OAuth2 Implementation Presentation (Java)
Download as pptx, pdf0 likes162 views
The document outlines the implementation of OAuth 2.0 and its significance in securing API access through a framework allowing third-party applications to access resources with user permission. It covers key concepts such as authorization roles, grant types, the authorization process, and differences between OAuth 1.0 and 2.0. Additionally, it emphasizes the importance of etiquette during sessions and provides guidance on submitting feedback and minimizing disturbances.
1 of 21
Downloaded 20 times



















Ad
Recommended
O auth
O authAshok Kumar N OAuth 2.0 is an authorization framework that allows third-party applications to obtain limited access to a user's data on another service, either on behalf of the user by facilitating an approval interaction or by obtaining access on its own behalf. It addresses the issue of sharing user credentials by introducing an authorization layer and separating the client from the resource owner. The client requests access to resources controlled by the resource owner and hosted by the resource server, and is issued a token rather than the user's credentials.
OAuth 2 Spring Boot 3 Integration Presentation
OAuth 2 Spring Boot 3 Integration PresentationKnoldus Inc. The document covers the integration of OAuth2 with Spring Boot 3, emphasizing its role as an open-standard authorization framework that enhances user security by allowing applications to access user data without exposing login credentials. It details the components of OAuth2, various authorization flows, and scopes that define access permissions, while stressing best practices for secure implementation. Additionally, it highlights real-world use cases of OAuth2, such as mobile app authentication and API protection.
Oauth2 and OWSM OAuth2 support
Oauth2 and OWSM OAuth2 supportGaurav Sharma The document discusses OAuth 2.0 and how it addresses issues with traditional approaches to authorizing third party access to user accounts and resources. It provides an overview of OAuth 2.0 concepts like authorization grants, access tokens, refresh tokens, and the roles of the client, resource owner, authorization server and resource server. It then describes the authorization code grant flow and client credentials flow in more detail through examples. The goal is to explain how OAuth 2.0 works and how it can be used to securely authorize access to resources while avoiding the risks of directly sharing user credentials.
OAuth2
OAuth2SPARK MEDIA The document discusses OAuth 2.0 and JSON Web Tokens (JWT). It defines OAuth 2.0 as the industry standard framework for authorization that enables third party applications to obtain limited access to HTTP services. It describes the common roles in OAuth 2.0 including the resource owner, resource server, client, and authorization server. It also explains the different token types used in OAuth like access tokens and refresh tokens. Finally, it provides an overview of JSON Web Tokens, defining them as a way to securely transmit information between parties as a JSON object using digital signatures.
Spring Security
Spring SecurityKnoldus Inc. Spring Security is a framework that provides authentication and authorization to create secure Java applications. It targets authentication and authorization of web requests, methods, and access to domains. OAuth 2.0 is an authorization framework that allows clients limited access to protected resources owned by a resource owner. It has four main roles: resource owner, client, authorization server, and resource server. The authorization server issues access tokens to clients which can then be used to request protected resources from the resource server on behalf of the authenticated resource owner. OAuth 2.0 offers advantages like flexibility, ability to share data without releasing personal information, use of tokenization for limited access, and ease of implementation with strong authentication.
An introduction to OAuth 2
An introduction to OAuth 2Sanjoy Kumar Roy This document provides an introduction and overview of OAuth 2.0. It discusses the key components and actors in the OAuth framework, including clients, protected resources, resource owners, and authorization servers. It describes the major steps of an OAuth transaction, issuing and using tokens. Specifically, it outlines the authorization code grant flow, how clients request and receive access tokens from authorization servers to access protected resources on behalf of resource owners. It also defines common OAuth concepts like scopes, refresh tokens, and authorization grants.
Spring4 security oauth2
Spring4 security oauth2Sang Shin The document discusses OAuth2 and the authorization code flow. OAuth2 is a protocol for authorization that allows clients to obtain limited access to user accounts and reduces the scope of access. It involves four main actors: a resource owner (user), client app, authorization server, and resource server. The authorization code flow involves the client redirecting the user to the authorization server to log in, the user authorizing access, and the authorization server issuing an authorization code to the client, which can then request an access token to access protected resources from the resource server on the user's behalf.
Spring4 security oauth2
Spring4 security oauth2axykim00 OAuth2 is a protocol for authorization that allows clients to access user resources stored on a resource server. It separates the client application from the resource owner credentials. The authorization code flow involves a client redirecting a user to an authorization server, the user authenticating and authorizing access, and the authorization server returning an authorization code to the client which can then request an access token to access protected resources from the resource server on the user's behalf, without exposing the user's credentials directly. This flow allows for single sign-on across microservices and fine-grained authorization of delegated access to resources.
Demystifying OAuth 2.0
Demystifying OAuth 2.0Karl McGuinness The document explains OAuth 2.0 as a delegated authorization framework designed for REST and APIs, enabling apps to access user data without sharing passwords. It discusses various OAuth flows, security considerations, and modern use cases, emphasizing the distinction between authorization and authentication. Additionally, it covers the integration of OpenID Connect, extending OAuth 2.0 for user identity and session management.
OAuth2 + API Security
OAuth2 + API SecurityAmila Paranawithana The document discusses OAuth 2.0 and how it provides a method for third party applications to access private resources from an API, while allowing the resource owners to authorize access without sharing credentials. It describes the four main roles in OAuth 2.0 - resource owner, client, authorization server, and resource server. It also summarizes the three main authorization flows - authorization code, implicit, and client credentials flows. The document provides details on how each flow works, including the request and response parameters.
(1) OAuth 2.0 Overview
(1) OAuth 2.0 Overviewanikristo OAuth 2.0 provides several authorization flows for developers including the web server flow. It has advantages like wide adoption and new authorization types but also disadvantages such as lack of interoperability between implementations and potential security issues if SSL is not used. The web server flow involves authenticating the client, obtaining an authorization code from the resource owner, exchanging the code for an access token, using the access token to access resources, and refreshing tokens as needed. OAuth 1.0 adds security features like digital signatures and nonces/timestamps but requires more complex implementation.
OAuth 2
OAuth 2ChrisWood262 OAuth 2 is an authorization framework that allows applications to access user data and perform actions on their behalf. It defines flows for applications to request access, and provides short-lived credentials in response. The main roles in OAuth are the resource owner (user), client (application), resource server (API), and authorization server (issues tokens). Common grant types include authorization code, implicit, and client credentials flows. Tokens returned include access and refresh tokens, and OpenID Connect adds optional ID tokens containing user information.
