Secure hashing algorithm
Download as ppt, pdf13 likes23,348 views
This document discusses secure hashing algorithms used for authentication rather than encryption. It provides an overview of the requirements for authentication including preventing masquerading, content modification, sequence modification, and timing modification. It then describes the basic theory behind hashing including producing a message digest, ensuring it is computationally infeasible to find two messages with the same digest, and being unable to recreate a message from its digest. Finally, it details the framework of the SHA-1 hashing algorithm including preprocessing the message, initializing buffers, processing the message in blocks, and outputting the final digest.
1 of 16
Downloaded 918 times









![SHA-1 Framework Final Step
Step 6: Processing Message in 512-bit
blocks (L blocks in total message)….
This is the main task of SHA1 algorithm which loops through the
padded and appended message in 512-bit blocks.
Input and predefined functions:
M[1, 2, ..., L]: Blocks of the padded and appended message
f(0;B,C,D), f(1,B,C,D), ..., f(79,B,C,D): 80 Processing Functions K(0),
K(1), ..., K(79): 80 Processing Constant Words
H0, H1, H2, H3, H4, H5: 5 Word buffers with initial values
http://www.herongyang.com](https://image.slidesharecdn.com/securehashingalgorithm-121216002452-phpapp01/85/Secure-hashing-algorithm-11-320.jpg)
![SHA-1 Framework Continued
Step 6: Pseudo Code….
For loop on k = 1 to L
(W(0),W(1),...,W(15)) = M[k] /* Divide M[k] into 16 words */
For t = 16 to 79 do:
W(t) = (W(t-3) XOR W(t-8) XOR W(t-14) XOR W(t-16)) <<< 1
A = H0, B = H1, C = H2, D = H3, E = H4
For t = 0 to 79 do:
TEMP = A<<<5 + f(t;B,C,D) + E + W(t) + K(t) E = D, D = C,
C = B<<<30, B = A, A = TEMP
End of for loop
H0 = H0 + A, H1 = H1 + B, H2 = H2 + C, H3 = H3 + D, H4 = H4 + E
End of for loop
Output:
H0, H1, H2, H3, H4, H5: Word buffers with final message digest
http://www.herongyang.com](https://image.slidesharecdn.com/securehashingalgorithm-121216002452-phpapp01/85/Secure-hashing-algorithm-12-320.jpg)




Ad
Recommended
SHA 1 Algorithm
SHA 1 AlgorithmShiva RamDam The document describes the SHA-1 hashing algorithm. SHA-1 produces a 160-bit hash value from an input of arbitrary length. It works by padding the input, appending the length, initializing hash buffers, processing the message through 80 rounds of compression, and outputting the final hash value. The compression function divides the padded message into 16-word blocks and schedules the words through the rounds using a message scheduling algorithm. It performs logical and bitwise operations on the words and chaining variables to generate a new hash.
Hash Function
Hash FunctionSiddharth Srivastava This document discusses message authentication techniques including message encryption, message authentication codes (MACs), and hash functions. It describes how each technique can be used to authenticate messages and protect against various security threats. It also covers how symmetric and asymmetric encryption can provide authentication when used with MACs or digital signatures. Specific MAC and hash functions are examined like HMAC, SHA-1, and SHA-2. X.509 is introduced as a standard for digital certificates.
SHA- Secure hashing algorithm
SHA- Secure hashing algorithmRuchi Maurya This document outlines the Secure Hashing Algorithm (SHA), focusing on SHA-1, developed by NIST and NSA in 1993 as a federal information processing standard. It details the functioning of SHA-1, including its input requirements, operational steps, and the processing of 512-bit blocks through multiple rounds and iterations. The algorithm is used in various applications, such as secure password hashing and digital signatures.
Hash function
Hash functionHarry Potter The document discusses hash functions and message authentication codes (MACs). It begins by defining hash functions and MACs, noting that hash functions generate a fingerprint for a message without a key while MACs use a keyed hash function. It then covers security requirements for hash functions like one-wayness and collision resistance. Popular hash functions are described like MD5, SHA-1, and the SHA-2 family. Constructions for hash functions based on block ciphers and iterated hash functions are also outlined. The document concludes by comparing hash functions and MACs and describing common MAC constructions.
Intro to modern cryptography
Intro to modern cryptographyzahid-mian The document discusses the history and concepts of encryption, including ancient encryption methods like hieroglyphs and the Caesar cipher. It then covers modern digital encryption, describing how public/private key encryption works using plaintexts, ciphertexts, encryption/decryption keys, and algorithms. The document also discusses hash values, digital signatures, types of attacks against encryption, different cipher implementations like DES and AES, and reasons why attacks can still succeed despite encryption.
Information and data security cryptographic hash functions
Information and data security cryptographic hash functionsMazin Alwaaly This document discusses hash functions and their cryptographic applications. It begins by defining hash functions and their properties like one-wayness and collision resistance. It then discusses various applications of cryptographic hash functions like message authentication codes, digital signatures, password files, and more. It provides details on how hash functions are used for message authentication and digital signatures. It also describes the Secure Hash Algorithm family of hash functions like SHA-1, SHA-2, and the NIST competition for the SHA-3 standard.
Hash function
Hash function Salman Memon A hash function compresses input data into a shorter, fixed-length output known as a hash value, often used for file integrity checks, password encryption, and data verification. It serves as a digital fingerprint, making it nearly impossible to alter the original data without changing the hash. Various hash functions exist, including MD5, SHA, and HMAC, each with specific applications and characteristics.
Hash Function
Hash Function ssuserdfb2da This document discusses cryptographic hash functions including their applications in message authentication and digital signatures. It describes the requirements for hash functions to be secure including resistance to brute force attacks and cryptanalysis. The document outlines some simple hash functions and provides details on the Secure Hash Algorithm (SHA) family of cryptographic hash functions used in standards like SHA-512 which operates on 1024-bit blocks through 80 rounds. It also mentions NIST's selection of the Keccak algorithm as the new SHA-3 standard.
RSA ALGORITHM
RSA ALGORITHMDr. Shashank Shetty The document summarizes the RSA encryption algorithm. It begins by explaining that RSA was developed in 1977 by Rivest, Shamir and Adleman. It then provides an example to demonstrate how RSA works step-by-step, generating keys, encrypting a message and decrypting the ciphertext. Finally, it discusses some challenges with breaking RSA encryption, including brute force attacks and mathematical attacks based on factoring the encryption keys, as well as timing attacks that aim to deduce keys based on variations in processing time.
Introduction to Cryptography
Introduction to CryptographyPopescu Petre The document provides an overview of cryptography, defining it as the practice of secure communication and outlining its two main branches: private key and public key cryptography. It explains private key cryptography with examples like the Caesar cipher and techniques for cracking it, while also detailing public key cryptography, particularly RSA, including its key generation process. The document emphasizes the importance of mathematics in cryptographic techniques and the need for key secrecy.
