Object oriented programming 8 basics of c++ programming
Download as pptx, pdf0 likes43 views
OOP was inventing to overcome the drawbacks of POP. It follows down -up approach. • In OOP, problem is considered as a collection of objects and objects are instance of classes.
1 of 21
Download to read offline






Ad
Recommended
Data types and Operators



Data types and Operatorsraksharao This document discusses Java primitive data types and operators. It describes the 8 primitive types in Java - boolean, byte, char, double, float, int, long, short - including their ranges and behaviors. It also covers literals, variables, scopes and lifetimes. For operators, it explains arithmetic, relational, logical, assignment, increment/decrement, shift, and ternary operators. It includes examples to demonstrate the usage of various data types and operators in Java programs.
Data Types



Data TypesNicole Ynne Estabillo This document discusses different data types in programming languages. It defines a data type as a set of values plus operations that can be performed on those values. There are two main types of data types: built-in/primitive types that are included in the language and class/programmer-defined types. Integer is one of the built-in data types that represents whole numbers and has specific valid value formats without decimals or commas. The escape character \ is also discussed as having a special meaning in C++ to change the interpretation of subsequent characters.
Constants and variables in c programming



Constants and variables in c programmingChitrank Dixit Constants are values that do not change during program execution and include numeric constants like integers and floating point numbers, as well as string or character constants. Variables are identifiers that are used to refer to values that can change during program execution. Common variable types in C include integers, floating point numbers, characters, and strings. Variables must be declared with a data type before being assigned values and have naming conventions like starting with a letter and being less than 32 characters.
Mesics lecture 3 c – constants and variables



Mesics lecture 3 c – constants and variableseShikshak The document discusses various types of constants and variables in C programming. It describes primary constants like integer, real, and character constants and defines rules for constructing each type. Secondary constants include arrays, pointers, structures, and unions. Variables represent unknown values that can change during program execution. The document outlines naming conventions and rules for defining variables. It also covers C data types like integer, floating point, characters, and void and provides details on their sizes and ranges. Initialization of variables through assignment at declaration or dynamically at runtime is also summarized.
C data type format specifier



C data type format specifierSandip Sitäulä The document discusses data types in C programming including basic types like int, float, char, and double. It also covers format specifiers used with input and output statements to specify the type of data, such as %d for integers and %f for floats. An example program is provided to determine if a user-input number is even or odd using the scanf and printf functions.
Constant and variacles in c



Constant and variacles in cyash patel The document discusses different types of constants and variables in C programming. It describes integer, real, character, and string constants. Integer constants can be decimal, octal, or hexadecimal. Real constants represent quantities that vary continuously, with a mantissa and exponent. Character constants contain a single character within single quotes. String constants contain a sequence of characters within double quotes. Variables are names that store changing data values during program execution, while constants remain unchanged. Variables must start with a letter and can contain letters, digits, and underscores.
MAGNITUDE COMPARATOR & DECODER



MAGNITUDE COMPARATOR & DECODERUsama ahmad This document discusses magnitude comparators and decoders. A magnitude comparator is a circuit that compares two input numbers in binary form and determines if one is greater than, less than, or equal to the other. Magnitude comparators are used in CPUs. Decoders are circuits that convert binary input into unique output lines. Common types include 2-to-4 decoders, 3-to-8 decoders used for 7-segment displays, and 4-to-10 decoders. Decoders have applications in memory systems, I/O selection, and displaying decimal numbers.
Data Type in C Programming



Data Type in C ProgrammingQazi Shahzad Ali This document provides an overview of data types in C programming, including:
1) It describes four main types of data types - fundamental, modifiers, derived, and user defined. Fundamental types include integer, character, float, void. Modifiers change properties of other types. Derived types include arrays and pointers.
2) It explains the integer, float, character, and void fundamental data types in more detail. Integer can be short, int, long. Float and double store numbers in mantissa and exponent. Character represents keyboard characters.
3) Common C data type sizes and value ranges are provided for integer, float, and character types along with their modifiers like short, long, signed, unsigned.
Decimal, Binary, Octal, And Hexadecimal number systems.



Decimal, Binary, Octal, And Hexadecimal number systems.AOUN ABBAS Details about DECIMAL, BINARY, OCTAL & HEXADECIMAL in the form of slides or ppt for presentation this topic.
Constant, variables, data types



Constant, variables, data typesPratik Devmurari This presentation for student, who study about CPU(Computer Programming Utilization) in first year or Sem1 and Sem2 of GTU and many more universities.
Object oriented programming 13 input stream and devices in cpp



Object oriented programming 13 input stream and devices in cppVaibhav Khanna In C++ input and output is performed in the form of a sequence of bytes or more commonly known as streams. Input Stream: If the direction of flow of bytes is from the device(for example, Keyboard) to the main memory then this process is called input.
Gates and Flip flop



Gates and Flip flophamza munir Logic gates are the basic building blocks of digital systems and have one or more inputs and one output. There are seven main logic gates: AND, OR, NOT, NAND, NOR, XOR, and XNOR. Each gate has a logical diagram, algebraic function, and truth table that defines the relationship between its inputs and output. Flip-flops are also digital logic circuits that have two states and maintain their state until triggered by an input pulse.
Introduction to binary number system



Introduction to binary number systemVikas Dongre This document discusses different number systems used in digital techniques. It defines analog and digital signals, with analog having continuous values and digital having a finite set of discrete values. Four main number systems are covered: decimal with base 10, binary with base 2, octal with base 8, and hexadecimal with base 16. Each system's base, symbols used, examples of representations, and how place values determine a number's value are explained. The document aims to introduce students to number systems and their applications in digital contexts.
Number Systems



Number SystemsGaditek This lecture discusses the von Neumann model of computer architecture and number systems. It describes the von Neumann model as having four subsystems - memory, ALU, control unit, and I/O. It stores both programs and data in memory, and executes instructions sequentially. The lecture also covers different number systems like binary, decimal, octal and hexadecimal that computers use to represent data, and how to convert between number bases.
Datatype in c++ unit 3 -topic 2



Datatype in c++ unit 3 -topic 2MOHIT TOMAR This document discusses data types in C++. It describes the three main categories of data types: primitive/fundamental types like int and char, derived types which are based on primitive types, and user-defined types created with structures. It also covers data type modifiers, constants/literals of different data types, and rules for declaring variables in C++ like their scope and naming conventions.
Object oriented programming 11 preprocessor directives and program structure



Object oriented programming 11 preprocessor directives and program structureVaibhav Khanna C++ Preprocessor. The preprocessors are the directives, which give instructions to the compiler to preprocess the information before actual compilation starts. All preprocessor directives begin with #, and only white-space characters may appear before a preprocessor directive on a line.
C programming Tutorial Session 1