ConFoo 2015 - Securing RESTful resources with OAuth2
ConFoo 2015 - Securing RESTful resources with OAuth2Rodrigo Cândido da Silva The document discusses securing RESTful resources using OAuth 2.0, highlighting its importance, concepts, and implementation strategies. It covers the evolution of OAuth, its grant types, and Java implementations, emphasizing the benefits and complexities associated with using OAuth 2.0 for authentication and authorization of APIs. Additionally, it provides practical insights and references for further exploration of OAuth 2.0 security practices.
Stateless Auth using OAUTH2 & JWT
Stateless Auth using OAUTH2 & JWTMobiliya The document discusses stateless authentication using OAuth2 and JWT, explaining the concepts of authentication, authorization, and single sign-on (SSO). It provides an in-depth look at OAuth2, detailing its actors, various grant flows, and the implementation of JWT as a token standard for secure authorization. Additionally, it outlines how to implement OAuth2 services, the differences between grant types, and the necessary setup for stateless authorization.
Stateless Auth using OAuth2 & JWT
Stateless Auth using OAuth2 & JWTGaurav Roy The document discusses stateless authorization using OAuth2 and JSON Web Tokens (JWT). It begins with an introduction to authentication, authorization, and single sign-on (SSO). It then provides an in-depth explanation of OAuth2 actors, flows, and grant types. The Authorization Code Grant flow and Implicit Grant flow are explained in detail. Finally, it introduces JWT and why it is a suitable standard for representing OAuth2 access tokens since it meets the requirements and libraries are available.
Lecture #25 : Oauth 2.0
Lecture #25 : Oauth 2.0Dr. Ramchandra Mangrulkar The document summarizes OAuth 2.0, an open standard for authorization. It describes the traditional client-server authentication model and its limitations that OAuth addresses. OAuth defines four roles in the authorization process and four grant types. It explains the authorization code grant type in five steps: the client requests authorization, the user authorizes access, the client receives an authorization code, the client requests an access token, and receives the access token. The document provides homework on further reading about OAuth authorization code flow and other grant types.
Devteach 2017 OAuth and Open id connect demystified
Devteach 2017 OAuth and Open id connect demystifiedTaswar Bhatti The document provides an extensive overview of OAuth 2.0 and OpenID Connect, discussing their roles in secure authorization and authentication, respectively. It outlines various OAuth flows, token types, and misconceptions surrounding the usage of OAuth, emphasizing its focus on delegation rather than traditional access control. Additionally, the document explains the JWT structure and introduces OpenID Connect as a means for single sign-on, building on OAuth 2.0's framework.
Oauth2.0 tutorial
Oauth2.0 tutorialHarikaReddy115 OAuth 2.0 is an open authorization protocol that allows clients to access user resources stored on another site, without using the user's credentials. It uses authorization tokens instead of passwords. The OAuth 2.0 architecture involves a client application requesting authorization from the resource owner to access protected resources from an authorization server. If authorized, the client receives an access token to access the protected resources on behalf of the resource owner.
O auth 2.0 authorization framework
O auth 2.0 authorization frameworkJohn Temoty Roca This document explains the OAuth 2.0 authorization framework, highlighting its objectives, key roles, and protocol flow. It contrasts traditional client-server authentication models with OAuth 2.0's benefits, including enhanced access control for resource owners. The document also outlines various authorization grants and protocols used within the framework.
OAuth
OAuthTom Elrod OAuth is an open standard for authorization that allows users to share private resources stored on one server with another server. It provides a process for users to authorize third-party access to their server resources without sharing credentials. OAuth has gone through several versions to address security issues and limitations of previous versions. OAuth involves resource owners, clients, and an authorization server, and defines common flows for authorization like authorization code flow and refresh token flow.
oauth-for-credentials-security-in-rest-api-access
oauth-for-credentials-security-in-rest-api-accessidsecconf The document discusses OAuth, an open standard for authorization in REST APIs. It allows users to grant third party applications access to their private data without sharing their usernames and passwords. OAuth uses tokens instead of passwords, allowing users to control what data apps can access and revoke access at any time. The OAuth process involves a consumer obtaining a request token, then redirecting the user to authorize access, and exchanging the request token for an access token to access private resources on the user's behalf according to their authorization.
Spring security oauth2
Spring security oauth2axykim00 OAuth2 is a protocol for authorization that allows clients limited access to user accounts and specifies four methods for obtaining an access token, including the authorization code flow. The authorization code flow involves a client redirecting a user to an authorization server, the user authorizing access, and the authorization server issuing an authorization code to the client, which can then request an access token to access a resource server on the user's behalf, while avoiding exposing the user's credentials directly.
Microservice security with spring security 5.1,Oauth 2.0 and open id connect
Microservice security with spring security 5.1,Oauth 2.0 and open id connect Nilanjan Roy This document provides an overview of microservice security using Spring Security 5.1, OAuth 2.0, and OpenID Connect. It defines OAuth 2.0 and its authorization framework, describing how applications can be authorized to access user data. It outlines the authorization code grant flow and other grant types, including how applications register and use client IDs and secrets. JSON Web Tokens are discussed as an access token format. OpenID Connect is described as extending OAuth 2.0 to provide authentication via ID tokens. Key components like access tokens, refresh tokens, and the client credentials flow are also summarized.
slides-101-edu-sesse-introduction-to-oauth-20-01.pdf
slides-101-edu-sesse-introduction-to-oauth-20-01.pdfGopalKrishna703039 The document provides an introduction to OAuth 2.0, a delegation protocol enabling third-party applications to gain limited access to HTTP services on behalf of resource owners. It outlines the roles involved (resource owner, authorization server, client, protected resource), the authorization code flow, and various OAuth use cases and flows including implicit, client credentials, resource owner password, and assertion flows. Additionally, it discusses key concepts like tokens, scopes, and the framework's flexibility for different applications.
O auth2.0 guide
O auth2.0 guideDilip Mohapatra OAuth allows users to grant third-party access to their resources like API's and websites without sharing their passwords. It uses authorization codes to obtain access tokens securely. The document discusses OAuth concepts like actors, endpoints, grant types and flows in detail to explain how OAuth works and how to implement it using PingFederate as the authorization server.