Hashing
HashingHossain Md Shakhawat A hash algorithm is a one-way function that converts a data string into a numeric string output of fixed length. It is collision resistant, meaning it is very unlikely for different data to produce the same hash value. Common hash algorithms include MD5 and SHA-1. A one-way hash function takes a variable-length input and produces a fixed-length output. It is easy to compute the hash but very difficult to reverse it or find collisions. Hash functions are used for password verification, digital signatures, and ensuring data integrity.
Public key cryptography and message authentication
Public key cryptography and message authenticationCAS The document discusses public-key cryptography and message authentication, focusing on secure hash functions (such as SHA), HMAC, and the RSA and Diffie-Hellman algorithms. It details how these cryptographic techniques ensure data integrity and secure key exchange, emphasizing the mechanisms behind hash functions and the mathematical principles governing RSA. The lecture is based on concepts from various authoritative sources in computer security.
MD5
MD5rokham khawaja The document discusses the MD5 algorithm used for generating message digests of arbitrary inputs. It describes the MD5 algorithm structure and implementation steps. The implementation involves padding the input message to a length congruent to 448 modulo 512 bits. A 64-bit representation of the original message length is then appended. The padded message is processed in 512-bit blocks, each divided into sixteen 32-bit words. Four initialization values are used to compute the message digest through four rounds of operations on each block.
CNIT 141: 6. Hash Functions
CNIT 141: 6. Hash FunctionsSam Bowne The document covers cryptography for computer networks, focusing on hash functions, their construction, and secure usage. It details various algorithms like SHA family and Blake2, explaining their unique features, vulnerabilities, and potential attacks such as length-extension and collision resistance. Additionally, it discusses practical applications of hash functions in digital signatures, message authentication, and integrity verification.
The SHA Hashing Algorithm
The SHA Hashing AlgorithmBob Landstrom The document discusses the importance of the SHA hashing algorithm and cryptography in protecting data integrity and privacy within data centers. It details the evolution of the SHA family, from SHA-0 to SHA-3, and provides recommendations on which algorithms to use based on data length. Additionally, it outlines the applications of SHA algorithms in ensuring message integrity across various internet protocols and for specific uses like password storage and Bitcoin transaction verification.
SHA
SHASubashiniRathinavel The Secure Hash Algorithm (SHA) was developed by NIST and NSA to generate a 160-bit message digest from inputs of less than 264 bits. SHA-1 works by padding the input message, appending the length, dividing into 512-bit blocks, initializing chain variables, and processing each block through 80 iterations involving logical, shift, and addition operations to update the variables. Each iteration uses a constant and the previous output to calculate the next output in order to make it difficult to determine the input from the digest or find colliding messages. Later versions such as SHA-256 increased security by lengthening the digest and number of steps.
DES (Data Encryption Standard) pressentation
DES (Data Encryption Standard) pressentationsarhadisoftengg This document discusses data encryption methods. It defines encryption as hiding information so it can only be accessed by those with the key. There are two main types: symmetric encryption uses one key, while asymmetric encryption uses two different but related keys. Encryption works by scrambling data using techniques like transposition, which rearranges the order, and substitution, which replaces parts with other values. The document specifically describes the Data Encryption Standard (DES) algorithm and the public key cryptosystem, which introduced the innovative approach of using different keys for encryption and decryption.
Digital Signature Standard
Digital Signature StandardSou Jana The document discusses digital signatures and the Digital Signature Standard (DSS). It explains that digital signatures authenticate the author, date, and contents of a message, and can be verified by third parties. The DSS is the US government approved digital signature scheme, developed by NIST and NSA, which uses the SHA hash algorithm and DSA digital signature algorithm. DSA creates a 320-bit signature using 512-1024 bit keys for security, is faster than RSA, and relies on the difficulty of computing discrete logarithms. The document outlines the DSA key generation, signature creation, and verification processes.
Elgamal & schnorr digital signature scheme copy
Elgamal & schnorr digital signature scheme copyNorth Cap University (NCU) Formely ITM University Digital signatures provide authentication of digital messages or documents. There are three main algorithms involved: hashing, signature generation, and signature verification. Common digital signature schemes include ElGamal, Schnorr, and the Digital Signature Standard (DSS). The DSS is based on ElGamal and Schnorr schemes. It uses smaller signatures than ElGamal by employing two moduli, one smaller than the other. Digital signatures are widely used to provide authentication in protocols like IPSec, SSL/TLS, and S/MIME.
Hash Function
Hash Functionstalin rijal A hash function maps data of arbitrary size to a fixed size value called a hash. Common hash functions include MD5 and SHA, with MD5 producing a 128-bit hash. While hashes were once used to securely store passwords, MD5 is now considered cryptographically broken due to collisions being found in its compression function. One-way signatures allow multiple users to generate linked signatures on the same message in a verifiable chain.
Cryptographic hash function md5
Cryptographic hash function md5Khulna University, Khulna, Bangladesh This document discusses the MD5 cryptographic hash function. It provides an introduction to hash functions and describes MD5, including its features, applications, algorithm, analysis, and drawbacks. MD5 produces a 128-bit hash value from a message of any size through a multi-step process involving padding, appending a length, initializing buffers, and processing in 16-word blocks. While once widely used, MD5 is now considered broken due to vulnerabilities found in its compression function and preimage resistance.
Cryptography and applications
Cryptography and applicationsthai This document provides an overview of cryptography and its applications. It discusses the history of cryptography beginning in ancient Egypt. It defines basic cryptography terminology like plaintext, ciphertext, cipher, key, encryption, decryption, cryptography, and cryptanalysis. It describes classical ciphers like the Caesar cipher and substitution ciphers. It also discusses cryptanalysis techniques, transposition ciphers, modern symmetric ciphers, public key cryptography including RSA, key distribution methods, and hybrid encryption.
AES KEY EXPANSION .pptx
AES KEY EXPANSION .pptxAhmudulHassan The document describes the AES key expansion process. The AES algorithm takes a 128-bit key as input and expands it into a linear array of 44 words using a key schedule. The key schedule applies the key expansion function g, which performs byte substitutions and XOR operations with round constants, to generate a key for each round. The initial key is added to the first four words of the expanded key schedule.
Secure Hash Algorithm
Secure Hash AlgorithmVishakha Agarwal Secure Hash Algorithm (SHA) was developed by NIST and NSA to hash messages into fixed-length message digests. SHA has multiple versions including SHA-1, SHA-2, and SHA-3. SHA-1 produces a 160-bit message digest and works by padding the input message, appending the length, dividing into blocks, initializing variables, and processing blocks through 80 rounds of operations to output the digest. SHA-512 is closely modeled after SHA-1 but produces a 512-bit digest and uses 1024-bit blocks.
