routing algorithms in computer Networks.ppt
- 1. COMPUTER NETWORKS Networking Standards (Network LAYER) Network Layer
- 2. Computer Networks 2 Question to be answered ? What is the main goal of Network layer? How does Network layer achieve its goal? Network Layer
- 3. Computer Networks 3 Network Layer - The network layer is concerned with getting packets from the source all the way to the destination. - Therefore, the main function (goal) of network layer is routing packets from the source machine to the destination machine. Network Layer
- 4. Computer Networks 4 To achieve its goal the network layer must: 1- Know about the topology of the communication subnet. 2- Choose appropriate paths through the subnet. 3- Avoid overloaded communication lines and routers (avoid congestion). Network Layer
- 5. Store-and-Forward Packet Switching The environment of the network layer protocols. fig 5-1
- 6. Computer Networks 6 Store-and-Forwarding Packet Switching In Store-and Forwarding Packet Switching mechanism, a host transmits a packet to the nearest router, the packet is stored there until it has fully arrived so the checksum can be verified, then it is forwarded to the next router along the path until it reaches the destination host. Network Layer
- 7. Computer Networks 7 Services provided to the Transport Layer There are two services provided by the network layer to the transport layer: 1) Connectionless service. 2) Connection-Oriented Service. Network Layer
- 8. Implementation of Connectionless Service Routing within a diagram subnet.
- 9. Implementation of Connection-Oriented Service Routing within a virtual-circuit subnet.
- 10. Comparison of Virtual-Circuit and Datagram Subnets 5-4
- 11. Computer Networks 11 Routing Algorithms In most subnets, packets require multiple hops to reach their destinations. The Routing algorithm is the software part of the network layer responsible for deciding which output line an incoming packet should be transmitted on. Network Layer
- 12. Computer Networks 12 Routing Algorithms The decision about the best route either calculated once as the case with connection-oriented paradigm or for every arriving data packet in the case of the subnet uses connectionless paradigm. Network Layer
- 13. Computer Networks 13 Routing Algorithms Desirable properties in a routing algorithm: 1) Correctness 2) Simplicity 3) Robustness (hardware or software failures) 4) Stability (to be run for long time) 5) Fairness 6) Optimality Network Layer
- 14. Routing Algorithms Conflict between fairness and optimality.
- 15. The Optimality Principle (a) A subnet. (b) A sink tree for router B.
- 16. Computer Networks 16 Routing Algorithms Routing Algorithms can be grouped in two major classes: 1) Non-adaptive algorithms (Static Routing) 2) Adaptive algorithms (Dynamic Routing) Network Layer
- 17. Computer Networks 17 Routing Algorithms 1) Non-adaptive algorithms, they do not base their routing decision on measurements or estimates of the current traffic and topology. Instead the route is computed in advance, off-line, and downloaded to the routers when the network is booted. Network Layer
- 18. Computer Networks 18 Routing Algorithms 2) Adaptive algorithms, they change their routing decisions to reflect changes in the topology, and usually the traffic as well. - Adaptive algorithms differ in where they get their information. Network Layer
- 19. Computer Networks 19 Routing Algorithms - What metric is used for optimization? - Distance - number of hops - estimated transit time - delay - bandwidth Network Layer
- 20. Computer Networks 20 Shortest Path Routing - The technique that is used in many routing algorithms is simple and easy to understand. - The idea is to build a graph of the subnet, with each node of the graph representing a router and each arc of the graph representing a communication line (link). To choose a route between a given pair of routers, the algorithm just finds the shortest path between them on the graph. Network Layer
- 21. Computer Networks 21 Shortest Path Routing Network Layer A B E F C D H G 2 7 3 3 2 2 2 6 1 2 4 Metric is number of hops - The path ABC is equal to path ABE. Metric is the distance in km - the path ABC is longer than the path ABE
- 22. Computer Networks 22 Shortest Path Routing There are several algorithms to compute the shortest path between two nodes of a graph. The most popular is Dijkstra algorithm. In this algorithm each node is labeled (in parentheses) with its distance from the source node along the best known path. Network Layer
- 24. Computer Networks 24 Shortest Path Routing - In Flooding Algorithm every packet is sent out on every outgoing line except the one it arrived on. - Timer is used to stop (limit) this flooding which can be a hop counter. - A practical selective flooding algorithm is used where the packets are sent only to the approximately in the right direction. - It is suitable for military applications. Network Layer
- 25. Collection of Subnetworks The Internet is an interconnected collection of many networks.