OAuth
OAuthAdi Challa OAuth 2.0 is an open standard for authorization that allows third-party applications to securely access private user data from APIs, without requiring the user to share their username and password. It specifies a process for users to authorize applications to access their data on other servers, issuing access tokens that applications can use to make API requests on the user's behalf. OAuth addresses issues with passwords by allowing temporary, limited access without exposing user credentials.
Draft Ietf Oauth V2 12
Draft Ietf Oauth V2 12Vishal Shah This document describes the OAuth 2.0 authorization protocol. It defines roles such as resource owner, client, authorization server, and resource server. It outlines the abstract protocol flow where a client requests authorization from the resource owner, receives an authorization grant, exchanges it for an access token at the authorization server, and uses the access token to access protected resources from the resource server. The document also defines key concepts such as access tokens and authorization grants.
Extended Security with WSO2 API Management Platform
Extended Security with WSO2 API Management PlatformWSO2 Uvindra Jayasinha from WSO2 presented on extending security with the WSO2 API Management platform. He covered best practices for OAuth 2.0 access tokens, adding SAML single sign-on, federated identity with third-party providers, enforcing fine-grained entitlement policies, and accessing user attributes. The presentation explained key OAuth concepts like grant types, actors, and tokens. It also described using SAML assertions, XACML policies, and JWT claims to pass user information and control access.
Angular Hydration Presentation (FrontEnd)
Angular Hydration Presentation (FrontEnd)Knoldus Inc. The document discusses Angular hydration, a process that transforms server-rendered HTML into a fully interactive Angular application. It highlights the importance of hydration for improved performance, SEO, and user experience while outlining the implementation steps and potential constraints that may arise. Key etiquette for participants during sessions is also provided, emphasizing punctuality and minimizing disruptions.
Optimizing Test Execution: Heuristic Algorithm for Self-Healing
Optimizing Test Execution: Heuristic Algorithm for Self-HealingKnoldus Inc. The document discusses the challenges of traditional test execution in software development and the importance of optimized processes for enhancing efficiency and reliability. It introduces self-healing techniques, particularly heuristic algorithms that enable automated test scripts to adapt to changes in application interfaces, thereby improving test coverage and minimizing false positives. Specific heuristic algorithms, such as adaptive locator recovery and annotation-based locators, are outlined with best practices for implementation in automated testing environments.
More Related Content
Similar to OAuth2 Implementation Presentation (Java) (20)
Demystifying OAuth 2.0
Demystifying OAuth 2.0Karl McGuinness The document explains OAuth 2.0 as a delegated authorization framework designed for REST and APIs, enabling apps to access user data without sharing passwords. It discusses various OAuth flows, security considerations, and modern use cases, emphasizing the distinction between authorization and authentication. Additionally, it covers the integration of OpenID Connect, extending OAuth 2.0 for user identity and session management.
OAuth2 + API Security
OAuth2 + API SecurityAmila Paranawithana The document discusses OAuth 2.0 and how it provides a method for third party applications to access private resources from an API, while allowing the resource owners to authorize access without sharing credentials. It describes the four main roles in OAuth 2.0 - resource owner, client, authorization server, and resource server. It also summarizes the three main authorization flows - authorization code, implicit, and client credentials flows. The document provides details on how each flow works, including the request and response parameters.
(1) OAuth 2.0 Overview
(1) OAuth 2.0 Overviewanikristo OAuth 2.0 provides several authorization flows for developers including the web server flow. It has advantages like wide adoption and new authorization types but also disadvantages such as lack of interoperability between implementations and potential security issues if SSL is not used. The web server flow involves authenticating the client, obtaining an authorization code from the resource owner, exchanging the code for an access token, using the access token to access resources, and refreshing tokens as needed. OAuth 1.0 adds security features like digital signatures and nonces/timestamps but requires more complex implementation.
OAuth 2
OAuth 2ChrisWood262 OAuth 2 is an authorization framework that allows applications to access user data and perform actions on their behalf. It defines flows for applications to request access, and provides short-lived credentials in response. The main roles in OAuth are the resource owner (user), client (application), resource server (API), and authorization server (issues tokens). Common grant types include authorization code, implicit, and client credentials flows. Tokens returned include access and refresh tokens, and OpenID Connect adds optional ID tokens containing user information.
ConFoo 2015 - Securing RESTful resources with OAuth2
ConFoo 2015 - Securing RESTful resources with OAuth2Rodrigo Cândido da Silva The document discusses securing RESTful resources using OAuth 2.0, highlighting its importance, concepts, and implementation strategies. It covers the evolution of OAuth, its grant types, and Java implementations, emphasizing the benefits and complexities associated with using OAuth 2.0 for authentication and authorization of APIs. Additionally, it provides practical insights and references for further exploration of OAuth 2.0 security practices.
Stateless Auth using OAUTH2 & JWT
Stateless Auth using OAUTH2 & JWTMobiliya The document discusses stateless authentication using OAuth2 and JWT, explaining the concepts of authentication, authorization, and single sign-on (SSO). It provides an in-depth look at OAuth2, detailing its actors, various grant flows, and the implementation of JWT as a token standard for secure authorization. Additionally, it outlines how to implement OAuth2 services, the differences between grant types, and the necessary setup for stateless authorization.
Stateless Auth using OAuth2 & JWT
Stateless Auth using OAuth2 & JWTGaurav Roy The document discusses stateless authorization using OAuth2 and JSON Web Tokens (JWT). It begins with an introduction to authentication, authorization, and single sign-on (SSO). It then provides an in-depth explanation of OAuth2 actors, flows, and grant types. The Authorization Code Grant flow and Implicit Grant flow are explained in detail. Finally, it introduces JWT and why it is a suitable standard for representing OAuth2 access tokens since it meets the requirements and libraries are available.
Lecture #25 : Oauth 2.0
Lecture #25 : Oauth 2.0Dr. Ramchandra Mangrulkar The document summarizes OAuth 2.0, an open standard for authorization. It describes the traditional client-server authentication model and its limitations that OAuth addresses. OAuth defines four roles in the authorization process and four grant types. It explains the authorization code grant type in five steps: the client requests authorization, the user authorizes access, the client receives an authorization code, the client requests an access token, and receives the access token. The document provides homework on further reading about OAuth authorization code flow and other grant types.
