Object oriented programming 10 variables input and output
Download as pptx, pdf0 likes82 views
cin is an object of the input stream and is used to take input from input streams like files, console, etc. cout is an object of the output stream that is used to show output. Basically, cin is an input statement while cout is an output statement. They also use different operators.
1 of 19
Download to read offline








Ad
Recommended
Object oriented programming 12 programming steps in cpp and example



Object oriented programming 12 programming steps in cpp and exampleVaibhav Khanna Designing and planning is important for projects and programmes alike.
It refers to the “process of setting goals, developing strategies, outlining the implementation arrangements and allocating resources to achieve those goals
Datapath design



Datapath designMd Nazmul Hossain Mir The document summarizes a presentation on datapath design. It discusses what a datapath is, which includes functional units like ALUs and registers that perform data processing. It then covers different arithmetic operations like addition, subtraction, multiplication and division that can be performed in a datapath. Specific circuit designs for performing operations like binary addition using half and full adders, parallel adders, fast parallel adders using carry lookahead, and sequential and combinational multipliers and dividers are described. Booth's algorithm for multiplication of signed binary numbers is also covered. The document concludes with a brief explanation of what an arithmetic logic unit is.
List - Operations and Implementation



List - Operations and ImplementationSagacious IT Solution This document discusses lists and their implementation. It describes static and dynamic lists, with static lists having fixed size and storing elements in an array, while dynamic lists can grow and shrink as nodes are linked together. It also covers array implementation of lists, including how to insert and delete nodes at a given position. Operations on static lists have complexity related to list size, while dynamic lists can grow and shrink as needed. The document also discusses using a list to implement a linear queue, with insertion only at the rear and deletion only at the front.
Memory Reference Instructions



Memory Reference InstructionsRabin BK Memory reference instructions used in computer architecture is well demonstrated with examples. It will probably help you understand each referencing instructions.
PROCESSOR AND CONTROL UNIT



PROCESSOR AND CONTROL UNITAmirthavalli Senthil A Basic MIPS implementation – Building a Datapath – Control Implementation Scheme – Pipelining – Pipelined datapath and control –
Matlab vectors



Matlab vectorspramodkumar1804 Vectors are one-dimensional arrays that can be either rows or columns. Row vectors use spaces or commas to separate elements within brackets, while column vectors use semicolons. Individual elements can be accessed using indices like v(i). A range of elements can be selected using colon notation like v(3:7). Vectors can be added, subtracted, multiplied by scalars, transposed, appended, have their magnitude and dot products calculated. They can also contain uniformly spaced elements.
Process of algorithm evaluation



Process of algorithm evaluationAshish Ranjan This document discusses the process of evaluating the time and space complexity of algorithms. It defines time complexity as the total amount of time required by an algorithm to complete execution. Space complexity is defined as the total amount of computer memory required. Examples are provided to illustrate constant and linear time and space complexity by analyzing simple algorithms.
Object oriented programming 9 expressions and type casting in c++



Object oriented programming 9 expressions and type casting in c++Vaibhav Khanna C++ is a strong-typed language, which mean have associated data type with a variable before it is being used in program. Conversion of an expression of a given type into another type is called as type casting. Type Casting is a mechanism which enables a variable of one datatype to be converted to another datatype.
C++ ch2



C++ ch2Venkateswarlu Vuggam This document provides an overview of the key concepts covered in Chapter 2 of the C++ Programming textbook. These include basic C++ program components like functions, data types, arithmetic operators, and input/output statements. It also discusses programming fundamentals like declaring variables, writing comments, using preprocessor directives, and properly structuring a C++ program with a main function. An example is provided to demonstrate how to write a program that converts between feet/inches and centimeters.
C++ Ch3



C++ Ch3Venkateswarlu Vuggam This chapter discusses input and output (I/O) in C++ programs. It introduces I/O streams as sequences of bytes or characters that move between sources and destinations. The standard input stream cin is used to extract data from the keyboard and the standard output stream cout is used to send output to the screen. Various I/O functions are described, including extraction operator >> to read data into variables from cin, and insertion operator << to write data from variables to cout. The chapter also covers file I/O, input/output formatting, and an example program that calculates movie ticket sales and a donation amount.
Object oriented programming 13 input stream and devices in cpp



Object oriented programming 13 input stream and devices in cppVaibhav Khanna In C++ input and output is performed in the form of a sequence of bytes or more commonly known as streams. Input Stream: If the direction of flow of bytes is from the device(for example, Keyboard) to the main memory then this process is called input.
Basic Elements of C++



Basic Elements of C++Jason J Pulikkottil This document provides an introduction to basic elements of C++ programming, including:
- The structure of a basic C++ program with an example main function.
- Common data types like integers, floating point numbers, characters, and strings.
- Arithmetic operators and precedence.
- Expressions, input/output, and type casting.
- Variables, memory allocation, and initializing variables.
- Control structures like increment/decrement operators.
- Program style guidelines including comments and formatting.
Introduction to c