C programming Tutorial Session 1Muhammad Ehtisham Siddiqui The document discusses the basics of C programming language. It defines commands, programs, and software. C was created in 1972 and is well-suited for systems programming and operating systems. The structure of a C program includes main functions, delimiters, comments, and the standard library. Problems are solved through algorithms, pseudocode, and flowcharts which use symbols to represent program logic and control flow.
Numeric Data Types & Strings



Numeric Data Types & StringsAbhinav Porwal This document summarizes different data types including numeric, enumeration, Boolean, character, character strings, pointers, files, and input-output. It provides details on integer, floating-point real numbers, fixed-point real numbers, character strings, and pointers and programmer-constructed data objects. Integer data types can represent a finite set of mathematical integers and have different sizes and may or may not contain negative values. Floating-point numbers use a mantissa-exponent representation similar to scientific notation. Fixed-point numbers have a predefined number of decimal places. Character strings can have fixed or variable lengths and support operations like concatenation and substring selection. Pointers reference data in memory and programmer-constructed objects can be complex data
2 expressions (ppt-2) in C++



2 expressions (ppt-2) in C++Kuntal Bhowmick C++ / CPP / C PLUS PLUS notes, object oriented programming using C++ / CPP / C PLUS PLUS, C++ / CPP / C PLUS PLUS tutorial, lecture notes, C++ / CPP / C PLUS PLUS programming notes, C++ / CPP / C PLUS PLUS example programs, C++ / CPP / C PLUS PLUS programs with explanation, C++ / CPP / C PLUS PLUS source code with output, C++ / CPP / C PLUS PLUS programs, C++ / CPP / C PLUS PLUS coding, C++ / CPP / C PLUS PLUS codes, C++ / CPP / C PLUS PLUS slides, C++ / CPP / C PLUS PLUS notes
Computer Programming



Computer ProgrammingBurhan Fakhar This document discusses C++ programming and includes several sections:
- It provides an overview of how a C++ program is processed by a compiler and linker before being executed.
- It explains the problem analysis-coding-execution cycle used for programming and problem solving.
- It presents an example algorithm for calculating the perimeter and area of a rectangle.
- It outlines the basic elements and components of a C++ program such as functions, data types, operators, and comments.
constants, variables and datatypes in C



constants, variables and datatypes in CSahithi Naraparaju This document provides an overview of constants, variables, and data types in the C programming language. It discusses the different categories of characters used in C, C tokens including keywords, identifiers, constants, strings, special symbols, and operators. It also covers rules for identifiers and variables, integer constants, real constants, single character constants, string constants, and backslash character constants. Finally, it describes the primary data types in C including integer, character, floating point, double, and void, as well as integer, floating point, and character types.
Data types



Data typesZahid Hussain This document discusses different data types in C/C++ including character, integer, and real (float) data types. It explains that character data can be signed or unsigned and occupies 1 byte, integer data represents whole numbers using the int type, and float data represents decimal numbers. The document also covers numeric and non-numeric constants in C/C++ such as integer, octal, hexadecimal, floating point, character, and string constants.
Data types



Data typesSyed Umair This document assigns a group project on data types in C++ to seven students. It discusses the three main data types in C++ - character, integer, and float. Character data can store single characters, integer data stores whole numbers, and float data stores numeric values with decimals. It also covers variable declaration and initialization in C++, noting that variables must be declared before use and can be initialized with a value upon declaration. The document assigns different aspects of the data types topic to the seven students listed at the top for further explanation in the project.
Cp presentation



Cp presentationMeetaPrajapati This document provides an overview of the basics of the C programming language, including its character set, tokens, symbolic constants, and data types. The character set of C consists of letters, digits, whitespace, and special symbols. The smallest units of a C program are tokens, which include keywords, identifiers, constants, operators, strings, and special symbols. Symbolic constants are user-defined names for fixed values, defined using the #define preprocessor directive. C supports primary, derived, and user-defined data types, including integer, floating-point, character, and other types that specify the size and range of variable values.
Numbersystem 130621192712-phpapp02



Numbersystem 130621192712-phpapp02muhammadsarab This document discusses different number systems including decimal, binary, octal, and hexadecimal. It provides information on how each system works including the base and valid digits used. Conversion methods between the different systems are also described, such as using repeated division to convert decimal to binary and multiplying place values to convert in the opposite direction. The relationships between the number systems are examined, like how each hexadecimal digit represents 4 binary digits.
Computerarchitecture by csa



Computerarchitecture by csabathala sudhakar This document discusses various methods of data representation in digital systems. It covers data types, number systems, representation of decimal and negative numbers using binary, BCD, signed magnitude, 1's complement and 2's complement. It also discusses floating point and fixed point representation, overflow detection, and error detecting codes like parity bits which can detect errors during data transmission.
Programming construction tools



Programming construction toolssunilchute1 The document provides information about programming tools and concepts in C programming. It discusses algorithms and flowcharts as programming construction tools. It defines an algorithm as step-by-step instructions to solve a problem and lists qualities of good algorithms. It also defines a flowchart as a diagram that represents an algorithm using different shapes and arrows. The document then discusses basic and derived data types in C language such as int, char, float, arrays, pointers, structures and unions. It lists keywords and rules for defining variables in C.
Basics of c++ Programming Language



Basics of c++ Programming LanguageAhmad Idrees The aim of this list of programming languages is to include all notable programming languages in existence, both those in current use and ... Note: This page does not list esoteric programming languages. .... Computer programming portal ...
C++ ch2



C++ ch2Venkateswarlu Vuggam This document provides an overview of the key concepts covered in Chapter 2 of the C++ Programming textbook. These include basic C++ program components like functions, data types, arithmetic operators, and input/output statements. It also discusses programming fundamentals like declaring variables, writing comments, using preprocessor directives, and properly structuring a C++ program with a main function. An example is provided to demonstrate how to write a program that converts between feet/inches and centimeters.
Chap_________________1_Introduction.pptx



Chap_________________1_Introduction.pptxRonaldo Aditya This document provides an overview of C++ programming and processing a C++ program. It discusses the evolution of programming languages and how a C++ program is compiled from source code to machine code. The document also explains that a C++ program is run by using an editor to create source code, preprocessing it, compiling it to create an object program, linking the object program, loading the executable code into memory, and executing it.
More Related Content
What's hot (19)
Decimal, Binary, Octal, And Hexadecimal number systems.