Devteach 2017 OAuth and Open id connect demystified
Devteach 2017 OAuth and Open id connect demystifiedTaswar Bhatti The document provides an extensive overview of OAuth 2.0 and OpenID Connect, discussing their roles in secure authorization and authentication, respectively. It outlines various OAuth flows, token types, and misconceptions surrounding the usage of OAuth, emphasizing its focus on delegation rather than traditional access control. Additionally, the document explains the JWT structure and introduces OpenID Connect as a means for single sign-on, building on OAuth 2.0's framework.
Oauth2.0 tutorial
Oauth2.0 tutorialHarikaReddy115 OAuth 2.0 is an open authorization protocol that allows clients to access user resources stored on another site, without using the user's credentials. It uses authorization tokens instead of passwords. The OAuth 2.0 architecture involves a client application requesting authorization from the resource owner to access protected resources from an authorization server. If authorized, the client receives an access token to access the protected resources on behalf of the resource owner.
O auth 2.0 authorization framework
O auth 2.0 authorization frameworkJohn Temoty Roca This document explains the OAuth 2.0 authorization framework, highlighting its objectives, key roles, and protocol flow. It contrasts traditional client-server authentication models with OAuth 2.0's benefits, including enhanced access control for resource owners. The document also outlines various authorization grants and protocols used within the framework.
OAuth
OAuthTom Elrod OAuth is an open standard for authorization that allows users to share private resources stored on one server with another server. It provides a process for users to authorize third-party access to their server resources without sharing credentials. OAuth has gone through several versions to address security issues and limitations of previous versions. OAuth involves resource owners, clients, and an authorization server, and defines common flows for authorization like authorization code flow and refresh token flow.
oauth-for-credentials-security-in-rest-api-access
oauth-for-credentials-security-in-rest-api-accessidsecconf The document discusses OAuth, an open standard for authorization in REST APIs. It allows users to grant third party applications access to their private data without sharing their usernames and passwords. OAuth uses tokens instead of passwords, allowing users to control what data apps can access and revoke access at any time. The OAuth process involves a consumer obtaining a request token, then redirecting the user to authorize access, and exchanging the request token for an access token to access private resources on the user's behalf according to their authorization.
Spring security oauth2
Spring security oauth2axykim00 OAuth2 is a protocol for authorization that allows clients limited access to user accounts and specifies four methods for obtaining an access token, including the authorization code flow. The authorization code flow involves a client redirecting a user to an authorization server, the user authorizing access, and the authorization server issuing an authorization code to the client, which can then request an access token to access a resource server on the user's behalf, while avoiding exposing the user's credentials directly.
Microservice security with spring security 5.1,Oauth 2.0 and open id connect
Microservice security with spring security 5.1,Oauth 2.0 and open id connect Nilanjan Roy This document provides an overview of microservice security using Spring Security 5.1, OAuth 2.0, and OpenID Connect. It defines OAuth 2.0 and its authorization framework, describing how applications can be authorized to access user data. It outlines the authorization code grant flow and other grant types, including how applications register and use client IDs and secrets. JSON Web Tokens are discussed as an access token format. OpenID Connect is described as extending OAuth 2.0 to provide authentication via ID tokens. Key components like access tokens, refresh tokens, and the client credentials flow are also summarized.
slides-101-edu-sesse-introduction-to-oauth-20-01.pdf
slides-101-edu-sesse-introduction-to-oauth-20-01.pdfGopalKrishna703039 The document provides an introduction to OAuth 2.0, a delegation protocol enabling third-party applications to gain limited access to HTTP services on behalf of resource owners. It outlines the roles involved (resource owner, authorization server, client, protected resource), the authorization code flow, and various OAuth use cases and flows including implicit, client credentials, resource owner password, and assertion flows. Additionally, it discusses key concepts like tokens, scopes, and the framework's flexibility for different applications.
O auth2.0 guide
O auth2.0 guideDilip Mohapatra OAuth allows users to grant third-party access to their resources like API's and websites without sharing their passwords. It uses authorization codes to obtain access tokens securely. The document discusses OAuth concepts like actors, endpoints, grant types and flows in detail to explain how OAuth works and how to implement it using PingFederate as the authorization server.
OAuth
OAuthAdi Challa OAuth 2.0 is an open standard for authorization that allows third-party applications to securely access private user data from APIs, without requiring the user to share their username and password. It specifies a process for users to authorize applications to access their data on other servers, issuing access tokens that applications can use to make API requests on the user's behalf. OAuth addresses issues with passwords by allowing temporary, limited access without exposing user credentials.
Draft Ietf Oauth V2 12
Draft Ietf Oauth V2 12Vishal Shah This document describes the OAuth 2.0 authorization protocol. It defines roles such as resource owner, client, authorization server, and resource server. It outlines the abstract protocol flow where a client requests authorization from the resource owner, receives an authorization grant, exchanges it for an access token at the authorization server, and uses the access token to access protected resources from the resource server. The document also defines key concepts such as access tokens and authorization grants.
Extended Security with WSO2 API Management Platform
Extended Security with WSO2 API Management PlatformWSO2 Uvindra Jayasinha from WSO2 presented on extending security with the WSO2 API Management platform. He covered best practices for OAuth 2.0 access tokens, adding SAML single sign-on, federated identity with third-party providers, enforcing fine-grained entitlement policies, and accessing user attributes. The presentation explained key OAuth concepts like grant types, actors, and tokens. It also described using SAML assertions, XACML policies, and JWT claims to pass user information and control access.
More from Knoldus Inc. (20)
Angular Hydration Presentation (FrontEnd)
Angular Hydration Presentation (FrontEnd)Knoldus Inc. The document discusses Angular hydration, a process that transforms server-rendered HTML into a fully interactive Angular application. It highlights the importance of hydration for improved performance, SEO, and user experience while outlining the implementation steps and potential constraints that may arise. Key etiquette for participants during sessions is also provided, emphasizing punctuality and minimizing disruptions.
Optimizing Test Execution: Heuristic Algorithm for Self-Healing
Optimizing Test Execution: Heuristic Algorithm for Self-HealingKnoldus Inc. The document discusses the challenges of traditional test execution in software development and the importance of optimized processes for enhancing efficiency and reliability. It introduces self-healing techniques, particularly heuristic algorithms that enable automated test scripts to adapt to changes in application interfaces, thereby improving test coverage and minimizing false positives. Specific heuristic algorithms, such as adaptive locator recovery and annotation-based locators, are outlined with best practices for implementation in automated testing environments.
