DevOps & Security: Here & Now
Download as pptx, pdf11 likes9,118 views
How do you integrate security within a Continuous Deployment (CD) environment - where every 5 minutes a feature, an enhancement, or a bug fix needs to be released? Traditional application security tools which require lengthy periods of configuration, tuning and application learning have become irrelevant in these fast-pace environments. Yet, falling back only on the secure coding practices of the developer cannot be tolerated. Secure coding requires a new approach where security tools become part of the development environment – and eliminate any unnecessary overhead. By collaborating with development teams, understanding their needs and requirements, you can pave the way to a secure deployment in minutes.
1 of 31
Downloaded 160 times






























Ad
Recommended
DevSecOps - The big picture



DevSecOps - The big pictureDevSecOpsSg This document discusses the concepts of DevSecOps at a high level. It begins with a brief history of development methodologies, from Waterfall to Agile, and how Ops became a bottleneck. This led to trends in Agile Operations and collaboration between Dev and Ops, known as DevOps. DevSecOps expands this to incorporate security. It discusses DevSecOps in terms of culture, processes, and technologies, with a focus on secure software development lifecycles, security pipelines, requirements management, and automated testing and monitoring. The goal of DevSecOps is to enable organizations to deliver inherently secure software at DevOps speed.
Static Analysis Security Testing for Dummies... and You



Static Analysis Security Testing for Dummies... and YouKevin Fealey Most enterprise application security teams have at least one Static Analysis Security Testing (SAST) tool in their tool-belt; but for many, the tool never leaves the belt. SAST tools have gotten a reputation for being slow, error-prone, and difficult to use; and out of the box, many of them are – but with a little more knowledge behind how these tools are designed, a SAST tool can be a valuable part of any security program.
In this talk, we’ll help you understand the strengths and weaknesses of SAST tools by illustrating how they trace your code for vulnerabilities. You’ll see out-of-the-box rules for commercial and open-source SAST tools, and learn how to write custom rules for the widely-used open source SAST tool, PMD. We’ll explain the value of customizing tools for your organization; and you’ll learn how to integrate SAST technologies into your existing build and deployment pipelines. Lastly, we’ll describe many of the common challenges organizations face when deploying a new security tool to security or development teams, as well as some helpful hints to resolve these issues
Maven Introduction



Maven IntroductionSandeep Chawla Maven is a build tool that can manage a project's build process, dependencies, documentation and reporting. It uses a Project Object Model (POM) file to store build configuration and metadata. Maven has advantages over Ant like built-in functionality for common tasks, cross-project reuse, and support for conditional logic. It works by defining the project with a POM file then running goals bound to default phases like compile, test, package to build the project.
Room 3 - 6 - Nguyễn Văn Thắng & Dzung Nguyen - Ứng dụng openzfs làm lưu trữ t...



Room 3 - 6 - Nguyễn Văn Thắng & Dzung Nguyen - Ứng dụng openzfs làm lưu trữ t...Vietnam Open Infrastructure User Group Nguyễn Văn Thắng & Dzung Nguyen - Ứng dụng openzfs làm lưu trữ tập trung
Simplified Security Code Review Process



Simplified Security Code Review ProcessSherif Koussa This document summarizes a presentation about simplifying secure code reviews. It discusses defining an effective security code review process, including reconnaissance, threat modeling, automation, manual review, confirmation, and reporting. It also discusses using the OWASP Top 10 list to focus code reviews, and defining trust boundaries to identify areas of code to review for specific vulnerabilities. The goal is to introduce a simplified process that can help development teams integrate security code reviews into their workflow.
Continuous Delivery in the Cloud with Bitbucket Pipelines



Continuous Delivery in the Cloud with Bitbucket PipelinesAtlassian This document discusses Bitbucket Pipelines, a continuous integration tool from Atlassian. It allows developers to automatically build, test, and deploy their code every time a change is merged into a shared repository. Pipelines uses Docker containers to run builds, allowing them to be fast, isolated from infrastructure concerns, and reproducible across environments. It also supports defining build configurations as code to make the pipeline definition versioned, reusable, and easy to understand at a glance.
Intro to DevOps



Intro to DevOpsErnest Mueller An introduction to DevOps - its definition and practice areas - for the Alamo Agilistas on March 23, 2017.
Bridging the Security Testing Gap in Your CI/CD Pipeline



Bridging the Security Testing Gap in Your CI/CD PipelineDevOps.com Are you struggling with application security testing? Do you wish it was easier, faster, and better? Join us to learn more about IAST, a next-generation application security tool that provides highly accurate, real-time vulnerability results without the need for application or source code scans. Learn how this nondisruptive tool can:
Run in the background and report vulnerabilities during functional testing, CI/CD, and QA activities.
Auto verify, prioritize and triage vulnerability findings in real time with 100% confidence.
Fully automate secure app delivery and deployment, without the need for extra security scans or processes.
Free up DevOps resources to focus on strategic or mission-critical tasks and contributions.
Apache Maven 3



Apache Maven 3Maxime Gréau Slides de présentation du livre "Apache Maven - Maîtrisez l'infrastructure d'un projet Java EE"
CI/CD Best Practices for Your DevOps Journey



CI/CD Best Practices for Your DevOps JourneyDevOps.com The journey to realizing DevOps in any organization is fraught with a number of obstacles for developers and other stakeholders. These challenges are often caused by key CI/CD practices being misunderstood, partially implemented or even completely skipped. Now, as the industry positions itself to build on DevOps practices with a Software Delivery Management strategy, it’s more important than ever that we implement CI/CD best practices, and prepare for the future.
Join host Mitchell Ashely, and CloudBees’ Brian Dawson, DevOps evangelist, and Doug Tidwell, technical marketing director, as they explore and review the CI/CD best practices which serve as your stepping stones to DevOps and a successful Software Delivery Management strategy.
The webinar will cover CI/CD best practices including:
Containers and environment management
Continuous delivery or deployment
Movement from Dev to Ops
By the end of the webinar, you’ll understand the key steps for implementing CI/CD and powering your journey to DevOps and beyond.
Micro Frontend Platforms for Kubernetes



Micro Frontend Platforms for KubernetesEntando Developing with micro frontends offers enterprises many benefits over monolithic frontend development, but MFEs also present challenges.
Micro frontend platforms provide DevOps benefits for large organizations seeking to innovate quickly while managing increasing complexity.
Container security



Container securityAnthony Chow This document discusses container security. It outlines the advantages and disadvantages of containers, including their small footprint, fast provisioning time, and ability to enable effective microservices. However, containers also pose security risks like reduced isolation and potential for cross-container attacks. The document then examines different approaches to container security, including host-based methods using namespaces, control groups, and Linux Security Modules, as well as container-based scanning and third-party security offerings. It provides examples of configuring security controls and evaluating containers for vulnerabilities.
DevSecOps: What Why and How : Blackhat 2019



DevSecOps: What Why and How : Blackhat 2019NotSoSecure Global Services This document discusses DevSecOps, including what it is, why it is needed, and how to implement it. DevSecOps aims to integrate security tools and a security-focused culture into the development lifecycle. It allows security to keep pace with rapid development. The document outlines how to incorporate security checks at various stages of the development pipeline from pre-commit hooks to monitoring in production. It provides examples of tools that can be used and discusses cultural and process aspects of DevSecOps implementation.
Room 1 - 4 - Phạm Tường Chiến & Trần Văn Thắng - Deliver managed Kubernetes C...



