Secure Programming In Php
- 1. Secure Web App Programming in PHPAkash Mahajan v1.0
- 2. Cross Site Scripting - XSSInjecting HTML/JS into the site. Non-persistent/Reflected/First OrderScript is taken from the request and displayed in the browser directlyexample.com/search?q=<script>alert(‘hi’);</script>Example.com/index.php?lang=path to php shell Persistent/Stored/Second OrderFirst name of a registration form is vuln and the value is stored in the databaseHello <iframesrc=http://f1y.in/0.js></iframe>DOM BasedNo example, mentioned by AmitKlien in his paper XSS of the Third Kind
- 3. XSS mitigation in PHPSanitize all globals ($_GET, $_POST, $_COOKIE)Use strip_tags()Use inpekt library code.google.com/p/inspektEscape everything before displayinghtmlentities(), htmlspeciachars()Client headers like user agent can be malicious as well. Thumb rule, if its not your data consider it bad. If you can verify it, consider it trusted good data.White listing helps in verifying good data more than black listing.See examples at xssed.com
- 4. SQL Injection Allowing SQL to be injected in the database query. Most common attack point is the search of any dynamic website and registration forms. These two will be definitely talking to the database. $sql = "SELECT * FROM table WHERE id = '" . $_REQUEST['id'] . "'";id = ‘ OR 1 UNION ALL SELECT * FROM table;Excellent examples http://google.com/search?q=site:slideshare.net sql injection
- 5. SQL Injection - Mitigationmysql_real_escape_string()$dbquery = sprintf(“SELECT name FROM user WHERE id=‘%s’”, mysql_real_escape_string(‘id’));Parameterized queries$res = $query(“SELECT name FROM user WHERE id=?”, $id);Standard mysql module in PHP doesn’t allow for parameterized queries. You need mysqli Stored ProceduresSee a kickass example of stored proc used to hack more than hundred thousand websiteshttp://www.breach.com/resources/breach-security-labs/alerts/mass-sql-injection-attack-evolutio
- 6. File UploadsWeb apps add a directory in document root for storing file uploads and give write access. They don’t randomize filenames. So a specially crafted image file which has PHP code written in it gets saved there. The malicious user is now free to call it using a GET request and it gets executed. http://www.scanit.be/uploads/php-file-upload.pdf
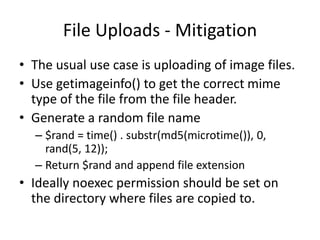
- 7. File Uploads - MitigationThe usual use case is uploading of image files. Use getimageinfo() to get the correct mime type of the file from the file header.Generate a random file name $rand = time() . substr(md5(microtime()), 0, rand(5, 12));Return $rand and append file extensionIdeally noexec permission should be set on the directory where files are copied to.
- 8. EndgameAt this point you have reasonable ensured that your PHP web application is not compromised. But the user connecting to your website are vulnerable to session hijacking, CSRF from your site etc.There are work around to the standard PHP functions like this one for mysql_real_escape_strings()http://shiflett.org/blog/2006/jan/addslashes-versus-mysql-real-escape-string




![SQL Injection Allowing SQL to be injected in the database query. Most common attack point is the search of any dynamic website and registration forms. These two will be definitely talking to the database. $sql = "SELECT * FROM table WHERE id = '" . $_REQUEST['id'] . "'";id = ‘ OR 1 UNION ALL SELECT * FROM table;Excellent examples http://google.com/search?q=site:slideshare.net sql injection](https://image.slidesharecdn.com/secureprogramminginphp-091014045522-phpapp01/85/Secure-Programming-In-Php-4-320.jpg)