Self-Healing Test Automation Framework - Healenium
Self-Healing Test Automation Framework - HealeniumKnoldus Inc. The document discusses Healenium, a self-healing test automation framework that uses machine learning to automatically update broken locators during runtime, ensuring consistent test execution in dynamic environments. It emphasizes the importance of self-healing in reducing test failures, decreasing flakiness, and improving test accuracy, while providing an overview of its features, integration methods, and challenges. Future trends in self-healing automation are also highlighted, indicating a shift towards more proactive and sophisticated algorithms.
Kanban Metrics Presentation (Project Management)
Kanban Metrics Presentation (Project Management)Knoldus Inc. The document discusses kanban metrics and principles, emphasizing the importance of etiquette in sessions, including punctuality and giving feedback. It details the history of kanban, particularly its origins in post-World War II Japan, and how it evolved from practices used in supermarkets to optimize manufacturing at Toyota. Key metrics for kanban in software development are also outlined, including lead time, cycle time, work in progress, and throughput, alongside the use of cumulative flow diagrams for workflow management.
Java 17 features and implementation.pptx
Java 17 features and implementation.pptxKnoldus Inc. Java 17, released in September 2021, is a long-term support (LTS) version that includes significant features such as pattern matching for switch, sealed classes, and improved memory management. This version enhances performance, security, and developer productivity, while promoting modern coding practices and compatibility with new libraries. Upgrading to Java 17 is crucial for developers to ensure stability and leverage its numerous enhancements for efficient application development.
Chaos Mesh Introducing Chaos in Kubernetes
Chaos Mesh Introducing Chaos in KubernetesKnoldus Inc. The document discusses chaos engineering, a method to find system weaknesses before they become major outages by simulating failures. It introduces Chaos Mesh, an open-source platform tailored for chaos experiments in Kubernetes, highlighting its features and various types of chaos experiments, such as pod and network failures. Key principles of chaos engineering include defining normal operation, hypothesizing impacts, introducing realistic faults, and observing system behavior.
GraalVM - A Step Ahead of JVM Presentation
GraalVM - A Step Ahead of JVM PresentationKnoldus Inc. The document presents an overview of GraalVM, highlighting its high-performance capabilities, resource efficiency, and polyglot support. It contrasts JIT (Just-In-Time) and AOT (Ahead-Of-Time) compilation methods, detailing the advantages and disadvantages of each. The content also includes etiquette for session participation, a demo outline, and performance benchmarks for applications compiled using GraalVM.
Nomad by HashiCorp Presentation (DevOps)
Nomad by HashiCorp Presentation (DevOps)Knoldus Inc. The document discusses HashiCorp's Nomad, a workload orchestrator designed for managing and deploying applications across various infrastructures. It highlights Nomad's simplicity, scalability, multi-datacenter support, and security features, comparing it with Kubernetes in terms of ease of use and workload support. Additionally, it outlines prerequisites for installation, architecture details, and key functionalities such as service discovery and job management.
Nomad by HashiCorp Presentation (DevOps)
Nomad by HashiCorp Presentation (DevOps)Knoldus Inc. The document outlines the etiquette and best practices for using HashiCorp's Nomad, a workload orchestrator designed to manage and deploy applications across infrastructures. It compares Nomad's simplicity and flexibility to Kubernetes, highlighting its capabilities in running various workloads, ease of integration with other HashiCorp tools, and robust architecture. Key features include multi-region and multi-datacenter support, scalability, security mechanisms, and the necessity of understanding specific prerequisites for implementation.
DAPR - Distributed Application Runtime Presentation
DAPR - Distributed Application Runtime PresentationKnoldus Inc. Dapr (Distributed Application Runtime) is a portable runtime designed to simplify the development of resilient microservices across cloud and edge environments, providing open APIs for various functionalities. Its core building blocks allow for extensibility and address common challenges in microservice architectures while ensuring observability and security through features such as end-to-end encryption and automated tracing. The document covers Dapr's configurations, resiliency management, and various use cases, including orchestration, edge computing, and integration with legacy systems.
Introduction to Azure Virtual WAN Presentation
Introduction to Azure Virtual WAN PresentationKnoldus Inc. Azure Virtual WAN is a comprehensive networking service that simplifies enterprise connectivity through a hub-and-spoke architecture, enhancing security and performance. It provides two main offerings, Basic and Standard, catering to different organizational needs, with features like VPN connectivity, advanced routing, and centralized management. This solution also facilitates optimal application performance and supports various use cases such as branch office connectivity and hybrid cloud integration.
Introduction to Argo Rollouts Presentation
Introduction to Argo Rollouts PresentationKnoldus Inc. This document discusses Argo Rollouts, an advanced open-source Kubernetes controller that enhances deployment strategies such as canary and blue-green deployments. It emphasizes best practices for using these deployments, including feedback submission, punctuality, and minimizing disturbances during sessions. The benefits of Argo Rollouts include reduced deployment risk, incremental updates, and automated rollbacks.
Intro to Azure Container App Presentation
Intro to Azure Container App PresentationKnoldus Inc. The document introduces Azure Container Apps, a serverless platform that supports deploying containerized applications while reducing infrastructure management. It outlines key features, benefits of microservices architecture, and compares Azure Container Apps with Kubernetes (AKS), emphasizing its user-friendly nature. Additionally, it discusses the functionality of the service, including scaling and integrations with open-source technologies like KEDA and Dapr.
Insights Unveiled Test Reporting and Observability Excellence
Insights Unveiled Test Reporting and Observability ExcellenceKnoldus Inc. The document discusses the significance of test reporting and observability in software development, detailing best practices, types of reports, and essential tools for effective implementation. It emphasizes the integration of test reporting with observability to provide a comprehensive understanding of system performance, address challenges, and improve collaboration among teams. Future trends highlight the role of AI, real-time reporting, and user-centric approaches in advancing these practices.
Introduction to Splunk Presentation (DevOps)
Introduction to Splunk Presentation (DevOps)Knoldus Inc. The document is an introduction to Splunk, detailing its features, functionality, and use cases. It emphasizes the importance of etiquette during sessions, such as punctuality and providing feedback. Splunk is a software platform that converts machine-generated data into actionable insights for businesses through data collection, analysis, and visualization.
