Skiena algorithm 2007 lecture16 introduction to dynamic programming
1 like1,023 views
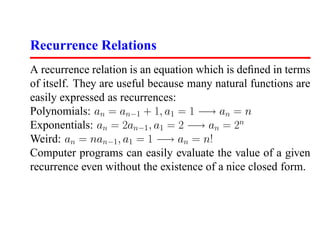
This document summarizes a lecture on dynamic programming. It begins by introducing dynamic programming as a powerful tool for solving optimization problems on ordered items like strings. It then contrasts greedy algorithms, which make locally optimal choices, with dynamic programming, which systematically searches all possibilities while storing results. The document provides examples of computing Fibonacci numbers and binomial coefficients using dynamic programming by storing partial results rather than recomputing them. It outlines three key steps to applying dynamic programming: formulating a recurrence, bounding subproblems, and specifying an evaluation order.
1 of 17
Downloaded 29 times













![Binomial Coefficients Implementation
long binomial coefficient(n,m)
int n,m; (* compute n choose m *)
{
int i,j; (* counters *)
long bc[MAXN][MAXN]; (* table of binomial coefficients *)
for (i=0; i<=n; i++) bc[i][0] = 1;
for (j=0; j<=n; j++) bc[j][j] = 1;
for (i=1; i<=n; i++)
for (j=1; j<i; j++)
bc[i][j] = bc[i-1][j-1] + bc[i-1][j];
return( bc[n][m] );
}](https://image.slidesharecdn.com/skienaalgorithm2007lecture16introductiontodynamicprogramming-111212074927-phpapp02/85/Skiena-algorithm-2007-lecture16-introduction-to-dynamic-programming-16-320.jpg)

Ad
Recommended
unit-4-dynamic programming
unit-4-dynamic programminghodcsencet Dynamic programming is used to solve optimization problems by combining solutions to overlapping subproblems. It works by breaking down problems into subproblems, solving each subproblem only once, and storing the solutions in a table to avoid recomputing them. There are two key properties for applying dynamic programming: overlapping subproblems and optimal substructure. Some applications of dynamic programming include finding shortest paths, matrix chain multiplication, the traveling salesperson problem, and knapsack problems.
5.3 dynamic programming 03
5.3 dynamic programming 03Krish_ver2 Dynamic programming is an algorithm design paradigm that can be applied to problems exhibiting optimal substructure and overlapping subproblems. It works by breaking down a problem into subproblems and storing the results of already solved subproblems, rather than recomputing them multiple times. This allows for an efficient bottom-up approach. Examples where dynamic programming can be applied include the matrix chain multiplication problem, the 0-1 knapsack problem, and finding the longest common subsequence between two strings.
Unit 3 daa
Unit 3 daaNv Thejaswini This document discusses dynamic programming and algorithms for solving all-pair shortest path problems. It begins by explaining dynamic programming as an optimization technique that works bottom-up by solving subproblems once and storing their solutions, rather than recomputing them. It then presents Floyd's algorithm for finding shortest paths between all pairs of nodes in a graph. The algorithm iterates through nodes, updating the shortest path lengths between all pairs that include that node by exploring paths through it. Finally, it discusses solving multistage graph problems using forward and backward methods that work through the graph stages in different orders.
Dynamic programming - fundamentals review
Dynamic programming - fundamentals reviewElifTech Dynamic programming is an algorithmic paradigm for solving complex problems by breaking them down into overlapping subproblems and storing their solutions to avoid redundancy. Key properties include overlapping subproblems and optimal substructure, which allow for problems like Fibonacci sequences, longest increasing subsequences, longest common subsequences, and more to be solved efficiently. Techniques such as memoization and tabulation are used to store solutions, significantly improving performance over naive recursive methods.
Dynamic Programming - Part II
Dynamic Programming - Part IIAmrinder Arora The document is a lecture on dynamic programming, focusing on various algorithms such as maximum value contiguous subarray, longest increasing subsequence, and coin change. It details algorithmic approaches, including brute force, greedy variations, and dynamic programming solutions with time complexities. Additionally, it includes sample runs and insights on optimal substructure in dynamic programming.
DP
DPSubba Oota Dynamic programming is an algorithmic technique that solves problems by breaking them down into smaller subproblems and storing the results of subproblems to avoid recomputing them. It is useful for optimization problems with overlapping subproblems. The key steps are to characterize the structure of an optimal solution, recursively define the value of an optimal solution, compute that value, and construct the optimal solution. Examples discussed include rod cutting, longest increasing subsequence, longest palindrome subsequence, and palindrome partitioning. Other problems that can be solved with dynamic programming include edit distance, shortest paths, optimal binary search trees, the traveling salesman problem, and reliability design.
Branch and bound
Branch and boundDr Shashikant Athawale The branch-and-bound method is used to solve optimization problems by traversing a state space tree. It computes a bound at each node to determine if the node is promising. Better approaches traverse nodes breadth-first and choose the most promising node using a bounding heuristic. The traveling salesperson problem is solved using branch-and-bound by finding an initial tour, defining a bounding heuristic as the actual cost plus minimum remaining cost, and expanding promising nodes in best-first order until finding the minimal tour.
Dynamic programming1
Dynamic programming1debolina13 The document discusses the dynamic programming approach to solving the matrix chain multiplication problem. It explains that dynamic programming breaks problems down into overlapping subproblems, solves each subproblem once, and stores the solutions in a table to avoid recomputing them. It then presents the algorithm MATRIX-CHAIN-ORDER that uses dynamic programming to solve the matrix chain multiplication problem in O(n^3) time, as opposed to a brute force approach that would take exponential time.
Dynamic Programming
Dynamic ProgrammingSahil Kumar The document discusses dynamic programming, focusing on the knapsack problem and optimal binary search trees. It explains the principle of optimality in dynamic programming, how to construct optimal binary search trees, and the algorithms for their implementation. Detailed examples illustrate the methods used to compute decisions and costs associated with these problems.
Matrix chain multiplication
Matrix chain multiplicationRespa Peter Dynamic programming is an algorithm design technique that uses a tabular method and divide-and-conquer to solve problems with interdependent subproblems. The document focuses on matrix-chain multiplication, emphasizing the importance of parenthesization to minimize scalar multiplications required for matrix products. It details a structured approach consisting of characterizing optimal solutions, defining their recursive values, computing solutions bottom-up, and constructing the final optimal solution.
Greedy Algorithms
Greedy AlgorithmsAmrinder Arora The document discusses the design and analysis of algorithms, focusing on greedy algorithms such as Kruskal's algorithm for minimum spanning trees and the knapsack problem. It highlights the greedy method's applications, including sorting, merging arrays, and optimization problems, along with their time complexity and properties. Additionally, it outlines when to appropriately use greedy algorithms and the importance of ensuring optimal solutions in practical scenarios.
Analysis of Algorithm
Analysis of Algorithmأحلام انصارى The document discusses approximation algorithms and genetic algorithms for solving optimization problems like the traveling salesman problem (TSP) and vertex cover problem. It provides examples of approximation algorithms for these NP-hard problems, including algorithms that find near-optimal solutions within polynomial time. Genetic algorithms are also presented as an approach to solve TSP and other problems by encoding potential solutions and applying genetic operators like crossover and mutation.
Dynamic programming
Dynamic programmingGopi Saiteja This document discusses the concept of dynamic programming. It provides examples of dynamic programming problems including assembly line scheduling and matrix chain multiplication. The key steps of a dynamic programming problem are: (1) characterize the optimal structure of a solution, (2) define the problem recursively, (3) compute the optimal solution in a bottom-up manner by solving subproblems only once and storing results, and (4) construct an optimal solution from the computed information.
dynamic programming Rod cutting class
dynamic programming Rod cutting classgiridaroori The document discusses the dynamic programming approach to solving the Fibonacci numbers problem and the rod cutting problem. It explains that dynamic programming formulations first express the problem recursively but then optimize it by storing results of subproblems to avoid recomputing them. This is done either through a top-down recursive approach with memoization or a bottom-up approach by filling a table with solutions to subproblems of increasing size. The document also introduces the matrix chain multiplication problem and how it can be optimized through dynamic programming by considering overlapping subproblems.