Room 1 - 4 - Phạm Tường Chiến & Trần Văn Thắng - Deliver managed Kubernetes C...Vietnam Open Infrastructure User Group Cluster API is a Kubernetes sub-project that provides declarative APIs and tooling to simplify provisioning, upgrading, and operating multiple Kubernetes clusters on any infrastructure. It works by having core Cluster API components along with plugins for different bootstrap, control-plane and infrastructure providers like Openstack, AWS, GCP etc. The presentation discusses Cluster API integration with Openstack, considerations for using it in production including separate internal and public connections and reusing Openstack networking, and proposes a time-saving deployment model leveraging various Cluster API and Gardener projects.
Version control



Version controlvisual28 This document provides an overview of version control systems, including their benefits and basic functions. Version control systems allow recording changes to files over time, allowing users to recall specific file versions. They offer advantages like backup and restoration of files, synchronization across multiple computers, and facilitating collaboration on teams. The document defines common version control terms and best practices for users.
Cloud Migration Checklist | Microsoft Azure Migration



Cloud Migration Checklist | Microsoft Azure MigrationIntellika This checklist walks you through the steps to plan, assess, and begin your cloud migration, and offers resources to help you move to the cloud with Microsoft Azure.
Learn more - https://www.intellika.in/cloud-migration/
Azure key vault



Azure key vaultRahul Nath Azure Key Vault is a cloud service that securely stores keys, secrets, and certificates. It allows storing cryptographic keys and secrets that applications and services use while keeping them safe from unauthorized access. Key Vault uses hardware security modules to encrypt keys and secrets. Typical applications would store secrets like connection strings in Key Vault rather than configuration files for improved security and management. Key Vault integrates with Azure Active Directory for authentication so applications can access secrets securely.
Introduction to appDynamics 



Introduction to appDynamics Siddhanta Rath It contents a basic introduction about AppDynamics tool.It has screenshot to understand how appD monitors your application and database without any flaw.No need to write command in putty or google analytics after using it.
Room 2 - 3 - Nguyễn Hoài Nam & Nguyễn Việt Hùng - Terraform & Pulumi Comparin...



Room 2 - 3 - Nguyễn Hoài Nam & Nguyễn Việt Hùng - Terraform & Pulumi Comparin...Vietnam Open Infrastructure User Group This document compares Terraform and Pulumi infrastructure as code tools. It provides overviews of each tool, including what they are, how they work, and why to use them. For Terraform, it describes it as an IaC tool that defines cloud and on-premise resources in configuration files. For Pulumi, it notes it uses familiar programming languages for IaC. The document also compares key differences like syntax, testing, structuring large projects, and state file troubleshooting. It ends with best practices for both tools.
Introduction to CI/CD



Introduction to CI/CDSteve Mactaggart In this session we will take an introduction look to Continuous Integration and Continuous Delivery workflow.
This is an introduction session to CI/CD and is best for people new to the CI/CD concepts, or looking to brush up on benefits of using these approaches.
* What CI & CD actually are
* What good looks like
* A method for tracking confidence
* The business value from CI/CD
DevSecOps Basics with Azure Pipelines 



DevSecOps Basics with Azure Pipelines Abdul_Mujeeb This document discusses DevSecOps, which integrates security practices into DevOps workflows to securely develop software through continuous integration and delivery. It outlines the basic DevOps process using Azure Pipelines for CI/CD and defines DevSecOps. The document then discusses challenges with security, benefits of DevSecOps for businesses, and common tools used, before concluding with an example DevSecOps demo using Azure Pipelines with security scans at various stages.
Azure DevOps



Azure DevOpsJuan Fabian This document provides information about Azure DevOps and DevOps practices. It discusses how DevOps brings together people, processes, and technology to automate software delivery and provide continuous value to users. It also outlines some key DevOps technologies like continuous integration, continuous delivery, and continuous monitoring. Additionally, the document shares how Azure DevOps can help teams deliver software faster and more reliably through tools for planning, source control, building, testing, and deploying.
ansible why ?



ansible why ?Yashar Esmaildokht This document contains information about the sys/net/sec admin Yashar Esmaildokht, including their contact information and websites. It then provides a brief overview of the open-source automation tool Ansible, describing its main features and uses for configuration management, application deployment, and cloud provisioning. Requirements and versions of Ansible are listed. The document concludes with examples of Ansible concepts including playbooks, tasks, modules, variables, and host inventory organization.
Metasploit framework in Network Security



Metasploit framework in Network SecurityAshok Reddy Medikonda Metasploit is an open source framework for penetration testing that allows users to perform vulnerability scanning, exploit development, and post-exploitation. It provides tools for information gathering, vulnerability scanning, pre-exploitation and post-exploitation tasks. Metasploit has modules for exploits and payloads that are used together, with payloads being the code executed on the target and encoders ensuring payloads reach their destination. The msfconsole interface provides centralized access to Metasploit's options like finding vulnerabilities through open ports and setting the listener, payload, and target for exploitation. Meterpreter is an advanced payload included in Metasploit that has additional features for tasks like keylogging and taking screenshots.
How To Become A Cloud Engineer | Cloud Engineer Salary | Cloud Computing Engi...



How To Become A Cloud Engineer | Cloud Engineer Salary | Cloud Computing Engi...Simplilearn This presentation on how to become a Cloud Computing Engineer will help you understand who is a cloud computing engineer, the different roles within cloud computing, the various steps to become a cloud computing engineer, and the salaries they can expect.
Cloud computing engineers are skilled professionals experienced in cloud computing platforms, programming languages, storage, networking, DevOps, and other cloud services.
Let us now take a look at how you can become a skilled cloud computing engineer.
Simplilearn’s Cloud Architect Master’s Program will build your Amazon Web Services (AWS) and Microsoft Azure cloud expertise from the ground up. You’ll learn to master the architectural principles and services of two of the top cloud platforms, design and deploy highly scalable, fault-tolerant applications and develop skills to transform yourself into an AWS and Azure cloud architect.
Why become a Cloud Architect?
With the increasing focus on cloud computing and infrastructure over the last several years, cloud architects are in great demand worldwide. Many organizations have moved to cloud platforms for better scalability, mobility, and security, and cloud solutions architects are among the highest paid professionals in the IT industry.
According to a study by Goldman Sachs, cloud computing is one of the top three initiatives planned by IT executives as they make cloud infrastructure an integral part of their organizations. According to Forbes, enterprise IT architects with cloud computing expertise are earning a median salary of $137,957.
Learn more at https://www.simplilearn.com/cloud-solutions-architect-masters-program-training
Software Composition Analysis Deep Dive



Software Composition Analysis Deep DiveUlisses Albuquerque Software composition analysis (SCA) is often sold as an easy win for application security, but ensuring that we have full visibility on the vulnerable components is a lot more challenging that it looks. The remediation costs can also stack up pretty quickly as we try to get rid of deeply nested vulnerable transitive dependencies.
Containers and Docker



Containers and DockerDamian T. Gordon This document discusses containers and Docker. It begins by explaining that cloud infrastructures comprise virtual resources like compute and storage nodes that are administered through software. Docker is introduced as a standard way to package code and dependencies into portable containers that can run anywhere. Key benefits of Docker include increased efficiency, consistency, and security compared to traditional virtual machines. Some weaknesses are that Docker may not be suitable for all applications and large container management can be difficult. Interesting uses of Docker include malware analysis sandboxes, isolating Skype sessions, and managing Raspberry Pi clusters with Docker Swarm.
Application Security Guide for Beginners 