Decimal, Binary, Octal, And Hexadecimal number systems.AOUN ABBAS Details about DECIMAL, BINARY, OCTAL & HEXADECIMAL in the form of slides or ppt for presentation this topic.
Constant, variables, data types



Constant, variables, data typesPratik Devmurari This presentation for student, who study about CPU(Computer Programming Utilization) in first year or Sem1 and Sem2 of GTU and many more universities.
Object oriented programming 13 input stream and devices in cpp



Object oriented programming 13 input stream and devices in cppVaibhav Khanna In C++ input and output is performed in the form of a sequence of bytes or more commonly known as streams. Input Stream: If the direction of flow of bytes is from the device(for example, Keyboard) to the main memory then this process is called input.
Gates and Flip flop



Gates and Flip flophamza munir Logic gates are the basic building blocks of digital systems and have one or more inputs and one output. There are seven main logic gates: AND, OR, NOT, NAND, NOR, XOR, and XNOR. Each gate has a logical diagram, algebraic function, and truth table that defines the relationship between its inputs and output. Flip-flops are also digital logic circuits that have two states and maintain their state until triggered by an input pulse.
Introduction to binary number system



Introduction to binary number systemVikas Dongre This document discusses different number systems used in digital techniques. It defines analog and digital signals, with analog having continuous values and digital having a finite set of discrete values. Four main number systems are covered: decimal with base 10, binary with base 2, octal with base 8, and hexadecimal with base 16. Each system's base, symbols used, examples of representations, and how place values determine a number's value are explained. The document aims to introduce students to number systems and their applications in digital contexts.
Number Systems



Number SystemsGaditek This lecture discusses the von Neumann model of computer architecture and number systems. It describes the von Neumann model as having four subsystems - memory, ALU, control unit, and I/O. It stores both programs and data in memory, and executes instructions sequentially. The lecture also covers different number systems like binary, decimal, octal and hexadecimal that computers use to represent data, and how to convert between number bases.
Datatype in c++ unit 3 -topic 2



Datatype in c++ unit 3 -topic 2MOHIT TOMAR This document discusses data types in C++. It describes the three main categories of data types: primitive/fundamental types like int and char, derived types which are based on primitive types, and user-defined types created with structures. It also covers data type modifiers, constants/literals of different data types, and rules for declaring variables in C++ like their scope and naming conventions.
Object oriented programming 11 preprocessor directives and program structure



Object oriented programming 11 preprocessor directives and program structureVaibhav Khanna C++ Preprocessor. The preprocessors are the directives, which give instructions to the compiler to preprocess the information before actual compilation starts. All preprocessor directives begin with #, and only white-space characters may appear before a preprocessor directive on a line.
C programming Tutorial Session 1



C programming Tutorial Session 1Muhammad Ehtisham Siddiqui The document discusses the basics of C programming language. It defines commands, programs, and software. C was created in 1972 and is well-suited for systems programming and operating systems. The structure of a C program includes main functions, delimiters, comments, and the standard library. Problems are solved through algorithms, pseudocode, and flowcharts which use symbols to represent program logic and control flow.
Numeric Data Types & Strings



Numeric Data Types & StringsAbhinav Porwal This document summarizes different data types including numeric, enumeration, Boolean, character, character strings, pointers, files, and input-output. It provides details on integer, floating-point real numbers, fixed-point real numbers, character strings, and pointers and programmer-constructed data objects. Integer data types can represent a finite set of mathematical integers and have different sizes and may or may not contain negative values. Floating-point numbers use a mantissa-exponent representation similar to scientific notation. Fixed-point numbers have a predefined number of decimal places. Character strings can have fixed or variable lengths and support operations like concatenation and substring selection. Pointers reference data in memory and programmer-constructed objects can be complex data
2 expressions (ppt-2) in C++



2 expressions (ppt-2) in C++Kuntal Bhowmick C++ / CPP / C PLUS PLUS notes, object oriented programming using C++ / CPP / C PLUS PLUS, C++ / CPP / C PLUS PLUS tutorial, lecture notes, C++ / CPP / C PLUS PLUS programming notes, C++ / CPP / C PLUS PLUS example programs, C++ / CPP / C PLUS PLUS programs with explanation, C++ / CPP / C PLUS PLUS source code with output, C++ / CPP / C PLUS PLUS programs, C++ / CPP / C PLUS PLUS coding, C++ / CPP / C PLUS PLUS codes, C++ / CPP / C PLUS PLUS slides, C++ / CPP / C PLUS PLUS notes
Computer Programming



Computer ProgrammingBurhan Fakhar This document discusses C++ programming and includes several sections:
- It provides an overview of how a C++ program is processed by a compiler and linker before being executed.
- It explains the problem analysis-coding-execution cycle used for programming and problem solving.
- It presents an example algorithm for calculating the perimeter and area of a rectangle.
- It outlines the basic elements and components of a C++ program such as functions, data types, operators, and comments.
constants, variables and datatypes in C



constants, variables and datatypes in CSahithi Naraparaju This document provides an overview of constants, variables, and data types in the C programming language. It discusses the different categories of characters used in C, C tokens including keywords, identifiers, constants, strings, special symbols, and operators. It also covers rules for identifiers and variables, integer constants, real constants, single character constants, string constants, and backslash character constants. Finally, it describes the primary data types in C including integer, character, floating point, double, and void, as well as integer, floating point, and character types.
Data types



Data typesZahid Hussain This document discusses different data types in C/C++ including character, integer, and real (float) data types. It explains that character data can be signed or unsigned and occupies 1 byte, integer data represents whole numbers using the int type, and float data represents decimal numbers. The document also covers numeric and non-numeric constants in C/C++ such as integer, octal, hexadecimal, floating point, character, and string constants.
Data types



Data typesSyed Umair This document assigns a group project on data types in C++ to seven students. It discusses the three main data types in C++ - character, integer, and float. Character data can store single characters, integer data stores whole numbers, and float data stores numeric values with decimals. It also covers variable declaration and initialization in C++, noting that variables must be declared before use and can be initialized with a value upon declaration. The document assigns different aspects of the data types topic to the seven students listed at the top for further explanation in the project.
Cp presentation



Cp presentationMeetaPrajapati This document provides an overview of the basics of the C programming language, including its character set, tokens, symbolic constants, and data types. The character set of C consists of letters, digits, whitespace, and special symbols. The smallest units of a C program are tokens, which include keywords, identifiers, constants, operators, strings, and special symbols. Symbolic constants are user-defined names for fixed values, defined using the #define preprocessor directive. C supports primary, derived, and user-defined data types, including integer, floating-point, character, and other types that specify the size and range of variable values.
Numbersystem 130621192712-phpapp02



Numbersystem 130621192712-phpapp02muhammadsarab This document discusses different number systems including decimal, binary, octal, and hexadecimal. It provides information on how each system works including the base and valid digits used. Conversion methods between the different systems are also described, such as using repeated division to convert decimal to binary and multiplying place values to convert in the opposite direction. The relationships between the number systems are examined, like how each hexadecimal digit represents 4 binary digits.
Computerarchitecture by csa