DS ppt
DS pptkirupasuchi1996 Dynamic programming is a mathematical optimization method and computer programming technique used to solve complex problems by breaking them down into simpler subproblems. It was developed by Richard Bellman in the 1950s and has been applied in many fields. Dynamic programming problems can be solved optimally by breaking them into subproblems with optimal substructures that can be solved recursively. It uses techniques like top-down or bottom-up approaches and storing results of subproblems to solve larger problems efficiently by avoiding recomputing the common subproblems. Multistage graphs are a type of problem well-suited for dynamic programming solutions using techniques like greedy algorithms, Dijkstra's algorithm, or dynamic programming to find shortest paths. Traversal and search algorithms like breadth-
Daa unit 3
Daa unit 3Abhimanyu Mishra The document discusses algorithms and data structures using divide and conquer and greedy approaches. It covers topics like matrix multiplication, convex hull, binary search, activity selection problem, knapsack problem, and their algorithms and time complexities. Examples are provided for convex hull, binary search, activity selection, and knapsack problem algorithms. The document is intended as teaching material on design and analysis of algorithms.
Dynamic Programming - Part 1
Dynamic Programming - Part 1Amrinder Arora This document discusses dynamic programming techniques. It covers matrix chain multiplication and all pairs shortest paths problems. Dynamic programming involves breaking down problems into overlapping subproblems and storing the results of already solved subproblems to avoid recomputing them. It has four main steps - defining a mathematical notation for subproblems, proving optimal substructure, deriving a recurrence relation, and developing an algorithm using the relation.
5.3 dynamic programming
5.3 dynamic programmingKrish_ver2 Dynamic programming is a technique for solving problems with overlapping subproblems and optimal substructure. It works by breaking problems down into smaller subproblems and storing the results in a table to avoid recomputing them. Examples where it can be applied include the knapsack problem, longest common subsequence, and computing Fibonacci numbers efficiently through bottom-up iteration rather than top-down recursion. The technique involves setting up recurrences relating larger instances to smaller ones, solving the smallest instances, and building up the full solution using the stored results.
Backtracking & branch and bound
Backtracking & branch and boundVipul Chauhan The document discusses backtracking and branch and bound algorithms. Backtracking incrementally builds candidates and abandons them (backtracks) when they cannot lead to a valid solution. Branch and bound systematically enumerates solutions and discards branches that cannot produce a better solution than the best found so far based on upper bounds. Examples provided are the N-Queens problem solved with backtracking and the knapsack problem solved with branch and bound. Pseudocode is given for both algorithms.
5.1 greedy
5.1 greedyKrish_ver2 The document discusses various optimization problems that can be solved using the greedy method. It begins by explaining that the greedy method involves making locally optimal choices at each step that combine to produce a globally optimal solution. Several examples are then provided to illustrate problems that can and cannot be solved with the greedy method. These include shortest path problems, minimum spanning trees, activity-on-edge networks, and Huffman coding. Specific greedy algorithms like Kruskal's algorithm, Prim's algorithm, and Dijkstra's algorithm are also covered. The document concludes by noting that the greedy method can only be applied to solve a small number of optimization problems.
Dynamicpgmming
DynamicpgmmingMuhammad Wasif This document discusses dynamic programming and provides examples to illustrate the technique. It begins by defining dynamic programming as a bottom-up approach to problem solving where solutions to smaller subproblems are stored and built upon to solve larger problems. It then provides examples of dynamic programming algorithms for calculating Fibonacci numbers, binomial coefficients, and finding shortest paths using Floyd's algorithm. The key aspects of dynamic programming like avoiding recomputing solutions and storing intermediate results in tables are emphasized.
Dynamic programming
Dynamic programmingJay Nagar Dynamic programming is a method for solving complex problems by breaking them into simpler subproblems, solving each only once, and storing their solutions. It is applicable in optimization problems where optimal substructure and overlapping subproblems are present, allowing for efficient solutions compared to divide-and-conquer strategies. The process involves characterizing the optimal solution structure, defining the problem recursively, computing values systematically, and sometimes constructing the optimal solution based on these computed values.
Lecture 8 dynamic programming
Lecture 8 dynamic programmingOye Tu This document discusses algorithms for finding minimum and maximum elements in an array, including simultaneous minimum and maximum algorithms. It introduces dynamic programming as a technique for improving inefficient divide-and-conquer algorithms by storing results of subproblems to avoid recomputing them. Examples of dynamic programming include calculating the Fibonacci sequence and solving an assembly line scheduling problem to minimize total time.
Daa:Dynamic Programing
Daa:Dynamic Programingrupali_2bonde Dynamic programming is used to solve optimization problems by breaking them down into subproblems. It solves each subproblem only once, storing the results in a table to lookup when the subproblem recurs. This avoids recomputing solutions and reduces computation. The key is determining the optimal substructure of problems. It involves characterizing optimal solutions recursively, computing values in a bottom-up table, and tracing back the optimal solution. An example is the 0/1 knapsack problem to maximize profit fitting items in a knapsack of limited capacity.
5.1 greedy 03
5.1 greedy 03Krish_ver2 This document discusses greedy algorithms and provides examples of their use. It begins by defining characteristics of greedy algorithms, such as making locally optimal choices that reduce a problem into smaller subproblems. The document then covers designing greedy algorithms, proving their optimality, and analyzing examples like the fractional knapsack problem and minimum spanning tree algorithms. Specific greedy algorithms covered in more depth include Kruskal's and Prim's minimum spanning tree algorithms and Huffman coding.
Comparitive Analysis of Algorithm strategies
Comparitive Analysis of Algorithm strategiesTalha Shaikh The document discusses various algorithm strategies including decrease and conquer, greedy approach, backtracking, and transform and conquer. It provides definitions, examples, advantages and disadvantages for each strategy. Decrease and conquer algorithms like insertion sort reduce the problem size at each step. Greedy algorithms make locally optimal choices at each step. Backtracking algorithms systematically explore all solutions using a depth first search approach.
Unit 3
Unit 3Gunasundari Selvaraj This document discusses dynamic programming and greedy algorithms. It begins by defining dynamic programming as a technique for solving problems with overlapping subproblems. Examples provided include computing the Fibonacci numbers and binomial coefficients. Greedy algorithms are introduced as constructing solutions piece by piece through locally optimal choices. Applications discussed are the change-making problem, minimum spanning trees using Prim's and Kruskal's algorithms, and single-source shortest paths. Floyd's algorithm for all pairs shortest paths and optimal binary search trees are also summarized.
Dynamic programming
Dynamic programmingAmit Kumar Rathi (1) Dynamic programming is an algorithm design technique that solves problems by breaking them down into smaller subproblems and storing the results of already solved subproblems. (2) It is applicable to problems where subproblems overlap and solving them recursively would result in redundant computations. (3) The key steps of a dynamic programming algorithm are to characterize the optimal structure, define the problem recursively in terms of optimal substructures, and compute the optimal solution bottom-up by solving subproblems only once.
Dynamic programming
Dynamic programmingMelaku Bayih Demessie Dynamic programming is an algorithm design technique for solving optimization problems defined by recurrences with overlapping subproblems, introduced by Richard Bellman in the 1950s. It involves solving smaller instances once and storing their solutions to avoid redundant computations, contrasting with divide-and-conquer methods. Applications include the knapsack problem, where optimal item selection is determined based on size and value constraints, and the edit distance problem, which calculates the minimum edit operations needed to transform one string into another.
Dynamic programming lcs
Dynamic programming lcsDepartment of Information Management Ming Chuan University, Taiwan This document discusses the longest common subsequence (LCS) problem and how to solve it using dynamic programming. It begins by defining key terms like subsequence and common subsequence. It then describes the optimal substructure of LCS problems and how they can be broken down into overlapping subproblems. The document provides pseudocode that uses dynamic programming to fill a table to compute the length of the LCS between two sequences in O(mn) time and also construct the optimal LCS. An example is worked through and references are provided.
More Related Content
What's hot (20)
Dynamic Programming
Dynamic ProgrammingSahil Kumar The document discusses dynamic programming, focusing on the knapsack problem and optimal binary search trees. It explains the principle of optimality in dynamic programming, how to construct optimal binary search trees, and the algorithms for their implementation. Detailed examples illustrate the methods used to compute decisions and costs associated with these problems.
Matrix chain multiplication
Matrix chain multiplicationRespa Peter Dynamic programming is an algorithm design technique that uses a tabular method and divide-and-conquer to solve problems with interdependent subproblems. The document focuses on matrix-chain multiplication, emphasizing the importance of parenthesization to minimize scalar multiplications required for matrix products. It details a structured approach consisting of characterizing optimal solutions, defining their recursive values, computing solutions bottom-up, and constructing the final optimal solution.
Greedy Algorithms
Greedy AlgorithmsAmrinder Arora The document discusses the design and analysis of algorithms, focusing on greedy algorithms such as Kruskal's algorithm for minimum spanning trees and the knapsack problem. It highlights the greedy method's applications, including sorting, merging arrays, and optimization problems, along with their time complexity and properties. Additionally, it outlines when to appropriately use greedy algorithms and the importance of ensuring optimal solutions in practical scenarios.
