PHP Built-in String Validation Functions
- 1. PHP5 Built-in String Filter Functions For Your Application Security By d0ubl3_h3lix http://yehg.org April 2008
- 2. Agenda Why We Use? Need to Know Secure Practice Validation Vs Sanization PHP5 Built-in Filtering Functions
- 3. Why We Use? 100% injection attacks (XSS,SQL,XPATH,OS CMD ...etc) come from inputs where filtering is weak or none Be aware of inputs as well as outputs You know Garbage In Garbage Out For attackers, Garbage In Gold Out
- 4. Need to Know A lot more issues in filtering such as encoding issues An attacker can send strings in different charset formats Causes your visitors’ browser auto-detect and interpret the way the attacker wants Reason: Application failed to convert this string to its intended charset since first stored in database
- 5. Secure Practice Always Convert Input/Output to Intended Charset Before Intensive Filtering/Sanitization
- 6. Validation Vs Sanization Validation means the string format is exactly what you want Validated String can't be assumed 'Secure' Can't know if validated string might have malicious characters meaningful for various back-end systems That's why, validated one needs to be sanitized!
- 7. PHP5 Built-in String Filter Functions
- 8. htmlspecialchars Description: Convert special characters to HTML entities Usage: string htmlspecialchars ( string string [, int quote_style [, string charset ]] )
- 9. Quote_Style ENT_COMPAT Will convert double-quotes and leave single-quotes alone. ENT_QUOTES Will convert both double and single quotes. ENT_NOQUOTES Will leave both double and single quotes unconverted.
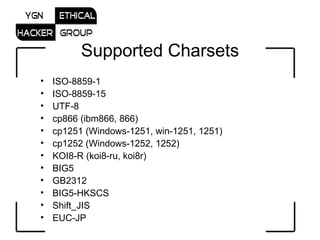
- 10. Supported Charsets ISO-8859-1 ISO-8859-15 UTF-8 cp866 (ibm866, 866) cp1251 (Windows-1251, win-1251, 1251) cp1252 (Windows-1252, 1252) KOI8-R (koi8-ru, koi8r) BIG5 GB2312 BIG5-HKSCS Shift_JIS EUC-JP
- 11. Not Secure: htmlspecialchars($untrusted_input); Relatively Secure: htmlspecialchars($untrusted_input, ENT_QUOTES, " UTF-8 " ); Example
- 12. htmlentities Description: Convert all applicable characters to HTML entities Usage: string htmlentities ( string string [, int quote_style [, string charset ]] )
- 13. Example Not Secure: htmlentities($untrusted_input); Relatively Secure: htmlentities($untrusted_input, ENT_QUOTES, " UTF-8 " );
- 14. htmlspecialchars vs htmlentities htmlentities() converts every char to html applicable chars while htmlspecialchars() converts only: & => & " => " ' => ' < => < > => >
- 16. Description: Strip HTML and PHP tags from a string Usage: string strip_tags ( string str [, string allowable_tags ] ) strip_tags
- 17. // Return Hello Admin!alert('0wned u'); strip_tags("<b>Hello Admin!</b><script>alert('0wned u');</script>"); // Return <b>Hello Admin!</b> Nice strip_tags("<b>bold</b> <i>Nice</i>" , "<b>"); Example: Stripping HTML
- 18. // Return Hello Admin! strip_tags("Hello Admin!<?php /*attacker's shellcode/backdoor script*/?>"); It's commonly embedded in images and some binary-like files Example: Stripping PHP
- 20. escapeshellcmd Description: Escape shell metacharacters - #&;`|*?~<>^()[]{}$\, \x0A and \xFF Usage: string escapeshellcmd ( string command )
- 21. $input = "solution & whoami &" escapeshellcmd("process $input"); // Process solution whoami // Escape & Example
- 23. Description: Escapes special characters in a string for use in a SQL statement ; First need to open database connection Usage: string mysql_real_escape_string ( string unescaped_string [, resource link_identifier] ) mysql_real_escape_string
- 24. mysql_escape_string Description: Escapes a string for use in a mysql_query ; First need to open database connection Usage: string mysql_escape_string ( string unescaped_string )
- 26. is_* Functions To Check whether a variable is desired Type: is_array -- Whether a variable is an array is_binary -- Whether a variable is a native binary string is_bool -- Whether a variable is a boolean is_buffer -- Whether a variable is a native unicode or binary string is_callable -- Verify that the contents of a variable can be called as a function is_double -- Alias of is_float()