Code Camp - Data Profiling and Quality Analysis Framework
Code Camp - Data Profiling and Quality Analysis FrameworkKnoldus Inc. The document outlines a data profiling and quality analysis framework aimed at enhancing data quality for effective test automation. It discusses the benefits, key components, and challenges of data profiling, as well as the role of AI and machine learning in improving data quality. Strategies for data quality improvement and best practices for effective data profiling and analysis are also provided to ensure accurate and reliable data management.
AWS: Messaging Services in AWS Presentation
AWS: Messaging Services in AWS PresentationKnoldus Inc. The document provides an overview of AWS messaging services, specifically Amazon SNS and SQS, highlighting their importance in distributed systems for decoupling components, scalability, reliability, and event-driven architecture. SNS is described as a push notification service for sending messages to multiple endpoints, while SQS is a pull-based message queuing service focusing on message persistence and processing. Key differences between SNS and SQS, along with use cases, polling methods, and pricing structures for both services, are also discussed.
Amazon Cognito: A Primer on Authentication and Authorization
Amazon Cognito: A Primer on Authentication and AuthorizationKnoldus Inc. The document outlines the Amazon Cognito service, which provides user identity management and data synchronization for mobile and web applications. It explains the features of user pools and identity pools, the benefits of using Amazon Cognito, and options for passwordless authentication. Additionally, it emphasizes the importance of etiquette during sessions, such as punctuality and submitting feedback.
ZIO Http A Functional Approach to Scalable and Type-Safe Web Development
ZIO Http A Functional Approach to Scalable and Type-Safe Web DevelopmentKnoldus Inc. The document outlines the etiquettes for attending a ZIO HTTP session led by Niloy Choudhury, emphasizing punctuality, providing feedback, and maintaining silence. It explains key concepts of ZIO HTTP, including routing, request handling, middleware, and server configuration, highlighting its type-safe approach for building robust HTTP servers. Overall, ZIO HTTP enables easy understanding, maintenance, and testing of server code.
Managing State & HTTP Requests In Ionic.
Managing State & HTTP Requests In Ionic.Knoldus Inc. The document discusses effective state management and HTTP requests in Ionic applications, emphasizing the importance of using RxJS subjects for centralized state handling. It outlines best practices for managing state, making HTTP requests, and ensuring secure and responsive applications. Additionally, it highlights the significance of error handling, performance optimization, and user experience improvements throughout the development process.
Ad
Recently uploaded (20)
Lessons Learned from Developing Secure AI Workflows.pdf
Lessons Learned from Developing Secure AI Workflows.pdfPriyanka Aash Lessons Learned from Developing Secure AI Workflows
Enhance GitHub Copilot using MCP - Enterprise version.pdf
Enhance GitHub Copilot using MCP - Enterprise version.pdfNilesh Gule Slide deck related to the GitHub Copilot Bootcamp in Melbourne on 17 June 2025
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdf
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdfPriyanka Aash GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now
Using the SQLExecutor for Data Quality Management: aka One man's love for the...
Using the SQLExecutor for Data Quality Management: aka One man's love for the...Safe Software The SQLExecutor is one of FME’s most powerful and flexible transformers. Pivvot maintains a robust internal metadata hierarchy used to support ingestion and curation of thousands of external data sources that must be managed for quality before entering our platform. By using the SQLExecutor, Pivvot can efficiently detect problems and perform analysis before data is extracted from our staging environment, removing the need for rollbacks or cycles waisted on a failed job. This presentation will walk through three distinct examples of how Pivvot uses the SQLExecutor to engage its metadata hierarchy and integrate with its Data Quality Management workflows efficiently and within the source postgres database. Spatial Validation –Validating spatial prerequisites before entering a production environment. Reference Data Validation - Dynamically validate domain-ed columns across any table and multiple columns per table. Practical De-duplication - Removing identical or near-identical well point locations from two distinct source datasets in the same table.
Security Tips for Enterprise Azure Solutions
Security Tips for Enterprise Azure SolutionsMichele Leroux Bustamante Delivering solutions to Azure may involve a variety of architecture patterns involving your applications, APIs data and associated Azure resources that comprise the solution. This session will use reference architectures to illustrate the security considerations to protect your Azure resources and data, how to achieve Zero Trust, and why it matters. Topics covered will include specific security recommendations for types Azure resources and related network security practices. The goal is to give you a breadth of understanding as to typical security requirements to meet compliance and security controls in an enterprise solution.
Curietech AI in action - Accelerate MuleSoft development
Curietech AI in action - Accelerate MuleSoft developmentshyamraj55 CurieTech AI in Action – Accelerate MuleSoft Development
Overview:
This presentation demonstrates how CurieTech AI’s purpose-built agents empower MuleSoft developers to create integration workflows faster, more accurately, and with less manual effort
linkedin.com
+12
curietech.ai
+12
meetups.mulesoft.com
+12
.
Key Highlights:
Dedicated AI agents for every stage: Coding, Testing (MUnit), Documentation, Code Review, and Migration
curietech.ai
+7
curietech.ai
+7
medium.com
+7
DataWeave automation: Generate mappings from tables or samples—95%+ complete within minutes
linkedin.com
+7
curietech.ai
+7
medium.com
+7
Integration flow generation: Auto-create Mule flows based on specifications—speeds up boilerplate development
curietech.ai
+1
medium.com
+1
Efficient code reviews: Gain intelligent feedback on flows, patterns, and error handling
youtube.com
+8
curietech.ai
+8
curietech.ai
+8
Test & documentation automation: Auto-generate MUnit test cases, sample data, and detailed docs from code
curietech.ai
+5
curietech.ai
+5
medium.com
+5
Why Now?
Achieve 10× productivity gains, slashing development time from hours to minutes
curietech.ai
+3
curietech.ai
+3
medium.com
+3
Maintain high accuracy with code quality matching or exceeding manual efforts
curietech.ai
+2
curietech.ai
+2
curietech.ai
+2
Ideal for developers, architects, and teams wanting to scale MuleSoft projects with AI efficiency
Conclusion:
CurieTech AI transforms MuleSoft development into an AI-accelerated workflow—letting you focus on innovation, not repetition.