Analysis of Algorithm
Analysis of Algorithmأحلام انصارى The document discusses approximation algorithms and genetic algorithms for solving optimization problems like the traveling salesman problem (TSP) and vertex cover problem. It provides examples of approximation algorithms for these NP-hard problems, including algorithms that find near-optimal solutions within polynomial time. Genetic algorithms are also presented as an approach to solve TSP and other problems by encoding potential solutions and applying genetic operators like crossover and mutation.
Dynamic programming
Dynamic programmingGopi Saiteja This document discusses the concept of dynamic programming. It provides examples of dynamic programming problems including assembly line scheduling and matrix chain multiplication. The key steps of a dynamic programming problem are: (1) characterize the optimal structure of a solution, (2) define the problem recursively, (3) compute the optimal solution in a bottom-up manner by solving subproblems only once and storing results, and (4) construct an optimal solution from the computed information.
dynamic programming Rod cutting class
dynamic programming Rod cutting classgiridaroori The document discusses the dynamic programming approach to solving the Fibonacci numbers problem and the rod cutting problem. It explains that dynamic programming formulations first express the problem recursively but then optimize it by storing results of subproblems to avoid recomputing them. This is done either through a top-down recursive approach with memoization or a bottom-up approach by filling a table with solutions to subproblems of increasing size. The document also introduces the matrix chain multiplication problem and how it can be optimized through dynamic programming by considering overlapping subproblems.
DS ppt
DS pptkirupasuchi1996 Dynamic programming is a mathematical optimization method and computer programming technique used to solve complex problems by breaking them down into simpler subproblems. It was developed by Richard Bellman in the 1950s and has been applied in many fields. Dynamic programming problems can be solved optimally by breaking them into subproblems with optimal substructures that can be solved recursively. It uses techniques like top-down or bottom-up approaches and storing results of subproblems to solve larger problems efficiently by avoiding recomputing the common subproblems. Multistage graphs are a type of problem well-suited for dynamic programming solutions using techniques like greedy algorithms, Dijkstra's algorithm, or dynamic programming to find shortest paths. Traversal and search algorithms like breadth-
Daa unit 3
Daa unit 3Abhimanyu Mishra The document discusses algorithms and data structures using divide and conquer and greedy approaches. It covers topics like matrix multiplication, convex hull, binary search, activity selection problem, knapsack problem, and their algorithms and time complexities. Examples are provided for convex hull, binary search, activity selection, and knapsack problem algorithms. The document is intended as teaching material on design and analysis of algorithms.
Dynamic Programming - Part 1
Dynamic Programming - Part 1Amrinder Arora This document discusses dynamic programming techniques. It covers matrix chain multiplication and all pairs shortest paths problems. Dynamic programming involves breaking down problems into overlapping subproblems and storing the results of already solved subproblems to avoid recomputing them. It has four main steps - defining a mathematical notation for subproblems, proving optimal substructure, deriving a recurrence relation, and developing an algorithm using the relation.
5.3 dynamic programming
5.3 dynamic programmingKrish_ver2 Dynamic programming is a technique for solving problems with overlapping subproblems and optimal substructure. It works by breaking problems down into smaller subproblems and storing the results in a table to avoid recomputing them. Examples where it can be applied include the knapsack problem, longest common subsequence, and computing Fibonacci numbers efficiently through bottom-up iteration rather than top-down recursion. The technique involves setting up recurrences relating larger instances to smaller ones, solving the smallest instances, and building up the full solution using the stored results.
Backtracking & branch and bound
Backtracking & branch and boundVipul Chauhan The document discusses backtracking and branch and bound algorithms. Backtracking incrementally builds candidates and abandons them (backtracks) when they cannot lead to a valid solution. Branch and bound systematically enumerates solutions and discards branches that cannot produce a better solution than the best found so far based on upper bounds. Examples provided are the N-Queens problem solved with backtracking and the knapsack problem solved with branch and bound. Pseudocode is given for both algorithms.
5.1 greedy
5.1 greedyKrish_ver2 The document discusses various optimization problems that can be solved using the greedy method. It begins by explaining that the greedy method involves making locally optimal choices at each step that combine to produce a globally optimal solution. Several examples are then provided to illustrate problems that can and cannot be solved with the greedy method. These include shortest path problems, minimum spanning trees, activity-on-edge networks, and Huffman coding. Specific greedy algorithms like Kruskal's algorithm, Prim's algorithm, and Dijkstra's algorithm are also covered. The document concludes by noting that the greedy method can only be applied to solve a small number of optimization problems.
Dynamicpgmming
DynamicpgmmingMuhammad Wasif This document discusses dynamic programming and provides examples to illustrate the technique. It begins by defining dynamic programming as a bottom-up approach to problem solving where solutions to smaller subproblems are stored and built upon to solve larger problems. It then provides examples of dynamic programming algorithms for calculating Fibonacci numbers, binomial coefficients, and finding shortest paths using Floyd's algorithm. The key aspects of dynamic programming like avoiding recomputing solutions and storing intermediate results in tables are emphasized.
Dynamic programming
Dynamic programmingJay Nagar Dynamic programming is a method for solving complex problems by breaking them into simpler subproblems, solving each only once, and storing their solutions. It is applicable in optimization problems where optimal substructure and overlapping subproblems are present, allowing for efficient solutions compared to divide-and-conquer strategies. The process involves characterizing the optimal solution structure, defining the problem recursively, computing values systematically, and sometimes constructing the optimal solution based on these computed values.
Lecture 8 dynamic programming
Lecture 8 dynamic programmingOye Tu This document discusses algorithms for finding minimum and maximum elements in an array, including simultaneous minimum and maximum algorithms. It introduces dynamic programming as a technique for improving inefficient divide-and-conquer algorithms by storing results of subproblems to avoid recomputing them. Examples of dynamic programming include calculating the Fibonacci sequence and solving an assembly line scheduling problem to minimize total time.
Daa:Dynamic Programing
Daa:Dynamic Programingrupali_2bonde Dynamic programming is used to solve optimization problems by breaking them down into subproblems. It solves each subproblem only once, storing the results in a table to lookup when the subproblem recurs. This avoids recomputing solutions and reduces computation. The key is determining the optimal substructure of problems. It involves characterizing optimal solutions recursively, computing values in a bottom-up table, and tracing back the optimal solution. An example is the 0/1 knapsack problem to maximize profit fitting items in a knapsack of limited capacity.
5.1 greedy 03
5.1 greedy 03Krish_ver2 This document discusses greedy algorithms and provides examples of their use. It begins by defining characteristics of greedy algorithms, such as making locally optimal choices that reduce a problem into smaller subproblems. The document then covers designing greedy algorithms, proving their optimality, and analyzing examples like the fractional knapsack problem and minimum spanning tree algorithms. Specific greedy algorithms covered in more depth include Kruskal's and Prim's minimum spanning tree algorithms and Huffman coding.
Comparitive Analysis of Algorithm strategies
Comparitive Analysis of Algorithm strategiesTalha Shaikh The document discusses various algorithm strategies including decrease and conquer, greedy approach, backtracking, and transform and conquer. It provides definitions, examples, advantages and disadvantages for each strategy. Decrease and conquer algorithms like insertion sort reduce the problem size at each step. Greedy algorithms make locally optimal choices at each step. Backtracking algorithms systematically explore all solutions using a depth first search approach.
Unit 3
Unit 3Gunasundari Selvaraj This document discusses dynamic programming and greedy algorithms. It begins by defining dynamic programming as a technique for solving problems with overlapping subproblems. Examples provided include computing the Fibonacci numbers and binomial coefficients. Greedy algorithms are introduced as constructing solutions piece by piece through locally optimal choices. Applications discussed are the change-making problem, minimum spanning trees using Prim's and Kruskal's algorithms, and single-source shortest paths. Floyd's algorithm for all pairs shortest paths and optimal binary search trees are also summarized.
Dynamic programming
Dynamic programmingAmit Kumar Rathi (1) Dynamic programming is an algorithm design technique that solves problems by breaking them down into smaller subproblems and storing the results of already solved subproblems. (2) It is applicable to problems where subproblems overlap and solving them recursively would result in redundant computations. (3) The key steps of a dynamic programming algorithm are to characterize the optimal structure, define the problem recursively in terms of optimal substructures, and compute the optimal solution bottom-up by solving subproblems only once.