Modern Cryptography
Modern CryptographyJames McGivern This document provides an overview of modern cryptography with a focus on algorithms and principles relevant to Java developers. It covers symmetric and asymmetric encryption, hash functions, cryptographic attacks, and quantum cryptography, detailing various algorithms and their security implications. The discussion concludes with insights into post-quantum cryptography and future challenges in the field.
MD5 ALGORITHM.pptx
MD5 ALGORITHM.pptxRajapriya82 The MD5 algorithm is a cryptographic hash function that generates a 128-bit digest from a message of any length. It works by first padding the message to a length that is a multiple of 512 bits, then appending the message length. It initializes buffers and processes the message in 512-bit blocks using four rounds of 16 operations each, applying different functions to update the buffers. The final buffer values become the MD5 digest. It is commonly used to verify file integrity but is now considered insecure due to possible hash collisions.
How Hashing Algorithms Work
How Hashing Algorithms WorkCheapSSLsecurity The document provides a comprehensive overview of hashing algorithms, detailing their purpose in ensuring data integrity by converting inputs into fixed-size hash values. Key characteristics include irreversibility and uniqueness, with hash functions playing a crucial role in this process. Popular hashing algorithms such as SHA and MD are also mentioned, emphasizing the importance of these algorithms in various applications like password storage and data comparison.
Elgamal digital signature
Elgamal digital signatureMDKAWSARAHMEDSAGAR The ElGamal digital signature scheme was described by Tahir Elgamal in 1985. It uses a key pair consisting of a public key and private key, where the private key is used to generate signatures and the public key is used to verify signatures. Signatures provide message authentication, integrity, and non-repudiation by proving the message was signed by the private key holder. The document then proceeds to describe the technical process of generating keys, signing messages, and verifying signatures using ElGamal signatures with an example.
SHA 1 Algorithm.ppt
SHA 1 Algorithm.pptRajapriya82 The SHA-1 algorithm is a cryptographic hash function that takes an input and produces a 160-bit hash value. It works by padding the input message, appending the length, and then processing the message in 512-bit blocks through 80 processing steps using functions and constants to calculate new hash values. The final hash value after all blocks are processed represents the message digest.
crypto secure-hash-algorithm-versions.ppt
crypto secure-hash-algorithm-versions.pptshuchiagarwal12 The document describes the Secure Hash Algorithm (SHA) and its variants SHA-1 and SHA-512. SHA was originally designed by NIST and NSA in 1993 to produce 160-bit hash values from messages of any size. It was later revised as SHA-1 in 1995. SHA-512, introduced in 2002, produces 512-bit hash values and has an increased security level compared to SHA-1. Both algorithms work by padding the input message, appending its length, dividing it into blocks, initializing a chaining variable, and processing each block through multiple rounds that update the chaining variable.
More Related Content
What's hot (20)
RSA ALGORITHM
RSA ALGORITHMDr. Shashank Shetty The document summarizes the RSA encryption algorithm. It begins by explaining that RSA was developed in 1977 by Rivest, Shamir and Adleman. It then provides an example to demonstrate how RSA works step-by-step, generating keys, encrypting a message and decrypting the ciphertext. Finally, it discusses some challenges with breaking RSA encryption, including brute force attacks and mathematical attacks based on factoring the encryption keys, as well as timing attacks that aim to deduce keys based on variations in processing time.
Introduction to Cryptography
Introduction to CryptographyPopescu Petre The document provides an overview of cryptography, defining it as the practice of secure communication and outlining its two main branches: private key and public key cryptography. It explains private key cryptography with examples like the Caesar cipher and techniques for cracking it, while also detailing public key cryptography, particularly RSA, including its key generation process. The document emphasizes the importance of mathematics in cryptographic techniques and the need for key secrecy.
Hashing
HashingHossain Md Shakhawat A hash algorithm is a one-way function that converts a data string into a numeric string output of fixed length. It is collision resistant, meaning it is very unlikely for different data to produce the same hash value. Common hash algorithms include MD5 and SHA-1. A one-way hash function takes a variable-length input and produces a fixed-length output. It is easy to compute the hash but very difficult to reverse it or find collisions. Hash functions are used for password verification, digital signatures, and ensuring data integrity.
Public key cryptography and message authentication
Public key cryptography and message authenticationCAS The document discusses public-key cryptography and message authentication, focusing on secure hash functions (such as SHA), HMAC, and the RSA and Diffie-Hellman algorithms. It details how these cryptographic techniques ensure data integrity and secure key exchange, emphasizing the mechanisms behind hash functions and the mathematical principles governing RSA. The lecture is based on concepts from various authoritative sources in computer security.
MD5
MD5rokham khawaja The document discusses the MD5 algorithm used for generating message digests of arbitrary inputs. It describes the MD5 algorithm structure and implementation steps. The implementation involves padding the input message to a length congruent to 448 modulo 512 bits. A 64-bit representation of the original message length is then appended. The padded message is processed in 512-bit blocks, each divided into sixteen 32-bit words. Four initialization values are used to compute the message digest through four rounds of operations on each block.
CNIT 141: 6. Hash Functions
CNIT 141: 6. Hash FunctionsSam Bowne The document covers cryptography for computer networks, focusing on hash functions, their construction, and secure usage. It details various algorithms like SHA family and Blake2, explaining their unique features, vulnerabilities, and potential attacks such as length-extension and collision resistance. Additionally, it discusses practical applications of hash functions in digital signatures, message authentication, and integrity verification.
The SHA Hashing Algorithm
The SHA Hashing AlgorithmBob Landstrom The document discusses the importance of the SHA hashing algorithm and cryptography in protecting data integrity and privacy within data centers. It details the evolution of the SHA family, from SHA-0 to SHA-3, and provides recommendations on which algorithms to use based on data length. Additionally, it outlines the applications of SHA algorithms in ensuring message integrity across various internet protocols and for specific uses like password storage and Bitcoin transaction verification.
SHA
SHASubashiniRathinavel The Secure Hash Algorithm (SHA) was developed by NIST and NSA to generate a 160-bit message digest from inputs of less than 264 bits. SHA-1 works by padding the input message, appending the length, dividing into 512-bit blocks, initializing chain variables, and processing each block through 80 iterations involving logical, shift, and addition operations to update the variables. Each iteration uses a constant and the previous output to calculate the next output in order to make it difficult to determine the input from the digest or find colliding messages. Later versions such as SHA-256 increased security by lengthening the digest and number of steps.
DES (Data Encryption Standard) pressentation
DES (Data Encryption Standard) pressentationsarhadisoftengg This document discusses data encryption methods. It defines encryption as hiding information so it can only be accessed by those with the key. There are two main types: symmetric encryption uses one key, while asymmetric encryption uses two different but related keys. Encryption works by scrambling data using techniques like transposition, which rearranges the order, and substitution, which replaces parts with other values. The document specifically describes the Data Encryption Standard (DES) algorithm and the public key cryptosystem, which introduced the innovative approach of using different keys for encryption and decryption.
