Secure coding | XSS Attacks on current Web Applications
- 1. Cross-Site Scripting Attacks on Current Web Applications
- 2. Introduction An attacker gets control of the user’s browser in order to execute a malicious script within the context of trust of the web application’s site. As a result, and if the embedded code is successfully executed, the attacker might then be able to access, passively or actively, to any sensitive browser resource associated to the web application (e.g., cookies, session IDs, etc.)
- 3. THREATS!!! Everything from account hijacking, changing of user settings, cookie theft/poisoning, or false advertising is possible. Steal cookies which can then be used to impersonate customer and have access to their data and privileges. This is also known as Session Hijacking. Redirect the user to another website of their choosing. Maybe one that may be quite offensive, or one that attempts to install malware onto users computer; Display alternate content on your own website.
- 4. History of Attacks October 2001, -----Hotmail ---- Remote attacker was allowed to steal .NET Passport identifiers of Hotmail’s users by collecting their cookies. October 2005, ------ MySpace, utilized by the worm Samy to propagate itself across MySpace’s user profiles. November 2006,Orkut, was vulnerable to cookie stealing by simply posting the stealing script into the attacker’s profile.
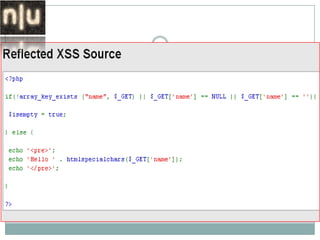
- 7. User input is reflected immediately on the page by server-side scripts without proper sanitization. To exploit, the attacker has to provide the victim with a modified URL, passing the code to be inserted as a parameter. This attack is done by encoding data in the URL, thus disguising the injected code from the user.
- 10. Persistent XSS Attacks When the data entered by the user are stored on the server for a certain length of time, the attack is called "persistent". All of the website's users have access to the page where the harmful code was introduced. Commonly found in: Contact/Feedback pages, Log viewers, Exception handlers, Chat applications/Forums, etc.
- 12. BACHAA V !!!
- 14. No Protection
- 15. Data Validation Application accepts correct data. User data must be validated to ensure it is of the corrected type, and discarded if it doesn’t pass the validation process. Allow a limited set of special characters.
- 16. Preg Match Performs a regular expression match.
- 17. Output Escaping Protects integrity of displayed/output data, Should escape the data when presenting it to the user. Prevents the browser from applying any unintended meaning to any special sequence of characters that may be found.
- 18. htmlspecialchars
- 20. Data Sanitization Manipulating the data to make sure it is safe. Removing any unwanted bits from the data and normalizing it to the correct form.
- 23. htmlentities Converts all applicable characters to HTML entities. Default value for this argument is ISO-8859-1 in versions of PHP prior to 5.4.0, and UTF-8 from PHP 5.4.0 onwards. ** http://coderstoolbox.net/
- 25. Available flags constants ID Description ENT_COMPAT Will convert double-quotes and leave single-quotes alone. ENT_QUOTES Will convert both double and single quotes. ENT_NOQUOTES Will leave both double and single quotes unconverted.
- 26. ID Flags FILTER_SANITIZE_EM AIL FILTER_SANITIZE_EN CODED Remove all characters except letters, digits and !#$%&'*+/=?^_`{|}~@.[]. FILTER_FLAG_STRIP_LOW , FILTER_FLAG_STRIP_HIG H, FILTER_FLAG_ENCODE_L OW, FILTER_FLAG_ENCODE_HI GH URL-encode string, optionally strip or encode special characters. Apply addslashes(). FILTER_SANITIZE_MAGIC _QUOTES FILTER_SANITIZE_NUMB ER_FLOAT Description FILTER_FLAG_ALLOW_FR ACTION, FILTER_FLAG_ALLOW_TH Remove all characters except digits, +- and optionally .,eE.
- 27. ID Flags FILTER_SANITIZE _NUMBER_INT Description Remove all characters except digits, plus and minus sign. FILTER_SANITIZE _SPECIAL_CHARS FILTER_FLAG_STRIP_LOW, FILTER_FLAG_STRIP_HIGH, FILTER_FLAG_ENCODE_HIGH HTMLescape '"<>& and characters with ASCII value less than 32, optionally strip or encode other special characters. FILTER_SANITIZE _STRING FILTER_FLAG_NO_ENCODE_Q UOTES, FILTER_FLAG_STRIP_LOW, FILTER_FLAG_STRIP_HIGH, FILTER_FLAG_ENCODE_LOW, FILTER_FLAG_ENCODE_HIGH, FILTER_FLAG_ENCODE_AMP Strip tags, optionally strip or encode special characters. FILTER_SANITIZE _STRIPPED Alias of "string" filter.