Viewers also liked (10)
Dynamic programming
Dynamic programmingMelaku Bayih Demessie Dynamic programming is an algorithm design technique for solving optimization problems defined by recurrences with overlapping subproblems, introduced by Richard Bellman in the 1950s. It involves solving smaller instances once and storing their solutions to avoid redundant computations, contrasting with divide-and-conquer methods. Applications include the knapsack problem, where optimal item selection is determined based on size and value constraints, and the edit distance problem, which calculates the minimum edit operations needed to transform one string into another.
Dynamic programming lcs
Dynamic programming lcsDepartment of Information Management Ming Chuan University, Taiwan This document discusses the longest common subsequence (LCS) problem and how to solve it using dynamic programming. It begins by defining key terms like subsequence and common subsequence. It then describes the optimal substructure of LCS problems and how they can be broken down into overlapping subproblems. The document provides pseudocode that uses dynamic programming to fill a table to compute the length of the LCS between two sequences in O(mn) time and also construct the optimal LCS. An example is worked through and references are provided.
lecture 23
lecture 23sajinsc The document discusses dynamic programming and amortized analysis. It reviews how dynamic tables use amortized analysis to achieve an overall cost of O(1) per insertion by occasionally doubling the table size and reinserting all elements. This results in a worst case cost of O(n) for a single insertion but averages to O(1) over many insertions. It also discusses using an accounting method with a $3 charge per insertion to pay for future table resizes, achieving an amortized cost of O(1) per operation. Finally, it introduces dynamic programming and uses the longest common subsequence problem to illustrate how it breaks problems into optimal subrecurring subproblems.
Longest Common Subsequence
Longest Common SubsequenceSwati Swati The document discusses the longest common subsequence (LCS) problem and how to solve it using dynamic programming. It begins by defining LCS as the longest sequence of characters that appear left-to-right in two given strings. It then describes solving LCS using a brute force method with exponential time complexity and using dynamic programming with polynomial time complexity. Finally, it provides an example of finding the LCS of two strings and discusses applications and references.
lecture 24
lecture 24sajinsc The document discusses dynamic programming and its application to solving the longest common subsequence (LCS) problem. It presents the LCS algorithm, which uses dynamic programming to find the length and sequence of the longest subsequence common to two strings X and Y in O(mn) time, where m and n are the lengths of X and Y, respectively. It provides an example running the LCS algorithm on strings X="ABCB" and Y="BDCAB" to determine their longest common subsequence is "BCB".
Longest common subsequence lcs
Longest common subsequence lcsShahariar Rabby The longest common subsequence (LCS) problem involves finding the longest subsequence that is common to two or more sequences. The document discusses various methods for solving this problem, including naive and dynamic programming approaches, along with their complexities and strengths. It also provides examples on how to compute LCS using sequences such as DNA strands.
Dynamic pgmming
Dynamic pgmmingDr. C.V. Suresh Babu This document provides an overview of dynamic programming. It begins by explaining that dynamic programming is a technique for solving optimization problems by breaking them down into overlapping subproblems and storing the results of solved subproblems in a table to avoid recomputing them. It then provides examples of problems that can be solved using dynamic programming, including Fibonacci numbers, binomial coefficients, shortest paths, and optimal binary search trees. The key aspects of dynamic programming algorithms, including defining subproblems and combining their solutions, are also outlined.
Elements of dynamic programming
Elements of dynamic programmingTafhim Islam Dynamic programming (DP) is a technique used to create efficient algorithms for specific problem classes, utilizing concepts such as optimal substructure and overlapping sub-problems. Optimal substructure involves choosing the best option from sub-components to solve larger problems, while overlapping sub-problems occur when the same smaller problems are resolved multiple times within different larger issues. Memoization is the technique of storing previously computed solutions to enhance efficiency in problem-solving.
Longest Common Subsequence (LCS) Algorithm
Longest Common Subsequence (LCS) AlgorithmDarshit Metaliya The document discusses the analysis and design of the Longest Common Subsequence (LCS) algorithm, including its definition, conditions for recursive calculations, and examples. It explains how to calculate the LCS for given sequences, providing specific examples and illustrating the recursive approach with a computation tree. The complexity of the LCS algorithm is noted as O(mn), where m and n are the lengths of the input strings.
Knapsack Problem
Knapsack ProblemJenny Galino The document discusses the knapsack problem, which involves selecting a subset of items that fit within a knapsack of limited capacity to maximize the total value. There are two versions - the 0-1 knapsack problem where items can only be selected entirely or not at all, and the fractional knapsack problem where items can be partially selected. Solutions include brute force, greedy algorithms, and dynamic programming. Dynamic programming builds up the optimal solution by considering all sub-problems.
Ad
Similar to Skiena algorithm 2007 lecture16 introduction to dynamic programming (20)
L16
L16FALLEE31188 The document discusses recursive definitions of sequences, functions, sets, and strings. It provides examples of recursively defining the Fibonacci sequence, factorial function, set of prices using quarters and dimes, and set of binary numbers. It also discusses recursively defining the length, empty string, concatenation, and reversal of strings.
Sienna 10 dynamic
Sienna 10 dynamicchidabdu This document discusses dynamic programming and provides examples of how it can be applied to optimize algorithms to solve problems with overlapping subproblems. It summarizes dynamic programming, provides examples for the Fibonacci numbers, binomial coefficients, and knapsack problems, and analyzes the time and space complexity of algorithms developed using dynamic programming approaches.
tutorial5.ppt
tutorial5.pptjvjfvvoa This document provides an overview of combinatorics and number theory concepts including basic counting techniques, recurrence relations, binomial coefficients, prime numbers, congruences, and proofs by induction. It discusses topics such as permutations, subsets, Pascal's triangle for calculating binomial coefficients efficiently, and using recurrence relations to solve problems like calculating the Fibonacci sequence or the number of ways to reach the last stage in a multi-stage process.
Presentation 3
Presentation 3KeatonTech The document discusses recurrence relations and provides examples of how they can be used to model real-world scenarios like loan payments. It explains that a recurrence relation is a function that includes itself, and provides examples of simple and more complex recurrence relations. It also gives an example of how a recurrence relation can model the remaining debt on a loan each month over the life of the loan based on the initial amount, monthly payment, and interest rate.
Algorithm chapter 8
Algorithm chapter 8chidabdu Dynamic programming is an algorithm design technique that solves problems by breaking them down into smaller overlapping subproblems and storing the solutions to subproblems to avoid recomputing them. It involves building up a solution using previously found subsolutions and working in a bottom-up fashion to solve larger subproblems from solutions to smaller subproblems. Examples where dynamic programming has been applied include computing Fibonacci numbers, finding the shortest paths in a graph, and solving optimization problems like the knapsack problem.
3. Recursion and Recurrences.ppt detail about recursive learning
3. Recursion and Recurrences.ppt detail about recursive learningKashifNadeem52 The document covers the concept of recursion as a problem-solving technique, explaining how it divides problems into smaller subproblems, with examples such as the factorial function and Fibonacci numbers. Additionally, it discusses the advantages and disadvantages of recursive algorithms, the divide-and-conquer method, and approaches to solve recurrences through methods like the substitution and iteration methods. It also introduces the Master Theorem for analyzing the running time of divide-and-conquer algorithms.
Sure interview algorithm-1103
Sure interview algorithm-1103Sure Interview The document discusses finding the longest common subsequence between two sequences and provides an algorithm using dynamic programming. It explains using a matrix to store the current alignment results, where each cell Aij is calculated based on the adjacent cells, with scores considered. There are two steps - find the length of the LCS using the matrix, then trace back to find the exact alignment. It also discusses the knapsack problem and how dynamic programming can be applied to optimize combination problems.
Dynamic programing
Dynamic programingAniketSingh609353 The document discusses the technique of dynamic programming. It begins with an example of using dynamic programming to compute the Fibonacci numbers more efficiently than a naive recursive solution. This involves storing previously computed values in a table to avoid recomputing them. The document then presents the problem of finding the longest increasing subsequence in an array. It defines the problem and subproblems, derives a recurrence relation, and provides both recursive and iterative memoized algorithms to solve it in quadratic time using dynamic programming.
d0a2de03-27d3-4ca2-9ac6-d83440657a6c.ppt
d0a2de03-27d3-4ca2-9ac6-d83440657a6c.pptSrishaUrala Dynamic programming is a method for solving problems with overlapping sub-problems by solving each sub-problem once and storing the results. This technique, introduced by Richard Bellman, can employ either a bottom-up or a top-down approach to efficiently compute solutions. Examples of problems that can be solved using dynamic programming include Fibonacci numbers, binomial coefficients, and various optimization problems like the traveling salesman and knapsack problem.