The Future of Product Management in AI ERA.pdf
The Future of Product Management in AI ERA.pdfAlyona Owens Hi, I’m Aly Owens, I have a special pleasure to stand here as over a decade ago I graduated from CityU as an international student with an MBA program. I enjoyed the diversity of the school, ability to work and study, the network that came with being here, and of course the price tag for students here has always been more affordable than most around.
Since then I have worked for major corporations like T-Mobile and Microsoft and many more, and I have founded a startup. I've also been teaching product management to ensure my students save time and money to get to the same level as me faster avoiding popular mistakes. Today as I’ve transitioned to teaching and focusing on the startup, I hear everybody being concerned about Ai stealing their jobs… We’ll talk about it shortly.
But before that, I want to take you back to 1997. One of my favorite movies is “Fifth Element”. It wowed me with futuristic predictions when I was a kid and I’m impressed by the number of these predictions that have already come true. Self-driving cars, video calls and smart TV, personalized ads and identity scanning. Sci-fi movies and books gave us many ideas and some are being implemented as we speak. But we often get ahead of ourselves:
Flying cars,Colonized planets, Human-like AI: not yet, Time travel, Mind-machine neural interfaces for everyone: Only in experimental stages (e.g. Neuralink).
Cyberpunk dystopias: Some vibes (neon signs + inequality + surveillance), but not total dystopia (thankfully).
On the bright side, we predict that the working hours should drop as Ai becomes our helper and there shouldn’t be a need to work 8 hours/day. Nobody knows for sure but we can require that from legislation. Instead of waiting to see what the government and billionaires come up with, I say we should design our own future.
So, we as humans, when we don’t know something - fear takes over. The same thing happened during the industrial revolution. In the Industrial Era, machines didn’t steal jobs—they transformed them but people were scared about their jobs. The AI era is making similar changes except it feels like robots will take the center stage instead of a human. First off, even when it comes to the hottest space in the military - drones, Ai does a fraction of work. AI algorithms enable real-time decision-making, obstacle avoidance, and mission optimization making drones far more autonomous and capable than traditional remote-controlled aircraft. Key technologies include computer vision for object detection, GPS-enhanced navigation, and neural networks for learning and adaptation. But guess what? There are only 2 companies right now that utilize Ai in drones to make autonomous decisions - Skydio and DJI.
AI Agents and FME: A How-to Guide on Generating Synthetic Metadata
AI Agents and FME: A How-to Guide on Generating Synthetic MetadataSafe Software In the world of AI agents, semantics is king. Good metadata is thus essential in an organization's AI readiness checklist. But how do we keep up with the massive influx of new data? In this talk we go over the tips and tricks in generating synthetic metadata for the consumption of human users and AI agents alike.
From Manual to Auto Searching- FME in the Driver's Seat
From Manual to Auto Searching- FME in the Driver's SeatSafe Software Finding a specific car online can be a time-consuming task, especially when checking multiple dealer websites. A few years ago, I faced this exact problem while searching for a particular vehicle in New Zealand. The local classified platform, Trade Me (similar to eBay), wasn’t yielding any results, so I expanded my search to second-hand dealer sites—only to realise that periodically checking each one was going to be tedious. That’s when I noticed something interesting: many of these websites used the same platform to manage their inventories. Recognising this, I reverse-engineered the platform’s structure and built an FME workspace that automated the search process for me. By integrating API calls and setting up periodic checks, I received real-time email alerts when matching cars were listed. In this presentation, I’ll walk through how I used FME to save hours of manual searching by creating a custom car-finding automation system. While FME can’t buy a car for you—yet—it can certainly help you find the one you’re after!
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical Universes
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical UniversesSaikat Basu Embark on a cosmic journey exploring the intersection of quantum
computing, consciousness, and ancient wisdom. Together we'll uncover the
recursive patterns that bind our reality.
"Database isolation: how we deal with hundreds of direct connections to the d...
"Database isolation: how we deal with hundreds of direct connections to the d...Fwdays What can go wrong if you allow each service to access the database directly? In a startup, this seems like a quick and easy solution, but as the system scales, problems appear that no one could have guessed.
In my talk, I'll share Solidgate's experience in transforming its architecture: from the chaos of direct connections to a service-based data access model. I will talk about the transition stages, bottlenecks, and how isolation affected infrastructure support. I will honestly show what worked and what didn't. In short, we will analyze the controversy of this talk.
PyCon SG 25 - Firecracker Made Easy with Python.pdf
PyCon SG 25 - Firecracker Made Easy with Python.pdfMuhammad Yuga Nugraha Explore the ease of managing Firecracker microVM with the firecracker-python. In this session, I will introduce the basics of Firecracker microVM and demonstrate how this custom SDK facilitates microVM operations easily. We will delve into the design and development process behind the SDK, providing a behind-the-scenes look at its creation and features. While traditional Firecracker SDKs were primarily available in Go, this module brings a simplicity of Python to the table.
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdf
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdfEarley Information Science As AI reshapes expectations in retail and B2B commerce, organizations are recognizing a critical reality: meaningful AI outcomes depend on well-structured, adaptable infrastructure. In this session, Seth Earley is joined by Phil Ryan - AI strategist, search technologist, and founder of Glass Leopard Technologies - for a candid conversation on what it truly means to engineer systems for scale, agility, and intelligence.
Phil draws on more than two decades of experience leading search and AI initiatives for enterprise organizations. Together, he and Seth explore the challenges businesses face when legacy architectures limit personalization, agility, and real-time decisioning - and what needs to change to support agentic technologies and next-best-action capabilities.
Key themes from the webinar include:
Composability as a prerequisite for AI - Why modular, loosely coupled systems are essential for adapting to rapid innovation and evolving business needs
Search and relevance as foundational to AI - How techniques honed-in enterprise search have laid the groundwork for more responsive and intelligent customer experiences
From MDM and CDP to agentic systems - How data platforms are evolving to support richer customer context and dynamic orchestration
Engineering for business alignment - Why successful AI programs require architectural decisions grounded in measurable outcomes
The conversation is practical and forward-looking, connecting deep technical understanding with real-world business needs. Whether you’re modernizing your commerce stack or exploring how AI can enhance product discovery, personalization, or customer journeys, this session provides a clear-eyed view of the capabilities, constraints, and priorities that matter most.