- 27. is_* Functions is_float -- Whether a variable is a float is_int -- Whether a variable is an integer is_integer -- Alias of is_int() is_long -- Alias of is_int() is_null -- Whether a variable is NULL is_numeric -- Whether a variable is a number or a numeric string is_object -- Whether a variable is an object is_real -- Alias of is_float() is_resource -- Whether a variable is a resource is_scalar -- Whether a variable is a scalar is_string -- Whether a variable is a string is_unicode -- Whether a variable is a unicode string
- 28. Good Practice With is_* For example: $start = (isset($_GET['num']) && is_numeric($_GET['num']))? (int)$_GET['num']:die("Hacking Attempt!");
- 30. filter_* Functions filter_has_var -- Checks if variable of specified type exists filter_id -- Returns the filter ID belonging to a named filter filter_input_array -- Gets multiple variables from outside PHP and optionally filters them filter_input -- Gets variable from outside PHP and optionally filters it filter_list -- Returns a list of all supported filters filter_var_array -- Gets multiple variables and optionally filters them filter_var -- Filters a variable with a specified filter
- 31. Filterable Types INPUT_POST ( integer ) POST variables. INPUT_GET ( integer ) GET variables. INPUT_COOKIE ( integer ) COOKIE variables. INPUT_ENV ( integer ) ENV variables. INPUT_SERVER ( integer ) SERVER variables. INPUT_SESSION ( integer ) SESSION variables. (not implemented yet in Php5) INPUT_REQUEST ( integer ) REQUEST variables. (not implemented yet in Php5)
- 32. Filter Options FILTER_FLAG_NONE ( integer ) No flags. FILTER_REQUIRE_SCALAR ( integer ) Flag used to require scalar as input Scalar variables are those containing an integer, float, string or boolean. Types array, object and resource are not scalar.
- 33. Filter Options FILTER_REQUIRE_ARRAY ( integer ) Require an array as input. FILTER_FORCE_ARRAY ( integer ) Always returns an array. FILTER_NULL_ON_FAILURE ( integer ) Use NULL instead of FALSE on failure.
- 34. Filter Options FILTER_VALIDATE_INT ( integer ) ID of "int" filter. FILTER_VALIDATE_BOOLEAN ( integer ) ID of "boolean" filter. FILTER_VALIDATE_FLOAT ( integer ) ID of "float" filter.
- 35. Filter Options FILTER_VALIDATE_REGEXP ( integer ) ID of "validate_regexp" filter. FILTER_VALIDATE_URL ( integer ) ID of "validate_url" filter. FILTER_VALIDATE_EMAIL ( integer ) ID of "validate_email" filter.
- 36. Filter Options FILTER_VALIDATE_IP ( integer ) ID of "validate_ip" filter. FILTER_DEFAULT ( integer ) ID of default ("string") filter. FILTER_UNSAFE_RAW ( integer ) ID of "unsafe_raw" filter. FILTER_SANITIZE_STRING ( integer ) ID of "string" filter.
- 37. Filter Options FILTER_SANITIZE_STRIPPED ( integer ) ID of "stripped" filter. FILTER_SANITIZE_ENCODED ( integer ) ID of "encoded" filter. FILTER_SANITIZE_SPECIAL_CHARS ( integer ) ID of "special_chars" filter. FILTER_SANITIZE_EMAIL ( integer ) ID of "email" filter.
- 38. Filter Options FILTER_SANITIZE_URL ( integer ) ID of "url" filter. FILTER_SANITIZE_NUMBER_INT ( integer ) ID of "number_int" filter. FILTER_SANITIZE_NUMBER_FLOAT ( integer ) ID of "number_float" filter. FILTER_SANITIZE_MAGIC_QUOTES ( integer ) ID of "magic_quotes" filter.
- 39. Filter Options FILTER_CALLBACK ( integer ) ID of "callback" filter. FILTER_FLAG_ALLOW_OCTAL ( integer ) Allow octal notation (0[0-7]+) in "int" filter. FILTER_FLAG_ALLOW_HEX ( integer ) Allow hex notation (0x[0-9a-fA-F]+) in "int" filter. FILTER_FLAG_STRIP_LOW ( integer ) Strip characters with ASCII value less than 32.
- 40. Filter Options FILTER_FLAG_STRIP_HIGH ( integer ) Strip characters with ASCII value greater than 127. FILTER_FLAG_ENCODE_LOW ( integer ) Encode characters with ASCII value less than 32. FILTER_FLAG_ENCODE_HIGH ( integer ) Encode characters with ASCII value greater than 127. FILTER_FLAG_ENCODE_AMP ( integer ) Encode &.
