. AES - Basic 8 Ø Multiple rounds • Rounds are (almost) identical – First and last round are a little different
- 9. High Level Description No MixColumns
- 10. AES - Overall Structure
- 11. AES - Cipher
- 12. AES -128-bit values 12 • Data block viewed as 4-by-4 table of bytes • Represented as 4 by 4 matrix of 8-bit bytes. • Key is expanded to array of 32 bits words 1 byte
- 13. AES - Data Unit
- 14. AES - Unit Transformation
- 15. AES - Changing Plaintext to State
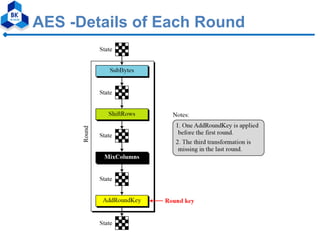
- 16. AES -Details of Each Round
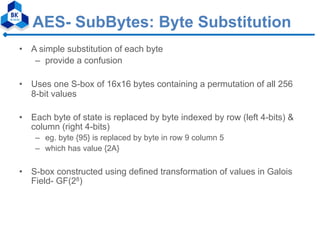
- 17. AES- SubBytes: Byte Substitution • A simple substitution of each byte – provide a confusion • Uses one S-box of 16x16 bytes containing a permutation of all 256 8-bit values • Each byte of state is replaced by byte indexed by row (left 4-bits) & column (right 4-bits) – eg. byte {95} is replaced by byte in row 9 column 5 – which has value {2A} • S-box constructed using defined transformation of values in Galois Field- GF(28)
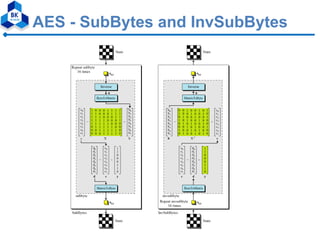
- 18. AES - SubBytes and InvSubBytes
- 19. AES - SubBytes Operation • The SubBytes operation involves 16 independent byte- to-byte transformations. • Interpret the byte as two hexadecimal digits xy • SW implementation, use row (x) and column (y) as lookup pointer S1,1 = xy16 x’y’16
- 20. AES - SubBytes Table • Implement by Table Lookup
- 21. AES - InvSubBytes Table
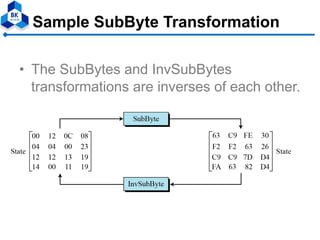
- 22. Sample SubByte Transformation • The SubBytes and InvSubBytes transformations are inverses of each other.
- 23. AES - ShiftRows • Shifting, which permutes the bytes. • A circular byte shift in each each – 1st row is unchanged – 2nd row does 1 byte circular shift to left – 3rd row does 2 byte circular shift to left – 4th row does 3 byte circular shift to left • In the encryption, the transformation is called ShiftRows • In the decryption, the transformation is called InvShiftRows and the shifting is to the right
- 24. AES - ShiftRows Scheme
- 25. AES - ShiftRows and InvShiftRows
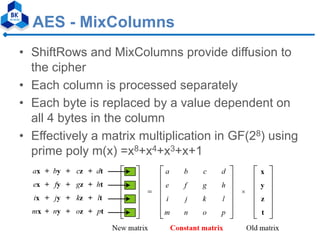
- 26. AES - MixColumns • ShiftRows and MixColumns provide diffusion to the cipher • Each column is processed separately • Each byte is replaced by a value dependent on all 4 bytes in the column • Effectively a matrix multiplication in GF(28) using prime poly m(x) =x8+x4+x3+x+1
- 27. AES -MixClumns Scheme The MixColumns transformation operates at the column level; it transforms each column of the state to a new column.
- 29. AES - AddRoundKey • XOR state with 128-bits of the round key • AddRoundKey proceeds one column at a time. – adds a round key word with each state column matrix – the operation is matrix addition • Inverse for decryption identical – since XOR own inverse, with reversed keys • Designed to be as simple as possible
- 30. AES - AddRoundKey Scheme
- 31. AES Round
- 32. AES Key Scheduling • takes 128-bits (16-bytes) key and expands into array of 44 32-bit words
- 33. AES -Key Expansion Scheme
- 34. AES -Key Expansion submodule • RotWord performs a one byte circular left shift on a word For example: RotWord[b0,b1,b2,b3] = [b1,b2,b3,b0] • SubWord performs a byte substitution on each byte of input word using the S-box • SubWord(RotWord(temp)) is XORed with RCon[j] – the round constant
- 35. AES Security • AES was designed after DES. • Most of the known attacks on DES were already tested on AES. • Brute-Force Attack – AES is definitely more secure than DES due to the larger-size key. • Statistical Attacks – Numerous tests have failed to do statistical analysis of the ciphertext • Differential and Linear Attacks – There are no differential and linear attacks on AES as yet.
- 36. AES ALGORITHM USING MULTIPLE S-BOXES vPROPOSED MODIFIED 128-AES ALGORITHM USING MULTIPLE S-BOXES Ø The MixColumns function is perceive to be requiring more computational resources in software implementation as compared to the other functions Ø Propose for a modified version of the 128-AES algorithm using two substitution boxes ü The first S-Box is the Rijndael S-Box ü The second S-Box is constructed using XOR operation and affine transformation
- 37. AES ALGORITHM USING MULTIPLE S-BOXES
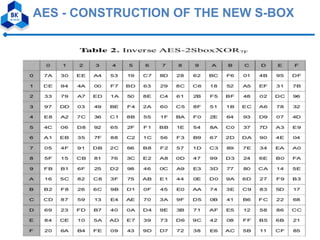
- 38. AES - CONSTRUCTION OF THE NEW S-BOX vThe second S-Box is derived from the original S- Box as designed in the AES ØExclusive OR Operation § each cell in the AES-Rijndael will be XORed with 7F AES-Rijndael[x,y] XOR (7F) § The Key[i] shall be any hexadecimal value between 00 to FF (Table 1. AES- 2SboxXOR7F)
- 39. AES - CONSTRUCTION OF THE NEW S-BOX
- 40. AES - CONSTRUCTION OF THE NEW S-BOX vThe second S-Box is derived from the original S- Box as designed in the AES ØExclusive OR Operation ØAffine Transform Operation ü After creating the initial values of AES- 2SboxXOR ü Scramble the bits in each byte value, we next apply the following transformation to each bit bi as stored in the initial AES-2SboxXOR7F:
- 41. AES - CONSTRUCTION OF THE NEW S-BOX ØAffine Transform Operation ü For the inverse AES-2SboxXOR, the following transformation to each bit was used for bit scrambling:
- 42. AES - CONSTRUCTION OF THE NEW S-BOX
- 46. CONCLUSION üModified AES algorithm using multiple S-boxes. üWe observed that the speed performance greatly increased in the modified AES algorithm using multiple S-Boxes, while the security side has slightly weakened. üEasily implemented using cheap processors and a minimum amount of memory. üVery efficient 49
- 47. Referents • [1] National Institute of Standards and Technology, Advanced Encryption Standard, FIPS 197 (2011). • [2] Paper “Modified AES Algorithm Using Multiple S-Boxes” • [3] Wiki & slide & Internet. 50
- 48. 51 Thanks for your attention!