Cracking the Code - Unveiling Synergies Between Open Source Security and AI.pdf
Cracking the Code - Unveiling Synergies Between Open Source Security and AI.pdfPriyanka Aash Cracking the Code - Unveiling Synergies Between Open Source Security and AI
Techniques for Automatic Device Identification and Network Assignment.pdf
Techniques for Automatic Device Identification and Network Assignment.pdfPriyanka Aash Techniques for Automatic Device Identification and Network Assignment
AI VIDEO MAGAZINE - June 2025 - r/aivideo
AI VIDEO MAGAZINE - June 2025 - r/aivideo1pcity Studios, Inc AI VIDEO MAGAZINE - r/aivideo community newsletter – Exclusive Tutorials: How to make an AI VIDEO from scratch, PLUS: How to make AI MUSIC, Hottest ai videos of 2025, Exclusive Interviews, New Tools, Previews, and MORE - JUNE 2025 ISSUE -
OpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.
Ad
OAuth2 Implementation Presentation (Java)
- 1. OAuth2 Implementation Presented By – Aasif Ali
- 2. Lack of etiquette and manners is a huge turn off. KnolX Etiquettes Punctuality Join the session 5 minutes prior to the session start time. We start on time and conclude on time! Feedback Make sure to submit a constructive feedback for all sessions as it is very helpful for the presenter. Silent Mode Keep your mobile devices in silent mode, feel free to move out of session in case you need to attend an urgent call. Avoid Disturbance Avoid unwanted chit chat during the session.
- 3. 1. Introduction to OAuth 2.0 2. OAuth 2.0 Roles 3. OAuth 2.0 Grant Types 4. Authorization Process 5. How It Works: The Building Blocks of OAuth 2.0 6. Setting up OAuth 2 in Spring Boot: Demo Example
- 5. What is Authorization Authorization is the process of determining whether an authenticated user or client has the necessary permissions to access a specific resource or perform a particular action within a system or application. "Are you allowed to do this?" It ensures that only authorized users or clients can access certain data or functionalities, protecting sensitive information and maintaining the security of the system.
- 6. What is OAuth 2? OAuth 2.0 (Open Authorization 2.0) is an authorization framework that enables third-party applications to access resources on behalf of a resource owner (user), with the resource owner's permission. It is widely used for securing APIs and enabling secure access to protected resources on the web. OAuth 2.0 is an evolution of OAuth 1.0, offering improvements in security, simplicity, and flexibility. OAuth 2.0 provides consented access and restricts actions of what the client app can perform on resources on behalf of the user, without ever sharing the user's credentials. OAuth 2.0 is an authorization protocol and NOT an authentication protocol. As such, it is designed primarily as a means of granting access to a set of resources, for example, remote APIs or user data.
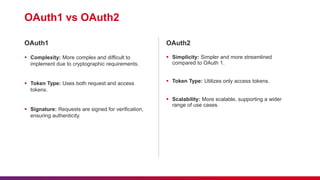
- 7. OAuth1 vs OAuth2 Complexity: More complex and difficult to implement due to cryptographic requirements. Token Type: Uses both request and access tokens. Signature: Requests are signed for verification, ensuring authenticity. OAuth1 Simplicity: Simpler and more streamlined compared to OAuth 1. Token Type: Utilizes only access tokens. Scalability: More scalable, supporting a wider range of use cases. OAuth2
- 8. 02
- 9. Resource Owner An entity capable of granting access to a protected resource. Typically, this is the end-user. OAuth 2 Roles Client An application requesting access to a protected resource on behalf of the resource owner. To access resources, the Client must hold the appropriate Access Token. Authorization Server The server that authenticates the resource owner and issues access tokens after obtaining authorization. Resource Server The server hosting the protected resources, capable of accepting and responding to requests using access tokens.
- 10. 03
- 11. Authorization Code The authorization code grant type is widely used for server-side applications, ensuring Client Secret confidentiality. It involves redirection, where the app communicates with the user's browser to receive authorization codes. OAuth 2 Grant Types Implicit A simplified flow where the Access Token is returned directly to the Client. In the Implicit flow, the authorization server may return the Access Token as a parameter in the callback URI or as a response to a form post. Resource Owner Password Credentials This grant requires the Client first to acquire the resource owner’s credentials, which are passed to the Authorization server. Allows users to provide their credentials directly to the application, which then exchanges them for an access token. It's useful for trusted applications like native mobile apps. Client Credentials Used for non-interactive applications e.g., automated processes, microservices, etc. It allows a client to request an access token using the resource owner's username and password directly, rather than going through an authorization process with redirects.
- 12. 04
- 13. Authorization Process The Client requests authorization (authorization request) from the Authorization server, supplying the client id and secret to as identification; it also provides the scopes and an endpoint URI (redirect URI) to send the Access Token or the Authorization Code to. The Authorization server authenticates the Client and verifies that the requested scopes are permitted. The Resource owner interacts with the Authorization server to grant access. The Authorization server redirects back to the Client with either an Authorization Code or Access Token, depending on the grant type. With the Access Token, the Client requests access to the resource from the Resource server.
- 15. 05
- 16. Scopes and Consent Scopes are mechanisms that define permissions and set boundaries for what an application or service does or does not have access to. When an app sends an authorization request, the user is presented with the specific scope of the request and must authorize consent. This consent serves as proof of authorization and allows an access token to be granted.
- 17. Actors The resource owner owns the data for which access is requested. The resource owner can be an individual end-user or a company. The resource server is the API or server that securely stores the data the application or service has requested to access. The resource server must accept and validate an access token from the requesting application to grant access to the data. The client is the application or service requesting access to the data the resource server is protecting. Clients gain access to the requested resources by presenting a valid access token to the resource server. The authorization server handles token management. It manages tokens, which are like keys to access resources. When a client wants access to something, like your photos, it asks the authorization server. Once you say yes, the server gives the client a new access token, like a special key, to use on the resource server.
- 18. Clients Confidential clients keep secrets and operate in secure areas inaccessible to end-users. Public clients, on the other hand, are less secure and include browsers, mobile apps, and IoT devices.
- 19. Tokens Access tokens are granted by the authorization server and used to access the data in the resource server. They typically allow clients to access resources for a few minutes up to a few hours. Refresh tokens are only granted to confidential clients with secure authentication protocols and can be valid for days, months, or even years - they can also be used to get new access tokens for other clients.
- 20. 06