Computerarchitecture by csabathala sudhakar This document discusses various methods of data representation in digital systems. It covers data types, number systems, representation of decimal and negative numbers using binary, BCD, signed magnitude, 1's complement and 2's complement. It also discusses floating point and fixed point representation, overflow detection, and error detecting codes like parity bits which can detect errors during data transmission.
Programming construction tools



Programming construction toolssunilchute1 The document provides information about programming tools and concepts in C programming. It discusses algorithms and flowcharts as programming construction tools. It defines an algorithm as step-by-step instructions to solve a problem and lists qualities of good algorithms. It also defines a flowchart as a diagram that represents an algorithm using different shapes and arrows. The document then discusses basic and derived data types in C language such as int, char, float, arrays, pointers, structures and unions. It lists keywords and rules for defining variables in C.
Similar to Object oriented programming 8 basics of c++ programming (20)
Basics of c++ Programming Language



Basics of c++ Programming LanguageAhmad Idrees The aim of this list of programming languages is to include all notable programming languages in existence, both those in current use and ... Note: This page does not list esoteric programming languages. .... Computer programming portal ...
C++ ch2



C++ ch2Venkateswarlu Vuggam This document provides an overview of the key concepts covered in Chapter 2 of the C++ Programming textbook. These include basic C++ program components like functions, data types, arithmetic operators, and input/output statements. It also discusses programming fundamentals like declaring variables, writing comments, using preprocessor directives, and properly structuring a C++ program with a main function. An example is provided to demonstrate how to write a program that converts between feet/inches and centimeters.
Chap_________________1_Introduction.pptx



Chap_________________1_Introduction.pptxRonaldo Aditya This document provides an overview of C++ programming and processing a C++ program. It discusses the evolution of programming languages and how a C++ program is compiled from source code to machine code. The document also explains that a C++ program is run by using an editor to create source code, preprocessing it, compiling it to create an object program, linking the object program, loading the executable code into memory, and executing it.
C++.ppt



C++.pptshweta210 This chapter discusses the basic elements of C++ programs, including functions, data types, operators, and input/output statements. It covers fundamental concepts like declaring variables and constants, arithmetic expressions, strings, and comments. The objectives are to familiarize readers with C++ syntax and semantics, and teach them how to properly structure a basic C++ program.
PPT slide_chapter 02 Basic element of C++.ppt



PPT slide_chapter 02 Basic element of C++.pptmasadjie Cpp programming from problem analysis to program design.
9781285852744 ppt ch02



9781285852744 ppt ch02Terry Yoast The chapter introduces the basic components of a C++ program, including functions, data types, operators, and statements. It discusses simple data types like integers, characters, and floating-point numbers. The chapter also covers arithmetic operators, expressions, and the order of precedence. It explains variable declaration, assignment statements, and how to input and output data. The goal is for readers to understand the basic structure and syntax of a C++ program.
Basic elements of java 



Basic elements of java Ahmad Idrees Java is a computer programming language that is concurrent, class-based, object-oriented, and specifically designed to have as few implementation dependencies as possible.
programming week 2.ppt



programming week 2.pptFatimaZafar68 The document provides an introduction to programming fundamentals in C++, including basic syntax and components of a C++ program. It covers variables and data types, input/output, comments, and how to write a simple C++ program with preprocessor directives and a main function. The key topics discussed are variable declaration, fundamental data types like int, float, char, comments, and how to write a basic "Hello World" program in C++.
Lecture 2 variables



Lecture 2 variablesTony Apreku This document provides an introduction to programming with C++, including comments, data types, variables, arithmetic operators, and expressions. It discusses single-line and multi-line comments to document code. The fundamental C++ data types are integer, floating point, and character, each with different size ranges. Variables are declared with a data type and assigned values. Arithmetic operators allow mathematical expressions to be evaluated using precedence rules. Relational operators enable boolean expressions.
BCP_u2.pptxBCP_u2.pptxBCP_u2.pptxBCP_u2.pptx



BCP_u2.pptxBCP_u2.pptxBCP_u2.pptxBCP_u2.pptxRutviBaraiya BCP_u2.pptxBCP_u2.pptxBCP_u2.pptxBCP_u2.pptxBCP_u2.pptxBCP_u2.pptx
5 conceptos progamacion2-tema4



5 conceptos progamacion2-tema4Elba Sepúlveda The document discusses various concepts related to computer problem solving including defining a problem, developing an algorithm to solve it, writing a computer program, testing the program, and interpreting results. It also covers fundamental programming concepts such as variables, constants, data types, operators, expressions, and equations that are used to represent and solve problems computationally. Problem solving with computers involves several defined steps and utilizes various programming constructs.
INTRODUCTION TO C PROGRAMMING in basic c language



INTRODUCTION TO C PROGRAMMING in basic c languageGOKULKANNANMMECLECTC This document provides an overview of C programming basics, including:
- The structure of a C program includes header files, source code files, and libraries that are compiled and linked.
- C programming supports various data types like characters, integers, floating-point numbers, and more to store values in memory.
- Key aspects of C programming covered include input/output operations, decision making, looping, and programming examples.
Data structure Unit-I Part A



Data structure Unit-I Part ASSN College of Engineering, Kalavakkam This document provides an overview of data structures and algorithms. It discusses pseudo code, abstract data types, atomic and composite data, data structures, algorithm efficiency using Big O notation, and various searching algorithms like sequential, binary, and hashed list searches. Key concepts covered include pseudo code structure and syntax, defining algorithms with headers and conditions, and analyzing different search algorithms.
Lecture 2



Lecture 2marvellous2 The document provides information on fundamental C data types including bits, bytes, words, integers, floating point numbers, enumerated types, variables, type conversions, constants, and basic operators. It defines common data types like char, int, float, and double. It also covers typecasting, variable declaration, and basic arithmetic, logical, relational, and bitwise operators.
C programming language



C programming languageAbin Rimal This document provides an introduction to the C programming language. It discusses that C was developed in 1972 by Dennis Ritchie at Bell Labs to create the UNIX operating system. C is a structured, procedural programming language that is widely used to develop operating systems, databases, networks, and more. The document then covers some key concepts in C including functions, header files, variables, data types, operators, and escape sequences. It provides examples of basic C programs and exercises for practicing programming concepts.
1.4 Work with data types and variables, numeric data, string data.pptx



1.4 Work with data types and variables, numeric data, string data.pptxVGaneshKarthikeyan This presentation covers Python data types, variables, and how to work with numeric and string data. It discusses the basic data types in Python including integers, floats, and strings. It explains how to assign values to variables and name variables appropriately. The presentation also covers arithmetic operators and order of precedence, how to perform calculations with numeric data, and common string operations like indexing, slicing, and escape sequences.
B.sc CSIT 2nd semester C++ Unit2