Application Security Guide for Beginners Checkmarx The document provides an overview of application security concepts and terms for beginners. It defines key terms like the software development lifecycle (SDLC) and secure SDLC, which incorporates security best practices into each stage of development. It also describes common application security testing methods like static application security testing (SAST) and dynamic application security testing (DAST). Finally, it outlines some common application security threats like SQL injection, cross-site scripting, and cross-site request forgery and their potential impacts.
Implementing an Application Security Pipeline in Jenkins



Implementing an Application Security Pipeline in JenkinsSuman Sourav Performing continuous security testing in a DevOps environment with short release cycles and a continuous delivery pipeline is a big challenge and the traditional secure SDLC model fails to deliver the desired results. DevOps understand the process of built, test and deploy. They have largely automated this process in a delivery pipeline, they deploy to production multiple times per day but the big challenge is how can they do this securely?
This session will focus on a strategy to build an application security pipeline in Jenkins, challenges and possible solutions, also how existing application security solutions (SAST, DAST, IAST, OpenSource Libraries Analysis) are playing a key role in growing the relationship between security and DevOps.
More Related Content
What's hot (20)
Apache Maven 3



Apache Maven 3Maxime Gréau Slides de présentation du livre "Apache Maven - Maîtrisez l'infrastructure d'un projet Java EE"
CI/CD Best Practices for Your DevOps Journey



CI/CD Best Practices for Your DevOps JourneyDevOps.com The journey to realizing DevOps in any organization is fraught with a number of obstacles for developers and other stakeholders. These challenges are often caused by key CI/CD practices being misunderstood, partially implemented or even completely skipped. Now, as the industry positions itself to build on DevOps practices with a Software Delivery Management strategy, it’s more important than ever that we implement CI/CD best practices, and prepare for the future.
Join host Mitchell Ashely, and CloudBees’ Brian Dawson, DevOps evangelist, and Doug Tidwell, technical marketing director, as they explore and review the CI/CD best practices which serve as your stepping stones to DevOps and a successful Software Delivery Management strategy.
The webinar will cover CI/CD best practices including:
Containers and environment management
Continuous delivery or deployment
Movement from Dev to Ops
By the end of the webinar, you’ll understand the key steps for implementing CI/CD and powering your journey to DevOps and beyond.
Micro Frontend Platforms for Kubernetes



Micro Frontend Platforms for KubernetesEntando Developing with micro frontends offers enterprises many benefits over monolithic frontend development, but MFEs also present challenges.
Micro frontend platforms provide DevOps benefits for large organizations seeking to innovate quickly while managing increasing complexity.
Container security



Container securityAnthony Chow This document discusses container security. It outlines the advantages and disadvantages of containers, including their small footprint, fast provisioning time, and ability to enable effective microservices. However, containers also pose security risks like reduced isolation and potential for cross-container attacks. The document then examines different approaches to container security, including host-based methods using namespaces, control groups, and Linux Security Modules, as well as container-based scanning and third-party security offerings. It provides examples of configuring security controls and evaluating containers for vulnerabilities.
DevSecOps: What Why and How : Blackhat 2019



DevSecOps: What Why and How : Blackhat 2019NotSoSecure Global Services This document discusses DevSecOps, including what it is, why it is needed, and how to implement it. DevSecOps aims to integrate security tools and a security-focused culture into the development lifecycle. It allows security to keep pace with rapid development. The document outlines how to incorporate security checks at various stages of the development pipeline from pre-commit hooks to monitoring in production. It provides examples of tools that can be used and discusses cultural and process aspects of DevSecOps implementation.
Room 1 - 4 - Phạm Tường Chiến & Trần Văn Thắng - Deliver managed Kubernetes C...



Room 1 - 4 - Phạm Tường Chiến & Trần Văn Thắng - Deliver managed Kubernetes C...Vietnam Open Infrastructure User Group Cluster API is a Kubernetes sub-project that provides declarative APIs and tooling to simplify provisioning, upgrading, and operating multiple Kubernetes clusters on any infrastructure. It works by having core Cluster API components along with plugins for different bootstrap, control-plane and infrastructure providers like Openstack, AWS, GCP etc. The presentation discusses Cluster API integration with Openstack, considerations for using it in production including separate internal and public connections and reusing Openstack networking, and proposes a time-saving deployment model leveraging various Cluster API and Gardener projects.
Version control



Version controlvisual28 This document provides an overview of version control systems, including their benefits and basic functions. Version control systems allow recording changes to files over time, allowing users to recall specific file versions. They offer advantages like backup and restoration of files, synchronization across multiple computers, and facilitating collaboration on teams. The document defines common version control terms and best practices for users.
Cloud Migration Checklist | Microsoft Azure Migration



Cloud Migration Checklist | Microsoft Azure MigrationIntellika This checklist walks you through the steps to plan, assess, and begin your cloud migration, and offers resources to help you move to the cloud with Microsoft Azure.
Learn more - https://www.intellika.in/cloud-migration/
Azure key vault



Azure key vaultRahul Nath Azure Key Vault is a cloud service that securely stores keys, secrets, and certificates. It allows storing cryptographic keys and secrets that applications and services use while keeping them safe from unauthorized access. Key Vault uses hardware security modules to encrypt keys and secrets. Typical applications would store secrets like connection strings in Key Vault rather than configuration files for improved security and management. Key Vault integrates with Azure Active Directory for authentication so applications can access secrets securely.
Introduction to appDynamics 



Introduction to appDynamics Siddhanta Rath It contents a basic introduction about AppDynamics tool.It has screenshot to understand how appD monitors your application and database without any flaw.No need to write command in putty or google analytics after using it.
Room 2 - 3 - Nguyễn Hoài Nam & Nguyễn Việt Hùng - Terraform & Pulumi Comparin...



Room 2 - 3 - Nguyễn Hoài Nam & Nguyễn Việt Hùng - Terraform & Pulumi Comparin...Vietnam Open Infrastructure User Group This document compares Terraform and Pulumi infrastructure as code tools. It provides overviews of each tool, including what they are, how they work, and why to use them. For Terraform, it describes it as an IaC tool that defines cloud and on-premise resources in configuration files. For Pulumi, it notes it uses familiar programming languages for IaC. The document also compares key differences like syntax, testing, structuring large projects, and state file troubleshooting. It ends with best practices for both tools.
Introduction to CI/CD



Introduction to CI/CDSteve Mactaggart In this session we will take an introduction look to Continuous Integration and Continuous Delivery workflow.
This is an introduction session to CI/CD and is best for people new to the CI/CD concepts, or looking to brush up on benefits of using these approaches.
* What CI & CD actually are
* What good looks like
* A method for tracking confidence
* The business value from CI/CD
DevSecOps Basics with Azure Pipelines 



DevSecOps Basics with Azure Pipelines Abdul_Mujeeb This document discusses DevSecOps, which integrates security practices into DevOps workflows to securely develop software through continuous integration and delivery. It outlines the basic DevOps process using Azure Pipelines for CI/CD and defines DevSecOps. The document then discusses challenges with security, benefits of DevSecOps for businesses, and common tools used, before concluding with an example DevSecOps demo using Azure Pipelines with security scans at various stages.
Azure DevOps



Azure DevOpsJuan Fabian This document provides information about Azure DevOps and DevOps practices. It discusses how DevOps brings together people, processes, and technology to automate software delivery and provide continuous value to users. It also outlines some key DevOps technologies like continuous integration, continuous delivery, and continuous monitoring. Additionally, the document shares how Azure DevOps can help teams deliver software faster and more reliably through tools for planning, source control, building, testing, and deploying.
ansible why ?



ansible why ?Yashar Esmaildokht This document contains information about the sys/net/sec admin Yashar Esmaildokht, including their contact information and websites. It then provides a brief overview of the open-source automation tool Ansible, describing its main features and uses for configuration management, application deployment, and cloud provisioning. Requirements and versions of Ansible are listed. The document concludes with examples of Ansible concepts including playbooks, tasks, modules, variables, and host inventory organization.
Metasploit framework in Network Security



Metasploit framework in Network SecurityAshok Reddy Medikonda Metasploit is an open source framework for penetration testing that allows users to perform vulnerability scanning, exploit development, and post-exploitation. It provides tools for information gathering, vulnerability scanning, pre-exploitation and post-exploitation tasks. Metasploit has modules for exploits and payloads that are used together, with payloads being the code executed on the target and encoders ensuring payloads reach their destination. The msfconsole interface provides centralized access to Metasploit's options like finding vulnerabilities through open ports and setting the listener, payload, and target for exploitation. Meterpreter is an advanced payload included in Metasploit that has additional features for tasks like keylogging and taking screenshots.
How To Become A Cloud Engineer | Cloud Engineer Salary | Cloud Computing Engi...