DS & Algo 6 - Dynamic Programming
DS & Algo 6 - Dynamic ProgrammingMohammad Imam Hossain The document discusses dynamic programming and provides examples of problems that can be solved using dynamic programming techniques. It describes characteristics of dynamic programming problems such as overlapping subproblems and optimal substructure properties. It also describes two common approaches to dynamic programming - top-down with memorization and bottom-up with tabulation. Finally, it lists 12 practice problems related to topics like staircase problem, tiling problem, friends pairing problem, house thief problem, minimum jumps problem, Catalan numbers, binomial coefficients, permutation coefficients, subset sum problem, 0/1 knapsack problem, longest common subsequence and edit distance that can be solved using dynamic programming.
815.07 machine learning using python.pdf
815.07 machine learning using python.pdfSairaAtta5 Recursive functions can be used to solve problems by breaking them down into smaller subproblems. Dynamic programming is a technique for solving recursive problems more efficiently by avoiding recomputing results. It works by either building up the solution from smallest to largest subproblems (bottom-up) or saving computed results to lookup later (top-down). Examples where dynamic programming improves performance include calculating factorials, Fibonacci numbers, binomial coefficients, and the Poisson-binomial distribution.
Fibonacci
FibonacciTabarnac Maria The document discusses the Fibonacci sequence and its connections to mathematical concepts like the golden ratio, continued fractions, and polynomial division. It begins by defining the Fibonacci sequence and exploring some of its properties and identities. It then shows how the golden ratio arises in the continued fraction representation of Fibonacci numbers. The document also examines how polynomial long division can be used to derive the Fibonacci sequence and discusses power series expansions involving Fibonacci numbers.
Recursive Definitions in Discrete Mathmatcs.pptx
Recursive Definitions in Discrete Mathmatcs.pptxgbikorno The document discusses recursive definitions, which define an object in terms of itself. It provides examples of recursively defined sequences, functions, and sets. Recursion is related to mathematical induction. Recursive algorithms solve problems by reducing them to smaller instances of the same problem. While recursive definitions and algorithms are elegant, iterative equivalents are typically more efficient in terms of time and space usage.
Lec-32 Recursion -Recursion in Computer Science
Lec-32 Recursion -Recursion in Computer ScienceAnil Yadav The document discusses mathematical functions with a focus on recursion, illustrating the calculation of specific values for functions like f(x) and factorials using recursive definitions. It emphasizes the importance of base cases to ensure recursion stops, highlighting examples such as the factorial function and Fibonacci numbers. Properly structured recursion can solve numerous algorithmic problems effectively.
Recursion
RecursionKasun Ranga Wijeweera This document discusses recursion, which is a fundamental concept in computer science and mathematics where a function calls itself. It provides examples of common recursive definitions like factorials and Fibonacci numbers. It explains how recursive programs work by dividing the problem into smaller subproblems until a base case is reached. The document also introduces the "divide and conquer" paradigm where most recursive programs make two recursive calls on halves of the input to solve problems more efficiently than iterative approaches.
CMSC 56 | Lecture 12: Recursive Definition & Algorithms, and Program Correctness
CMSC 56 | Lecture 12: Recursive Definition & Algorithms, and Program Correctnessallyn joy calcaben This document discusses recursive definitions, algorithms, and program correctness. It provides examples of recursively defining functions and sets using a basis step and recursive step. Examples of recursive algorithms are given for computing factorials and exponentials. The difference between recursion and iteration is explained. Program verification and correctness are defined, and examples are worked through to show initial and final assertions for program segments. The document concludes with an announcement about an upcoming exam.
Copy of y16 02-2119divide-and-conquer
Copy of y16 02-2119divide-and-conquerJoepang2015 The document discusses recursive algorithms and divide-and-conquer approaches. It provides examples of recursively defining problems like calculating factorials and solving the Tower of Hanoi puzzle. It also discusses analyzing the time complexity of recursive algorithms by modeling the running time as a recursive function and solving the recursion. The document suggests three methods for solving recurrences: substitution, recursion trees, and the master method.
Recursion
RecursionAbdur Rehman Recursion is a process where an object is defined in terms of smaller versions of itself. It involves a base case, which is the simplest definition that cannot be further reduced, and a recursive case that defines the object for larger inputs in terms of smaller ones until the base case is reached. Examples where recursion is commonly used include defining mathematical functions, number sequences, data structures, and language grammars. While recursion can elegantly solve problems, iterative algorithms are generally more efficient.
Recursion DM
Recursion DMRokonuzzaman Rony The document discusses recursion and recursively defined sequences, functions, and algorithms. It provides examples of recursively defined sequences like powers of 2 and the Fibonacci sequence. Recursively defined functions are given, such as factorials and Fibonacci numbers. Recursive algorithms solve problems by reducing them to smaller instances of the same problem, like the Euclidean algorithm to find the greatest common divisor or a recursive Fibonacci algorithm. While recursive solutions are often shorter and more elegant, iterative algorithms using loops are usually more efficient.
Ad
More from zukun (20)
My lyn tutorial 2009
My lyn tutorial 2009zukun Mylyn helps address information overload and context loss when multi-tasking. It integrates tasks into the IDE workflow and uses a degree-of-interest model to monitor user interaction and provide a task-focused UI with features like view filtering, element decoration, automatic folding and content assist ranking. This creates a single view of all tasks that are centrally managed within the IDE.
ETHZ CV2012: Tutorial openCV
ETHZ CV2012: Tutorial openCVzukun This document provides an overview of OpenCV, an open source computer vision and machine learning software library. It discusses OpenCV's core functionality for representing images as matrices and directly accessing pixel data. It also covers topics like camera calibration, feature point extraction and matching, and estimating camera pose through techniques like structure from motion and planar homography. Hints are provided for Android developers on required permissions and for planar homography estimation using additional constraints rather than OpenCV's general homography function.
ETHZ CV2012: Information
ETHZ CV2012: Informationzukun This document provides information about the Computer Vision Laboratory 2012 course at the Institute of Visual Computing. The course focuses on computer vision on mobile devices and will involve 180 hours of project work per person. Students will work in groups of 1-2 people on topics like 3D reconstruction from silhouettes or stereo images on mobile devices. Key dates are provided for submitting a work plan, mid-term presentation, and final report. Contact information is given for the lecturers and teaching assistant.
Siwei lyu: natural image statistics
Siwei lyu: natural image statisticszukun This document summarizes a presentation on natural image statistics given by Siwei Lyu at the 2009 CIFAR NCAP Summer School. The presentation covered several key topics:
1) It discussed the motivation for studying natural image statistics, which is to understand representations in the visual system and develop computer vision applications like denoising.
2) It reviewed common statistical properties found in natural images like 1/f power spectra and non-Gaussian distributions.
3) Maximum entropy and Bayesian models were presented as approaches to model these statistics, with Gaussian and independent component analysis discussed as specific examples.
4) Efficient coding principles from information theory were introduced as a framework for understanding neural representations that aim to decorrelate and
Lecture9 camera calibration
Lecture9 camera calibrationzukun Camera calibration involves determining the internal camera parameters like focal length, image center, distortion, and scaling factors that affect the imaging process. These parameters are important for applications like 3D reconstruction and robotics that require understanding the relationship between 3D world points and their 2D projections in an image. The document describes estimating internal parameters by taking images of a calibration target with known geometry and solving the equations that relate the 3D target points to their 2D image locations. Homogeneous coordinates and projection matrices are used to represent the calibration transformations mathematically.
Brunelli 2008: template matching techniques in computer vision
Brunelli 2008: template matching techniques in computer visionzukun The document discusses template matching techniques in computer vision. It begins with an overview that defines template matching and discusses some common computer vision tasks it can be used for, like object detection. It then covers topics like detection as hypothesis testing, training and testing techniques, and provides a bibliography.
Modern features-part-4-evaluation
Modern features-part-4-evaluationzukun The HARVEST Programme evaluates feature detectors and descriptors through indirect and direct benchmarks. Indirect benchmarks measure repeatability and matching scores on the affine covariant testbed to evaluate how features persist across transformations. Direct benchmarks evaluate features on image retrieval tasks using the Oxford 5k dataset to measure real-world performance. VLBenchmarks provides software for easily running these benchmarks and reproducing published results. It allows comparing features and selecting the best for a given application.
Modern features-part-3-software
Modern features-part-3-softwarezukun This document summarizes VLFeat, an open source computer vision library. It provides concise summaries of VLFeat's features, including SIFT, MSER, and other covariant detectors. It also compares VLFeat's performance to other libraries like OpenCV. The document highlights how VLFeat achieves state-of-the-art results in tasks like feature detection, description and matching while maintaining a simple MATLAB interface.
