Object oriented programming 12 programming steps in cpp and example
Download as pptx, pdf0 likes45 views
Designing and planning is important for projects and programmes alike. It refers to the “process of setting goals, developing strategies, outlining the implementation arrangements and allocating resources to achieve those goals
1 of 16
Download to read offline













Ad
Recommended
Arithmetic and Arithmetic assignment operators



Arithmetic and Arithmetic assignment operatorsimtiazalijoono Arithmetic and Arithmetic assignment operators
Operators, Arithmetic and Arithmetic assignment operators.
Increment Operator, Decrement Operator.
Relational Operator
Lesson 5 .1 selection structure



Lesson 5 .1 selection structureMLG College of Learning, Inc The document discusses selection structures in C++ programming. It defines single-alternative and dual-alternative selection structures and explains how to represent them using pseudocode, flowcharts, and the if/else statement. It covers comparison operators that can be used in selection conditions like <, >, ==, and !=. An example program demonstrates how to use an if statement to swap two numeric values if the first is greater than the second.
Lecture 7



Lecture 7Tanveer Malik This document discusses various input statement functions in C programming. It covers the scanf(), gets(), getchar(), getch() and getc() functions. Scanf() is used to read numeric and string data from keyboard. Gets() reads a line from stdin and stores it in a string. Getchar() and getc() read a single character from stdin, with getchar() being equivalent to getc(stdin). Getch() is a non-standard function that reads a character without echoing it. The document provides the syntax and usage of each function.
halstead software science measures



halstead software science measuresDeepti Pillai The document discusses Halstead's software science measures for analyzing programs. It defines key metrics like program vocabulary, length, volume, difficulty level, and effort required. These metrics are calculated based on the number of unique operators and operands in a program. Formulas are provided to estimate values of length, volume, level and effort based on operator and operand counts. An example C program is analyzed to demonstrate calculating these metrics.
test(3)arithmetic in c



test(3)arithmetic in cJaya Malathy C supports various arithmetic operators to perform calculations on integer, float, and double data types. Expressions in C are made up of operands and operators, and follow specific precedence rules when evaluating complex expressions. Parentheses can be used to alter the default order of operations. Functions like increment/decrement can be applied either before or after using the operand in an expression.
Introduction to design and analysis of algorithm



Introduction to design and analysis of algorithmDevaKumari Vijay This document defines algorithms and describes how to analyze their efficiency. It states that an algorithm is a set of unambiguous instructions that accepts input and produces output within a finite number of steps. The document outlines criteria algorithms must satisfy like being definite, finite, and effective. It also describes different representations of algorithms like pseudocode and flowcharts. The document then discusses analyzing algorithms' time and space efficiency using asymptotic notations like Big-O, Big-Omega, and Big-Theta. It defines these notations and provides examples to classify algorithms' order of growth.
Process of algorithm evaluation



Process of algorithm evaluationAshish Ranjan This document discusses the process of evaluating the time and space complexity of algorithms. It defines time complexity as the total amount of time required by an algorithm to complete execution. Space complexity is defined as the total amount of computer memory required. Examples are provided to illustrate constant and linear time and space complexity by analyzing simple algorithms.
Object oriented programming 11 preprocessor directives and program structure



Object oriented programming 11 preprocessor directives and program structureVaibhav Khanna C++ Preprocessor. The preprocessors are the directives, which give instructions to the compiler to preprocess the information before actual compilation starts. All preprocessor directives begin with #, and only white-space characters may appear before a preprocessor directive on a line.
Ninth session



Ninth sessionAliMohammad155 This document discusses lambda functions and the import keyword in Python. It defines lambda functions as small anonymous functions that can take any number of arguments but only have one expression. Examples are provided to demonstrate lambda functions that add, multiply, and return values. The import keyword is used to import libraries into code. Syntax for importing a whole library, a single method, or all methods using wildcards is described. Examples import the os, matplotlib, scikit-learn, and cryptography libraries.
Daa



DaaPrabhat Agrawal There are two main ways to show that an algorithm works correctly: testing and proofs of correctness. Testing an algorithm on sample inputs can find bugs but does not guarantee correctness. Proving correctness mathematically is better but more difficult. To prove the correctness of a recursive algorithm, it must be proved by mathematical induction that each recursive call solves a smaller subproblem and that the base cases are solved correctly. Examples are given of using induction to prove the correctness of recursive algorithms for calculating Fibonacci numbers, finding the maximum value, and multiplying numbers.
P3



P3lksoo This document describes Programming Assignment 3 which involves implementing a bigint class that can handle integers with up to 45 decimal digits. The bigint class must overload common operators like +, -, <, >, ==, !=, <<, and >> to behave similarly to built-in int types. It also requires various constructors and storing the digit values in a private array. Students are provided guidelines for completing the assignment and submitting their code.
Cse115 lecture02overviewofprogramming



Cse115 lecture02overviewofprogrammingMd. Ashikur Rahman This document discusses number systems and complement notation in computing. It begins by explaining that complement is the negative equivalent of a number. There are two types of complement: r's complement and (r-1)'s complement. Shortcut methods are provided for calculating both types of complement in various number systems like binary, octal, decimal, and hexadecimal. Examples are given to illustrate complement calculations. The document also discusses the use of complement for performing subtraction using addition.
C++ programming program design including data structures 



C++ programming program design including data structures Ahmad Idrees The aim of this list of programming languages is to include all notable programming languages in existence, both those in current use and ... Note: This page does not list esoteric programming languages. .... Computer programming portal ...
C++ Ch3



C++ Ch3Venkateswarlu Vuggam This chapter discusses input and output (I/O) in C++ programs. It introduces I/O streams as sequences of bytes or characters that move between sources and destinations. The standard input stream cin is used to extract data from the keyboard and the standard output stream cout is used to send output to the screen. Various I/O functions are described, including extraction operator >> to read data into variables from cin, and insertion operator << to write data from variables to cout. The chapter also covers file I/O, input/output formatting, and an example program that calculates movie ticket sales and a donation amount.
Cse115 lecture03problemsolving