How To Become A Cloud Engineer | Cloud Engineer Salary | Cloud Computing Engi...Simplilearn This presentation on how to become a Cloud Computing Engineer will help you understand who is a cloud computing engineer, the different roles within cloud computing, the various steps to become a cloud computing engineer, and the salaries they can expect.
Cloud computing engineers are skilled professionals experienced in cloud computing platforms, programming languages, storage, networking, DevOps, and other cloud services.
Let us now take a look at how you can become a skilled cloud computing engineer.
Simplilearn’s Cloud Architect Master’s Program will build your Amazon Web Services (AWS) and Microsoft Azure cloud expertise from the ground up. You’ll learn to master the architectural principles and services of two of the top cloud platforms, design and deploy highly scalable, fault-tolerant applications and develop skills to transform yourself into an AWS and Azure cloud architect.
Why become a Cloud Architect?
With the increasing focus on cloud computing and infrastructure over the last several years, cloud architects are in great demand worldwide. Many organizations have moved to cloud platforms for better scalability, mobility, and security, and cloud solutions architects are among the highest paid professionals in the IT industry.
According to a study by Goldman Sachs, cloud computing is one of the top three initiatives planned by IT executives as they make cloud infrastructure an integral part of their organizations. According to Forbes, enterprise IT architects with cloud computing expertise are earning a median salary of $137,957.
Learn more at https://www.simplilearn.com/cloud-solutions-architect-masters-program-training
Software Composition Analysis Deep Dive



Software Composition Analysis Deep DiveUlisses Albuquerque Software composition analysis (SCA) is often sold as an easy win for application security, but ensuring that we have full visibility on the vulnerable components is a lot more challenging that it looks. The remediation costs can also stack up pretty quickly as we try to get rid of deeply nested vulnerable transitive dependencies.
Containers and Docker



Containers and DockerDamian T. Gordon This document discusses containers and Docker. It begins by explaining that cloud infrastructures comprise virtual resources like compute and storage nodes that are administered through software. Docker is introduced as a standard way to package code and dependencies into portable containers that can run anywhere. Key benefits of Docker include increased efficiency, consistency, and security compared to traditional virtual machines. Some weaknesses are that Docker may not be suitable for all applications and large container management can be difficult. Interesting uses of Docker include malware analysis sandboxes, isolating Skype sessions, and managing Raspberry Pi clusters with Docker Swarm.
Room 1 - 4 - Phạm Tường Chiến & Trần Văn Thắng - Deliver managed Kubernetes C...



Room 1 - 4 - Phạm Tường Chiến & Trần Văn Thắng - Deliver managed Kubernetes C...Vietnam Open Infrastructure User Group
Room 2 - 3 - Nguyễn Hoài Nam & Nguyễn Việt Hùng - Terraform & Pulumi Comparin...



Room 2 - 3 - Nguyễn Hoài Nam & Nguyễn Việt Hùng - Terraform & Pulumi Comparin...Vietnam Open Infrastructure User Group
Viewers also liked (13)
Application Security Guide for Beginners 



Application Security Guide for Beginners Checkmarx The document provides an overview of application security concepts and terms for beginners. It defines key terms like the software development lifecycle (SDLC) and secure SDLC, which incorporates security best practices into each stage of development. It also describes common application security testing methods like static application security testing (SAST) and dynamic application security testing (DAST). Finally, it outlines some common application security threats like SQL injection, cross-site scripting, and cross-site request forgery and their potential impacts.
Implementing an Application Security Pipeline in Jenkins



Implementing an Application Security Pipeline in JenkinsSuman Sourav Performing continuous security testing in a DevOps environment with short release cycles and a continuous delivery pipeline is a big challenge and the traditional secure SDLC model fails to deliver the desired results. DevOps understand the process of built, test and deploy. They have largely automated this process in a delivery pipeline, they deploy to production multiple times per day but the big challenge is how can they do this securely?
This session will focus on a strategy to build an application security pipeline in Jenkins, challenges and possible solutions, also how existing application security solutions (SAST, DAST, IAST, OpenSource Libraries Analysis) are playing a key role in growing the relationship between security and DevOps.
DevSecOps Singapore 2017 - Security in the Delivery Pipeline



DevSecOps Singapore 2017 - Security in the Delivery PipelineJames Wickett This talk is from DevSecOps Singapore, June 29th, 2017.
Continuous Delivery and Security are traveling companions if we want them to be. This talk highlights how to make that happen in three areas of the delivery pipeline.
Devops security-An Insight into Secure-SDLC



Devops security-An Insight into Secure-SDLCSuman Sourav The integration of Security into DevOps is already happening out of necessity. DevOps is a powerful paradigm shift and companies often don’t understand how security fits. Aim of this session is to give an overview of DevOps security and How security can be integrated and automated into each phases of software development life-cycle.
Security Tests as Part of CI - Nir Koren, SAP - DevOpsDays Tel Aviv 2015



Security Tests as Part of CI - Nir Koren, SAP - DevOpsDays Tel Aviv 2015DevOpsDays Tel Aviv This document summarizes a presentation on integrating security testing into continuous integration processes. It discusses the benefits of automating security scans as part of CI/CD pipelines, including providing fast feedback to developers, frequent scans to catch vulnerabilities early, and transparency through automated reporting and notifications. It also provides examples of implementing security testing tools like IBM AppScan, HP Fortify, and CheckMarx in Jenkins pipelines.
A Successful SAST Tool Implementation



A Successful SAST Tool ImplementationCheckmarx The document discusses implementing a static application security testing (SAST) tool. It recommends starting with a central scanning model where a security team scans code and reports vulnerabilities. Over time, the organization can transition to a full software development lifecycle model where developers use the tool during coding. Key factors for a successful implementation include choosing the right scanning model, training users, and establishing processes for fixing and verifying issues. The document also provides tips on maximizing returns and reducing costs such as licensing the tool granularly and keeping deployment and training short.
DevSecOps in Baby Steps



DevSecOps in Baby StepsPriyanka Aash The document discusses moving from traditional security practices to a DevSecOps model where security is integrated into the development lifecycle. It encourages making DevOps the security team's job, hardening the development toolchain, planning security epics and user stories, and sprinting to automate security practices. Specific examples provided include building an AWS Lambda function to respond to CloudTrail events and using AWS CodeDeploy for security tasks like imaging instance memory.
Bringing Security Testing to Development: How to Enable Developers to Act as ...