Modern features-part-2-descriptors
Modern features-part-2-descriptorszukun This document summarizes and compares local image descriptors. It begins with an introduction to modern descriptors like SIFT, SURF and DAISY. It then discusses efficient descriptors such as binary descriptors like BRIEF, ORB and BRISK which use comparisons of intensity value pairs. The document concludes with an overview section.
Modern features-part-1-detectors
Modern features-part-1-detectorszukun This document discusses various feature detectors used in computer vision. It begins by describing classic detectors such as the Harris detector and Hessian detector that search scale space to find distinguished locations. It then discusses detecting features at multiple scales using the Laplacian of Gaussian and determinant of Hessian. The document also covers affine covariant detectors such as maximally stable extremal regions and affine shape adaptation. It discusses approaches for speeding up detection using approximations like those in SURF and learning to emulate detectors. Finally, it outlines new developments in feature detection.
Modern features-part-0-intro
Modern features-part-0-introzukun The document discusses modern feature detection techniques. It provides an introduction and agenda for a talk on advances in feature detectors and descriptors, including improvements since a 2005 paper. It also discusses software suites and benchmarks for feature detection. Several application domains are described, such as wide baseline matching, panoramic image stitching, 3D reconstruction, image search, location recognition, and object tracking.
Lecture 02 internet video search
Lecture 02 internet video searchzukun System 1 and System 2 were basic early systems for image matching that used color and texture matching. Descriptor-based approaches like SIFT provided more invariance but not perfect invariance. Patch descriptors like SIFT were improved by making them more invariant to lighting changes like color and illumination shifts. The best performance came from combining descriptors with color invariance. Representing images as histograms of visual word occurrences captured patterns in local image patches and allowed measuring similarity between images. Large vocabularies of visual words provided more discriminative power but were costly to compute and store.
Lecture 01 internet video search
Lecture 01 internet video searchzukun This document summarizes a research paper on internet video search. It discusses several key challenges: [1] the large variation in how the same thing can appear in images/videos due to lighting, viewpoint etc., [2] defining what defines different objects, and [3] the huge number of different things that exist. It also notes gaps in narrative understanding, shared concepts between humans and machines, and addressing diverse query contexts. The document advocates developing powerful yet simple visual features that capture uniqueness with invariance to irrelevant changes.
Lecture 03 internet video search
Lecture 03 internet video searchzukun The document discusses computer vision techniques for object detection and localization. It describes methods like selective search that group image regions hierarchically to propose object locations. Large datasets like ImageNet and LabelMe that provide training examples are also discussed. Performance on object detection benchmarks like PASCAL VOC is shown to improve significantly over time. Evaluation standards for concept detection like those used in TRECVID are presented. The document concludes that results are impressively improving each year but that the number of detectable concepts remains limited. It also discusses making feature extraction more efficient using techniques like SURF that take advantage of integral images.
Icml2012 tutorial representation_learning
Icml2012 tutorial representation_learningzukun This document provides an outline and overview of Yoshua Bengio's 2012 tutorial on representation learning. The key points covered include:
1) The tutorial will cover motivations for representation learning, algorithms such as probabilistic models and auto-encoders, and analysis and practical issues.
2) Representation learning aims to automatically learn good representations of data rather than relying on handcrafted features. Learning representations can help address challenges like exploiting unlabeled data and the curse of dimensionality.
3) Deep learning algorithms attempt to learn multiple levels of increasingly complex representations, with the goal of developing more abstract, disentangled representations that generalize beyond local patterns in the data.
Advances in discrete energy minimisation for computer vision
Advances in discrete energy minimisation for computer visionzukun This document discusses string algorithms and data structures. It introduces the Knuth-Morris-Pratt algorithm for finding patterns in strings in O(n+m) time where n is the length of the text and m is the length of the pattern. It also discusses common string data structures like tries, suffix trees, and suffix arrays. Suffix trees and suffix arrays store all suffixes of a string and support efficient pattern matching and other string operations in linear time or O(m+logn) time where m is the pattern length and n is the text length.
Gephi tutorial: quick start
Gephi tutorial: quick startzukun This document provides a tutorial on how to use Gephi software to analyze and visualize network graphs. It outlines the basic steps of importing a sample graph file, applying layout algorithms to organize the nodes, calculating metrics, detecting communities, filtering the graph, and exporting/saving the results. The tutorial demonstrates features of Gephi including node ranking, partitioning, and interactive visualization of the graph.
EM algorithm and its application in probabilistic latent semantic analysis
EM algorithm and its application in probabilistic latent semantic analysiszukun The document discusses the EM algorithm and its application in Probabilistic Latent Semantic Analysis (pLSA). It begins by introducing the parameter estimation problem and comparing frequentist and Bayesian approaches. It then describes the EM algorithm, which iteratively computes lower bounds to the log-likelihood function. Finally, it applies the EM algorithm to pLSA by modeling documents and words as arising from a mixture of latent topics.
Object recognition with pictorial structures
Object recognition with pictorial structureszukun This document describes an efficient framework for part-based object recognition using pictorial structures. The framework represents objects as graphs of parts with spatial relationships. It finds the optimal configuration of parts through global minimization using distance transforms, allowing fast computation despite modeling complex spatial relationships between parts. This enables soft detection to handle partial occlusion without early decisions about part locations.
Iccv2011 learning spatiotemporal graphs of human activities
Iccv2011 learning spatiotemporal graphs of human activities zukun The document presents a new approach for learning spatiotemporal graphs of human activities from weakly supervised video data. The approach uses 2D+t tubes as mid-level features to represent activities as segmentation graphs, with nodes describing tubes and edges describing various relations. A probabilistic graph mixture model is used to model activities, and learning estimates the model parameters and permutation matrices using a structural EM algorithm. The learned models allow recognizing and segmenting activities in new videos through robust least squares inference. Evaluation on benchmark datasets demonstrates the ability to learn characteristic parts of activities and recognize them under weak supervision.
Recently uploaded (20)
Kubernetes Security Act Now Before It’s Too Late
Kubernetes Security Act Now Before It’s Too LateMichael Furman In today's cloud-native landscape, Kubernetes has become the de facto standard for orchestrating containerized applications, but its inherent complexity introduces unique security challenges. Are you one YAML away from disaster?
This presentation, "Kubernetes Security: Act Now Before It’s Too Late," is your essential guide to understanding and mitigating the critical security risks within your Kubernetes environments. This presentation dives deep into the OWASP Kubernetes Top Ten, providing actionable insights to harden your clusters.
We will cover:
The fundamental architecture of Kubernetes and why its security is paramount.
In-depth strategies for protecting your Kubernetes Control Plane, including kube-apiserver and etcd.
Crucial best practices for securing your workloads and nodes, covering topics like privileged containers, root filesystem security, and the essential role of Pod Security Admission.
Don't wait for a breach. Learn how to identify, prevent, and respond to Kubernetes security threats effectively.
It's time to act now before it's too late!
Enabling BIM / GIS integrations with Other Systems with FME
Enabling BIM / GIS integrations with Other Systems with FMESafe Software Jacobs has successfully utilized FME to tackle the complexities of integrating diverse data sources in a confidential $1 billion campus improvement project. The project aimed to create a comprehensive digital twin by merging Building Information Modeling (BIM) data, Construction Operations Building Information Exchange (COBie) data, and various other data sources into a unified Geographic Information System (GIS) platform. The challenge lay in the disparate nature of these data sources, which were siloed and incompatible with each other, hindering efficient data management and decision-making processes.
To address this, Jacobs leveraged FME to automate the extraction, transformation, and loading (ETL) of data between ArcGIS Indoors and IBM Maximo. This process ensured accurate transfer of maintainable asset and work order data, creating a comprehensive 2D and 3D representation of the campus for Facility Management. FME's server capabilities enabled real-time updates and synchronization between ArcGIS Indoors and Maximo, facilitating automatic updates of asset information and work orders. Additionally, Survey123 forms allowed field personnel to capture and submit data directly from their mobile devices, triggering FME workflows via webhooks for real-time data updates. This seamless integration has significantly enhanced data management, improved decision-making processes, and ensured data consistency across the project lifecycle.