Cse115 lecture03problemsolvingMd. Ashikur Rahman This document discusses problem solving and the software development method. It introduces problem solving as transforming a problem description into a solution using knowledge and strategies. The software development method includes specification of needs, problem analysis, design, implementation, testing, and documentation. Pseudocode and flowcharts are presented as ways to design algorithms using control structures like sequence, selection, and repetition. Examples are provided to illustrate these concepts. Homework problems are listed at the end involving calculations, sums, and determining prime numbers.
Cse115 lecture04introtoc programming



Cse115 lecture04introtoc programmingMd. Ashikur Rahman The document provides an introduction to C programming. It discusses the main components of a C program including preprocessor directives, the main function, declarations, executable statements, and standard libraries. It then provides an example C program that converts miles to kilometers. The example demonstrates key concepts like variables, data types, input/output functions like printf and scanf, and the general flow of a C program.
Functions in c++,



Functions in c++,Padma Kannan The document discusses various concepts related to functions in C++ including:
- The main() function is the entry point of any C++ program.
- Function prototypes declare a function's name, return type, and parameters.
- Functions can pass arguments by reference by copying the reference rather than the value.
- A C++ function can return a reference similar to a pointer.
- The inline keyword before a function definition requests the compiler to replace function calls with the body code.
- Default arguments provide default values if no argument is passed during a function call.
- Function overloading allows defining multiple functions with the same name but different parameters.
Fundamental



Fundamentalguest579258 The document contains instructions for 11 fundamental programming problems to be solved in the Raptor programming language. It asks the reader to write programs that add and sum numbers, find the largest and smallest values from inputs, perform division, print even and odd numbers within ranges, and find the value of x from an equation given a, b, and c values. It specifies that each program should be saved with a naming convention of the reader's roll number and problem number, and that all programs should be compiled into a folder named with the reader's roll number.
Debugging Python with Pdb!



Debugging Python with Pdb!Noelle Daley A brief introduction python's handy built-in debugger, Pdb. Presented as a part of the Hackbright Academy summer fellowship.
Cse115 lecture08repetitionstructures part02



Cse115 lecture08repetitionstructures part02Md. Ashikur Rahman The document discusses repetition structures in C programming such as for loops, while loops, and nested loops. It provides examples of calculating a series sum using a for loop, checking if a number is prime using a for loop and selection statement inside the loop, and calculating an alternating series using a for loop. It also demonstrates the use of break and continue statements inside loops. Finally, it presents some homework problems involving loop structures.
Pa1 loops



Pa1 loopsaiclub_slides The document discusses loops in Python. It explains that a for loop iterates over a range of values and any code indented below the for statement will execute each time. It provides examples of using different range values and statements within for loops. It also mentions combining loops with conditionals, breaking out of loops, and nesting loops. Finally, it provides two programming challenges - to print even numbers and calculate factorials.
Parallel adder



Parallel adderKamil Hussain The document discusses parallel adders and subtractors. It describes a parallel binary adder as a circuit consisting of n full adders that adds n-bit binary numbers and outputs n sum bits and a carry bit, with the COUT of one full adder connected to the CIN of the next. It also mentions parallel binary adders for 2 and 4 bits, as well as a parallel binary subtractor.
4 bit add sub



4 bit add subdennis gookyi This document describes the implementation of a 4-bit adder-subtractor circuit. It first covers the implementation of a half-adder, including its truth table, circuit diagram, and module. It then covers the implementation of a full-adder, including its truth table, circuit diagram, module, and RTL schematic. Finally, it discusses the implementation of the 4-bit adder-subtractor, including its block diagram, flow chart, module, testbench, waveform, and RTL schematic. The 4-bit adder-subtractor can perform addition or subtraction depending on the carry-in bit value.
C++ ch2



C++ ch2Venkateswarlu Vuggam This document provides an overview of the key concepts covered in Chapter 2 of the C++ Programming textbook. These include basic C++ program components like functions, data types, arithmetic operators, and input/output statements. It also discusses programming fundamentals like declaring variables, writing comments, using preprocessor directives, and properly structuring a C++ program with a main function. An example is provided to demonstrate how to write a program that converts between feet/inches and centimeters.
Code optimization 



Code optimization baabtra.com - No. 1 supplier of quality freshers The document discusses various code optimization techniques that can be used to improve the efficiency of a program without changing its functionality. It covers techniques like using appropriate data types, avoiding global variables, using arrays instead of switch-case statements, combining loops, putting loops inside functions, and early termination of loops. Optimizing variables, control structures, functions and loops can help reduce memory usage and improve execution speed of a program.
parellel computing



parellel computingkatakdound 1) The document discusses parallelizing an application by dividing the work across multiple processors. It provides a simple example of summing 10^12 real numbers between 0 and 1 in parallel.
2) The example shows dividing the work of computing the sum across 8 processors. Each processor generates a portion of the input numbers and computes a partial sum, which are then combined.
3) The key steps of parallelizing an existing application are profiling it to find the most time-consuming part, designing a parallel method for that part, implementing it using a programming model like MPI, and measuring/tuning performance.
Basic Programming concepts - Programming with C++



Basic Programming concepts - Programming with C++Mohamed El Desouki أساسيات البرمجة - شرح بإستخدام لغة السى بلس بلس - C++
https://www.youtube.com/watch?v=Fr6wJ5_Hok0&list=PL1DUmTEdeA6IUD9Gt5rZlQfbZyAWXd-oD
Basic Elements of C++



Basic Elements of C++Jason J Pulikkottil This document provides an introduction to basic elements of C++ programming, including:
- The structure of a basic C++ program with an example main function.
- Common data types like integers, floating point numbers, characters, and strings.
- Arithmetic operators and precedence.
- Expressions, input/output, and type casting.
- Variables, memory allocation, and initializing variables.
- Control structures like increment/decrement operators.
- Program style guidelines including comments and formatting.
OOPS using C++