Bringing Security Testing to Development: How to Enable Developers to Act as ...Achim D. Brucker Security testing is an important part of any security development life-cycle (SDLC) and, thus, should be a part of any software development life-cycle.
We will present SAP's Security Testing Strategy that enables developers to find security vulnerabilities early by applying a variety of different security testing methods and tools. We explain the motivation behind it, how we enable global development teams to implement the strategy, across different SDLCs and report on our experiences.
Application Security Management with ThreadFix



Application Security Management with ThreadFixVirtual Forge How to efficiently identify and remediate critical vulnerabilities in SAP and other Business Applications.
Vulnerabilities in individual applications harbor enormous risks for companies because they can be exploited by hackers to gain access to the corporate network and critical IT infrastructure such as SAP systems. An effective approach to application security management therefore must take the entire application portfolio of a company into consideration. It must evaluate critical vulnerabilities uniform and must be capable to track their remediation, regardless of the programming language or the development environment used.
This approach is facilitated by ThreadFix, an open source software offered by Denim Group. In our webinar APPLICATION SECURITY MANAGEMENT we show you:
- How you can scan your SAP and other business applications automatically for critical vulnerabilities
- How you can easily track the remediation of vulnerabilities with ThreadFix
- How you can accomplish important security and quality milestones more easily in your projects
DEVSECOPS: Coding DevSecOps journey



DEVSECOPS: Coding DevSecOps journeyJason Suttie In the world of DevSecOps as you may predict we have three teams working together. Development, the Security team and Operations.
The “Sec” of DevSecOps introduces changes into the following:
• Engineering
• Operations
• Data Science
• Compliance
Graph Visualization - OWASP NYC Chapter



Graph Visualization - OWASP NYC ChapterCheckmarx The presentation that was given by Maty Siman, Checkmarx's CTO during the OWASP NYC/NJ local chapter meeting held on the 11th of April 2013.
[ITAS.VN]CxSuite Enterprise Edition![[ITAS.VN]CxSuite Enterprise Edition](https://cdn.slidesharecdn.com/ss_thumbnails/itascxsuiteenterpriseedition-120130231915-phpapp01-thumbnail.jpg?width=560&fit=bounds)
![[ITAS.VN]CxSuite Enterprise Edition](https://cdn.slidesharecdn.com/ss_thumbnails/itascxsuiteenterpriseedition-120130231915-phpapp01-thumbnail.jpg?width=560&fit=bounds)
![[ITAS.VN]CxSuite Enterprise Edition](https://cdn.slidesharecdn.com/ss_thumbnails/itascxsuiteenterpriseedition-120130231915-phpapp01-thumbnail.jpg?width=560&fit=bounds)
![[ITAS.VN]CxSuite Enterprise Edition](https://cdn.slidesharecdn.com/ss_thumbnails/itascxsuiteenterpriseedition-120130231915-phpapp01-thumbnail.jpg?width=560&fit=bounds)
[ITAS.VN]CxSuite Enterprise EditionITAS VIETNAM CxSuite is a source code analysis solution that allows organizations to identify, track, and fix security flaws in source code. It provides flexibility in supporting various programming languages, platforms, and vulnerability categories. CxSuite integrates into the software development lifecycle to help organizations address the challenge of securing code while reducing time and costs. It uses a virtual compiler to scan unbuilt code and pinpoints vulnerabilities without requiring a real compiler.
Ad
Similar to DevOps & Security: Here & Now (20)
Dev opsandsecurity owasp



Dev opsandsecurity owaspHelen Bravo The document discusses integrating security practices within DevOps environments. It begins by introducing DevOps and noting that traditional security controls like penetration testing and code analysis are too slow for continuous deployment. It then outlines a three step approach to DevOps security: 1) Plan security requirements upfront, 2) Engage developers in security, and 3) Automate security checks into the continuous integration/deployment pipeline. The key takeaways are to plan security thoroughly, involve developers, and integrate security testing automatically into the build process.
You Build It, You Secure It: Introduction to DevSecOps



You Build It, You Secure It: Introduction to DevSecOpsSumo Logic In this presentation, DevOps and DevSecOps expert John Willis dives into how to implement DevSecOps, including:
- Why traditional DevOps has shifted and what this shift means
- How DevSecOps can change the game for your team
- Tips and tricks for getting DevSecOps started within your organization
Secure DevOPS Implementation Guidance



Secure DevOPS Implementation GuidanceTej Luthra Awareness and Guide to a Practical Implementation.
Discover how to automate security testing, and ensure every bit of code is scanned before it leaves the developer’s hands
https://bsidesdc2018.busyconf.com/schedule#day_5acff470ec4a15f24e000036
Scale security for a dollar or less



Scale security for a dollar or lessMohammed A. Imran Security is tough and is even tougher to do, in complex environments with lots of dependencies and monolithic architecture. With emergence of Microservice architecture, security has become a bit easier however it introduces its own set of security challenges. This talk will showcase how we can leverage DevSecOps techniques to secure APIs/Microservices using free and open source software. We will also discuss how emerging technologies like Docker, Kubernetes, Clair, ansible, consul, vault, etc., can be used to scale/strengthen the security program for free.
More details here - https://www.practical-devsecops.com/
DevSecOps 101



DevSecOps 101Narudom Roongsiriwong, CISSP Security teams are often seen as roadblocks to rapid development or operations implementations, slowing down production code pushes. As a result, security organizations will likely have to change so they can fully support and facilitate cloud operations.
This presentation will explain how DevOps and information security can co-exist through the application of a new approach referred to as DevSecOps.
AppSec How-To: Achieving Security in DevOps



AppSec How-To: Achieving Security in DevOpsCheckmarx How do you integrate security within a Continuous Deployment (CD) environment, where every 5 minutes a feature, an enhancement, or a bug fix needs to be released? Find out in this Checkmarx How-To Paper.
Strengthen and Scale Security Using DevSecOps - OWASP Indonesia



Strengthen and Scale Security Using DevSecOps - OWASP IndonesiaMohammed A. Imran Strengthen and Scale Security Using DevSecOps - OWASP Indonesia
More details here - https://www.practical-devsecops.com/
Strengthen and Scale Security for a dollar or less



Strengthen and Scale Security for a dollar or lessMohammed A. Imran Strengthen and Scale Security for a dollar or less
More details here - https://www.practical-devsecops.com/
AddingtheSecToDevOpsBSides (1).pptx for Bsides Nairobi 22 with Joylynn Kirui



AddingtheSecToDevOpsBSides (1).pptx for Bsides Nairobi 22 with Joylynn Kiruiellan12 Presentation on DevSecOps for BSides Nairobi
DevSecOps and Drupal: Securing your applications in a modern IT landscape



DevSecOps and Drupal: Securing your applications in a modern IT landscapeWill Hall Securing applications in a cloud environment can be difficult. This presentation discusses the automate and changes to be able to embed security into you application pipelines and deployments.
Introduction to DevSecOps



Introduction to DevSecOpsabhimanyubhogwan Link to Youtube video: https://youtu.be/-awH_CC4DLo
You can contact me at [email protected]
My linkdin id : https://www.linkedin.com/in/abhimanyu-bhogwan-cissp-ctprp-98978437/
Basic Introduction to DevSecOps concept
Why What and How for DevSecOps
Basic intro for Threat Modeling
Basic Intro for Security Champions
3 pillars of DevSecOps
6 important components of a DevSecOps approach
DevSecOps Security Best Practices
How to integrate security in CI/CD pipeline
Secure DevOps - Evolution or Revolution?