B.sc CSIT 2nd semester C++ Unit2Tekendra Nath Yogi This document provides an overview of the C++ programming language. It discusses that C++ is a statically typed, compiled language that supports procedural and object-oriented programming. C++ was developed in 1979 by Bjarne Stroustrup as an enhancement to C with object-oriented capabilities. The document then covers various C++ concepts like data types, operators, program structure, and differences between C and C++.
Ad
More from Vaibhav Khanna (20)
Information and network security 47 authentication applications



Information and network security 47 authentication applicationsVaibhav Khanna Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users. In Kerberos Authentication server and database is used for client authentication. Kerberos runs as a third-party trusted server known as the Key Distribution Center (KDC).
Information and network security 46 digital signature algorithm



Information and network security 46 digital signature algorithmVaibhav Khanna The Digital Signature Algorithm (DSA) is a Federal Information Processing Standard for digital signatures, based on the mathematical concept of modular exponentiation and the discrete logarithm problem. DSA is a variant of the Schnorr and ElGamal signature schemes
Information and network security 45 digital signature standard



Information and network security 45 digital signature standardVaibhav Khanna The Digital Signature Standard is a Federal Information Processing Standard specifying a suite of algorithms that can be used to generate digital signatures established by the U.S. National Institute of Standards and Technology in 1994
Information and network security 44 direct digital signatures



Information and network security 44 direct digital signaturesVaibhav Khanna The Direct Digital Signature is only include two parties one to send message and other one to receive it. According to direct digital signature both parties trust each other and knows there public key. The message are prone to get corrupted and the sender can declines about the message sent by him any time
Information and network security 43 digital signatures



Information and network security 43 digital signaturesVaibhav Khanna Digital signatures are the public-key primitives of message authentication. In the physical world, it is common to use handwritten signatures on handwritten or typed messages. ... Digital signature is a cryptographic value that is calculated from the data and a secret key known only by the signer
Information and network security 42 security of message authentication code



Information and network security 42 security of message authentication codeVaibhav Khanna Message Authentication Requirements
Disclosure: Release of message contents to any person or process not possess- ing the appropriate cryptographic key.
Traffic analysis: Discovery of the pattern of traffic between parties. ...
Masquerade: Insertion of messages into the network from a fraudulent source
Information and network security 41 message authentication code



Information and network security 41 message authentication codeVaibhav Khanna Message authentication aims to protect integrity, validate originator identity, and provide non-repudiation. It addresses threats like masquerading, content or sequence modification, and source/destination repudiation. A Message Authentication Code (MAC) provides assurance that a message is unaltered and from the sender by appending a cryptographic checksum to the message dependent on the key and content. The receiver can validate the MAC to verify integrity and authenticity.
Information and network security 40 sha3 secure hash algorithm



Information and network security 40 sha3 secure hash algorithmVaibhav Khanna SHA-3 is the latest member of the Secure Hash Algorithm family of standards, released by NIST on August 5, 2015. Although part of the same series of standards, SHA-3 is internally different from the MD5-like structure of SHA-1 and SHA-2
Information and network security 39 secure hash algorithm



Information and network security 39 secure hash algorithmVaibhav Khanna The Secure Hash Algorithm (SHA) is a cryptographic hash function developed by the US National Security Agency. SHA-512 is the latest version that produces a 512-bit hash value. It processes message blocks of 1024 bits using an 80-step compression function that updates a 512-bit buffer. Each step uses a 64-bit value derived from the message and a round constant. SHA-512 supports messages up to 2^128 bits in length and adds between 1 and 1023 padding bits as needed.
Information and network security 38 birthday attacks and security of hash fun...



Information and network security 38 birthday attacks and security of hash fun...Vaibhav Khanna Birthday attack can be used in communication abusage between two or more parties. ... The mathematics behind this problem led to a well-known cryptographic attack called the birthday attack, which uses this probabilistic model to reduce the complexity of cracking a hash function
Information and network security 37 hash functions and message authentication



Information and network security 37 hash functions and message authenticationVaibhav Khanna Message Authentication Code ... A message authentication code (MAC) is similar to a cryptographic hash, except that it is based on a secret key
Information and network security 35 the chinese remainder theorem



Information and network security 35 the chinese remainder theoremVaibhav Khanna In number theory, the Chinese remainder theorem states that if one knows the remainders of the Euclidean division of an integer n by several integers, then one can determine uniquely the remainder of the division of n by the product of these integers, under the condition that the divisors are pairwise coprime.
Information and network security 34 primality



Information and network security 34 primalityVaibhav Khanna A primality test is an algorithm for determining whether an input number is prime. Among other fields of mathematics, it is used for cryptography. Unlike integer factorization, primality tests do not generally give prime factors, only stating whether the input number is prime or not
Information and network security 33 rsa algorithm



Information and network security 33 rsa algorithmVaibhav Khanna RSA algorithm is asymmetric cryptography algorithm. Asymmetric actually means that it works on two different keys i.e. Public Key and Private Key. As the name describes that the Public Key is given to everyone and Private key is kept private
Information and network security 32 principles of public key cryptosystems



Information and network security 32 principles of public key cryptosystemsVaibhav Khanna Public-key cryptography, or asymmetric cryptography, is an encryption scheme that uses two mathematically related, but not identical, keys - a public key and a private key. Unlike symmetric key algorithms that rely on one key to both encrypt and decrypt, each key performs a unique function.
Information and network security 31 public key cryptography



Information and network security 31 public key cryptographyVaibhav Khanna Public-key cryptography, or asymmetric cryptography, is a cryptographic system that uses pairs of keys: public keys, and private keys. The generation of such key pairs depends on cryptographic algorithms which are based on mathematical problems termed one-way function
Information and network security 30 random numbers



Information and network security 30 random numbersVaibhav Khanna Random numbers are fundamental building blocks of cryptographic systems and as such, play a key role in each of these elements. Random numbers are used to inject unpredictable or non-deterministic data into cryptographic algorithms and protocols to make the resulting data streams unrepeatable and virtually unguessable
Information and network security 29 international data encryption algorithm



Information and network security 29 international data encryption algorithmVaibhav Khanna International Data Encryption Algorithm (IDEA) is a once-proprietary free and open block cipher that was once intended to replace Data Encryption Standard (DES). IDEA has been and is optionally available for use with Pretty Good Privacy (PGP). IDEA has been succeeded by the IDEA NXT algorithm
Information and network security 28 blowfish