Introduction to csunila tharagaturi This PPT contains A to Z topics of C programming language. It makes learners to find it easy to learn C. Tutors also can use the PPT for better presentation.
Basic Programming concepts - Programming with C++



Basic Programming concepts - Programming with C++Mohamed El Desouki أساسيات البرمجة - شرح بإستخدام لغة السى بلس بلس - C++
https://www.youtube.com/watch?v=Fr6wJ5_Hok0&list=PL1DUmTEdeA6IUD9Gt5rZlQfbZyAWXd-oD
Lesson 4.1 completing the problem solving process



Lesson 4.1 completing the problem solving processMLG College of Learning, Inc This document discusses coding the algorithm into a program, which is the fourth step of the problem-solving process. It covers declaring variables, coding instructions, getting input from the keyboard using cin, displaying output to the screen using cout, arithmetic expressions and operators, type conversions, and assignment statements. Arithmetic assignment operators can abbreviate statements that contain an operator and assignment.
Object oriented programming 14 output formatting using manipulators



Object oriented programming 14 output formatting using manipulatorsVaibhav Khanna Manipulators are operators used in C++ for formatting output. The data is manipulated by the programmer's choice of display. In this C++ tutorial, you will learn what a manipulator is, endl manipulator, setw manipulator, setfill manipulator and setprecision manipulator are all explained along with syntax and examples
K-Means Algorithm Implementation In python



K-Means Algorithm Implementation In pythonAfzal Ahmad This is K-Means clustering Algorithm Implementation In python as well as python script to convert xml to csv format
CP 04.pptx



CP 04.pptxRehmanRasheed3 This document provides an overview of key concepts in C++ programming including program structure, variables, data types, operators, input/output, control structures, and functions. It discusses the basic building blocks of a C++ program including comments, header files, declaring variables, reading/writing data, and program flow. Control structures like if/else, switch, while, for, break and continue are explained. The document also covers fundamental C++ concepts such as variables, data types, operators, and basic input/output.
ch02-primitive-data-definite-loops.ppt



ch02-primitive-data-definite-loops.pptMahyuddin8 The document discusses Java's primitive data types and for loops. It introduces Java's primitive types like int, double, char, and boolean. It covers expressions, operators, and precedence. It then introduces variables, declaring and initializing variables, and using variables in expressions. Finally, it covers the for loop structure with initialization, test, and update sections to allow repetition of code.
ch02-primitive-data-definite-loops.ppt



ch02-primitive-data-definite-loops.pptghoitsun The document discusses Java's primitive data types and for loops. It introduces Java's primitive types like int, double, char, and boolean. It covers expressions, operators, and precedence. It then introduces variables, declaring and initializing variables, and using variables in expressions. Finally, it covers the for loop structure with initialization, test, and update sections to allow repetition of code.
Basics of c++ Programming Language



Basics of c++ Programming LanguageAhmad Idrees The aim of this list of programming languages is to include all notable programming languages in existence, both those in current use and ... Note: This page does not list esoteric programming languages. .... Computer programming portal ...
02 functions, variables, basic input and output of c++



02 functions, variables, basic input and output of c++Manzoor ALam This document discusses computer programming functions, variables, and basic input/output in C and C++. It covers:
- Defining and calling functions, function parameters and return values.
- Declaring and assigning values to variables of different data types like int, float, and double.
- Using basic input/output functions like cout and cin to display output and get user input.
- The scope of variables and how they work within and outside of functions.
Lecture-2-Python-Basic-Elements-Sep04-2018.pptx



Lecture-2-Python-Basic-Elements-Sep04-2018.pptxAbdulQadeerBilal The document summarizes basic elements of Python programs including literals, assignments, data types, identifiers, and expressions. Literals represent specific values like numbers and strings. Variables store values that can change. Expressions combine values using operators to produce new values. Input is obtained using assignments combined with the input function. Data types can be converted between integer, float, and string formats.
Chap 3 c++



Chap 3 c++Widad Jamaluddin This document provides an overview of input and output operations, preprocessor directives, and debugging syntax errors in C++. It discusses including the iostream and string libraries for input/output and string processing. It covers input and output statements using cin and cout, constants, and increment/decrement operators. The document also reviews preprocessor directives like #include and #define, and manipulators for formatting output. It concludes with debugging syntax errors and understanding semantics.
Unit 3 Stacks and Queues.pptx



Unit 3 Stacks and Queues.pptxYogesh Pawar 1. The document discusses stacks and queues as linear data structures. It describes stack operations like push and pop and provides algorithms for implementing these operations.
2. An example program for implementing a stack using an array is presented, with functions defined for push, pop, and display operations on the stack.
3. Applications of stacks discussed include reversing a list or string by pushing characters onto a stack and popping them off in reverse order, and converting infix expressions to postfix using a stack.
Information and network security 47 authentication applications