- 28. ID Flags FILTER_SANITIZE_UR L Description Remove all characters except letters, digits and $_.+!*'(),{}|^~[]`<> #%";/?:@&=. FILTER_UNSAFE_RA W FILTER_FLAG_STRIP_LOW Do nothing, optionally , strip or encode special FILTER_FLAG_STRIP_HIG characters. H, FILTER_FLAG_ENCODE_L OW, FILTER_FLAG_ENCODE_HI GH, FILTER_FLAG_ENCODE_A MP FILTER_SANITIZE_FU LL_SPECIAL_CHARS FILTER_FLAG_NO_ENCOD E_QUOTES, Equivalent to callinghtmlspecialchar s() withENT_QUOT ES set. Encoding quotes can be disabled
- 29. Mod Security(Web Application Firewall) Protects against attacks that target websites. csrf_protection session_hijacking comment_spam authentication_tracking protocol_violations sql_injection_attacks xss_attacks brute_force, and many more
- 33. How to change Contact info Go to : • binariesapacheerror • Open contact.html.var
- 34. Modified Code Change contact information
- 35. Disable Apache Signature and/or Apache Banner ADD in httpd.config of apache to remove apache version disclosure ServerTokens ProductOnly ServerTokens takes 1 argument, 'Prod', 'Major', 'Minor', 'Min', 'OS', or 'Full'""
- 36. Before After
- 37. ADD/replace/change in php.ini to remove php version disclosure expose_php = Off display_errors=Off register_globals = Off
- 39. Disable Version Disclosure Go to : • binariesapacheerrorinclude • Open bottom.html By Default we see this
- 42. My customized error page !!
- 43. Stopping Sensitive file disclosure Turn off automatic indexing. Instruct Apache to reject all requests for files matching a series of regular expressions given below. Goto httpd.conf file to deny access to . htaccess files.
- 44. Protecting bakup files Add in httpd.config TheFilesMatchdirective only looks at the last part of the full filename
- 45. Disable Directory Indexing Listing of files like see in Windows Explorer as opposed to a web page. Attacker can gain valuable information about your site. Files may may include sensitive information, such as backup script files htaccess files, or text files with note. Can allow access files outside the web root directory, leading to the stealing of system files.
- 46. How to Disable Directory Listings in Apache Navigate to your Apache config file (httpd.conf) Find – “Options FollowSymLinks Indexes” Replace by – “Options FollowSymLinks” Done
- 47. FollowSymLinks makes Apache follow system symbolic links (shortcuts, if you would) in your file system. Indexes allows access to open folders within your file system.
- 49. Disable powerful functions in php Disable functions that may be useful to an attacker but not necessary to the application. Disable execution of OS commands Open php.ini and search “disable_functions”. Write “shell_exec “ (without comma in front of disable_functions).
- 51. Other functions exec, passthru, shell_exec, system, proc_open, popen, curl_exec, curl_multi_exec, pcntl_exec, dl". If the application needs to execute OS commands, it should use "pcntl_exec", because it provides better abstraction of parameters than the others.
























![ID
Flags
FILTER_SANITIZE_EM
AIL
FILTER_SANITIZE_EN
CODED
Remove all characters
except letters, digits
and !#$%&'*+/=?^_`{|}~@.[].
FILTER_FLAG_STRIP_LOW
,
FILTER_FLAG_STRIP_HIG
H,
FILTER_FLAG_ENCODE_L
OW,
FILTER_FLAG_ENCODE_HI
GH
URL-encode string,
optionally strip or
encode special
characters.
Apply addslashes().
FILTER_SANITIZE_MAGIC
_QUOTES
FILTER_SANITIZE_NUMB
ER_FLOAT
Description
FILTER_FLAG_ALLOW_FR
ACTION,
FILTER_FLAG_ALLOW_TH
Remove all characters
except digits, +- and
optionally .,eE.](https://image.slidesharecdn.com/securecoding-140225042400-phpapp01/85/Secure-coding-XSS-Attacks-on-current-Web-Applications-26-320.jpg)

![ID
Flags
FILTER_SANITIZE_UR
L
Description
Remove all characters
except letters, digits
and $_.+!*'(),{}|^~[]`<>
#%";/?:@&=.
FILTER_UNSAFE_RA
W
FILTER_FLAG_STRIP_LOW Do nothing, optionally
,
strip or encode special
FILTER_FLAG_STRIP_HIG characters.
H,
FILTER_FLAG_ENCODE_L
OW,
FILTER_FLAG_ENCODE_HI
GH,
FILTER_FLAG_ENCODE_A
MP
FILTER_SANITIZE_FU
LL_SPECIAL_CHARS
FILTER_FLAG_NO_ENCOD
E_QUOTES,
Equivalent to
callinghtmlspecialchar
s() withENT_QUOT
ES set. Encoding
quotes can be disabled](https://image.slidesharecdn.com/securecoding-140225042400-phpapp01/85/Secure-coding-XSS-Attacks-on-current-Web-Applications-28-320.jpg)
