Secure DevOps - Evolution or Revolution?Security Innovation DevOps continues to be a buzzword in the software development and operations world, but is it really a paradigm shift? It depends on what lens you view it through.
Roman Garber, an active software security engineering and software team lead thinks so. Ed Adams, Security Innovation CEO, a 20-year software quality veteran and former mechanical engineer, curmudgeonly disagrees.
DevSecOps : an Introduction



DevSecOps : an IntroductionPrashanth B. P. DevSecOps is a cultural change that incorporates security practices into software development through people, processes, and technologies. It aims to address security without slowing delivery by establishing secure-by-design approaches, automating security tools and processes, and promoting collaboration between developers, security engineers, and operations teams. As software and connected devices continue proliferating, application security must be a central focus of the development lifecycle through a DevSecOps methodology.
You build it - Cyber Chicago Keynote



You build it - Cyber Chicago KeynoteJohn Willis This document provides an introduction to DevSecOps practices. It discusses how DevOps aims to accelerate software delivery through practices like continuous delivery, automation, and removing silos. It notes that security has become the new bottleneck in software delivery. DevSecOps aims to integrate security practices and tools into the software development pipeline to shift security left. This allows security to be addressed continuously throughout development and deployment rather than as a separate phase. The document outlines some DevSecOps basics like security training, threat modeling, and integrating static code analysis and vulnerability scanning into the CI/CD pipeline.
DevSecCon KeyNote London 2015



DevSecCon KeyNote London 2015Shannon Lietz This document discusses the evolution of security practices to enable secure innovation at speed and scale through a DevSecOps approach. It outlines how traditional security controls can be transformed into self-aware, self-reporting components that integrate seamlessly into the DevOps pipeline. Specific examples are provided for how perimeter testing, configuration management, encrypting sensitive data, access management, and multi-factor authentication can move from annual certifications to continuous monitoring and enforcement. The document advocates for collaboration, experimentation, and a focus on simplicity and automation to evolve security practices for DevOps.
DevSecCon Keynote



DevSecCon KeynoteShannon Lietz DevSecOps is a new way to deliver security as part of the Software Supply Chain. It supports a built-in process and faster security feedback loop for DevOps teams.
DevOps or DevSecOps



DevOps or DevSecOpsMichelangelo van Dam In 2009 Patrick Dubois coined the term "DevOps" when he organised the first "DevOpsDays" In Ghent, Belgium. Since then the term has become a term to explain the collaboration between all organisational stakeholders in IT projects (developers, operations, QA, marketing, security, legal, …) to deliver high quality, reliable solutions where issues are tackled early on in the value stream.
But reality shows that many businesses that implement "DevOps" are actually talking about a collaboration between development, QA and operations (DQO). Solutions are being provided but lack the security and/or legal regulations causing hard-to-fix problems in production environments.
In this talk I will explain how the original idea of Patrick to include all stakeholders got reduced to development, QA and operations and why it's so difficult to apply security or compliance improvements in this model. I will also talk about ways to make the DQO model welcoming for security experts and legal teams and why "DevSecOps" is now the term to be used to ensure security is no longer omitted from the value process.
Finally we'll have a vote if we keep the term "DevOps" as an all-inclusive representation for all stakeholders or if we need to start using "DevSecOps" to ensure the business understands can no longer ignore the importance of security.
Introduction to DevSecOps OWASP Ahmedabad



Introduction to DevSecOps OWASP Ahmedabadkunwaratul hax0r Here I have shared a basic introduction about DevOps and DevSecOps. What approach a organization should follow, benefits of CI/CD Pipelines etc.
Why Security Engineer Need Shift-Left to DevSecOps?



Why Security Engineer Need Shift-Left to DevSecOps?Najib Radzuan In the fusion between DevOps and DevSecOps, the pace and agility of the DevSecOps approach made AppSec and InfoSec were a little left behind. The DevOps squad topology does not involve any of the organization's AppSec and InfoSec Engineer. Many DevOps team are also not included them since they lack the information on how to manage and configure DevOps CI / CD pipelines and DevSecOps approaches. There's no shortage of talent — you probably don't have a mission worth getting out of bed or a culture that fosters continuous learning such DevSecOps skill and tools and growth where people feel psychologically safe. Besides, there is no shortage of skills — most have a poor understanding of what they need to be successful or the skills that need to leverage to improve their security posture.
Ad
More from Checkmarx (9)
The Web AppSec How-To: The Defender's Toolbox



The Web AppSec How-To: The Defender's ToolboxCheckmarx Web application security has made headline news in the past few years. In this article, we review the various Web application security tools and highlight important decision factors to help you choose the application security technology best suited for your environment.
10 Tips to Keep Your Software a Step Ahead of the Hackers



10 Tips to Keep Your Software a Step Ahead of the HackersCheckmarx Checkmarx provides software security solutions to help organizations introduce security into their software development lifecycle. Their product allows developers and auditors to easily scan code for security vulnerabilities in major coding languages. The document provides 10 tips for keeping software secure, such as performing threat modeling, scrutinizing open source components and frameworks, treating security as part of the development process, and using whitelist input validation. To learn more about Checkmarx's products and services, contact their team.
The 5 Biggest Benefits of Source Code Analysis



The 5 Biggest Benefits of Source Code AnalysisCheckmarx Static Code Analysis is the technique of automatically analyzing the application’s source and binary code to find security vulnerabilities.
Two categories exist in this realm:
Binary – or byte- code analysis (BCA) analyzes the binary/ byte code that is created by the compiler.
Source code analysis (SCA) analyzes the actual source code of the program without the requirement of retrieving all code for a compilation.
Both offerings promise to deliver security and the requirement of incorporating security into the software development lifecycle (SDLC). Faced with the BCA vs SCA dilemma, which should you choose?
A Platform for Application Risk Intelligence



A Platform for Application Risk IntelligenceCheckmarx Using Source Code Understanding as a Risk Barometer:
Source Code Analysis technologies have significantly evolved in recent years – making improvements in precision and accuracy with the introduction of new analysis techniques like flow analysis. This article describes this evolution and how the most advanced capabilities available today like query-based analysis and Knowledge Discovery can be leveraged to create a platform for Application Risk Intelligence (ARI) to help implement a proactive security program.
How Virtual Compilation Transforms Static Code Analysis



How Virtual Compilation Transforms Static Code AnalysisCheckmarx Many assume that code analysis requires code compilation as a prerequisite. Today, all major static code analyzers are built on this assumption and only scan post compilation - requiring buildable code. The reliance on compilation has major and negative implications for all stake holders: developers, auditors, CISOs, as well as the organizations that hope to build a secure development lifecycle (SDLC). Historically, static code analysis required a complete and buildable project to run against, which made the logical place to do the analysis at the build server and in-line with the entire build process. The “buildable” requirement also forced the execution of the scan nearer the end of the development process, making security repairs to code more expensive and greatly reducing any benefits.
Source Code vs. Binary Code Analysis



Source Code vs. Binary Code AnalysisCheckmarx Secure software development has become a priority for all organizations whether they build their own software or outsource. And code analysis is becoming the de facto choice to introduce secure development as well as measure inherent software risk.
The App Sec How-To: Choosing a SAST Tool



The App Sec How-To: Choosing a SAST ToolCheckmarx Given the wide range of Source Code Analysis Tools, security professionals, auditors and developers alike are faced with the same developers alike are faced with the question: What is the best way to assess a Static Application Security Testing (SAST) tool for deployment?
Choosing the right tool requires different considerations during each stage of the SAST tool evaluation process.
The Security State of The Most Popular WordPress Plug-Ins



The Security State of The Most Popular WordPress Plug-InsCheckmarx Checkmarx's research lab identified that more than 20% of the 50 most popular WordPress pluins were vulnerable to common Web attacks including SQL Injection, and that 70% of e-commerce plugins contained vulnerabilities.
10 Steps To Secure Agile Development