- 41. Filter Options FILTER_FLAG_NO_ENCODE_QUOTES ( integer ) Don't encode ' and ". FILTER_FLAG_EMPTY_STRING_NULL ( integer ) (No use for now.) FILTER_FLAG_ALLOW_FRACTION ( integer ) Allow fractional part in "number_float" filter.
- 42. Filter Options FILTER_FLAG_ALLOW_THOUSAND ( integer ) Allow thousand separator (,) in "number_float" filter. FILTER_FLAG_ALLOW_SCIENTIFIC ( integer ) Allow scientific notation (e, E) in "number_float" filter. FILTER_FLAG_SCHEME_REQUIRED ( integer ) Require scheme in "validate_url" filter.
- 43. Filter Options FILTER_FLAG_HOST_REQUIRED ( integer ) Require host in "validate_url" filter. FILTER_FLAG_PATH_REQUIRED ( integer ) Require path in "validate_url" filter. FILTER_FLAG_QUERY_REQUIRED ( integer ) Require query in "validate_url" filter.
- 44. Filter Options FILTER_FLAG_IPV4 ( integer ) Allow only IPv4 address in "validate_ip" filter. FILTER_FLAG_IPV6 ( integer ) Allow only IPv6 address in "validate_ip" filter. FILTER_FLAG_NO_RES_RANGE ( integer ) Deny reserved addresses in "validate_ip" filter. FILTER_FLAG_NO_PRIV_RANGE ( integer ) Deny private addresses in "validate_ip" filter.
- 45. Filter Definitions ID: FILTER_VALIDATE_INT Options: min_range, max_range Flags: FILTER_FLAG_ALLOW_OCTAL , FILTER_FLAG_ALLOW_HEX Description: Validates value as integer, optionally from the specified range.
- 46. Filter Definitions ID: FILTER_VALIDATE_BOOLEAN Flags: FILTER_NULL_ON_FAILURE Description: Returns TRUE for "1", "true", "on" and "yes", FALSE for "0", "false", "off", "no", and "", NULL otherwise.
- 47. Filter Definitions ID: FILTER_VALIDATE_FLOAT Flags: FILTER_FLAG_ALLOW_THOUSAND Description: Validates value as float.
- 48. Filter Definitions ID: FILTER_VALIDATE_REGEXP Options: regexp Description: Validates value against regexp, a Perl-compatible regular expression.
- 49. Filter Definitions ID: FILTER_VALIDATE_URL Flags: FILTER_FLAG_PATH_REQUIRED , FILTER_FLAG_QUERY_REQUIRED Description: Validates value as URL, optionally with required components.
- 50. Filter Definitions ID: FILTER_VALIDATE_EMAIL Description: Validates value as e-mail.
- 51. Filter Definitions ID: FILTER_VALIDATE_IP Flags: FILTER_FLAG_IPV4 , FILTER_FLAG_IPV6 , FILTER_FLAG_NO_PRIV_RANGE , FILTER_FLAG_NO_RES_RANGE Description: Validates value as IP address, optionally only IPv4 or IPv6 or not from private or reserved ranges.
- 52. Filter Definitions ID: FILTER_SANITIZE_STRING Flags: FILTER_FLAG_NO_ENCODE_QUOTES , FILTER_FLAG_STRIP_LOW , FILTER_FLAG_STRIP_HIGH , FILTER_FLAG_ENCODE_LOW , FILTER_FLAG_ENCODE_HIGH , FILTER_FLAG_ENCODE_AMP Description: Strip tags, optionally strip or encode special characters.
- 53. Filter Definitions ID: FILTER_SANITIZE_STRIPPED Alias of FILTER_SANITIZE_STRING .
- 54. Filter Definitions ID: FILTER_SANITIZE_ENCODED Flags: FILTER_FLAG_STRIP_LOW , FILTER_FLAG_STRIP_HIGH , FILTER_FLAG_ENCODE_LOW , FILTER_FLAG_ENCODE_HIGH Description: URL-encode string, optionally strip or encode special characters .
- 55. Filter Definitions ID: FILTER_SANITIZE_SPECIAL_CHARS Flags: FILTER_FLAG_STRIP_LOW , FILTER_FLAG_STRIP_HIGH , FILTER_FLAG_ENCODE_HIGH Description: HTML-escape '"<>& and characters with ASCII value less than 32, optionally strip or encode other special characters.
- 56. Filter Definitions ID: FILTER_UNSAFE_RAW Flags: FILTER_FLAG_STRIP_LOW , FILTER_FLAG_STRIP_HIGH , FILTER_FLAG_ENCODE_LOW , FILTER_FLAG_ENCODE_HIGH , FILTER_FLAG_ENCODE_AMP Description: Do nothing, optionally strip or encode special characters.
- 57. Filter Definitions ID: FILTER_SANITIZE_EMAIL Description: Remove all characters except letters, digits and !#$%&'*+-/=?^_`{|}~@.[].
- 58. Filter Definitions ID: FILTER_SANITIZE_URL Description: Remove all characters except letters, digits and $-_.+!*'(),{}|\\^~[]`<>#%";/?:@&=.
- 59. Filter Definitions ID: FILTER_SANITIZE_NUMBER_INT Description: Remove all characters except digits and +-.