Information and network security 28 blowfishVaibhav Khanna Blowfish is a symmetric block cipher designed as a replacement for DES. It encrypts data in 64-bit blocks using a variable-length key. The algorithm uses substitution boxes and a complex key schedule to encrypt the data in multiple rounds. It is very fast, uses little memory, and is resistant to cryptanalysis due to its complex key schedule and substitution boxes.
Information and network security 27 triple des



Information and network security 27 triple desVaibhav Khanna Part of what Triple DES does is to protect against brute force attacks. The original DES symmetric encryption algorithm specified the use of 56-bit keys -- not enough, by 1999, to protect against practical brute force attacks. Triple DES specifies the use of three distinct DES keys, for a total key length of 168 bits
Ad
Recently uploaded (20)
FME as an Orchestration Tool - Peak of Data & AI 2025



FME as an Orchestration Tool - Peak of Data & AI 2025Safe Software Processing huge amounts of data through FME can have performance consequences, but as an orchestration tool, FME is brilliant! We'll take a look at the principles of data gravity, best practices, pros, cons, tips and tricks. And of course all spiced up with relevant examples!
How Insurance Policy Management Software Streamlines Operations



How Insurance Policy Management Software Streamlines OperationsInsurance Tech Services Insurance policy management software transforms complex, manual insurance operations into streamlined, efficient digital workflows, enhancing productivity, accuracy, customer service, and profitability for insurers. Visit https://www.damcogroup.com/insurance/policy-management-software for more details!
Wondershare PDFelement Pro 11.4.20.3548 Crack Free Download



Wondershare PDFelement Pro 11.4.20.3548 Crack Free DownloadPuppy jhon ➡ 🌍📱👉COPY & PASTE LINK👉👉👉 ➤ ➤➤ https://drfiles.net/
Wondershare PDFelement Professional is professional software that can edit PDF files. This digital tool can manipulate elements in PDF documents.
OpenTelemetry 101 Cloud Native Barcelona



OpenTelemetry 101 Cloud Native BarcelonaImma Valls Bernaus A brief introduction to OpenTelemetry, with a practical example of auto-instrumenting a Java web application with the Grafana stack (Loki, Grafana, Tempo, and Mimir).
Software Engineering Process, Notation & Tools Introduction - Part 4



Software Engineering Process, Notation & Tools Introduction - Part 4Gaurav Sharma Software Engineering Process, Notation & Tools Introduction
Migrating to Azure Cosmos DB the Right Way



Migrating to Azure Cosmos DB the Right WayAlexander (Alex) Komyagin In this session we cover the benefits of a migration to Cosmos DB, migration paths, common pain points and best practices. We share our firsthand experiences and customer stories. Adiom is the trusted partner for migration solutions that enable seamless online database migrations from MongoDB to Cosmos DB vCore, and DynamoDB to Cosmos DB for NoSQL.
Meet You in the Middle: 1000x Performance for Parquet Queries on PB-Scale Dat...



Meet You in the Middle: 1000x Performance for Parquet Queries on PB-Scale Dat...Alluxio, Inc. Alluxio Webinar
June 10, 2025
For more Alluxio Events: https://www.alluxio.io/events/
Speaker:
David Zhu (Engineering Manager @ Alluxio)
Storing data as Parquet files on cloud object storage, such as AWS S3, has become prevalent not only for large-scale data lakes but also as lightweight feature stores for training and inference, or as document stores for Retrieval-Augmented Generation (RAG). However, querying petabyte-to-exabyte-scale data lakes directly from S3 remains notoriously slow, with latencies typically ranging from hundreds of milliseconds to several seconds.
In this webinar, David Zhu, Software Engineering Manager at Alluxio, will present the results of a joint collaboration between Alluxio and a leading SaaS and data infrastructure enterprise that explored leveraging Alluxio as a high-performance caching and acceleration layer atop AWS S3 for ultra-fast querying of Parquet files at PB scale.
David will share:
- How Alluxio delivers sub-millisecond Time-to-First-Byte (TTFB) for Parquet queries, comparable to S3 Express One Zone, without requiring specialized hardware, data format changes, or data migration from your existing data lake.
- The architecture that enables Alluxio’s throughput to scale linearly with cluster size, achieving one million queries per second on a modest 50-node deployment, surpassing S3 Express single-account throughput by 50x without latency degradation.
- Specifics on how Alluxio offloads partial Parquet read operations and reduces overhead, enabling direct, ultra-low-latency point queries in hundreds of microseconds and achieving a 1,000x performance gain over traditional S3 querying methods.
IBM Rational Unified Process For Software Engineering - Introduction



IBM Rational Unified Process For Software Engineering - IntroductionGaurav Sharma IBM Rational Unified Process For Software Engineering
Who will create the languages of the future?



Who will create the languages of the future?Jordi Cabot Will future languages be created by language engineers?
Can you "vibe" a DSL?
In this talk, we will explore the changing landscape of language engineering and discuss how Artificial Intelligence and low-code/no-code techniques can play a role in this future by helping in the definition, use, execution, and testing of new languages. Even empowering non-tech users to create their own language infrastructure. Maybe without them even realizing.
Maintaining + Optimizing Database Health: Vendors, Orchestrations, Enrichment...



Maintaining + Optimizing Database Health: Vendors, Orchestrations, Enrichment...BradBedford3 Join the Denver Marketo User Group, Captello and Integrate as we dive into the best practices, tools, and strategies for maintaining robust, high-performing databases. From managing vendors and automating orchestrations to enriching data for better insights, this session will unpack the key elements that keep your data ecosystem running smoothly—and smartly.
We will hear from Steve Armenti, Twelfth, and Aaron Karpaty, Captello, and Frannie Danzinger, Integrate.
Agentic Techniques in Retrieval-Augmented Generation with Azure AI Search



Agentic Techniques in Retrieval-Augmented Generation with Azure AI SearchMaxim Salnikov Discover how Agentic Retrieval in Azure AI Search takes Retrieval-Augmented Generation (RAG) to the next level by intelligently breaking down complex queries, leveraging full conversation history, and executing parallel searches through a new LLM-powered query planner. This session introduces a cutting-edge approach that delivers significantly more accurate, relevant, and grounded answers—unlocking new capabilities for building smarter, more responsive generative AI applications.
Traditional Retrieval-Augmented Generation (RAG) pipelines work well for simple queries—but when users ask complex, multi-part questions or refer to previous conversation history, they often fall short. That’s where Agentic Retrieval comes in: a game-changing advancement in Azure AI Search that brings LLM-powered reasoning directly into the retrieval layer.
This session unveils how agentic techniques elevate your RAG-based applications by introducing intelligent query planning, subquery decomposition, parallel execution, and result merging—all orchestrated by a new Knowledge Agent. You’ll learn how this approach significantly boosts relevance, groundedness, and answer quality, especially for sophisticated enterprise use cases.
Key takeaways:
- Understand the evolution from keyword and vector search to agentic query orchestration
- See how full conversation context improves retrieval accuracy
- Explore measurable improvements in answer relevance and completeness (up to 40% gains!)
- Get hands-on guidance on integrating Agentic Retrieval with Azure AI Foundry and SDKs
- Discover how to build scalable, AI-first applications powered by this new paradigm
Whether you're building intelligent copilots, enterprise Q&A bots, or AI-driven search solutions, this session will equip you with the tools and patterns to push beyond traditional RAG.
Build Smarter, Deliver Faster with Choreo - An AI Native Internal Developer P...