Information and network security 47 authentication applicationsVaibhav Khanna Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users. In Kerberos Authentication server and database is used for client authentication. Kerberos runs as a third-party trusted server known as the Key Distribution Center (KDC).
Information and network security 46 digital signature algorithm



Information and network security 46 digital signature algorithmVaibhav Khanna The Digital Signature Algorithm (DSA) is a Federal Information Processing Standard for digital signatures, based on the mathematical concept of modular exponentiation and the discrete logarithm problem. DSA is a variant of the Schnorr and ElGamal signature schemes
More Related Content
Similar to Object oriented programming 10 variables input and output (20)
C++ ch2



C++ ch2Venkateswarlu Vuggam This document provides an overview of the key concepts covered in Chapter 2 of the C++ Programming textbook. These include basic C++ program components like functions, data types, arithmetic operators, and input/output statements. It also discusses programming fundamentals like declaring variables, writing comments, using preprocessor directives, and properly structuring a C++ program with a main function. An example is provided to demonstrate how to write a program that converts between feet/inches and centimeters.
C++ Ch3



C++ Ch3Venkateswarlu Vuggam This chapter discusses input and output (I/O) in C++ programs. It introduces I/O streams as sequences of bytes or characters that move between sources and destinations. The standard input stream cin is used to extract data from the keyboard and the standard output stream cout is used to send output to the screen. Various I/O functions are described, including extraction operator >> to read data into variables from cin, and insertion operator << to write data from variables to cout. The chapter also covers file I/O, input/output formatting, and an example program that calculates movie ticket sales and a donation amount.
Object oriented programming 13 input stream and devices in cpp



Object oriented programming 13 input stream and devices in cppVaibhav Khanna In C++ input and output is performed in the form of a sequence of bytes or more commonly known as streams. Input Stream: If the direction of flow of bytes is from the device(for example, Keyboard) to the main memory then this process is called input.
Basic Elements of C++



Basic Elements of C++Jason J Pulikkottil This document provides an introduction to basic elements of C++ programming, including:
- The structure of a basic C++ program with an example main function.
- Common data types like integers, floating point numbers, characters, and strings.
- Arithmetic operators and precedence.
- Expressions, input/output, and type casting.
- Variables, memory allocation, and initializing variables.
- Control structures like increment/decrement operators.
- Program style guidelines including comments and formatting.
Introduction to c



Introduction to csunila tharagaturi This PPT contains A to Z topics of C programming language. It makes learners to find it easy to learn C. Tutors also can use the PPT for better presentation.
Basic Programming concepts - Programming with C++



Basic Programming concepts - Programming with C++Mohamed El Desouki أساسيات البرمجة - شرح بإستخدام لغة السى بلس بلس - C++
https://www.youtube.com/watch?v=Fr6wJ5_Hok0&list=PL1DUmTEdeA6IUD9Gt5rZlQfbZyAWXd-oD
Lesson 4.1 completing the problem solving process



Lesson 4.1 completing the problem solving processMLG College of Learning, Inc This document discusses coding the algorithm into a program, which is the fourth step of the problem-solving process. It covers declaring variables, coding instructions, getting input from the keyboard using cin, displaying output to the screen using cout, arithmetic expressions and operators, type conversions, and assignment statements. Arithmetic assignment operators can abbreviate statements that contain an operator and assignment.
Object oriented programming 14 output formatting using manipulators



Object oriented programming 14 output formatting using manipulatorsVaibhav Khanna Manipulators are operators used in C++ for formatting output. The data is manipulated by the programmer's choice of display. In this C++ tutorial, you will learn what a manipulator is, endl manipulator, setw manipulator, setfill manipulator and setprecision manipulator are all explained along with syntax and examples
K-Means Algorithm Implementation In python



K-Means Algorithm Implementation In pythonAfzal Ahmad This is K-Means clustering Algorithm Implementation In python as well as python script to convert xml to csv format
CP 04.pptx



CP 04.pptxRehmanRasheed3 This document provides an overview of key concepts in C++ programming including program structure, variables, data types, operators, input/output, control structures, and functions. It discusses the basic building blocks of a C++ program including comments, header files, declaring variables, reading/writing data, and program flow. Control structures like if/else, switch, while, for, break and continue are explained. The document also covers fundamental C++ concepts such as variables, data types, operators, and basic input/output.
ch02-primitive-data-definite-loops.ppt



ch02-primitive-data-definite-loops.pptMahyuddin8 The document discusses Java's primitive data types and for loops. It introduces Java's primitive types like int, double, char, and boolean. It covers expressions, operators, and precedence. It then introduces variables, declaring and initializing variables, and using variables in expressions. Finally, it covers the for loop structure with initialization, test, and update sections to allow repetition of code.
ch02-primitive-data-definite-loops.ppt



ch02-primitive-data-definite-loops.pptghoitsun The document discusses Java's primitive data types and for loops. It introduces Java's primitive types like int, double, char, and boolean. It covers expressions, operators, and precedence. It then introduces variables, declaring and initializing variables, and using variables in expressions. Finally, it covers the for loop structure with initialization, test, and update sections to allow repetition of code.
Basics of c++ Programming Language