10 Steps To Secure Agile DevelopmentCheckmarx In Agile’s fast-paced environment with frequent releases,
security reviews and testing can sound like an impediment to success. How can you keep up with Agile development's demands of continuous integration and deployment without
abandoning security best practices? These 10 steps will help you get the best of both worlds.
Recently uploaded (20)
Floods in Valencia: Two FME-Powered Stories of Data Resilience



Floods in Valencia: Two FME-Powered Stories of Data ResilienceSafe Software In October 2024, the Spanish region of Valencia faced severe flooding that underscored the critical need for accessible and actionable data. This presentation will explore two innovative use cases where FME facilitated data integration and availability during the crisis. The first case demonstrates how FME was used to process and convert satellite imagery and other geospatial data into formats tailored for rapid analysis by emergency teams. The second case delves into making human mobility data—collected from mobile phone signals—accessible as source-destination matrices, offering key insights into population movements during and after the flooding. These stories highlight how FME's powerful capabilities can bridge the gap between raw data and decision-making, fostering resilience and preparedness in the face of natural disasters. Attendees will gain practical insights into how FME can support crisis management and urban planning in a changing climate.
Kubernetes Security Act Now Before It’s Too Late



Kubernetes Security Act Now Before It’s Too LateMichael Furman In today's cloud-native landscape, Kubernetes has become the de facto standard for orchestrating containerized applications, but its inherent complexity introduces unique security challenges. Are you one YAML away from disaster?
This presentation, "Kubernetes Security: Act Now Before It’s Too Late," is your essential guide to understanding and mitigating the critical security risks within your Kubernetes environments. This presentation dives deep into the OWASP Kubernetes Top Ten, providing actionable insights to harden your clusters.
We will cover:
The fundamental architecture of Kubernetes and why its security is paramount.
In-depth strategies for protecting your Kubernetes Control Plane, including kube-apiserver and etcd.
Crucial best practices for securing your workloads and nodes, covering topics like privileged containers, root filesystem security, and the essential role of Pod Security Admission.
Don't wait for a breach. Learn how to identify, prevent, and respond to Kubernetes security threats effectively.
It's time to act now before it's too late!
Oracle Cloud Infrastructure AI Foundations



Oracle Cloud Infrastructure AI FoundationsVICTOR MAESTRE RAMIREZ Oracle Cloud Infrastructure AI Foundations
June Patch Tuesday



June Patch TuesdayIvanti Ivanti’s Patch Tuesday breakdown goes beyond patching your applications and brings you the intelligence and guidance needed to prioritize where to focus your attention first. Catch early analysis on our Ivanti blog, then join industry expert Chris Goettl for the Patch Tuesday Webinar Event. There we’ll do a deep dive into each of the bulletins and give guidance on the risks associated with the newly-identified vulnerabilities.
National Fuels Treatments Initiative: Building a Seamless Map of Hazardous Fu...



National Fuels Treatments Initiative: Building a Seamless Map of Hazardous Fu...Safe Software The National Fuels Treatments Initiative (NFT) is transforming wildfire mitigation by creating a standardized map of nationwide fuels treatment locations across all land ownerships in the United States. While existing state and federal systems capture this data in diverse formats, NFT bridges these gaps, delivering the first truly integrated national view. This dataset will be used to measure the implementation of the National Cohesive Wildland Strategy and demonstrate the positive impact of collective investments in hazardous fuels reduction nationwide. In Phase 1, we developed an ETL pipeline template in FME Form, leveraging a schema-agnostic workflow with dynamic feature handling intended for fast roll-out and light maintenance. This was key as the initiative scaled from a few to over fifty contributors nationwide. By directly pulling from agency data stores, oftentimes ArcGIS Feature Services, NFT preserves existing structures, minimizing preparation needs. External mapping tables ensure consistent attribute and domain alignment, while robust change detection processes keep data current and actionable. Now in Phase 2, we’re migrating pipelines to FME Flow to take advantage of advanced scheduling, monitoring dashboards, and automated notifications to streamline operations. Join us to explore how this initiative exemplifies the power of technology, blending FME, ArcGIS Online, and AWS to solve a national business problem with a scalable, automated solution.
Providing an OGC API Processes REST Interface for FME Flow



Providing an OGC API Processes REST Interface for FME FlowSafe Software This presentation will showcase an adapter for FME Flow that provides REST endpoints for FME Workspaces following the OGC API Processes specification. The implementation delivers robust, user-friendly API endpoints, including standardized methods for parameter provision. Additionally, it enhances security and user management by supporting OAuth2 authentication. Join us to discover how these advancements can elevate your enterprise integration workflows and ensure seamless, secure interactions with FME Flow.
Trends Artificial Intelligence - Mary Meeker



Trends Artificial Intelligence - Mary MeekerClive Dickens Mary Meeker’s 2024 AI report highlights a seismic shift in productivity, creativity, and business value driven by generative AI. She charts the rapid adoption of tools like ChatGPT and Midjourney, likening today’s moment to the dawn of the internet. The report emphasizes AI’s impact on knowledge work, software development, and personalized services—while also cautioning about data quality, ethical use, and the human-AI partnership. In short, Meeker sees AI as a transformative force accelerating innovation and redefining how we live and work.
Secure Access with Azure Active Directory



Secure Access with Azure Active DirectoryVICTOR MAESTRE RAMIREZ Secure Access with Azure Active Directory
Mastering AI Workflows with FME - Peak of Data & AI 2025



Mastering AI Workflows with FME - Peak of Data & AI 2025Safe Software Harness the full potential of AI with FME: From creating high-quality training data to optimizing models and utilizing results, FME supports every step of your AI workflow. Seamlessly integrate a wide range of models, including those for data enhancement, forecasting, image and object recognition, and large language models. Customize AI models to meet your exact needs with FME’s powerful tools for training, optimization, and seamless integration
Enabling BIM / GIS integrations with Other Systems with FME



Enabling BIM / GIS integrations with Other Systems with FMESafe Software Jacobs has successfully utilized FME to tackle the complexities of integrating diverse data sources in a confidential $1 billion campus improvement project. The project aimed to create a comprehensive digital twin by merging Building Information Modeling (BIM) data, Construction Operations Building Information Exchange (COBie) data, and various other data sources into a unified Geographic Information System (GIS) platform. The challenge lay in the disparate nature of these data sources, which were siloed and incompatible with each other, hindering efficient data management and decision-making processes.
To address this, Jacobs leveraged FME to automate the extraction, transformation, and loading (ETL) of data between ArcGIS Indoors and IBM Maximo. This process ensured accurate transfer of maintainable asset and work order data, creating a comprehensive 2D and 3D representation of the campus for Facility Management. FME's server capabilities enabled real-time updates and synchronization between ArcGIS Indoors and Maximo, facilitating automatic updates of asset information and work orders. Additionally, Survey123 forms allowed field personnel to capture and submit data directly from their mobile devices, triggering FME workflows via webhooks for real-time data updates. This seamless integration has significantly enhanced data management, improved decision-making processes, and ensured data consistency across the project lifecycle.
How Advanced Environmental Detection Is Revolutionizing Oil & Gas Safety.pdf