Crypto Super 500 - 14th Report - June2025.pdf
Crypto Super 500 - 14th Report - June2025.pdfStephen Perrenod This OrionX's 14th semi-annual report on the state of the cryptocurrency mining market. The report focuses on Proof-of-Work cryptocurrencies since those use substantial supercomputer power to mint new coins and encode transactions on their blockchains. Only two make the cut this time, Bitcoin with $18 billion of annual economic value produced and Dogecoin with $1 billion. Bitcoin has now reached the Zettascale with typical hash rates of 0.9 Zettahashes per second. Bitcoin is powered by the world's largest decentralized supercomputer in a continuous winner take all lottery incentive network.
FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptx
FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptxFIDO Alliance FIDO Seminar: Perspectives on Passkeys & Consumer Adoption
June Patch Tuesday
June Patch TuesdayIvanti Ivanti’s Patch Tuesday breakdown goes beyond patching your applications and brings you the intelligence and guidance needed to prioritize where to focus your attention first. Catch early analysis on our Ivanti blog, then join industry expert Chris Goettl for the Patch Tuesday Webinar Event. There we’ll do a deep dive into each of the bulletins and give guidance on the risks associated with the newly-identified vulnerabilities.
Mastering AI Workflows with FME - Peak of Data & AI 2025
Mastering AI Workflows with FME - Peak of Data & AI 2025Safe Software Harness the full potential of AI with FME: From creating high-quality training data to optimizing models and utilizing results, FME supports every step of your AI workflow. Seamlessly integrate a wide range of models, including those for data enhancement, forecasting, image and object recognition, and large language models. Customize AI models to meet your exact needs with FME’s powerful tools for training, optimization, and seamless integration
PyData - Graph Theory for Multi-Agent Integration
PyData - Graph Theory for Multi-Agent Integrationbarqawicloud Graph theory is a well-known concept for algorithms and can be used to orchestrate the building of multi-model pipelines. By translating tasks and dependencies into a Directed Acyclic Graph, we can orchestrate diverse AI models, including NLP, vision, and recommendation capabilities. This tutorial provides a step-by-step approach to designing graph-based AI model pipelines, focusing on clinical use cases from the field.
National Fuels Treatments Initiative: Building a Seamless Map of Hazardous Fu...
National Fuels Treatments Initiative: Building a Seamless Map of Hazardous Fu...Safe Software The National Fuels Treatments Initiative (NFT) is transforming wildfire mitigation by creating a standardized map of nationwide fuels treatment locations across all land ownerships in the United States. While existing state and federal systems capture this data in diverse formats, NFT bridges these gaps, delivering the first truly integrated national view. This dataset will be used to measure the implementation of the National Cohesive Wildland Strategy and demonstrate the positive impact of collective investments in hazardous fuels reduction nationwide. In Phase 1, we developed an ETL pipeline template in FME Form, leveraging a schema-agnostic workflow with dynamic feature handling intended for fast roll-out and light maintenance. This was key as the initiative scaled from a few to over fifty contributors nationwide. By directly pulling from agency data stores, oftentimes ArcGIS Feature Services, NFT preserves existing structures, minimizing preparation needs. External mapping tables ensure consistent attribute and domain alignment, while robust change detection processes keep data current and actionable. Now in Phase 2, we’re migrating pipelines to FME Flow to take advantage of advanced scheduling, monitoring dashboards, and automated notifications to streamline operations. Join us to explore how this initiative exemplifies the power of technology, blending FME, ArcGIS Online, and AWS to solve a national business problem with a scalable, automated solution.
Artificial Intelligence in the Nonprofit Boardroom.pdf
Artificial Intelligence in the Nonprofit Boardroom.pdfOnBoard OnBoard recently partnered with Microsoft Tech for Social Impact on the AI in the Nonprofit Boardroom Survey, an initiative designed to uncover the current and future role of artificial intelligence in nonprofit governance.
Agentic AI: Beyond the Buzz- LangGraph Studio V2
Agentic AI: Beyond the Buzz- LangGraph Studio V2Shashikant Jagtap Presentation given at the LangChain community meetup London
https://lu.ma/9d5fntgj
Coveres
Agentic AI: Beyond the Buzz
Introduction to AI Agent and Agentic AI
Agent Use case and stats
Introduction to LangGraph
Build agent with LangGraph Studio V2
Reducing Conflicts and Increasing Safety Along the Cycling Networks of East-F...
Reducing Conflicts and Increasing Safety Along the Cycling Networks of East-F...Safe Software In partnership with the Belgian Province of East-Flanders this project aimed to reduce conflicts and increase safety along a cycling route between the cities of Oudenaarde and Ghent. To achieve this goal, the current cycling network data needed some extra key information, including: Speed limits for segments, Access restrictions for different users (pedestrians, cyclists, motor vehicles, etc.), Priority rules at intersections. Using a 360° camera and GPS mounted on a measuring bicycle, we collected images of traffic signs and ground markings along the cycling lanes building up mobile mapping data. Image recognition technologies identified the road signs, creating a dataset with their locations and codes. The data processing entailed three FME workspaces. These included identifying valid intersections with other networks (e.g., roads, railways), creating a topological network between segments and intersections and linking road signs to segments and intersections based on proximity and orientation. Additional features, such as speed zones, inheritance of speed and access to neighbouring segments were also implemented to further enhance the data. The final results were visualized in ArcGIS, enabling analysis for the end users. The project provided them with key insights, including statistics on accessible road segments, speed limits, and intersection priorities. These will make the cycling paths more safe and uniform, by reducing conflicts between users.
No-Code Workflows for CAD & 3D Data: Scaling AI-Driven Infrastructure
No-Code Workflows for CAD & 3D Data: Scaling AI-Driven InfrastructureSafe Software When projects depend on fast, reliable spatial data, every minute counts.
AI Clearing needed a faster way to handle complex spatial data from drone surveys, CAD designs and 3D project models across construction sites. With FME Form, they built no-code workflows to clean, convert, integrate, and validate dozens of data formats – cutting analysis time from 5 hours to just 30 minutes.
Join us, our partner Globema, and customer AI Clearing to see how they:
-Automate processing of 2D, 3D, drone, spatial, and non-spatial data
-Analyze construction progress 10x faster and with fewer errors
-Handle diverse formats like DWG, KML, SHP, and PDF with ease
-Scale their workflows for international projects in solar, roads, and pipelines
If you work with complex data, join us to learn how to optimize your own processes and transform your results with FME.
Edge-banding-machines-edgeteq-s-200-en-.pdf
Edge-banding-machines-edgeteq-s-200-en-.pdfAmirStern2 מכונת קנטים המתאימה לנגריות קטנות או גדולות (כמכונת גיבוי).
מדביקה קנטים מגליל או פסים, עד עובי קנט – 3 מ"מ ועובי חומר עד 40 מ"מ. בקר ממוחשב המתריע על תקלות, ומנועים מאסיביים תעשייתיים כמו במכונות הגדולות.
Oracle Cloud and AI Specialization Program
Oracle Cloud and AI Specialization ProgramVICTOR MAESTRE RAMIREZ Oracle Cloud and AI Specialization Program
Bridging the divide: A conversation on tariffs today in the book industry - T...
Bridging the divide: A conversation on tariffs today in the book industry - T...BookNet Canada A collaboration-focused conversation on the recently imposed US and Canadian tariffs where speakers shared insights into the current legislative landscape, ongoing advocacy efforts, and recommended next steps. This event was presented in partnership with the Book Industry Study Group.
Link to accompanying resource: https://bnctechforum.ca/sessions/bridging-the-divide-a-conversation-on-tariffs-today-in-the-book-industry/
Presented by BookNet Canada and the Book Industry Study Group on May 29, 2025 with support from the Department of Canadian Heritage.
FME for Good: Integrating Multiple Data Sources with APIs to Support Local Ch...
FME for Good: Integrating Multiple Data Sources with APIs to Support Local Ch...Safe Software Have-a-skate-with-Bob (HASB-KC) is a local charity that holds two Hockey Tournaments every year to raise money in the fight against Pancreatic Cancer. The FME Form software is used to integrate and exchange data via API, between Google Forms, Google Sheets, Stripe payments, SmartWaiver, and the GoDaddy email marketing tools to build a grass-roots Customer Relationship Management (CRM) system for the charity. The CRM is used to communicate effectively and readily with the participants of the hockey events and most importantly the local area sponsors of the event. Communication consists of a BLOG used to inform participants of event details including, the ever-important team rosters. Funds raised by these events are used to support families in the local area to fight cancer and support PanCan research efforts to find a cure against this insidious disease. FME Form removes the tedium and error-prone manual ETL processes against these systems into 1 or 2 workbenches that put the data needed at the fingertips of the event organizers daily freeing them to work on outreach and marketing of the events in the community.
cnc-drilling-dowel-inserting-machine-drillteq-d-510-english.pdf
cnc-drilling-dowel-inserting-machine-drillteq-d-510-english.pdfAmirStern2 CNC מכונות קידוח drillteq d-510
MuleSoft for AgentForce : Topic Center and API Catalog
MuleSoft for AgentForce : Topic Center and API Catalogshyamraj55 This presentation dives into how MuleSoft empowers AgentForce with organized API discovery and streamlined integration using Topic Center and the API Catalog. Learn how these tools help structure APIs around business needs, improve reusability, and simplify collaboration across teams. Ideal for developers, architects, and business stakeholders looking to build a connected and scalable API ecosystem within AgentForce.