Basics of c++ Programming LanguageAhmad Idrees The aim of this list of programming languages is to include all notable programming languages in existence, both those in current use and ... Note: This page does not list esoteric programming languages. .... Computer programming portal ...
02 functions, variables, basic input and output of c++



02 functions, variables, basic input and output of c++Manzoor ALam This document discusses computer programming functions, variables, and basic input/output in C and C++. It covers:
- Defining and calling functions, function parameters and return values.
- Declaring and assigning values to variables of different data types like int, float, and double.
- Using basic input/output functions like cout and cin to display output and get user input.
- The scope of variables and how they work within and outside of functions.
Lecture-2-Python-Basic-Elements-Sep04-2018.pptx



Lecture-2-Python-Basic-Elements-Sep04-2018.pptxAbdulQadeerBilal The document summarizes basic elements of Python programs including literals, assignments, data types, identifiers, and expressions. Literals represent specific values like numbers and strings. Variables store values that can change. Expressions combine values using operators to produce new values. Input is obtained using assignments combined with the input function. Data types can be converted between integer, float, and string formats.
Chap 3 c++



Chap 3 c++Widad Jamaluddin This document provides an overview of input and output operations, preprocessor directives, and debugging syntax errors in C++. It discusses including the iostream and string libraries for input/output and string processing. It covers input and output statements using cin and cout, constants, and increment/decrement operators. The document also reviews preprocessor directives like #include and #define, and manipulators for formatting output. It concludes with debugging syntax errors and understanding semantics.
Unit 3 Stacks and Queues.pptx



Unit 3 Stacks and Queues.pptxYogesh Pawar 1. The document discusses stacks and queues as linear data structures. It describes stack operations like push and pop and provides algorithms for implementing these operations.
2. An example program for implementing a stack using an array is presented, with functions defined for push, pop, and display operations on the stack.
3. Applications of stacks discussed include reversing a list or string by pushing characters onto a stack and popping them off in reverse order, and converting infix expressions to postfix using a stack.
More from Vaibhav Khanna (20)
Information and network security 47 authentication applications



Information and network security 47 authentication applicationsVaibhav Khanna Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users. In Kerberos Authentication server and database is used for client authentication. Kerberos runs as a third-party trusted server known as the Key Distribution Center (KDC).
Information and network security 46 digital signature algorithm



Information and network security 46 digital signature algorithmVaibhav Khanna The Digital Signature Algorithm (DSA) is a Federal Information Processing Standard for digital signatures, based on the mathematical concept of modular exponentiation and the discrete logarithm problem. DSA is a variant of the Schnorr and ElGamal signature schemes
Information and network security 45 digital signature standard



Information and network security 45 digital signature standardVaibhav Khanna The Digital Signature Standard is a Federal Information Processing Standard specifying a suite of algorithms that can be used to generate digital signatures established by the U.S. National Institute of Standards and Technology in 1994
Information and network security 44 direct digital signatures



Information and network security 44 direct digital signaturesVaibhav Khanna The Direct Digital Signature is only include two parties one to send message and other one to receive it. According to direct digital signature both parties trust each other and knows there public key. The message are prone to get corrupted and the sender can declines about the message sent by him any time
Information and network security 43 digital signatures



Information and network security 43 digital signaturesVaibhav Khanna Digital signatures are the public-key primitives of message authentication. In the physical world, it is common to use handwritten signatures on handwritten or typed messages. ... Digital signature is a cryptographic value that is calculated from the data and a secret key known only by the signer
Information and network security 42 security of message authentication code



Information and network security 42 security of message authentication codeVaibhav Khanna Message Authentication Requirements
Disclosure: Release of message contents to any person or process not possess- ing the appropriate cryptographic key.
Traffic analysis: Discovery of the pattern of traffic between parties. ...
Masquerade: Insertion of messages into the network from a fraudulent source
Information and network security 41 message authentication code



Information and network security 41 message authentication codeVaibhav Khanna Message authentication aims to protect integrity, validate originator identity, and provide non-repudiation. It addresses threats like masquerading, content or sequence modification, and source/destination repudiation. A Message Authentication Code (MAC) provides assurance that a message is unaltered and from the sender by appending a cryptographic checksum to the message dependent on the key and content. The receiver can validate the MAC to verify integrity and authenticity.
Information and network security 40 sha3 secure hash algorithm



Information and network security 40 sha3 secure hash algorithmVaibhav Khanna SHA-3 is the latest member of the Secure Hash Algorithm family of standards, released by NIST on August 5, 2015. Although part of the same series of standards, SHA-3 is internally different from the MD5-like structure of SHA-1 and SHA-2
Information and network security 39 secure hash algorithm



Information and network security 39 secure hash algorithmVaibhav Khanna The Secure Hash Algorithm (SHA) is a cryptographic hash function developed by the US National Security Agency. SHA-512 is the latest version that produces a 512-bit hash value. It processes message blocks of 1024 bits using an 80-step compression function that updates a 512-bit buffer. Each step uses a 64-bit value derived from the message and a round constant. SHA-512 supports messages up to 2^128 bits in length and adds between 1 and 1023 padding bits as needed.
Information and network security 38 birthday attacks and security of hash fun...



