
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
Authentication Bypass using SQL Injection on Login Page
SQL Injection is a common security vulnerability. It occurs when an attacker manipulates a web application's database queries by injecting malicious SQL code. One of the most critical areas for SQL Injection exploitation is the login page of an application. When a user enters their credentials, these inputs are typically used to construct a database query to verify the user's identity.
If the application does not properly sanitize these inputs, an attacker can bypass authentication by injecting SQL statements that modify the intended query, granting them unauthorized access.
What is SQL Injection?
SQL injection is a code injection technique that exploits vulnerabilities in an application's software by inserting or "injecting" SQL queries through input fields.
When user input is not properly sanitized, an attacker can manipulate SQL queries executed by the database, potentially gaining unauthorized access to data.
Mechanism of SQL Injection in Login Pages
Consider a simple login form where users enter their username and password. The back end might execute an SQL query like this.
SELECT * FROM users WHERE username = 'username' AND password = 'password';
If the application doesn't properly sanitize the "$username" and "$password" inputs, an attacker can inject malicious SQL code to manipulate the query.
We need to be cautious while performing SQL injection attacks and obtain proper permission from the website owners or mentors. In some cases, it can lead to data loss.
Sample SQL Injection Attack
For this illustration, we used Portswigger Lab. To perform SQL Injection you need to install Burp-suite. Depending on your convenience you can install either the Community Edition or the Professional Edition.
Lab Link: https://portswigger.net/web-security/sql-injection/lab-login-bypass
Burpsuite Link: https://portswigger.net/burp/communitydownload
Follow the steps given below ?
Step 1: Open a website that contains a Login Page.
Step 2: Type "administrator" in the Username field and any random password such as "admin".

Step 3: Open Burp suite and capture the current Login Request. You should see 200 OK in the Interceptor.

Step 4: In the background, the SQL query will looks like this:

Step 5: Here, "users" is the table name, that contains the username and password in the database.

Step 6: Now, if you submit the request you will receive an error in the Login window stating "Invalid username or Password".

Step 7: If the username field contains a single quote, it will trigger an error when the query is executed.

Step 8: The application generates a 500 Internal Server Error in the Interceptor and an Invalid username or Password error in the HTTP response.

Step 9: Now, the actual SQL Payload looks like " administrator'-- ".

Step 10: The -- sequence is used as a comment delimiter in SQL. When an attacker injects -- into a query, it instructs the SQL database to ignore the rest of the line. This is useful for manipulating the intended SQL query.

Step 11: After a successful login, users can access their account in the My Account dashboard.
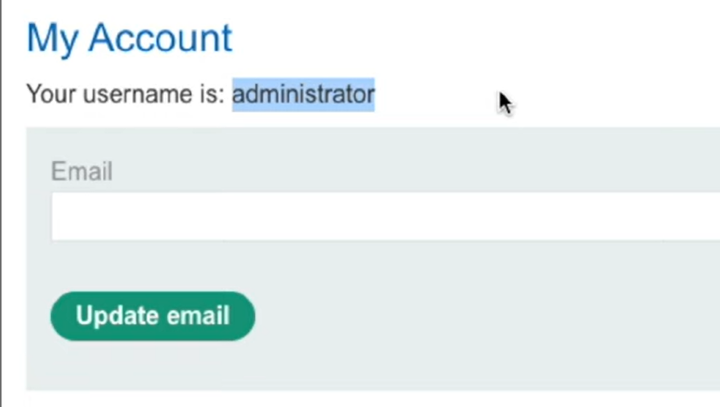
Here's how this manipulation works ?
- The condition '1'='1' always evaluates to true.
- The -- comments out the rest of the SQL statement, effectively bypassing the password check.
- This can lead to unauthorized access, as the query returns a valid user record.
Common SQL Injection Techniques on Login Pages:
- Error-Based Attacks
- Union-Based Attacks
- Time-Based Attacks
Preventing SQL Injection on Login Pages
You can prevent SQL Injection on Login Pages by following these steps?
- Parameterized Queries: Prepared statements ensure that user input is treated as data rather than executable code.
- Input Validation: Always validate and sanitize user inputs. Use regular expressions to allow only expected formats (e.g., alphanumeric characters for usernames).
- Utilize ORM Frameworks: Use Object-Relational Mapping (ORM) tools, such as Entity Framework or Hibernate. These tools automatically handle query generation safely. Reducing the risk of injection.
Employ Web Application Firewalls (WAF)
A WAF can help filter and monitor HTTP requests to detect and block SQL injection attempts.
Conclusion
In summary, SQL Injection poses a significant risk, particularly in login functionalities. By exploiting this vulnerability, attackers can bypass authentication and gain access to sensitive information or systems.
- To protect against SQL Injection attacks, developers should implement robust input validation, utilize parameterized queries, and regularly test applications for vulnerabilities.
- By taking these measures, the security of web applications can be significantly improved.
- Additionally, ensuring that only authorized users have access sensitive data.