OOPS using C++CHANDERPRABHU JAIN COLLEGE OF HIGHER STUDIES & SCHOOL OF LAW This document provides an overview of a C++ programming course. It introduces fundamental C++ concepts like data types, variables, input/output statements, and arithmetic, relational, and logical operators. It also presents some simple example programs to calculate the mean of input numbers to demonstrate basic programming constructs like comments, functions, and conditional statements.
More Related Content
What's hot (18)
Ninth session



Ninth sessionAliMohammad155 This document discusses lambda functions and the import keyword in Python. It defines lambda functions as small anonymous functions that can take any number of arguments but only have one expression. Examples are provided to demonstrate lambda functions that add, multiply, and return values. The import keyword is used to import libraries into code. Syntax for importing a whole library, a single method, or all methods using wildcards is described. Examples import the os, matplotlib, scikit-learn, and cryptography libraries.
Daa



DaaPrabhat Agrawal There are two main ways to show that an algorithm works correctly: testing and proofs of correctness. Testing an algorithm on sample inputs can find bugs but does not guarantee correctness. Proving correctness mathematically is better but more difficult. To prove the correctness of a recursive algorithm, it must be proved by mathematical induction that each recursive call solves a smaller subproblem and that the base cases are solved correctly. Examples are given of using induction to prove the correctness of recursive algorithms for calculating Fibonacci numbers, finding the maximum value, and multiplying numbers.
P3



P3lksoo This document describes Programming Assignment 3 which involves implementing a bigint class that can handle integers with up to 45 decimal digits. The bigint class must overload common operators like +, -, <, >, ==, !=, <<, and >> to behave similarly to built-in int types. It also requires various constructors and storing the digit values in a private array. Students are provided guidelines for completing the assignment and submitting their code.
Cse115 lecture02overviewofprogramming



Cse115 lecture02overviewofprogrammingMd. Ashikur Rahman This document discusses number systems and complement notation in computing. It begins by explaining that complement is the negative equivalent of a number. There are two types of complement: r's complement and (r-1)'s complement. Shortcut methods are provided for calculating both types of complement in various number systems like binary, octal, decimal, and hexadecimal. Examples are given to illustrate complement calculations. The document also discusses the use of complement for performing subtraction using addition.
C++ programming program design including data structures 



C++ programming program design including data structures Ahmad Idrees The aim of this list of programming languages is to include all notable programming languages in existence, both those in current use and ... Note: This page does not list esoteric programming languages. .... Computer programming portal ...
C++ Ch3



C++ Ch3Venkateswarlu Vuggam This chapter discusses input and output (I/O) in C++ programs. It introduces I/O streams as sequences of bytes or characters that move between sources and destinations. The standard input stream cin is used to extract data from the keyboard and the standard output stream cout is used to send output to the screen. Various I/O functions are described, including extraction operator >> to read data into variables from cin, and insertion operator << to write data from variables to cout. The chapter also covers file I/O, input/output formatting, and an example program that calculates movie ticket sales and a donation amount.
Cse115 lecture03problemsolving



Cse115 lecture03problemsolvingMd. Ashikur Rahman This document discusses problem solving and the software development method. It introduces problem solving as transforming a problem description into a solution using knowledge and strategies. The software development method includes specification of needs, problem analysis, design, implementation, testing, and documentation. Pseudocode and flowcharts are presented as ways to design algorithms using control structures like sequence, selection, and repetition. Examples are provided to illustrate these concepts. Homework problems are listed at the end involving calculations, sums, and determining prime numbers.
Cse115 lecture04introtoc programming



Cse115 lecture04introtoc programmingMd. Ashikur Rahman The document provides an introduction to C programming. It discusses the main components of a C program including preprocessor directives, the main function, declarations, executable statements, and standard libraries. It then provides an example C program that converts miles to kilometers. The example demonstrates key concepts like variables, data types, input/output functions like printf and scanf, and the general flow of a C program.
Functions in c++,



Functions in c++,Padma Kannan The document discusses various concepts related to functions in C++ including:
- The main() function is the entry point of any C++ program.
- Function prototypes declare a function's name, return type, and parameters.
- Functions can pass arguments by reference by copying the reference rather than the value.
- A C++ function can return a reference similar to a pointer.
- The inline keyword before a function definition requests the compiler to replace function calls with the body code.
- Default arguments provide default values if no argument is passed during a function call.
- Function overloading allows defining multiple functions with the same name but different parameters.
Fundamental



Fundamentalguest579258 The document contains instructions for 11 fundamental programming problems to be solved in the Raptor programming language. It asks the reader to write programs that add and sum numbers, find the largest and smallest values from inputs, perform division, print even and odd numbers within ranges, and find the value of x from an equation given a, b, and c values. It specifies that each program should be saved with a naming convention of the reader's roll number and problem number, and that all programs should be compiled into a folder named with the reader's roll number.
Debugging Python with Pdb!



Debugging Python with Pdb!Noelle Daley A brief introduction python's handy built-in debugger, Pdb. Presented as a part of the Hackbright Academy summer fellowship.
Cse115 lecture08repetitionstructures part02



Cse115 lecture08repetitionstructures part02Md. Ashikur Rahman The document discusses repetition structures in C programming such as for loops, while loops, and nested loops. It provides examples of calculating a series sum using a for loop, checking if a number is prime using a for loop and selection statement inside the loop, and calculating an alternating series using a for loop. It also demonstrates the use of break and continue statements inside loops. Finally, it presents some homework problems involving loop structures.
Pa1 loops



Pa1 loopsaiclub_slides The document discusses loops in Python. It explains that a for loop iterates over a range of values and any code indented below the for statement will execute each time. It provides examples of using different range values and statements within for loops. It also mentions combining loops with conditionals, breaking out of loops, and nesting loops. Finally, it provides two programming challenges - to print even numbers and calculate factorials.
Parallel adder



Parallel adderKamil Hussain The document discusses parallel adders and subtractors. It describes a parallel binary adder as a circuit consisting of n full adders that adds n-bit binary numbers and outputs n sum bits and a carry bit, with the COUT of one full adder connected to the CIN of the next. It also mentions parallel binary adders for 2 and 4 bits, as well as a parallel binary subtractor.
4 bit add sub