Information and network security 38 birthday attacks and security of hash fun...Vaibhav Khanna Birthday attack can be used in communication abusage between two or more parties. ... The mathematics behind this problem led to a well-known cryptographic attack called the birthday attack, which uses this probabilistic model to reduce the complexity of cracking a hash function
Information and network security 37 hash functions and message authentication



Information and network security 37 hash functions and message authenticationVaibhav Khanna Message Authentication Code ... A message authentication code (MAC) is similar to a cryptographic hash, except that it is based on a secret key
Information and network security 35 the chinese remainder theorem



Information and network security 35 the chinese remainder theoremVaibhav Khanna In number theory, the Chinese remainder theorem states that if one knows the remainders of the Euclidean division of an integer n by several integers, then one can determine uniquely the remainder of the division of n by the product of these integers, under the condition that the divisors are pairwise coprime.
Information and network security 34 primality



Information and network security 34 primalityVaibhav Khanna A primality test is an algorithm for determining whether an input number is prime. Among other fields of mathematics, it is used for cryptography. Unlike integer factorization, primality tests do not generally give prime factors, only stating whether the input number is prime or not
Information and network security 33 rsa algorithm



Information and network security 33 rsa algorithmVaibhav Khanna RSA algorithm is asymmetric cryptography algorithm. Asymmetric actually means that it works on two different keys i.e. Public Key and Private Key. As the name describes that the Public Key is given to everyone and Private key is kept private
Information and network security 32 principles of public key cryptosystems



Information and network security 32 principles of public key cryptosystemsVaibhav Khanna Public-key cryptography, or asymmetric cryptography, is an encryption scheme that uses two mathematically related, but not identical, keys - a public key and a private key. Unlike symmetric key algorithms that rely on one key to both encrypt and decrypt, each key performs a unique function.
Information and network security 31 public key cryptography



Information and network security 31 public key cryptographyVaibhav Khanna Public-key cryptography, or asymmetric cryptography, is a cryptographic system that uses pairs of keys: public keys, and private keys. The generation of such key pairs depends on cryptographic algorithms which are based on mathematical problems termed one-way function
Information and network security 30 random numbers



Information and network security 30 random numbersVaibhav Khanna Random numbers are fundamental building blocks of cryptographic systems and as such, play a key role in each of these elements. Random numbers are used to inject unpredictable or non-deterministic data into cryptographic algorithms and protocols to make the resulting data streams unrepeatable and virtually unguessable
Information and network security 29 international data encryption algorithm



Information and network security 29 international data encryption algorithmVaibhav Khanna International Data Encryption Algorithm (IDEA) is a once-proprietary free and open block cipher that was once intended to replace Data Encryption Standard (DES). IDEA has been and is optionally available for use with Pretty Good Privacy (PGP). IDEA has been succeeded by the IDEA NXT algorithm
Information and network security 28 blowfish



Information and network security 28 blowfishVaibhav Khanna Blowfish is a symmetric block cipher designed as a replacement for DES. It encrypts data in 64-bit blocks using a variable-length key. The algorithm uses substitution boxes and a complex key schedule to encrypt the data in multiple rounds. It is very fast, uses little memory, and is resistant to cryptanalysis due to its complex key schedule and substitution boxes.
Information and network security 27 triple des



Information and network security 27 triple desVaibhav Khanna Part of what Triple DES does is to protect against brute force attacks. The original DES symmetric encryption algorithm specified the use of 56-bit keys -- not enough, by 1999, to protect against practical brute force attacks. Triple DES specifies the use of three distinct DES keys, for a total key length of 168 bits
Ad
Recently uploaded (20)
Making significant Software Architecture decisions



Making significant Software Architecture decisionsBert Jan Schrijver Presented at the iSAQB Software Architecture Community NL meetup on 12-6-2025
Migrating to Azure Cosmos DB the Right Way



Migrating to Azure Cosmos DB the Right WayAlexander (Alex) Komyagin In this session we cover the benefits of a migration to Cosmos DB, migration paths, common pain points and best practices. We share our firsthand experiences and customer stories. Adiom is the trusted partner for migration solutions that enable seamless online database migrations from MongoDB to Cosmos DB vCore, and DynamoDB to Cosmos DB for NoSQL.
Milwaukee Marketo User Group June 2025 - Optimize and Enhance Efficiency - Sm...