How Advanced Environmental Detection Is Revolutionizing Oil & Gas Safety.pdfRejig Digital Unlock the future of oil & gas safety with advanced environmental detection technologies that transform hazard monitoring and risk management. This presentation explores cutting-edge innovations that enhance workplace safety, protect critical assets, and ensure regulatory compliance in high-risk environments.
🔍 What You’ll Learn:
✅ How advanced sensors detect environmental threats in real-time for proactive hazard prevention
🔧 Integration of IoT and AI to enable rapid response and minimize incident impact
📡 Enhancing workforce protection through continuous monitoring and data-driven safety protocols
💡 Case studies highlighting successful deployment of environmental detection systems in oil & gas operations
Ideal for safety managers, operations leaders, and technology innovators in the oil & gas industry, this presentation offers practical insights and strategies to revolutionize safety standards and boost operational resilience.
👉 Learn more: https://www.rejigdigital.com/blog/continuous-monitoring-prevent-blowouts-well-control-issues/
Oracle Cloud and AI Specialization Program



Oracle Cloud and AI Specialization ProgramVICTOR MAESTRE RAMIREZ Oracle Cloud and AI Specialization Program
If You Use Databricks, You Definitely Need FME



If You Use Databricks, You Definitely Need FMESafe Software DataBricks makes it easy to use Apache Spark. It provides a platform with the potential to analyze and process huge volumes of data. Sounds awesome. The sales brochure reads as if it is a can-do-all data integration platform. Does it replace our beloved FME platform or does it provide opportunities for FME to shine? Challenge accepted
Your startup on AWS - How to architect and maintain a Lean and Mean account J...



Your startup on AWS - How to architect and maintain a Lean and Mean account J...angelo60207 Prevent infrastructure costs from becoming a significant line item on your startup’s budget! Serial entrepreneur and software architect Angelo Mandato will share his experience with AWS Activate (startup credits from AWS) and knowledge on how to architect a lean and mean AWS account ideal for budget minded and bootstrapped startups. In this session you will learn how to manage a production ready AWS account capable of scaling as your startup grows for less than $100/month before credits. We will discuss AWS Budgets, Cost Explorer, architect priorities, and the importance of having flexible, optimized Infrastructure as Code. We will wrap everything up discussing opportunities where to save with AWS services such as S3, EC2, Load Balancers, Lambda Functions, RDS, and many others.
Bridging the divide: A conversation on tariffs today in the book industry - T...



Bridging the divide: A conversation on tariffs today in the book industry - T...BookNet Canada A collaboration-focused conversation on the recently imposed US and Canadian tariffs where speakers shared insights into the current legislative landscape, ongoing advocacy efforts, and recommended next steps. This event was presented in partnership with the Book Industry Study Group.
Link to accompanying resource: https://bnctechforum.ca/sessions/bridging-the-divide-a-conversation-on-tariffs-today-in-the-book-industry/
Presented by BookNet Canada and the Book Industry Study Group on May 29, 2025 with support from the Department of Canadian Heritage.
Can We Use Rust to Develop Extensions for PostgreSQL? (POSETTE: An Event for ...



Can We Use Rust to Develop Extensions for PostgreSQL? (POSETTE: An Event for ...NTT DATA Technology & Innovation Can We Use Rust to Develop Extensions for PostgreSQL?
(POSETTE: An Event for Postgres 2025)
June 11, 2025
Shinya Kato
NTT DATA Japan Corporation
Crypto Super 500 - 14th Report - June2025.pdf



Crypto Super 500 - 14th Report - June2025.pdfStephen Perrenod This OrionX's 14th semi-annual report on the state of the cryptocurrency mining market. The report focuses on Proof-of-Work cryptocurrencies since those use substantial supercomputer power to mint new coins and encode transactions on their blockchains. Only two make the cut this time, Bitcoin with $18 billion of annual economic value produced and Dogecoin with $1 billion. Bitcoin has now reached the Zettascale with typical hash rates of 0.9 Zettahashes per second. Bitcoin is powered by the world's largest decentralized supercomputer in a continuous winner take all lottery incentive network.
Viral>Wondershare Filmora 14.5.18.12900 Crack Free Download



Viral>Wondershare Filmora 14.5.18.12900 Crack Free DownloadPuppy jhon ➡ 🌍📱👉COPY & PASTE LINK👉👉👉 ➤ ➤➤ https://drfiles.net/
Wondershare Filmora Crack is a user-friendly video editing software designed for both beginners and experienced users.
Can We Use Rust to Develop Extensions for PostgreSQL? (POSETTE: An Event for ...



Can We Use Rust to Develop Extensions for PostgreSQL? (POSETTE: An Event for ...NTT DATA Technology & Innovation
DevOps & Security: Here & Now
- 1. DevOps and Security: It’s Happening. Right Now. Helen Bravo Director of Product Management at Checkmarx [email protected]
- 2. Agenda • Intro to DevOps • Integrating security within DevOps – Problems with traditional controls – Steps to DevOps security
- 3. What is DevOps About? An unstoppable deployment process … in small chunks of time
- 4. DevOps is Happening Companies that have adopted DevOps
- 5. Can TRADITIONAL web application security controls fit in… … a DevOps environment?!
- 6. Traditional Web Application Security Controls • Penetration Testing • WAF (Web Application Firewall) • Code Analysis
- 7. Penetration Testing- Takes Time!
- 8. Penetration Testing – 300 pages report – 3 weeks assessment time – 2 weeks to get it into development
- 9. Web Application Firewall (WAF) Thinking Continuous Deployment? Think Continuous Configuration!
- 10. Code Analysis • Setup time • Running time • Analysis time … just too slow!
- 12. … Do Nothing?
- 13. Required: A New Secure SDLC Approach
- 14. Step by Step
- 15. Step 1: Plan for Security
- 16. Step 1: Plan for Security • Identify unsecured APIs and frameworks • Map security sensitive code portions. E.g. password changes mechanism, user authentication mechanism. • Anticipate regulatory problems, plan for it.
- 17. Step 2: Engage the Developers. And Be Engaged
- 18. Step 2: Engage the Developers. And Be Engaged • Connect developers to security – Going to OWASP? Bring a developer with you! • Is your house on fire? Share the details with your developers. • Have an open door approach • Set up an online collaboration platform E.g. Jive, Confluence etc.
- 19. Step 3: Arm the Developers
- 20. Step 3: Arm the Developer • Secure frameworks: – Use a secure framework such as Spring Security, JAAS, Apache Shiro, Symfony2 – ESAPI is a very useful OWASP security framework • SCA tools that can provide security feedback on pre-commit stage. – Rapid response – Small chunks
- 21. Step 3: Automate the Process
- 22. Step 3: Automate the Process • Integrate within your build (Jenkins, Bamboo, TeamCity, etc.) – SAST – DAST • Fail the build if security does not pass the bar.
- 23. Continuous Deployment Unit Tests Develop Code Commit Source Control Build Trigger Deploy to Test Env Report & Notify Publish to release repository Deploy to Production
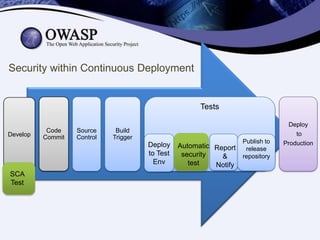
- 24. Security within Continuous Deployment Tests Develop Code Commit Source Control Build Trigger Deploy to Test Env SCA Test Publish to Automatic Report release security repository & test Notify Deploy to Production
- 25. Step 5: Use Old Tools Wisely
- 26. Step 5: Use Old Tools Wisely • Periodic pen testing • WAF on main functions • Code review for security sensitive code portions.
- 27. Summary
- 28. Summary • DevOps is happening. Right Now. – During the time of this talk, Amazon has released 75 features and bug fixes. • Security should not be compromised • Don’t be overwhelmed. Start small
- 29. The 3 Takeaways 1. Plan from the ground 2. Engage with your developers 3. Integrate security into automatic build process.
- 30. Questions?