Build Smarter, Deliver Faster with Choreo - An AI Native Internal Developer P...WSO2 Enterprises must deliver intelligent, cloud native applications quickly—without compromising governance or scalability. This session explores how an internal developer platform increases productivity via AI for code and accelerates AI-native app delivery via code for AI. Learn practical techniques for embedding AI in the software lifecycle, automating governance with AI agents, and applying a cell-based architecture for modularity and scalability. Real-world examples and proven patterns will illustrate how to simplify delivery, enhance developer productivity, and drive measurable outcomes.
Learn more: https://wso2.com/choreo
Async-ronizing Success at Wix - Patterns for Seamless Microservices - Devoxx ...



Async-ronizing Success at Wix - Patterns for Seamless Microservices - Devoxx ...Natan Silnitsky In a world where speed, resilience, and fault tolerance define success, Wix leverages Kafka to power asynchronous programming across 4,000 microservices. This talk explores four key patterns that boost developer velocity while solving common challenges with scalable, efficient, and reliable solutions:
1. Integration Events: Shift from synchronous calls to pre-fetching to reduce query latency and improve user experience.
2. Task Queue: Offload non-critical tasks like notifications to streamline request flows.
3. Task Scheduler: Enable precise, fault-tolerant delayed or recurring workflows with robust scheduling.
4. Iterator for Long-running Jobs: Process extensive workloads via chunked execution, optimizing scalability and resilience.
For each pattern, we’ll discuss benefits, challenges, and how we mitigate drawbacks to create practical solutions
This session offers actionable insights for developers and architects tackling distributed systems, helping refine microservices and adopting Kafka-driven async excellence.
Agile Software Engineering Methodologies



Agile Software Engineering MethodologiesGaurav Sharma Software Engineering Process, Notation & Tools Introduction
GDG Douglas - Google AI Agents: Your Next Intern?



GDG Douglas - Google AI Agents: Your Next Intern?felipeceotto Presentation done at the GDG Douglas event for June 2025.
A first look at Google's new Agent Development Kit.
Agent Development Kit is a new open-source framework from Google designed to simplify the full stack end-to-end development of agents and multi-agent systems.
How the US Navy Approaches DevSecOps with Raise 2.0



How the US Navy Approaches DevSecOps with Raise 2.0Anchore Join us as Anchore's solutions architect reveals how the U.S. Navy successfully approaches the shift left philosophy to DevSecOps with the RAISE 2.0 Implementation Guide to support its Cyber Ready initiative. This session will showcase practical strategies for defense application teams to pivot from a time-intensive compliance checklist and mindset to continuous cyber-readiness with real-time visibility.
Learn how to break down organizational silos through RAISE 2.0 principles and build efficient, secure pipeline automation that produces the critical security artifacts needed for Authorization to Operate (ATO) approval across military environments.
Plooma is a writing platform to plan, write, and shape books your way



Plooma is a writing platform to plan, write, and shape books your wayPlooma Plooma is your all in one writing companion, designed to support authors at every twist and turn of the book creation journey. Whether you're sketching out your story's blueprint, breathing life into characters, or crafting chapters, Plooma provides a seamless space to organize all your ideas and materials without the overwhelm. Its intuitive interface makes building rich narratives and immersive worlds feel effortless.
Packed with powerful story and character organization tools, Plooma lets you track character development and manage world building details with ease. When it’s time to write, the distraction-free mode offers a clean, minimal environment to help you dive deep and write consistently. Plus, built-in editing tools catch grammar slips and style quirks in real-time, polishing your story so you don’t have to juggle multiple apps.
What really sets Plooma apart is its smart AI assistant - analyzing chapters for continuity, helping you generate character portraits, and flagging inconsistencies to keep your story tight and cohesive. This clever support saves you time and builds confidence, especially during those complex, detail packed projects.
Getting started is simple: outline your story’s structure and key characters with Plooma’s user-friendly planning tools, then write your chapters in the focused editor, using analytics to shape your words. Throughout your journey, Plooma’s AI offers helpful feedback and suggestions, guiding you toward a polished, well-crafted book ready to share with the world.
With Plooma by your side, you get a powerful toolkit that simplifies the creative process, boosts your productivity, and elevates your writing - making the path from idea to finished book smoother, more fun, and totally doable.
Get Started here: https://www.plooma.ink/
Key AI Technologies Used by Indian Artificial Intelligence Companies



Key AI Technologies Used by Indian Artificial Intelligence CompaniesMypcot Infotech Indian tech firms are rapidly adopting advanced tools like machine learning, natural language processing, and computer vision to drive innovation. These key AI technologies enable smarter automation, data analysis, and decision-making. Leading developments are shaping the future of digital transformation among top artificial intelligence companies in India.
For more information please visit here https://www.mypcot.com/artificial-intelligence
Shell Skill Tree - LabEx Certification (LabEx)



Shell Skill Tree - LabEx Certification (LabEx)VICTOR MAESTRE RAMIREZ Shell Skill Tree - LabEx Certification (LabEx)
Marketo & Dynamics can be Most Excellent to Each Other – The Sequel