Milwaukee Marketo User Group June 2025 - Optimize and Enhance Efficiency - Sm...BradBedford3 Inspired by the Adobe Summit hands-on lab, Optimize Your Marketo Instance Performance, review the recording from June 5th to learn best practices that can optimize your smart campaign and smart list processing time, inefficient practices to try to avoid, and tips and tricks for keeping your instance running smooth!
You will learn:
How smart campaign queueing works, how flow steps are prioritized, and configurations that slow down smart campaign processing.
Best practices for smart list and smart campaign configurations that yield greater reliability and processing efficiencies.
Generally recommended timelines for reviewing instance performance: walk away from this session with a guideline of what to review in Marketo and how often to review it.
This session will be helpful for any Marketo administrator looking for opportunities to improve and streamline their instance performance. Be sure to watch to learn best practices and connect with your local Marketo peers!
GDG Douglas - Google AI Agents: Your Next Intern?



GDG Douglas - Google AI Agents: Your Next Intern?felipeceotto Presentation done at the GDG Douglas event for June 2025.
A first look at Google's new Agent Development Kit.
Agent Development Kit is a new open-source framework from Google designed to simplify the full stack end-to-end development of agents and multi-agent systems.
Step by step guide to install Flutter and Dart



Step by step guide to install Flutter and DartS Pranav (Deepu) Flutter is basically Google’s portable user
interface (UI) toolkit, used to build and
develop eye-catching, natively-built
applications for mobile, desktop, and web,
from a single codebase. Flutter is free, open-
sourced, and compatible with existing code. It
is utilized by companies and developers
around the world, due to its user-friendly
interface and fairly simple, yet to-the-point
commands.
Who will create the languages of the future?



Who will create the languages of the future?Jordi Cabot Will future languages be created by language engineers?
Can you "vibe" a DSL?
In this talk, we will explore the changing landscape of language engineering and discuss how Artificial Intelligence and low-code/no-code techniques can play a role in this future by helping in the definition, use, execution, and testing of new languages. Even empowering non-tech users to create their own language infrastructure. Maybe without them even realizing.
Porting Qt 5 QML Modules to Qt 6 Webinar



Porting Qt 5 QML Modules to Qt 6 WebinarICS Have you upgraded your application from Qt 5 to Qt 6? If so, your QML modules might still be stuck in the old Qt 5 style—technically compatible, but far from optimal. Qt 6 introduces a modernized approach to QML modules that offers better integration with CMake, enhanced maintainability, and significant productivity gains.
In this webinar, we’ll walk you through the benefits of adopting Qt 6 style QML modules and show you how to make the transition. You'll learn how to leverage the new module system to reduce boilerplate, simplify builds, and modernize your application architecture. Whether you're planning a full migration or just exploring what's new, this session will help you get the most out of your move to Qt 6.
Async-ronizing Success at Wix - Patterns for Seamless Microservices - Devoxx ...



Async-ronizing Success at Wix - Patterns for Seamless Microservices - Devoxx ...Natan Silnitsky In a world where speed, resilience, and fault tolerance define success, Wix leverages Kafka to power asynchronous programming across 4,000 microservices. This talk explores four key patterns that boost developer velocity while solving common challenges with scalable, efficient, and reliable solutions:
1. Integration Events: Shift from synchronous calls to pre-fetching to reduce query latency and improve user experience.
2. Task Queue: Offload non-critical tasks like notifications to streamline request flows.
3. Task Scheduler: Enable precise, fault-tolerant delayed or recurring workflows with robust scheduling.
4. Iterator for Long-running Jobs: Process extensive workloads via chunked execution, optimizing scalability and resilience.
For each pattern, we’ll discuss benefits, challenges, and how we mitigate drawbacks to create practical solutions
This session offers actionable insights for developers and architects tackling distributed systems, helping refine microservices and adopting Kafka-driven async excellence.
Application Modernization with Choreo - The AI-Native Internal Developer Plat...



Application Modernization with Choreo - The AI-Native Internal Developer Plat...WSO2 In this slide deck, we explore the challenges and best practices of application modernization. We also deep dive how an internal developer platform as a service like Choreo can fast track your modernization journey with AI capabilities and end-to-end workflow automation.
Smart Financial Solutions: Money Lender Software, Daily Pigmy & Personal Loan...



Smart Financial Solutions: Money Lender Software, Daily Pigmy & Personal Loan...Intelli grow Explore innovative tools tailored for modern finance with our Money Lender Software Development, efficient Daily Pigmy Collection Software, and streamlined Personal Loan Software. This presentation showcases how these solutions simplify loan management, boost collection efficiency, and enhance customer experience for NBFCs, microfinance firms, and individual lenders.
What is data visualization and how data visualization tool can help.pdf



What is data visualization and how data visualization tool can help.pdfVarsha Nayak An open source data visualization tool enhances this process by providing flexible, cost-effective solutions that allow users to customize and scale their visualizations according to their needs. These tools enable organizations to make data-driven decisions with complete freedom from proprietary software limitations. Whether you're a data scientist, marketer, or business leader, understanding how to utilize an open source data visualization tool can significantly improve your ability to communicate insights effectively.
Automated Migration of ESRI Geodatabases Using XML Control Files and FME