- 60. Filter Definitions ID: FILTER_SANITIZE_NUMBER_FLOAT Flags: FILTER_FLAG_ALLOW_FRACTION , FILTER_FLAG_ALLOW_THOUSAND , FILTER_FLAG_ALLOW_SCIENTIFIC Description: Remove all characters except digits, +- and optionally .,eE.
- 61. Filter Definitions ID: FILTER_SANITIZE_MAGIC_QUOTES Description: Apply addslashes() .
- 62. Filter Definitions ID: FILTER_CALLBACK Options: callback function or method Description: Call user-defined function to filter data.
- 64. Remind: filter_* Functions filter_has_var -- Checks if variable of specified type exists filter_id -- Returns the filter ID belonging to a named filter filter_input_array -- Gets multiple variables from outside PHP and optionally filters them filter_input -- Gets variable from outside PHP and optionally filters it filter_list -- Returns a list of all supported filters filter_var_array -- Gets multiple variables and optionally filters them filter_var -- Filters a variable with a specified filter
- 65. Description: Checks if variable of specified type exists Usage: bool filter_has_var ( int type , string variable_name ) filter_has_var
- 66. Example filter_has_var(INPUT_GET,'searchstr'); is equivalent to isset($_GET['searchstr'])
- 67. Description: Returns the filter ID belonging to a named filter Usage: int filter_id ( string filtername ) filter_id
- 68. Description: Returns a list of all supported filters Usage: array filter_list ( void ) filter_list
- 69. Description: Gets variable from outside PHP and optionally filters it Usage: mixed filter_input ( int type, string variable_name [, int filter [, mixed options ]] ) filter_input
- 70. filter_input(INPUT_GET, 'search', FILTER_SANITIZE_SPECIAL_CHARS); filter_input (INPUT_GET, 'number',FILTER_VALIDATE_INT, array( 'flags' => FILTER_FLAG_ARRAY, 'options' => array('min_range' => 1, 'max_range' => 10) ) ); Example
- 71. Description: Gets multiple variables from outside PHP and optionally filters them Usage: mixed filter_input_array ( int type [, mixed definition] ) filter_input_array
- 72. /* Let's say: data come from POST as follows:*/ $_POST = array( 'visitor_name' => 'MgMg', 'visitor_email' => '[email protected]', 'visitor_url' => 'http://myanmar.com'); Example
- 73. We can write filter rules like: $visitor_sanitized_rules = array( 'visitor_name' => FILTER_SANITIZE__SPECIAL_CHARS, 'visitor_email' => FILTER_VALIDATE_EMAIL, 'visitor_url' => FILTER_VALIDATE_URL ); Example
- 74. Then, we can implement like: $visitor_inputs = filter_input_array( INPUT_POST, $visitor_sanitized_rules ); Example
- 75. No Real Difference! filter_input(_array) Vs filter_var(_array) are totally same.
- 76. Description: Filters a variable with a specified filter Usage: mixed filter_var ( mixed variable [, int filter [, mixed options]] ) filter_var
- 77. filter_var($_POST['visitor_name'], FILTER_SANITIZE_SPECIAL_CHARS); filter_var($_POST['visitor_email'], FILTER_VALIDATE_EMAIL); filter_var($_POST['visitor_url'], FILTER_VALIDATE_URL, FILTER_FLAG_SCHEME_REQUIRED); Example
- 78. Description: Gets multiple variables and optionally filters them Usage: mixed filter_var_array ( array data [, mixed definition] ) filter_var_array
- 79. /* Same as before. No big difference:*/ $visitor_data = array( 'visitor_name' => 'MgMg', 'visitor_email' => '[email protected]', 'visitor_url' => 'http://myanmar.com'); Example
- 80. We can write filter rules like: $visitor_sanitized_rules = array( 'visitor_name' => FILTER_SANITIZE__SPECIAL_CHARS, 'visitor_email' => FILTER_VALIDATE_EMAIL, 'visitor_url' => FILTER_VALIDATE_URL ); Example
- 81. Then, we can implement like: $visitor_inputs = filter_input_array( $visitor_data , $visitor_sanitized_rules ); Example
- 82. Last But Not Least, Did you notice two things lack in Filter_* Functions ?
- 83. First .. Have to filter twice for some cases like: $email = $_GET['email']; $email = filter_var($email,FILTER_VALIDATE_EMAIL); $email = filter_var($email,FILTER_SANITIZE_EMAIL);
- 84. Second … No Charset Conversion Functions! Do-It-Yourself Exercise!
- 85. Thank You!
- 86. Reference PHP 5.25 Manual