Marketo & Dynamics can be Most Excellent to Each Other – The SequelBradBedford3 So you’ve built trust in your Marketo Engage-Dynamics integration—excellent. But now what?
This sequel picks up where our last adventure left off, offering a step-by-step guide to move from stable sync to strategic power moves. We’ll share real-world project examples that empower sales and marketing to work smarter and stay aligned.
If you’re ready to go beyond the basics and do truly most excellent stuff, this session is your guide.
Object oriented programming 8 basics of c++ programming
- 1. Object Oriented Programming: 8 Basics of C++ Programming Prof Neeraj Bhargava Vaibhav Khanna Department of Computer Science School of Engineering and Systems Sciences Maharshi Dayanand Saraswati University Ajmer
- 2. 2 The Basics of a C++ Program • Function: collection of statements; when executed, accomplishes something – May be predefined or standard • Syntax: rules that specify which statements (instructions) are legal • Programming language: a set of rules, symbols, and special words • Semantic rule: meaning of the instruction
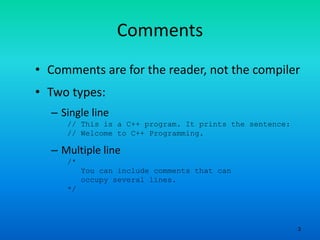
- 3. 3 Comments • Comments are for the reader, not the compiler • Two types: – Single line // This is a C++ program. It prints the sentence: // Welcome to C++ Programming. – Multiple line /* You can include comments that can occupy several lines. */
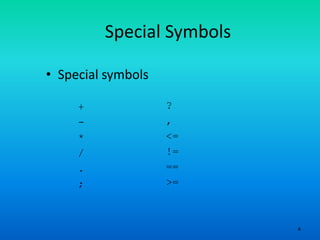
- 4. 4 Special Symbols • Special symbols + - * / . ; ? , <= != == >=
- 5. 5 Reserved Words (Keywords) • Reserved words, keywords, or word symbols – Include: • int • float • double • char • const • void • return
- 6. 6 Identifiers • Consist of letters, digits, and the underscore character (_) • Must begin with a letter or underscore • C++ is case sensitive – NUMBER is not the same as number • Two predefined identifiers are cout and cin • Unlike reserved words, predefined identifiers may be redefined, but it is not a good idea
- 7. 7 Identifiers (continued) • The following are legal identifiers in C++: – first – conversion – payRate
- 8. 8 Whitespaces • Every C++ program contains whitespaces – Include blanks, tabs, and newline characters • Used to separate special symbols, reserved words, and identifiers • Proper utilization of whitespaces is important – Can be used to make the program readable
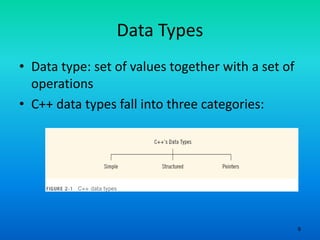
- 9. 9 Data Types • Data type: set of values together with a set of operations • C++ data types fall into three categories:
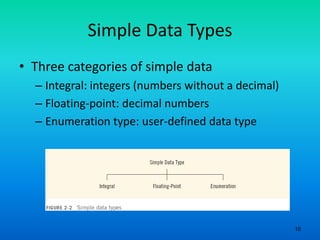
- 10. 10 Simple Data Types • Three categories of simple data – Integral: integers (numbers without a decimal) – Floating-point: decimal numbers – Enumeration type: user-defined data type
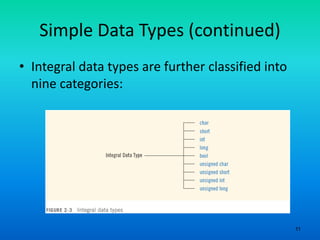
- 11. 11 Simple Data Types (continued) • Integral data types are further classified into nine categories:
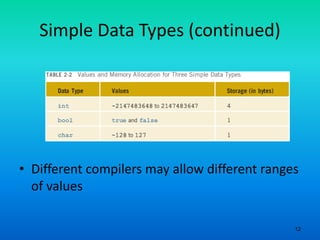
- 12. 12 Simple Data Types (continued) • Different compilers may allow different ranges of values
- 13. 13 int Data Type • Examples: -6728 0 78 +763 • Positive integers do not need a + sign • No commas are used within an integer – Commas are used for separating items in a list
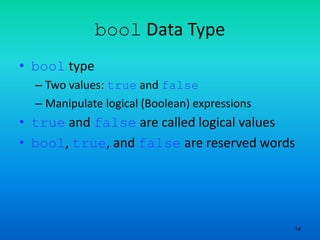
- 14. 14 bool Data Type • bool type – Two values: true and false – Manipulate logical (Boolean) expressions • true and false are called logical values • bool, true, and false are reserved words
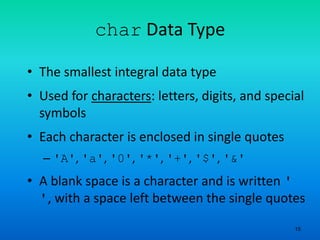
- 15. 15 char Data Type • The smallest integral data type • Used for characters: letters, digits, and special symbols • Each character is enclosed in single quotes – 'A', 'a', '0', '*', '+', '$', '&' • A blank space is a character and is written ' ', with a space left between the single quotes
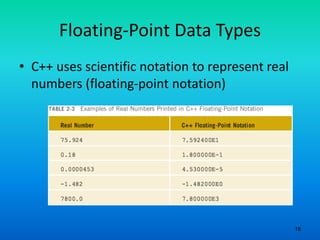
- 16. 16 • C++ uses scientific notation to represent real numbers (floating-point notation) Floating-Point Data Types
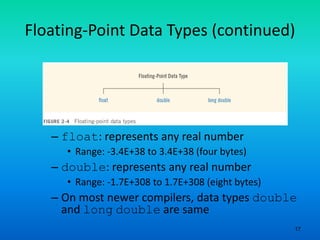
- 17. 17 Floating-Point Data Types (continued) – float: represents any real number • Range: -3.4E+38 to 3.4E+38 (four bytes) – double: represents any real number • Range: -1.7E+308 to 1.7E+308 (eight bytes) – On most newer compilers, data types double and long double are same
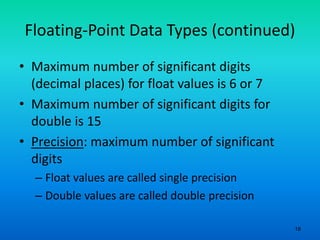
- 18. 18 Floating-Point Data Types (continued) • Maximum number of significant digits (decimal places) for float values is 6 or 7 • Maximum number of significant digits for double is 15 • Precision: maximum number of significant digits – Float values are called single precision – Double values are called double precision
- 19. 19 Arithmetic Operators and Operator Precedence • C++ arithmetic operators: – + addition – - subtraction – * multiplication – / division – % modulus operator • +, -, *, and / can be used with integral and floating-point data types • Operators can be unary or binary
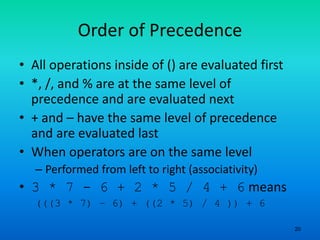
- 20. 20 Order of Precedence • All operations inside of () are evaluated first • *, /, and % are at the same level of precedence and are evaluated next • + and – have the same level of precedence and are evaluated last • When operators are on the same level – Performed from left to right (associativity) • 3 * 7 - 6 + 2 * 5 / 4 + 6 means (((3 * 7) – 6) + ((2 * 5) / 4 )) + 6
- 21. Assignment • Discuss in detail the rules related to Identifiers in C++ • What are the data types available in C++