Automated Migration of ESRI Geodatabases Using XML Control Files and FMESafe Software Efficient data migration is a critical challenge in geospatial data management, especially when working with complex data structures. This presentation explores an automated approach to migrating ESRI Geodatabases using FME and XML-based control files. A key advantage of this method is its adaptability: changes to the data model are seamlessly incorporated into the migration process without requiring modifications to the underlying FME workflow. By separating data model definitions from migration logic, this approach ensures flexibility, reduces maintenance effort, and enhances scalability.
Wondershare PDFelement Pro 11.4.20.3548 Crack Free Download



Wondershare PDFelement Pro 11.4.20.3548 Crack Free DownloadPuppy jhon ➡ 🌍📱👉COPY & PASTE LINK👉👉👉 ➤ ➤➤ https://drfiles.net/
Wondershare PDFelement Professional is professional software that can edit PDF files. This digital tool can manipulate elements in PDF documents.
IBM Rational Unified Process For Software Engineering - Introduction



IBM Rational Unified Process For Software Engineering - IntroductionGaurav Sharma IBM Rational Unified Process For Software Engineering
AI and Deep Learning with NVIDIA Technologies



AI and Deep Learning with NVIDIA TechnologiesSandeepKS52 Artificial intelligence and deep learning are transforming various fields by enabling machines to learn from data and make decisions. Understanding how to prepare data effectively is crucial, as it lays the foundation for training models that can recognize patterns and improve over time. Once models are trained, the focus shifts to deployment, where these intelligent systems are integrated into real-world applications, allowing them to perform tasks and provide insights based on new information. This exploration of AI encompasses the entire process from initial concepts to practical implementation, highlighting the importance of each stage in creating effective and reliable AI solutions.
Meet You in the Middle: 1000x Performance for Parquet Queries on PB-Scale Dat...



Meet You in the Middle: 1000x Performance for Parquet Queries on PB-Scale Dat...Alluxio, Inc. Alluxio Webinar
June 10, 2025
For more Alluxio Events: https://www.alluxio.io/events/
Speaker:
David Zhu (Engineering Manager @ Alluxio)
Storing data as Parquet files on cloud object storage, such as AWS S3, has become prevalent not only for large-scale data lakes but also as lightweight feature stores for training and inference, or as document stores for Retrieval-Augmented Generation (RAG). However, querying petabyte-to-exabyte-scale data lakes directly from S3 remains notoriously slow, with latencies typically ranging from hundreds of milliseconds to several seconds.
In this webinar, David Zhu, Software Engineering Manager at Alluxio, will present the results of a joint collaboration between Alluxio and a leading SaaS and data infrastructure enterprise that explored leveraging Alluxio as a high-performance caching and acceleration layer atop AWS S3 for ultra-fast querying of Parquet files at PB scale.
David will share:
- How Alluxio delivers sub-millisecond Time-to-First-Byte (TTFB) for Parquet queries, comparable to S3 Express One Zone, without requiring specialized hardware, data format changes, or data migration from your existing data lake.
- The architecture that enables Alluxio’s throughput to scale linearly with cluster size, achieving one million queries per second on a modest 50-node deployment, surpassing S3 Express single-account throughput by 50x without latency degradation.
- Specifics on how Alluxio offloads partial Parquet read operations and reduces overhead, enabling direct, ultra-low-latency point queries in hundreds of microseconds and achieving a 1,000x performance gain over traditional S3 querying methods.
Smadav Pro 2025 Rev 15.4 Crack Full Version With Registration Key