![htmlspecialchars Description: Convert special characters to HTML entities Usage: string htmlspecialchars ( string string [, int quote_style [, string charset ]] )](https://image.slidesharecdn.com/php5-builtin-string-filter-functions-1214834838323604-9/85/PHP-Built-in-String-Validation-Functions-8-320.jpg)


![htmlentities Description: Convert all applicable characters to HTML entities Usage: string htmlentities ( string string [, int quote_style [, string charset ]] )](https://image.slidesharecdn.com/php5-builtin-string-filter-functions-1214834838323604-9/85/PHP-Built-in-String-Validation-Functions-12-320.jpg)



![Description: Strip HTML and PHP tags from a string Usage: string strip_tags ( string str [, string allowable_tags ] ) strip_tags](https://image.slidesharecdn.com/php5-builtin-string-filter-functions-1214834838323604-9/85/PHP-Built-in-String-Validation-Functions-16-320.jpg)



![escapeshellcmd Description: Escape shell metacharacters - #&;`|*?~<>^()[]{}$\, \x0A and \xFF Usage: string escapeshellcmd ( string command )](https://image.slidesharecdn.com/php5-builtin-string-filter-functions-1214834838323604-9/85/PHP-Built-in-String-Validation-Functions-20-320.jpg)


![Description: Escapes special characters in a string for use in a SQL statement ; First need to open database connection Usage: string mysql_real_escape_string ( string unescaped_string [, resource link_identifier] ) mysql_real_escape_string](https://image.slidesharecdn.com/php5-builtin-string-filter-functions-1214834838323604-9/85/PHP-Built-in-String-Validation-Functions-23-320.jpg)