Digital Signature Standard
Digital Signature StandardSou Jana The document discusses digital signatures and the Digital Signature Standard (DSS). It explains that digital signatures authenticate the author, date, and contents of a message, and can be verified by third parties. The DSS is the US government approved digital signature scheme, developed by NIST and NSA, which uses the SHA hash algorithm and DSA digital signature algorithm. DSA creates a 320-bit signature using 512-1024 bit keys for security, is faster than RSA, and relies on the difficulty of computing discrete logarithms. The document outlines the DSA key generation, signature creation, and verification processes.
Elgamal & schnorr digital signature scheme copy
Elgamal & schnorr digital signature scheme copyNorth Cap University (NCU) Formely ITM University Digital signatures provide authentication of digital messages or documents. There are three main algorithms involved: hashing, signature generation, and signature verification. Common digital signature schemes include ElGamal, Schnorr, and the Digital Signature Standard (DSS). The DSS is based on ElGamal and Schnorr schemes. It uses smaller signatures than ElGamal by employing two moduli, one smaller than the other. Digital signatures are widely used to provide authentication in protocols like IPSec, SSL/TLS, and S/MIME.
Hash Function
Hash Functionstalin rijal A hash function maps data of arbitrary size to a fixed size value called a hash. Common hash functions include MD5 and SHA, with MD5 producing a 128-bit hash. While hashes were once used to securely store passwords, MD5 is now considered cryptographically broken due to collisions being found in its compression function. One-way signatures allow multiple users to generate linked signatures on the same message in a verifiable chain.
Cryptographic hash function md5
Cryptographic hash function md5Khulna University, Khulna, Bangladesh This document discusses the MD5 cryptographic hash function. It provides an introduction to hash functions and describes MD5, including its features, applications, algorithm, analysis, and drawbacks. MD5 produces a 128-bit hash value from a message of any size through a multi-step process involving padding, appending a length, initializing buffers, and processing in 16-word blocks. While once widely used, MD5 is now considered broken due to vulnerabilities found in its compression function and preimage resistance.
Cryptography and applications
Cryptography and applicationsthai This document provides an overview of cryptography and its applications. It discusses the history of cryptography beginning in ancient Egypt. It defines basic cryptography terminology like plaintext, ciphertext, cipher, key, encryption, decryption, cryptography, and cryptanalysis. It describes classical ciphers like the Caesar cipher and substitution ciphers. It also discusses cryptanalysis techniques, transposition ciphers, modern symmetric ciphers, public key cryptography including RSA, key distribution methods, and hybrid encryption.
AES KEY EXPANSION .pptx
AES KEY EXPANSION .pptxAhmudulHassan The document describes the AES key expansion process. The AES algorithm takes a 128-bit key as input and expands it into a linear array of 44 words using a key schedule. The key schedule applies the key expansion function g, which performs byte substitutions and XOR operations with round constants, to generate a key for each round. The initial key is added to the first four words of the expanded key schedule.
Secure Hash Algorithm
Secure Hash AlgorithmVishakha Agarwal Secure Hash Algorithm (SHA) was developed by NIST and NSA to hash messages into fixed-length message digests. SHA has multiple versions including SHA-1, SHA-2, and SHA-3. SHA-1 produces a 160-bit message digest and works by padding the input message, appending the length, dividing into blocks, initializing variables, and processing blocks through 80 rounds of operations to output the digest. SHA-512 is closely modeled after SHA-1 but produces a 512-bit digest and uses 1024-bit blocks.
Modern Cryptography
Modern CryptographyJames McGivern This document provides an overview of modern cryptography with a focus on algorithms and principles relevant to Java developers. It covers symmetric and asymmetric encryption, hash functions, cryptographic attacks, and quantum cryptography, detailing various algorithms and their security implications. The discussion concludes with insights into post-quantum cryptography and future challenges in the field.
MD5 ALGORITHM.pptx
MD5 ALGORITHM.pptxRajapriya82 The MD5 algorithm is a cryptographic hash function that generates a 128-bit digest from a message of any length. It works by first padding the message to a length that is a multiple of 512 bits, then appending the message length. It initializes buffers and processes the message in 512-bit blocks using four rounds of 16 operations each, applying different functions to update the buffers. The final buffer values become the MD5 digest. It is commonly used to verify file integrity but is now considered insecure due to possible hash collisions.
How Hashing Algorithms Work
How Hashing Algorithms WorkCheapSSLsecurity The document provides a comprehensive overview of hashing algorithms, detailing their purpose in ensuring data integrity by converting inputs into fixed-size hash values. Key characteristics include irreversibility and uniqueness, with hash functions playing a crucial role in this process. Popular hashing algorithms such as SHA and MD are also mentioned, emphasizing the importance of these algorithms in various applications like password storage and data comparison.
Elgamal digital signature
Elgamal digital signatureMDKAWSARAHMEDSAGAR The ElGamal digital signature scheme was described by Tahir Elgamal in 1985. It uses a key pair consisting of a public key and private key, where the private key is used to generate signatures and the public key is used to verify signatures. Signatures provide message authentication, integrity, and non-repudiation by proving the message was signed by the private key holder. The document then proceeds to describe the technical process of generating keys, signing messages, and verifying signatures using ElGamal signatures with an example.
Elgamal & schnorr digital signature scheme copy
Elgamal & schnorr digital signature scheme copyNorth Cap University (NCU) Formely ITM University
Similar to Secure hashing algorithm (20)
SHA 1 Algorithm.ppt
SHA 1 Algorithm.pptRajapriya82 The SHA-1 algorithm is a cryptographic hash function that takes an input and produces a 160-bit hash value. It works by padding the input message, appending the length, and then processing the message in 512-bit blocks through 80 processing steps using functions and constants to calculate new hash values. The final hash value after all blocks are processed represents the message digest.
crypto secure-hash-algorithm-versions.ppt
crypto secure-hash-algorithm-versions.pptshuchiagarwal12 The document describes the Secure Hash Algorithm (SHA) and its variants SHA-1 and SHA-512. SHA was originally designed by NIST and NSA in 1993 to produce 160-bit hash values from messages of any size. It was later revised as SHA-1 in 1995. SHA-512, introduced in 2002, produces 512-bit hash values and has an increased security level compared to SHA-1. Both algorithms work by padding the input message, appending its length, dividing it into blocks, initializing a chaining variable, and processing each block through multiple rounds that update the chaining variable.