- 26. 3 Distance Vector Routing (1) (a) A subnet. (b) Input from A, I, H, K, and the new routing table for J.
- 27. 3 Distance Vector Routing (2) The count-to-infinity problem.
- 28. 3 Distance Vector Routing (3): Loop- Breaking Heuristics Set infinity to a limited number, e.g. 16. Split horizon Split horizon with poison reverse
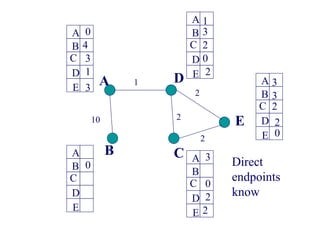
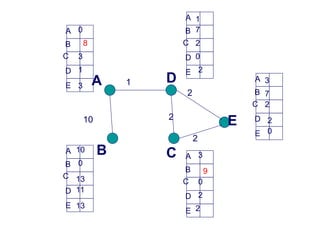
- 29. 1 10 2 2 2 A B C E D A C E B D A C E B D A C E B D A C E B D A C E B D 0 0 0 0 0 Initialization 3 Example:
- 31. 1 10 2 2 2 A B C E D A C E B D A C E B D A C E B D A C E B D A C E B D 0 0 0 0 0 10 1 10 2 2 2 2 2 2 1 3 3 11 3 3 11 Neighbours of neighbours
- 32. 1 10 2 2 2 A B C E D A C E B D A C E B D A C E B D A C E B D A C E B D 0 0 0 0 0 10 1 10 2 2 2 2 2 2 1 3 3 11 3 3 11 13 13 13 13 Neighbours of neighbours of neighbours
- 34. 1 10 2 2 2 A B C E D A C E B D A C E B D A C E B D A C E B D A C E B D 0 0 0 0 0 10 1 10 2 2 2 2 2 2 1 3 3 11 3 3 11 13 13 13 13 1 Good news: A new link!
- 37. 1 10 2 2 2 A B C E D A C E B D A C E B D A C E B D A C E B D A C E B D 0 0 0 0 0 4 1 4 2 2 2 2 2 2 1 3 3 3 3 3 3 1 3 1 3 1 Neighbours of neighbours know
- 38. 1 10 2 2 2 A B C E D A C E B D A C E B D A C E B D A C E B D A C E B D 0 0 0 0 0 4 1 4 2 2 2 2 2 2 1 3 3 3 3 3 3 1 3 1 3 1 A happy and stable network
- 39. 1 10 2 2 2 A B C E D A C E B D A C E B D A C E B D A C E B D A C E B D 0 0 0 0 0 4 1 4 2 2 2 2 2 2 1 3 3 3 3 3 3 1 3 1 3 Bad news: Link crash!!
- 42. 1 10 2 2 2 A B C E D A C E B D A C E B D A C E B D A C E B D A C E B D 0 0 0 0 0 4 1 2 2 2 2 2 2 1 3 3 3 3 3 3 10 5 13 11 13 Get help from neighbours
- 43. 1 10 2 2 2 A B C E D A C E B D A C E B D A C E B D A C E B D A C E B D 0 0 0 0 0 4 1 2 2 2 2 2 2 1 3 3 3 3 7 7 10 5 13 11 13 Routing loop (due to inconsistent state info)
- 49. 4 Link State Routing (1) Each router must do the following: • Discover its neighbors, learn their network address. • Measure the delay or cost to each of its neighbors. • Construct a packet telling all it has just learned. • Send this packet to all other routers. • Compute the shortest path to every other router.