Smadav Pro 2025 Rev 15.4 Crack Full Version With Registration Keyjoybepari360 ➡️ 🌍📱👉COPY & PASTE LINK👉👉👉
https://crackpurely.site/smadav-pro-crack-full-version-registration-key/
Ad
Object oriented programming 10 variables input and output
- 1. Object Oriented Programming: 10 Variables Input and Output Prof Neeraj Bhargava Vaibhav Khanna Department of Computer Science School of Engineering and Systems Sciences Maharshi Dayanand Saraswati University Ajmer
- 2. 2 Input • Data must be loaded into main memory before it can be manipulated • Storing data in memory is a two-step process: – Instruct computer to allocate memory – Include statements to put data into memory
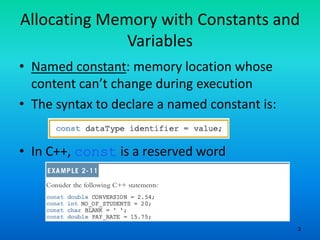
- 3. 3 Allocating Memory with Constants and Variables • Named constant: memory location whose content can’t change during execution • The syntax to declare a named constant is: • In C++, const is a reserved word
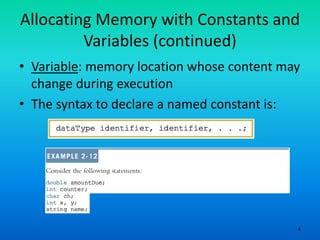
- 4. 4 Allocating Memory with Constants and Variables (continued) • Variable: memory location whose content may change during execution • The syntax to declare a named constant is:
- 5. 5 Putting Data into Variables • Ways to place data into a variable: – Use C++’s assignment statement – Use input (read) statements
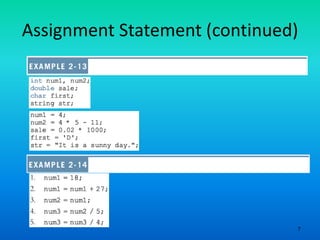
- 6. 6 Assignment Statement • The assignment statement takes the form: • Expression is evaluated and its value is assigned to the variable on the left side • In C++, = is called the assignment operator
- 8. 8 Saving and Using the Value of an Expression • To save the value of an expression: – Declare a variable of the appropriate data type – Assign the value of the expression to the variable that was declared • Use the assignment statement • Wherever the value of the expression is needed, use the variable holding the value
- 9. 9 Declaring & Initializing Variables • Variables can be initialized when declared: int first=13, second=10; char ch=' '; double x=12.6; • All variables must be initialized before they are used – But not necessarily during declaration
- 10. 10 Input (Read) Statement • cin is used with >> to gather input • The stream extraction operator is >> • For example, if miles is a double variable cin >> miles; – Causes computer to get a value of type double – Places it in the variable miles
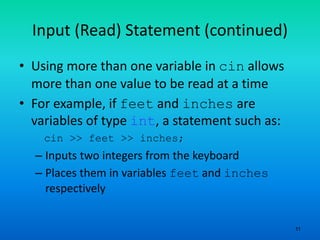
- 11. 11 Input (Read) Statement (continued) • Using more than one variable in cin allows more than one value to be read at a time • For example, if feet and inches are variables of type int, a statement such as: cin >> feet >> inches; – Inputs two integers from the keyboard – Places them in variables feet and inches respectively
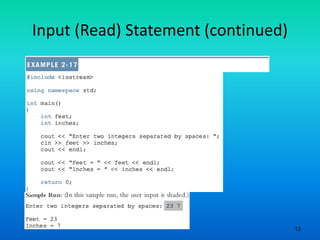
- 12. 12 Input (Read) Statement (continued)
- 13. 13 Variable Initialization • There are two ways to initialize a variable: int feet; – By using the assignment statement feet = 35; – By using a read statement cin >> feet;
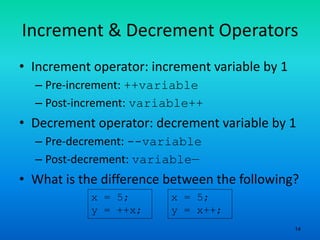
- 14. 14 Increment & Decrement Operators • Increment operator: increment variable by 1 – Pre-increment: ++variable – Post-increment: variable++ • Decrement operator: decrement variable by 1 – Pre-decrement: --variable – Post-decrement: variable— • What is the difference between the following? x = 5; y = ++x; x = 5; y = x++;
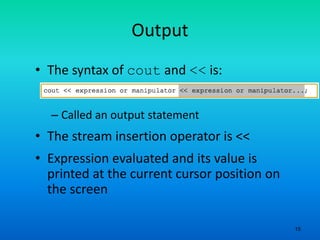
- 15. 15 Output • The syntax of cout and << is: – Called an output statement • The stream insertion operator is << • Expression evaluated and its value is printed at the current cursor position on the screen
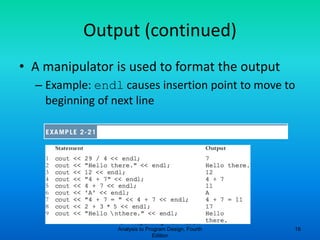
- 16. C++ Programming: From Problem Analysis to Program Design, Fourth Edition 16 Output (continued) • A manipulator is used to format the output – Example: endl causes insertion point to move to beginning of next line
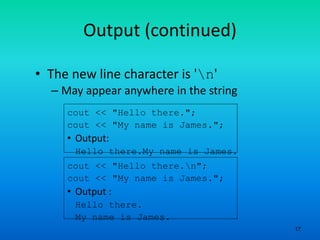
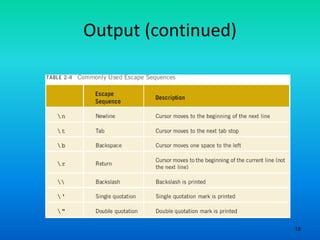
- 17. 17 Output (continued) • The new line character is 'n' – May appear anywhere in the string cout << "Hello there."; cout << "My name is James."; • Output: Hello there.My name is James. cout << "Hello there.n"; cout << "My name is James."; • Output : Hello there. My name is James.
- 19. Assignment Discuss the Usage of Assignment Operator and Declaration and Initiation of Variables in C++ Explain the Input and Output management in C++