4 bit add subdennis gookyi This document describes the implementation of a 4-bit adder-subtractor circuit. It first covers the implementation of a half-adder, including its truth table, circuit diagram, and module. It then covers the implementation of a full-adder, including its truth table, circuit diagram, module, and RTL schematic. Finally, it discusses the implementation of the 4-bit adder-subtractor, including its block diagram, flow chart, module, testbench, waveform, and RTL schematic. The 4-bit adder-subtractor can perform addition or subtraction depending on the carry-in bit value.
C++ ch2



C++ ch2Venkateswarlu Vuggam This document provides an overview of the key concepts covered in Chapter 2 of the C++ Programming textbook. These include basic C++ program components like functions, data types, arithmetic operators, and input/output statements. It also discusses programming fundamentals like declaring variables, writing comments, using preprocessor directives, and properly structuring a C++ program with a main function. An example is provided to demonstrate how to write a program that converts between feet/inches and centimeters.
Code optimization 



Code optimization baabtra.com - No. 1 supplier of quality freshers The document discusses various code optimization techniques that can be used to improve the efficiency of a program without changing its functionality. It covers techniques like using appropriate data types, avoiding global variables, using arrays instead of switch-case statements, combining loops, putting loops inside functions, and early termination of loops. Optimizing variables, control structures, functions and loops can help reduce memory usage and improve execution speed of a program.
parellel computing



parellel computingkatakdound 1) The document discusses parallelizing an application by dividing the work across multiple processors. It provides a simple example of summing 10^12 real numbers between 0 and 1 in parallel.
2) The example shows dividing the work of computing the sum across 8 processors. Each processor generates a portion of the input numbers and computes a partial sum, which are then combined.
3) The key steps of parallelizing an existing application are profiling it to find the most time-consuming part, designing a parallel method for that part, implementing it using a programming model like MPI, and measuring/tuning performance.
Similar to Object oriented programming 12 programming steps in cpp and example (20)
Basic Programming concepts - Programming with C++



Basic Programming concepts - Programming with C++Mohamed El Desouki أساسيات البرمجة - شرح بإستخدام لغة السى بلس بلس - C++
https://www.youtube.com/watch?v=Fr6wJ5_Hok0&list=PL1DUmTEdeA6IUD9Gt5rZlQfbZyAWXd-oD
Basic Elements of C++



Basic Elements of C++Jason J Pulikkottil This document provides an introduction to basic elements of C++ programming, including:
- The structure of a basic C++ program with an example main function.
- Common data types like integers, floating point numbers, characters, and strings.
- Arithmetic operators and precedence.
- Expressions, input/output, and type casting.
- Variables, memory allocation, and initializing variables.
- Control structures like increment/decrement operators.
- Program style guidelines including comments and formatting.
OOPS using C++



OOPS using C++CHANDERPRABHU JAIN COLLEGE OF HIGHER STUDIES & SCHOOL OF LAW This document provides an overview of a C++ programming course. It introduces fundamental C++ concepts like data types, variables, input/output statements, and arithmetic, relational, and logical operators. It also presents some simple example programs to calculate the mean of input numbers to demonstrate basic programming constructs like comments, functions, and conditional statements.
Fundamentals of Data Structures Unit 1.pptx



Fundamentals of Data Structures Unit 1.pptxVigneshkumar Ponnusamy This document outlines the objectives and topics covered in the course EC8393 - Fundamentals of Data Structures in C. The course aims to teach students about linear and non-linear data structures and their applications using the C programming language. Key topics include implementing various data structure operations in C, choosing appropriate data structures, and modifying existing or designing new data structures for applications. Assessment includes continuous internal assessments, a university exam, and a minimum 80% attendance requirement.
l1-introduction_to_computers_and_c_programming.pptx



l1-introduction_to_computers_and_c_programming.pptxssuser6f38e5 A Lecture for the c++ Course Each slide has its own narration in an audio file. For the explanation of any slide, click on the audio icon to start the narration ...
Programming using c++ tool



Programming using c++ toolAbdullah Jan I prepared these slides for the student of FSC BSC BS Computer science.these slides are very easily understanding the concept of programming in C++.All topics are clear with the help of examples easy in reading the topic and understanding the logic.
Lesson 4.1 completing the problem solving process



Lesson 4.1 completing the problem solving processMLG College of Learning, Inc This document discusses coding the algorithm into a program, which is the fourth step of the problem-solving process. It covers declaring variables, coding instructions, getting input from the keyboard using cin, displaying output to the screen using cout, arithmetic expressions and operators, type conversions, and assignment statements. Arithmetic assignment operators can abbreviate statements that contain an operator and assignment.
Prog1-L1.pdf



Prog1-L1.pdfvalerie5142000 The document introduces programming concepts in C++ including:
- The software development cycle of compile, link, and execute source code using an IDE.
- Key programming language elements like keywords, variables, operators, and constructs and how every language has a defined syntax.
- Object-oriented programming concepts in C++ like classes, objects, and inheritance hierarchies.
- A simple "Hello World" C++ program structure and basic data types and output statements.
chapter11 - Programming.pdf



chapter11 - Programming.pdfsatonaka3 This document provides an overview of computer programming concepts including:
- The difference between low-level and high-level programming languages, using Assembly and Java as examples.
- The structure of a program including algorithms, pseudocode, variables, operators, and control structures.
- Programming language basics like data types, variables, operators, and control flow are introduced using Java syntax.
- Key terms are defined like algorithms, pseudocode, compilers, interpreters, variables, data types, and operators.
Lecture1



Lecture1Andrew Raj The document summarizes the topics covered in an introduction to programming and problem solving lecture, including: 1) the six basic computer operations, 2) what programming is and the steps of program development, 3) structured programming and the three main control structures (sequence, selection, repetition), 4) data and data structures, and 5) two examples (calculating the area and circumference of a circle and solving a payroll problem) to illustrate the concepts.
Performance analysis(Time & Space Complexity)