Analysis and Evolution of SHA-1 Algorithm - Analytical Technique
Analysis and Evolution of SHA-1 Algorithm - Analytical TechniqueIJCNCJournal The document provides a comprehensive analysis of the SHA-1 cryptographic hash algorithm, detailing its 160-bit output and the mathematical processes involved in generating hash values. Despite being cryptographically broken, SHA-1 remains in use for various applications, with the paper discussing its theory, implementation, and various configurations. The analysis covers the algorithm's architecture, including message expansion, padding, word generation, and compression functions, illustrating the technical details necessary for understanding SHA-1's operation.
Analysis and Evolution of SHA-1 Algorithm - Analytical Technique
Analysis and Evolution of SHA-1 Algorithm - Analytical TechniqueIJCNCJournal The document analyzes the SHA-1 algorithm, a cryptographic hash function that produces a 160-bit hash value, and discusses its theoretical foundations and practical applications despite being cryptographically compromised. It details the algorithm's process, including message encoding, padding, chunking, and the use of mathematical techniques for word expansion, ultimately highlighting its ongoing relevance despite known vulnerabilities. The work aims to provide insights into SHA-1's operation, its relationship with other hash functions, and the structure of digital signatures.
Sha
Shaha123 Hash functions take a variable-length input and produce a fixed-length output. They are used to verify data integrity and ensure data has not been altered. Cryptographic hash functions have properties of being one-way and collision resistant. Secure Hash Algorithm 512 (SHA-512) is an iterative cryptographic hash function that produces a 512-bit hash value. It works by processing the input message in 1024-bit blocks through 80 rounds of compression functions using logical operations and round constants. SHA-512 and other cryptographic hash functions have applications in security protocols like TLS, PGP, and DNSSEC.
Network security CS6
Network security CS6Infinity Tech Solutions The document covers network security topics, specifically focusing on modes of operation, hash functions, and message authentication codes. It provides detailed explanations of SHA-1, including its processing steps, functions, constants, and buffer initialization. Additionally, it briefly addresses SHA-3 and includes a summary of various types of message authentication.
Secure Hash Algorithm (SHA 256) - Detailed Architecture
Secure Hash Algorithm (SHA 256) - Detailed ArchitectureSaravananPalani22 SHA-256, a secure hashing algorithm developed by the NSA in 2001, produces a 256-bit hash and is part of the SHA-2 family, offering superior security compared to MD5, SHA-0, and SHA-1. The document outlines the pre-processing of input into a 512-bit format and the step-by-step process to generate the final hash, using examples like the hashing of the word 'password'. Additionally, it emphasizes the immense time required to perform collision attacks at current hash rates, making SHA-256 highly secure.
Hash Techniques in Cryptography
Hash Techniques in CryptographyBasudev Saha Hash functions are used to compress variable length messages into fixed length digests. They provide compression, efficiency, and hide message content. Properties include one-way, weak collision, and strong collision resistance. Merkle-Damgard iteration is used to build cryptographic hash functions from compression functions. Applications include digital signatures, message authentication codes, and key derivation. Common hash functions are MD4, MD5, and SHA which use Boolean functions and updating rules in their algorithms. Hash functions provide security by making it difficult to find collisions or inputs that result in specific outputs.
Hash Function & Analysis
Hash Function & AnalysisPawandeep Kaur This document discusses hash functions and their analysis for a network security seminar. It begins by defining a hash function as a mathematical function that converts a large amount of data into a small string of integers. Common applications of hash functions include hash tables for quickly searching data, eliminating data redundancy, caches, bloom filters, and pattern matching. Cryptographic hash functions have properties like preimage and second preimage resistance as well as collision resistance. Popular cryptographic hash functions discussed include MD2, MD4, MD5, SHA-1, and SHA-2, along with their advantages, limitations, and examples of attacks.
Chapter 7-Hash-Function in Cryptography.ppt
Chapter 7-Hash-Function in Cryptography.pptKrishnenduRarhi The document discusses various cryptographic hash functions, focusing on SHA-512 and MD5, including their structures and resistance to attacks. It outlines SHA-512's message length limitations, padding requirements, and compression functions, while also detailing MD5's processing methodology and known vulnerabilities. The importance of preimage resistance, second preimage resistance, and collision resistance in cryptographic hash functions is emphasized throughout.
27-SHA1.ppt
27-SHA1.pptPranjalSinha23 This document discusses hash functions and the Secure Hash Algorithm 1 (SHA-1). It describes the goals of hash functions as providing a unique fingerprint of a message through fast computation of a digest in a way that is one-way and makes collisions difficult to find. SHA-1 is presented as iterating over message blocks to compress them into a 160-bit digest value through repeated applications of a compression function. The compression function expands each block before applying four rounds of nonlinear mixing via modular addition and bitwise operations. The document raises the prospect of birthday attacks finding collisions in SHA-1 and implies its security may degrade over time.
Hash mac algorithms
Hash mac algorithmsFraboni Ec This document provides an overview of hash functions, secure hash algorithms (SHA), and HMAC.
It describes how hash functions work by taking a message and producing a fixed-size hash value. SHA algorithms like SHA-1, SHA-256, SHA-384, and SHA-512 are described as secure hash functions developed by NIST. The document outlines the 5 steps of the SHA-512 algorithm: 1) append padding bits, 2) append length, 3) initialize hash buffer, 4) process message in blocks, and 5) output hash value.
HMAC is then introduced as a way to incorporate a secret key into an existing hash algorithm like MD5 or SHA-1 to produce a message authentication code
Hash mac algorithms
Hash mac algorithmsTony Nguyen This document discusses hash and MAC algorithms. It provides details on hash functions, the Secure Hash Algorithm (SHA), and HMAC.
Hash functions take a message and produce a fixed-size hash value. SHA is a secure hash algorithm developed by NIST that produces 160-bit or longer hash values. It works by padding the message, appending the length, initializing buffers, processing the message in blocks through compression functions, and outputting the hash value.
HMAC is a MAC algorithm that incorporates a secret key into an existing hash function like MD5 or SHA. It works by padding the key, XORing it with ipad or opad, appending the message or hash, and applying the hash function to produce the
Hash mac algorithms
Hash mac algorithmsLuis Goldster This document discusses hash and MAC algorithms. It provides details on hash functions, the Secure Hash Algorithm (SHA), and HMAC.
Hash functions take a message and produce a fixed-size hash value. SHA is a secure hash algorithm developed by NIST that produces 160-bit or longer hash values. It works by padding the message, appending the length, initializing buffers, processing the message in blocks through compression functions, and outputting the hash value.
HMAC is a MAC algorithm that incorporates a secret key into an existing hash function like MD5 or SHA. It works by padding the key, XORing it with ipad or opad, appending the message or hash, and applying the hash function to produce the
Hash mac algorithms
Hash mac algorithmsDavid Hoen This document discusses hash and MAC algorithms. It provides details on hash functions, the Secure Hash Algorithm (SHA), and HMAC.