- 50. 4 Link State Routing (2): Learning about the Neighbors (a) Nine routers and a LAN. (b) A graph model of (a).
- 51. 4 Link State Routing (3): Measuring Line Cost A subnet in which the East and West parts are connected by two lines.
- 52. 4 Link State Routing (4): Building Link State Packets (a) A subnet. (b) The link state packets for this subnet.
- 53. 4 Link State Routing (5): Distributing the Link State Packets The packet buffer for router B in the previous slide (Fig. 5-13).
- 54. 5 Hierarchical Routing Hierarchical routing.
- 55. 6. Routing in Ad Hoc Networks (1) Possibilities when the routers are mobile: Military vehicles on battlefield. • No infrastructure. A fleet of ships at sea. • All moving all the time Emergency works at earthquake . • The infrastructure destroyed. A gathering of people with notebook computers. • In an area lacking 802.11.
- 56. 6. Routing in Ad Hoc Networks (2): Route Discovery (a) Range of A's broadcast. (b) After B and D have received A's broadcast. (c) After C, F, and G have received A's broadcast. (d) After E, H, and I have received A's broadcast. Shaded nodes are new recipients. Arrows show possible reverse routes.
- 57. 6. Routing in Ad Hoc Networks (3): Route Discovery Format of a ROUTE REQUEST packet.
- 58. 6. Routing in Ad Hoc Networks (4): Route Discovery Format of a ROUTE REPLY packet.
- 59. 6. Routing in Ad Hoc Networks (5): Route Maintenance (a) D's routing table before G goes down. (b) The graph after G has gone down.
- 60. 4. RIP ( Routing Information Protocol) (1) Distance vector algorithm Included in BSD-UNIX Distribution in 1982 Distance metric: # of hops (max = 15 hops) D C B A u v w x y z destination hops u 1 v 2 w 2 x 3 y 3 z 2 From router A to subsets:
- 61. 4. RIP (2): advertisements •Distance vectors: exchanged among neighbors every 30 sec via Response Message (also called advertisement) •Each advertisement: list of up to 25 destination nets within AS
- 62. 4. RIP (3): Example Destination Network Next Router Num. of hops to dest. w A 2 y B 2 z B 7 x -- 1 …. …. .... w x y z A C D B Routing table in D
- 63. 4. RIP (4) : Example Destination Network Next Router Num. of hops to dest. w A 2 y B 2 z B A 7 5 x -- 1 …. …. .... Routing table in D w x y z A C D B Dest Next hops w - 1 x - 1 z C 4 …. … ... Advertisement from A to D
- 64. 4. RIP (5): Link Failure and Recovery If no advertisement heard after 180 sec --> neighbor/link declared dead • routes via neighbor invalidated • new advertisements sent to neighbors • neighbors in turn send out new advertisements (if tables changed) • link failure info quickly propagates to entire net • poison reverse used to prevent ping-pong loops (infinite distance = 16 hops)
- 65. 4. RIP (6): Table processing RIP routing tables managed by application-level process called route-d (daemon) advertisements sent in UDP packets, periodically repeated physical link network forwarding (IP) table Transport (UDP) routed physical link network (IP) Transport (UDP) routed forwarding table
- 66. 4. OSPF (1) (Open Shortest Path First) •“open”: publicly available •Uses Link State algorithm – LS packet dissemination – Topology map at each node – Route computation using Dijkstra’s algorithm •OSPF advertisement carries one entry per neighbor router •Advertisements disseminated to entire AS (via flooding) • Carried in OSPF messages directly over IP (rather than TCP or UDP
- 67. 4. Hierarchical OSPF (2)
- 68. 4. Hierarchical OSPF (3) • Two-level hierarchy: local area, backbone. – Link-state advertisements only in area – each nodes has detailed area topology; only know direction (shortest path) to nets in other areas. • Area border routers: “summarize” distances to nets in own area, advertise to other Area Border routers. • Backbone routers: run OSPF routing limited to backbone. • Boundary routers: connect to other AS’s.