Performance analysis(Time & Space Complexity)swapnac12 The document discusses algorithms analysis and design. It covers time complexity and space complexity analysis using approaches like counting the number of basic operations like assignments, comparisons etc. and analyzing how they vary with the size of the input. Common complexities like constant, linear, quadratic and cubic are explained with examples. Frequency count method is presented to determine tight bounds of time and space complexity of algorithms.
C programming language



C programming languageAbin Rimal This document provides an introduction to the C programming language. It discusses that C was developed in 1972 by Dennis Ritchie at Bell Labs to create the UNIX operating system. C is a structured, procedural programming language that is widely used to develop operating systems, databases, networks, and more. The document then covers some key concepts in C including functions, header files, variables, data types, operators, and escape sequences. It provides examples of basic C programs and exercises for practicing programming concepts.
L1. Basic Programming Concepts.pdf



L1. Basic Programming Concepts.pdfMMRF2 Computer programs contain instructions that tell computers what to do. Programs are written using programming languages as computers only understand machine code. There are different types of programming languages including machine language, assembly language, and high-level languages. High-level languages are easier for humans to read but must be compiled into machine code for computers to execute. Programming involves defining a problem, describing inputs and outputs, developing an algorithmic solution, and testing the program.
Chap_________________1_Introduction.pptx



Chap_________________1_Introduction.pptxRonaldo Aditya This document provides an overview of C++ programming and processing a C++ program. It discusses the evolution of programming languages and how a C++ program is compiled from source code to machine code. The document also explains that a C++ program is run by using an editor to create source code, preprocessing it, compiling it to create an object program, linking the object program, loading the executable code into memory, and executing it.
Object oriented programming 7 first steps in oop using c++



Object oriented programming 7 first steps in oop using c++Vaibhav Khanna Advantages of C++
Portability. C++ offers the feature of portability or platform independence which allows the user to run the same program on different operating systems or interfaces at ease. ...
Object-oriented. ...
Multi-paradigm. ...
Low-level Manipulation. ...
Memory Management. ...
Large Community Support. ...
Compatibility with C. ...
Scalability.
OOP Using Java Ch2 all about oop .pptx



OOP Using Java Ch2 all about oop .pptxdoopagamer This document discusses Java programming concepts such as input/output, variables, data types, operators, and conditional statements. It covers creating a Scanner to obtain user input, declaring and initializing variables, performing arithmetic operations, and using if/else statements to make decisions based on relational operators. The key topics are explained through examples of simple Java programs that print output, perform calculations, and test conditions.
Ad
More from Vaibhav Khanna (20)
Information and network security 47 authentication applications



Information and network security 47 authentication applicationsVaibhav Khanna Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users. In Kerberos Authentication server and database is used for client authentication. Kerberos runs as a third-party trusted server known as the Key Distribution Center (KDC).
Information and network security 46 digital signature algorithm



Information and network security 46 digital signature algorithmVaibhav Khanna The Digital Signature Algorithm (DSA) is a Federal Information Processing Standard for digital signatures, based on the mathematical concept of modular exponentiation and the discrete logarithm problem. DSA is a variant of the Schnorr and ElGamal signature schemes
Information and network security 45 digital signature standard



Information and network security 45 digital signature standardVaibhav Khanna The Digital Signature Standard is a Federal Information Processing Standard specifying a suite of algorithms that can be used to generate digital signatures established by the U.S. National Institute of Standards and Technology in 1994
Information and network security 44 direct digital signatures



Information and network security 44 direct digital signaturesVaibhav Khanna The Direct Digital Signature is only include two parties one to send message and other one to receive it. According to direct digital signature both parties trust each other and knows there public key. The message are prone to get corrupted and the sender can declines about the message sent by him any time
Information and network security 43 digital signatures



Information and network security 43 digital signaturesVaibhav Khanna Digital signatures are the public-key primitives of message authentication. In the physical world, it is common to use handwritten signatures on handwritten or typed messages. ... Digital signature is a cryptographic value that is calculated from the data and a secret key known only by the signer
Information and network security 42 security of message authentication code



Information and network security 42 security of message authentication codeVaibhav Khanna Message Authentication Requirements
Disclosure: Release of message contents to any person or process not possess- ing the appropriate cryptographic key.
Traffic analysis: Discovery of the pattern of traffic between parties. ...
Masquerade: Insertion of messages into the network from a fraudulent source
Information and network security 41 message authentication code



Information and network security 41 message authentication codeVaibhav Khanna Message authentication aims to protect integrity, validate originator identity, and provide non-repudiation. It addresses threats like masquerading, content or sequence modification, and source/destination repudiation. A Message Authentication Code (MAC) provides assurance that a message is unaltered and from the sender by appending a cryptographic checksum to the message dependent on the key and content. The receiver can validate the MAC to verify integrity and authenticity.
Information and network security 40 sha3 secure hash algorithm



Information and network security 40 sha3 secure hash algorithmVaibhav Khanna SHA-3 is the latest member of the Secure Hash Algorithm family of standards, released by NIST on August 5, 2015. Although part of the same series of standards, SHA-3 is internally different from the MD5-like structure of SHA-1 and SHA-2
Information and network security 39 secure hash algorithm



Information and network security 39 secure hash algorithmVaibhav Khanna The Secure Hash Algorithm (SHA) is a cryptographic hash function developed by the US National Security Agency. SHA-512 is the latest version that produces a 512-bit hash value. It processes message blocks of 1024 bits using an 80-step compression function that updates a 512-bit buffer. Each step uses a 64-bit value derived from the message and a round constant. SHA-512 supports messages up to 2^128 bits in length and adds between 1 and 1023 padding bits as needed.
Information and network security 38 birthday attacks and security of hash fun...