Hash functions take a message and produce a fixed-size hash value. SHA is a secure hash algorithm developed by NIST that produces 160-bit or longer hash values. It works by padding and processing the message in blocks, using a compression function and initialization vector.
HMAC is a MAC algorithm that incorporates a secret key into the hashing process. It works by XORing the key with ipad and opad pads, hashing the padded message, and outputting the result. HMAC allows existing hash functions to be used for message authentication in a way that relies on the secret
Hash mac algorithms
Hash mac algorithmsJames Wong This document discusses hash and MAC algorithms. It provides details on hash functions, the Secure Hash Algorithm (SHA), and HMAC.
Hash functions take a message and produce a fixed-size hash value. SHA is a secure hash algorithm developed by NIST that produces 160-bit or longer hash values. It works by padding and processing the message in blocks, using a compression function and initialization vector.
HMAC is a MAC algorithm that incorporates a secret key into an existing hash function like MD5 or SHA. It works by XORing the key with ipad and opad pads, hashing the padded message, and outputting the result. HMAC executes with similar speed to the underlying hash function.
Hash& mac algorithms
Hash& mac algorithmsHarry Potter This document discusses hash and MAC algorithms. It provides details on hash functions, the Secure Hash Algorithm (SHA), and HMAC.
Hash functions take a message and produce a fixed-size hash value. SHA is a secure hash algorithm developed by NIST that produces 160-bit or longer hash values. It involves padding the message, initializing a buffer, processing the message in blocks through a compression function, and outputting the final hash.
HMAC is a MAC algorithm that incorporates a secret key into an existing hash function like MD5 or SHA. It pads and XORs the key, hashes the result with the message, then hashes again with a padded key to produce the MAC value.
Hash mac algorithms
Hash mac algorithmsYoung Alista The document discusses hash and MAC algorithms, focusing on Secure Hash Algorithms (SHA) and HMAC. It details the steps involved in SHA operations, particularly SHA-512, emphasizing the addition of padding, length, and the processing of message blocks using compression functions. HMAC is introduced as a method for constructing message authentication codes using existing hash functions, outlining its design objectives and security considerations.
Data streaming algorithms
Data streaming algorithmsHridyesh Bisht The document discusses data streaming algorithms, particularly focusing on approximate counting and hashing algorithms. It details concepts such as distinct elements counting, frequency estimation, and the workings of various hashing functions like MD5, SHA-1, and SHA-2. Additionally, it describes algorithms for approximating the f0-norm to count distinct items in data streams and highlights the applications of these algorithms in areas like data compression and artificial intelligence.
Hashfunction
HashfunctionFraboni Ec The document discusses hash functions and message authentication codes (MACs). It begins by defining hash functions and MACs, noting that hash functions generate a fingerprint for a message without a key while MACs use a keyed hash function. It then covers security requirements for hash functions like one-wayness and collision resistance. Popular hash functions are described like MD5, SHA-1, and the SHA-2 family. Constructions for hash functions based on block ciphers and iterated hash functions are also outlined. The document concludes by comparing hash functions and MACs and describing common MAC constructions.
Ad
Recently uploaded (20)
Pests of Maize: An comprehensive overview.pptx
Pests of Maize: An comprehensive overview.pptxArshad Shaikh Maize is susceptible to various pests that can significantly impact yields. Key pests include the fall armyworm, stem borers, cob earworms, shoot fly. These pests can cause extensive damage, from leaf feeding and stalk tunneling to grain destruction. Effective management strategies, such as integrated pest management (IPM), resistant varieties, biological control, and judicious use of chemicals, are essential to mitigate losses and ensure sustainable maize production.
K12 Tableau User Group virtual event June 18, 2025
K12 Tableau User Group virtual event June 18, 2025dogden2 National K12 Tableau User Group: June 2025 meeting slides
Paper 107 | From Watchdog to Lapdog: Ishiguro’s Fiction and the Rise of “Godi...
Paper 107 | From Watchdog to Lapdog: Ishiguro’s Fiction and the Rise of “Godi...Rajdeep Bavaliya Dive into a captivating analysis where Kazuo Ishiguro’s nuanced fiction meets the stark realities of post‑2014 Indian journalism. Uncover how “Godi Media” turned from watchdog to lapdog, echoing the moral compromises of Ishiguro’s protagonists. We’ll draw parallels between restrained narrative silences and sensationalist headlines—are our media heroes or traitors? Don’t forget to follow for more deep dives!
M.A. Sem - 2 | Presentation
Presentation Season - 2
Paper - 107: The Twentieth Century Literature: From World War II to the End of the Century
Submitted Date: April 4, 2025
Paper Name: The Twentieth Century Literature: From World War II to the End of the Century
Topic: From Watchdog to Lapdog: Ishiguro’s Fiction and the Rise of “Godi Media” in Post-2014 Indian Journalism
[Please copy the link and paste it into any web browser to access the content.]
Video Link: https://youtu.be/kIEqwzhHJ54
For a more in-depth discussion of this presentation, please visit the full blog post at the following link: https://rajdeepbavaliya2.blogspot.com/2025/04/from-watchdog-to-lapdog-ishiguro-s-fiction-and-the-rise-of-godi-media-in-post-2014-indian-journalism.html
Please visit this blog to explore additional presentations from this season:
Hashtags:
#GodiMedia #Ishiguro #MediaEthics #WatchdogVsLapdog #IndianJournalism #PressFreedom #LiteraryCritique #AnArtistOfTheFloatingWorld #MediaCapture #KazuoIshiguro
Keyword Tags:
Godi Media, Ishiguro fiction, post-2014 Indian journalism, media capture, Kazuo Ishiguro analysis, watchdog to lapdog, press freedom India, media ethics, literature and media, An Artist of the Floating World
Plate Tectonic Boundaries and Continental Drift Theory
Plate Tectonic Boundaries and Continental Drift TheoryMarie This 28 slide presentation covers the basics of plate tectonics and continental drift theory. It is an effective introduction into a full plate tectonics unit study, but does not cover faults, stress, seismic waves, or seafloor spreading.
To download PDF, visit The Homeschool Daily. We will be uploading more slideshows to follow this one. Blessings, Marie
Tanja Vujicic - PISA for Schools contact Info
Tanja Vujicic - PISA for Schools contact InfoEduSkills OECD Tanja Vujicic, Senior Analyst and PISA for School’s Project Manager at the OECD spoke at the OECD webinar 'Turning insights into impact: What do early case studies reveal about the power of PISA for Schools?' on 20 June 2025
PISA for Schools is an OECD assessment that evaluates 15-year-old performance on reading, mathematics, and science. It also gathers insights into students’ learning environment, engagement and well-being, offering schools valuable data that help them benchmark performance internationally and improve education outcomes. A central ambition, and ongoing challenge, has been translating these insights into meaningful actions that drives lasting school improvement.