![Good Practice With is_* For example: $start = (isset($_GET['num']) && is_numeric($_GET['num']))? (int)$_GET['num']:die("Hacking Attempt!");](https://image.slidesharecdn.com/php5-builtin-string-filter-functions-1214834838323604-9/85/PHP-Built-in-String-Validation-Functions-28-320.jpg)










![Filter Options FILTER_CALLBACK ( integer ) ID of "callback" filter. FILTER_FLAG_ALLOW_OCTAL ( integer ) Allow octal notation (0[0-7]+) in "int" filter. FILTER_FLAG_ALLOW_HEX ( integer ) Allow hex notation (0x[0-9a-fA-F]+) in "int" filter. FILTER_FLAG_STRIP_LOW ( integer ) Strip characters with ASCII value less than 32.](https://image.slidesharecdn.com/php5-builtin-string-filter-functions-1214834838323604-9/85/PHP-Built-in-String-Validation-Functions-39-320.jpg)

















![Filter Definitions ID: FILTER_SANITIZE_EMAIL Description: Remove all characters except letters, digits and !#$%&'*+-/=?^_`{|}~@.[].](https://image.slidesharecdn.com/php5-builtin-string-filter-functions-1214834838323604-9/85/PHP-Built-in-String-Validation-Functions-57-320.jpg)
![Filter Definitions ID: FILTER_SANITIZE_URL Description: Remove all characters except letters, digits and $-_.+!*'(),{}|\\^~[]`<>#%";/?:@&=.](https://image.slidesharecdn.com/php5-builtin-string-filter-functions-1214834838323604-9/85/PHP-Built-in-String-Validation-Functions-58-320.jpg)







![Example filter_has_var(INPUT_GET,'searchstr'); is equivalent to isset($_GET['searchstr'])](https://image.slidesharecdn.com/php5-builtin-string-filter-functions-1214834838323604-9/85/PHP-Built-in-String-Validation-Functions-66-320.jpg)


![Description: Gets variable from outside PHP and optionally filters it Usage: mixed filter_input ( int type, string variable_name [, int filter [, mixed options ]] ) filter_input](https://image.slidesharecdn.com/php5-builtin-string-filter-functions-1214834838323604-9/85/PHP-Built-in-String-Validation-Functions-69-320.jpg)

![Description: Gets multiple variables from outside PHP and optionally filters them Usage: mixed filter_input_array ( int type [, mixed definition] ) filter_input_array](https://image.slidesharecdn.com/php5-builtin-string-filter-functions-1214834838323604-9/85/PHP-Built-in-String-Validation-Functions-71-320.jpg)




![Description: Filters a variable with a specified filter Usage: mixed filter_var ( mixed variable [, int filter [, mixed options]] ) filter_var](https://image.slidesharecdn.com/php5-builtin-string-filter-functions-1214834838323604-9/85/PHP-Built-in-String-Validation-Functions-76-320.jpg)
![filter_var($_POST['visitor_name'], FILTER_SANITIZE_SPECIAL_CHARS); filter_var($_POST['visitor_email'], FILTER_VALIDATE_EMAIL); filter_var($_POST['visitor_url'], FILTER_VALIDATE_URL, FILTER_FLAG_SCHEME_REQUIRED); Example](https://image.slidesharecdn.com/php5-builtin-string-filter-functions-1214834838323604-9/85/PHP-Built-in-String-Validation-Functions-77-320.jpg)
![Description: Gets multiple variables and optionally filters them Usage: mixed filter_var_array ( array data [, mixed definition] ) filter_var_array](https://image.slidesharecdn.com/php5-builtin-string-filter-functions-1214834838323604-9/85/PHP-Built-in-String-Validation-Functions-78-320.jpg)




![First .. Have to filter twice for some cases like: $email = $_GET['email']; $email = filter_var($email,FILTER_VALIDATE_EMAIL); $email = filter_var($email,FILTER_SANITIZE_EMAIL);](https://image.slidesharecdn.com/php5-builtin-string-filter-functions-1214834838323604-9/85/PHP-Built-in-String-Validation-Functions-83-320.jpg)