- 69. 5. BGP (1) • BGP (Border Gateway Protocol): the de facto standard • BGP provides each AS a means to: – Obtain subnet reachability information from neighboring ASs. – Propagate the reachability information to all routers internal to the AS. – Determine “good” routes to subnets based on reachability information and policy. • Allows a subnet to advertise its existence to rest of the Internet: “I am here”
- 70. 5. BGP (2): basics • Pairs of routers (BGP peers) exchange routing info over semi-permanent TCP connections: BGP sessions • Note that BGP sessions do not correspond to physical links. • When AS2 advertises a prefix to AS1, AS2 is promising it will forward any datagrams destined to that prefix towards the prefix. – AS2 can aggregate prefixes in its advertisement 3b 1d 3a 1c 2a AS3 AS1 AS2 1a 2c 2b 1b 3c eBGP session iBGP session
- 71. 5. BGP (3): Distributing reachability info •With eBGP session between 3a and 1c, AS3 sends prefix reachability info to AS1. •1c can then use iBGP do distribute this new prefix reach info to all routers in AS1. •1b can then re-advertise the new reach info to AS2 over the 1b-to-2a eBGP session. •When router learns about a new prefix, it creates an entry for the prefix in its forwarding table. 3b 1d 3a 1c 2a AS3 AS1 AS2 1a 2c 2b 1b 3c eBGP session iBGP session
- 72. 5. BGP (4): Path attributes & BGP routes • When advertising a prefix, advert includes BGP attributes. – prefix + attributes = “route” • Two important attributes: – AS-PATH: contains the ASs through which the advert for the prefix passed: AS 67 AS 17 – NEXT-HOP: Indicates the specific internal-AS router to next-hop AS. (There may be multiple links from current AS to next-hop-AS.) • When gateway router receives route advert, uses import policy to accept/decline.
- 73. 5. BGP (5): route selection • Router may learn about more than 1 route to some prefix. Router must select route. • Elimination rules: 1. Local preference value attribute: policy decision 2. Shortest AS-PATH 3. Closest NEXT-HOP router: hot potato routing 4. Additional criteria
- 74. 5. BGP (6): messages •BGP messages exchanged using TCP. •BGP messages: – OPEN: opens TCP connection to peer and authenticates sender – UPDATE: advertises new path (or withdraws old) – KEEPALIVE keeps connection alive in absence of UPDATES; also ACKs OPEN request – NOTIFICATION: reports errors in previous msg; also used to close connection
- 75. 5. BGP (7): routing policy Figure 4.5-BGPnew: a simple BGP scenario A B C W X Y legend: customer network: provider network •A,B,C are provider networks •X,W,Y are customer (of provider networks) •X is dual-homed: attached to two networks – X does not want to route from B via X to C – .. so X will not advertise to B a route to C
- 76. 5. BGP (8): routing policy Figure 4.5-BGPnew: a simple BGP scenario A B C W X Y legend: customer network: provider network •A advertises to B the path AW •B advertises to X the path BAW •Should B advertise to C the path BAW? – No way! B gets no “revenue” for routing CBAW since neither W nor C are B’s customers – B wants to force C to route to w via A – B wants to route only to/from its customers!
Editor's Notes
- #13: Robustness means RA should be able to cope with changes in the topology and traffic without requiring all jobs in all hosts to be aborted and the network to be rebooted every time some router crashes.
- #21: Different metric are possible with different means faster longer less delay By changing the weighting function, the algorithm would then compute the “shortest” path measured to any one of a number of criteria or to a combination of criteria.