Information and network security 38 birthday attacks and security of hash fun...Vaibhav Khanna Birthday attack can be used in communication abusage between two or more parties. ... The mathematics behind this problem led to a well-known cryptographic attack called the birthday attack, which uses this probabilistic model to reduce the complexity of cracking a hash function
Information and network security 37 hash functions and message authentication



Information and network security 37 hash functions and message authenticationVaibhav Khanna Message Authentication Code ... A message authentication code (MAC) is similar to a cryptographic hash, except that it is based on a secret key
Information and network security 35 the chinese remainder theorem



Information and network security 35 the chinese remainder theoremVaibhav Khanna In number theory, the Chinese remainder theorem states that if one knows the remainders of the Euclidean division of an integer n by several integers, then one can determine uniquely the remainder of the division of n by the product of these integers, under the condition that the divisors are pairwise coprime.
Information and network security 34 primality



Information and network security 34 primalityVaibhav Khanna A primality test is an algorithm for determining whether an input number is prime. Among other fields of mathematics, it is used for cryptography. Unlike integer factorization, primality tests do not generally give prime factors, only stating whether the input number is prime or not
Information and network security 33 rsa algorithm



Information and network security 33 rsa algorithmVaibhav Khanna RSA algorithm is asymmetric cryptography algorithm. Asymmetric actually means that it works on two different keys i.e. Public Key and Private Key. As the name describes that the Public Key is given to everyone and Private key is kept private
Information and network security 32 principles of public key cryptosystems



Information and network security 32 principles of public key cryptosystemsVaibhav Khanna Public-key cryptography, or asymmetric cryptography, is an encryption scheme that uses two mathematically related, but not identical, keys - a public key and a private key. Unlike symmetric key algorithms that rely on one key to both encrypt and decrypt, each key performs a unique function.
Information and network security 31 public key cryptography



Information and network security 31 public key cryptographyVaibhav Khanna Public-key cryptography, or asymmetric cryptography, is a cryptographic system that uses pairs of keys: public keys, and private keys. The generation of such key pairs depends on cryptographic algorithms which are based on mathematical problems termed one-way function
Information and network security 30 random numbers



Information and network security 30 random numbersVaibhav Khanna Random numbers are fundamental building blocks of cryptographic systems and as such, play a key role in each of these elements. Random numbers are used to inject unpredictable or non-deterministic data into cryptographic algorithms and protocols to make the resulting data streams unrepeatable and virtually unguessable
Information and network security 29 international data encryption algorithm



Information and network security 29 international data encryption algorithmVaibhav Khanna International Data Encryption Algorithm (IDEA) is a once-proprietary free and open block cipher that was once intended to replace Data Encryption Standard (DES). IDEA has been and is optionally available for use with Pretty Good Privacy (PGP). IDEA has been succeeded by the IDEA NXT algorithm
Information and network security 28 blowfish



Information and network security 28 blowfishVaibhav Khanna Blowfish is a symmetric block cipher designed as a replacement for DES. It encrypts data in 64-bit blocks using a variable-length key. The algorithm uses substitution boxes and a complex key schedule to encrypt the data in multiple rounds. It is very fast, uses little memory, and is resistant to cryptanalysis due to its complex key schedule and substitution boxes.
Information and network security 27 triple des



Information and network security 27 triple desVaibhav Khanna Part of what Triple DES does is to protect against brute force attacks. The original DES symmetric encryption algorithm specified the use of 56-bit keys -- not enough, by 1999, to protect against practical brute force attacks. Triple DES specifies the use of three distinct DES keys, for a total key length of 168 bits
Ad
Recently uploaded (20)
Generative Artificial Intelligence and its Applications



Generative Artificial Intelligence and its ApplicationsSandeepKS52 The exploration of generative AI begins with an overview of its fundamental concepts, highlighting how these technologies create new content and ideas by learning from existing data. Following this, the focus shifts to the processes involved in training and fine-tuning models, which are essential for enhancing their performance and ensuring they meet specific needs. Finally, the importance of responsible AI practices is emphasized, addressing ethical considerations and the impact of AI on society, which are crucial for developing systems that are not only effective but also beneficial and fair.
Code and No-Code Journeys: The Coverage Overlook



Code and No-Code Journeys: The Coverage OverlookApplitools Explore practical ways to expand visual and functional UI coverage without deep coding or heavy maintenance in this session. Session recording and more info at applitools.com
COBOL Programming with VSCode - IBM Certificate



COBOL Programming with VSCode - IBM CertificateVICTOR MAESTRE RAMIREZ COBOL Programming with VSCode - IBM Certificate
Who will create the languages of the future?



Who will create the languages of the future?Jordi Cabot Will future languages be created by language engineers?
Can you "vibe" a DSL?
In this talk, we will explore the changing landscape of language engineering and discuss how Artificial Intelligence and low-code/no-code techniques can play a role in this future by helping in the definition, use, execution, and testing of new languages. Even empowering non-tech users to create their own language infrastructure. Maybe without them even realizing.
Bonk coin airdrop_ Everything You Need to Know.pdf



Bonk coin airdrop_ Everything You Need to Know.pdfHerond Labs The Bonk airdrop, one of the largest in Solana’s history, distributed 50% of its total supply to community members, significantly boosting its popularity and Solana’s network activity. Below is everything you need to know about the Bonk coin airdrop, including its history, eligibility, how to claim tokens, risks, and current status.
https://blog.herond.org/bonk-coin-airdrop/
Leveraging Foundation Models to Infer Intents



Leveraging Foundation Models to Infer IntentsKeheliya Gallaba Invited Talk at RAISE 2025: Requirements engineering for AI-powered SoftwarE Workshop co-located with ICSE, the IEEE/ACM International Conference on Software Engineering.
Abstract: Foundation Models (FMs) have shown remarkable capabilities in various natural language tasks. However, their ability to accurately capture stakeholder requirements remains a significant challenge for using FMs for software development. This paper introduces a novel approach that leverages an FM-powered multi-agent system called AlignMind to address this issue. By having a cognitive architecture that enhances FMs with Theory-of-Mind capabilities, our approach considers the mental states and perspectives of software makers. This allows our solution to iteratively clarify the beliefs, desires, and intentions of stakeholders, translating these into a set of refined requirements and a corresponding actionable natural language workflow in the often-overlooked requirements refinement phase of software engineering, which is crucial after initial elicitation. Through a multifaceted evaluation covering 150 diverse use cases, we demonstrate that our approach can accurately capture the intents and requirements of stakeholders, articulating them as both specifications and a step-by-step plan of action. Our findings suggest that the potential for significant improvements in the software development process justifies these investments. Our work lays the groundwork for future innovation in building intent-first development environments, where software makers can seamlessly collaborate with AIs to create software that truly meets their needs.
Marketo & Dynamics can be Most Excellent to Each Other – The Sequel