High Availability On-Premises FME Flow.pdf
High Availability On-Premises FME Flow.pdfSafe Software FME Flow is a highly robust tool for transforming data both automatically and by user-initiated workflows. At the Finnish telecommunications company Elisa, FME Flow serves processes and internal stakeholders that require 24/7 availability from underlying systems, while imposing limitations on the use of cloud based systems. In response to these business requirements, Elisa has implemented a high-availability on-premises setup of FME Flow, where all components of the system have been duplicated or clustered. The goal of the presentation is to provide insights into the architecture behind the high-availability functionality. The presentation will show in basic technical terms how the different parts of the system work together. Basic level understanding of IT technologies is required to understand the technical portion of the presentation, namely understanding the purpose of the following components: load balancer, FME Flow host nodes, FME Flow worker nodes, network file storage drives, databases, and external authentication services. The presentation will also outline our lessons learned from the high-availability project, both benefits and challenges to consider.
“Why It’s Critical to Have an Integrated Development Methodology for Edge AI,...
“Why It’s Critical to Have an Integrated Development Methodology for Edge AI,...Edge AI and Vision Alliance For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2025/06/why-its-critical-to-have-an-integrated-development-methodology-for-edge-ai-a-presentation-from-lattice-semiconductor/
Sreepada Hegade, Director of ML Systems and Software at Lattice Semiconductor, presents the “Why It’s Critical to Have an Integrated Development Methodology for Edge AI” tutorial at the May 2025 Embedded Vision Summit.
The deployment of neural networks near sensors brings well-known advantages such as lower latency, privacy and reduced overall system cost—but also brings significant challenges that complicate development. These challenges can be addressed effectively by choosing the right solution and design methodology. The low-power FPGAs from Lattice are well poised to enable efficient edge implementation of models, while Lattice’s proven development methodology helps to mitigate the challenges and risks associated with edge model deployment.
In this presentation, Hegade explains the importance of an integrated framework that tightly consolidates different aspects of edge AI development, including training, quantization of networks for edge deployment, integration with sensors and inferencing. He also illustrates how Lattice’s simplified tool flow helps to achieve the best trade-off between power, performance and efficiency using low-power FPGAs for edge deployment of various AI workloads.
“Why It’s Critical to Have an Integrated Development Methodology for Edge AI,...
“Why It’s Critical to Have an Integrated Development Methodology for Edge AI,...Edge AI and Vision Alliance
Skiena algorithm 2007 lecture16 introduction to dynamic programming
- 1. Lecture 16: Introduction to Dynamic Programming Steven Skiena Department of Computer Science State University of New York Stony Brook, NY 11794–4400 http://www.cs.sunysb.edu/∼skiena
- 2. Problem of the Day Multisets are allowed to have repeated elements. A multiset of n items may thus have fewer than n! distinct permutations. For example, {1, 1, 2, 2} has only six different permutations: {1, 1, 2, 2}, {1, 2, 1, 2}, {1, 2, 2, 1}, {2, 1, 1, 2}, {2, 1, 2, 1}, and {2, 2, 1, 1}. Design and implement an efficient algorithm for constructing all permutations of a multiset.
- 3. Dynamic Programming Dynamic programming is a very powerful, general tool for solving optimization problems on left-right-ordered items such as character strings. Once understood it is relatively easy to apply, it looks like magic until you have seen enough examples. Floyd’s all-pairs shortest-path algorithm was an example of dynamic programming.
- 4. Greedy vs. Exhaustive Search Greedy algorithms focus on making the best local choice at each decision point. In the absence of a correctness proof such greedy algorithms are very likely to fail. Dynamic programming gives us a way to design custom algorithms which systematically search all possibilities (thus guaranteeing correctness) while storing results to avoid recomputing (thus providing efficiency).
- 5. Recurrence Relations A recurrence relation is an equation which is defined in terms of itself. They are useful because many natural functions are easily expressed as recurrences: Polynomials: an = an−1 + 1, a1 = 1 −→ an = n Exponentials: an = 2an−1 , a1 = 2 −→ an = 2n Weird: an = nan−1 , a1 = 1 −→ an = n! Computer programs can easily evaluate the value of a given recurrence even without the existence of a nice closed form.
- 6. Computing Fibonacci Numbers Fn = Fn−1 + Fn−2, F0 = 0, F1 = 1 Implementing this as a recursive procedure is easy, but slow because we keep calculating the same value over and over. F(6)=13 F(5) F(4) F(4) F(3) F(3) F(2) F(2) F(1) F(2) F(1) F(1) F(0) F(3) F(2) F(2) F(1) F(1) F(1) F(0) F(0) F(1) F(0) F(1) F(0)
- 7. How Slow? √ Fn+1/Fn ≈ φ = (1 + 5)/2 ≈ 1.61803 Thus Fn ≈ 1.6n . Since our recursion tree has 0 and 1 as leaves, computing Fn requires ≈ 1.6n calls!
- 8. What about Dynamic Programming? We can calculate Fn in linear time by storing small values: F0 = 0 F1 = 1 For i = 1 to n Fi = Fi−1 + Fi−2 Moral: we traded space for time.
- 9. Why I Love Dynamic Programming Dynamic programming is a technique for efficiently comput- ing recurrences by storing partial results. Once you understand dynamic programming, it is usually easier to reinvent certain algorithms than try to look them up! I have found dynamic programming to be one of the most useful algorithmic techniques in practice: • Morphing in computer graphics. • Data compression for high density bar codes. • Designing genes to avoid or contain specified patterns.
- 10. Avoiding Recomputation by Storing Partial Results The trick to dynamic program is to see that the naive recursive algorithm repeatedly computes the same subproblems over and over and over again. If so, storing the answers to them in a table instead of recomputing can lead to an efficient algorithm. Thus we must first hunt for a correct recursive algorithm – later we can worry about speeding it up by using a results matrix.
- 11. Binomial Coefficients The most important class of counting numbers are the binomial coefficients, where ( ) counts the number of ways n k to choose k things out of n possibilities. • Committees – How many ways are there to form a k- member committee from n people? By definition, ( ). n k • Paths Across a Grid – How many ways are there to travel from the upper-left corner of an n × m grid to the lower- right corner by walking only down and to the right? Every path must consist of n + m steps, n downward and m to the right, so there are ( ) such sets/paths. n+m n
- 12. Computing Binomial Coefficients Since ( ) = n!/((n − k)!k!), in principle you can compute n k them straight from factorials. However, intermediate calculations can easily cause arith- metic overflow even when the final coefficient fits comfort- ably within an integer.
- 13. Pascal’s Triangle No doubt you played with this arrangement of numbers in high school. Each number is the sum of the two numbers directly above it: 1 11 121 1331 14641 1 5 10 10 5 1
- 14. Pascal’s Recurrence A more stable way to compute binomial coefficients is using the recurrence relation implicit in the construction of Pascal’s triangle, namely, that ()=( )+( ) n k n−1 k−1 n−1 k It works because the nth element either appears or does not appear in one of the ( ) subsets of k elements. n k
- 15. Basis Case No recurrence is complete without basis cases. How many ways are there to choose 0 things from a set? Exactly one, the empty set. The right term of the sum drives us up to ( ). How many ways k k are there to choose k things from a k-element set? Exactly one, the complete set.
- 16. Binomial Coefficients Implementation long binomial coefficient(n,m) int n,m; (* compute n choose m *) { int i,j; (* counters *) long bc[MAXN][MAXN]; (* table of binomial coefficients *) for (i=0; i<=n; i++) bc[i][0] = 1; for (j=0; j<=n; j++) bc[j][j] = 1; for (i=1; i<=n; i++) for (j=1; j<i; j++) bc[i][j] = bc[i-1][j-1] + bc[i-1][j]; return( bc[n][m] ); }
- 17. Three Steps to Dynamic Programming 1. Formulate the answer as a recurrence relation or recursive algorithm. 2. Show that the number of different instances of your recurrence is bounded by a polynomial. 3. Specify an order of evaluation for the recurrence so you always have what you need.