INDUCTIVE EFFECT slide for first prof pharamacy students
INDUCTIVE EFFECT slide for first prof pharamacy studentsSHABNAM FAIZ The inductive effect is the electron-withdrawing or electron-donating effect transmitted through sigma (σ) bonds in a molecule due to differences in electronegativity between atoms.
---
🔹 Definition:
The inductive effect is the permanent shifting of electrons in a sigma bond caused by the electronegativity difference of atoms, resulting in partial charges within the molecule.
Code Profiling in Odoo 18 - Odoo 18 Slides
Code Profiling in Odoo 18 - Odoo 18 SlidesCeline George Profiling in Odoo identifies slow code and resource-heavy processes, ensuring better system performance. Odoo code profiling detects bottlenecks in custom modules, making it easier to improve speed and scalability.
SCHIZOPHRENIA OTHER PSYCHOTIC DISORDER LIKE Persistent delusion/Capgras syndr...
SCHIZOPHRENIA OTHER PSYCHOTIC DISORDER LIKE Persistent delusion/Capgras syndr...parmarjuli1412 SCHIZOPHRENIA INCLUDED TOPIC IS INTRODUCTION, DEFINITION OF GENERAL TERM IN PSYCHIATRIC, THEN DIFINITION OF SCHIZOPHRENIA, EPIDERMIOLOGY, ETIOLOGICAL FACTORS, CLINICAL FEATURE(SIGN AND SYMPTOMS OF SCHIZOPHRENIA), CLINICAL TYPES OF SCHIZOPHRENIA, DIAGNOSIS, INVESTIGATION, TREATMENT MODALITIES(PHARMACOLOGICAL MANAGEMENT, PSYCHOTHERAPY, ECT, PSYCHO-SOCIO-REHABILITATION), NURSING MANAGEMENT(ASSESSMENT,DIAGNOSIS,NURSING INTERVENTION,AND EVALUATION), OTHER PSYCHOTIC DISORDER LIKE Persistent delusion/Capgras syndrome(The Delusion of Doubles)/Acute and Transient Psychotic Disorders/Induced Delusional Disorders/Schizoaffective Disorder /CAPGRAS SYNDROME(DELUSION OF DOUBLE), GERIATRIC CONSIDERATION, FOLLOW UP, HOMECARE AND REHABILITATION OF THE PATIENT,
2025 June Year 9 Presentation: Subject selection.pptx
2025 June Year 9 Presentation: Subject selection.pptxmansk2 2025 June Year 9 Presentation: Subject selection
June 2025 Progress Update With Board Call_In process.pptx
June 2025 Progress Update With Board Call_In process.pptxInternational Society of Service Innovation Professionals ---
June 25 ISSIP Event - slides in process
20250618 PPre-Event Presentation Summary - Progress Update with Board Series June 25
ISSIP Website Upcoming Events Description: https://issip.org/event/semi-annual-issip-progress-call/
Register here (even if you cannot attend live online, all who register will get link to recording and slides post-event): https://docs.google.com/forms/d/e/1FAIpQLSdThrop1rafOCo4PQkYiS2XApclJuMjYONEHRMGBsceRdcQqg/viewform
This pre-event presentation: https://www.slideshare.net/slideshow/june-2025-progress-update-with-board-call_in-process-pptx/280718770
This pre-event recording: https://youtu.be/Shjgd5o488o
---
VCE Literature Section A Exam Response Guide
VCE Literature Section A Exam Response Guidejpinnuck This practical guide shows students of Unit 3&4 VCE Literature how to write responses to Section A of the exam. Including a range of examples writing about different types of texts, this guide:
*Breaks down and explains what Q1 and Q2 tasks involve and expect
*Breaks down example responses for each question
*Explains and scaffolds students to write responses for each question
*Includes a comprehensive range of sentence starters and vocabulary for responding to each question
*Includes critical theory vocabulary lists to support Q2 responses
IIT KGP Quiz Week 2024 Sports Quiz (Prelims + Finals)
IIT KGP Quiz Week 2024 Sports Quiz (Prelims + Finals)IIT Kharagpur Quiz Club The document outlines the format for the Sports Quiz at Quiz Week 2024, covering various sports & games and requiring participants to Answer without external sources. It includes specific details about question types, scoring, and examples of quiz questions. The document emphasizes fair play and enjoyment of the quiz experience.
Paper 108 | Thoreau’s Influence on Gandhi: The Evolution of Civil Disobedience
Paper 108 | Thoreau’s Influence on Gandhi: The Evolution of Civil DisobedienceRajdeep Bavaliya Dive into the powerful journey from Thoreau’s 19th‑century essay to Gandhi’s mass movement, and discover how one man’s moral stand became the backbone of nonviolent resistance worldwide. Learn how conscience met strategy to spark revolutions, and why their legacy still inspires today’s social justice warriors. Uncover the evolution of civil disobedience. Don’t forget to like, share, and follow for more deep dives into the ideas that changed the world.
M.A. Sem - 2 | Presentation
Presentation Season - 2
Paper - 108: The American Literature
Submitted Date: April 2, 2025
Paper Name: The American Literature
Topic: Thoreau’s Influence on Gandhi: The Evolution of Civil Disobedience
[Please copy the link and paste it into any web browser to access the content.]
Video Link: https://youtu.be/HXeq6utg7iQ
For a more in-depth discussion of this presentation, please visit the full blog post at the following link: https://rajdeepbavaliya2.blogspot.com/2025/04/thoreau-s-influence-on-gandhi-the-evolution-of-civil-disobedience.html
Please visit this blog to explore additional presentations from this season:
Hashtags:
#CivilDisobedience #ThoreauToGandhi #NonviolentResistance #Satyagraha #Transcendentalism #SocialJustice #HistoryUncovered #GandhiLegacy #ThoreauInfluence #PeacefulProtest
Keyword Tags:
civil disobedience, Thoreau, Gandhi, Satyagraha, nonviolent protest, transcendentalism, moral resistance, Gandhi Thoreau connection, social change, political philosophy
Birnagar High School Platinum Jubilee Quiz.pptx
Birnagar High School Platinum Jubilee Quiz.pptxSourav Kr Podder Birnagar High School Platinum Jubilee Celebration Quiz
THE PSYCHOANALYTIC OF THE BLACK CAT BY EDGAR ALLAN POE (1).pdf
THE PSYCHOANALYTIC OF THE BLACK CAT BY EDGAR ALLAN POE (1).pdfnabilahk908 Psychoanalytic Analysis of The Black Cat by Edgar Allan Poe explores the deep psychological dimensions of the narrator’s disturbed mind through the lens of Sigmund Freud’s psychoanalytic theory. According to Freud (1923), the human psyche is structured into three components: the Id, which contains primitive and unconscious desires; the Ego, which operates on the reality principle and mediates between the Id and the external world; and the Superego, which reflects internalized moral standards.