Marketo & Dynamics can be Most Excellent to Each Other – The SequelBradBedford3 So you’ve built trust in your Marketo Engage-Dynamics integration—excellent. But now what?
This sequel picks up where our last adventure left off, offering a step-by-step guide to move from stable sync to strategic power moves. We’ll share real-world project examples that empower sales and marketing to work smarter and stay aligned.
If you’re ready to go beyond the basics and do truly most excellent stuff, this session is your guide.
Artificial Intelligence Applications Across Industries



Artificial Intelligence Applications Across IndustriesSandeepKS52 Artificial Intelligence is a rapidly growing field that influences many aspects of modern life, including transportation, healthcare, and finance. Understanding the basics of AI provides insight into how machines can learn and make decisions, which is essential for grasping its applications in various industries. In the automotive sector, AI enhances vehicle safety and efficiency through advanced technologies like self-driving systems and predictive maintenance. Similarly, in healthcare, AI plays a crucial role in diagnosing diseases and personalizing treatment plans, while in financial services, it helps in fraud detection and risk management. By exploring these themes, a clearer picture of AI's transformative impact on society emerges, highlighting both its potential benefits and challenges.
Software Testing & it’s types (DevOps)



Software Testing & it’s types (DevOps)S Pranav (Deepu) NTRODUCTION TO SOFTWARE TESTING
• Definition:
• Software testing is the process of evaluating and
verifying that a software application or system meets
specified requirements and functions correctly.
• Purpose:
• Identify defects and bugs in the software.
• Ensure the software meets quality standards.
• Validate that the software performs as intended in
various scenarios.
• Importance:
• Reduces risks associated with software failures.
• Improves user satisfaction and trust in the product.
• Enhances the overall reliability and performance of
the software
The Future of Open Source Reporting Best Alternatives to Jaspersoft.pdf



The Future of Open Source Reporting Best Alternatives to Jaspersoft.pdfVarsha Nayak In recent years, organizations have increasingly sought robust open source alternative to Jasper Reports as the landscape of open-source reporting tools rapidly evolves. While Jaspersoft has been a longstanding choice for generating complex business intelligence and analytics reports, factors such as licensing changes and growing demands for flexibility have prompted many businesses to explore other options. Among the most notable alternatives to Jaspersoft, Helical Insight stands out for its powerful open-source architecture, intuitive analytics, and dynamic dashboard capabilities. Designed to be both flexible and budget-friendly, Helical Insight empowers users with advanced features—such as in-memory reporting, extensive data source integration, and customizable visualizations—making it an ideal solution for organizations seeking a modern, scalable reporting platform. This article explores the future of open-source reporting and highlights why Helical Insight and other emerging tools are redefining the standards for business intelligence solutions.
Key AI Technologies Used by Indian Artificial Intelligence Companies



Key AI Technologies Used by Indian Artificial Intelligence CompaniesMypcot Infotech Indian tech firms are rapidly adopting advanced tools like machine learning, natural language processing, and computer vision to drive innovation. These key AI technologies enable smarter automation, data analysis, and decision-making. Leading developments are shaping the future of digital transformation among top artificial intelligence companies in India.
For more information please visit here https://www.mypcot.com/artificial-intelligence
Maintaining + Optimizing Database Health: Vendors, Orchestrations, Enrichment...



Maintaining + Optimizing Database Health: Vendors, Orchestrations, Enrichment...BradBedford3 Join the Denver Marketo User Group, Captello and Integrate as we dive into the best practices, tools, and strategies for maintaining robust, high-performing databases. From managing vendors and automating orchestrations to enriching data for better insights, this session will unpack the key elements that keep your data ecosystem running smoothly—and smartly.
We will hear from Steve Armenti, Twelfth, and Aaron Karpaty, Captello, and Frannie Danzinger, Integrate.
Top 11 Fleet Management Software Providers in 2025 (2).pdf



Top 11 Fleet Management Software Providers in 2025 (2).pdfTrackobit Overwhelmed by the many fleet management software options on the market? Here’s a list of the top 11 providers available in 2025 to help you decide.
FME as an Orchestration Tool - Peak of Data & AI 2025



FME as an Orchestration Tool - Peak of Data & AI 2025Safe Software Processing huge amounts of data through FME can have performance consequences, but as an orchestration tool, FME is brilliant! We'll take a look at the principles of data gravity, best practices, pros, cons, tips and tricks. And of course all spiced up with relevant examples!
Agile Software Engineering Methodologies



Agile Software Engineering MethodologiesGaurav Sharma Software Engineering Process, Notation & Tools Introduction
Porting Qt 5 QML Modules to Qt 6 Webinar



Porting Qt 5 QML Modules to Qt 6 WebinarICS Have you upgraded your application from Qt 5 to Qt 6? If so, your QML modules might still be stuck in the old Qt 5 style—technically compatible, but far from optimal. Qt 6 introduces a modernized approach to QML modules that offers better integration with CMake, enhanced maintainability, and significant productivity gains.
In this webinar, we’ll walk you through the benefits of adopting Qt 6 style QML modules and show you how to make the transition. You'll learn how to leverage the new module system to reduce boilerplate, simplify builds, and modernize your application architecture. Whether you're planning a full migration or just exploring what's new, this session will help you get the most out of your move to Qt 6.
wAIred_RabobankIgniteSession_12062025.pptx



wAIred_RabobankIgniteSession_12062025.pptxSimonedeGijt In today's world, artificial intelligence (AI) is transforming the way we learn.
This talk will explore how we can use AI tools to enhance our learning experiences, by looking at some (recent) research that has been done on the matter.
But as we embrace these new technologies, we must also ask ourselves:
Are we becoming less capable of thinking for ourselves?
Do these tools make us smarter, or do they risk dulling our critical thinking skills?
This talk will encourage us to think critically about the role of AI in our education. Together, we will discover how to use AI to support our learning journey while still developing our ability to think critically.
FME for Climate Data: Turning Big Data into Actionable Insights



FME for Climate Data: Turning Big Data into Actionable InsightsSafe Software Regional and local governments aim to provide essential services for stormwater management systems. However, rapid urbanization and the increasing impacts of climate change are putting growing pressure on these governments to identify stormwater needs and develop effective plans. To address these challenges, GHD developed an FME solution to process over 20 years of rainfall data from rain gauges and USGS radar datasets. This solution extracts, organizes, and analyzes Next Generation Weather Radar (NEXRAD) big data, validates it with other data sources, and produces Intensity Duration Frequency (IDF) curves and future climate projections tailored to local needs. This presentation will showcase how FME can be leveraged to manage big data and prioritize infrastructure investments.
Build Smarter, Deliver Faster with Choreo - An AI Native Internal Developer P...



Build Smarter, Deliver Faster with Choreo - An AI Native Internal Developer P...WSO2 Enterprises must deliver intelligent, cloud native applications quickly—without compromising governance or scalability. This session explores how an internal developer platform increases productivity via AI for code and accelerates AI-native app delivery via code for AI. Learn practical techniques for embedding AI in the software lifecycle, automating governance with AI agents, and applying a cell-based architecture for modularity and scalability. Real-world examples and proven patterns will illustrate how to simplify delivery, enhance developer productivity, and drive measurable outcomes.
Learn more: https://wso2.com/choreo
Object oriented programming 12 programming steps in cpp and example
- 1. Object Oriented Programming:12 Programming Steps in C++ and Example Program Prof Neeraj Bhargava Vaibhav Khanna Department of Computer Science School of Engineering and Systems Sciences Maharshi Dayanand Saraswati University Ajmer
- 2. 2 Programming Example: Convert Length • Write a program that takes as input a given length expressed in feet and inches – Convert and output the length in centimeters • Input: length in feet and inches • Output: equivalent length in centimeters • Lengths are given in feet and inches • Program computes the equivalent length in centimeters • One inch is equal to 2.54 centimeters
- 3. 3 Programming Example: Convert Length (continued) • Convert the length in feet and inches to all inches: – Multiply the number of feet by 12 – Add given inches • Use the conversion formula (1 inch = 2.54 centimeters) to find the equivalent length in centimeters
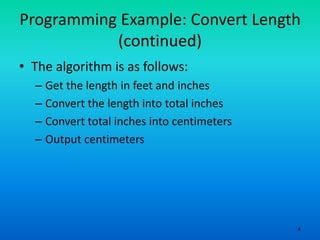
- 4. 4 Programming Example: Convert Length (continued) • The algorithm is as follows: – Get the length in feet and inches – Convert the length into total inches – Convert total inches into centimeters – Output centimeters
- 5. 5 Programming Example: Variables and Constants • Variables int feet; //variable to hold given feet int inches; //variable to hold given inches int totalInches; //variable to hold total inches double centimeters; //variable to hold length in //centimeters • Named Constant const double CENTIMETERS_PER_INCH = 2.54; const int INCHES_PER_FOOT = 12;
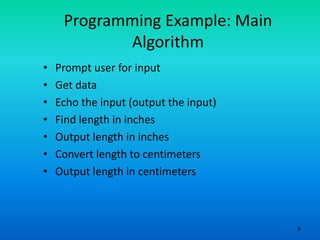
- 6. 6 Programming Example: Main Algorithm • Prompt user for input • Get data • Echo the input (output the input) • Find length in inches • Output length in inches • Convert length to centimeters • Output length in centimeters
- 7. 7 Programming Example: Putting It Together • Program begins with comments • System resources will be used for I/O • Use input statements to get data and output statements to print results • Data comes from keyboard and the output will display on the screen • The first statement of the program, after comments, is preprocessor directive to include header file iostream
- 8. 8 Programming Example: Putting It Together (continued) • Two types of memory locations for data manipulation: – Named constants • Usually put before main – Variables • This program has only one function (main), which will contain all the code • The program needs variables to manipulate data, which are declared in main
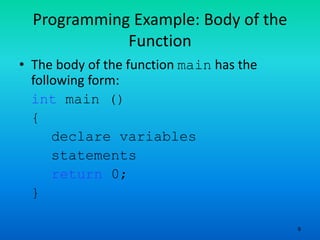
- 9. 9 Programming Example: Body of the Function • The body of the function main has the following form: int main () { declare variables statements return 0; }
- 10. 10 Programming Example: Writing a Complete Program • Begin the program with comments for documentation • Include header files • Declare named constants, if any • Write the definition of the function main
- 11. 11
- 12. 12 Programming Example: Sample Run Enter two integers, one for feet, one for inches: 15 7 The numbers you entered are 15 for feet and 7 for inches. The total number of inches = 187 The number of centimeters = 474.98
- 13. 13 Summary • C++ program: collection of functions where each program has a function called main • Identifier consists of letters, digits, and underscores, and begins with letter or underscore • The arithmetic operators in C++ are addition (+), subtraction (-),multiplication (*), division (/), and modulus (%) • Arithmetic expressions are evaluated using the precedence associativity rules
- 14. 14 Summary (continued) • All operands in an integral expression are integers and all operands in a floating-point expression are decimal numbers • Mixed expression: contains both integers and decimal numbers • Use the cast operator to explicitly convert values from one data type to another • A named constant is initialized when declared • All variables must be declared before used
- 15. 15 Summary (continued) • Use cin and stream extraction operator >> to input from the standard input device • Use cout and stream insertion operator << to output to the standard output device • Preprocessor commands are processed before the program goes through the compiler • A file containing a C++ program usually ends with the extension .cpp
- 16. Assignment • Describe in detail the programming steps for converting length in Feet and inches to centimeters • Explain the importance of “program planning and design documentation” before implementing the code / actual program