In this story, Poe presents a narrator who experiences a psychological breakdown triggered by repressed guilt, aggression, and internal conflict. This analysis focuses not only on the gothic horror elements of the narrative but also on the narrator’s mental instability and emotional repression, demonstrating how the imbalance of these three psychic forces contributes to his downfall.
LDMMIA Shop & Student News Summer Solstice 25
LDMMIA Shop & Student News Summer Solstice 25LDM & Mia eStudios 6/18/25
Shop, Upcoming: Final Notes to Review as we Close Level One. Make sure to review the orientation and videos as well. There’s more to come and material to cover in Levels 2-3. The content will be a combination of Reiki and Yoga. Also energy topics of our spiritual collective.
Thanks again all future Practitioner Level Students. Our Levels so far are: Guest, Grad, and Practitioner. We have had over 5k Spring Views.
https://ldm-mia.creator-spring.com
June 2025 Progress Update With Board Call_In process.pptx
June 2025 Progress Update With Board Call_In process.pptxInternational Society of Service Innovation Professionals
Ad
Secure hashing algorithm
- 1. SECURE HASHING ALGORITHM By: Ruth Betcher
- 2. Purpose: Authentication Not Encryption Authentication Requirements: Masquerade – Insertion of message from fraudulent source Content Modification – Changing content of message Sequence Modification – Insertion, deletion and reordering sequence Timing Modification – Replaying valid sessions
- 3. Background Theory • Message Digest or “Fingerprint” → Condensed Representation → Easy to generate for a given file. • Computationally infeasible to produce two messages with same message digest • Impossible to recreate a message given a message digest. • Data Integrity and Comparison Checking → Message Integrity Validation
- 4. Applications: One-way hash functions • Public Key Algorithms – Password Logins – Encryption Key Management – Digital Signatures • Integrity Checking – Virus and Malware Scanning • Authentication – Secure Web Connections • (PGP, SSL, SSH, S/MIME)
- 5. Variants • MD4 and MD5 by Ron Rivest (1990,1994) • SHA-0, SHA-1 by NSA (1993, 1995) • RIPEMD-160 (1996) • SHA-2 (2002 – 224, 256, 385, 512) • Whirlpool • Tiger • GOST-3411 • SHA-3 • Winner selected from solicitations in 2012
- 6. Basic Hash Function Diagram
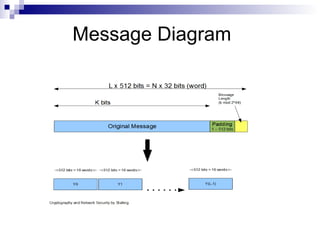
- 8. SHA-1 (160 bit message) Algorithm Framework Step 1: Append Padding Bits…. Message is “padded” with a 1 and as many 0’s as necessary to bring the message length to 64 bits fewer than an even multiple of 512. Step 2: Append Length.... 64 bits are appended to the end of the padded message. These bits hold the binary format of 64 bits indicating the length of the original message. http://www.herongyang.com f
- 9. SHA-1 Framework Continued Step 3: Prepare Processing Functions…. SHA1 requires 80 processing functions defined as: f(t;B,C,D) = (B AND C) OR ((NOT B) AND D) ( 0 <= t <= 19) f(t;B,C,D) = B XOR C XOR D (20 <= t <= 39) f(t;B,C,D) = (B AND C) OR (B AND D) OR (C AND D) (40 <= t <=59) f(t;B,C,D) = B XOR C XOR D (60 <= t <= 79) Step 4: Prepare Processing Constants.... SHA1 requires 80 processing constant words defined as: K(t) = 0x5A827999 ( 0 <= t <= 19) K(t) = 0x6ED9EBA1 (20 <= t <= 39) K(t) = 0x8F1BBCDC (40 <= t <= 59) K(t) = 0xCA62C1D6 (60 <= t <= 79) http://www.herongyang.com
- 10. SHA-1 Framework Continued Step 5: Initialize Buffers…. SHA1 requires 160 bits or 5 buffers of words (32 bits): H0 = 0x67452301 H1 = 0xEFCDAB89 H2 = 0x98BADCFE H3 = 0x10325476 H4 = 0xC3D2E1F0 http://www.herongyang.com
- 11. SHA-1 Framework Final Step Step 6: Processing Message in 512-bit blocks (L blocks in total message)…. This is the main task of SHA1 algorithm which loops through the padded and appended message in 512-bit blocks. Input and predefined functions: M[1, 2, ..., L]: Blocks of the padded and appended message f(0;B,C,D), f(1,B,C,D), ..., f(79,B,C,D): 80 Processing Functions K(0), K(1), ..., K(79): 80 Processing Constant Words H0, H1, H2, H3, H4, H5: 5 Word buffers with initial values http://www.herongyang.com
- 12. SHA-1 Framework Continued Step 6: Pseudo Code…. For loop on k = 1 to L (W(0),W(1),...,W(15)) = M[k] /* Divide M[k] into 16 words */ For t = 16 to 79 do: W(t) = (W(t-3) XOR W(t-8) XOR W(t-14) XOR W(t-16)) <<< 1 A = H0, B = H1, C = H2, D = H3, E = H4 For t = 0 to 79 do: TEMP = A<<<5 + f(t;B,C,D) + E + W(t) + K(t) E = D, D = C, C = B<<<30, B = A, A = TEMP End of for loop H0 = H0 + A, H1 = H1 + B, H2 = H2 + C, H3 = H3 + D, H4 = H4 + E End of for loop Output: H0, H1, H2, H3, H4, H5: Word buffers with final message digest http://www.herongyang.com
- 13. Message Diagram
- 14. SHA-1 Message Digest The message digest of the string: “This is a test for theory of computation” 4480afca4407400b035d9debeb88bfc402db514f
- 15. Cryptanalysis and Limitation • Key Premises for Hash Functions: 1. Impossible to re-create a message given a fingerprint 2. Collision Free • SHA-1 failure using brute force attack in 280 operations • Collision failure found in 2005 in 233 operations
- 16. Bibliography http://www.herongyang.com http://www.ipa.go.jp/security Salomon, David, Foundations of Computer Security Springer-Verlag London Limited 2006. Schneier, Bruce, “Opinion: Cryptanalysis of MD % and SHA: Time for a new standard”, Computer World, August 2004. Stallings, William, Cryptography and Network Security, Prentice Hall, 1999. Tanenbaum, Andrew, Computer Networks, Prentice Hall, 2003.
Editor's Notes
- #3: Verify that received messages come from the alleged source and have not been altered. Also verify the sequence and timing. Digital Signature is used to combat denial of receipt of a message by either the source or desitination.
- #6: All variants have a similar framework. The variation is in the bits compressed into the digest. Thereby, differ in the number of blocks and words of data used in hashing.
